Kali Linux offers many tools that could be useful for web-based attacks. Here are some additional tools available in Kali Linux that have not been covered and could be used for remote Penetration Testing.
DNSChef is a DNS proxy for Penetration Testers and Malware Analysts. A DNS proxy also known as "Fake DNS" is a tool used for application network traffic analysis and other use cases. Domain Name System (DNS) is a distributed naming system for computers, services, or any resource connected to the Internet or private network. Providing fake DNS addresses can redirect traffic to other desired locations.
For example, a DNS proxy can be used to fake requests for badguy.com to point to a local machine for termination or interception instead of a real host somewhere on the Internet. For this to work, you need to gain access and modify DNS entries on a single server or poison the real DNS so that traffic gets to the Kali Linux server. The DNSChef tool is easy to use; however, the challenge is the DNS attack method to direct traffic to Kali Linux.

SniffJoke handles your TCP connection transparently, providing delay, modifying, and injecting fake packets inside your transmission. This process makes it extremely difficult for a passive wiretapping technology such as an IDS/IPS or sniffer to interpret the traffic correctly. This is done by exploiting what is presumed recorded by a sniffer and what is transmitted by the client, making this inconsistent for the algorithm of packet reassembly. The next two diagrams showcase wiretapping traffic between two users without and with SniffJoke.


Siege is a HTTP/HTTPS stress testing utility designed for web developers to measure the performance of their code under duress. Siege offers multi-threaded HTTP load testing and benchmarking by hitting a web server with a configurable number of concurrent, simulated users. Siege offers a regression, Internet simulation and brute force modes.
You can find Siege under Stress Testing | Network Stress Testing | Siege:
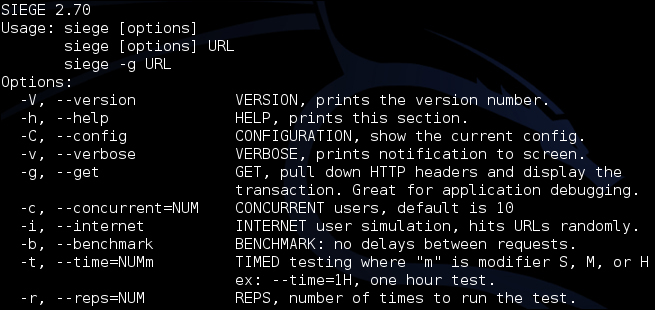
To run Siege, type the following command:
siege [options] <target URL>
The following screenshot shows running Siege against www.thesecurityblogger.com. The default user count is 15, as shown in the screenshot. When you stop the Siege testing, the tool provides a report post stress test as follows:


Inundator is a tool that evades Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) by flooding their log files. The concept is that you may want to flood a target with false positives so you can hide a real attack from a reaction and forensic viewpoint. Inundator can also be used to test the effectiveness of the alerting system of your security reporting tools, such as SIEM and IDS/IPS.
TCPReplay uses previously captured traffic in libpcap format to test a variety of network devices. TCPReplay can classify traffic as client or server, rewrite Layer 2, 3, and 4 headers and replay the traffic back onto the network as well as through other devices, such as switches, routers, firewalls, and IDS/IPS. TCPReplay supports single and dual NIC modes for testing both sniffing and inline devices.
Basically, TCPReplay can capture traffic between a client and server, and replay it anywhere in the network.
