Every computer connected to a network must follow a set of rules and specifications that define the characteristics of both the physical connection and the form and structure of the data that moves from one computer to another. Without these rules, the people using the network cannot be sure that their computers will communicate successfully.
For example, the plugs at the ends of data cables must match the sockets on each computer and other network hardware. If a cable uses a square plug with two pins, but the computer has a round socket with four holes, they won't fit together. The same thing applies to the electrical voltages, timing, error checking, and other issues. There are many different kinds of networks, each with its own rules. This chapter explains a few general principles about networks and describes the network types that you're most likely to see in a home or small office network.
You can use a network without understanding all the internal details of network communications, but if you're designing and building a new network, you should know how to choose the best options for your particular requirements. You can treat individual network components as a series of black boxes, but you still have to know which black boxes to use. And when something goes wrong, knowing what's inside those boxes will make troubleshooting a lot easier.
Before we talk about specific network types, let's look at the common elements of every computer network.
As you probably know, computers reduce all information to only two information states: Either a signal is present, or there is no signal. These two conditions are usually described as 1 and 0, or on and off, or mark and space. Each instance of a 1 or a 0 is a "bit." Anything described as "digital" can be reduced to those ones and zeroes.
The form that each 1 or 0 takes is different in different types of communication channels. It could be a light, sound, or electrical charge that is either on or off; a series of long and short sounds or light flashes; or two different audio tones, electrical voltages, or radio frequencies. In a very simple system, the 1 might correspond to "yes" and the 0 to "no," or any other pair of options.
Individual bits only offer two options, so they're not particularly useful, but when you string eight of them together (into a byte), you can have 256 different combinations (2 × 2 × 2 × 2 × 2 × 2 × 2 × 2). That's enough to assign a different sequence to every letter of the alphabet (both upper- and lowercase), the ten digits from 0 to 9, spaces between words, and other symbols such as punctuation marks and many letters used in foreign alphabets. A byte is the basic building block of computer communication. The most widely used coding system for converting bytes to characters is called ASCII (American Standard Code for Information Interchange). Figure 2-1 shows a typical sequence of two bytes.
ASCII is fine for text, but a computer can also convert many other forms of information to digital data. For example, it can divide every second of sound from a microphone or an analog recording into thousands of very short segments and use 16 or 24 bits to specify the content of each segment, or divide a picture into millions of individual points (called pixels, short for picture elements) and use a series of bits to specify the color of each bit.
A wire or other data link can carry only one bit at a time. Either there's a signal on the line or there isn't. Over short distances, it's possible to send the data through a cable that carries eight (or some multiple of eight) signals in parallel through eight separate wires. Obviously, a parallel connection can be eight times faster than sending one bit at a time through a single wire, but those eight wires cost eight times as much as a single wire. That added cost is insignificant when the wires extend only a foot or two, but the additional cost of parallel wires can add up quickly when you're trying to send the data over a long distance. And when you're using existing circuits such as telephone lines, you don't have any choice; you must find a way to send one bit at a time, with some additional bits and pauses that identify the beginning of each new byte. This is a serial data communications channel, because you're sending the bits one after another. At this stage, it doesn't matter what medium you use to transmit those bits—it could be electrical impulses on a wire, or two different audio tones, or a series of flashing lights, or even a lot of notes attached to the legs of carrier pigeons—but you must have a way to convert the text or other output of the computer to the signals used by the transmission medium, and to convert the same signals back again at the other end.
Communication over a direct physical connection (such as a wire) between a single origin and destination doesn't need any kind of address or routing information to tell a message where to go. You might have to set up the connection first (by placing a telephone call or plugging cables into a switchboard), but after you're connected, the link remains in place until you instruct the system to disconnect. This kind of connection is great for voice and for simple data links, but it's not particularly efficient for digital data on a complex network that serves many origins and destinations, because a single connection ties up the circuit all the time, even when no data is moving through the channel.
The alternative is to send your message to a switching center that will hold it until a link to the destination becomes available. This is known as a store and forward system. If the network has been properly designed for the type of data and the amount of traffic in the system, the waiting time will be insignificant. If the communications network covers a lot of territory, you can forward the message to one or more intermediate switching centers before it reaches the ultimate destination.
To make the network even more efficient, you can divide messages that are longer than some arbitrary limit into separate pieces, called packets or frames. Packets from more than one message can alternate with packets containing other messages as they travel between switching centers, and reassemble themselves into the original messages at the destination.
The great advantage of this approach is that many messages can share the same circuits on an as-available basis. The packets from a single message might alternate with packets from one or more other messages as they move through parts of the network. For example, if you send a message to a recipient in another city, the packets usually move through an inter-city channel along with many other messages.
Each data packet must also contain yet another set of information: the address of the packet's destination, the sequence order of this packet relative to other packets in the original transmission, and so forth. Some of this information provides additional error checking and instructs the switching centers where to forward each packet, while other information tells the destination device how to reassemble the data in the packet back into the original message.
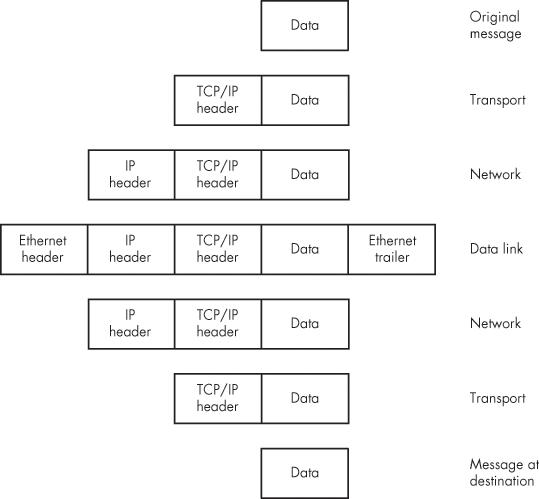
The headers (at the beginning of a packet) and trailers (at the end of a packet) attached to each packet include the address of the packet's destination, information that allows the recipient to confirm that the packet's content is accurate, and information that the recipient uses to reassemble the packets in the original order. Between the origin and the destination, network routing equipment sometimes adds more headers or trailers that contain routing instructions and other administrative information.
Figure 2-2 shows how a network adds and removes headers and trailers at different stages of a communication session. The specific names of the headers and trailer don't matter right now; the point is that they surround the original data packet.
That same pattern repeats every time you add another layer of activity to a communications system. Each layer may attach additional information to the original message and strip off that information after it has done whatever the added information instructed it to do. By the time a message travels from a laptop computer on a wireless network through an office network and a gateway to the Internet, and onward to a distant computer connected to another local network, a dozen or more information attachments might be added and removed before the recipient reads the original text. A package of data that includes address and control information ahead of the bits that contain the content of the message, followed by an error-checking sequence, is called a frame. Both wired and wireless networks divide the data stream into frames that contain various forms of handshaking information along with the original data.
Note
The network deals with packets and frames at different places during the process of transmitting data. Fortunately, this all happens automatically, so you (as a network user) don't have to worry about adding or removing them by hand.
In a perfect transmission channel, the signal that goes in at one end would be absolutely identical to the one that comes out at the other end. But in the real world, there's almost always some kind of noise along the line that can interfere with the original signal. Noise is defined as anything that interrupts or is added to the original signal; it could be caused by a lightning strike, interference from another communications channel, devices not working correctly, or dirt on an electrical contact someplace in the circuit (or in the case of carrier pigeons, an attack by a marauding hawk). Whatever the source, noise in the channel can interrupt the flow of data. In a modern communications system, those bits are pouring through the circuit extremely quickly—millions of them every second—so a noise hit for even a fraction of a second can obliterate enough bits to turn your data into digital gibberish.
Therefore, your data stream must include a process called error checking. Error checking is accomplished by adding some kind of standard information to each byte. In a simple computer data network, the handshaking information is called the parity bit, which tells the device receiving each byte whether the sum of the ones and zeroes inside the byte is odd or even. This value is called a checksum. If the receiving device discovers that the parity bit is not correct, it instructs the transmitter to send the same byte again. More complex networks, including wireless systems, include additional error-checking handshaking data with each string of data.
The computer that originates a message or a stream of data can't just jump online and start sending bytes. First it has to warn the device at the other end that it is ready to send and make sure the intended recipient is ready to accept data. To accomplish this, a series of "handshaking" requests and answers must surround the actual data.
The sequence of requests goes something like this:
Origin: "Hey destination! I have some data for you."
Destination: "Okay, origin, go ahead. I'm ready."
Origin: "Here comes the data."
Origin: Data data data data . . . checksum
Origin: "That's the message. Did you get it?"
Destination: "I got something, but it appears to be damaged."
Origin: "Here it is again."
Origin: Data data data data . . . checksum
Origin: "Did you get it that time?"
Destination: "Yup, I got it. I'm ready for more data."
We can leave the specific form of handshaking information to the network designers and engineers, but it's important to understand that not every bit that moves through a computer data network is part of the original block of information that arrived at the input computer. In a complex network such as a wireless data channel, as much as 40 percent or more of the transmitted data is handshaking and other overhead. It's all essential, but every one of those bits increases the amount of time that the message needs to move through the network.