We can summarize the end user interaction in four steps, as follows:
- After PAM is deployed, a user in one of the corporate forests (for us TFC), will request the role activation (some sort of elevation) of a secondary account that resides in a managed domain. If the request is performed via the PowerShell cmdlet, then a call is made directly to the MIM service, whereas if a custom PAM client is used, then the call is made to the REST API first, which interacts with the MIM service.
- If the role request requires approval, then we will wait for approval. In Windows 2012 R2 deployments, once approved or autoapproved, the MIM service account (in the management forest) adds the end user's secondary account (in the management forest) to a shadow group (in the management forest). The SID of the sourced TFC group will be in the shadow group's SID History. Note that we did not change the membership of any TFC groups; however, you will see the shadow group membership change.
- The person then authenticates and works with the account that is granted time sensitive privileges, which could be 30 minutes or whatever is defined in the role. If we were to look at the Kerberos group membership of the elevated account (in the management forest), it would have membership of the corporate group and the shadowed group.
- After the role request expires, the account (in the management forest) is removed from the shadow group (in the management forest) by the PAM component service account in Windows 2012 R2 deployments. As already noted, the PAM component service is not used in Windows 2016 deployments and is handled by the server directly without the need for an extra MIM PAM service.
If the PAM component removes group membership in the management domain, what does the PAM monitor service provide? The PAM monitor watches the account state as well as five Active Directory attributes. For the state, the PAM monitor checks to see whether the account is disabled, locked, or deleted and will synchronize the states with their corresponding PRIV accounts:
- The
ACCOUNTDISABLEflag ofuserAccountControl, which specifies whether the account is enabled or disabled - The
LOCK_OUTflag ofms-DS-User-Account-Control-Computed, which specifies whether the account is locked out.
The PAM monitor additionally synchronizes the sAMAccountName, domain, phoneNumber, and mail attributes.
If TFCJIngalls has a PAM user account named PRIVPriv.JIngalls, when the TFCJIngalls Active Directory account is disabled, the PAM monitor service account will disable PRIVPriv.JIngalls. The same applies when the TFC account is locked out or if one of the attributes listed before changes. Further, if the TFCJingalls account is deleted, PRIVJingalls will be deleted:
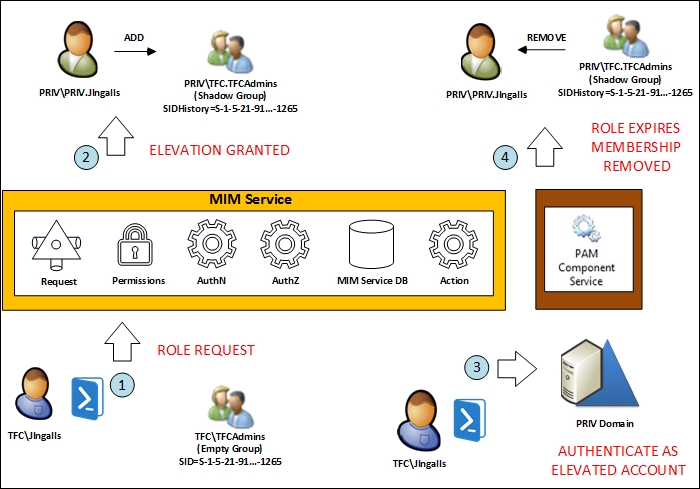
The expiration of the
access elevation does not use temporal resources, as in the MIM portal. For Windows 2012 R2 deployments, PAM request expiration is handled by a new component called the PAM component service. The Windows 2016 server has built-in mechanisms to handle request expiration. In our example, we will use PowerShell to do this, although a custom client could be used to handle PAM requests and approvals too. Also, note that the PAM clients and the PAM REST API talk directly to the MIM service. The PAM clients could be in the privileged forest or in the corporate forest(s) as long as the clients can communicate to the MIM service (ports 5725 and 5726), which exists in the privileged forest.
