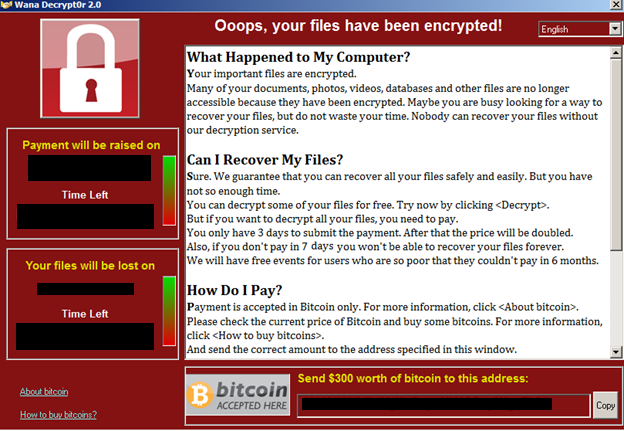
WannaCry was the huge global outbreak of 2017. It was first reported on May 12, 2017 infecting UK hospitals. Wannacry demanded a ransom of $300-$600 in bitcoin. WannaCry is also known as Wannacrypt and Wcry.
WannaCry took advantage of an exploit called EternalBlue. Shadowbrokers, a hacker group, leaked the EternalBlue exploit. EternalBlue is known to exploit a vulnerability in Server Message Block (SMB) protocol version 1. The vulnerability has been described here: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0144. SMB is a protocol that is used for sharing files within an organization. So by exploiting the vulnerability, WannaCry spreads into the internal network of an organization. We call this lateral movement, as it spread within the network. We talked about lateral movement in Chapter 3, Ransomware Distribution.
Here is a small explanation for the spread of wannaCry. WannaCry first scans the systems in the network that have smbv1 installed. It does this by scanning internal IPs in the network. After locating the systems that have SMBv1, it then tries to exploit those systems using the EternalBlue exploit. If a system is successfully exploited, WannaCry gains access to the system. After that, it uses another tool called DoublePulsar to copy itself into the exploited system. DoublePulsar is another hacking tool that acts as a backdoor. WannaCry is also known to install a TOR client on the system so that it can use it to communicate with its CnC. WannaCry is also known to use Mimikatz. Mimikatz is a hacktool (described in Chapter 1, Malware from Fun to Profit) that can retrieve passwords from Windows:
The following are the steps used by wannacry to encrypt the files on the victim machine:
- A public/private RSA-20148 key pair is generated.
- The private RSA key is never delivered to the victim, but the public key is sent to the victim and it's embedded in the wannacry itself.
- On the victim machine, a random AES key is generated for each key that needs to be encrypted.
- The AES is then encrypted by the RSA public key embedded in the malware. So to retrieve the AES key used to encrypt files, you need the private RSA key which is with the hacker.
- Wannacry thus does not need to contact its C&C to encrypt files.
- The encrypted files have the extension .wcry or wannacry.
The following are the list of file extension that wannacry encrypts:
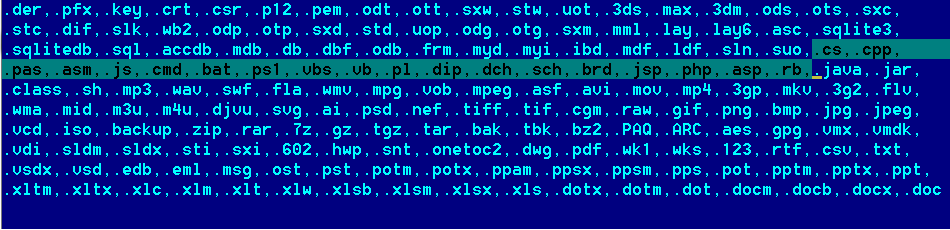
Wannacry also encrypts files used by the programmers. Files with the extension .cpp contain source code for C programs. Similarly, .asm stands for assembly language.
Here is a screenshot of the virtual memory of a wannacry sample:

In virtual memory, you can see strings such as WANNACRY, @[email protected], @[email protected], @[email protected]. [email protected], and @[email protected] are used to show the ransom note to the victim. You can see a list of file extensions that will be encrypted by the ransomware too. The administrator can use these strings to create rules for detecting wannacry.
Microsoft has released patches for the EternalBlue exploit. A patch, delivered in time, could have saved the wannacry outbreak. WannaCry tries to evade sandboxes by trying to reach a non-existent domain. We explained about sandboxes in Chapter 10, Ransomware Prevention and Detection. If malware tries to connect to its CnC, many sandboxes stop it and instead send back a fake response to the malware. Fakenet is a malware analysis tool that does a similar thing by blocking the actual connection and sending back a fake response to the malware. So wannacry tries to connect to a domain that does not exist. If it gets a response back, it assumes that it's executing in a sandbox or malware analysis environment and it terminates. It turned out to be a benefit for the security community itself. MalwareTechblog mentioned registering this fake domain: iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com on 12 May 2017. This slowed down the ransomware. This domain was called killswitch, as it stopped WannaCry from causing further infections.
