Why VLANs?
Many people will tell you VLANs are so darn virtual that you tend to lose them for no apparent reason. I'll save that discussion for the “Shooting Trouble with VLANs” section and the Trouble Tickets. To get a handle on VLANs, I want you to think about the function of a router. Physically each interface or wire is a broadcast domain, but it is more often referred to as a subnet. Traffic from one router can pass from one local interface to another because the router knows about its directly connected networks. Interrouter communications occur because of not only physical components but also because of routed and routing protocols.
Switch broadcast domains are called VLANs. By default all ports on a switch belong to VLAN1, as you can verify in Example 7-8. Other VLANs can be configured to facilitate smaller broadcast domains and smaller spanning trees. However, traffic from one VLAN cannot pass directly to another VLAN, whether within a switch or between switches, without a router of some sort.
Example 7-8. By Default All Ports Are in VLAN1 (1 Broadcast Domain)
sw3512xl#show vlan VLAN Name Status Ports ---- -------------------------------- --------- ------------------------------- 1 default active Fa0/1, Fa0/2, Fa0/3, Fa0/4, Fa0/5, Fa0/6, Fa0/7, Fa0/8, Fa0/9, Fa0/10, Fa0/11, Fa0/12, Gi0/1, Gi0/2 1002 fddi-default active 1003 token-ring-default active 1004 fddinet-default active 1005 trnet-default active !!!these are the default or reserved vlans VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2 ---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------ 1 enet 100001 1500 - - - - - 1002 1003 1002 fddi 101002 1500 - - - - - 1 1003 1003 tr 101003 1500 1005 0 - - srb 1 1002 1004 fdnet 101004 1500 - - 1 ibm - 0 0 1005 trnet 101005 1500 - - 1 ibm - 0 0 sw2900> (enable) show vlan VLAN Name Status IfIndex Mod/Ports, Vlans ---- -------------------------------- --------- ------- ------------------------ 1 default active 28 1/1-2 2/1-12 1002 fddi-default active 29 1003 token-ring-default active 32 1004 fddinet-default active 30 1005 trnet-default active 31 |
Example 7-8 displays a couple of sections. The first section is a quick status of the VLANs and the associated ports on the 3512XL. The second section displays the default VLANs, including the maximum transmission unit (MTU) size and other Token Ring and FDDI parameters. The second section is not shown for the CatOS 2900, but all ports are in VLAN 1 by default. 1002 FDDI and 1003 TRCRF are reserved for FDDI and Token Ring transparent bridging; whereas 1004 FDNET and 1005 TRBRF are reserved for Token Ring and source route bridging. Although the default reserved VLANs can't be removed, they can be modified (as you can prove by trying to clear one of the defaults). If I were to type clear vlan 1002 on the 2900 right now, for example, it would tell me that the VLAN needs to be within the range of 2 to 1000.
Understanding what VLANs are and how they work is half the battle of supporting them. Think of a physical switch or switches that are divided up into logical bridges to assist with broadcasts. Logical bridges or broadcast domains, more often referred to as VLANs, are possible within or between switches, as you can see in Figure 7-2.
NOTE
If you have more VLANs in your lab scenario, at this point you may need to clear them or delete flash:vlan.dat to completely remove them. My devices are in the out-of-the-box default VLAN Trunking Protocol (VTP) server mode and default to Inter-Switch Link (ISL) encapsulation. (Your equipment may vary.) You might need to change your boxes to server mode or change the encapsulation to follow along and understand.
Figure 7-2 illustrates two switches where ports are logically grouped into three different VLANs: RED, GREEN, and BLUE. The RED VLAN members are able to talk to others within the same VLAN (subnet). The GREEN VLAN members are able to talk to others within the same VLAN (subnet). The BLUE VLAN members are able to talk to others within the same VLAN (subnet). Although the VLANs are isolated from one another, intra-VLAN communications can occur. Intra-VLAN traffic can occur within or between the switches because the trunk carries RED, GREEN, and BLUE VLAN traffic. However, inter-VLAN communications such as RED to GREEN, RED to BLUE, GREEN to BLUE, and so on are not possible without some Layer 3 decisions because each VLAN is a separate subnet. The Route Switch Module/Multilayer Switch Feature Card (RSM/MSFC) (router blade) in Figure 7-2 is one way of supporting VLAN-to-VLAN communications. It uses a separate physical or logical interface for each VLAN to support the inter-VLAN routing function. By logically grouping the ports on a switch or among different switches, you can virtually create separate bridges within a switch and have a router route the packets between them. Next, I want to look into some of the practical advantages to using VLANs.
VLAN Advantages
The following are some advantages of VLANs:
Security— VLANs enable you to isolate groups of users. Can you imagine a student adjusting a teacher's salary because they are physically on the same network? How about health records? Police records?
Segment broadcasts— If you are only talking about one particular box causing the majority of broadcast traffic, you should probably look at just isolating that box. If broadcasts come from various stations, VLANs can assist.
Better utilization of bandwidth— You can separate management and control traffic from that of the end user. Smaller spanning trees help with Layer 2 convergence.
Reduced latency— Smaller broadcast domains using Layer 2 devices to minimize the number of Layer 3 devices.
Easy to move users— For example, a user moves from the Sales department to the Engineering department. Just associate the appropriate port with the appropriate VLAN instead of making wiring closet physical changes.
As you can see, there are multiple reasons to use VLANs, and understanding them a little better will certainly help you keep a more stable network.
Trial and error has proven that flat networks and end-to-end VLANs do not scale. Modern implementations use Layer 2 switches for the access layer and Layer 3 switches in the distribution and core layers. Regardless of the equipment, it is up to you and me to make sure end-to-end communications occur and that everyone is happy.
NOTE
Catalyst VLANs are very port-centric, and proper planning is critical to ease the maintenance thereof. For example, it is not a good VLAN design to mix control and management traffic with end-user traffic. You should analyze the various types of VLAN traffic so that you can at a minimum separate the management and control traffic from the user traffic.
VLAN Traffic Types
Types of VLAN traffic include the following:
Control— Protocol traffic such as Spanning Tree Protocol (STP), CDP, Dynamic Trunking Protocol (DTP), VTP, and Port Aggregation Protocol (PAgP) typically use VLAN1.
End-user— VLANs create isolation. If one workstation goes berserk, the impact is limited to the user VLAN.
Management— Services such as telnet, Simple Network Management Protocol (SNMP), VLAN Membership Policy Server (VMPS), and Syslog normally use whatever VLAN that is assigned to the Supervisor Console (sc0) port.
Configuring VLANs
Planning is the most important part of VLANs. VLANs are subnets and thus are part of the IP addressing design. Often it is helpful to have a recognizable pattern. Perhaps you might use something like 10.bldg.vlan.node/24 with .1, .2, and .3 reserved for Hot Standby Router Protocol (HSRP) and .4 through .20 for router interfaces, servers, and printers.
NOTE
If you attach a hub to a port assigned to a VLAN, all ports on the hub are part of the VLAN.
Other things the support person should be familiar with include the fact that all ports start out in VLAN1. If you associate a port with a different VLAN and then delete that VLAN with clear vlan #, however, all ports associated with that VLAN will be in an inactive state. You can fix that by creating the VLANs again, which is much easier if you previously saved the configuration to a file. As you configure the chapter scenario, you will experience these and other VLAN advantages and disadvantages.
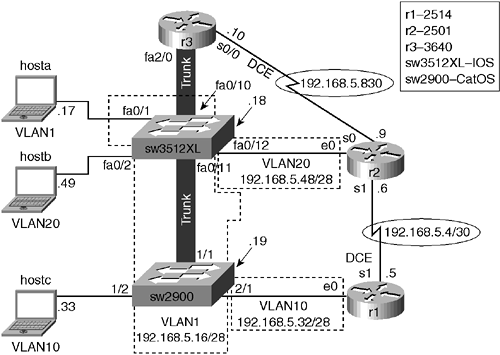
Start your planning and configuring using the chapter scenario VLANs in Figure 7-3. Each VLAN has a number and an associated network (such as IP or IPX). VLANs are Layer 2; however, inter-VLAN connectivity is through routers (Layer 3). Use subnet 192.168.5.16/28 for VLAN1, 192.168.5.32/28 for VLAN10, 192.168.5.48/28 for VLAN20, and subnet 192.168.5.0/30 for the serial links. Create the VLANs, associate ports, and assign IP addresses using Figure 7-3 as a guide. Assign host default gateways using the last address (not the broadcast) for each subnet. Use Table 7-2 if you need more host detail. Do not configure the VLAN-to-VLAN routing or trunking yet.
NOTE
Refer to Tables 7-1 and 6-7 for assistance with IOS compared to CatOS VLAN commands.
| Host | IP Address | Subnet Mask | Gateway |
|---|---|---|---|
| hosta (VLAN1) | 192.168.5.17 | 255.255.255.240 | 192.168.5.30 |
| hostb (VLAN20) | 192.168.5.49 | 255.255.255.240 | 192.168.5.62 |
| hostc (VLAN10) | 192.168.5.33 | 255.255.255.240 | 192.168.5.46 |
After your host configuration, create VLAN20 using the VLAN database mode as in Example 7-9. Pay particular attention that this is not performed from global configuration mode. The command to exit and apply the changes is exit.
Example 7-9. Creating VLAN20 on the 3512XL (IOS)
sw3512xl#vlan database sw3512xl(vlan)#vlan 20 name vlan20 VLAN 20 added: Name: vlan20 sw3512xl(vlan)#? VLAN database editing buffer manipulation commands: abort Exit mode without applying the changes apply Apply current changes and bump revision number exit Apply changes, bump revision number, and exit mode no Negate a command or set its defaults reset Abandon current changes and reread current database show Show database information vlan Add, delete, or modify values associated with a single VLAN vtp Perform VTP administrative functions. sw3512xl(vlan)#exit APPLY completed. Exiting.... |
Example 7-10 continues the configuration by associating interface fa0/2 and fa0/12 with VLAN20.
Example 7-10. Associating fa0/2 and fa0/12 with VLAN20 on the 3512XL (IOS)
sw3512xl(config)#interface fastethernet 0/2 sw3512xl(config-if)#switchport ? access Set access mode characteristics of the interface mode Set trunking mode of the interface multi Set characteristics when in multi-VLAN mode trunk Set trunking characteristics of the interface sw3512xl(config-if)#switchport access vlan 20 sw3512xl(config-if)#interface fastethernet 0/12 sw3512xl(config-if)#switchport access vlan 20 sw3512xl(config-if)#end |
Next, verify that the ports were in fact added to VLAN20 as in Example 7-11.
Example 7-11. Verifying the VLAN Configuration
sw3512xl#show vlan VLAN Name Status Ports ---- -------------------------------- --------- ------------------------------- 1 default active Fa0/1, Fa0/3, Fa0/4, Fa0/5, Fa0/6, Fa0/7, Fa0/8, Fa0/9, Fa0/10, Fa0/11, Gi0/1, Gi0/2 20 vlan20 active Fa0/2, Fa0/12 1002 fddi-default active 1003 token-ring-default active 1004 fddinet-default active 1005 trnet-default active ... |
Don't forget to configure and verify the VLAN1 IP parameters for management purposes so that you can telnet to the device (see Example 7-12). In such a small lab scenario, VLAN 1 is fine. However, it is a better practice to use another VLAN for management purposes.
Example 7-12. In-band Management for the 3512XL (IOS)
sw3512xl(config)#interface vlan1 sw3512xl(config-if)#ip address 192.168.5.18 255.255.255.240 sw3512xl(config-if)#no shut sw3512xl(config-if)#end sw3512xl#copy running-config startup-config sw3512xl#show interface vlan1 VLAN1 is up, line protocol is up Hardware is CPU Interface, address is 00d0.7968.8480 (bia 00d0.7968.8480) Internet address is 192.168.5.18/28 ... |
IOS offers Layer 3 interfaces and Layer 2 ports or switchports. To convert the interface from a routed interface to a switched port, you use the interface command switchport mode access. This sets the port as an access port rather than a trunk port. On many devices, the interface range command enables you to do this to lots of ports simultaneously interface range 6/1-24, 7/1-12. The command enables you to configure ports 1 through 24 on module 6 and ports 1 through 12 on module 7 all at once. These switchports default to VLAN1, but the switchport access vlan vlan# command enables you to assign the port to a particular VLAN. Because these ports are technically Layer 2 now, you can't assign an IP address to them directly. Instead, you need a separate interface to act as a routed interface for both of them. This calls for a switched virtual interface (SVI), which you created in Example 7-12 using the interface vlan1 command. You assigned it an IP address and verified it using the show interface vlan1 command.
Next, create VLAN10 and associate the ports as in Figure 7-3 on the CatOS-based 2900 switch as in Example 7-13.
Example 7-13. Creating VLAN10 and Associating the Ports on the 2900 (CatOS)
sw2900> (enable) set vlan 10 name vlan10 Cannot add/modify VLANs on a VTP server without a domain name. sw2900> (enable) set vtp ? Usage: set vtp [domain <name>] [mode <mode>] [passwd <passwd>] [pruning <enable | disable>] [v2 <enable | disable> (mode = client | server | transparent Use passwd '0' to clear vtp password) Usage: set vtp pruneeligible <vlans> (vlans = 2..1000 An example of vlans is 2-10,1000) sw2900> (enable) set vtp domain donna VTP domain donna modified sw2900> (enable) set vlan 10 name vlan10 Vlan 10 configuration successful sw2900> (enable) set vlan 10 1/2,2/1 VLAN 10 modified. VLAN 1 modified. VLAN Mod/Ports ---- ----------------------- 10 1/1-2 2/1 sw2900> (enable) show vlan VLAN Name Status IfIndex Mod/Ports, Vlans ---- -------------------------------- --------- ------- ------------------------ 1 default active 5 2/2-12 10 vlan10 active 10 1/2 2/1 ... |
Notice how Example 7-13 insisted you create a VTP domain name before you could create any VLANs or associate the ports. VTP is the VLAN Trunking Protocol (discussed in more detail in the section “Managing VLANs”). Next, set up the 2900 IP parameters to allow telnet to the box. Example 7-14 illustrates how to configure the Supervisor Console.
Example 7-14. In-band Management for the 2900 (CatOS)
sw2900> (enable) set interface sc0 1 192.168.5.19 255.255.255.240 Interface sc0 vlan set, IP address and netmask set. sw2900> (enable) set interface sc0 up Interface sc0 administratively up. |
After the VLAN was created, I noticed some error messages on the port in my example. However, the counters had never been cleared, so I cleared them and didn't notice any more errors. The sc0 port was used to assign the IP address to the CatOS-based switch like the SVI for the IOS-based switch. In practical application use another VLAN other than VLAN1.
As you can verify in the previous examples, making VLANs work is a multistep process. However, you only created VLANs on two switches. What if you had 500?
VLAN Membership Policy Server (VMPS)
An alternative to manual VLAN association is the dynamic VMPS. However, it is still lots of work to build the initial database, which is why many choose to just go with static VLANs. The VMPS database is a text file residing on a TFTP server. The VMPS server reads the text file and remembers the data. Dynamic VLANs then look to the VMPS server for MAC lookup when it attaches to a port. Other Catalysts are configured as VMPS clients that communicate with the server over UDP port 1589 for port-to-VLAN authorization. You then use commands such as show vmps and show port to display the dynamic ports. Two optional Cisco tools for building the database include the User Registration Tool (URT) and CiscoWorks for Switched Networks (CWSI). URT is based on NetBIOS login information and managed with CWSI. The User Tracker for CWSI keeps track of individual stations on the network and automatically populates the VMPS server. See Cisco.com or Cisco LAN Switching (Cisco Press) by Kennedy Clark and Kevin Hamilton for more detail on configuring dynamic VLANs. In practical application of VLANs, static VLANs are by far the most common.
NOTE
The GARP Registration Protocol (GVRP) provides dynamic VLAN creation for IEEE 802.1Q-compliant VLANs. GARP stands for Generic Attribute Registration Protocol. GVRP(802.1P) is also used for standards-based VLAN pruning.
Thus far, you have worked with access links. Because they are designed for one VLAN only, they do not scale. Next, you will learn about trunking so that you see how VLANs on one switch can communicate with others in the same VLAN on another switch via a trunk port.