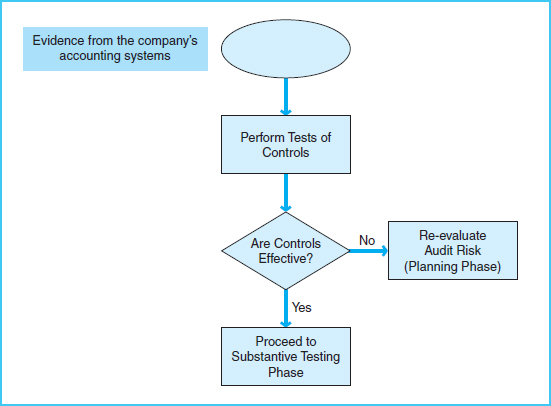
TESTS OF CONTROLS (STUDY OBJECTIVE 8)
Exhibit 7-6 presents the components of the tests of controls phase of the audit.
The tests of controls involve audit procedures designed to evaluate both general controls and application controls. Recall from Chapter 4 that general controls relate to all aspects of the IT environment, whereas application controls relate to specific software applications that cover a particular type of transaction. During audit planning, auditors must learn about the types of controls that exist within their client's IT environment. Then they may test those controls to determine whether they are reliable as a means of reducing risk. Tests of controls are sometimes referred to as “compliance tests,” because they are designed to determine whether the controls are functioning in compliance with management's intentions. The following section discusses how these controls are evaluated.
GENERAL CONTROLS
General controls must be tested before application controls are. Since general controls are the automated controls that affect all computer applications, the reliability of application controls is considered only after general controls are deemed reliable. In other words, even when application controls are believed to be strong, misstatements may still exist as a result of weak general controls. For example, if there were a lack of physical controls, a company's hardware and software could be accessed by an unauthorized user who could alter the data or the programs. So even if the application controls were working as designed, the general control deficiency could result in errors in the underlying information. Accordingly, the effectiveness of general controls is the foundation for the IT control environment. If general controls are not functioning as designed, auditors will not devote attention to the testing of application controls; rather, they will reevaluate the audit approach (according to Exhibit 7-4) with reduced reliance on controls.
Exhibit 7-6 Controls Testing Phase Process Map
There are two broad categories of general controls that relate to IT systems:
- IT administration and the related operating systems development and maintenance processes
- Security controls and related access issues
Each of these categories and the related audit techniques are described in detail next.
IT Administration
IT departments should be organized so that an effective and efficient workplace is created and supported. Auditors should verify that the company's management promotes high standards with regard to controlling its IT environment. Related audit tests include review for the existence and communication of company policies regarding the following important aspects of administrative control:
- Personal accountability and segregation of incompatible responsibilities
- Job descriptions and clear lines of authority
- Computer security and virus protection
- IT systems documentation
If the company does not separate the functions of system design, programming, and operations, auditors should observe activities to ensure that supervisors carefully review the work performed by employees with incompatible duties, to determine whether managerial oversight is in place as a compensating control.
In order to verify proper control over operations of the IT system, auditors should review the policies and procedures manuals covering operator tasks. The manuals should identify the hardware and software used and the timetable for performing tasks. Detailed instructions for carrying out the tasks should be documented, along with a list of employees who should have access to the outputs. Also, in order to test for adequate segregation of duties, auditors should make sure that the operator manuals do not include information about the system design or program code.
Details about the internal logic of computer systems should be documented in IT manuals. Auditors should verify that such documentation exists and is kept up-to-date. IT documentation often includes system flowcharts and other systems development data. System operators and users should not have access to this information, in order for the company to maintain good segregation of duties.
In order to evaluate a company's administrative effectiveness in terms of IT maintenance, auditors should review system documentation to find out whether system maintenance projects are properly authorized. In addition, auditors should determine whether the company maintains control over systems documentation and programs by using a system librarian. A librarian is responsible for maintaining and controlling access to up-to-date systems documentation and programs. Additional tests to be performed when the company makes changes in its IT environment are described later in this chapter, and other access control issues are discussed in the next section.
Security Controls
Auditors are concerned about whether a company's computer system has controls in place to prevent unauthorized access to or destruction of information within the accounting information systems. Unauthorized access may occur internally when employees retrieve information that they should not have, or externally when unauthorized users (or hackers) outside the company retrieve information that they should not have. Access risks tend to escalate as companies embrace newer technologies and allow sensitive data to be shared via smart devices, Web and mobile applications, and social networks. Destruction of information may occur as a result of natural disasters, accidents, and other environmental conditions. Controls that protect the company from these risks include various access controls, physical controls, environmental controls, and business continuity policies. You may find it helpful to refer back to Exhibit 4-5, which presents the various types of controls that a company may use to prevent risk of loss due to unauthorized use, network break-ins, and environmental problems. As auditors gain an understanding of a company's information systems, they can find out if the types of controls listed in Exhibit 4-5 are being used to prevent or detect the related risk. When controls are in place, they can be tested for effective operation. Following are some ways that an auditor can test these controls.
In order to test internal access controls, auditors should determine that the company has properly segregated IT duties or compensated for a lack of segregation by improving supervisory reviews. The company's authority table should be tested to find out whether access to programs and data files is limited to authorized employees. Auditors should perform authenticity tests for valid use of the company's computer system, according to the authority tables. Policy and procedure manuals should describe control over the use of passwords, security tokens, biometric devices, etc. Employees should be required to have passwords, and their level of access should be consistent with their job responsibilities. Auditors can design controls tests to determine whether access is being controlled in accordance with company policies. Computer logs can also be reviewed for login failures, to gauge access times for reasonableness in light of the types of tasks performed, or to detect any unusual activity that may have occurred. In such cases, audit tests may need to be expanded for appropriate follow up. Many computer systems permit an auditor to view an electronic audit trail to determine whether access to operating systems has taken place according to the company's policies. Auditors should also perform tests to be sure that computer access privileges are blocked for employees who have been terminated or revised for employees who have changed job responsibilities.
In order to test external access controls, auditors may perform the following procedures:
- Authenticity tests, as previously described.
- Penetration tests, which involve various methods of entering the company's system to determine whether controls are working as intended. For example, auditors may search for weaknesses in a company's firewall by attempting unauthorized access to the system.
- Vulnerability assessments, which analyze a company's control environment for possible weaknesses. For example, auditors may send test messages through a company's system to find out whether encryption of private information is occurring properly. Special software programs are available to help auditors identify weak points in a company's security measures.
- Review access logs to identify unauthorized users or failed access attempts. Discuss with IT managers the factors involved in rejecting unauthorized access, and verify the consistency of the managers' explanations with documented policies.
In order to maintain good controls, a company's managers should not rely on their auditors to test for computer access violations, but should also monitor the systems on their own on an ongoing basis. The auditors can examine security reports issued by the IT department or review its security detection systems as a way to test the effectiveness of the company's access controls. The frequency of reporting and the manner of following up are important elements of the control environment.
One of the most effective ways a company can protect its computer system is to place physical and environmental controls in the computer center. Physical controls include locks, security guards, alarms, cameras, and card keys. Physical controls not only limit access to the company's computers, but also are important for preventing damage to computer resources. In addition to assessing physical controls, auditors should evaluate the IT environment to determine that proper temperature control is maintained, fireproofing systems are installed, and an emergency power supply is in place.
To test another important feature of effective security control, auditors should determine whether the company would be able to continue its accounting processes in the event of a loss due to a catastrophe caused by human error, crime, acts of nature, or other unforeseen events. All possible causes should be considered in deciding whether the company is protected. To make such a determination, audits typically review the company's disaster recovery plan, backup procedures, virus protection procedures, and insurance coverage, and discuss with management the reasonableness of these policies and the supporting documentation.
As mentioned earlier, application controls are tested only after the general controls are proven to be strong. When general controls have been tested and found to be operating effectively, auditors then test applications controls to see if they are also working as intended.
APPLICATION CONTROLS
Application controls are computerized controls over application programs. Since any company may use many different computer programs in its day-to-day business, there may be many different types of application controls to consider in an audit. Auditors test the company's systems documentation to be sure that adequate details exist for all application programs. The details should include a list of all applications critical to the information being audited, along with supporting source code that is kept up to date in the IT library. Backup copies should be stored off-site. In addition to testing systems documentation, auditors should test the three main functions of the computer applications, including input, processing, and output.
Input Controls
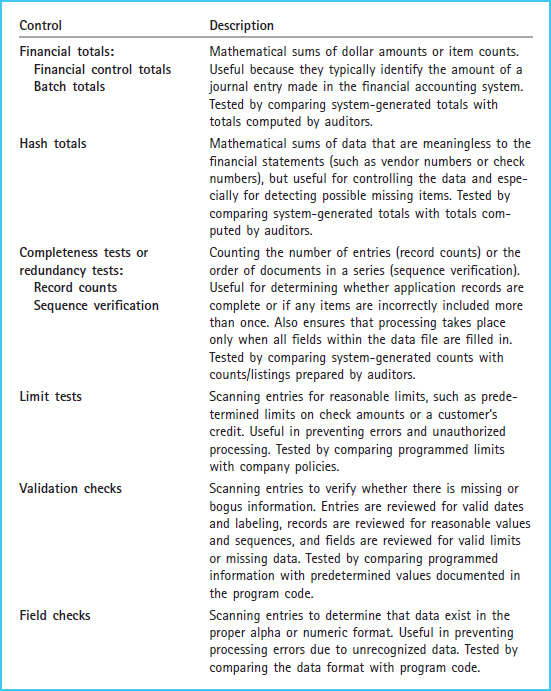
Auditors perform tests to verify the correctness of information input to software programs. Auditors are concerned about whether errors are being prevented and detected during the input stage of data processing. Some of the most widely used computer tests of input controls are summarized in Exhibit 7-7.
Each of the controls presented in Exhibit 7-7 may be used by the company as an internal control measure. In most cases, the same type of function can be performed by auditors as a test of the related control. Auditors test these controls to determine whether control risks are being prevented or detected. Auditors observe controls that the company has in place and perform the comparisons on a limited basis to determine their effectiveness. These tests can be performed manually or by electronic methods.
Processing Controls
IT audit procedures typically include a combination of data accuracy tests, whereby the data processed by computer applications are reviewed for correct dollar amounts or other numerical values. For example, limit tests, described previously as an input control, can also be an effective processing control. Run-to-run totals involve the recalculation of amounts from one process to the next to determine whether data have been lost or altered during the process. Balancing tests involve a comparison of different items that are expected to have the same values, such as comparing two batches or comparing actual data against a predetermined control total. Mathematical accuracy tests verify whether system calculations are correct. Completeness tests and redundancy tests, introduced earlier, check for inclusion of the correct data. Many other procedures, previously described as input control tests, can be performed again during applications processing to check for the possibility of lost or unprocessed data.
When evaluating financial information, auditors can often use Benford's Law to help discover whether errors or fraud may exist in a data set. Benford's Law, also known as the first-digit law, was named for a physicist, Frank Benford, who discovered a specific, but nonuniform pattern in the frequency of digits occurring as the first number in a list of numbers. Benford found that the number 1 is likely to be the leading digit approximately one-third of the time, and the number 2 is the leading digit about 18 percent of the time. The number 9, on the other hand, is a leading digit in less than 5 percent of occurrences. Benford's Law applies to large data sets of naturally occurring numbers and is therefore useful to auditors in evaluating possible errors or fraud in sales and accounts receivable balances, accounts payable and disbursements balances, income tax data, and more. It would predict, for instance, that about half of the numerical observations within the data set of cash disbursements should begin with a 1 or 2. If the numbers had been fabricated, they would not likely follow this natural distribution. However, Benford's Law is not applicable to assigned numbers (such as customer account numbers or phone numbers). Audit procedures that apply Benford's Law can be carried out using spreadsheet programs or special application of audit software.
Exhibit 7-8 presents a comparison of several computer assisted audit techniques (CAATs). The test data method is an audit and control technique often used to test the processing accuracy of software applications. Test data are fictitious information developed by auditors and entered in the company's application system. Test data are processed under the company's normal operating conditions. The results of the test are compared with predicted results to determine whether the application is functioning properly. Auditors must carefully design the test data to include items that appear authentic, as well as some that are illogical. Therefore, it is expected that the system will accurately process the realistic data and isolate the rejected (nonsense) data in an error report. After this testing is complete, auditors should make sure that test items are removed from the company's system to avoid contaminating its actual data. The test data method is well suited to tests of controls in batch systems. The batch of test data can be processed as a single batch so that it will not interrupt or interfere with regular batch processing. The batch nature of the test data approach makes it a static approach to testing controls. This means that the test data method provides a picture of the operation of the internal controls at only one point in time and not over the entire year. This static nature of the test data method makes it less likely to detect fraudulent transactions. The person conducting fraud through changing an application within the IT system could temporarily change it back to the normal operation at the time the test data are processed. Then, after the data have been tested, the application could be reverted to its fraudulent operation.
A slight variation of the test data method involves the auditor testing fictitious data, using a copy of the company's application. The test data may be processed through the application on a different (nonclient) computer. Under these conditions, an auditor can also use another test data method, program tracing, whereby bits of actual data are followed through the application in order to verify the accuracy of its processing. Program mapping, on the other hand, counts the number of times each program statement is executed, so it can identify whether program code has been bypassed.
An integrated test facility (ITF) may be used to test application controls without disrupting the client's operations. Under this approach, test data are input directly into the client's system along with actual data, but the system is programmed to exclude the test data from its master files. The test data and test master files are often called dummy transactions and dummy entities. The dummy transactions are accumulated in the dummy entity files, which are used only by the auditors. Accordingly, auditors can evaluate the applications in light of predetermined expectations (similar to the test data method) during a company's normal operating conditions, without affecting real accounting results. The ITF method is well suited to testing controls in online—as well as online, real-time—systems. The dummy transactions can be processed at intervals throughout the year. Thus, ITF provides an ongoing analysis, rather than a static picture, of the internal controls.
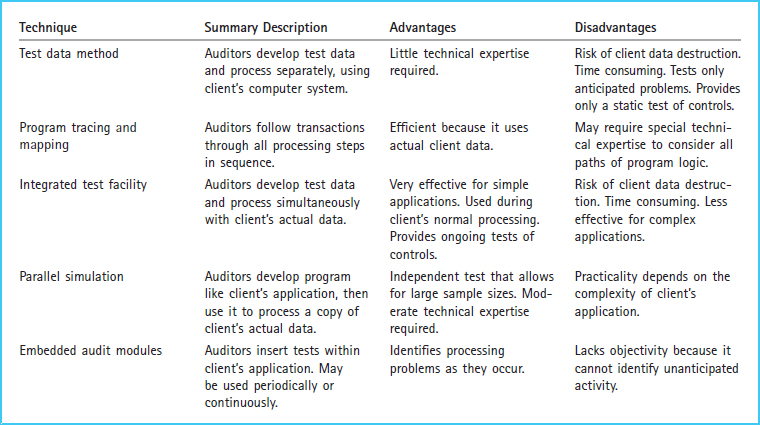
Exhibit 7-8 Comparison of Computer-Assisted Audit Techniques (CAATs) for Testing Applications Controls
Parallel simulation is an audit technique that processes company data through a controlled program designed to resemble the company's application. Parallel simulations are run to find out whether the same results are achieved under different systems. Simulated results are compared with the company's actual results. Auditors should be careful in forming conclusions on the basis of differences noted in parallel simulations. Although such differences may be the result of control weaknesses in the company's application, they could also be caused by mistakes in developing the simulation.
The embedded audit module approach involves placing special audit testing programs within the company's operating system. The test modules search the data and analyze transactions or account balances that meet specified conditions of interest to the auditor. For instance, transactions with a key customer or those that exceed a given dollar amount may be captured in the audit module. The auditors analyze the evidence in the audit module to determine whether it is being recorded accurately. The embedded audit module approach is similar to parallel simulation, except that the embedded audit module approach can be programmed to work either periodically (at each quarter end, for instance) or continuously throughout the period. Parallel simulations, on the other hand, are conducted at a particular point in time.
THE REAL WORLD
Ernst & Young LLP employs thousands of auditors in its IT Risk and Assurance Advisory Services group. This specialized group assists with financial statement audits and provides other services concerning its clients' information systems. Information systems assurance services focus on audits of business information systems, assessment of the underlying control environment, and the use of CAATs to verify accounting and financial data.
As one of the Big Four CPA firms, Ernst & Young is responsible for auditing the financial statements of many public companies. It serves clients in hundreds of locations in approximately 140 countries. These client companies are quite diverse in terms of the type of business they perform, their size, and their complexity, but tend to be alike in their need for timely information. The use of CAATs helps Ernst & Young provide timely service to its clients, while accumulating audit evidence necessary for doing its job as auditor.
Output Controls
Audit tests that evaluate general controls over access and backup procedures may also be used in the testing of specific computer application outputs. It is important that auditors test for proper control of financial information resulting from applications processing. Regardless of whether the results are printed or retained electronically, auditors may perform the following procedures to test application outputs:
- Reasonableness tests compare the reports and other results with test data or other criteria.
- Audit trail tests trace transactions through the application to ensure that the reporting is a correct reflection of the processing and inputs.
- Rounding errors tests determine whether significant errors exist due to the way amounts are rounded and summarized.
As part of the controls testing phase of an audit, auditors should also verify that the company is performing timely and accurate reconciliations. A reconciliation is a detailed report assessing the correctness of an account balance or transaction record that is consistent with supporting documentation and the company's policies and procedures. Account balance details and supporting documentation may be derived from applications outputs. In order to enhance controls, reconciliations should be performed by company personnel who are independent from the tasks of initiating or recording the transactions within the accounts being reconciled.
THE REAL WORLD
The embezzlement case at Koss Corporation, introduced in Chapter 3, described the fraudulent acts of the company's VP of Finance, Sue Sachdeva. In the aftermath of the discovery of the frauds, an SEC investigation revealed many control failures at Koss, including problems with account reconciliations. Either the reconciliations were not maintained in the accounting records, not prepared correctly, or not prepared at all. Some of the reconciliations were performed by Sachdeva herself, despite the fact that she had been involved in the initial authorization or recording of the underlying transactions. This provided an opportunity for Sachdeva to modify the reconciliations in order to conceal her wrongdoing. The CPA firm that audited Koss's financial statements was dismissed because its audit procedures did not uncover these serious problems.
At the conclusion of the controls testing phase of the audit, an auditor must determine the overall reliability of the client's internal controls. Auditors strive to rely on internal controls as a way to reduce the amount of evidence needed in the remaining phases of the audit. They can be reasonably sure that information is accurate when it comes from a system that is proven to have strong controls. Therefore, once the general and application controls are tested and found to be effective, the amount of additional evidence needed in the next phase of the audit can be minimized. It is also worthwhile to note that controls testing can be done nearly anytime during the period, so auditors can schedule their work at a convenient time. This convenience factor, plus the reduction in additional audit evidence required, makes testing controls more efficient than testing transactions and account balances.
