We examined the basics of the Social Engineering Toolkit (SET) in Chapter 4. We are going to revisit SET and look at some advanced concepts of password harvesting and capturing privileged information.
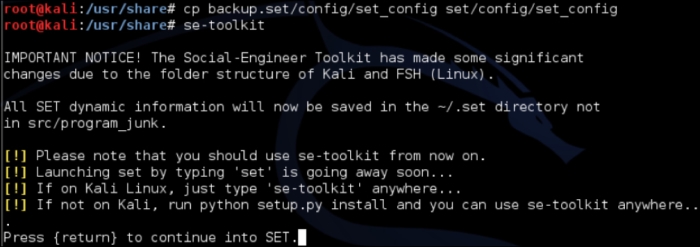
As a refresher, we will launch SET by going to Exploitation Tools | Social Engineering Tools | se-toolkit.
Make sure SET is updated if this if the first time using it. Steps for updating SET and verifying whether GIT is installed can be found in Chapter 4.
Tip
When SET clones a website, it will run a web server. It is important that whoever is being targeted is able to connect to your web server. This means any Internet-based attack will need to leverage a public IP address (either through NAT or directly on Kali Linux), as well as opening firewall rules to permit access to Kali from a remote location.
Once you have taken care of any IP configurations, it is time to launch SET:
We will now use SET to harvest passwords. SET has the ability to clone any website you want. We are actually going to pick one of the most popular social engineering sites in this example to clone. Agree to any license agreements you may come across with SET:

Tip
Selecting option 5 is recommended to update SET prior to using the tool to ensure you have the latest updates. If you receive an error stating no GIT repositories exist, you may have installed GIT incorrectly, or the steps have changed since the writing of this text. Refer to the publisher's website, Aamir Lakhani's blog at www.DrChaos.com or Joseph Muniz's blog at www.thesecurityblogger.com for more tricks on using SET with Kali Linux.
You have a few choices on how you want to clone a website. SET has templates for popular sites, such as Facebook and Gmail. Sometimes these templates don't work; however, we recommended starting with these or cloning another website. To clone a website, you need a URL, and SET will automatically try to clone it.
If you already have cloned a website or have the HTML files loaded on Kali, you can select custom import. When you select this option, you will need to tell Kali where the HTML files are located on the local file system.
For our example, we will choose web templates. SET will ask on what IP address it should listen. This will be the IP address for the interface on Kali Linux. The exception to this is when using NAT on a firewall. In that case, you will need to use the NAT or public address rather than IP address on Kali Linux so that targets can access the system. The next example will use the local loopback address of 127.0.0.1.
Next, SET will ask to select a template. For this example, we will select Facebook.
The next example shows a web browser going to 127.0.0.1 and displaying our fake Facebook page. If a template page does not look quite right, you may want to use a different template or clone the desired page:

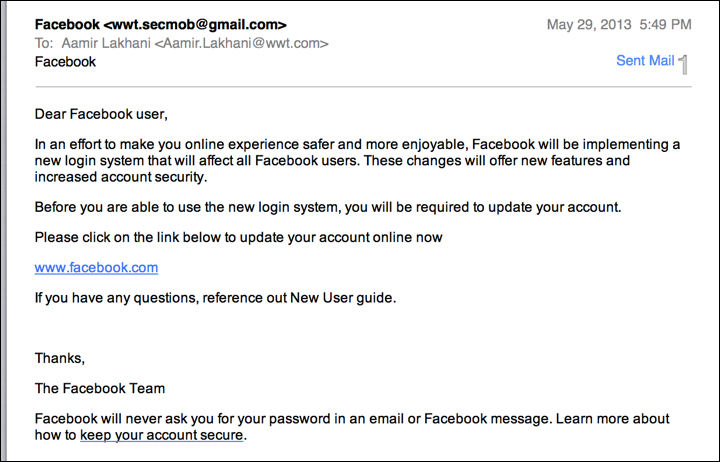
Notice our address bar states 127.0.0.1. Typically, you will need to use some other attack vector to fool users to go to your website. There are numerous ways to do this, such as sending them a link or a fake email:
When we enter our username in the fake Facebook website, SET captures the traffic. SET will also redirect users to the real website. The hope is that the victims will believe they entered their password wrong when redirected to the real Facebook and continue using Facebook without knowing that SET captured their login credentials:
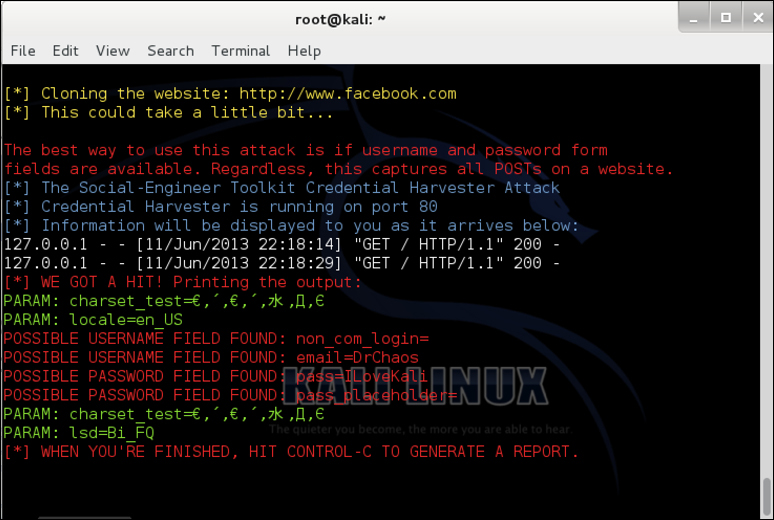
The previous example shows SET had captured our username: DrChaos, and our Password as ILoveKali.
When you have completed this exercise, press Ctrl +C to exit the SET tool, and generate an HTML report. SET creates a professional report that can be used in your Penetration Test reports: