18. Creating a Windows Network
Creating or Joining a Network
If you have two or more computers in your home or office, for about the cost of a trip to the movies, you can set up a network that will let everyone trade music, videos, and documents, use the same printer and Internet connection, and back up files, almost effortlessly. It’s not as hard or expensive as you might think. After you’ve done the planning and shopping, you should be able to get a network up and running in an hour or two.
This chapter should give you all the information you need. Then check out Chapter 19, “Connecting Your Network to the Internet,” and if you have computers with older versions of Windows or other operating systems, Chapter 20, “Networking with Other Operating Systems.”
If you’re just adding a computer to an existing Ethernet network, you can skip ahead to the section “Installing Network Adapters.” If you’re joining an existing wireless network, see “Joining a Wireless Network” in Chapter 36, “Wireless Networking.”
If you have high-speed Internet service and your ISP provided you with a router when you started your service, you already have the makings of a network. If you want to share files and printers, perform backups, and so on, you just need to make sure that your router is set up securely, and you might need to change a few settings in Windows. You can skip ahead to “Installing Network Adapters,” later in this chapter, to see how to do this.
Planning Your Network
You must plan your network around your own particular needs. What do you expect from a network? The following tasks are some you might want your network to perform:
![]() Share printers, files, optical (Blu-ray, DVD, and CD) drives, music, and videos between your devices
Share printers, files, optical (Blu-ray, DVD, and CD) drives, music, and videos between your devices
![]() Share an Internet connection
Share an Internet connection
![]() Provide wireless Internet access to laptops and mobile devices
Provide wireless Internet access to laptops and mobile devices
![]() Receive faxes directly in one computer and print or route them to individuals automatically
Receive faxes directly in one computer and print or route them to individuals automatically
![]() Provide access to another network at another location
Provide access to another network at another location
![]() Provide remote access so that you can reach your LAN from elsewhere, via the Internet or even a modem
Provide remote access so that you can reach your LAN from elsewhere, via the Internet or even a modem
![]() Host a website
Host a website
![]() Operate a database server
Operate a database server
![]() Play multiuser games
Play multiuser games
You should make a list of your networking goals. You must provide adequate capacity to meet these and future needs, but you also don’t need to overbuild.
On the other hand, if you need access to large databases, require the centralized user account control provided by the Windows Server operating system, or require centralized backup of all workstations, you must plan and invest more carefully. We discuss some of the issues you should consider in the next section.
Are You Being Served?
If you’re planning a network of more than just a few computers, you need to make a big decision: whether to use Windows Server. The Server versions provide a raft of networking services that Windows 10 doesn’t have, but you must learn how to configure and support them.
![]() Note
Note
When we talk about Windows Server here, we mean the business Server versions. There was at one time a product called Windows Home Server, but it was meant just to let you back up files across the network.
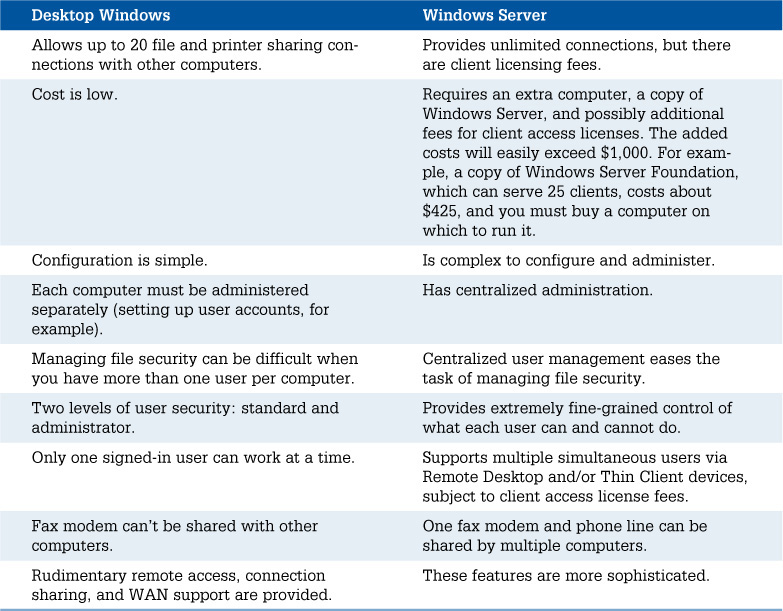
Table 18.1 lists the primary trade-offs between the regular desktop versions of Windows and Windows Server.
For us, manageability is the main issue. As you add more and more users, centralized management becomes more and more important. If you have a network of 10 or more computers, we recommend using at least one copy of Windows Server.
You can certainly use Server with smaller networks, too. The following are reasons for doing so:
![]() You want to join your network to a Server domain somewhere else. This is often the case in a business’s branch office.
You want to join your network to a Server domain somewhere else. This is often the case in a business’s branch office.
![]() You want to support multiple simultaneous remote desktop or virtual private network (VPN) users. (Alternatively, you could buy inexpensive VPN routers or software to handle this task.)
You want to support multiple simultaneous remote desktop or virtual private network (VPN) users. (Alternatively, you could buy inexpensive VPN routers or software to handle this task.)
![]() You want to exercise strict security controls, support multiple signed-in users on one computer, restrict your users’ abilities to change system settings, or use automatic application installation.
You want to exercise strict security controls, support multiple signed-in users on one computer, restrict your users’ abilities to change system settings, or use automatic application installation.
![]() You want to take advantage of advanced networking services such as Group Policy, DHCP, DNS, and so on.
You want to take advantage of advanced networking services such as Group Policy, DHCP, DNS, and so on.
If you decide you need or want Windows Server, you should get a book dedicated to that OS and a big box of Alka-Seltzer before you go any further.
When to Hire a Professional
You’ve probably heard this adage: “If you want something done right, do it yourself!” It is true, to a point. Sometimes, though, the benefit of hiring someone else outweighs the pleasure of doing it yourself.
For a home network, you should definitely try to set it up yourself. Call it a learning experience, get friends to help, and, if you run into problems, a high-school–aged neighbor can probably get them straightened out in 15 minutes. As long as you don’t have to run wires through the wall or construct your own cables, you should be able to manage this job even with no prior networking experience. When something is called “Plug and Play” now, it really is.
The balance tips the other way for a business. If you depend on your computers to get your work done, getting them set up should be your first concern, but keeping them working should be your second, third, and fourth. When your business is hanging in the balance, you should consider the cost of computer failure when you’re deciding whether it’s worth spending money on setup and installation. Hiring a good consultant and/or contractor will give you the following:
![]() An established relationship. If something goes wrong, you’ll already know whom to call, and that person will already know the details of your system.
An established relationship. If something goes wrong, you’ll already know whom to call, and that person will already know the details of your system.
![]() A professional installation job.
A professional installation job.
![]() The benefit of full-time experience in network and system design without needing to pay a full-time salary.
The benefit of full-time experience in network and system design without needing to pay a full-time salary.
![]() Documentation that describes how your network is set up.
Documentation that describes how your network is set up.
![]() Time you can spend doing something more productive than installing a network.
Time you can spend doing something more productive than installing a network.
If you do hire someone else to build your network, you should check out that person’s references first. You also should stay involved in the process so that you understand the choices and decisions that are made.
Choosing a Network and Cabling System
For a simple home or small office network, you can choose among four types of network connections:
![]() 10/100BASE-T Ethernet over CAT-5 cables—These cables look like telephone cables, with a fatter version of a telephone modular connector at each end. This networking scheme is dirt cheap and ultra-reliable, and can carry data at up to 100Mbps.
10/100BASE-T Ethernet over CAT-5 cables—These cables look like telephone cables, with a fatter version of a telephone modular connector at each end. This networking scheme is dirt cheap and ultra-reliable, and can carry data at up to 100Mbps.
![]() 1000Mbps (Gigabit) Ethernet over CAT-5E cables—These cables look like CAT-5 cables, but they are capable of carrying the higher-speed signals required by Gigabit Ethernet. The higher speed is great, but worth the extra cost only if you routinely back up hard disks or copy huge video files over your network, and if the devices you’re copying to and from can keep up with gigabit speeds. (Many can’t.) You’ll also want to consider using Gigabit Ethernet if you have Internet service that provides 50 Mbps or more. We talk more about this in the following sections. You’ll often see Gigabit Ethernet referred to in computer specs as 10/100/1000Mbps.
1000Mbps (Gigabit) Ethernet over CAT-5E cables—These cables look like CAT-5 cables, but they are capable of carrying the higher-speed signals required by Gigabit Ethernet. The higher speed is great, but worth the extra cost only if you routinely back up hard disks or copy huge video files over your network, and if the devices you’re copying to and from can keep up with gigabit speeds. (Many can’t.) You’ll also want to consider using Gigabit Ethernet if you have Internet service that provides 50 Mbps or more. We talk more about this in the following sections. You’ll often see Gigabit Ethernet referred to in computer specs as 10/100/1000Mbps.
![]() 802.11n, -ac or -g wireless networking—Wireless (Wi-Fi) networking sends data over a radio signal, so no cabling is necessary. It’s easy to set up, but it can’t be used over long distances, and in some buildings the signal might not go as far or as fast as the advertising leads you to believe it will.
802.11n, -ac or -g wireless networking—Wireless (Wi-Fi) networking sends data over a radio signal, so no cabling is necessary. It’s easy to set up, but it can’t be used over long distances, and in some buildings the signal might not go as far or as fast as the advertising leads you to believe it will.
![]() Powerline networking—You can purchase network adapters that send data signals between your electrical outlets. In most cases, though, you might be better off using Wi-Fi.
Powerline networking—You can purchase network adapters that send data signals between your electrical outlets. In most cases, though, you might be better off using Wi-Fi.
![]() Note
Note
The CAT in CAT-5 cable stands for Category, a rating scheme that indicates the maximum speed at which the cable is designed and certified to carry data at distances of up to 100 meters (about 330 feet):

All of these cable types have four pairs of wires, with the wires in each pair twisted together to minimize the effect of outside electrical interference. The most commonly used CAT-1 through CAT-6 cabling has no metal or foil wrapped around the outside of the wires, just a plastic jacket. This type of cable is called unshielded twisted pair, or UTP. Shielded STP cable adds a braided metal or foil layer around the twisted wires to provide additional protection from electrical interference. CAT-6a cable is shielded, and (expensive) shielded versions of the lower CAT levels exist for use in electrically noisy environments such as factories.
For any given type of service you must use cabling of the required CAT level or higher, but never lower. You could use CAT-6 cabling for telephone wiring, but you can’t expect reliable service if you try to use CAT-3 cable for gigabit Ethernet. You may notice that CAT-5e and CAT-6 have the same maximum speed. CAT-6 works better for Gigabit Ethernet on long cable runs, and can carry 10Gbps Ethernet up to 50 meters.
Each step up on the CAT scale increases the cost of the cable by about 20%, give or take. Still, we recommend CAT-5e for all new installations, so that if you decide now or later to upgrade to gigabit Ethernet you won’t have to replace your cabling.
For most homes and offices, a combination of 10/100 Ethernet and wireless is a winning combination, but any of these four options will provide perfectly adequate performance.
In the following sections, we go over each type in a little more detail. Then we discuss additional network features you might want to consider, such as printing and Internet connectivity.
10/100BASE-T Ethernet
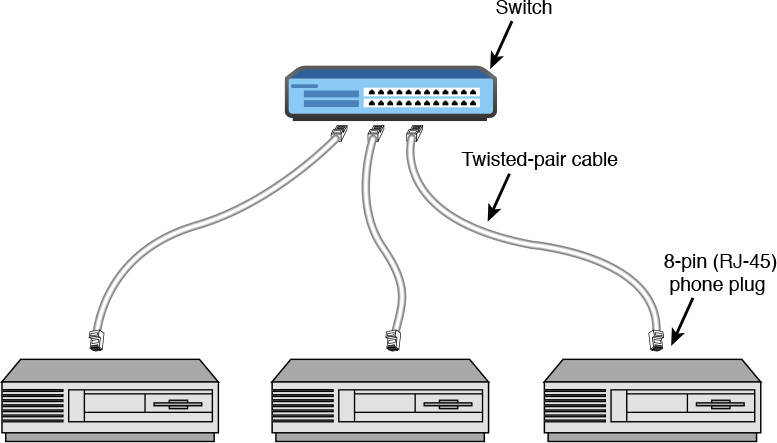
10/100BASE-T Ethernet networks use unshielded twisted-pair cabling (commonly called UTP or CAT-5 cable) run from each computer to a device called a switch or router, as shown in Figure 18.1.
Figure 18.1 A 10/100BASE-T network connects each computer to a central device called a switch, router, or hub.
![]() Tip
Tip
Most home routers, which are used to share a broadband Internet connection and establish a wireless network, include a switch, and most people can base their network on one of these.
Whether or not you’re going to set up a shared broadband Internet connection, we recommend that you buy a wireless router instead of a plain switch, just to get the wireless networking and DHCP services it provides (more on that later in the chapter). On sale, these routers can cost no more than a plain switch. We’ve even seen ads for $20 routers with a $20 mail-in rebate. See Chapter 19 for advice about hardware-connection-sharing devices.
The 10/100 part of the name means that the equipment can run at 100Mbps, but it can automatically slow down to 10Mbps if it’s connected to older 10BASE-T equipment. However, 10BASE-T equipment hasn’t been made in more than a decade, so that’s unlikely to be an issue.
The cables look like telephone cables, and the connectors look like wider versions of telephone modular plugs, but it’s a dangerous comparison because the electrical properties of the cables and connectors are specifically tuned for networking, and ordinary telephone cabling will not work.
These networks require you to use cable designated CAT-5 or better. They have labels on the wire that state this clearly. CAT-5, CAT-5e, and CAT-6 are all fine. You can buy premade network cables in lengths of 3–50 feet, or you can buy bulk cable and attach the connectors yourself. We discuss this more in the “Installing Network Wiring” section, later in this chapter. All cable connectors and data wall jacks must be CAT-5 certified as well.
![]() Tip
Tip
If your network is small and/or temporary, you can run network cables along walls and desks. Otherwise, you probably should keep them out of the way and protect them from accidental damage by installing them within the walls or ceiling of your home or office. If you use in-wall wiring, the work should be done by someone with professional-level skills. You also can get cable covers and sleeves to hide and protect cables where they run across floors, walls, or furniture.
A cable is run from each computer to a switch, which routes the signals between each computer. You must get a switch that has at least as many ports (sockets) as you have computers, plus a spare or two. 10/100BASE-T switches cost roughly $5–$10 per port.
No 10/100 BASE-T cable can be more than 100 meters (328 feet) in length. To extend farther than that, you must add an additional switch in the middle of a longer cable run or use fiber optic cabling.
![]() Tip
Tip
Multiple switches can be connected if your network grows beyond the capacity of your first switch. Therefore, you can add on instead of entirely replacing your original equipment.
For the rare computer that doesn’t have a built-in Ethernet adapter, 10/100BASE-T network interface cards (NICs) are available for as little as $5 each (if you catch a sale) and are made by dozens of companies. Most generic-brand, cheap-o NICs are based on one of a handful of standard circuit chips, so they’ll usually work just fine, even if they’re not listed in the Windows Compatibility Center at www.microsoft.com/windows/compatibility.
Overall, 10/100BASE-T networking is as inexpensive as it gets. Hooking up three computers will set you back between $20 and $75. It’s easy to set up, and it’s very reliable. On the down side, though, you do need to run those wires around.
![]() Note
Note
Add-on adapters come in three styles: internal PCI cards for desktop computers; external adapters that you connect to a USB socket; and thin, credit-card-sized PC Card or ExpressCard adapters for laptops. You probably don’t need to add one, though, because just about any computer capable of running Windows 10 already has a Wi-Fi adapter or 10/100 or 10/100/1000 Ethernet adapter built in.
801.11ac, 802.11n, and 802.11g Wireless (Wi-Fi) Networking
One way to build a network without switches, cables, connectors, drills, swearing, tools, or outside contractors is to go wireless. Prices have fallen to the point that wireless connectivity is competitive with wired networks, even before the installation cost savings are factored in.
There are three common standards for wireless data networking: 802.11g (or Wireless-G), 802.11n (or Wireless-N), and the latest generation of wireless titled 802.11ac (Wireless-AC), named after the industry standard documents on which they’re based. Networking hardware is labeled and marketed using the fastest standard it supports, so for example, you might see a router labeled as an 802.11n router, but the software in the devices can typically also support at least some older, slower standards.
802.11g supports data speeds up to 54Mbps and is compatible with older equipment designed for 802.11b (11Mbps). Some manufacturers offer Wireless-G equipment that operates at up to 108Mbps, but you get this speed boost only if you buy all your equipment from the same manufacturer (and even then, you must read the packaging carefully to see whether the double-speed function will work with the particular parts you’re buying). Wireless-G can transmit data about 100 feet indoors and up to 300 feet outdoors—at most. And at these longer distances, lower signal strengths will result in data errors, so the equipment will switch down to lower data speeds.
![]() Note
Note
Some additional terminology: Wi-Fi stands for Wireless Fidelity. It’s an industry term that doesn’t mean anything in particular, but it’s kind of catchy. It’s used to refer to any variant of 802.11 wireless networking. Wireless local area networks are often called WLANs.
A better level of service is offered by the newer 802.11n (Wireless-N) standard. It comes with higher speeds—up to 150Mbps—and greater range than Wireless-G. Here’s the skinny on Wireless-N:
![]() Devices designed for Wireless-N, -G, and -B are compatible and can be used together on the same network. That is, a -G network adapter in a computer can talk with an -N router, and vice versa. However, they’ll communicate with each other at the lower -G speed. Older -B equipment can be used, too, but again, at the lower -B speed.
Devices designed for Wireless-N, -G, and -B are compatible and can be used together on the same network. That is, a -G network adapter in a computer can talk with an -N router, and vice versa. However, they’ll communicate with each other at the lower -G speed. Older -B equipment can be used, too, but again, at the lower -B speed.
![]() Having -G or -B equipment on the network can drag down the speed as much as 25%, even for -N devices talking to -N, if the older devices are transmitting at the same time.
Having -G or -B equipment on the network can drag down the speed as much as 25%, even for -N devices talking to -N, if the older devices are transmitting at the same time.
![]() Wireless-N signals should travel about twice as far as Wireless-G: about 200 feet indoors and about 600 feet outdoors. However, this applies only when an -N device is talking to another -N device. Getting a Wireless-N router won’t improve reception for a distant Wireless-G or -B device.
Wireless-N signals should travel about twice as far as Wireless-G: about 200 feet indoors and about 600 feet outdoors. However, this applies only when an -N device is talking to another -N device. Getting a Wireless-N router won’t improve reception for a distant Wireless-G or -B device.
![]() Wireless-N can operate in the 2.4GHz frequency band and the 5GHz band. Only “dual-radio” routers can operate at both frequencies at the same time, however. Single-radio routers must switch back and forth, slowing performance if both frequencies are used at the same time. The 5GHz band tends to work better than 2.4GHz at shorter distances. At 5GHz, the signal can’t travel as far, but there tends to be less interference from neighboring networks, cordless phones, and so on.
Wireless-N can operate in the 2.4GHz frequency band and the 5GHz band. Only “dual-radio” routers can operate at both frequencies at the same time, however. Single-radio routers must switch back and forth, slowing performance if both frequencies are used at the same time. The 5GHz band tends to work better than 2.4GHz at shorter distances. At 5GHz, the signal can’t travel as far, but there tends to be less interference from neighboring networks, cordless phones, and so on.
Most Wi-Fi equipment sold today is Wireless-N.
The newest standard is 802.11ac, which offers transfer rates of 500Mbps to well over 1Gbps—staggeringly fast for a wireless connection, at a commensurately high price. To get the top speeds, you need an expensive multiple-antenna router and a multiple-antenna wireless adapter on each computer and home entertainment device. Considering that most home Internet service can feed your network at less than one-tenth of Wireless-AC’s speed, unless you have ultra-high-speed Internet service or you’re distributing video to ultra-high-def televisions, for most users this level of Wi-Fi service is overkill.
Whichever version you use, Wi-Fi networking products in real-world operating conditions typically provide data throughput at about half the advertised speed. If your computer doesn’t have Wi-Fi built in, the cost of adding a USB or internal adapter is about $25–$70. You also must add a device that coordinates the communication between Wi-Fi–enabled computers, the Internet, and any computers that have wired Ethernet connections. There are three types of devices:
![]() Router—These devices transfer data to and from Wi-Fi–connected devices, and typically also have Ethernet jacks for wired computers. They also have one designated Ethernet port that connects to a DSL or cable Internet modem or other external network. The routing function isolates your wireless and Ethernet-wired computers from that Internet connection so that you can safely share files and other content on your network. Many broadband (cable or DSL) modems have a Wi-Fi router built in.
Router—These devices transfer data to and from Wi-Fi–connected devices, and typically also have Ethernet jacks for wired computers. They also have one designated Ethernet port that connects to a DSL or cable Internet modem or other external network. The routing function isolates your wireless and Ethernet-wired computers from that Internet connection so that you can safely share files and other content on your network. Many broadband (cable or DSL) modems have a Wi-Fi router built in.
![]() Access Point or Wireless/Ethernet Bridge—These are like routers except they simply pass data back and forth between Wi-Fi devices and a wired, Ethernet network, without the firewall function that a router provides.
Access Point or Wireless/Ethernet Bridge—These are like routers except they simply pass data back and forth between Wi-Fi devices and a wired, Ethernet network, without the firewall function that a router provides.
![]() Wireless Range Extender—These simply relay data between Wi-Fi–connected devices and another router or access point. If you find that your computer or tablet can’t get a good signal when it tries to connect directly to your router or access point, you might be able to get better performance by installing a range extender halfway between them.
Wireless Range Extender—These simply relay data between Wi-Fi–connected devices and another router or access point. If you find that your computer or tablet can’t get a good signal when it tries to connect directly to your router or access point, you might be able to get better performance by installing a range extender halfway between them.
Some manufactures make devices that can perform more than one or even all three of these functions by changing software settings in the device.
Wi-Fi works well in typical home environments where you don’t have solid metal sheeting separating rooms or floors, over distances of several rooms. For longer distances, or in office settings, you might need to install multiple Wi-Fi devices (called routers, repeaters, or access points) to get good coverage. We talk more about these shortly. Wi-Fi equipment tends to lose the signal every so often, struggling for a few seconds to regain the connection. For this reason, wired Ethernet is the more reliable, faster option for computers that are within easy wiring distance. You can use both, because most Wi-Fi routers have Ethernet jacks that let you plug in wired computers.
Figure 18.2 shows a typical family of wireless products: a wireless access point (Wireless-Ethernet bridge), a wireless router that can also share a DSL or other broadband Internet connection, an internal wireless network adapter for desktop computers, and a PC card adapter for older laptops.
Figure 18.2 Typical wireless networking equipment. Clockwise from upper left: access point, router, PCI adapter, PC Card adapter. (Photo used by permission of D-Link.)
Powerline Networking
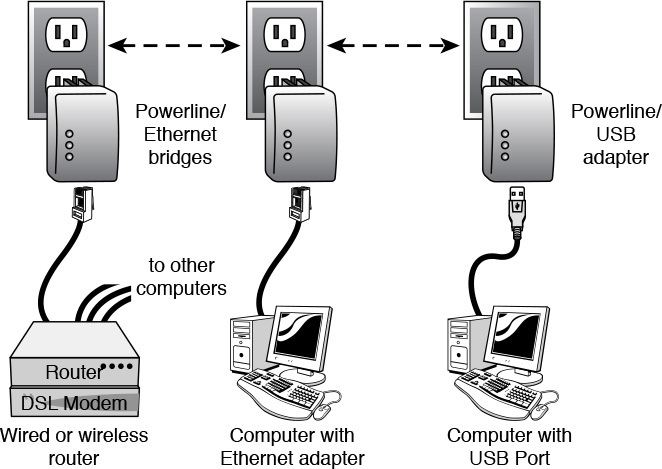
HomePlug (HomePlug Powerline Alliance) adapters send network data through your home or office’s electrical wiring and are plugged in to a wall socket. These provide 10Mbps performance, and all you need is an electrical outlet near each of the connected computers. Powerline networking can’t cross the utility company’s transformers, though, so it usually works only within a single home or office.
In addition, you can get HomePlug devices called bridges, which are specifically designed to link a wired network to the powerline network, for about $50. You can use one of these to connect with a router and/or wired computers. Figure 18.3 shows how this would look in a typical home network.
Adapters that can piggyback network signals on your home’s telephone wiring (called HomePNA or HPNA equipment) also are available, but this technology has fallen out of favor and is not manufactured by the major networking companies anymore.
1000Mbps Ethernet (Gigabit Ethernet)
Gigabit Ethernet networking is probably overkill for most home and small office networks, but Gigabit speed can help if you back up your hard disk over your network from one computer to another, routinely copy large video files, or stream high-definition video to multiple televisions. The adapter cost is so low that many new PCs and all Macs come with 10/100/1000Mbps Ethernet adapters built in as standard equipment.
It sounds great at first, but here are some things to consider:
![]() It won’t speed up your Internet connection (unless, perhaps, you have Fiber-to-the-Home service), and it won’t improve the streaming of regular HD video within your home. Standard 100Mbps Ethernet will do just fine for these applications.
It won’t speed up your Internet connection (unless, perhaps, you have Fiber-to-the-Home service), and it won’t improve the streaming of regular HD video within your home. Standard 100Mbps Ethernet will do just fine for these applications.
![]() Most Internet modems/routers have a built-in Ethernet switch that supports only 100Mbps connections. So, any computers plugged in to them won’t get gigabit throughput to each other. We discuss this in the accompanying note.
Most Internet modems/routers have a built-in Ethernet switch that supports only 100Mbps connections. So, any computers plugged in to them won’t get gigabit throughput to each other. We discuss this in the accompanying note.
![]() You will realize a speed benefit only when a large amount of data is moving between two devices that both have gigabit connections and when both can actually feed data to the network at a high speed.
You will realize a speed benefit only when a large amount of data is moving between two devices that both have gigabit connections and when both can actually feed data to the network at a high speed.
![]() If you have to buy a gigabit Ethernet adapter for a desktop computer (that is, if the adapter built in to the computer’s motherboard is only 10/100Mbps), it makes sense to go gigabit only if you can install a PCI-e adapter. Regular PCI cards and USB adapters can’t move data to and from the CPU fast enough to make gigabit worthwhile.
If you have to buy a gigabit Ethernet adapter for a desktop computer (that is, if the adapter built in to the computer’s motherboard is only 10/100Mbps), it makes sense to go gigabit only if you can install a PCI-e adapter. Regular PCI cards and USB adapters can’t move data to and from the CPU fast enough to make gigabit worthwhile.
![]() Most consumer/small office network-attached storage (disk) devices are way too slow internally to benefit from gigabit connections. You should see a benefit when backing up to or copying files to or from another Windows computer’s shared drive.
Most consumer/small office network-attached storage (disk) devices are way too slow internally to benefit from gigabit connections. You should see a benefit when backing up to or copying files to or from another Windows computer’s shared drive.
![]() Note
Note
Most wireless cable/DSL-sharing routers have built-in switches that support at most only 100Mbps, or only 10Mbps in some cases. If you use a combination cable/DSL modem and router, and yours tops out at 100Mbps, plug in your computers to a gigabit (10/100/1000Mbps) switch using CAT-6 cables and then connect the switch’s “cascade” port to your router. Otherwise, your computers will talk only at 100Mbps maximum.
If you want to use Gigabit Ethernet, you must use CAT-5E or CAT-6 certified connectors and cabling; CAT-5 gear might work for very short cable lengths, but don’t chance it. You should use only commercially manufactured patch cables or professional-quality custom wiring.
Adding Additional Networking Functions
Besides sharing files between computers, you can do several other things with a network. In the next few sections, we outline some additional features you might want to include in your network.
Printing and Faxing
Individual computers can share the local printers attached to them on the local network. Other computers can then access the printer through the network, provided the host computer is running. However, if you need to put a printer farther than about 10 feet away from a networked computer, beyond the reach of a standard USB or parallel cable, you have three choices:
![]() Get a really long cable and take your chances. The electrical signal for a USB or parallel printer connection is not supposed to be extended more than a few feet (10 feet for USB, 12 feet for USB-2). Buy a high-quality shielded cable. You might get data errors (bad printed characters) with this approach.
Get a really long cable and take your chances. The electrical signal for a USB or parallel printer connection is not supposed to be extended more than a few feet (10 feet for USB, 12 feet for USB-2). Buy a high-quality shielded cable. You might get data errors (bad printed characters) with this approach.
![]() Alternatively, you can buy a “print server” module, which connects to the printer on one side and to a network cable on the other, for about $40. Network supply catalogs list myriad such devices. Some newer Internet routers and wireless access points have a print server built in.
Alternatively, you can buy a “print server” module, which connects to the printer on one side and to a network cable on the other, for about $40. Network supply catalogs list myriad such devices. Some newer Internet routers and wireless access points have a print server built in.
![]() Use a network-capable printer and connect it directly to your network. Some printers have Ethernet or wireless networking capability built in. For some printers, you can buy an add-on network printer module.
Use a network-capable printer and connect it directly to your network. Some printers have Ethernet or wireless networking capability built in. For some printers, you can buy an add-on network printer module.
![]() Note
Note
A network-capable all-in-one laser printer/scanner/fax/copier is a great addition. Anyone on the network can use it to print, send faxes, or scan documents. Read reviews before you buy, though, because some devices are great at advanced networking but not so great at the basics, such as feeding paper through without getting jammed up.
The last two approaches are very nice because they allow any computer to communicate directly with the printer. They don’t require you to leave one computer turned on all the time. With standard printer sharing, the computer that “owns” the printer must be turned on for other computers to use the printer.
If several people on your network need to send or receive faxes, you might want to set up a network-based faxing system. Unfortunately, Windows 10 does not let you share your fax modem with other users on your network, as Windows Server does. If you want to share a single fax line with several users on your network, you must use a third-party solution. The easiest approach is to use a “network-ready” all-in-one printer/scanner/fax unit. If you shop for one of these, be sure that its faxing features are network compatible.
Third-party software products are available that can give network users shared access to a fax modem. The former gold standard product was Symantec’s WinFax Pro, but it has been discontinued, and most of the products still on the market seem to be oriented toward large corporations. For a small office network, you might consider products such as Snappy Fax Network Server from www.snappysoftware.com or ActFax from www.actfax.com.
Providing Internet Connectivity
One of the best reasons for having a network is to share high-speed Internet service. It’s far less expensive, and far safer security-wise, to have one connection to the Internet for the entire LAN than to let users fend for themselves. In fact, many DSL and cable Internet providers now supply preconfigured routers when you start your service. If that’s the case for you, you might only need to configure your computers to use the shared connection, as we discuss later in this chapter under “Configuring a Peer-to-Peer Network.”
Windows has a built-in Internet Connection Sharing feature that lets a single computer use a dial-up, cable, or DSL modem and make the connection on behalf of any user on your LAN. You can also use an inexpensive hardware device called a router to make the connection. I strongly prefer the hardware devices over Windows Internet Connection Sharing. This topic is important enough that it gets its own chapter. If you want to share an Internet connection on your network, you should read Chapter 19 before you buy any equipment.
You should also study Chapter 33, “Protecting Your Network from Hackers and Snoops,” and pay close attention to the section titled “Preparation: Network Security Basics” to build in proper safeguards against hacking and abuse. This is especially important with full-time cable/DSL connections.
Providing Remote Access
You also can provide connectivity to your network from the outside world, either through the Internet or a dial-up modem. This connectivity enables you to access your LAN resources from home or out in the field, with full assurance that your network is safe from outside attacks. Chapter 37, “Networking on the Road,” covers Internet VPN network access, and Chapter 39, “Remote Desktop and Remote Access,” covers Remote Desktop.
If you want to access your home network while you’re away, you might also consider getting a connection-sharing router with built-in VPN support, as mentioned in the next section. These days, most people use a cloud-based file storage system, such as OneDrive or Google Drive, to eliminate the need for this kind of remote access, but you must weigh the convenience they provide against the potential loss of privacy that comes with the cloud services.
Connecting to a Remote Network
Windows supports a Virtual Private Networking (VPN) mechanism that lets you temporarily connect your Windows device to a network in a remote location through the Internet. (We talk about that in Chapter 37.)
You could also permanently tie your entire LAN to a network in another location so that you and the other network’s users can share files and printers as if you were all in the same room, without having to establish individual temporary connections. Windows Server has many features to support this capability, but you can also do it with smaller networks without Windows Server. There are two straightforward ways to do this: by getting routers that have built-in virtual private networking (VPN) support and by using a software service. For a hardware approach, Linksys, Asus, Trendnet, and other manufacturers sell inexpensive routers with VPN capability. The router in one office is set up as the VPN “host” or server, and the routers in other offices are set up to connect to that. This ties the separate networks together. For a software solution, check out the Hamachi product from logmein.com. You can tie individual computers into a VPN, or you can set up one computer on each network to act as a “gateway.”
Installing Network Adapters
Most computers capable of running Windows 10 already have an Ethernet or Wi-Fi adapter built in. However, if yours doesn’t have one, or if you have to add an additional adapter in your computer, follow the manufacturer’s instructions for installing its product for Windows 10, 8.1, or 8. If there are instructions for Windows 7 or Vista but not Windows 8, 8.1, or 10, those instructions should work fine. And if there are no instructions at all, just follow these steps:
1. If you have purchased an internal card, shut down Windows, shut off the computer, unplug it, open the case, and install the card in an empty slot. Close the case, plug in the cord, and then restart Windows.
If you are adding an external USB adapter, be sure you’re logged on with an administrator account, plug it in while Windows is running, and skip ahead to step 3.
![]() Tip
Tip
If you’ve never worked inside your computer, jump ahead to Chapter 28, “Managing Your Hardware,” for advice and handy tips.
2. When you’re back at the Windows sign-in screen, sign in using an account with administrator privileges. Windows displays the New Hardware Detected dialog box when you log in.
3. In most cases, Windows should already have the software it needs to run your network adapter. If Windows cannot find a suitable driver for your adapter, it might ask you to insert the driver disc that your network card’s manufacturer should have provided. It also might offer to get a driver from Windows Update. If you have an Internet connection up at this time, this online option is very useful.
![]() Note
Note
The exact names of the folders containing device drivers vary from vendor to vendor. You might have to poke around a little on the disc to find the right folder.
If you are asked, insert the requested disc and click OK. In the unlikely event that Windows says that it cannot locate an appropriate device driver, try again, but this time click the Browse button. Locate a folder whose name resembles that of your version of Windows, and click OK. If both 32-bit and 64-bit folders are listed, be sure to choose the version that matches your version of Windows.
4. After Windows has installed the card’s driver software, it automatically configures and uses the card. Check the Device Manager, as described in the next section, to see whether the card is installed and functioning. Then you can proceed to “Installing Network Wiring,” later in this chapter.
![]() For more detailed instructions about installing devices and drivers, see “Installing Devices,” p. 647 and “Working with Device Drivers,” p. 659.
For more detailed instructions about installing devices and drivers, see “Installing Devices,” p. 647 and “Working with Device Drivers,” p. 659.
Checking Existing Adapters
If your adapter was already installed when you set up Windows, it should be ready to go. Follow these steps to see whether the adapter is already set up:
1. Press Windows Logo+X and select Device Manager. Expand the Network Adapters section by clicking the triangular arrow icon to the left of its name.
2. Look for an entry for your network card. If it appears and does not have a yellow icon with an exclamation point (!) in it to the left of its name, the card is installed and correctly configured. In this case, you can skip ahead to “Installing Network Wiring.”
If an entry appears but has a yellow exclamation point icon by its name, the card is not correctly configured.
![]() Note
Note
If you see an exclamation point icon in the Network Adapters list, skip ahead to Chapter 26, “Troubleshooting and Repairing Problems,” for tips on getting the card to work before you proceed. Here’s a tip: Network adapters are really inexpensive, so if you’re having trouble with an old adapter, just go get a new one.
3. If no entry exists for the card, the adapter is not fully plugged in to its connector, it’s damaged, or it is not Plug-and-Play capable. Be sure the card is installed correctly. If you can’t get it to appear, replace it.
Installing Multiple Network Adapters
You might want to install multiple network adapters in your computer in the following situations:
![]() You simultaneously connect to two or more different networks with different IP addresses or protocols. You’d use a separate adapter to connect to each network.
You simultaneously connect to two or more different networks with different IP addresses or protocols. You’d use a separate adapter to connect to each network.
![]() You want to share a broadband cable or DSL Internet connection with other computers on your LAN without using a router. We strongly recommend using a router, as discussed in Chapter 20, but you can also do this using one adapter to connect to your LAN and another to connect to your cable or DSL modem.
You want to share a broadband cable or DSL Internet connection with other computers on your LAN without using a router. We strongly recommend using a router, as discussed in Chapter 20, but you can also do this using one adapter to connect to your LAN and another to connect to your cable or DSL modem.
![]() You have two different network types, such as powerline and Ethernet, and you want the computers on both LAN types to be able to communicate. You could use a hardware bridge or access point, but you could also install both types of adapters in one of your computers and use the Bridging feature to connect the networks. We discuss bridging later in this chapter.
You have two different network types, such as powerline and Ethernet, and you want the computers on both LAN types to be able to communicate. You could use a hardware bridge or access point, but you could also install both types of adapters in one of your computers and use the Bridging feature to connect the networks. We discuss bridging later in this chapter.
We suggest you use the following procedure to install multiple adapters:
1. Install, configure, and test the first adapter. (If you’re doing this to share an Internet connection, install and configure the one you’ll use for the Internet connection first. Be sure you can successfully browse the Internet before you proceed.)
2. Right-click the network icon at the right end of the taskbar and select Open Network and Sharing Center. Click Change Adapter Settings on the left side of the window. Select the icon for the network adapter—it will likely be named Ethernet or Local Area Connection—and choose Rename This Connection in the ribbon. (Or right-click the icon and select Rename.) Change the connection’s name to something that indicates what it’s used for, such as “Connection to Cable Modem” or “Office Ethernet Network.”
3. Write the name on a piece of tape or a sticky label and apply it to the back of your computer above the network adapter or on the edge plate of the network card.
4. Install the second adapter. Configure it and repeat steps 2 and 3 with the new connection icon. Rename this connection appropriately—for example, “LAN” or “Wireless Net”—and label the adapter socket.
If you follow these steps, you’ll be able to easily distinguish the two connections instead of needing to remember which connection icon is which.
Installing Network Wiring
When your network adapters are installed, the next step is to get your computers connected. Installing the cables can be the most difficult task of setting up a network if you have to run cable through walls. How you proceed depends on the type of networking adapters you have:
![]() If you’re using wireless adapters, of course, you don’t need to worry about wiring. Lucky you. You can just skip ahead to “Installing a Wireless Network,” later in this chapter.
If you’re using wireless adapters, of course, you don’t need to worry about wiring. Lucky you. You can just skip ahead to “Installing a Wireless Network,” later in this chapter.
![]() If you’re using a powerline networking adapter, follow the manufacturer’s installation instructions. If you’re using a powerline bridge, plug in the bridge to a wall socket and connect it to your computer or other networked device with a CAT-5 cable. Follow the manufacturer’s instructions for configuring the adapter’s security features. You should enable encryption if it’s available. Then skip ahead to the “Configuring a Peer-to-Peer Network” section, later in the chapter.
If you’re using a powerline networking adapter, follow the manufacturer’s installation instructions. If you’re using a powerline bridge, plug in the bridge to a wall socket and connect it to your computer or other networked device with a CAT-5 cable. Follow the manufacturer’s instructions for configuring the adapter’s security features. You should enable encryption if it’s available. Then skip ahead to the “Configuring a Peer-to-Peer Network” section, later in the chapter.
![]() If you’re using wired Ethernet adapters, you must decide how to route your wiring and what type of cables to use.
If you’re using wired Ethernet adapters, you must decide how to route your wiring and what type of cables to use.
The remainder of this section discusses Ethernet wiring.
Cabling for Ethernet Networks
If your computers are close together, you can purchase Ethernet cables to connect your computers to a switch or router. (They are often called patch cables, a term that originated in the telephone industry. In the old days, switchboard operators used flexible cables to connect, or “patch,” one phone circuit to another.) You can run these cables through the habitable area of your home or office by routing them behind furniture, around partitions, and so on. Just don’t put them where they’ll be crushed, walked on, tripped over, run over by desk chair wheels, or chewed by pets. Office supply and hardware stores sell special cable covers that you can use if you need to run a cable where it’s exposed to foot traffic (where it would be a tripping hazard) or to protect from a pet that likes to chew on things. These covers are also good for wires that need to run up walls or over doorways.
![]() Tip
Tip
As you install each network card and plug in the cables, you should see a green light turn on at the switch or router and at the network adapter. These lights indicate that the network wiring is correct.
You can do a web search for the phrase “Cable Management” to get some ideas of what kinds of products are available.
If the cables need to run through walls or stretch long distances, you should consider having them installed inside the walls with plug-in jacks, just like your telephone wiring. We discuss this topic later in this section.
General Cabling Tips
You can determine how much cable you need by measuring the distance between computers and your switch location(s). Remember to account for vertical distances, too, where cables run from the floor up to a desktop or go up and over a partition or wall.
![]() Caution
Caution
If you need to run cables through the ceiling space of an office building, you should check with your building management to see whether the ceiling is listed as a plenum or air-conditioning air return. You might be required by law to use certified plenum cable and follow all applicable electrical codes. Plenum cable is formulated not to emit toxic smoke in a fire.
Keep in mind the following points:
![]() We refer to CAT-5 here, but if you’re using 1000Mbps Ethernet, you must use CAT-5E or CAT-6 cable and connectors.
We refer to CAT-5 here, but if you’re using 1000Mbps Ethernet, you must use CAT-5E or CAT-6 cable and connectors.
![]() Existing household telephone wire probably won’t work. If the wires inside the cable jacket are red, green, black, and yellow: no way. The jacket must have CAT-5 (or higher) printed on it. It must have color-matched twisted pairs of wires; usually, each pair has one wire in a solid color and the other white with colored stripes. The colors are usually green, orange, blue, and brown.
Existing household telephone wire probably won’t work. If the wires inside the cable jacket are red, green, black, and yellow: no way. The jacket must have CAT-5 (or higher) printed on it. It must have color-matched twisted pairs of wires; usually, each pair has one wire in a solid color and the other white with colored stripes. The colors are usually green, orange, blue, and brown.
![]() You must use at least CAT-5-quality wiring and components throughout, and not just the cables. Any jacks, plugs, connectors, terminal blocks, patch cables, and so on also must be at least CAT-5 certified.
You must use at least CAT-5-quality wiring and components throughout, and not just the cables. Any jacks, plugs, connectors, terminal blocks, patch cables, and so on also must be at least CAT-5 certified.
![]() If you’re installing in-wall wiring, follow professional CAT-5 wiring practices throughout. Be sure not to untwist more than half an inch of any pair of wires when attaching cables to connectors. Don’t solder or splice the wires.
If you’re installing in-wall wiring, follow professional CAT-5 wiring practices throughout. Be sure not to untwist more than half an inch of any pair of wires when attaching cables to connectors. Don’t solder or splice the wires.
![]() When you’re installing cables, be gentle. Don’t pull, kink, or stretch them. Don’t bend them sharply around corners; you should allow at least a 1-inch radius for bends. To attach cables to a wall or baseboard, use only special cable staples or rigid cable clips that don’t squeeze the cable, as shown in Figure 18.4. Your local electronics store or hardware store can sell you the right kind of clips.
When you’re installing cables, be gentle. Don’t pull, kink, or stretch them. Don’t bend them sharply around corners; you should allow at least a 1-inch radius for bends. To attach cables to a wall or baseboard, use only special cable staples or rigid cable clips that don’t squeeze the cable, as shown in Figure 18.4. Your local electronics store or hardware store can sell you the right kind of clips.
Figure 18.4 Use rigid cable clips or staples that don’t squeeze the cable if you nail it to a wall or baseboard.
![]() Keep network cables away from AC power wiring and away from electrically noisy devices such as fluorescent lights, arc welders, diathermy machines, and the like. (I’ve never actually seen a diathermy machine, but I hear they’re trouble.)
Keep network cables away from AC power wiring and away from electrically noisy devices such as fluorescent lights, arc welders, diathermy machines, and the like. (I’ve never actually seen a diathermy machine, but I hear they’re trouble.)
![]() Note
Note
If you really want to get into the nuts and bolts, so to speak, of pulling your own cable, a good starting point is Frank Derfler and Les Freed’s Practical Network Cabling (Que, ISBN 078972247X).
Wiring with Patch Cables
If your computers are close together and you can simply run cables directly between your computers and switch, you’ve got it made. Buy CAT-5 (or better) cables of the appropriate length online or at your local computer store. Just plug (click) them in, and you’re finished. Figure 18.1 shows how to connect your computers to the switch.
![]() Note
Note
The modular plugs used in Ethernet networking are often called RJ-45 connectors. To pick a technical nit here, the connector used in networking is really called an 8P8C connector. The “true telephone RJ-45” connector is slightly different, and not compatible. If you’re buying RJ-45 connectors, just make sure that the package says that they’re for networking use.
If you have the desire and patience, you can build custom-length cables from crimp-on connectors and bulk cable stock. Making your own cables requires about $75 worth of tools, though, and more detailed instructions than we can give here. Making just a few cables probably doesn’t make buying the tools worthwhile. Factory-assembled cables are also more reliable than homemade ones because the connectors are attached by machine. They’re worth the extra few dollars.
For the ambitious or parsimonious reader, Figure 18.5 shows the correct way to order the wires in the connector.
Installing In-Wall Wiring
In-wall wiring is the most professional and permanent way to go. However, this job often involves climbing around in the attic or under a building, drilling through walls, or working in an office telephone closet. Hiring someone to get the job done might cost $30–$75 per computer or more, but you’ll get a professional job.
In-wall wiring is brought out to network-style modular jacks mounted to the baseboard of your wall. These RJ-45 jacks look similar to telephone modular jacks but are wider. You need patch cables to connect the jacks to your computers and switch, as shown in Figure 18.6.
![]() Tip
Tip
Search a printed or online directory of local businesses (such as yellowpages.com or maps.yahoo.com) for “Telephone Wiring,” and ask the contractors you call whether they have experience with network wiring.
Connecting Just Two Computers
If you’re making a network of just two computers (say, to copy files from an old to a new computer), you might be able to take a shortcut and eliminate the need for a network switch or additional special hardware. If you want to add on to your network later, you can always add the extra gear then.
If you are connecting two computers, simply run a special cable called an Ethernet crossover cable from one computer’s network adapter to the other, and you’re finished. This special type of cable reverses the send and receive signals between the two ends and eliminates the need for a switch. You can purchase an Ethernet crossover cable from a computer store or network supply shop, or you can make one, as shown in Figure 18.7.
Figure 18.7 Wiring for a UTP crossover cable. The cable reverses the send and receive wires so that two network cards can be directly connected without a switch. Note that the green pair and orange pair are reversed across the cable.
Be sure that your crossover cable is labeled as such. It won’t work to connect a computer to a switch, and you’ll go nuts wondering what’s wrong if you try. Factory-made models usually have yellow ends. (When I make them myself, I draw three rings around each end of the cable with a permanent-ink marker.)
If you have a cable that you’re not sure about, look at the colors on the little wires inside the clear plastic connectors at the two ends. Considering just the colors on the wires, without regard to whether the colors are solid or striped:
![]() If you can see that each color is in the exact same position at both ends of the cable, in the arrangement AABCCBDD, you have a standard Ethernet patch cable.
If you can see that each color is in the exact same position at both ends of the cable, in the arrangement AABCCBDD, you have a standard Ethernet patch cable.
![]() If a pair of wires that is together at one end of the cable is split apart at the other end (that is, if one end has the pattern AABCCBDD and the other has BBACCADD), you have an Ethernet crossover cable.
If a pair of wires that is together at one end of the cable is split apart at the other end (that is, if one end has the pattern AABCCBDD and the other has BBACCADD), you have an Ethernet crossover cable.
![]() If the pairs of wire are arranged symmetrically around the center of the connector (that is, if the pattern is ABCDDCBA), the cable is a telephone cable and not an Ethernet cable. You can’t use this type of cable for networking.
If the pairs of wire are arranged symmetrically around the center of the connector (that is, if the pattern is ABCDDCBA), the cable is a telephone cable and not an Ethernet cable. You can’t use this type of cable for networking.
Connecting Multiple Switches
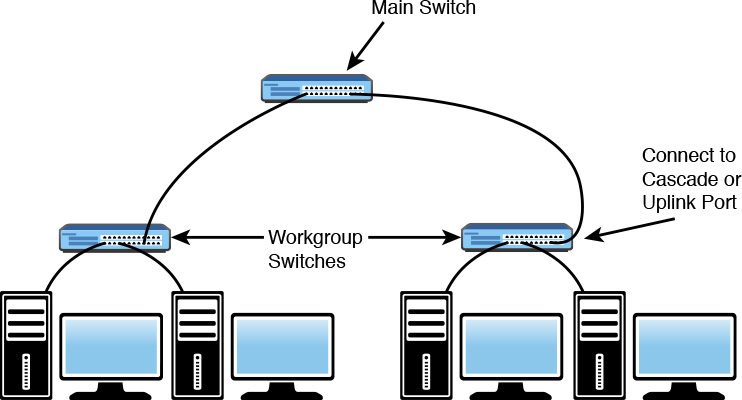
You might want to use more than one switch to reduce the number of long network cables you need if you have groups of computers in two or more locations. For example, you can connect the computers on each “end” of the network to the nearest switch and then connect the switch to a main switch. Figure 18.8 shows a typical arrangement using this technique.
Figure 18.8 You can connect groups of computers with multiple switches to reduce the number of long cables needed. Use the cascade port on the remote switches to connect to the central switch.
![]() Note
Note
A switch’s uplink or cascade port is a connector designed to be connected to another switch. Some switches have a separate connector for this purpose, whereas others make one of their regular ports do double-duty by providing a pushbutton that turns the last switch port into a cascade port. Still others handle this automatically. Refer to your switch’s manual to see what to do with your particular hardware.
If you need to add a computer to your LAN and your switch has no unused connectors, you don’t need to replace the switch; you can just add a switch. To add a computer to a fully loaded switch, unplug one cable from the original switch to free up a port. Connect this cable and your new computer to the new switch. Finally, connect the new switch’s cascade port to the now-free port on the original switch, as shown in Figure 18.9.
Figure 18.9 You can expand your network by cascading switches. The instructions included with your switch describe how to connect two switches using a patch cable. Some switches have a dedicated uplink port, some have a pushbutton that turns a regular port into an uplink port, and some figure it out automatically.
Installing a Wireless Network
If you are using a wireless router, you must configure wireless security and networking options after installing your network adapters. You must do this even if you are just using it for its wired Ethernet connections and don’t plan on using its wireless capability.
You really do have to worry about wireless network security. In my home, I can pick up signals from four separate wireless networks: mine, the house next door’s, and two others (I can’t tell whose they are). It’s not uncommon to find that you can receive signals from several neighbors. And people do actually drive around with laptops in their car, looking for free Internet access or looking to break in to your computers. To protect against both freeloaders and hackers, you can use one or two protection techniques: encryption, which scrambles data, and authentication, which certifies that a given computer should be allowed to connect to the network. You can use either encryption alone or both encryption and authentication.
Wireless Network Setup Choices
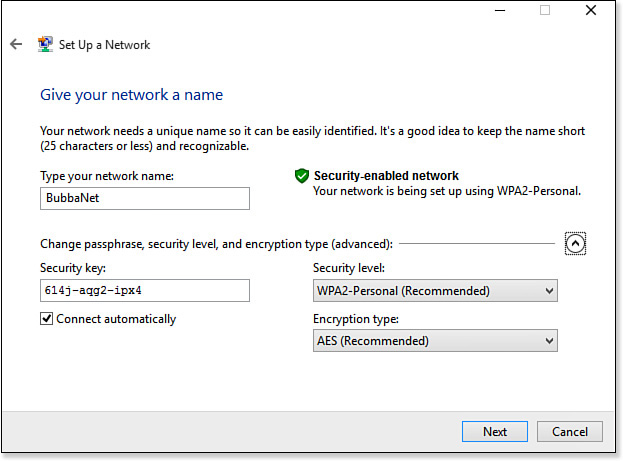
To be able to distinguish your network’s signal from others and to secure your network, you will be asked to make the following choices when you set up a wireless network:
![]() Caution
Caution
If you want to use file and printer sharing on your wireless network, you must use wireless security; otherwise, random people will be able to get at your computer.
If you want to set up an “open” wireless hot spot to share your Internet connection with friends, neighbors, or the world, that’s great, but you must not use file and printer sharing on the same network. See “Special Notes for Wireless Networking” in Chapter 19 for a safer option.
![]() An SSID (Service Set Identifier)—A short name that you give your network, up to 32 characters in length. This could be your last name, your company name, your pet’s name, or whatever makes sense to you. If you want to ensure that your network can never be shared with others via Microsoft’s Wi-Fi Sense feature, put the
An SSID (Service Set Identifier)—A short name that you give your network, up to 32 characters in length. This could be your last name, your company name, your pet’s name, or whatever makes sense to you. If you want to ensure that your network can never be shared with others via Microsoft’s Wi-Fi Sense feature, put the phrase _optout somewhere in the network name. For example, you might name the network lucynet_optout.
![]() To learn more about Wi-Fi Sense, see “Wi-Fi Sense,” p. 21, and “Sharing Wi-Fi Network Settings with Friends,” p. 397.
To learn more about Wi-Fi Sense, see “Wi-Fi Sense,” p. 21, and “Sharing Wi-Fi Network Settings with Friends,” p. 397.
![]() A security type—The authentication method that your network uses to determine whether a given computer should be allowed to connect, and for ensuring that you really are connecting to the router or access point you intend to use, rather than a malicious device impersonating it. For home and small office use, the choices are as follows, in order of increasing security:
A security type—The authentication method that your network uses to determine whether a given computer should be allowed to connect, and for ensuring that you really are connecting to the router or access point you intend to use, rather than a malicious device impersonating it. For home and small office use, the choices are as follows, in order of increasing security:
![]() No Authentication (open)—No authentication is performed; any computer can connect to the network.
No Authentication (open)—No authentication is performed; any computer can connect to the network.
![]() WPA-Personal—A method that uses a passphrase to validate each computer’s membership in the network. The passphrase also serves as an encryption key. It has been found to be insecure—a determined hacker can bypass it. Don’t use it unless your wireless router can’t use WPA2 and its software can’t be upgraded.
WPA-Personal—A method that uses a passphrase to validate each computer’s membership in the network. The passphrase also serves as an encryption key. It has been found to be insecure—a determined hacker can bypass it. Don’t use it unless your wireless router can’t use WPA2 and its software can’t be upgraded.
![]() WPA2-Personal—An improved version of WPA-Personal. This is the best choice for home and small office networks.
WPA2-Personal—An improved version of WPA-Personal. This is the best choice for home and small office networks.
On corporate networks, other security types are sometimes used: 802.1X, WPA-Enterprise, and WPA2-Enterprise. These systems use a network server, smart card, or software certificate to validate network membership.
![]() An encryption type—The encryption method used to secure network data against eavesdropping. The options available depend on the security (authentication) type selected. The choices, in increasing order of security, are as follows:
An encryption type—The encryption method used to secure network data against eavesdropping. The options available depend on the security (authentication) type selected. The choices, in increasing order of security, are as follows:
![]() None—No data encryption is performed. This option is available only when the security type is set to No Authentication.
None—No data encryption is performed. This option is available only when the security type is set to No Authentication.
![]() WEP—Data is encrypted using the WEP protocol, using a 40-, 128-, or 256-bit key. WEP encryption can very easily be broken by a hacker using easily available software. Don’t use it unless you have no choice (for example, if your network must support an old TiVo unit that can’t use a better security option).
WEP—Data is encrypted using the WEP protocol, using a 40-, 128-, or 256-bit key. WEP encryption can very easily be broken by a hacker using easily available software. Don’t use it unless you have no choice (for example, if your network must support an old TiVo unit that can’t use a better security option).
![]() TKIP—An encryption method that can be used with any of the WPA security types. It, too, can be broken by hackers. A better choice is AES.
TKIP—An encryption method that can be used with any of the WPA security types. It, too, can be broken by hackers. A better choice is AES.
![]() AES—An improved encryption method that can be used with any of the WPA security types. AES is more secure and may offer faster network transmission. This is the best choice for home and small office networks.
AES—An improved encryption method that can be used with any of the WPA security types. AES is more secure and may offer faster network transmission. This is the best choice for home and small office networks.
Your router might offer an AEK/TKIP option; that is, it can let newer equipment use AEK while older equipment uses TKIP. Don’t select this option unless you really do have old equipment that can’t use AES. Making TKIP available under any circumstance opens the security hole. Choose just AES.
![]() An encryption key—The key used to encrypt and decrypt data sent over the network. The different encryption methods use keys of different lengths. Longer (more bits) is better.
An encryption key—The key used to encrypt and decrypt data sent over the network. The different encryption methods use keys of different lengths. Longer (more bits) is better.
![]() For WEP encryption, Windows 10 supports 40-bit and 128-bit security. A 128-bit WEP key must be exactly 26 hexadecimal digits—that is, the numerals 0 through 9 and the letters A through F. It could look something like this:
For WEP encryption, Windows 10 supports 40-bit and 128-bit security. A 128-bit WEP key must be exactly 26 hexadecimal digits—that is, the numerals 0 through 9 and the letters A through F. It could look something like this: 5e534e503d4e214d7b6758284c. You can Google “Random WEP Key Generator” if you want help coming up with one.
A 40-bit key consists of exactly 10 hexadecimal digits. Windows 10 will let you join an existing 40-bit WEP network but not create a new one.
Some routers and some earlier versions of Windows let you enter a WEP key as a text phrase, but the text method was not standardized and was pretty much guaranteed not to work across brands of wireless routers and access points, so it has been abandoned.
![]() For WPA or WPA encryption, enter a passphrase: a word or phrase using any eight or more letters or characters—the more the better, up to 63. The passphrase is case sensitive and can contain spaces but must not begin or end with a space. You might use two random words separated by punctuation symbols (for example, something like
For WPA or WPA encryption, enter a passphrase: a word or phrase using any eight or more letters or characters—the more the better, up to 63. The passphrase is case sensitive and can contain spaces but must not begin or end with a space. You might use two random words separated by punctuation symbols (for example, something like topiary#clownlike).
![]() The encryption key should be kept secret because, with it, someone can connect to your network, and from there get to your data and your shared files.
The encryption key should be kept secret because, with it, someone can connect to your network, and from there get to your data and your shared files.
Whatever method you use, you might want to write down the passphrase or key on a sticky note and put it on the underside of your wireless router.
![]() A channel number—The channel number selects the frequency used to transmit your network’s data. The channels used in North America are usually 1, 6, and 11. The other channels overlap these and can interfere with each other. For double-bandwidth Wireless-N, the choices are 3 and 11. The preferred channel numbers are different in other countries.
A channel number—The channel number selects the frequency used to transmit your network’s data. The channels used in North America are usually 1, 6, and 11. The other channels overlap these and can interfere with each other. For double-bandwidth Wireless-N, the choices are 3 and 11. The preferred channel numbers are different in other countries.
Some wireless routers select a channel automatically. If you must choose one, see the tips under “Getting Maximum Wireless Speed,” later in this chapter.
![]() Note
Note
Finally, one more bit of nomenclature: If you have a router or access point, you are setting up what is called an infrastructure network. Windows has a wizard to help you choose the correct settings. We go through this in the next section.
When you use a router or Wi-Fi access point, you have what is called an infrastructure network. Sending Wi-Fi data directly between two or more computers without a router or access point is called ad hoc wireless networking. The capability to easily use ad hoc networking was in Windows 7, but it was removed from Windows 10 and 8. We talk about a way to get around this in Chapter 36 under “Ad Hoc Networks and Meetings.” In this chapter, we focus on infrastructure networks because using a router makes it easier to network with wired-in computers and also to share an Internet connection.
Why are there so many different security methods? Because thieves, like rust, never sleep, and it seems that as soon as a new, safer method is standardized, someone figures out a way to break it. WEP stands for Wired-Equivalent Privacy, but that turned out to be overly optimistic: A determined person can break WEP security in as little as a minute. WPA (which stands for Wi-Fi Protected Access) uses an improved encrypting scheme and can deter most attacks, but it, too, turns out to be crackable. WPA2 is a further improvement upon that, and it’s the best option we have at present. It should deter even the most determined hacker (although I suspect that it wouldn’t keep the National Security Agency scratching its collective head for too long, if you know what I mean).
![]() Note
Note
Windows 10, 8.1, 8, 7, Vista, and XP with Service Pack 3 all have built-in support for WPA2. If your router doesn’t support WPA2 or WPA, you might be able to install updated firmware to get it. If that’s not possible, a new wireless router shouldn’t set you back more than $20 to $90. Just sayin’.
Which encryption method should you use to set up your network? On a home or small office network, you’re limited by the least capable of the devices on your network—your weakest link. So, use the strongest encryption method and the longest key that is supported by all of the devices and computers on your network. This means that if you have even one computer that doesn’t support WPA, you must use WEP, and if you have even one computer that doesn’t support 256-bit keys, you must use a 128-bit key. If you have a router, access point, or network adapter that doesn’t support WPA, it’s worth checking to see whether you can update its internal software (firmware) or drivers to support this stronger encryption method.
Setting Up a New Wireless Network
If you’re setting up a new wireless network using a wireless router or access point, the hardest part of the job is correctly setting up security and Internet access settings in the router itself. There are three ways to configure a new router:
![]() You can use a setup program provided by the router’s manufacturer on a CD or DVD. This is usually the quickest and easiest method because the setup program knows exactly how to configure your router. Using high-speed Internet service, the setup program also might be able to set up the router to connect to your Internet service at the same time. (The next two options don’t do that.)
You can use a setup program provided by the router’s manufacturer on a CD or DVD. This is usually the quickest and easiest method because the setup program knows exactly how to configure your router. Using high-speed Internet service, the setup program also might be able to set up the router to connect to your Internet service at the same time. (The next two options don’t do that.)
![]() If your router supports Wi-Fi Protected Setup (WPS), you can use the Set Up a Network Wizard provided with Windows 10. If your router has an eight-digit numeric PIN code printed on the bottom, or if it has a pushbutton labeled WPS, you can use this wizard.
If your router supports Wi-Fi Protected Setup (WPS), you can use the Set Up a Network Wizard provided with Windows 10. If your router has an eight-digit numeric PIN code printed on the bottom, or if it has a pushbutton labeled WPS, you can use this wizard.
![]() You can set it up manually, by connecting to the router using a web browser.
You can set it up manually, by connecting to the router using a web browser.
![]() Tip
Tip
Before you get started, you might want to check the router manufacturer’s website to see whether a firmware update is available. (Firmware is the software built in to the device.) Firmware updates are usually issued when serious bugs have been found and fixed, so it’s definitely worth checking. Update the firmware following the manufacturer’s instructions before you start using the network because the update process sometimes blows out any settings you’ve made in the router, and you’ll have to start over as if it were new.
We give general instructions for these three setup methods in the following sections. The manufacturer’s instructions will be more detailed.
Whichever method you use, as mentioned in the previous section, you need to select up to five things to set up a wireless network: an SSID (name), security type, encryption type, encryption key, and possibly a channel number. A setup program or the Set Up a Network Wizard in Windows might help you make these selections automatically.
Using the Manufacturer’s Setup Program
The easiest way to set up a wireless router is using a program provided by the manufacturer. Connect one of your computers to the wireless router using an Ethernet cable, and then run the program from the manufacturer’s CD or DVD.
The setup program will typically prompt you for the settings required by the Internet access part of the router, which it uses to connect to your Internet service provider. It will also suggest default settings for the Wi-Fi side of the router, which you may change. As mentioned previously, select WPA2/AES security unless your router or one or more of your computers doesn’t support it.
You should write down the final settings, especially the security key. The setup program will then install the settings in the router. When your computers detect the new wireless network, you can connect to it and type in the security key.
Using the Set Up a Network Wizard
If your router supports the Wi-Fi Protected Setup (WPS) automatic configuration scheme, Windows 10 can set up the router for you automatically. You’ll need the router’s eight-digit PIN to use this method. The PIN might be printed on a label on the bottom of the router, or you might be able to find out what the PIN is by connecting to the router using a web browser. We tell how to do this shortly. Also, this method works only on a router that has all of its factory-default settings and hasn’t yet been configured. (If you have a used WPS-capable router, you might be able to use its setup web page to restore its factory-default settings.)
To use the Set Up a Network Wizard, follow these steps:
1. Connect your computer to one of the LAN ports on your wireless router using an Ethernet cable, and then power up the router. Wait 60 seconds or so before proceeding. If Windows asks, “Do you want to allow your PC to be discoverable by PCs and other devices on this network?” select Yes. This tells Windows that you are on a trusted, private network.
2. Right-click or touch and hold the Network icon in the taskbar, and then select Open Network and Sharing Center.
Notice that a network name is listed at the top of the window, as shown in Figure 18.10. (In the figure, the name is Network, although if you have previously attached to the same router using a Wi-Fi connection, Windows might display the Wi-Fi network’s name.) If under that it says “Private Network,” proceed to step 3. If it says “Public Network,” click or touch the Network icon in the taskbar, click or touch the name of the network to which you’re connected, and turn on Find Devices and Content. Then go back to the Network and Sharing Center.
Figure 18.10 To use the wizard to set up a wireless router, the network location must say “Private Network.”
3. Under Change Your Networking Settings, select Set Up a New Connection or Network. Highlight Set Up a New Network and click Next.
4. Wait for your wireless router to appear in the dialog box. When it does, select it and click Next.
If it doesn’t appear within 90 seconds, it might not be WPS capable, or it might already have been configured. If so, skip ahead to the next section, “Configuring Manually.”
5. Enter the PIN code printed on your router and click Next. If the PIN is not printed, see whether you can get it out of the router. Follow steps 2 through 5 in the section titled “Configuring Manually” to get into the router. See whether any of its setup screens display the WPS PIN. (On one router I tested, I found this under Wireless, Wi-Fi Protected Setup.)
6. Click the arrow next to Change Passphrase, Security Level and Encryption Type. Adjust the network name if you like, as shown in Figure 18.11. You may also change the passphrase if you want.
Figure 18.11 The Set Up a Network Wizard lets you change the default network name and security settings.
If not all of your computers support WPA2 security, you can downgrade the security level to WPA or WEP, but we strongly recommend against this. (See the discussion earlier in this chapter under “Wireless Network Setup Choices.”)
When the settings are made, click Next.
7. The wizard will configure the router and eventually display the security key. Write this down and keep a copy of it in a safe place. (If your location is secure, you can write in on a sticky note and attach it to the router itself, being sure not to block any ventilation holes.)
We suggest that you also click Print These Network Settings. If you don’t have a printer set up, select Print as a PDF and save the resulting file in your Documents library.
After you’ve followed these steps, your computers can all attach to the wireless network using the network key that you or the wizard selected.
![]() If you need to set up Internet service as well, see “Setting Up Internet Service,” p. 397.
If you need to set up Internet service as well, see “Setting Up Internet Service,” p. 397.
Configuring Manually
If you must configure your router manually, your best bet is to follow the manufacturer’s instructions. We can’t give you specific instructions here, but we can give a general outline of the process:
1. Connect your computer to one of the LAN ports on your wireless router using an Ethernet cable, and then power up the router. Wait 60 seconds or so before proceeding. If you are prompted to turn sharing on or off, turn on sharing.
2. Press Windows Logo+X and select Command Prompt or Windows PowerShell from the pop-up menu, whichever appears. Type the command ipconfig and press Enter.
3. Look for the heading that reads something like “Ethernet Adapter Ethernet,” and under that, look for the Default Gateway setting. It will look like 192.168.0.1 or 192.168.1.1, or something similar.
4. Open Internet Explorer, and in the Address bar, type http:// followed by the default gateway numbers (for example, http://192.168.0.1) and press Enter.
5. Log on to the router using its administrative username and password. In many cases, you can use admin for both the username and password, but this varies by manufacturer. You’ll have to read the instruction manual or search the Web to find the default password for your router.
You might want to change the default password as your first step. If you do change it, be sure to write down the new password and store it in a secure place.
6. Use the router’s web page menus to locate the Wireless Configuration page. Enter a network name (SSID), select a security type, and enter a key.
7. Use the appropriate “save settings” button or menu choice, wait 30 seconds, and try to have one of your other computers connect to the router using a wireless adapter, following the instructions under “Joining a Wireless Network” on p. 845.
When other computers can connect successfully, if the computer you used for setup has a wireless adapter, you can disconnect the Ethernet cable. Ethernet connections are faster and more reliable than wireless, though, so use wired connections whenever it’s convenient to do so.
When your computer can connect to the wireless router, you can have the router establish an Internet connection for you.
Setting Up Internet Service
When your wireless network is working and your computers can connect to the wireless router, you will probably want to have the router share a high-speed Internet connection.
If you used the manufacturer’s setup program to configure your router, it might have set this up for you already. If you have to set up the Internet side of your router manually, try to follow the manufacturer’s instructions. We can give you only general instructions here.
Routers are usually factory-set to use automatic address assignment (this is called DHCP configuration), so in many cases you can simply plug in the router’s WAN port to your cable or DSL modem, and it will immediately work. It depends on your Internet service, though, and in many instances you must do some setup.
To set up shared Internet service, go to the router’s setup web pages by following steps 2 through 5 in the preceding section, “Configuring Manually.” Locate the router’s wide area network (WAN) or Internet setup web pages. Many routers have a menu option you can select to run an Internet setup wizard; otherwise, you’ll have to set up the connection manually.
In general terms, there are three ways to connect:
![]() If your wireless router’s WAN (Internet) port is connected to a network that already has a full-time Internet connection, choose the router’s “direct connection” option.
If your wireless router’s WAN (Internet) port is connected to a network that already has a full-time Internet connection, choose the router’s “direct connection” option.
![]() If you use cable Internet service, most likely you’ll select the DHCP option. You might have to enter a specific hostname supplied by your cable company. Other cable ISPs key off your network adapter’s MAC address, so you might have to call your ISP to inform it of the router’s MAC address. This is usually printed on the bottom of the router.
If you use cable Internet service, most likely you’ll select the DHCP option. You might have to enter a specific hostname supplied by your cable company. Other cable ISPs key off your network adapter’s MAC address, so you might have to call your ISP to inform it of the router’s MAC address. This is usually printed on the bottom of the router.
![]() If you use DSL service, most likely you’ll select the PPPoE option. You’ll have to enter a username and password.
If you use DSL service, most likely you’ll select the PPPoE option. You’ll have to enter a username and password.
Your ISP should help you get the Internet connection working, or at least it should provide you with the information you need to get the connection working.
See Chapter 19 for more detailed instructions on connecting your LAN to the Internet.
Sharing Wi-Fi Network Settings with Friends
Windows 10 has a feature called Wi-Fi Sense that lets you and others connect to Wi-Fi networks without knowing the networks’ passwords. The feature was conceived as a way to let phone and tablet users save money on cellular data transfer fees by automatically using free Wi-Fi service whenever possible.
Microsoft learns about free, unsecured hotspots by monitoring the use of networks to which you and other Windows users successfully connect (which is creepy, but also helpful). When Microsoft sees that several users have made successful high-speed connections to a given network, it disseminates information about that network to other Windows users. If you set up an unsecured Wi-Fi network, Wi-Fi Sense might well assist the general public in using it. (This is, of course, what you’re inviting by setting up an unsecured network.)
If you have set up a secured (password-protected) Wi-Fi network, you can also let Wi-Fi Sense let your friends use your network, giving them Internet access without providing them with your Wi-Fi security key or giving them access to computers on your network. Connections made through Wi-Fi Sense get access only to the Internet, not to the local LAN. Your friends will never see your Wi-Fi password. It’s transmitted in encrypted form from Microsoft to Windows and can’t be displayed.
To share your secured network this way, you must be using a Microsoft (online) account, and both you and your friends must be using Windows 10 (or Windows Phone 8) and must be in each other’s contact lists in your Microsoft or Skype accounts, or you must be friends on Facebook. To enable sharing, follow these steps:
1. Click or touch Start, Settings, Network & Internet, Wi-Fi, Manage Wi-Fi Settings.
2. Under For Networks I Select, choose the contacts lists with which you want to share. You can’t select individual people in these lists. You can only choose to share with all contacts in the list or none.
3. Under Manage Known Networks, click or touch the name of the network you want to make available, and select Share. Enter the network’s key (password), and then select Share.
![]() Note
Note
Whether you set up an open or secured network, you can prevent Microsoft from adding it to the Wi-Fi Sense database by adding the phrase _optout to the network’s name, as discussed earlier in the chapter. This will prevent others who know your network’s password from sharing it with their friends using Wi-Fi Sense.
You can stop sharing the network by following the same steps, except select Stop Sharing. Either way, when you share or stop sharing a network, it can take several days for the information to work its way out to your friends’ devices.
By the way, if you know someone else’s Wi-Fi password, it would be bad form to share their network via Wi-Fi Sense, unless you have their permission.
Getting Maximum Wireless Speed
802.11n wireless networking supports speeds of up to 150Mbps, which is a huge improvement over older 801.11g and 802.11b equipment. However, you won’t get the maximum possible speed if any of these conditions exist:
![]() There are other nearby networks using radio channels that overlap your network.
There are other nearby networks using radio channels that overlap your network.
![]() You have older Wireless-G or -B equipment on the same network as -N (perhaps an old laptop or TiVo). Wi-Fi equipment can’t run at full speed when it is also communicating with equipment running older Wi-Fi protocols.
You have older Wireless-G or -B equipment on the same network as -N (perhaps an old laptop or TiVo). Wi-Fi equipment can’t run at full speed when it is also communicating with equipment running older Wi-Fi protocols.
![]() You are using the insecure WEP or WPA security protocol (perhaps because you have older equipment that doesn’t support WPA2) or are using TKIP encryption. The 802.11n specification sets a maximum speed of 54Mbps if WEP, WPA, or TKIP are in use. Higher speeds are permitted by the specification only with WPA2/AES.
You are using the insecure WEP or WPA security protocol (perhaps because you have older equipment that doesn’t support WPA2) or are using TKIP encryption. The 802.11n specification sets a maximum speed of 54Mbps if WEP, WPA, or TKIP are in use. Higher speeds are permitted by the specification only with WPA2/AES.
![]() Your router is not using the legal maximum transmitting power.
Your router is not using the legal maximum transmitting power.
The following sections tell you how to fix these conditions.
Eliminate Overlapping Channels
The 2.4GHz band used by wireless gear supports 11 to 14 radio frequency channels so that you don’t have to share radio bandwidth with your neighbors. The surprising fact is that many of these channels overlap each other to a large extent; a given channel overlaps about two and a half channels on either side. If your neighbor’s wireless router is using channel 1 and you set your router to use channel 2, there can still be considerable interference. Plus, both networks will be slowed down if you’re both using them at the same time.
To avoid this situation, press Windows Logo+X and select Command Prompt or Windows PowerShell from the pop-up menu, whichever appears. Type netsh wlan show networks mode=bssid and press Enter. This lists each neighboring network, its signal strength (as a percentage of something—what, I don’t know), and its channel. Examine the list, ignoring your own network. Select a channel for your network that doesn’t conflict with at least the strongest of your neighbors’ networks.
In the United States, Canada, and Mexico, if you are using Wireless-G, or a standard 20MHz bandwidth Wireless-N router, try to select from channels 1, 6, and 11 only. Try to pick a channel that’s five channels away from any strong neighboring signals. Also, some cordless phones use the same 2.4GHz radio band as Wi-Fi. You can help prevent this interference by using 900MHz cordless phones.
If you are using a double-rate 40MHz bandwidth 2.4GHz Wireless-N router, use either channel 3 or 11. In Europe and elsewhere, find out what channels are recommended in your region.
Set your router to use this channel. Your other wireless devices will automatically catch on within minutes.
You could also repeat this exercise in the 5GHz band, if your router supports it. Many more channels are available, there’s much less overlap between them, and not many cordless phones use the 5GHz band. Use a channel several numbers away from any neighboring 5GHz networks.
Tune Up Wireless Security
If you want to get the best Wireless-N performance, use the WPA2/AES security setting on your router. Doing so just requires a setting change on the router. The connecting devices will work it out on their own.
If you have some equipment that doesn’t support WPA2, you’ll get maximum performance if you set up to use a separate, lower-speed network, as described in the next section.
Separate Your Wireless-AC, -N, -G, and -B Networks
Wireless-AC, -N, -G, and -B equipment can all interoperate; however, having lower-speed equipment can slow down the performance of higher-speed equipment when both are transmitting at the same time and even for several seconds afterward. If you have mixed equipment, you can get peak speed on your network in two ways:
![]() Use a two-radio (simultaneous dual-band) router. Set up different network names (SSIDs) for the two frequency bands. Set any Wireless-N equipment to use the 5GHz network and all of your -B and -G equipment to use the 2.4GHz network. This requires a two-radio router, however, and 5GHz signals don’t have the same reach as 2.4GHz. (Wireless-AC always uses 5GHz.)
Use a two-radio (simultaneous dual-band) router. Set up different network names (SSIDs) for the two frequency bands. Set any Wireless-N equipment to use the 5GHz network and all of your -B and -G equipment to use the 2.4GHz network. This requires a two-radio router, however, and 5GHz signals don’t have the same reach as 2.4GHz. (Wireless-AC always uses 5GHz.)
![]() Alternatively, use two routers: one for your high-speed devices and an inexpensive second one for your older gear.
Alternatively, use two routers: one for your high-speed devices and an inexpensive second one for your older gear.
To set up two routers, configure the first Wireless-AC or -N router as your primary wireless network. Choose a clear channel, as described previously, and give it a network name (SSID) like “MyWirelessN.” Set it up with WPA2/AES security.
Configure the other router as an access point. This turns off its routing features and turns it into a simple “repeater,” so that devices on the separate wireless networks can communicate directly. (That is, so that you can use Windows file and printer sharing between computers on the different networks.) Most routers can be set up this way; check the instructions. Select a channel that doesn’t conflict with your other router. (For example, in the United States, if your main router is set for channel 1, set this one to channel 6 or 13.) Give it a distinct SSID name, like “MyWirelessG.” Set up WPA2/AES security if the router and your -G and -B devices support it. Position it at least 6 feet away from the other router. Now, just plug in this device’s WAN port to one of your first router’s LAN ports. Have your slower devices connect to this alternative network name. You won’t be able to share files or printers between the two networks.
Bump Up the Power?
Around the world, countries have differing regulations for the allowed frequencies and maximum power that unlicensed transmitters such as wireless routers can use. To play it safe, most routers are shipped with settings that adhere to the lowest common denominator, which means that your router might be operating at a lower power than is legally permissible in your area. It can be worth checking your router’s advanced wireless settings to see if there is a setting for the regulatory domain (operating region) or the transmitter power.
The rules for the maximum-allowed power are esoteric, and the allowed wattage depends on the frequency band and the efficiency (gain) of the antenna used. For most antennas, in North America the maximum 2.4GHz power is 100mW. If your router came configured with a power setting lower than 60mW, you might bump up the power to 60mW to see if this improves your data speed. It might not. (And for many routers, much more than 60mW could shorten the life of the router and actually degrade the signal.) If increasing the power doesn’t improve your data speed, put it back to the original setting.
Configuring a Peer-to-Peer Network
When you’re sure that the wired or wireless physical connection between your computers is set up correctly, you’re ready to configure Windows 10. With today’s Plug-and-Play network adapters, and with all the needed software built in to Windows, this configuration is a snap.
If your computer is part of a Windows Server domain network, which is often the case in a corporate setting, skip ahead to “Joining a Windows Domain Network.”
Configuring the TCP/IP Protocol
After your network adapters are all installed—and, if you’re using a wired network, cabled together—you must ensure that each computer is assigned an IP address. This is a number that uniquely identifies each computer on the network. These numbers are assigned in one of the following ways:
![]() If you have a router, or if one of your computers shares its Internet connection using Windows Internet Connection Sharing, or if you are on a corporate LAN running Windows Server, each computer will be assigned an IP address automatically. They’re doled out by the Dynamic Host Configuration Protocol (DHCP) service that runs on the router or in the sharing computer. This is why we recommend using a router even if you aren’t setting up a shared Internet connection.
If you have a router, or if one of your computers shares its Internet connection using Windows Internet Connection Sharing, or if you are on a corporate LAN running Windows Server, each computer will be assigned an IP address automatically. They’re doled out by the Dynamic Host Configuration Protocol (DHCP) service that runs on the router or in the sharing computer. This is why we recommend using a router even if you aren’t setting up a shared Internet connection.
By default, Windows sets up new network adapters to receive an address this way. If your network fits into this category, you don’t have to change any settings, and you can just skip ahead to the section “If You Have a Shared Internet Connection.”
![]() Each computer can be given an address manually, which is called a static address as opposed to a dynamic (automatic) one. If you are not going to use a router or a shared Internet connection, you should set up static addressing. We tell you how shortly.
Each computer can be given an address manually, which is called a static address as opposed to a dynamic (automatic) one. If you are not going to use a router or a shared Internet connection, you should set up static addressing. We tell you how shortly.
![]() If no static settings are made but no DHCP server exists on the network, Windows will automatically assign IP addresses anyway. Although the network will work, this is not an ideal situation and can slow down Windows. The setup steps shown in the following two sections let you avoid having IP addresses be assigned this way.
If no static settings are made but no DHCP server exists on the network, Windows will automatically assign IP addresses anyway. Although the network will work, this is not an ideal situation and can slow down Windows. The setup steps shown in the following two sections let you avoid having IP addresses be assigned this way.
If you’re setting up a new computer on an existing network, use whatever scheme the existing computers use; check their settings and follow suit with your new one. Otherwise, use either of the schemes described in the following two sections.
If You Have No Shared Internet Connection
If you’re setting up a new network from scratch, and you do not have a connection-sharing computer, router, or wireless access point, you should use static addressing.
For most home and small office networks, the following static address scheme should work fine:
![]() IP Address—192.168.1.11 for your first computer, 192.168.1.12 for your second computer, 192.168.1.13 for your third, and so on.
IP Address—192.168.1.11 for your first computer, 192.168.1.12 for your second computer, 192.168.1.13 for your third, and so on.
We strongly suggest that you keep a list of your computers and the addresses you assign to them.
![]() Subnet Mask—255.255.255.0
Subnet Mask—255.255.255.0
![]() Default Gateway—Leave blank
Default Gateway—Leave blank
![]() Preferred DNS Server—Leave blank
Preferred DNS Server—Leave blank
![]() Alternate DNS Server—Leave blank
Alternate DNS Server—Leave blank
Follow these steps on each computer to ensure that the network is set up correctly:
1. Right-click the Network icon that appears at the right end of the taskbar. Select Open Network and Sharing Center. (You also can get here from the Control Panel.) At the left side, select Change Adapter Settings. Right-click the Ethernet or Wireless Connection icon that corresponds to your LAN connection and select Properties.
2. In the Networking tab, scroll to the bottom of the list box and select Internet Protocol Version 4 (TCP/IPv4). Click Properties.
3. In the General tab, change the settings. Figure 18.12 shows an example, but you must use the address values appropriate for your computer and your network.
Figure 18.12 Make IP address settings within the Internet Protocol Version 4 (TCP/IPv4) Properties dialog box.
![]() Tip
Tip
If your computer will move back and forth between a network that uses automatic configuration and a network that uses static settings—say, between work and home—select Obtain an IP Address Automatically. A tab named Alternate Configuration appears. Select the Alternate Configuration tab and configure the static settings. Windows will use these static settings only when a DHCP server is not present.
If You Have a Shared Internet Connection
As mentioned previously, if you plan to share an Internet connection with all the computers on your network, you should read Chapter 19 first. Keep the following tips in mind:
![]() If you will use Windows Internet Connection Sharing, first set up the one computer that will be sharing its connection, as described in Chapter 19, and then set up networking in your other computers.
If you will use Windows Internet Connection Sharing, first set up the one computer that will be sharing its connection, as described in Chapter 19, and then set up networking in your other computers.
![]() All the computers, including the one sharing its Internet connection, should have their Ethernet connections set to Obtain an IP Address Automatically and Obtain DNS Server Address Automatically (refer to Figure 18.12).
All the computers, including the one sharing its Internet connection, should have their Ethernet connections set to Obtain an IP Address Automatically and Obtain DNS Server Address Automatically (refer to Figure 18.12).
![]() If you will be using a router, configure the router first, following the manufacturer’s instructions. Enable its DHCP feature. If you can, set the starting DHCP IP address to 100 so that numbers from 2 to 99 can be used for computers with static settings. Also, if your ISP has provided you with a static IP address for your router, be sure to enter your ISP’s DNS server addresses in the router’s setup screens so it can pass them to your computers.
If you will be using a router, configure the router first, following the manufacturer’s instructions. Enable its DHCP feature. If you can, set the starting DHCP IP address to 100 so that numbers from 2 to 99 can be used for computers with static settings. Also, if your ISP has provided you with a static IP address for your router, be sure to enter your ISP’s DNS server addresses in the router’s setup screens so it can pass them to your computers.
![]() Note
Note
If you add a shared Internet connection later, go to every one of your computers, bring up the TCP/IPv4 Properties dialog box shown in Figure 18.12 again, and select Obtain an IP Address Automatically and Obtain DNS Server Address Automatically. Otherwise, the shared connection will not work.
Now that your new network connection is set up, be sure to set the correct file sharing option, as described in the next section. This is a critical part of Windows networking security.
Enabling and Disabling Sharing
When you connect to a new network for the first time, Windows 10 automatically disables file and printer sharing through the connection, to protect you from hackers. It initially assumes that the network is public, thus untrusted, even dangerous. It will then prompt you, asking whether to enable sharing on the network. The choice you make determines the Windows Firewall settings that are applied and the networking features that will be available. If you need to, you can later change this setting manually.
The sharing setting is also called Network Location, and two choices are available:
![]() When you connect to a private network, you can choose to enable sharing. A private network is one where you trust the other computers on the network. (That is, you trust the people using the other computers.) When you elect to enable sharing, file and printer sharing is enabled, as is Network Discovery, which makes your computer visible to other users and makes their computers visible to you. It’s also possible to join a homegroup, which we discuss shortly.
When you connect to a private network, you can choose to enable sharing. A private network is one where you trust the other computers on the network. (That is, you trust the people using the other computers.) When you elect to enable sharing, file and printer sharing is enabled, as is Network Discovery, which makes your computer visible to other users and makes their computers visible to you. It’s also possible to join a homegroup, which we discuss shortly.
![]() When you connect to a public network, you must disable sharing. A public network is one where you don’t trust the other users or computers; for example, on any direct connection to a cable or DSL modem, on networks and Internet connections in hotels, Internet cafes, airports, clients’ offices, dorms, and anywhere else where you don’t want random people poking into your computer. File and printer sharing and Network Discovery are disabled on this network connection.
When you connect to a public network, you must disable sharing. A public network is one where you don’t trust the other users or computers; for example, on any direct connection to a cable or DSL modem, on networks and Internet connections in hotels, Internet cafes, airports, clients’ offices, dorms, and anywhere else where you don’t want random people poking into your computer. File and printer sharing and Network Discovery are disabled on this network connection.
![]() Caution
Caution
Any connection that leads directly to the Internet without your own firewall or router in between must have sharing turned off and be designated a public network, to protect your computer from the hackers and bad software “out there.” This holds no matter how you make the connection: plug-in Ethernet, wireless, dial-up, or a direct connection to a cable or DSL modem.
Here’s a good rule of thumb: If you don’t need to use file sharing and printer sharing in a given location, disable sharing on the connection.
As we mentioned, sharing is automatically disabled when you first connect to a new network. That is, when you move your computer from one network to another, Windows detects the change and turns off sharing.
Within a few moments, though, it should then display a settings panel that asks, “Do you want to allow your PC to be discoverable by PCs and other devices on this network?” Select Yes to indicate you are on a private network and want to enable sharing. Select No to indicate you are on a public network and want to disable sharing.
To change the sharing (Network Location) setting manually, follow these steps:
1. Touch or click the network icon on the taskbar and select Network Settings.
2. Touch or click the icon labeled with the name of your network connection.
3. To signify that your network is private, turn on Find Devices and Content. To signify that your network is public, turn off Find Devices and Content.
The Find Devices and Content switch sets the network location as Public or Private and enables or disables file sharing and automatic device discovery.
To control sharing and device discovery on a private network separately, in the taskbar’s search box, type the word sharing, select Network and Sharing Center, Change Advanced Sharing Settings, and then expand the Private section. You will see individual controls for file and printer sharing and for network discovery there.
Setting Your Computer Identification
After you’ve configured your network, the next step is to make sure that each of the computers on your network is a member of the same domain or workgroup.
If you are part of a Windows domain-type network, your system administrator will give you the information you need to set your computer identification.
If you are setting up your own network without Windows Server, press Windows Logo+X and select System on each of the computers on your network. Does each have a different full computer name and the same workgroup name? If so, you’re all set.
If not, click Change Settings, and in the Computer Name tab, click the Network ID button. You are asked to select the option that best describes your computer:
![]() This Computer Is Part of a Business Network; I Use It to Connect to Other Computers at Work.
This Computer Is Part of a Business Network; I Use It to Connect to Other Computers at Work.
![]() This Is a Home Computer; It’s Not Part of a Business Network.
This Is a Home Computer; It’s Not Part of a Business Network.
![]() Caution
Caution
You should be sure that every computer on your network uses the same workgroup name if you want them to be able to easily share files and printers.
Which one you choose makes a significant difference. If you choose the “Home Computer” option, click Next, then Finish, as directed. The wizard sets up your computer for peer-to-peer networking with the workgroup name WORKGROUP and then finishes.
If you are on a business network with Windows Server, the rest of the procedure is described under “Joining a Windows Domain Network” later in this chapter.
Configuring Windows Firewall
It is a good idea to check that Windows Firewall is set up correctly; otherwise, you could end up exposed to Internet hacking, or you could find that your network is so locked down that you can’t use file and printer sharing. Windows Firewall is discussed in more detail in Chapter 33.
If your Windows 10 computer is connected to a domain network, your network manager will set up a firewall “profile” that controls security when you are connected to the corporate network. You shouldn’t be able to change these settings. Your network manager will also probably configure another “default” profile to protect you when you are disconnected from the corporate network, such as when you are traveling or using your computer at home.
In this section, we assume that you are managing your own computer and that your network is not protected by a professionally installed firewall. As a home or small office user, go through this quick checklist of steps to confirm that your network will function safely:
1. In the Start menu, search for the word fire. In the search results, select Windows Firewall.
2. You should see that you are connected to a private network, and within the Private Networks box, you should see that Windows Firewall is on. If it’s not, and you haven’t installed an alternative Internet security program that has a replacement firewall, at the left, select Turn Windows Firewall On or Off. In both the Private and Public sections, be sure that Turn On Windows Firewall is selected and that Notify Me When Windows Firewall Blocks a New App is checked.
In general, Block All Incoming Connections doesn’t need to be checked. You can check it in the Public profile section to get the strongest security, but you might not be able to use some Internet services, such as FTP (file transfer), telephone, and voice/video chat.
These are the default settings, but it’s best to check them to be sure.
File and Printer Sharing Without a Router: Avoiding the Unidentified Network Problem
If you are setting up a small network of computers that connect with each other through an Ethernet switch but not a router, you’ll run in to a problem with the Windows Network Location feature. This is the mechanism that Windows uses to identify one network from another so that it can then label them as public or private. Windows uniquely identifies each network that your computer joins by the Media Access Control address (MAC address), a physical hardware identification number, of the network adapter at the network’s TCP/IP gateway address. On a computer without a router, Windows automatically assigns IP addresses; however, there is no gateway address and thus no MAC address to examine, so Windows cannot tell this network from any other network. It will call the network an unidentified network and will not let you enable file or printer sharing on it.
You can solve this problem in either of two ways:
![]() Use an inexpensive DSL/modem connection-sharing router instead of a switch, and just don’t connect its WAN port to a DSL or cable modem. You can get these used on eBay or Craigslist for just a few dollars.
Use an inexpensive DSL/modem connection-sharing router instead of a switch, and just don’t connect its WAN port to a DSL or cable modem. You can get these used on eBay or Craigslist for just a few dollars.
![]() Assign IP addresses to each of your computers manually, using addresses like 192.168.0.2, 192.168.0.3, and upward. (Skip 192.168.0.1 in case you eventually do add a router.) In each computer, when you assign an IP address using the dialog box shown in Figure 18.12, enter as the gateway address the IP address of one of the other computers on your network. This workaround is clunky, but it works. The other computer must be turned on for your computer to be able to identify the network and enable sharing. When you save the address settings, Windows will ask you whether you want your computer to be discoverable by PCs and other devices on your network. To enable sharing, select Yes.
Assign IP addresses to each of your computers manually, using addresses like 192.168.0.2, 192.168.0.3, and upward. (Skip 192.168.0.1 in case you eventually do add a router.) In each computer, when you assign an IP address using the dialog box shown in Figure 18.12, enter as the gateway address the IP address of one of the other computers on your network. This workaround is clunky, but it works. The other computer must be turned on for your computer to be able to identify the network and enable sharing. When you save the address settings, Windows will ask you whether you want your computer to be discoverable by PCs and other devices on your network. To enable sharing, select Yes.
Setting Up a Homegroup
Windows versions 7 and later include a networking feature called HomeGroup that can make sharing files, folders, printers, and music/video media very easy. A homegroup lets each user decide whether to share specific categories of documents, music, video, printers, and so on, or even specific folders and files. Every user on every computer in the homegroup can see the items, once shared, without worrying about passwords or usernames. It’s all just there, organized, and easy to get to.
![]() Note
Note
It’s HomeGroup here and homegroup almost everywhere else in this chapter because the genius lawyers at Microsoft want people to use the trademarked word HomeGroup when we talk about the product feature but use homegroup when we talk about a group of computers that use the feature. Got that?
HomeGroup networking works by setting up a password that is used to join each computer to the group. Any user on any of the member computers can see any of the group’s shared folders and printers.
Is a homegroup right for you? Consider these points to decide whether to use this feature:
![]() The HomeGroup feature works only with Windows 7 and later. (However, computers running Windows Vista, XP, Mac OS, Linux, and so on can still share with a homegroup, and use folders and printers shared by a homegroup, if you take the additional steps discussed under “Using Windows Vista and XP with a Homegroup,” in Chapter 20.)
The HomeGroup feature works only with Windows 7 and later. (However, computers running Windows Vista, XP, Mac OS, Linux, and so on can still share with a homegroup, and use folders and printers shared by a homegroup, if you take the additional steps discussed under “Using Windows Vista and XP with a Homegroup,” in Chapter 20.)
![]() Within a homegroup, you can’t decide individually which other users can see your shared stuff and which users can’t. Anybody who can use a computer that’s a member of the homegroup can use the content that you decide to share.
Within a homegroup, you can’t decide individually which other users can see your shared stuff and which users can’t. Anybody who can use a computer that’s a member of the homegroup can use the content that you decide to share.
What you can control is whether to share your stuff, and whether the other users can just view and use your stuff or modify, delete, and add to it.
![]() Note
Note
If you have a computer that is part of a domain network when you connect at work, you can still join it to your homegroup at home. You’ll be able to use folders and printers shared by other computers in the homegroup, but you won’t be able to share any of your computer’s folders with the group.
If you don’t need to control access on a person-by-person basis, a homegroup is definitely a convenient thing to set up. If a homegroup isn’t right for you, skip ahead to the next section, “Alternatives to Using a Homegroup.” Changing your mind later on is easy, so don’t worry too much about this issue.
To set up a new homegroup, log on to one of your Windows 10 computers and perform the following steps:
1. In the taskbar’s search box, type homegr. Then, in the search results, select Homegroup. Alternatively, click the network icon in the taskbar and select Network Settings, HomeGroup.
2. Click Create.
3. Select which types of your content you want to share with everyone else in the homegroup, as shown in Figure 18.13. For each category (Pictures, Documents, Music, and/or Videos), select Shared to let other users see your files. For Printers and Devices, select Shared so that other users can use your computer’s printer. (You can easily change these selections later, as discussed in Chapter 21, “Using a Windows Network.”)
Figure 18.13 Select the types of files you want to share with everyone else in the homegroup. This selection applies only to your own files; other users get to choose for themselves what they want to share.
For any of these categories, you can select Not Shared so that other users can’t see your files or use your devices.
4. Scroll down to the bottom of the list of settings, if necessary, to view the Password listed in the Membership section. Jot this down. You’ll need it to join your other Windows 7, 8, 8.1, and 10 computers to the homegroup. Upper- and lowercase matter, by the way.
If you want to use a different HomeGroup password than the one Windows chose, you can, and now is the time to change it. In the taskbar’s search box, type homegr. In the search results, select Change HomeGroup Password. Then click Change the Password and follow the prompts.
If you are signed in to Windows with a Microsoft (online) account when you set up your homegroup, and then use that same account to sign in to another computer on your network, the HomeGroup password will be automatically filled in for you when you start to enroll this new computer into the group. HomeGroup passwords are one of the things that Windows syncs between the computers you use. (It’s an odd thing for Microsoft to have done, because HomeGroup passwords are a “per-computer” rather than a “per-user” attribute.)
5. You or another computer owner can now go to another Windows 10, 8.1, or 8 computer on your network, log on, and repeat this process. This time, instead of “Create,” you’ll be able to join the existing homegroup.
![]() Tip
Tip
If you forget the password, in the taskbar’s search box, type homegr, select HomeGroup, and then select View or Print the Homegroup Password.
On a Windows 7 computer, go to the Control Panel. Select Homegroup and Sharing Options and then Join Now.
Repeat step 5 with any other Windows 7 through 10 computers that you want to join to the homegroup.
Users on each computer will have to log on and decide which of their materials they want to share with the homegroup. Until they do, their names won’t appear in the HomeGroup listing in File Explorer. We talk about this in the section “Sharing with a Homegroup” in Chapter 21.
![]() Note
Note
If you have computers running Windows XP, Vista, Mac OS, Linux, or other OSs, read Chapter 20 to see how to make it easier to share files and printers with these other OSs.
Alternatives to Using a Homegroup
HomeGroup security gives anyone in the group access to any shared folder or printer. If you need to restrict access to shared folders and printers on a user-by-user basis, or if you have computers that don’t run Windows 7 and later, you might instead want to set up the traditional Windows file sharing scheme. There are two ways you can configure traditional sharing:
![]() If you have OSs other than Windows 7 and later on your network and you don’t need per-user security, you can turn off Password Protected Sharing. To do this, right-click the network icon at the right end of the taskbar and select Open Network and Sharing Center. At the left, select Change Advanced Sharing Settings. Scroll down to All Networks and click the down arrow to open the list. Scroll down more and select Turn Off Password Protected Sharing.
If you have OSs other than Windows 7 and later on your network and you don’t need per-user security, you can turn off Password Protected Sharing. To do this, right-click the network icon at the right end of the taskbar and select Open Network and Sharing Center. At the left, select Change Advanced Sharing Settings. Scroll down to All Networks and click the down arrow to open the list. Scroll down more and select Turn Off Password Protected Sharing.
This makes any shared folder or printer available to anybody who can connect to your network, with no passwords required at all.
If you have computers running Windows XP, Vista, Mac OS, Linux, or other OSs, read Chapter 20 for more information on sharing with these OSs.
![]() If you need to control in detail which users can use which shared files and folders, leave Password Protected Sharing turned on (which is the same as disabling Simple File Sharing on Windows XP). You will have to set up the same user accounts with the same passwords on each of your computers so that people can access shared folders and printers.
If you need to control in detail which users can use which shared files and folders, leave Password Protected Sharing turned on (which is the same as disabling Simple File Sharing on Windows XP). You will have to set up the same user accounts with the same passwords on each of your computers so that people can access shared folders and printers.
![]() For more information on Password Protected Sharing, including ways it works differently on Windows 8 and 10 than previous versions of Windows, see “Configuring Passwords and File Sharing,” p. 784.
For more information on Password Protected Sharing, including ways it works differently on Windows 8 and 10 than previous versions of Windows, see “Configuring Passwords and File Sharing,” p. 784.
Wrapping Up
This step completes the procedure for setting up Windows networking on one Windows 10 computer. After you have configured, connected, and—if required to—restarted each of your computers, click the File Explorer (folder) icon in the taskbar, or press Windows Logo+X and select File Explorer. Look for the Network and Homegroup items at the left edge of the Window, as shown in Figure 18.14.
Figure 18.14 Links at the left edge of File Explorer let you explore your network, and your homegroup if you have one.
If your network is up and running and sharing and discovery are enabled, you should see one icon for every computer you’ve connected. Double-click any icon to see what that computer is sharing with the network.
![]() If you don’t see other computers in the Network window, well, we have a whole chapter devoted to network troubleshooting. For suggestions, see “Getting Started,” p. 486.
If you don’t see other computers in the Network window, well, we have a whole chapter devoted to network troubleshooting. For suggestions, see “Getting Started,” p. 486.
If you set up a homegroup, the Homegroup list will have an entry for each user who has elected to share files. There might be entries for the other users on your own computer, as well as users on other computers. Shared printers should already be listed automatically in your Devices and Printers Control Panel applet, although if you have one or more printers that are not connected via USB cables, you might have to take additional steps to share them.
You’re almost finished. You have just a little more reading do to:
![]() You’ll certainly be connecting to the Internet, and when you do, you risk exposing your network to the entire world. Refer to Chapter 33 to find out what risks you’ll be exposed to and what you can do to protect your LAN. If you use Internet Connection Sharing or a connection-sharing router, you’re in pretty good shape. But in any case, going through Chapter 33 carefully is very important.
You’ll certainly be connecting to the Internet, and when you do, you risk exposing your network to the entire world. Refer to Chapter 33 to find out what risks you’ll be exposed to and what you can do to protect your LAN. If you use Internet Connection Sharing or a connection-sharing router, you’re in pretty good shape. But in any case, going through Chapter 33 carefully is very important.
![]() Read Chapter 21 to learn how to get the most out of your Windows network.
Read Chapter 21 to learn how to get the most out of your Windows network.
![]() See Chapter 37 for instructions on enabling remote access to your computer and network.
See Chapter 37 for instructions on enabling remote access to your computer and network.
![]() See Chapter 20 for information about networking with Macs, Unix, Linux, and older versions of Windows, as well as installing advanced networking services.
See Chapter 20 for information about networking with Macs, Unix, Linux, and older versions of Windows, as well as installing advanced networking services.
Joining a Windows Domain Network
If your computer is to be part of a domain network run by a version of Windows Server, it must be “joined” to the domain so that Windows will delegate its security functions to the network. Your network administrator should take care of this task for you. If you must do it yourself, you will need four pieces of information:
![]() The name to be given to your computer.
The name to be given to your computer.
![]() The domain name for your network.
The domain name for your network.
![]() Your domain logon name and password.
Your domain logon name and password.
![]() Any specific configuration information for the Internet Protocol (TCP/IP). In most cases, it is not necessary to make any changes in the default settings.
Any specific configuration information for the Internet Protocol (TCP/IP). In most cases, it is not necessary to make any changes in the default settings.
Use the following procedure to make your computer a member of your network domain:
1. Sign in to Windows with a Computer Administrator account.
2. Right-click the Start button or press Windows Logo+X and select System. In the Computer Name, Domain, and Workgroup settings section, click Change Settings. Then click the Network ID button.
3. Select This Computer Is Part of a Business Network; I Use It to Connect to Other Computers at Work and then click Next. Select My Company Uses a Network with a Domain and then click Next twice.
4. Enter the network login name, password, and network domain name supplied by your network administrator. Then click Next.
5. If the network administrator prepared the domain to accept your computer, a box will pop up saying “An account for this computer has been found....” Click Yes.
6. You will be prompted for the credentials for an account that has domain administrator privileges. An administrator might have to assist you here.
7. The next prompt asks, “Do you want to enable a domain user account to this computer?” You have two choices:
![]() If you want your domain account to be able to manage hardware, software, and files on your own computer, select Add the Following Domain User Account, and then enter your domain logon name and domain name. Click Next. Select Administrator and then click Next.
If you want your domain account to be able to manage hardware, software, and files on your own computer, select Add the Following Domain User Account, and then enter your domain logon name and domain name. Click Next. Select Administrator and then click Next.
![]() If you want to manage your computer using your original “local” account, select Do Not Add a Domain User Account and then click Next.
If you want to manage your computer using your original “local” account, select Do Not Add a Domain User Account and then click Next.
8. Click Finish. Click OK to close the System Properties dialog box and then click Restart Now.
When your computer has been joined to the domain and restarted, the login process might be slightly changed. If the Welcome screen says “Press Ctrl+Alt+Del to sign in,” type this key combination. (Hold down the Ctrl and Alt keys, press the Del key, and then release all of the keys.)
The first time you sign in, the icon for your original nondomain (“local”) account might still appear. If an icon for your domain account does not appear, select Other User. Then enter the username and password for your domain account. If the correct domain name doesn’t appear, enter your account name in the format domainnameusername.
![]() Note
Note
If your computer is disconnected from the network or you want to install new hardware, you can still sign in using a local account. At the Welcome screen, select Other User.
To sign in using a local account, select Other Account. Under Sign In Options, select the “key” icon, and then select How Do I Sign On to Another Domain? Enter your local account name in the format computernameusername, as shown on the screen.
To sign in using a Microsoft account, select the “box-and-cursor” icon and enter your online account name and password.
Bridging Two Network Types
A Windows computer can connect or bridge two different network types through software, letting the devices on both networks communicate with each other. This can eliminate the need to buy a hardware device to connect two disparate networks (although it works only when your Windows computer is turned on). Figure 18.15 shows an example of what bridging can do. In the figure, one computer serves as a bridge between an Ethernet LAN and a powerline LAN. (Previous versions of Windows could do this too. In this book, we just describe how to set it up using a Windows 10 computer as the bridge.)
Figure 18.15 Bridging a powerline and Ethernet network with Windows 10. Computers on either network can communicate as if they were directly connected.
Bridging is similar to routing, but it’s more appropriate for small LANs because it’s easier to configure and doesn’t require different sets of IP addresses on each network segment. Technically, bridging occurs at the physical level of the network protocol stack. Windows forwards network traffic, including broadcasts and packets of all protocol types received on either adapter, to the other. In effect, it creates one larger network.
To enable bridging in your Windows 10 computer, install and configure two or more network adapters, as described under “Installing Multiple Network Adapters,” earlier in this chapter. However, don’t worry about setting up the Internet Protocol (TCP/IP) parameters for either of the adapters yet. Then do the following:
1. At the right end of the taskbar, right-click the network icon and select Open Network and Sharing Center. (You can also get there via the Control Panel entry by selecting View Network Status and Tasks.) In the left panel, select Change Adapter Settings.
2. Select the icons you want to bridge by clicking the first, holding down the Ctrl key, and clicking the second.
3. Right-click one of the now-highlighted icons and select Bridge Connections.
4. A new icon named Network Bridge appears. Select this new icon and, if you want, rename it appropriately—for example, “Ethernet to Powerline Bridge.”
5. Double-click the new Network Bridge icon. Select Internet Protocol (TCP/IP) and configure your computer’s TCP/IP settings. You must do this last because any TCP/IP settings for the original two adapters are lost.
After you’ve created a bridge, your two network adapters function as one and share one IP address, so Microsoft disables the “network properties” of the individual network adapters. You must configure your computer’s network properties with the Network Bridge icon.
Remember that the connection between the two networks depends on the computer with the bridge being powered on.
You can remove the bridge later by right-clicking the Network Bridge icon and clicking Delete.