What kinds of behavior can we expect from ransomware?
- Ransomware that is meant to encrypt files on a machine is expected to show the following behavior:
- File modification: you can see a lot of file modifications related to a lot of file extensions.
- Registry changes: This can be similar to other malware.
- Network communication: Ransomware tries to connect to its C&C server. It can send information about the victim to the hacker who has control of the C&C server. Sometimes, ransomware also fetches keys from the server in order to encrypt files on the victim machine. We will explain this in Chapter 4, Ransomware techniques of hijacking the system. Most of the time, this communication is encrypted and cannot be understood easily without deeply analyzing the malware.
- Process memory:
- One can see the ransom messages in the ransomware memory. We usually call these messages, ransom notes.
- Often you can see the list of file extensions the ransomware is going to encrypt.
- We can also see commands used by ransomware.
- Ransomware sometimes changes the extensions of files to its own extension. Locky Ransomware changes the extension of encrypted files to .locky:
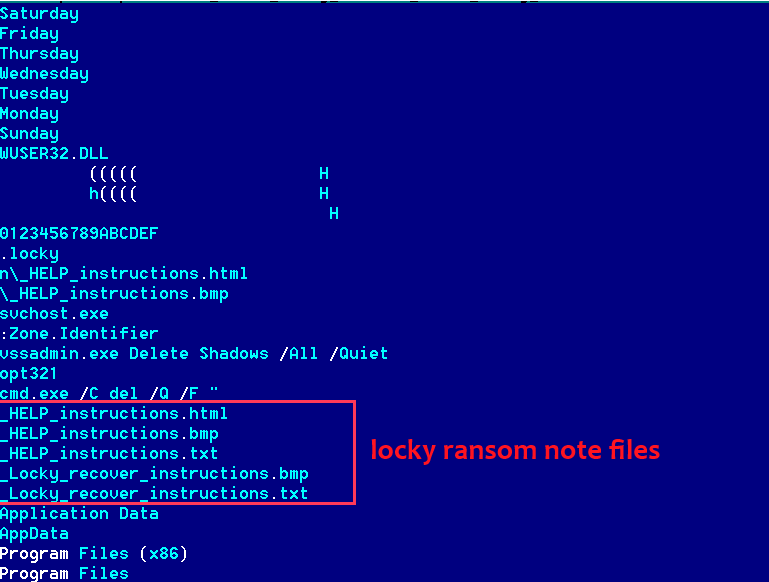
Locky ransomware memory
In Locky ransomware memory, you can see .locky, which is enough to identify the malware as Locky. You can also see _HELP_instructions.html, _HELP_instructions.bmp", and _HELP_instructions.bmp strings in the screenshots. These are files created by Locky on the victim machine. These files contain ransom notes that contain ransom messages and talk about how the victim should pay the ransom.
