Chapter 18. Tuning and Monitoring IPS
This chapter covers the following topics:
![]() Monitoring and tuning Cisco ASA 5500-X Series IPS devices
Monitoring and tuning Cisco ASA 5500-X Series IPS devices
![]() Displaying and clearing statistics
Displaying and clearing statistics
In Chapter 17, “Implementing ASA Intrusion Prevention System (IPS),” you learned how to configure the Cisco ASA IPS module and learned that it comes with a preset number of signatures enabled. These signatures are suitable in most cases; however, it is important that you tune your Cisco ASA IPS modules when you first deploy them and then tune them again periodically. Failing to do so could result in numerous false positive events (false alarms), which could cause you to overlook real security incidents. The initial tuning probably takes more time than any subsequent tuning. This chapter explains how to tune and monitor the Cisco ASA IPS.
IPS Tuning Process
Tuning is the process by which you configure the Cisco ASA IPS appropriately to decrease the number of false positives and false negatives. Figure 18-1 shows the guidelines to follow when deploying and tuning IPS devices.
The following are the IPS deployment and tuning steps outlined in Figure 18-1:
1. Identify strategic locations for all IPS devices and how they will be configured. For example, consider performance, scalability, and what traffic you are trying to monitor. Cisco recommends that you place IPS devices behind firewalls and any traffic filtering devices. Traffic is filtered, and only traffic destined for the internal devices is processed by the IDS/IPS device. This reduces the device workload and increases performance. This is easily accomplished with the Cisco ASA IPS module.
2. Apply the initial configuration, as covered in Chapter 17.
3. Monitor and analyze the IPS logs and identify which alarms are being triggered because of malicious activity versus normal network activity. Disable alarms that are creating false positives, as discussed later in this section.
The initial monitoring period can last several days to generate sufficient logs and create a baseline of network activity.
You can also deploy a threat-analysis system to help validate the alarms’ significance, impact, and appropriate response. Cisco Security Manager (CSM) allows you to configure and manage sensors, which can be dedicated standalone network appliances, Catalyst 6500 switch modules, service modules running in supported ASA devices or routers, and IPS-enabled Cisco IOS Software images running on integrated services routers. CSM also includes an event manager service that provides an automated, real-time analysis of IPS alarms to eliminate false positives. Other commercial tools useful for monitoring and tuning are covered later in this chapter.
4. Implement the most adequate response actions, such as TCP resets, drop, shunning, and IP logging. Steps on how to configure IPS response actions are covered in Chapter 17.
5. Continuously update the IPS signatures. Configuring automatic signature updates is recommended for ease of management and scalability.
Change a signature’s status by using the status subcommand in signature definition submode. With the use of this command, you can disable or retire a specific signature, as described in the following sections.
Due to the nature of the IPS signatures that are used to detect malicious activity, it is almost impossible to completely eliminate false positives without severely degrading the effectiveness of the IPS or seriously disrupting the computing infrastructure of an organization (such as hosts and networks). Customized tuning when an IPS is deployed minimizes false positives. Periodic retuning is required when the computing environment changes (for example, when new systems and applications are deployed). IPS devices provide a flexible tuning capability that minimizes false positives during steady-state operations. An example of a false positive is a network management station that periodically builds a network discovery map by running ping sweeps. A ping sweep triggers the ICMP Network Sweep with Echo signature (signature ID 2100). Thus, ICMP Network Sweep with Echo events that have the IP address of the network management station as the source address are actually expected and desired events.
As advanced persistent threats (APT), botnets, and other blended threats evolve, signature-based content inspection alone becomes insufficient for threat identification and mitigation. Cisco ASA IPS with Global Correlation provides advanced features to identify and mitigate attackers—not just signature-based attacks. With Cisco IPS global correlation backed by Cisco Security Intelligence Operations (SIO), Cisco ASA IPS gains visibility into hundreds of additional security parameters, millions of rules, and big-data threat intelligence.
Risk Ratings
In Cisco IPS, the risk rating (RR) is a value that characterizes a numerical representation of the risk associated with a particular event triggered by the IPS sensor.
The RR is a value between 0 and 100 (the higher the number, the higher the risk). It is important to know that the RR is associated with the generated IPS alerts, not IPS signatures. This is very useful for an IPS administrator, because it allows you to prioritize alerts that need immediate attention.
Note
The risk rating is reported in the evIdsAlert field.
This risk calculation takes into account the following metrics:
![]() Attack severity rating (ASR)
Attack severity rating (ASR)
![]() Target value rating (TVR)
Target value rating (TVR)
![]() Signature fidelity rating (SFR)
Signature fidelity rating (SFR)
![]() Attack relevance rating (ARR)
Attack relevance rating (ARR)
![]() Promiscuous delta (PD)
Promiscuous delta (PD)
![]() Watch list rating (WLR)
Watch list rating (WLR)
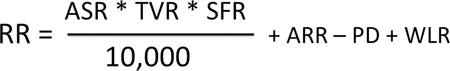
The following is the RR formula:
ASR
The ASR is the metric related with the severity of a successful exploit of a given vulnerability. This is calculated from the alert severity parameter of a specific IPS signature (informational, low, medium, or high).
Note
The ASR is configured on a per-signature basis and does not signify how accurately the IPS module event is detected.
TVR
The TVR is the metric related to the alleged value of the target or victim. The TVR is a user-configurable value (zero, low, medium, high, or mission critical) that identifies the importance of a network asset (through its IP address). Depending on your corporate security policy and your environment, you can assign a TVR to critical systems in the network. For instance, you can assign a higher TVR value to a server in the data center that hosts a critical database, and assign a lower TVR to a user workstation or a printer. The TVR is configured in the event action rules policy.
SFR
The SFR is the metric related to how accurate the IPS signature might be in the network without specific knowledge of the victim. The SFR is assigned on a per-signature basis and defines how accurately the signature detects a potential threat on the network. The IPS signature author is the one that calculates and assigns the SFR. If the signature came from Cisco, it is assigned by the IPS signature developer.
ARR
The ARR is the metric associated with the relevancy of the targeted victim and is a resulting value of how relevant, unknown, or not relevant the target victim. For example, if the IPS signature/event is related to a Linux kernel vulnerability and the targeted host is a Windows server, the attack is not too relevant.
PD
Promiscuous delta is the metric related with the promiscuous delta, which can be subtracted from the overall risk rating if the IPS device runs in promiscuous mode. The PD is configured on a per-signature basis and is a value in the range of 0 to 30. For instance, if the IPS sensor is not inline, the promiscuous delta is subtracted from the overall RR.
WLR
This value is based on events reported in the Cisco Security Agent (CSA) watch list. The value for this factor is between 0 and 35. (The watch list rating was introduced in Cisco IPS Sensor Software Version 6.0.) CSA is no longer sold by Cisco. If CSA is not deployed, this value will be 0.
Disabling IPS Signatures
During the tuning process, you may decide to disable a specific IPS signature if it is no longer relevant or is producing a lot of false positives. If a signature is just disabled, it is still processed by the signature engine and configuration list, but it does not generate any logs. The following steps demonstrate how to disable a specific signature from the Cisco ASA IPS CLI:
1. Log in to the CLI and enter into signature configuration submode:
NewYorkSSM# configure terminal
NewYorkSSM(config)# service signature-definition sig0
2. Select the signature to be disabled:
NewYorkSSM(config-sig)# signatures 20961 0
Signature 20961 is selected in this example.
3. Change the status of the selected signature:
NewYorkSSM(config-sig-sig)# status
NewYorkSSM(config-sig-sig-sta)# enabled false
4. Verify the settings by invoking the show settings command:
NewYorkSSM(config-sig-sig-sta)# show settings
status
------------------------
enabled: false default: false
retired: false <defaulted>
------------------------
5. Exit signature configuration submode and apply the changes to the configuration:
NewYorkSSM(config-sig-sig-sta)# exit
NewYorkSSM(config-sig-sig)# exit
NewYorkSSM(config-sig)# exit
Apply Changes:?[yes]: yes
To disable a specific signature using Cisco Adaptive Security Device Manager (ASDM), navigate to Configuration > IPS > Policies > Signature Definitions > sig0 > All Signatures, search for the specific signature, and uncheck the Enabled check box.
Retiring IPS Signatures
When a signature is retired, it is removed from the engine but remains in the signature configuration list. This signature can later be activated. However, when you reactivate a retired signature, the Cisco ASA IPS needs to rebuild the signature list for that engine, which could delay signature processing. This process could take several minutes.
The following steps demonstrate how to retire a specific signature on the Cisco ASA IPS:
1. Log in to the CLI and enter into signature definition submode:
NewYorkSSM# configure terminal
NewYorkSSM(config)# service signature-definition sig0
2. Select the signature to be retired:
NewYorkSSM(config-sig)# signatures 23456 0
Signature 23456 is selected in this example.
3. Change the status of the selected signature and retire the signature:
NewYorkSSM(config-sig-sig)# status
NewYorkSSM(config-sig-sig-sta)# retired true
4. Verify the settings by invoking the show settings command:
NewYorkSSM(config-sig-sig-sta)# show settings
status
------------------------
enabled: false default: false
retired: true default: false
------------------------
5. Exit signature configuration submode and apply the changes to the configuration:
NewYorkSSM(config-sig-sig-sta)# exit
NewYorkSSM(config-sig-sig)# exit
NewYorkSSM(config-sig)# exit
Apply Changes:?[yes]: yes
To retire a specific signature using ASDM, navigate to Configuration > IPS > Policies > Signature Definitions > sig0 > All Signatures, search for the specific signature, and check the Retired check box under the Status section.
Tools to Help with Monitoring and Tuning
There are several tools and products that enable you to identify, classify, validate, and mitigate security threats, as well as tune your configurations. The analysis and manipulation of the data provided by these features can be a time-consuming process and, in some environments, may even be impossible because of staff requirements.
The following are some of the most popular tools that can help you monitor, tune, and manage your IPS configuration:
![]() Cisco ASDM and Cisco IPS Manager Express (IME)
Cisco ASDM and Cisco IPS Manager Express (IME)
ASDM and IME
ASDM uses IME to configure the Cisco ASA IPS services. ASDM offers the following:
![]() Provisioning, monitoring, and troubleshooting
Provisioning, monitoring, and troubleshooting
![]() Drag-and-drop dashboard gadgets that provide easy customization and personalized views that retain your settings to minimize setup time
Drag-and-drop dashboard gadgets that provide easy customization and personalized views that retain your settings to minimize setup time
![]() A flexible reporting tool for generating custom and compliance reports in seconds
A flexible reporting tool for generating custom and compliance reports in seconds
To access the IPS monitoring capabilities from ASDM, click Monitoring > IPS.
CSM Event Manager
CSM enables a security administrator to manage security policies related to firewall, VPN, and IPS services across Cisco IOS routers, ASA, IPS sensors and modules, Catalyst 6500 and 7600 Series ASA Services Module (ASASM), and several other services modules for Catalyst switches and modules for several Cisco IOS routers.
CSM is used in small-to-medium environments where the network consists of a few devices and in large networks with thousands of devices. CSM provides a tool called Event Manager that can be used to monitor IPS devices, including the Cisco ASA IPS. CSM Event Manager allows you to remove false positive IPS events from the event table very easily.
Removing False Positive IPS Events from the Event Table
The security administrator has the following options to remove false-positive IPS events from the CSM Event Viewer event table:
![]() Filter events from known “trusted” sources
Filter events from known “trusted” sources
![]() Disable the IPS signature in the IPS device
Disable the IPS signature in the IPS device
In certain situations, you may want to filter IPS events or false positives from a trusted known host. When you filter an event in the CSM Event Viewer event table, you do not stop the actual event generation in the IPS device; the events are just not shown in the event table. There are two main disadvantages to using this method:
![]() The events continue to be generated in the IPS device, filling up the event store.
The events continue to be generated in the IPS device, filling up the event store.
![]() The filter excludes all events from a host. You cannot create a custom filter that excludes a combination of an IPS signature triggered by a specific host.
The filter excludes all events from a host. You cannot create a custom filter that excludes a combination of an IPS signature triggered by a specific host.
Splunk
Splunk is a commercial product that can be used to monitor and correlate events from numerous systems, including servers, hosts, virtual machines, databases, network infrastructure devices (i.e., routers and switches), firewalls, and IPS devices. Splunk supports Cisco IPS devices, including the Cisco ASA IPS. For more information about Splunk, visit http://splunk.com.
RSA Security Analytics
RSA Security Analytics is a commercial product, developed by EMC. It can also be used to monitor and correlate events from many different sources and also supports Cisco IPS devices. For more information about RSA Security Analytics, go to http://www.emc.com/security/security-analytics/security-analytics.htm.
Displaying and Clearing Statistics in the Cisco ASA IPS
The CLI enables you to collect statistics about different IPS services, components, and applications. The show statistics command is used to display such information. Example 18-1 shows the show statistics command options.
Example 18-1 show statistics Command Options
NewYorkSSM# show statistics ?
analysis-engine Display analysis engine statistics.
authentication Display authentication statistics.
denied-attackers Display denied attacker statistics.
event-server Display event server statistics.
event-store Display event store statistics.
host Display host statistics.
logger Display logger statistics.
network-access Display network access controller statistics.
notification Display notification statistics.
sdee-server Display SDEE server statistics.
transaction-server Display transaction server statistics.
transaction-source Display transaction source statistics.
virtual-sensor Display virtual sensor statistics.
web-server Display web server statistics.
The show statistics analysis-engine command displays traffic statistics and health information about the Cisco ASA IPS analysis engine. Example 18-2 includes the output of this command.
Example 18-2 show statistics analysis-engine Command Output
NewYorkSSM# show statistics analysis-engine
Analysis Engine Statistics
Number of seconds since service started = 1665921
Measure of the level of current resource utilization = 0
Measure of the level of maximum resource utilization = 0
The rate of TCP connections tracked per second = 0
The rate of packets per second = 0
The rate of bytes per second = 0
Receiver Statistics
Total number of packets processed since reset = 0
Total number of IP packets processed since reset = 0
Transmitter Statistics
Total number of packets transmitted = 0
Total number of packets denied = 0
Total number of packets reset = 0
Fragment Reassembly Unit Statistics
Number of fragments currently in FRU = 0
Number of datagrams currently in FRU = 0
TCP Stream Reassembly Unit Statistics
TCP streams currently in the embryonic state = 0
TCP streams currently in the established state = 0
TCP streams currently in the closing state = 0
TCP streams currently in the system = 0
TCP Packets currently queued for reassembly = 0
The Signature Database Statistics.
Total nodes active = 0
TCP nodes keyed on both IP addresses and both ports = 0
UDP nodes keyed on both IP addresses and both ports = 0
IP nodes keyed on both IP addresses = 0
Statistics for Signature Events
Number of SigEvents since reset = 0
Statistics for Actions executed on a SigEvent
Number of Alerts written to the IdsEventStore = 0
Use the show statistics authentication command to display statistics on failed and total authentication attempts to the Cisco ASA IPS module. Example 18-3 illustrates the output of this command.
Example 18-3 show statistics authentication Command Output
NewYorkSSM# show statistics authentication
General
totalAuthenticationAttempts = 144
failedAuthenticationAttempts = 9
Example 18-3 shows 9 failed authentication attempts out of 144 total attempts.
Example 18-4 includes the output of the show statistics event-server command. This command is used to display the number of open and blocked connections to the Cisco ASA IPS from event management stations.
Example 18-4 show statistics event-server Command Output
NewYorkSSM# show statistics event-server
General
openSubscriptions = 10
blockedSubscriptions = 0
Subscriptions
The show statistics event-store command gives you more useful information. It displays details regarding the event store. Example 18-5 includes the output of this command.
Example 18-5 show statistics event-store Command Output
NewYorkSSM# show statistics event-store
Event store statistics
General information about the event store
The current number of open subscriptions = 10
The number of events lost by subscriptions and queries = 0
The number of queries issued = 0
The number of times the event store circular buffer has wrapped = 0
Number of events of each type currently stored
Debug events = 0
Status events = 59
Log transaction events = 0
Shun request events = 0
Error events, warning = 1
Error events, error = 8
Error events, fatal = 0
Alert events, informational = 2
Alert events, low = 0
Alert events, medium = 0
Alert events, high = 0
Another command that is very useful for troubleshooting is the show statistics host command. It includes network and link statistics, health of the Cisco ASA IPS module (for example, CPU and memory utilization), and other administrative items such as NTP and auto-update statistics. Example 18-6 includes the output of this command.
Example 18-6 show statistics host Command Output
NewYorkSSM# show statistics host
General Statistics
Last Change To Host Config (UTC) = 03:00:39 Tue Feb 15 2005
Command Control Port Device = GigabitEthernet0/0
Network Statistics
ge0_0 Link encap:Ethernet HWaddr 00:0B:FC:F8:01:2C
inet addr:172.23.62.92 Bcast:172.23.62.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:3758776 errors:0 dropped:0 overruns:0 frame:0
TX packets:272436 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:471408183 (449.5 MiB) TX bytes:183240697 (174.7 MiB)
Base address:0xbc00 Memory:f8200000-f8220000
NTP Statistics
status = Not applicable
Memory Usage
usedBytes = 500649984
freeBytes = 1484054528
totalBytes = 1984704512
Swap Usage
Used Bytes = 0
Free Bytes = 0
Total Bytes = 0
Summertime Statistics
start = 03:00:00 PDT Sun Apr 03 2005
end = 01:00:00 GMT-08:00 Sun Oct 30 2005
CPU Statistics
Usage over last 5 seconds = 0
Usage over last minute = 0
Usage over last 5 minutes = 0
Memory Statistics
Memory usage (bytes) = 500559872
Memory free (bytes) = 1484144640
Auto Update Statistics
lastDirectoryReadAttempt = 01:03:09 GMT-08:00 Mon Mar 31 2014
Read directory: scp://[email protected]//updates/sigupdatefile.pkg/
Error: Failed attempt to get directory listing from remote auto update server:
ssh: connect to host 192.168.10.188 port 22: Connection timed out
lastDownloadAttempt = N/A
lastInstallAttempt = N/A
nextAttempt = 01:00:00 GMT-08:00 Wed Feb 16 2005
In the shaded lines in Example 18-6, notice that the Cisco ASA IPS attempted to connect to the server with IP address 192.168.10.188 over SSH (TCP port 22) without success. The connection timed out because of network connectivity problems.
To display IP logger statistics, use the show statistics logger command. The output of this command is included in Example 18-7.
Example 18-7 show statistics logger Command Output
NewYorkSSM# show statistics logger
The number of Log interprocessor FIFO overruns = 0
The number of syslog messages received = 331
The number of <evError> events written to the event store by severity
Fatal Severity = 0
Error Severity = 78
Warning Severity = 358
TOTAL = 436
The number of log messages written to the message log by severity
Fatal Severity = 0
Error Severity = 78
Warning Severity = 27
Timing Severity = 0
Debug Severity = 0
Unknown Severity = 62
TOTAL = 167
Summary
In the “real world,” it is almost impossible to completely eliminate false positives without severely degrading the effectiveness of the IPS or severely disrupting the computing infrastructure of an organization. Customized tuning when an IPS is deployed minimizes false positives. This chapter introduced the importance of carefully tuning IPS devices, including the Cisco ASA IPS, to minimize the risk of false positives and false negatives. Instructions on how to disable and retire IPS signatures were provided. Careful monitoring is crucial to the security lifecycle. This chapter introduced several Cisco and non-Cisco security tools that can be used to monitor IPS devices, making the tuning process a lot easier. High-level monitoring and statistical commands were also covered to enhance learning.

