We saw in Chapter 6, Case Studies of Famous Ransomware that the Petya ransomware uses bootkit. Windows has introduced Unified Extensible Firmware Interface (UEFI) safe booting to protect against bootkit infection in Windows 8 onward.
We talked about the boot process of an older version of Windows in Chapter 5, Ransomware Techniques of Hijacking the System. Now we will talk about the feature introduced in Windows 8 and later versions. According to Microsoft, the Secure Boot or UEFI booting process is as follows:
- After the PC is turned on, the signature databases are each checked against the platform key.
- If the firmware is not trusted, the UEFI firmware must initiate OEM-specific recovery to restore the trusted firmware.
- If there is a problem with Windows Boot Manager, the firmware will attempt to boot a backup copy of Windows Boot Manager. If this also fails, the firmware must initiate OEM-specific remediation.
- After Windows Boot Manager has started running, if there is a problem with the drivers or NTOS kernel, Windows Recovery Environment (Windows RE) is loaded so that these drivers or the kernel image can be recovered.
- Windows loads anti-malware software.
- Windows loads other kernel drivers and initializes the user mode processes:

Prevention measures in Windows are not limited to antivirus, anti-exploit, and safe-boot. There are a few other important features that can be useful in prevention.
User Account Control (UAC) is one such feature that has a warning pop-up box that spawns up when a new program tries to launch itself. You can find the setting for UAC on Windows 7 by going to Control Panel | System and Security | Action Center | Change user control setting:
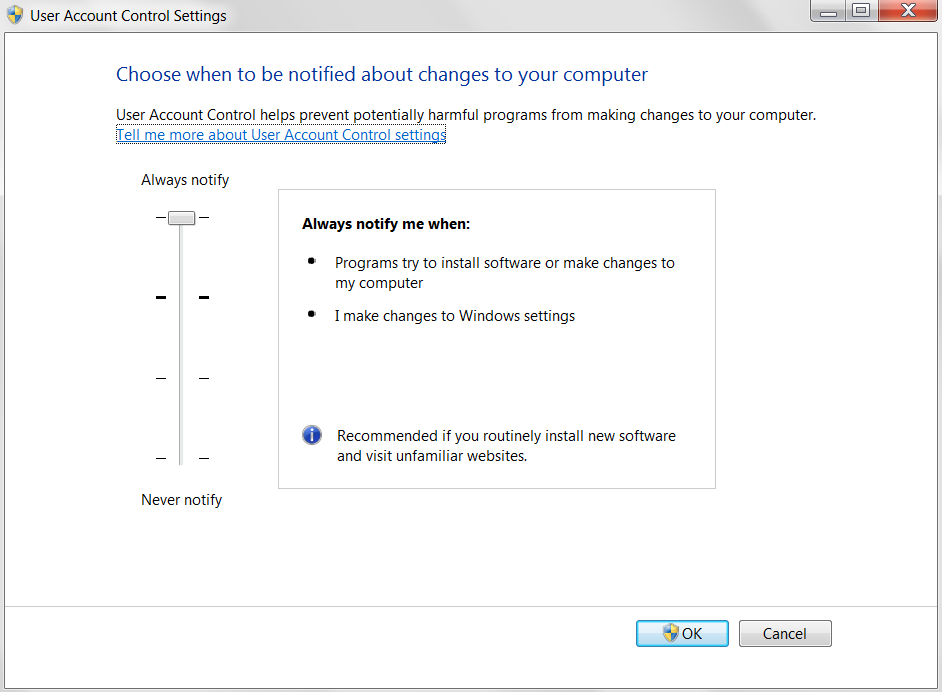
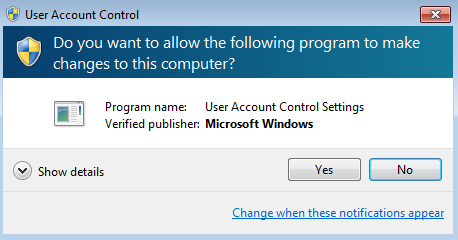
In the UAC setting, when it is set to Always notify, we always get a popup similar to one shown in the following screenshot whenever a program tries to launch. Although this may be bit irritating sometimes, it's a useful preventive feature:
There are features in an operating system that are meant to facilitate users. Unfortunately, malware often misuses these features. We have seen that if a CD or pen drive is inserted, Windows automatically shows us the contents. We call this feature AutoRun or AutoPlay and malware uses this feature to spread to other computers. We have talked about this in Chapter 1, Malware for Fun and Profit.
As a preventive measure, we would recommend you to disable this. Here is how one can disable it. Type in gpedit.msc and you will get the gpedit Window (group policy editor). You can browse through Administrative Templates | Windows Components | Autoplay Policies:

Windows also comes with a default firewall where you can restrict applications on the computer. You can get the firewall settings by simply typing in firewall in the search bar of Windows 7, then go to Windows Firewall with Advanced Security:

The preceding screenshot shows the Windows firewall, which displays various programs running on the system and their network connection, which includes remote IP address, remote port, local IP address, local port, and network protocol. If the administrator finds that some program is not supported to be run on the machine, they can disable it. Malware programs can create a backdoor which is a local open port. Administrators can disable it.
