A database stores data and organizes it in some sort of logical manner. Oracle and Microsoft SQL are popular examples of database management systems that allow users to create multiple types of databases used to store, query, and organize data in creative ways.
Structured Query Language, which is better known as SQL, is the underlining common programing language that is understood by most database management systems. It provides a common way for application to access the data in the database by using a common set of commands the database can understand.
Attackers exploit these databases by making them output information that they should not be displaying. Sometimes this is as simple as the attacker asking for privileged information from the database management system. Other times, it is taking advantage of poor configurations by database administrators. Attackers may also take advantage of a vulnerability in the database management system that allows the attacker to view or write privileged commands to and from the database.
Attackers typically send malicious code through forms or other parts of a webpage that have the ability to accept user input. For example, an attacker may enter random characters, as well as long statements, with the goal of identifying weakness in how the input variables and parameters are designed. If an input field is set to only accept usernames up to 15 characters long, an error message may appear revealing details about how the database is configured.
The Firefox plugin HackBar will let you test SQL queries and inject your own queries for changing SQL requests. The HackBar plugin will also let a Penetration Tester examine HTTP post information.

In the following example, we will try to perform a SQL injection on the website DrChaos.com. Let's navigate to www.DrChaos.com using Firefox on our Kali server console and try to log into the website. First, we will try the username administrator and the password 12345 to login. You should see that will fail.
Now, navigate to the View menu bar in Firefox and select the HackBar menu. Click the Load URL button and click the Enable Post data button. You will see the URL we were logging into as well as the username and password we just attempted.
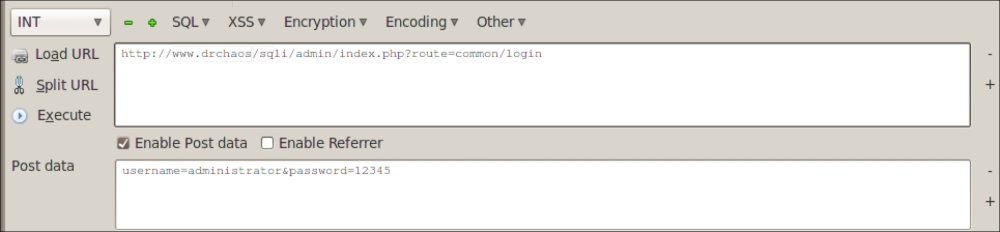
We will now add a single quotation mark after the administrator username. Soon as we click on the Execute button, we receive a SQL injection. This may mean the server is vulnerable to SQL injection, because the server is responding to SQL errors.

We will put in SQL injection by adding an OR 1=1 ## statement at the end of the line.

Once we execute the code, we are logged on as administrator to www.drchaos.com.
We have patched www.DrChaos.com so it is no longer vulnerable to this attack. However, you can see SQL injections are very valuable to attack, because they give a web Penetration Tester an easy method to gain full access to a system.
SQL injection success is dependent on the attackers knowledge of SQL commands. If you need to brush up on your SQL skills, we recommend looking at W3 School of SQL at: http://www.w3schools.com/sql/sql_intro.asp.
sqlmap automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. sqlmap comes with a detection engine, as well as a broad range of Penetration Testing features that range from database fingerprinting to accessing the underlying file system and executing commands on the operating system via out-of-band connections.
Features include support for common database management systems, support for many SQL injection techniques, enumerating users, password hashes, and many others. sqlmap also supports database process' user privilege escalation using Metasploit's Meterpreter getsystem command.
sqlmap is a tool that can be used to exploit database servers and is built into Kali. To use sqlmap, you will need to point the tool to a URL of a SQL script on a webserver. These can be identified because they usually have php in the URL.
You can find sqlmap under Vulnerabilty Analysis | Database Assessment | sqlmap. A Terminal window will open displaying the sqlmap help page.
The basic syntax to use sqlmap is:
sqlmap –u URL -- function
A common function is dbs. The dbs keyword will have sqlmap get the databases.
sqlmap -u http://www.drchaous.com/article.php?id=5 --dbs
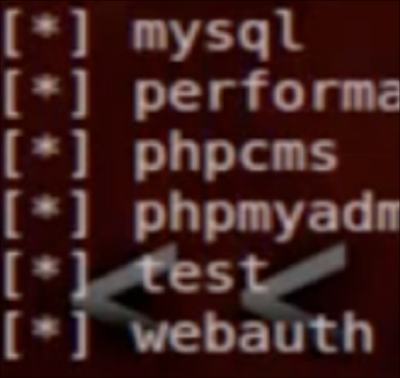
You can see from our results we have several databases that were found. For this example, we will concentrate on the test database.
Once you have found a vulnerable web server, you select the database by using the –D command and the name of the database.
sqlmap –u http://www.drchaos.com/article.php?id=5 -D test --tables
The table keyword is used to retrieve all the tables in the test database on our web server. We see we have successfully retrieved two tables, admin and content.

Once you issue the following command, sqlmap will display all tables:
sqlmap -u http://www.drchaous.com/article.php?id=5 -D test --tables
Specific columns can be selected by using the following command:
sqlmap -u http://www.drchaous.com/article.php?id=5 -T tablesnamehere --columns
If there is any relevant information in the tables, it can be retrieved using the following command:
sqlmap -u http://www.drchaous.com/article.php?id=5 -T tablesnamehere -U test --dump -U test –dump
This will create a file named test, and dump all the raw information from the database table to that file. In many cases, this can include passwords and other sensitive information.
