The VMCA, in vSphere 6, provisions a signed certificate to each ESXi host. The certificate specifies the VMCA as the root certificate authority by default. The certificate is provisioned when the ESXi host is added to vCenter Server, or installed or upgraded to ESXi 6.0 or later.
If the VMCA is a subordinate certificate authority, it is allowed to sign certificates for the ESXi hosts. This can be done using the vSphere Web Client. To do so, log into the vSphere Web Client and navigate to the Hosts and Cluster inventory view. Right-click on the ESXi host, and select Certificates | Renew Certificate.

This will bring up the Renew Certificate dialog; click on the Yes button.

This can also be done without making the VMCA a subordinate certificate authority. This process would need to be before the certificate expires or if the hostname is changed. However, if the certificate has already expired, just disconnect and remove the ESXi host from the inventory and then reconnect it. The vCenter Server will renew an expired certificate when a host is added to the inventory.
By default, the ESXi host uses the automatically generated certificates that were created at installation. If required by security policy, these certificates may be replaced.
To begin this process:
- Log into the ESXi shell with root privileges.
- Navigate to the
/etc/vmware/ssldirectory and use thelscommand to view the contents of this location. The.crtfile and the.keyfile will be listed.
- It's a good idea to keep the old
.crtand.keyfile in case of any issues. To rename those files, use themvcommand, as shown:mv rui.crt old.rui.crtmv rui.key old.rui.key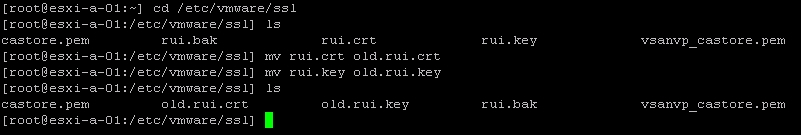
- Next, copy the new certificate and key to
/etc/vmware/ssl. Any file transfer application that uses an HTTPS session may be used, however, the following screenshot demonstrates using WinSCP. - If the certificate and key are not currently named
rui.crtandrui.key(respectively) then rename the files to match the aforementioned names.
- Once the certificates are in place in the
/etc/vmware/ssldirectory, restart the ESXi host. (Or the host could be put into maintenance mode, the new certificates installed and the management agents restarted).
