Day 30 Network Models and Applications
CCNA 640-802 Exam Topics
![]() Describe common networked applications, including web applications.
Describe common networked applications, including web applications.
![]() Describe the purpose and basic operation of the protocols in the OSI and TCP models.
Describe the purpose and basic operation of the protocols in the OSI and TCP models.
![]() Describe the impact of applications (Voice over IP and Video over IP) on a network.
Describe the impact of applications (Voice over IP and Video over IP) on a network.
Key Points
As a new student to networking, one of the very first topics you probably learned was the layers of the OSI and TCP/IP models. Now that you have completed your studies and are reviewing for the CCNA exam, you more than likely can see the benefit of using these models. Each helps our understanding of networks in its own way. Today we review the OSI and TCP/IP models, as well as the applications and protocols that are commonly used in networks.
The OSI and TCP/IP Models
To understand how communication occurs across the network, we use layered models as a framework for representing and explaining networking concepts and technologies. Network models provide a variety of benefits:
![]() Reduce complexity
Reduce complexity
![]() Standardize interfaces
Standardize interfaces
![]() Assist understanding
Assist understanding
![]() Promote rapid product development
Promote rapid product development
![]() Support interoperability
Support interoperability
![]() Facilitate modular engineering
Facilitate modular engineering
Initially, networks were built on proprietary standards and hardware. Layered models, such as the TCP/IP and OSI models, support interoperability between competing vendor product lines.
The OSI model development began in the 1970s with the goal to provide a standards-based suite of protocols that would allow communication between all computer systems. Although the U.S. government required the use of OSI products in the 1980s and 1990s, the Defense Advanced Research Projects Agency (DARPA) under the Department of Defense—and with the help of researchers at various universities—had designed the competing TCP/IP model. For various reasons, including the popularity of TCP/IP, by 1983 the ARPANET had chosen TCP/IP as its principle protocol suit. By 1994, all U.S. government agencies were required to switch over from OSI protocols to TCP/IP.
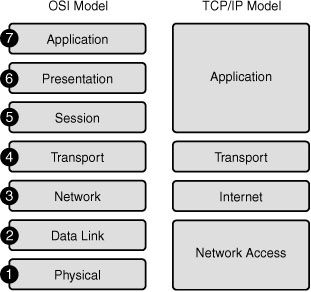
Today, we use the OSI model principally as a tool for explaining networking concepts. However, the protocols of the TCP/IP suite are the rules by which networks now operate. Because both models are important, you should be well versed in each model’s layers as well as how the models map to each other. Figure 30-1 summarizes the two models.
It can be confusing using two models. However, this simple rule might help. When discussing layers of a model, we are usually referring to the OSI model. When discussing protocols, we are usually referring to the TCP/IP model. So let’s quickly review the OSI layers and the TCP/IP protocols.
OSI Layers
Table 30-1 summarizes the layers of the OSI model and provides a brief functional description.
The following mnemonic phrase where the first letter represents the layer (“A” stands for “Application”) can be helpful to memorize the name and order of the layers from top to bottom.
All People Seem To Need Data Processing
TCP/IP Layers and Protocols
The TCP/IP model defines four categories of functions that must occur for communications to be successful. Most protocol models describe a vendor-specific protocol stack. However, because the TCP/IP model is an open standard, one company does not control the definition of the model.
Table 30-2 summarizes the TCP/IP layers, their functions, and the most common protocols.
In coming days, we will review these protocols in more detail. For now, a brief description of the main TCP/IP protocols follows:
![]() Domain Name System (DNS): Provides the IP address of a website or domain name so a host can connect to it.
Domain Name System (DNS): Provides the IP address of a website or domain name so a host can connect to it.
![]() Telnet: Allows administrators to log in to a host from a remote location.
Telnet: Allows administrators to log in to a host from a remote location.
![]() Simple Mail Transfer Protocol (SMTP), Post Office Protocol (POP3), and Internet Message Access Protocol (IMAP): Used to send email messages between clients and servers.
Simple Mail Transfer Protocol (SMTP), Post Office Protocol (POP3), and Internet Message Access Protocol (IMAP): Used to send email messages between clients and servers.
![]() Dynamic Host Configuration Protocol (DHCP): Assigns IP addressing to requesting clients.
Dynamic Host Configuration Protocol (DHCP): Assigns IP addressing to requesting clients.
![]() Hypertext Transfer Protocol (HTTP): Used to transfer information between web clients and web servers.
Hypertext Transfer Protocol (HTTP): Used to transfer information between web clients and web servers.
![]() File Transfer Protocol (FTP): Allows the download and upload of files between an FTP client and FTP server.
File Transfer Protocol (FTP): Allows the download and upload of files between an FTP client and FTP server.
![]() Simple Network Management Protocol (SNMP): Used by network management systems to monitor devices attached to the network.
Simple Network Management Protocol (SNMP): Used by network management systems to monitor devices attached to the network.
![]() Transmission Control Protocol (TCP): Allows virtual connections between hosts on the network to provide reliable delivery of data.
Transmission Control Protocol (TCP): Allows virtual connections between hosts on the network to provide reliable delivery of data.
![]() User Datagram Protocol (UDP): Allows faster, unreliable delivery of data that is either lightweight or time-sensitive.
User Datagram Protocol (UDP): Allows faster, unreliable delivery of data that is either lightweight or time-sensitive.
![]() Internet Protocol (IP): Provides a unique global address to computers for communicating over the network.
Internet Protocol (IP): Provides a unique global address to computers for communicating over the network.
![]() Address Resolution Protocol (ARP): Finds a host’s hardware address when only the IP address is known.
Address Resolution Protocol (ARP): Finds a host’s hardware address when only the IP address is known.
![]() Internet Control Message Protocol (ICMP): Used to send error and control messages including reachability to another host and availability of services.
Internet Control Message Protocol (ICMP): Used to send error and control messages including reachability to another host and availability of services.
![]() Ethernet: The most popular LAN standard for framing and preparing data for transmission onto the media.
Ethernet: The most popular LAN standard for framing and preparing data for transmission onto the media.
![]() Frame Relay: Also a framing standard; one of the most cost-effective WAN technologies used to connect LANs.
Frame Relay: Also a framing standard; one of the most cost-effective WAN technologies used to connect LANs.
Protocol Data Units and Encapsulation
As application data is passed down the protocol stack on its way to be transmitted across the network media, various protocols add information to it at each level. This is commonly known as the encapsulation process. The data structure at any given layer is called a protocol data unit (PDU). Table 30-3 lists the PDUs at each layer of the OSI model.
The communication process from any source to any destination can be summarized with the following steps:
-
Creation of data at the application layer of the originating source end device
-
Segmentation and encapsulation of data as it passes down the protocol stack in the source end device
-
Generation of the data onto the media at the network access layer of the stack
-
Transportation of the data through the internetwork, which consists of media and any intermediary devices
-
Reception of the data at the network access layer of the destination end device
-
Decapsulation and reassembly of the data as it passes up the stack in the destination device
-
Passing this data to the destination application at the application layer of the destination end device
Growth of Network-Based Applications
Besides all the common applications we discuss in networking studies, programmers and entrepreneurs are continuously developing applications to take advantage of network resources and the Internet. Today, people create, store, and access information as well as communicate with others on the network using a variety of applications. In addition to the traditional email and web browser applications, people are increasingly using newer forms of communication including instant messaging, blogs, podcasting, peer-to-peer file sharing, wikis, and collaborative tools that allow viewing and working on documents simultaneously. The online gaming industry has grown exponentially over the past several years. All these applications and online experiences place great demands on the network infrastructure and resources. One way of handling the sheer volume of data is to rank packets based on the quality of service that the source application needs—especially considering the increased use of the network in general and the recent rise of voice and video applications that have a very low tolerance for delay and jitter.
Quality of Service
The priority and guaranteed level of service to the flow of data through the network is increasingly important as new applications place greater demands on the processing power and bandwidth of the networks we use. When we place a call over an IP phone, we want at least as good a service as we receive on a traditional land line. Therefore, networks need to use quality of service (QoS) mechanisms to ensure that limited network resources are prioritized based on traffic content. Without QoS implementation, an email message or web page request crossing a switch or a router will have the same priority as voice or video traffic.
Each type of application can be analyzed in terms of its QoS requirements on the network, so if the network meets those requirements, the application will work well.
Increased Network Usage
Applications have tended to increase the need for more bandwidth while demanding lower delay. Here are some of the types of data applications that have entered the marketplace and their impact on the network:
![]() Graphics-capable terminals and printers: Increased the required bytes for the same interaction as the old text-based terminals and printers.
Graphics-capable terminals and printers: Increased the required bytes for the same interaction as the old text-based terminals and printers.
![]() File transfers: Introduced much larger volumes of data, but with no significant response time requirements.
File transfers: Introduced much larger volumes of data, but with no significant response time requirements.
![]() File servers: Allow users to store files on a server—which might require a large volume of data transfer, but with a much smaller end-user response time requirement.
File servers: Allow users to store files on a server—which might require a large volume of data transfer, but with a much smaller end-user response time requirement.
![]() The maturation of database technology: Making vast amounts of data available to casual users, vastly increasing the number of users wanting access to data.
The maturation of database technology: Making vast amounts of data available to casual users, vastly increasing the number of users wanting access to data.
![]() The migration of common applications to web browsers: Encourages more users to access data.
The migration of common applications to web browsers: Encourages more users to access data.
![]() The growth of email: The general acceptance of email as both a personal and business communications service has greatly increased the amount of email traffic.
The growth of email: The general acceptance of email as both a personal and business communications service has greatly increased the amount of email traffic.
![]() The rapid commercialization of the Internet: Enabling companies to offer data directly to their customers via the data network rather than via phone calls.
The rapid commercialization of the Internet: Enabling companies to offer data directly to their customers via the data network rather than via phone calls.
The Impact of Voice and Video on the Network
Currently, voice and video are in the midst of a migration to traditional IP data networks. Before the late 1990s, voice and video used separate networking facilities. Most companies today are either migrating or plan to migrate to IP phones, which pass voice data over the data network inside IP packets using application protocols generally referred to as voice over IP (VoIP).
Figure 30-2 show a few details of how VoIP works from a home high-speed Internet connection, with a generic voice adapter (VA) converting the analog signal from a normal telephone to an IP packet.
VoIP does not place a demand on the network for additional capacity. A voice call typically consumes less than 30 kbps of bandwidth. However, VoIP is sensitive to delay, jitter, and packet loss:
![]() Low delay: VoIP requires a very low delay between the sending phone and the receiving phone—typically less than 200 milliseconds (.2 seconds). This is a much lower delay than what is required by typical data applications.
Low delay: VoIP requires a very low delay between the sending phone and the receiving phone—typically less than 200 milliseconds (.2 seconds). This is a much lower delay than what is required by typical data applications.
![]() Low jitter: Jitter is the variation in delay. VoIP requires very low jitter as well, whereas data applications can tolerate much higher jitter. For example, the jitter for consecutive VoIP packets should not exceed 30 milliseconds (.03 seconds) or the quality degrades.
Low jitter: Jitter is the variation in delay. VoIP requires very low jitter as well, whereas data applications can tolerate much higher jitter. For example, the jitter for consecutive VoIP packets should not exceed 30 milliseconds (.03 seconds) or the quality degrades.
![]() Loss: If a VoIP packet is lost in transit because of errors or because a router doesn’t have room to store the packet while waiting to send it, the lost VoIP packet is not retransmitted across the network. Lost packets can sound like a break in the sound of the VoIP call.
Loss: If a VoIP packet is lost in transit because of errors or because a router doesn’t have room to store the packet while waiting to send it, the lost VoIP packet is not retransmitted across the network. Lost packets can sound like a break in the sound of the VoIP call.
Video over IP has the same performance issues as voice. However, video requires a lot more bandwidth—anywhere from 300 kbps to 10 Mbps, depending on the quality demanded.
To support the QoS requirements of voice, video, and other quality or time-sensitive applications, routers and switches can be configured with a variety of QoS tools. These configurations are beyond the scope of the CCNA exam topics.