Scareware is malicious software that usually suggests that the user has some problem in the system and then lures the user to buy fake software. Although we can't categorize scareware as ransomware, they certainly trick you into buying software.
A lot of them use simple Windows APIs to find out what software is executing on your system. They then display the drivers, registry, and software found on your system with a fake message that there are some errors in the system.
There are a lot of fake applications that claim to clean and fix registries, drivers, and other software on the victim's machine. They have a great graphical interface that can easily convince somebody without knowledge of security software. They even have toll free numbers for assisting their victims. A lot of these were distributed on well-known software repository sites and were also visible at the top in search engines:
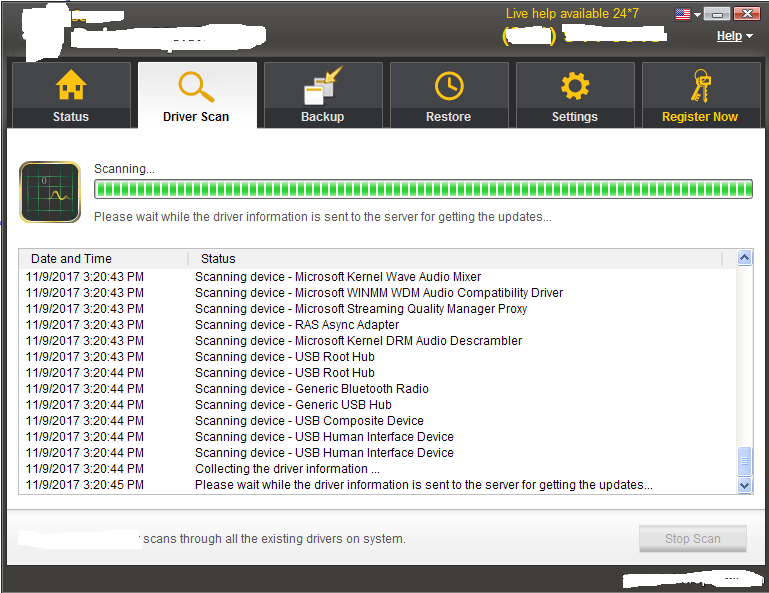
Fake Antivirus (FakeAVs) took the lead over rogue software in 2009. FakeAVs are a replica of real antivirus software. They are also known as rogue antivirus in the security industry. There was a huge distribution of fake antivirus from 2009 to 2012. Several attack vectors were involved in the distribution of fake antivirus. Rogue antivirus is known to be distributed from exploit kit spam emails. In early 2009, they were known to be distributed through fake video codec web pages. These web pages claim to have a video one is interested in. The name of the video could be related to some latest movie or event, which tempts the victim to view it. The victim is asked to download and install a codec in order to view the video. The victim downloads the codec, which is a binary file for the fake antivirus. The victim gets infected after trying to install the so-called codec:

It has the following specific components, which make it look like a real antivirus:
- The progress bar shows scanning is in progress, although the real scanning does not take place
- The detection names shown looks very similar to a genuine antivirus engine
- It blocks the legitimate program from launching, saying that the program is infected
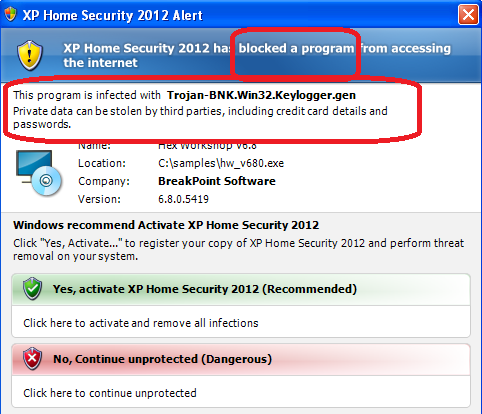
- There is a user interface option to register or buy
- Some fake antivirus also display a toll-free number

A lot of the rogue antivirus were kept at low prices, such as one dollar, which lures users. People were so lured by fakeAVs that many bought it and people were even known to search for the keys, cracks, and keygens on forums.
The FakeAV infection makes the following changes to the system:
- Disables regedit.
- Disables task manager.
- Disables firewall.
- Disables UAC (user access control)—this is a warning popup when you try to execute a program. It asks if the user wants to run a program.
- Kills other antivirus software.
- Creates a run entry to survive reboots.
- Does not allow the user to do other stuff on the system. Its window remains at the top of other windows. A similar technique is used by lockscreen ransomware explained in the next section.
How are FakeAVs and scareware related to ransomware?
FakeAVs and scareware do not blackmail the victim, but certainly they create fear in the victim. There are a lot of warning messages on the system and since the victim is not able to use his system, he feels the need to pay for the fake antivirus in order to rescue himself.
