Trunking
Routing provides inter-VLAN connectivity, whereas trunking provides intra-VLAN connectivity. Trunks, whether between switches, from a router to a switch, or from a switch to a file server, minimize the number of interfaces and cables to transport multi-VLAN traffic.
There are various methods of multiplexing VLANs in trunking:
Cisco
- Ethernet—ISL or 802.1Q
- FDDI—802.10
- ATM—LAN Emulation (LANE) or multiprotocol over ATM (MPOA)
Mixed-vendor environment
- 802.1Q
- LANE or MPOA
Cisco uses its own proprietary ISL and the standards-based IEEE 802.1Q for trunking. (See Figure 7-4.) However, Cisco has started to favor 802.1Q over ISL. Some newer switches such as the 2950 support only 802.1Q.
Go ahead and configure ISL trunking from the 3512XL to the 2900 using Example 7-15 and Figure 7-3 as guides.
Example 7-15. Configuring Cisco ISL Trunking Between the 2900 and 3512
sw3512xl(config)#interface fastethernet 0/11 sw3512xl(config-if)#switchport mode trunk sw3512xl(config-if)#end sw3512xl#show interfaces fastethernet 0/11 switchport Name: Fa0/11 Switchport: Enabled Administrative mode: trunk Operational Mode: trunk Administrative Trunking Encapsulation: isl Operational Trunking Encapsulation: isl Negotiation of Trunking: Disabled Access Mode VLAN: 0 ((Inactive)) Trunking Native Mode VLAN: 1 (default) Trunking VLANs Enabled: ALL Trunking VLANs Active: 1,20 Pruning VLANs Enabled: NONE sw3512xl#copy running-config startup-config |
ISL is the default trunking encapsulation here, but always check the port capabilities on your particular switch to see what is actually available. Next, configure the other end of the trunk on the 2900 CatOS box as in Example 7-16.
Example 7-16. Trunking on the 2900 CatOS
sw2900> (enable)set trunk 1/1 on Port(s) 1/1 trunk mode set to on. sw2900> (enable) %DTP-5-TRUNKPORTON:Port 1/1 has become isl trunk sw2900> (enable)show trunk Port Mode Encapsulation Status Native vlan -------- ----------- ------------- ------------ ----------- 1/1 on isl trunking 1 Port Vlans allowed on trunk -------- --------------------------------------------------------------------- 1/1 1-1005 Port Vlans allowed and active in management domain -------- --------------------------------------------------------------------- 1/1 1,10 Port Vlans in spanning tree forwarding state and not pruned -------- --------------------------------------------------------------------- 1/1 sw2900>show port capabilities 1/1 Model WS-X2900 Port 1/1 Type 100BaseTX Speed 100 Duplex half,full Trunk encap type ISL Trunk mode on,off,desirable,auto,nonegotiate Channel no Broadcast suppression no Flow control no Security yes Membership static,dynamic Fast start yes Rewrite no sw2900> (enable) |
The switchport mode trunk IOS command turned the fa0/11 port into a trunk, which you verified with show interfaces fastethernet 0/11 switchport. Besides trunking, the preceding show command displayed encapsulation and active VLANs, too. All VLANs are allowed by default, but you can remove VLANs with the switchport trunk allowed vlan remove 11-1000 command; the numbers at the end are the VLANs you want to remove. The commands were different for the CatOS 2900, but the effect was the same. The show port capabilities command is quite helpful to know what the port is capable of in terms of speed, duplex, encapsulation, and trunking.
NOTE
Notice the shaded output about DTP, which is a trunk negotiation protocol. The XL switches do not yet support DTP, so the switch on the other end of the trunk link must be manually set to trunk.
Save your configurations and then experiment for a moment. Bounce (shut/no shut) fa0/11 on the 3512. Verify your VTP status on both switches as in Example 7-17. Look at your VLANs again in Example 7-18.
Example 7-17. The Result of Bouncing an Interface
sw3512xl#copy running-config startup-config sw3512xl(config)#interface fastethernet 0/11 sw3512xl(config-if)#shut sw3512xl(config-if)#no shut sw3512xl(config-if)#end sw3512xl#show vtp status VTP Version : 2 Configuration Revision : 1 Maximum VLANs supported locally : 254 Number of existing VLANs : 6 VTP Operating Mode : Server VTP Domain Name : donna VTP Pruning Mode : Disabled VTP V2 Mode : Disabled VTP Traps Generation : Disabled MD5 digest : 0x1F 0xAF 0x58 0x06 0x31 0x48 0x80 0xD9 Configuration last modified by 0.0.0.0 at 5-26-02 12:34:06 sw3512xl#!!!the vtp domain name is donna yet you only set it on the 2900 sw2900> (enable)show vtp domain Domain Name Domain Index VTP Version Local Mode Password -------------------------------- ------------ ----------- ----------- ---------- donna 1 2 server - ... |
Example 7-18. Verifying VLANs
sw2900> (enable)show vlan VLAN Name Status IfIndex Mod/Ports, Vlans ---- -------------------------------- --------- ------- ------------------------ 1 default active 28 2/2-12 10 vlan10 active 10 1/2 2/1 ... sw3512xl#show vlan VLAN Name Status Ports --- -------------------------------- --------- ------------------------------- 1 default active Fa0/1, Fa0/2, Fa0/3, Fa0/4, Fa0/5, Fa0/6, Fa0/7, Fa0/8, Fa0/9, Fa0/10, Gi0/1, Gi0/2 10 vlan10 active 1002 fddi-default active 1003 token-ring-default active 1004 fddinet-default active 1005 trnet-default active |
You are not imagining things. Some of your VLANs disappeared. VLAN10 is on both switches, but VLAN20 totally disappeared. Both switches are in the VTP server mode and use revision numbers to track changes; thus the highest revision number wins. Certainly what happened here is not what you want to happen in a practical environment. It is recommended to have all transparent or a series of client/server boxes in your network. The penalty for using transparent mode is that you need to manually create your VLANs on all your switches. The section “Managing VLANs” discusses VTP in more detail.
Change the 3512XL to transparent mode, configure VLAN20 once again, and verify your configuration as in Example 7-19.
Example 7-19. Changing the 3512 to Transparent Mode
sw3512xl#vlan database sw3512xl(vlan)#vtp transparent Setting device to VTP TRANSPARENT mode. sw3512xl(vlan)#exit APPLY completed. Exiting.... sw3512xl(vlan)#vtp transparent Device mode already VTP TRANSPARENT. sw3512xl(vlan)#vlan 20 name vlan20 VLAN 20 added: Name: vlan20 sw3512xl(vlan)#exit APPLY completed. Exiting.... sw3512xl#show vlan VLAN Name Status Ports ---- -------------------------------- --------- ------------------------------- 1 default active Fa0/1, Fa0/3, Fa0/4, Fa0/5, Fa0/6, Fa0/7, Fa0/8, Fa0/9, Gi0/1, Gi0/2 10 vlan10 active 20 vlan20 active Fa0/2, Fa0/12 ... sw3512xl#copy running-config startup-config |
Note that fa0/2 and fa0/12 are the active ports for VLAN20. The port association was automatic because it was there before. Now view the VLANs on the 2900 in Example 7-20.
Example 7-20. Viewing the VLANs on the 2900
sw2900> (enable)show vlan VLAN Name Status IfIndex Mod/Ports, Vlans ---- -------------------------------- --------- ------- ------------------------ 1 default active 28 2/2-12 10 vlan10 active 33 1/2,2/1 ... |
Perform a shut/no shut on interface fa0/11 once again and verify your VLANs as in Example 7-21.
Example 7-21. Verifying VLANs
sw3512xl(config)#interface fastethernet 0/11 sw3512xl(config-if)#shut sw3512xl(config-if)#no shut sw3512xl(config-if)#end sw3512xl#show vlan VLAN Name Status Ports ---- -------------------------------- --------- ------------------------------- 1 default active Fa0/1, Fa0/3, Fa0/4, Fa0/5, Fa0/6, Fa0/7, Fa0/8, Fa0/9, Fa0/10, Gi0/1, Gi0/2 10 vlan10 active 20 vlan20 active Fa0/2, Fa0/12 ... sw2900> (enable)show vlan VLAN Name Status IfIndex Mod/Ports, Vlans ---- -------------------------------- --------- ------- ------------------------ 1 default active 28 2/2-12 10 vlan10 active 10 1/2 2/1 ... |
It is correct that the 3512XL shows both VLANs because it previously learned about VLAN10 via VTP from the 2900, when it was in server mode. It is also correct that the 2900 only displays VLAN10 because VLAN20 was created in the 3512XL while it was in transparent mode (so VLAN20 did not get propagated throughout the VTP domain).
Now that your switches are in a more stable state, the VLANs are configured, and the ISL trunking is passing VTP information, I want to continue discussing other trunking methods.
NOTE
You cannot route from VLAN to VLAN for a couple of reasons at this point, but I will revisit that issue and more VTP management details soon.
Inter-Switch Link (ISL)
ISL is a Cisco proprietary VLAN tagging method that is used only for point-to-point connections on equipment that supports ISL trunking. For that matter, any trunk must be point-to-point. Although 100 Mbps or better is recommended, the specifications support 10 Mbps, too. You set your trunks to ISL encapsulation. (Actually, that was the default for the lab scenario switches.)
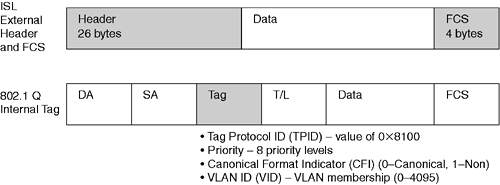
When a frame goes out an ISL trunk, it gets encapsulated by tagging it with a 26-byte ISL header and another 4-byte cyclical redundancy check (CRC) trailer. Therefore it is possible for an ISL frame to be 1518 + 30 = 1548 bytes, also known as a “baby giant.” ISL trunks can carry not only Ethernet traffic, but also Token Ring and FDDI due to the reserved field in the ISL header.
Previously, you had to manually configure ISL on both ends, but DTP allows the switch to negotiate trunking. Frames are sent out every 30 seconds through the same multicast MAC as CDP but with a different Subnetwork Access Protocol (SNAP) value. The trunk modes for use with the set trunk mod#/port# mode command are on, off, desirable, auto, and nonegotiate. Do you recall the DTP message when you set the trunk on the 2900. Look back at Example 7-16 to review it now. DTP enhances the older Dynamic Inter-Switch Link (DISL) functionality in that it negotiates trunking for not only ISL, but also IEEE 802.1Q.
Because negotiation is in progress, there is room for negotiation not to occur. Things are fine when the results are on/on because both ends are trunking. If the result is off/off, you probably are looking at an access link and not a trunk. It is when you end up with on/off or off/on that you need to investigate the settings. Normally, desirable or auto on one side with the other side of the trunk set to on works just fine. Consider hard coding your critical links.
Whether negotiated or hard coded, by default all VLANs can use the trunk. Create another VLAN on the 2900 and set some trunk restrictions as in Example 7-22.
Example 7-22. Trunk Restrictions
sw2900> (enable)set vlan 100 Vlan 100 configuration successful sw2900> (enable)show trunk Port Mode Encapsulation Status Native vlan -------- ----------- ------------- ------------ ----------- 1/1 on isl trunking 1 Port Vlans allowed on trunk -------- --------------------------------------------------------------------- 1/1 1-1005 Port Vlans allowed and active in management domain -------- --------------------------------------------------------------------- 1/1 1,10,100 Port Vlans in spanning tree forwarding state and not pruned -------- --------------------------------------------------------------------- 1/1 1,10 sw2900> (enable)clear trunk ? Usage: clear trunk <mod/ports...> [vlans...] (An example of mod/ports is 1/1,2/1-12,3/1-2,4/1-12 vlans = 2..1005 An example of vlans is 2-10,1005) sw2900> (enable)clear trunk 1/1 100 Removing Vlan(s) 100 from allowed list. Port 1/1 allowed vlans modified to 1-99,101-1005. |
Another method of controlling which VLANS are allowed is the set trunk mod#/port# ? command. Available options include the following:
Usage: set trunk <mod_num/port_num> [on | off | desirable | auto | nonegotiate] [vlans]
[trunk_type]
(vlans = 1..1005
An example of vlans is 2-10,1005)
(trunk_type = isl,dot1q,dot10,lane,negotiate)
Example 7-23 illustrates first using CatOS and then using IOS for trunk restrictions.
Example 7-23. Trunk Restrictions
sw2900> (enable)!!!CatOS Example sw2900> (enable)set trunk 1/1 on ? Usage: set trunk <mod_num/port_num> [on | off | desirable | auto | nonegotiate] [vlans] [trunk_type] (vlans = 1..1005 An example of vlans is 2-10,1005) (trunk_type = isl,dot1q,dot10,lane,negotiate) sw2900> (enable) sw3512xl#!!!IOS Example sw3512xl(config-if)#switchport trunk allowed vlan ? WORD VLAN IDs of the allowed VLANs when this port is in trunking mode add add VLANs to the current list all all VLANs except all VLANs except the following remove remove VLANs from the current list |
Because the chapter scenario equipment you are using is all Cisco and uses ISL, that has been the focus thus far. However, dot1Q provides multivendor support.
IEEE 802.1Q (dot1Q)
Unlike ISL, IEEE 802.1Q offers multivendor support. As shown in Figure 7-5, ISL is more of an encapsulation (external tagging) method, whereas 802.1Q is an internal frame tagging method of VLAN identification.
802.1Q also allows prioritization of traffic using the Priority field within the 802.1Q tag. ISL has three COS bits as well; they automatically map to the IP TOS field. 802.3ac extends Ethernet's frame size to 1522 bytes to allow for the internal tag. Obviously, equipment that doesn't understand these so-called baby giant frames complains.
802.1Q allows VLAN values up to 4095, but the Catalyst may only allow up to 1005, so in a mixed environment it is best practice to not go above 1005.
Configuring 802.1Q on the Catalyst is as easy as using the following command:
set trunk mod#/port# [on | desirable | auto | nonegotiate] dot1q
Using the commands from the ISL section, check your hardware and IOS version to see whether your environment supports ISL, 802.1Q, or both. Although my lab switches default to ISL, there are many switches that default to the dot1Q standard.
EtherChannel is another method of combining multiple segments into one that I briefly mention in the next subsection. Normally if you have multiple parallel connections between the same two switches, you would pass traffic on only one of them. (STP would put the others into blocking state, and they would provide redundancy but no performance advantage.) With EtherChannel, STP treats the aggregate bundle of connections as one logical connection and the individual ports are in forwarding state.
EtherChannel
EtherChannel combines multiple Fast or Gigabit segments where the speeds match into groups of two, four, or eight. However, some switches and cards are less restrictive than others with the way bandwidth is aggregated. On the Cat6000 family, for instance, you can load share traffic on a source/destination IP address basis, in addition to the regular source and destination MAC method. Use the show module command to see whether your switch supports EtherChannel frame distribution so that you can decide whether MAC or IP load sharing is best for your environment.
The EtherChannel group is known by one MAC address: that of the primary link. The primary link is the link with the lowest MAC address, and it is used for control messages and monitoring. Recovery is very important. If the primary link dies, what happens? In the past, the whole group would die. Now, in 4 kbps, 5 kbps, and 6 kbps switches, the link with the next lowest MAC address takes over. In XL-based switches, the link with the lowest utilization at that moment takes over. In the 1900s, you can only have two links in an EtherChannel, so the one left is alone. The bundles can be configured as an EtherChannel trunk. Then when you configure any port in the channel, it applies to all ports. Cisco created the PAgP for channel negotiation with auto and desirable modes.
If two ports are desirable, they trunk in EtherChannel.
Auto and desirable trunk in EtherChannel.
Auto and auto do not trunk because they never negotiate.
You might run across the terms Fast EtherChannel (FEC) and Gigabit EtherChannel (BEC), which are faster Ethernet technologies leveraging off of the link aggregation provided via EtherChannel.
Table 7-3 provides the basic commands to configure EtherChannel. For a more exhaustive list that pertains to additional devices, refer to Cisco.com.
| CatOS | IOS |
|---|---|
| set port channel mod#/ports [admin group] set port channel mod#/port# mode [on|off|desirable|auto] [silent|non-silent] | interface fa0/1
interface fa0/2
|
On MSFC:
interface vlan1
| interface vlan 1
|
| set port channel all distribution {ip|mac}[source|destination|both] | interface fa0/1
|
| show channel group
show channel cost show channel | show etherchannel [summary] show interfaces etherchannel |
If you want to set it up, you could certainly connect the 1900 up to the 2900 or 3512XL to experiment in your lab. However, be careful with switches, such as the XL series, that do not support PAgP. It is recommended to disable the ports on both ends and create the port channel on the XL switch first. Next, create the port channel and set the mode on the CatOS box; then you can re-enable the ports. (The rest of this chapter and the Trouble Tickets do not assume that EtherChannel is configured, however.)
Other Trunking
Other trunking methods are beyond the scope of the book, but are important to you if you are using FDDI or ATM. To enable multiple VLANs to use an FDDI ring, 802.10 encapsulation is available. On the router, the encapsulation type is sde. On the Catalyst, set the VLAN type to FDDI as you create your VLAN, as follows:
set vlan vlan# type fddi
When you create an FDDI VLAN, the switch adds 100,000 to your VLAN number to arrive at a security association identifier (SAID). Verify the SAID with the show vlan command. Catalyst switches also support LANE and MPOA for ATM trunking.
Obviously VLANs are great in that they assist with broadcast domains to help localize traffic. Also, VLANs enable you to use more switches and fewer routers. If not set up and managed properly, however, VLANs result in broken networks. Common issues may include incorrect VTP modes (vanishing VLANs), addressing, access or trunk ports, encapsulation, and STP.