Firewalls are one of the oldest concepts in the security world. Firewalls are network components that monitor and control both incoming and outgoing traffic. As the name suggests, they act as a barrier between the internal, trusted network they protect and the external, untrusted network. Firewalls can range from packet filtering operating on layer 3 firewalls to app ID firewalls operating on top of layer 7. Layer 3 and layer 7 refer to the layers in an OSI networking model.
Firewalls can be categorized based on where they are deployed. For example, web app firewalls such as modsec, which protects web servers, are deployed in the server. Network firewalls are deployed at the network perimeter or gateway. pfSense is an example of an open source network firewall. A firewall that is deployed on a desktop or host machine is called a host-based firewall. We referred to the Windows firewall in the previous section, which is a host-based firewall since it is available on the Windows desktop.
We will talk a bit about network firewalls in this section. Based on the functionality and granularity of traffic analysis, firewalls have evolved and can be categorized into packet filtering firewalls and stateful firewalls. In networking, we cannot transfer all of the data in a single shot. When we see a video, we don't receive all the data related to the video instantly. Instead, it is transferred to us in various installments of smaller network packets. Packet filtering firewalls were the first-generation firewalls and are considered to be non-stateful. Stateful firewalls are those which can relate the packets that belong to the same transaction or, as an example, a stateful firewall can identify all the packets that relate to the same video. So if an attacker sends data by splitting the data into multiple packets, a non-stateful or packet filtering firewall cannot identify the attack. The filtering decision in a packet filtering firewall is based on IP addresses, port numbers of source and destination computers, and the protocol used in a communication. iptables is a packet filtering firewall implemented in Linux. Modern firewalls and other network security products are implemented statefully. All the packets related to a particular transaction are taken into consideration while inspecting:
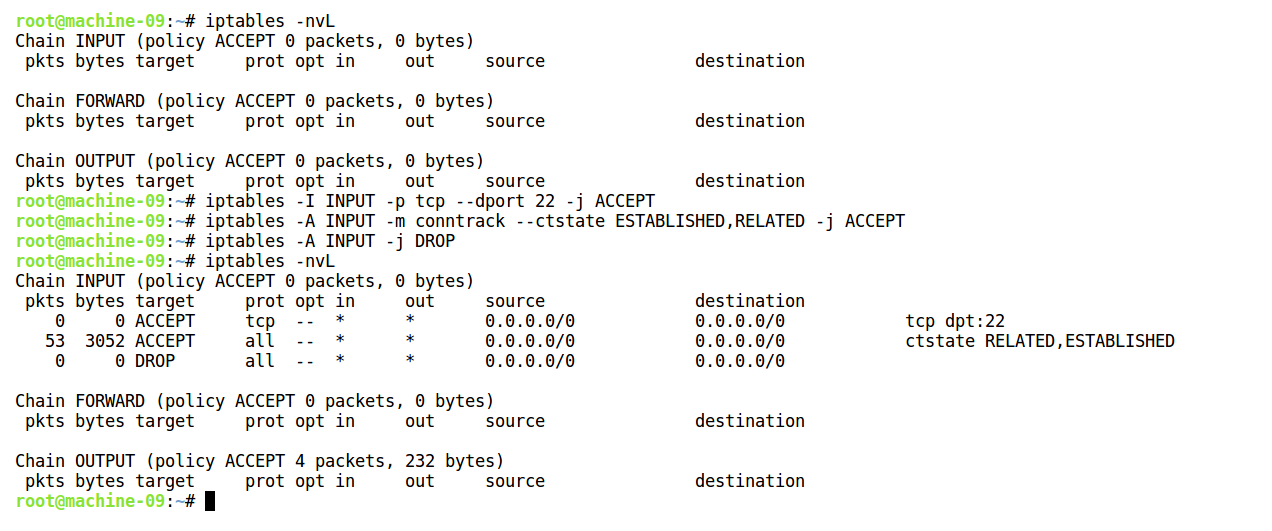
The preceding screenshot shows iptables rules that disallow any new incoming connections to the host machine from the outside network, unless it is an SSH connection. Basically, this allows anyone from outside the network to only connect to the port 22 on the host, which is the SSH server port, but not to any other ports on the host machine.
We have seen in section 3.1 Exploit Kits in Chapter 3, Ransomware Distribution, that attacks can compromise a web application and then host exploit kits on it, which in turn is known to download ransomware. A web application firewall can be a preventive measure in this case if you are hosting your website. A web application firewall can monitor traffic to and from a web application. It can be hosted on the server which hosts your web application or any other place in the network. These days, a web application firewall is also hosted on the cloud and traffic is routed through it. A web application firewall can protect against attacks such as SQL injection and XSS:

There are application layer or layer 7 firewalls, which can understand layer 7 protocols such as HTTP, SMTP, IMAP, SMB, and so on. The most recent generation of firewalls operate on applications that run on top of layer 7 protocols and can be termed application firewalls or app-id firewalls. These firewalls can identify applications such as Facebook or Skype running, or other applications on top of layer 7 protocols such as HTTP and can identify actions within the identified applications. For example, these firewalls can identify actions such as a user posting on Facebook, or uploading documents to cloud services such as Dropbox, and so on.
Firewalls usually comprise various other services combined into one, which includes but is not limited to VPN, SSL termination, NAT, IDS/IPS, URL filtering, AV integration, file analysis, and sandbox integration.
