A symmetric key is simpler to implement but it faces the problem of exchanging the keys in a secure manner. A public or asymmetric key has overcome the problem of key exchange by using a pair of keys: public and private. A public key can be distributed in an unsecured manner, while the private key is always kept with the owner secretly. Any one of the keys can be used to encrypt and the other can be used to decrypt:
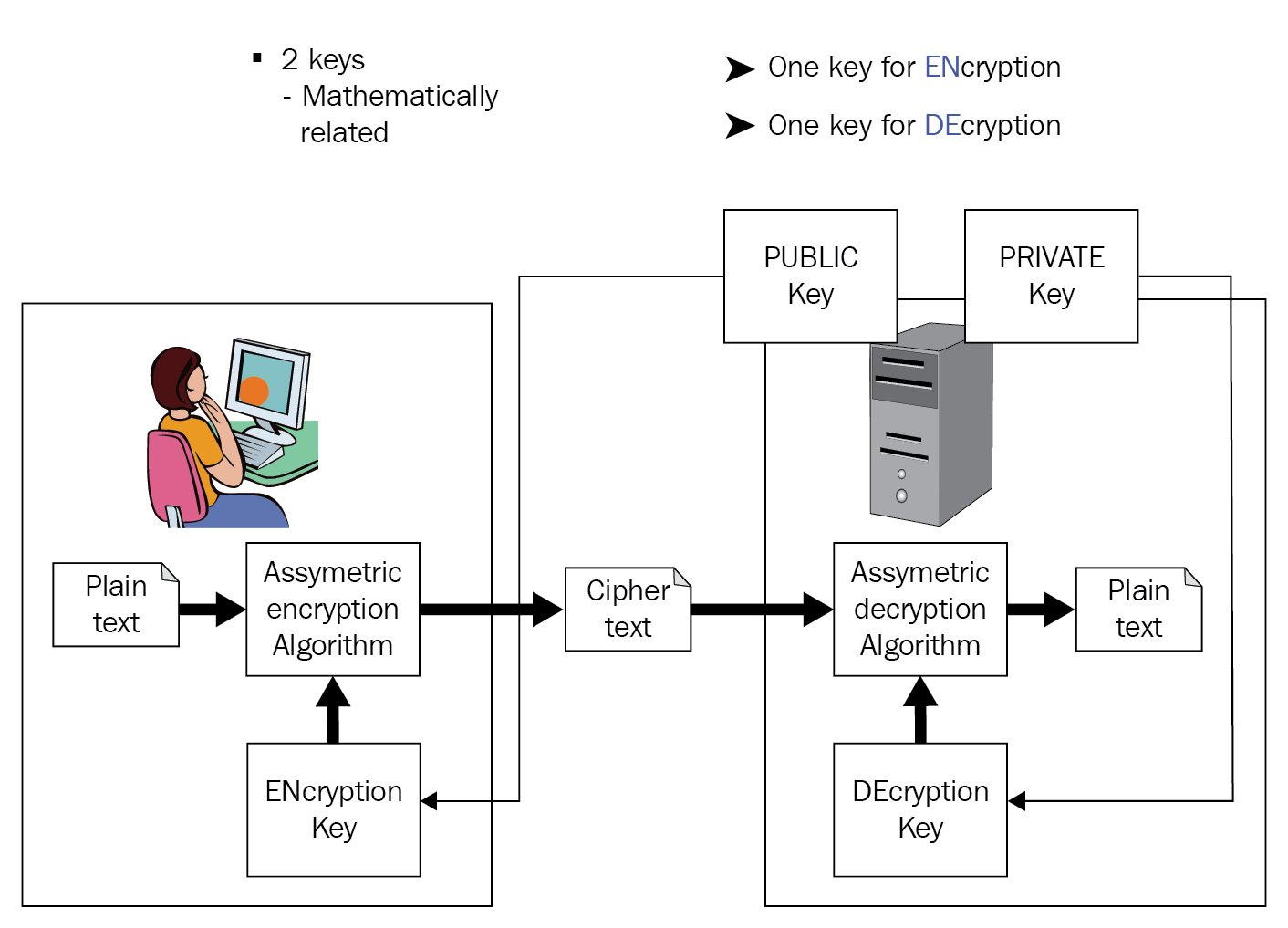
Here, the most popular algorithms are:
- RSA
- Diffie Hellman
- ECC
- DSA
Secure protocols such as SSH have been implemented using public keys.
