Cerber is a crypto ransomware that was widespread like Locky, and was considered to be the twin of Locky. Cerber was also known to be talking ransomware, as it used to read aloud the ransomware warning message. It was spread via an email spam campaign, exploit kits, and via Botnet. Cerber was first seen in May 2015, but it was more prevalent in 2017.
Several dridex email spam campaigns spread it across the globe, together with Locky or sometimes alone. The emails contained docx attachments posing as invoices. When the victim attempts to read these attachments, he gets a message that the document has a bad encoding. The victim is tempted to enable Word macros. The macros will decrypt the encoded VBScript embedded in it then execute it. The VBScript further downloads Cerber. Cerber was also known to be downloaded from the Rig and magnitude exploit kits.
A newer version of Cerber evaded security solutions by splitting up its code into smaller chunks of code. These smaller chunks were extracted and read into own process when it executes, without dropping the components into a physical drive. Thus, scanning the drive with an antivirus engine does not give good results. Most importantly, it was a pioneer of Ransomware as a Service (RAAS-explained in Chapter 5, Ransomware Economics), which aimed to a ripe profit of $1 million to $2.5 million. The Ransomware developers were expected to get 40% of the Ransom.
Several versions of Cerber were discovered over time. We have listed some here, along with when they were seen:
- Cerber 1 (May 2015)
- Cerber 2 (Aug 2016)
- Cerber 3 (Sep 2016)
- Cerber 4.0 (Oct 2016)
- Cerber 4.1.0 (Nov 2016)
- Cerber 5.0 (Nov 2016)
- Cerber 5.1.0 (Nov 2016)
- Cerber 6.0 (March 2017)
Initial variants of Cerber encrypted files and added extensions such as .cerber, .cerber2 and .cerber3, whereas the rest of them started to display on the desktop wallpaper itself.
Some versions of Cerber had a configuration file in it or downloaded it. The configuration file is in JSON format. The configuration file provides the facility to update itself easily. Just downloading the configuration file extends the functionality of Cerber. The malware refers to the configuration file while executing its activities. The configuration file states what encryption should be used to encrypt the files, which file extensions to encrypt, which processes should be shut down, and so on.

The Cerber configuration file has following components:
- blacklist: Tells Cerber what not to be - which folder files not to encrypt and which countries should be infected
- close_process: Tells Cerber which processes should be shut down
- encrypt - keys: Used in the file encryption process
- help_files: Tells about files with a ransom note
- self_deleting: Tells whether malware has to delete itself
- servers: It has a list of C&C servers
- wallpaper: The desktop wallpaper to be set by the malware post infection
- whitelist: List of file extensions that need to be encrypted
Here is a part of the Cerber configuration file, which shows the blacklist. Cerber should not infect computers in countries shown in the list. Also, it shows what files it should not infect:

Cerber used RC4 and RSA 2048-bit encryption algorithm to encrypt files; however, the RSA key length was 880 for this variant. One of the variants was also known to skip the initial 512 bytes of the target file (the file it is going to encrypt on victim machine) and encrypt the rest of the file. Cerber is also known to encrypt database files. To do so, it will shut down all processes related to the database. Here is a list of database-related processes present in the configuration file that would be shut down by cerber before encrypting the database files:

Cerber can encrypt document files, such as those with the extensions pdf, doc, and docx . Also, as mentioned earlier, it encrypts database files. Here is a list of database files. The list is very long and we discovered this by debugging a Cerber version. This list is also present in the configuration file:
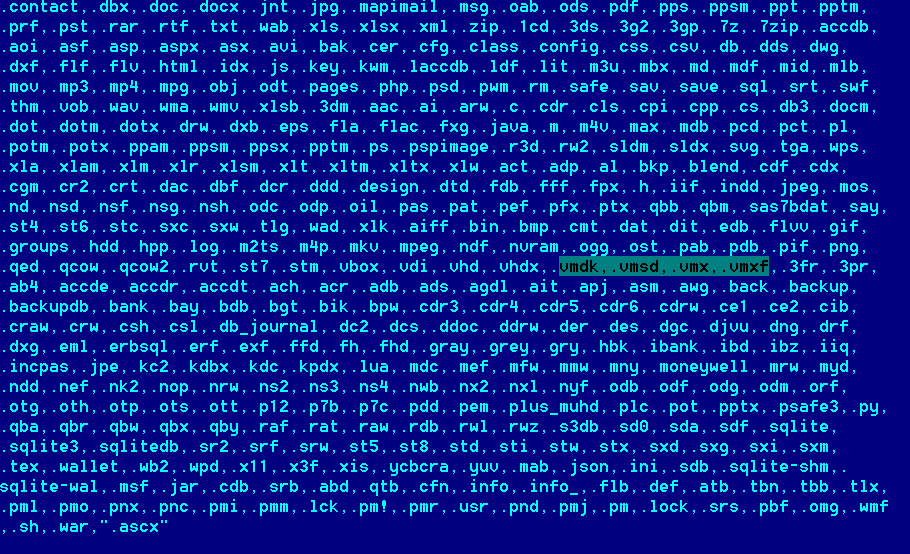
Cerber has a long list of file extension that it encrypts. It includes source code of C files (cpp), Python(.py), Java, files related to virtual machines (.vmx, .vmdk), and so on.
Encryption was irrevocable unless you paid a ransom and got a private key with the decryptor. Cerber leaves behind files with ransom notes in the directories that it encrypts. Here are the names of the ransom note files:
- # DECRYPT MY FILES #.html
- # DECRYPT MY FILES #.TXT
- # DECRYPT MY FILES #.vbs
The HTML, when opened in a browser, looks like the following screenshot:

Cerber also replaces the desktop wallpaper with a ransom message:

A Cerber unpacked file or memory may have these strings:
- .cerber
- DECRYPT MY FILES.html
- DECRYPT MY FILES.vbs
You can use these strings to create rules for malware detection.
