Fimap is a Python tool that can find, prepare, audit, exploit and Google automatically for local and remote file Inclusion (LFI and RFI) bugs in web applications.
Fimap can be found under Web Applications | Web Vulnerability Scanners | Fimap. When you open Fimap, a terminal window opens displaying the home screen. Fimap has a few plugin options, which you can download by using the following command:
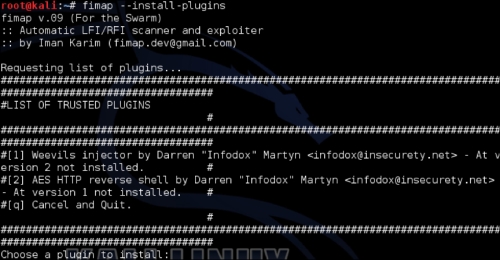
fimap --install –plugins
All available plugins will be displayed as a list, with the option to select one to install or else quit. In the following example, there are two available plugins to install. You will have to run the install command twice to install each plugin individually:
To use Fimap, you first need to determine your target by specifying the URL. There are options for specifying a URL, a list of URLs using Google to acquire URLs, or other methods such as harvesting URLs from other URLs, as well as looking at forms and headers. For the following example, we will target www.thesecurityblogger.com.
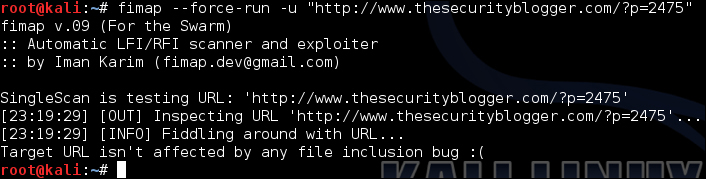
To scan thesecurityblogger.com website, type the following command:
fimap -u 'http://wwwthesecurityblogger.com'
Fimap will attempt to identify any file inclusion vulnerabilities. The following example shows that our target is not vulnerable to a file inclusion attack: