Kali offers various utilities to bypass password security. Password cracking tools can be found under Password Attacks and divided into tools used for offline and online attacks. This section will focus on tools used to compromise host systems during a web application Penetration Test. There are other tools available in Kali, such as tools designed to crack passwords for wireless protocols; however, that is out of scope for this text.
Note
Note that John the Ripper command line and Hydra were covered in Chapter 3, Server-side Attacks.
Johnny is a GUI for the very popular John the Ripper password cracking tool. We covered the traditional command-line version of John the Ripper is Chapter 3, Server-side Attacks. Like the command-line version, Johnny has several engines that allows it to crack different types of passwords, including encrypted and hashed passwords. Johnny has the ability to auto-detect most hashes and encrypted passwords, making the process easier for Penetration Testers. Attackers like the tool because it is very customizable and can be configured in a variety of different ways to speedup password cracking.
John the Ripper operates in the following manner:
- Attempts cracking passwords with dictionary words
- Uses dictionary words with alphanumeric characters appended and prepended
- Puts dictionary words together
- Adds alphanumeric characters to combine words
- Runs dictionary words with special characters mixed in
- When all else fails, attempts brute-force.
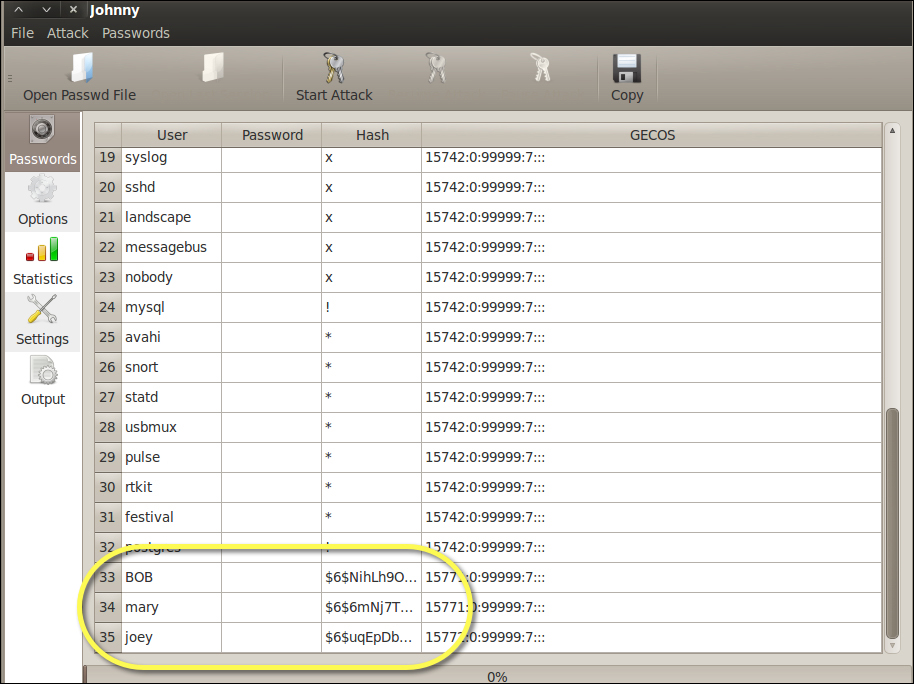
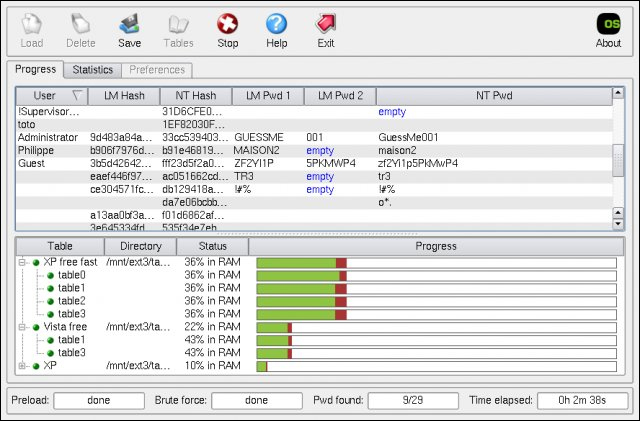
To use Johnny, go to Password Attacks | Offline Attacks and select Johnny. Click on Open Password File and select the password file you want to crack. The following screenshot shows a shadow file with users BOB, mary, and joey as the targets.
The Password tab will be filled as Johnny cracks the passwords.
Johnny has configuration tabs on the left side. The Options tab is where you select the type of attack. The following screenshot shows a definition of the default behavior and options for selecting the type of hash. Johnny's auto-detection is typically 90 percent correct.

The Statistics tab displays how long Johnny has been running an active session. The Settings tab specifies how Johnny will run as shown in the following example:

The Output tab showcases what Johnny is attacking. You will also find error messages and updates on the status of an attack session. The following example shows a message displaying Johnny identifying the type of hash:
John the Ripper and its GUI frontend's default wordlists are very limited. We recommend using a larger list, which can be found by searching online. To use a custom wordlist, go to the Options tab and select Wordlist mode. Browse to your custom wordlist and click on Apply.

Johnny will fill the password cells next to usernames as passwords are cracked. The following screenshot shows two of the three passwords cracked:


hashcat and oclHashcat are password cracker utilities. oclHashcat is a GPGPU-based version. The hashcat/oclHashcat utilities are multithread tools that can handle multiple hashes and password lists during a single attack session. The hashcat/oclHashcat utilities offer many attack options, such as brute-force, combinator, dictionary, hybrid, mask, and rule-based attacks.
BackTrack offers many versions of hashcat found under Privilege Escalation | Password Attacks | Offline Attacks. The "ocl", or open cl, is the open implementation to unify the Nvidia and ATI GPU drivers. Some versions may not run even after updating BackTrack. You may need to download the updated versions from www.hashcat.net.
To use hashcat, open the hashcat application or navigate to Password Attacks | Offline Attacks | hashcat.
To use hashcat on a document, type hashcat [options] hashfile [wordfiles|directories. The following example shows hashcat running a wordlist against a shadow file:
hashcat offers a GUI as well, which acts as a frontend for the CLI. Some people like it, because it's simple to use and includes displaying the command-line code at the bottom window.

samdump2 is a utility that dumps the Microsoft Windows password hashes from a SAM file so that they can be cracked by an offline tool. For newer versions of Windows, you will need another tool to capture the SYSKEY (boot key) file to access the hashes stored in the SAM database.
samdump2 can be found under Password Attacks | Offline Attacks | samdump2. When you open samdump, a Terminal window will pop up.

You must mount your target Windows system so that samdump can access the SAM file.
Next, copy the SAM and SYSTEM files into your attack directory.
cp SAM SYSTEM /root/AttackDirectory
Navigate to the attack directory and issue bkhive SYSTEM bootkey to obtain the bootkey. Copy the bootkey into a text file so that samdump has the SAM file with bootkey.
cd /root/AttackDirectory > windowshashfiles.txt
Execute samdump using the samdump SAM bootkey command. Copy the output into a second text file.
Samdump2 SAM bootkey > windowshashfiles2.txt
Now use a password cracking tool such as John the Ripper to crack the hashes!
chntpw is a tool on Kali Linux, Backtrack, and other Linux distributions that resets local passwords on Windows 8 and earlier versions of Windows. It modifies the Windows password database. This tool is primarily used for getting into Windows boxes when you do not know the password.
To use chntpw, boot up the Windows machine with the Kali Live CD. To download Kali Linux, go to http://www.kali.org/downloads/ and download the ISO image.
Burn the ISO to a CD and boot the Windows machine with the Live CD. On the boot menu for Kali, select Forensics option.

The SAM file is usually located under /Windows/System32/config. You will need to navigate in the Terminal screen to this directory. On your system, it may look something like this:
/media/hda1/Windows/System32/config
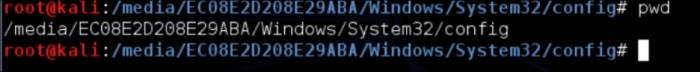
Every system might be slightly different. In this example, Kali seems to be using the serial number of my hard drive as the device location. This is because I have booted up a Windows 7 virtual machine with the Kali Live CD. The SAM database is usually in the /media/name_of_hard_drive /Windows/System32/config.
The following screenshot lists the SAM database file on my hard drive:
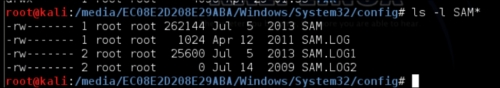
The command chntpw -l SAM will list out all the usernames that are contained on the Windows system. The following screenshot shows us the result of running the command chntpw –l SAM:

The command gives us a list of usernames on the system. When we have the username we want to modify, we run the command chntpw -u "username" SAM.
In this example, we have typed chntpw -u "Administrator" SAM, and we got the following menu:
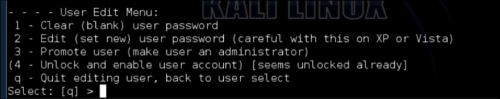
We now have the option of clearing the password, changing the password, or promoting the user to administrator. Changing the password does not always work on Windows 7 systems, so we recommend clearing the password. By doing this, you will be able to log into the target system with a blank password.
To access chntpw, go to Password Attacks | Offline Attacks | chntpw. A Terminal window will open, showcasing the welcome screen for chntpw. There are a few ways to use chntpw, as described on the main landing page as follows:
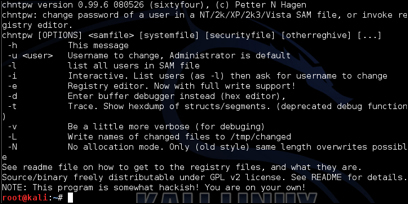
To use the interactive mode, type chntpw -i and the path to the SAM file. If the target is a mounted system, you will need to specify the location of the SAM file inside the mounted directory.
A menu will popup providing options for changing the SAM file. You can select option 1 to blank out the password.

Ophcrack is a Windows password cracker based on Rainbow tables. Kali offers a CLI and GUI version. Ophcrack can import hashes from a variety of formats including dumping directly from the SAM files of Windows. The following screenshot shows some of the available formats to load into Ophcrack:
Ophcrack comes with built-in Rainbow tables, as shown in the following example. We recommend loading the latest Rainbow tables rather than using the default tables.
Rainbow tables are available from online sources such as the developer's website http://ophcrack.sourceforge.net/tables.php.
To access ophcrack, go to Password Attacks | Offline Attacks and select either the CLI or GUI version. Click on Load, and select the path to the file you want to crack (for example, a Windows SAM file).
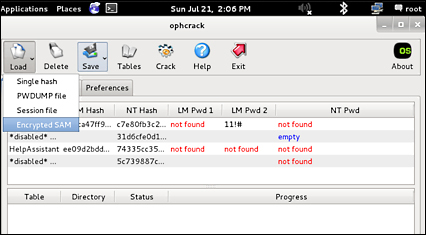
For this example, we used the Kali ISO on a Windows machine and booted Kali in Forensics mode. We browsed to the /windows/system32/config directory to get to the SAM database. You can learn more about using Kali Linux in the Forensics mode in Chapter 7, Defensive Countermeasures, of this book. You can also use an offline copy of the SAM database directly with Kali.

You should see the hash with the username and user ID. Click on the Crack button and wait for the password.
Crunch is a tool used to generate password lists. This can be extremely helpful if you are able to gather intelligence on how your target creates passwords. For example, if you capture two passwords and notice the target uses a phase followed by random digits, Crunch can be used to quickly generate a list of that phrase followed by all the possible random digits.
Crunch has special characters that translate to the following:
@: Inserts lowercase characters%: Inserts numbers,: Inserts uppercase characters^: Inserts symbols
For this example, we will assume we know our target uses pass followed by two unknown characters in their password. To run Crunch for a six character password having pass followed by two unknown numbers, use %% to represent any number. To run this and place the output in a text file named newpasswordlist.txt, use the example input:
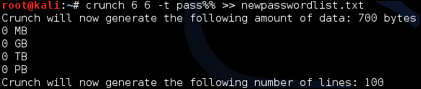
The output text file will contain all the possible number combinations. The following screenshot shows the top of the output file:
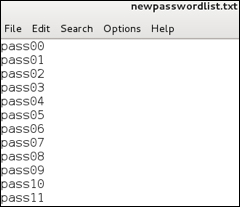
To add all lowercase letters, use crunch 6 6 -t pass followed by @@ representing all the lowercase letters, as shown in the following example:
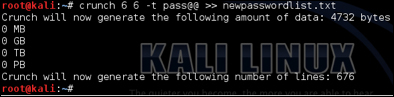
Now the text file has all lowercase letters and numbers as shown in the following example:

