Chapter 18. Security Concepts in SAP R/3 Query-Based Reporting Tools
In this chapter
Security for the SAP Query Tool 226
Security for the InfoSet (Ad Hoc) Query and QuickViewer Tools 228
This chapter addresses how you can configure the SAP environment to permit varying levels of use of the SAP Query tools to users. It does not have to do with what a person can see when executing a SAP query. Recall from Chapter 2, “One-Time Configuration for Query Tool Use,” that SAP standard logical databases are used whenever InfoSets are created. As noted in Chapter 2, you should always use logical databases as the data source within InfoSets that are used for query-based reporting. Using a logical database as your data source guarantees that the SAP solution is smart enough to know which areas of the data a user is allowed to see so that only the appropriate data will show in an SAP query report. Regardless of what type of security access the person who created the report has, the system is smart enough to display only the appropriate data for the user executing the report. (Note that this is the case only when logical databases are used as the data source if a SAP query is created using an InfoSet that is based on anything other than a logical database (for example, a table, a table join, a program). It is fair to say that no security whatsoever is in place when the query is run because all records within the tables are displayed in the report output.)
Note
Dedicated professionals in each organization are responsible for security. It is recommended that the security decisions, configuration, and administration described in this chapter be performed by those dedicated security professionals. The basics of how security works for SAP queries are described here so that you have a full picture of the reporting solution. I recommend that you follow your company’s established guidelines for modifying security roles and that you make the information in this chapter available to your designated security professionals. A system administrator can control access rights to the InfoSet (Ad Hoc) Query tool by using roles or query groups. Exactly one SAP query group must be assigned to a role (an InfoSet must be associated with the query group), although the user does not need to be listed in the query group. If users want to save their reports, they need authorization object S_QUERY, field ACTVT, value 02; otherwise, they can only create and execute reports.
Security for the SAP Query Tool
You can use two methods to ensure security for the SAP Query tool: query groups and authorizations. The following sections describe these two methods.
Using Query Groups to Provide Security for the SAP Query Tool
Chapter 2 mentions that a query group (known as a user group in versions of SAP prior to version 4.6) is a collection of SAP users who are grouped. A user’s assignment to a query group determines which queries he or she can execute or maintain. It also designates which InfoSets (that is, data sources) the user can access. Basically, query groups permit users to create, modify, and execute reports in a certain area within SAP R/3.
Using query groups is an easy way to group and segregate report users and reports. You can also use query groups as an avenue for security. For example, if a user is not placed in any query group, he or she cannot create or maintain queries. If you decide a user should not have access to SAP queries (via the Query tool’s initial entry screen, which you reach by using transaction code SQ01), you should simply not assign that user to any query groups. A user who is not assigned to any query groups cannot create, execute, or change any queries, because he or she is unable to access the screen to do so by using transaction code SQ01.
SAP Query reports can also be assigned to transaction codes so that users who do not belong to a query group and/or do not have access to transaction code SQ01 can access them.
Using Authorizations to Provide Security for the SAP Query Tool
The specific authorization object for the SAP Query tool is S_QUERY. The security administrator can set the field ACTVT for the authorization object to designate that a user can create, configure, or translate (for multiple language configurations) SAP queries. A security administrator can use the information shown in Table 18.1 to assign authorizations specific to the ACTVT authorization object. These authorizations are valid within both standard and global query areas. (See Chapter 1, “Getting Started with the SAP R/3 Query Reporting Tools,” for more information on application areas.)
Table 18.1. Assigning Authorizations Specific to the ACTVT Object
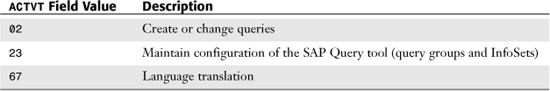
Authorizations for Creating or Changing Queries (ACTVT= 02)
Users need the ACTVT value set to 02 to create new SAP queries and/or modify existing queries via the main SAP Query tool screen found via transaction code SQ01.
Authorizations for Maintaining Configuration of SAP Query (Query Groups and InfoSets) (ACTVT = 23)
As discussed in Chapters 1 and 2, the process of configuring the SAP Query tool, including the creation of query groups and InfoSets, is very easy to do but should be done only by a trained technical person within the development environment of a SAP solution. A user who will be responsible for this configuration needs to have the ACTVT value set to 23.
If a technical developer will be expanding the use of the logical database to include any custom programs or ABAP, he or she needs to have authorization for maintaining the authorization object S_DEVELOP with the value PROG for field OBJTYPE and the value AQ* for the field OBJNAME. This authorization should be given only to trained ABAP programmers in the development environment. It is the same authorization that a user needs to access the ABAP Editor (via transaction code SE38) to create or change programs whose names begin with AQ. Users who can create and maintain InfoSets without this special designation can only select fields, connect additional tables or structures, and define parameters and selection criteria.
Authorizations for Language Comparison
SAP’s language translation capabilities make it possible for end users to customize the text elements (named objects) within their SAP solution for multiple languages. When a user creates an SAP query, he or she begins by inputting a title in the language the user logged in with. As with all other named objects entered by the user, these objects exist in SAP in the user’s logon language. Language translation is possible such that a user can enter the equivalent named object text in another language to accommodate a user who will be logging on to the solution in a different language. Users need the ACTVT value set to 67 to utilize the language comparison utility.
Users who have authorization for the authorization object S_QUERY with both the values 02 and 23 have authorization to access all queries of all query groups without being explicitly entered in each query group.
Helpful Hint
If a query accesses a certain table when it is run, the user needs display authorization for authorization object S_TABU_DIS. The field DICBERCLS must contain the table’s authorization groups. This sophisticated authorization object protects SAP tables from unauthorized access. It is important to note that this is the same authorization that you need to be able to display tables using either the Data Browser (transaction SE16) or the initial table maintenance screen (transaction SM31).
Security for the InfoSet (Ad Hoc) Query and QuickViewer Tools
You can use two methods to ensure security for the InfoSet (Ad Hoc) Query tool and the QuickViewer tool: query groups and roles. The following sections describe these two methods.
Using Query Groups to Provide Security for the InfoSet (Ad Hoc) Query and QuickViewer Tools
You control access rights to the InfoSet (Ad Hoc) Query and QuickViewer tools by using query groups exactly the same way as you do with the SAP Query tool, as described earlier in this chapter, in the section “Using Query Groups to Provide Security for the SAP Query Tool.”
Using Roles to Provide Security for the InfoSet (Ad Hoc) Query and QuickViewer Tools
Exactly one query group (with InfoSets assigned) must be assigned to a role. It is not required to enter or select individual usernames in the query group, because they are assigned in the role assignment. This means that a user who is assigned to a role is automatically copied into the query group assigned to the role. This assignment functions only when the user uses the role to navigate to (that is, call) the InfoSet (Ad Hoc) Query or QuickViewer tools. If the InfoSet (Ad Hoc) Query or QuickViewer tools are accessed via another method, the traditional access authorization implemented using SAP query groups is applicable. For a user to be able to save InfoSet queries or QuickViews, he or she needs authorization object S_QUERY, with the field ACTVT set to 02. If the user does not have this authorization, he or she can execute the available InfoSets and queries within the role, but he or she cannot save queries.
Things to Remember
• The configuration of security for any area within SAP should be performed by a trained SAP security administrator.
• Options for SAP Query tool authorizations are based on query groups and authorizations.
• Restricting users based on query groups is an easy way of limiting their access.
• Options for InfoSet (Ad Hoc) Query tool and QuickViewer tool authorizations are based on query groups and roles.
• A special security authorization is required for users to be able to use the language translation facility.
