Any time you operate a network, you must protect it against intrusions from outsiders and damage caused by intentional or accidental misuse or abuse by internal network users. Computer networks are vulnerable to several forms of attack, including unauthorized access to files, theft of service, and denial of service caused by excessive network-connection requests. Strictly speaking, attacks on individual computers, such as viruses, worms, and Trojan horses, are a separate issue from network vulnerabilities, but a good network security plan will include firewalls and other tools that also protect the computers connected to the network.
This chapter describes the basic steps that every home and small business network manager must take to keep his or her network secure.
Intruders break into networks for several reasons:
They want to open files and read documents, either to steal confidential information or just to overcome the challenge of "cracking" protected files.
They want to use the network to obtain a high-speed Internet connection.
They want to use the network to forward unsavory or illegal data (such as spam or pornography) to the Internet or download similar material.
They want to steal passwords, credit card numbers, bank account information, and other forms of data that they can either sell or use to order items of value.
They want to interfere with normal network operation by overloading the network's ability to handle data, altering or deleting essential software, or causing hardware to break down.
Two important objectives of network security are to limit access to authorized users and to keep those same users away from configuration settings and confidential data. The most important tools for maintaining a secure network include different access levels for different users, passwords, and firewalls. If they're not adequate, more complex methods are also possible, including kernel-level mandatory access control systems, authentication and authorization mechanisms, and data encryption.
Almost all computer operating systems have at least two levels of user accounts: administrators and users. Administrators have access to all of the computer's configuration settings, such as installing or removing printers, joining a network, and so forth. Users can read and write programs and data files assigned to their own accounts and to resources whose owners allow other people to use them. On a network, a guest account has its own access settings for those who use a computer's resources through the network rather than through the keyboard and other input devices connected directly to each computer.
Each user has exclusive control of his or her files. The owner of every account can set access controls on files that keep them either private and confidential or public and accessible to other users. Even if other users have accounts on the same computer, they can't read somebody else's private files. The exception is a system administrator account that provides access and control to almost all files.
Passwords are the first line of defense against unwanted access to a computer or a network. If a would-be intruder can't get the computer to start the operating system, opening data files or using the network is a lot more difficult (but not impossible—a determined intruder with enough time and resources can often get around a password to open and read unencrypted files).
You may be tempted to set up your computer without a startup password, but that completely defeats most of the computer's security features and those of the network connected to it. Unless you're absolutely certain that no strangers will ever get close enough to turn on your computer or gain access through a wired or wireless network, and you trust everybody else in the house or office to respect your privacy, it's worth the extra time needed to enter a password every time you turn on the computer or connect to it through a network.
An effective password should be difficult to guess and long enough to make it hard to find with a brute-force program (a program that applies massive computing resources to trying one password after another until it stumbles upon the right one).
Too many people use one of these items as a password:
Your own first name or middle name
The name of your spouse, child, or pet
Your mother's maiden name or any other family name
Your favorite entertainer, band, team, or song
Your own first initial and last name (such as JSmith)
An obvious string of numbers, letters, or both (such as 123456, abcxyz, or abc123)
Your birthday or some other significant date
Your home town or country
A string of characters from your keyboard (such as qwerty or !@#$%)
The word password
The phrase letmein (that is, let me in, not the name of a Chinese noodle dish)
The phrase trustno1 (Fox Mulder's password on The X-Files TV series)
The word swordfish (originally used in the Marx Brothers' Horse Feathers and in many subsequent movies, books, and computer games)
The word sex or any common curse or obscenity
The word God or Jesus (or any other deity of your choice)
Any of these words or phrases spelled backward
When a "computer security expert" in a movie or TV show finds the right password to break into the bad guy's computer on the third try, he probably tried some of the passwords on this list.
Many network routers, modems, and other hardware come with default passwords preset at the factory. These passwords are well known by crackers and easy to find in equipment manuals and on the Internet.
The best passwords are random strings of letters, numbers, and other characters, at least seven or eight characters in length. One expert tested a brute-force password-cracking program; Table 13-1 shows the amount of time that one programmer (Jimmy Ruska) needed to discover passwords of different lengths by creating and testing every possible combination. (The specific numbers in this table apply only to his particular program. You should pay attention to how the amount of time increases as you add more characters to a password rather than the exact times.) The time to crack is even greater if your password includes one or more symbols, such as !, @, #, $, &, and +.
Table 13-1. Time to Test All Possible Passwords[a]
Password Length | Letters Only | Letters and Numbers |
|---|---|---|
| [a] | ||
3 characters | 1 second | 2 seconds |
4 characters | 3 seconds | 10 seconds |
5 characters | 1 minute, 17 seconds | 6 minutes |
6 characters | 26 minutes | 3 hours, 30 minutes |
7 characters | 14 hours | 6 days |
8 characters | 15 days | 205 days |
Other cracking methods can be slower or faster, but the general point—that longer passwords are more difficult to crack—still applies.
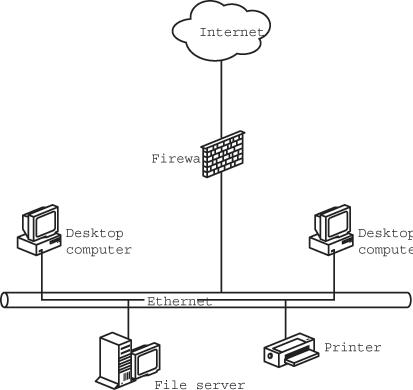
A firewall is a server that uses a set of rules established by the network manager to inspect incoming data and to block data from a source that isn't on a list or files that match a particular description (such as a virus). Or the firewall might pass all data moving from the LAN to the Internet but only allow certain types of data from the Internet. The most common use of a firewall in a LAN is at the gateway to the Internet, as shown in Figure 13-1. The firewall monitors all inbound and outbound data between the computers on the local network on one side and the Internet on the other. This kind of firewall is intended to protect the computers on the LAN from unauthorized intrusion from the Internet.
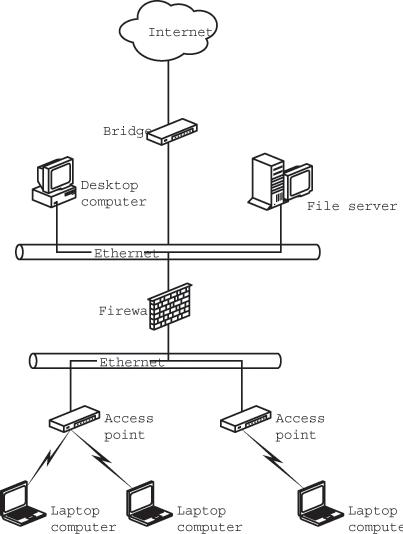
In a wireless network, a firewall can also be placed at the gateway between the wireless access points and the wired network. This firewall isolates the wireless portion of the network from the wired LAN, so intruders who have connected their computer to the network without permission can't use the wireless connection to reach the Internet or the wired part of the LAN. Figure 13-2 shows the location of a firewall in a mixed network that includes both wired and wireless connections.
A firewall in a wireless network can perform several functions:
It can act as a gateway router between the wireless network and a wired LAN.
It can protect a direct connection from a single computer to the Internet.
It can block all traffic moving from the wireless side to the wired network that doesn't come from an authenticated user.
It passes commands, messages, and file transfers from trusted users to the Internet.
Therefore, a legitimate user can connect to network nodes on the wired part of a mixed LAN or on the Internet, but an intruder would be cut off at the firewall.
Because authorized wireless users and intruders are both on the unprotected side of the firewall, it does not isolate the wireless nodes from one another. An intruder can still gain access to another computer on the same wireless network and read shared files, so it's a good idea to turn off file sharing on any computer connected to a wireless network and to use firewall software on individual computers.
A firewall for a wireless network should use some kind of authentication to allow legitimate users through the gateway, but it should reject everybody else. If access control based on MAC addresses is built into Wi-Fi networks and the added authentication in 802.1x are not adequate, then an outboard firewall should require all users to enter a login and password before they can connect to the Internet.
If your wireless network includes computers running more than one operating system, your firewall must use a login tool that works on any platform. The easiest way to accomplish this is with a web-based authentication server, such as the one included with the Apache web server (http://httpd.apache.org/).
The Apache web server is available as a Linux or Unix application that can run on an old, slow computer with an early Pentium or even an antique 486 CPU, so you can often recycle an old junker and use it as a firewall. Both the Apache application and the operating system are available as open source software, so it ought to be possible to build an extremely low-cost Apache firewall.
If you prefer to use Windows, or if you don't want to assemble your own firewall, you have several options. You can use the Windows version of Apache, or you can use a commercial utility such as the ones listed at http://www.thegild.com/firewall/.
Attacks on a wireless LAN don't all come through the air. A wireless network also requires the same kind of firewall protection against attacks from the Internet as an entirely wired network. Many wireless access points include configurable firewall features, but if yours does not, the network should include a firewall program on each computer, along with a separate router or a dedicated computer acting as a network firewall.
Client firewall programs provide another line of defense against attacks coming from the Internet. Some of these attacks come from miscreants who are looking for a way to read your files and other resources that you don't want the entire world to see. Others might want to use your computer as a relay point for spam or attempts to break into some other computer halfway around the world in order to make the real source more difficult to identify. Still others spread viruses or use really unpleasant programs called rootkits that take control of a PC or display threatening messages.
An unprotected system with a lot of unused storage space can be an attractive target for hackers who want to distribute pirated software, music, or video files (you didn't think they store that stuff on their own computers, did you?).
The number of such idiots and creeps on the Internet is surprisingly large; if you install a firewall that notifies you when an outside computer tries to connect to your network, your firewall log will probably list several break-in attempts every day.
The easiest firewall to use with a wireless network is one that's built into an access point. Many wireless access points combine the functions of a wireless access point with a broadband router and an Ethernet switch, so they support both wired and wireless network clients.
As you know, a network router translates addresses between the numeric IP address that identifies the LAN to the Internet and the internal IP addresses that identify individual computers within the local network. The firewall normally blocks all incoming requests for data to network hosts, but this creates problems when you want to use one or more of the computers on the local network as file servers. So the firewall redirects certain types of requests to the appropriate computer inside the firewall.
Each request to connect to a server includes a specific port number that identifies the type of server. For example, web servers operate on port 80, and FTP servers use port 21, so those port numbers are part of the request for access. To accept access requests to a server, you must instruct the firewall's Network Address Translation (NAT) function to forward those requests to a specific computer within the LAN. Table 13-2 lists the most common service port numbers.
Hundreds of other port numbers have been assigned, but you will never see most of them in actual use. The official list of port assignments is available online at http://www.iana.org/assignments/port-numbers.
NAT assumes that each internal server's IP address doesn't change from one request to the next. A web server on 192.168.0.23 today won't migrate to 192.168.0.47 next week. That's generally not a problem on a wired network, but in a wireless setting where network clients join and leave the network all the time, the DHCP server automatically assigns the next available address to each new client. If one of those clients is the home of one of the network's service ports, the NAT probably won't find it. This problem is not common, because most networks don't use portable computers as servers, but it can happen. The solution is to turn off the DHCP server and assign a permanent IP address to each client.
A wireless gateway firewall at the interface between the access point and the wired part of your LAN will keep intruders from using your network to reach the Internet, and a firewall at the Internet connection will turn away attempts to connect to your network from the Internet, but a wireless network still needs one more form of protection. If somebody gains access to your wireless LAN without permission, you want to keep them away from the other legitimate computers on the same network, so each network node needs a client firewall program.
Client firewalls perform the same functions at a computer's network interface that a LAN or enterprise firewall performs for the entire network; a client firewall detects attempts to connect to TCP service ports and rejects them unless they match one or more of the firewall program's configuration settings. Several good firewall products are available as shareware, and others are free to noncommercial users. It's easy to try them on your own system and choose the one you like best. ZoneAlarm (http://www.zonealarm.com/) and LANguard (http://www.languard.com/) are both well-regarded Windows firewall software products. There's also a firewall built into Windows XP and Windows Vista that is adequate for most home and small business networks.
Linux and Unix users also have plenty of firewall options. Most of them were written for stand-alone firewall computers that are commonly used as network gateways, but they could be equally appropriate as protection for individual network clients.
In Linux, the iptables firewall is part of the kernel. It's well-documented at http://www.netfilter.org/projects/iptables/index.html. Port Scan Attack Detector (psad) is another set of tools that identify port scans and other intrusions on many Linux systems. For more information, see http://www.cipherdyne.org/psad/.
IP Filter is a software package that provides firewall services to FreeBSD and NetBSD systems. The official IP Filter website is http://coombs.anu.edu.au/~avalon, and you can download an excellent HOWTO document at http://www.obfuscation.org/ipf/ipf-howto.txt. The program can deny or permit any packet from passing through the firewall, and it can filter by netmask or host address, establish service port restrictions, and provide NAT services.
OpenBSD, FreeBSD, and NetBSD can all use the Packet Filter, or PF, facility to perform firewalling. More information is available at http://www.openbsd.org/faq/pf/.
NetBSD/i386 Firewall is another free Unix firewall. It will operate on any PC with a 486 or later CPU and as little as 8MB of memory. The NetBSD/i386 Firewall Project home page is http://firewall.dubbele.com/.