Day 8 Mitigating Security Threats and Best Practices
CCNA 640-802 Exam Topics
![]() Describe today’s increasing network security threats and explain the need to implement a comprehensive security policy to mitigate the threats.
Describe today’s increasing network security threats and explain the need to implement a comprehensive security policy to mitigate the threats.
![]() Explain general methods to mitigate common security threats to network devices, hosts, and applications.
Explain general methods to mitigate common security threats to network devices, hosts, and applications.
![]() Describe the functions of common security appliances and applications.
Describe the functions of common security appliances and applications.
![]() Describe security recommended practices including initial steps to secure network devices.
Describe security recommended practices including initial steps to secure network devices.
Key Topics
Security is a fundamental component of every network design. Attacks that previously required an advanced knowledge in computing can now be done with easily downloaded and freely available tools that any average computer-literate person can figure out how to use. Security is clearly a big issue, and one that requires serious attention. For the purposes of the exam topics for today, the goal is to review some of the basic terminology, types of security issues, and some of the common tools used to mitigate security risks.
The Importance of Security
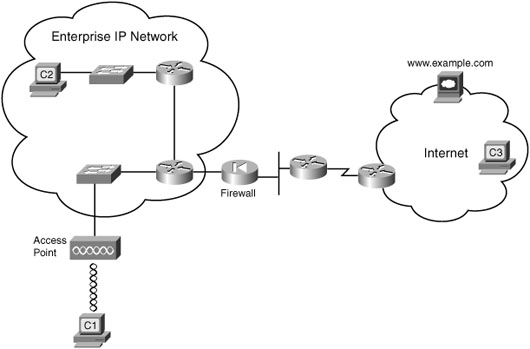
Attacks can be launched from various locations both inside and outside the organization, as shown in Figure 8-1.
As e-business and Internet applications continue to grow, finding the balance between being isolated and being open is critical. In addition, the rise of mobile commerce and wireless networks demands that security solutions become seamlessly integrated, more transparent, and more flexible. Network administrators must carefully balance accessibility to network resources with security.
Attacker Terminology
Over the years, network attack tools and methods have evolved, as well as the terminology to describe the individuals involved. Some of the most common terms are the following:
![]() White hat: An individual who looks for vulnerabilities in systems or networks and then reports these vulnerabilities to the system’s owners so that they can be fixed.
White hat: An individual who looks for vulnerabilities in systems or networks and then reports these vulnerabilities to the system’s owners so that they can be fixed.
![]() Hacker: A general term that has historically been used to describe a computer programming expert. More recently, this term is often used in a negative way to describe an individual with malicious intent who attempts to gain unauthorized access to network resources.
Hacker: A general term that has historically been used to describe a computer programming expert. More recently, this term is often used in a negative way to describe an individual with malicious intent who attempts to gain unauthorized access to network resources.
![]() Black hat: Another term for individuals who use their knowledge of computer systems to break into systems or networks that they are not authorized to use.
Black hat: Another term for individuals who use their knowledge of computer systems to break into systems or networks that they are not authorized to use.
![]() Cracker: Someone with malicious intent who tries to gain unauthorized access to network resources.
Cracker: Someone with malicious intent who tries to gain unauthorized access to network resources.
![]() Phreaker: An individual who manipulates the phone network to cause it to perform a function that is not allowed, such as to make free long-distance calls.
Phreaker: An individual who manipulates the phone network to cause it to perform a function that is not allowed, such as to make free long-distance calls.
![]() Spammer: An individual who sends large quantities of unsolicited email messages.
Spammer: An individual who sends large quantities of unsolicited email messages.
![]() Phisher: Uses email or other means to masquerade as a trusted party so that victims are enticed into providing sensitive information, such as credit card numbers or passwords.
Phisher: Uses email or other means to masquerade as a trusted party so that victims are enticed into providing sensitive information, such as credit card numbers or passwords.
Thinking Like an Attacker
Many attackers use this seven-step process to gain information and start an attack:
Step 1 Perform footprint analysis (reconnaissance).
A company web page can lead to information, such as the IP addresses of servers. From there, an attacker can create a picture of the company’s security profile or “footprint.”
Step 2 Enumerate information.
An attacker can expand on the footprint by monitoring network traffic with a packet sniffer such as Wireshark, finding useful information such as version numbers of FTP servers and mail servers.
Step 3 Manipulate users to gain access.
Sometimes employees choose passwords that are easily crackable. In other instances, employees can be duped by talented attackers into giving up sensitive access-related information (social engineering).
Step 4 Escalate privileges.
After attackers gain basic access, they use their skills to increase their network privileges.
Step 5 Gather additional passwords and secrets.
With improved access privileges, attackers use their talents to gain access to well-guarded, sensitive information.
Step 6 Install back doors.
Back doors give the attacker a way to enter the system without being detected. The most common back door is an open listening TCP or UDP port.
Step 7 Leverage the compromised system.
After a system is compromised, an attacker uses it to stage attacks on other hosts in the network.
Balancing Security and Availability
Organizations must find a balance between two important needs:
![]() Keeping networks open to support evolving business requirements
Keeping networks open to support evolving business requirements
![]() Protecting private, personal, and strategic business information
Protecting private, personal, and strategic business information
To address these needs, network security models follow a progressive scale. On one end is “open,” which means that any service is permitted unless it is expressly denied. Although the security risks are self-evident, there are some advantages to an open network:
![]() Easy to configure and administer.
Easy to configure and administer.
![]() Easy for end users to access network resources.
Easy for end users to access network resources.
![]() Security costs are much less.
Security costs are much less.
On the other end is the most restrictive network system, which means that services are denied by default unless deemed necessary. Although the benefits of implementing a completely restrictive network system are evident, it does present some drawbacks:
![]() More difficult to configure and administer.
More difficult to configure and administer.
![]() More difficult for end users to access resources.
More difficult for end users to access resources.
![]() Security costs are greater than those for an open network.
Security costs are greater than those for an open network.
Developing a Security Policy
The first step any organization should take to protect its data and itself from a liability challenge is to develop a security policy. A security policy is a set of principles that guides decision-making processes and enables leaders in an organization to distribute authority confidently. A security policy can be as simple as a brief “Acceptable Use Policy” for network resources, or it can be several hundred pages long and detail every element of connectivity and associated policies.
A security policy meets the following goals:
![]() Informs users, staff, and managers of their obligations for protecting technology and information assets.
Informs users, staff, and managers of their obligations for protecting technology and information assets.
![]() Specifies the mechanisms through which these requirements can be met.
Specifies the mechanisms through which these requirements can be met.
![]() Provides a baseline from which to acquire, configure, and audit computer systems and networks for compliance with the policy.
Provides a baseline from which to acquire, configure, and audit computer systems and networks for compliance with the policy.
Common Security Threats
When discussing network security, three common factors are vulnerabilities, threats, and attacks, as described in the sections that follow.
Vulnerabilities
Vulnerability is the degree of weakness that is inherent in every network and device. Threats are people who are interested in and capable of taking advantage of each security weakness.
Following are the three primary categories of vulnerabilities:
![]() Technological weaknesses, including the following:
Technological weaknesses, including the following:
— The TCP/IP protocol suite
— Operating system security issues
— Network equipment weaknesses
![]() Configuration weaknesses, including the following:
Configuration weaknesses, including the following:
— Unsecured user accounts
— System accounts with easily guessed passwords
— Misconfigured Internet services
— Unsecured default settings
— Misconfigured network equipment
![]() Security policy weaknesses, including the following:
Security policy weaknesses, including the following:
— Lack of written security policy
— Corporate politics making it difficult to implement a consistent policy
— Lack of continuity
— Inadequate monitoring and auditing of security
— Software and hardware installations and upgrades that do not follow policy
— Nonexistent disaster recovery plan
Threats to Physical Infrastructure
An attacker can deny the use of network resources if those resources can be physically compromised. The four classes of physical threats are as follows:
![]() Hardware threats: Theft or vandalism causing physical damage to servers, routers, switches, cabling plants, and workstations
Hardware threats: Theft or vandalism causing physical damage to servers, routers, switches, cabling plants, and workstations
![]() Environmental threats: Temperature extremes or humidity extremes
Environmental threats: Temperature extremes or humidity extremes
![]() Electrical threats: Voltage spikes, insufficient supply voltage, unconditioned power, and total power loss
Electrical threats: Voltage spikes, insufficient supply voltage, unconditioned power, and total power loss
![]() Maintenance threats: Poor handling of key electrical components, lack of critical spare parts, poor cabling, and poor labeling
Maintenance threats: Poor handling of key electrical components, lack of critical spare parts, poor cabling, and poor labeling
Threats to Networks
Crimes that have implications for network security can be grouped into two primary classes of threats to networks:
![]() Unstructured threats: Consist of mostly inexperienced individuals using easily available hacking tools, such as shell scripts and password crackers.
Unstructured threats: Consist of mostly inexperienced individuals using easily available hacking tools, such as shell scripts and password crackers.
![]() Structured threats: Structured threats come from individuals or groups who are more highly motivated and technically competent. These people know system vulnerabilities and use sophisticated hacking techniques to penetrate unsuspecting businesses.
Structured threats: Structured threats come from individuals or groups who are more highly motivated and technically competent. These people know system vulnerabilities and use sophisticated hacking techniques to penetrate unsuspecting businesses.
These two primary classes of threats can further be categorized as follows:
![]() External threats: External threats can arise from individuals or organizations working outside of a company who do not have authorized access to the computer systems or network.
External threats: External threats can arise from individuals or organizations working outside of a company who do not have authorized access to the computer systems or network.
![]() Internal threats: Internal threats occur when someone has authorized access to the network with either an account or physical access.
Internal threats: Internal threats occur when someone has authorized access to the network with either an account or physical access.
Types of Network Attacks
Various types of attacks can be launched against an organization. There are four primary classes of attacks:
![]() Reconnaissance attacks: The unauthorized discovery and mapping of systems, services, or vulnerabilities using readily available tools to launch the following attacks:
Reconnaissance attacks: The unauthorized discovery and mapping of systems, services, or vulnerabilities using readily available tools to launch the following attacks:
— Internet information queries: Use of tools such as nslookup and whois utilities to easily determine the IP address space assigned to the target organization.
— Ping sweeps: After IP address space is discovered, the attacker uses a ping utility to send pings to every IP address in the address space to determine which addresses are open.
— Port scans: The attacker then scans the active IP addresses to see which ports are open.
— Packet capturing sniffers: Internal attackers may attempt to “eavesdrop” on network traffic to gather or steal information.
![]() Access attacks: Entering or accessing systems by running a hack, script, or tool that exploits a known vulnerability of the system or application being attacked. Common access attacks include the following:
Access attacks: Entering or accessing systems by running a hack, script, or tool that exploits a known vulnerability of the system or application being attacked. Common access attacks include the following:
— Password attacks: Password attacks usually refer to repeated attempts to log in to a shared resource, such as a server or router, to identify a user account, password, or both. These repeated attempts are called dictionary attacks or brute-force attacks.
— Trust exploitation: The process of compromising a trusted host and then using it to stage attacks on other hosts in a network.
— Port redirection: A type of trust exploitation attack that uses a compromised host to pass traffic through a firewall that would otherwise be blocked.
— Man-in-the-Middle attacks: An attack carried out by persons who manage to position themselves between two legitimate hosts. If attackers manage to get into a strategic position, they can steal information, hijack an ongoing session to gain access to private network resources, conduct denial-of-service attacks, corrupt transmitted data, or introduce new information into network sessions.
![]() Denial-of-service (DoS) attacks: DoS attacks involve rendering a system unavailable by physically disconnecting a system, crashing the system, or slowing it down to the point that it is unusable. Some examples of DoS attacks include the following:
Denial-of-service (DoS) attacks: DoS attacks involve rendering a system unavailable by physically disconnecting a system, crashing the system, or slowing it down to the point that it is unusable. Some examples of DoS attacks include the following:
— Ping-of-Death attacks: Sending ping packets that are much larger than expected, which may crash older network systems.
— SYN Flood attacks: Sending thousands of requests for a TCP connection (SYN bit is set) to a targeted server. The server leaves the connection open, waiting for an acknowledgement from the attacker, which never comes.
— Distributed DoS (DDoS) attacks: Similar to DoS, but with hundreds or thousands of attack points that attempt to overwhelm a target.
![]() Malicious code attacks: Malicious software can be inserted onto a host to damage or corrupt a system; replicate itself; or deny access to networks, systems, or services. Common names for this type of software are worms, viruses, and Trojan horses.
Malicious code attacks: Malicious software can be inserted onto a host to damage or corrupt a system; replicate itself; or deny access to networks, systems, or services. Common names for this type of software are worms, viruses, and Trojan horses.
— Worm: A worm executes code and installs copies of itself in the memory of the infected computer, which can, in turn, infect other hosts.
— Virus: A virus is malicious software that is attached to another program to execute a particular unwanted function on a workstation. A virus normally requires a deliver mechanism, such as a zip file or some other executable file attached to an email. The key element that distinguishes a computer worm from a computer virus is that human interaction is required to facilitate the spread of a virus.
— Trojan horse: Differs from a worm or virus only in that the entire application is written to look like something else, when in fact it is an attack tool.
General Mitigation Techniques
Each type of network attack reviewed has mitigation techniques that you should implement, including end user systems, servers, and network devices. The sections that follow describe these mitigation techniques in more detail.
Host and Server Security
Host- and server-based security must be applied to all network systems. Mitigation techniques for these devices include the following:
![]() Device hardening: New systems usually arrive with default values that are rarely secure enough to adhere to the security policy. Most new systems require the following out-of-the-box security configuration:
Device hardening: New systems usually arrive with default values that are rarely secure enough to adhere to the security policy. Most new systems require the following out-of-the-box security configuration:
— Default usernames and passwords should be changed.
— Administrator-level resources should be restricted to those authorized access.
— Unnecessary services should be disabled or uninstalled.
— System logging and tracking should be configured.
![]() Antivirus software: Install host antivirus software to protect against known attacks, and make sure it is updated regularly.
Antivirus software: Install host antivirus software to protect against known attacks, and make sure it is updated regularly.
![]() Personal firewalls: Personal firewalls are meant for PCs that connect directly to the Internet without the benefit of corporate firewalls.
Personal firewalls: Personal firewalls are meant for PCs that connect directly to the Internet without the benefit of corporate firewalls.
![]() Operating system patches: The most effective way to mitigate a worm and its variants is to download security updates and patch all vulnerable systems.
Operating system patches: The most effective way to mitigate a worm and its variants is to download security updates and patch all vulnerable systems.
Intrusion Detection and Prevention
Intrusion detection systems (IDS) detect attacks against a network and send logs to a management console. Intrusion prevention systems (IPS) prevent attacks against the network. Either technology can be implemented at the network level or host level, or both for maximum protection.
Host-based intrusion prevention (HIPS) stops an attack, prevents damage, and blocks the propagation of worms and viruses. Active detection can be set to shut down the network connection or stop impacted services automatically. Corrective action can be taken immediately.
The advantage of HIPS is that it can monitor operating system processes and protect critical system resources, including files that may exist only on that specific host. This means it can notify network managers when some external process tries to modify a system file in a way that might include a hidden back-door program.
Security Appliances and Applications
Figure 8-2 shows a common network topology with a firewall. The firewall’s role is to stop packets that the network administrator has deemed unsafe. The firewall mainly looks at the transport layer port numbers and the application layer headers to prevent certain ports and applications from getting packets into the enterprise.
However, a firewall by itself is no longer adequate for securing a network. An integrated approach involving a firewall, intrusion prevention, and a virtual private network (VPN) might be necessary.
An integrated approach to security and the devices necessary to make it happen follow these building blocks:
![]() Threat control: Regulates network access, isolates infected systems, prevents intrusions, and protects assets by counteracting malicious traffic. Cisco devices and applications that provide threat control solutions include the following:
Threat control: Regulates network access, isolates infected systems, prevents intrusions, and protects assets by counteracting malicious traffic. Cisco devices and applications that provide threat control solutions include the following:
— Cisco ASA 5500 series Adaptive Security Appliances (ASA)
— Integrated Services Routers (ISR)
— Network admission control (NAC)
— Cisco Security Agent for Desktops
— Cisco intrusion prevention systems
![]() Secure communications: Secures network endpoints with a VPN. The devices that allow an organization to deploy a VPN are Cisco ISR routers with a Cisco IOS VPN solution, and the Cisco 5500 ASA and Cisco Catalyst 6500 switches.
Secure communications: Secures network endpoints with a VPN. The devices that allow an organization to deploy a VPN are Cisco ISR routers with a Cisco IOS VPN solution, and the Cisco 5500 ASA and Cisco Catalyst 6500 switches.
![]() Network admission control: Provides a roles-based method of preventing unauthorized access to a network. Cisco offers a NAC appliance.
Network admission control: Provides a roles-based method of preventing unauthorized access to a network. Cisco offers a NAC appliance.
Maintaining Security
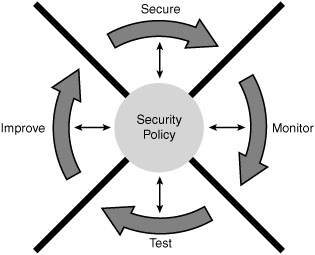
The network security wheel shown in Figure 8-3 can assist with the compliance of the security policy as well as provide a way to improve security as new threats are revealed.
The security policy is the hub upon which the four steps of the security wheel are based:
Step 1 Secure: Secure the network by applying the security policy and implementing the following security solutions:
— Threat defense using device-hardening techniques, antivirus, and spyware tools.
— Intrusion prevention systems to actively stop malicious traffic.
— Vulnerability patching to stop the exploitation of known vulnerabilities.
— Disable unnecessary services.
— Stateful inspection and packet filtering.
— VPNs to encrypt network traffic when traversing the public Internet.
— Trust and identity constraints.
— Authentication.
— Policy enforcement.
Step 2 Monitor: Monitoring security involves both active and passive methods of detecting security violations. System administrators must ensure that all sensitive and vital hosts on the network are being audited. They must also take the time to check and interpret the log file entries.
An added benefit of network monitoring is verifying that the security measures implemented in Step 1 are working properly.
Step 3 Test: Security measures are proactively tested. Specifically, the functionality of the security solutions implemented in Step 1 and the system auditing and intrusion detection methods implemented in Step 2 are verified.
Step 4 Improve: Analyze the data collected during the monitoring and testing phases in order to develop and implement improvement mechanisms that augment the security policy and results in adding items to Step 1. The cycle now repeats with Step 1.