We explained earlier how malware evades antivirus signatures. We saw that static detection is a drawback for antivirus signatures. On the other hand, it's really tough to implement an antivirus that can capture the behavior of malware on a desktop system as it is really performance intensive. Sandboxes are the latest addition to the infrastructure security that can be used to capture the behavior of a file and then associate the behavior with malware or clean ones. We gave a brief introduction about sandboxes in section 3.5 Armoring in chapter 1, Malware from Fun to Profit. A sandbox is an automated malware analysis system. Cuckoo is one of the famous open source projects (https://cuckoosandbox.org/).
A basic sandbox can produce the following data for a sample provided:
- Static analysis engine
- Behavioral analysis engine
A static engine, as the name suggests, can show the static properties of the file, in case of Windows PE properties. A behavior engine can show data that relates to behavior. Behavior can include API logs, network connection files, and registry changes. We have talked enough about malicious behavior in Chapter 1 and Chapter 2, so we do not need to reiterate it. Here is a basic architecture for a sandbox:

The core components of a sandbox consist of an agent, controller, and a virtual machine. The virtual machine can be any of VMware, virtual box, or qemu. An agent is a piece of code that is placed in inside the virtual machine. The agent receives commands from the controller code that is outside of the virtual machine. A snapshot of the virtual machine is saved, that has all required tools, such as an API logger, file logger, and network logger, needed to analyze a sample. The controller sends the file to be analyzed to the agent. It then instructs the agent to execute the file. If the file is an executable, the agent will run it (we execute an exe by double-clicking it). If the sample is a PDF file, the agent opens the sample with an Adobe reader. After execution of the file, the agent is instructed to collect the log files for the analysis and then send it to the controller. The controller then hands over the behavior analysis code to the rest of the sandbox code. Since the analysis has created changes in the virtual machine, the controller reverts back the virtual machine to the snapshot mentioned earlier. The behavior and static logs are further analyzed to derive whether the sample is clean or malicious.
The following screenshot shows part of the cuckoo log that shows some details about a process such as process ID, process name, and parent process. The cuckoo community has created rules that can be added to cuckoo. These rules can parse cuckoo logs and identify the behavior:
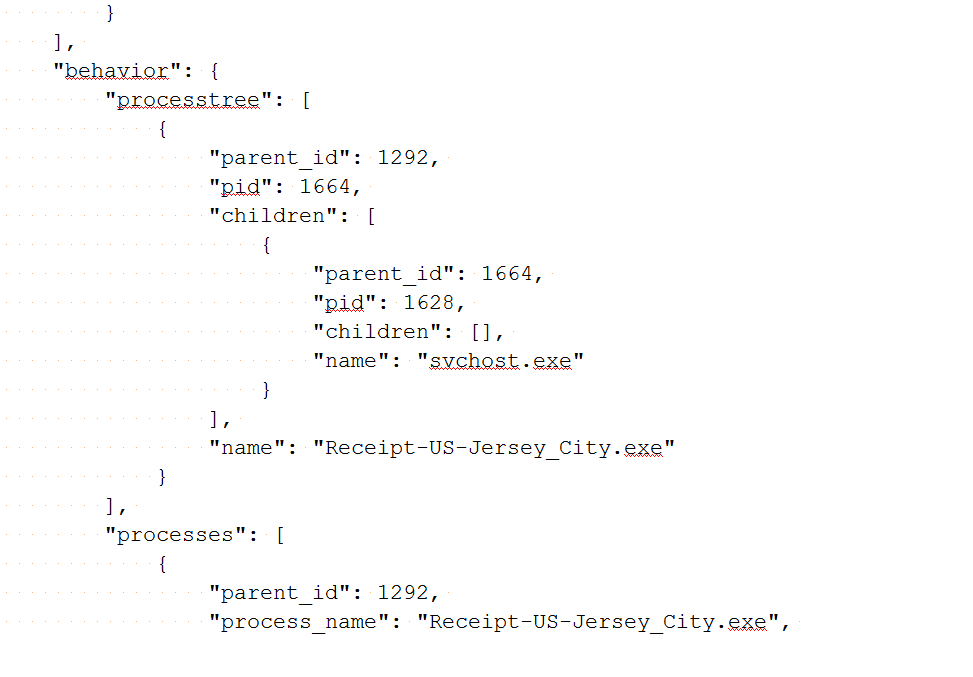
Here is the repository for cuckoo behavior rules: https://github.com/cuckoosandbox/community/tree/master/modules/signatures.
Behavior signatures can be a sequence of APIs, maybe with specific parameters. A crypto-ransomware API log will consist of a lot of file modifications. For crypto-ransomware on Windows, we will see a lot of createfile() and writefile() APIs in the logs. This can be used to identify part of a behavior signature. We have talked a lot about strings present in the virtual memory of malware. Cuckoo has the provision to extract memory from virtual memory. Cuckoo also has a provision to create a YARA signature that can be applied in the extracted memory. Network administrators who have installed cuckoo can create a signature using the strings in memory.
These days, a lot of security vendors ship a sandbox as a part of the security product, which can be hardware that consists of a firewall and an intrusion detection system. The hardware is installed at the gateway and network traffic is intercepted to extract files passing into the network. These files are then analyzed in the sandbox. The sandbox has a demerit for taking too much time to analyze a file. Hence, the sandbox analysis is usually offline. It's not easy to stop an attack using a sandbox. It cannot be considered as a preventive system but can alert the administrator that an attack has happened. The administrator can then take the necessary steps to stop future attacks. The advantage of a sandbox is that the rules can be written on the behavior of a malware. Hence, unknown malware can also be caught if a there is any behavior rule for similar malware. This overcomes the disadvantage of static rules used in antivirus.
The latest version of cuckoo also supports YARA rules and is also capable of extracting virtual memory. We have described the strings present in various ransomware as well as various other types of malware in earlier chapters. You can create YARA rules using those strings and deploy it.
A sandbox should be configured to analyze files getting into the network. In particular, passing email attachments through a sandbox is important. Ransomware such as Locky is known to be downloaded from JavaScript that was sent as email attachments to the victim.
