No secret agent device worth its name would be complete without a self-destruct mechanism. While we can't quite make the Pi disappear in a puff of smoke, we can rig a sneaky booby trap that will eliminate all traces of our secret agent setup if the Pi were to get caught behind enemy lines.
First we are going to encrypt our entire home directory. Since we've been doing all of our pranks and projects inside the pi user's home directory, if someone were to read the SD card on another computer, they wouldn't be able to get any valuable data from the card except for a pretty standard Raspbian installation.
Then we'll add an optional wipe trigger-mechanism, which can be initiated either locally from a USB keyboard, or remotely via SSH, that will erase our encrypted home directory and replace it with an empty, innocent-looking, and original home directory.
eCryptfs is a stacked cryptographic file system. Unlike the cryptsetup/LUKS encryption system that we saw in the previous section, it is layered on top of an existing file system and encrypts/decrypts individual files on the fly (as they are read and written).
Note: For this exercise to work successfully, you need to be logged directly into the Pi's Terminal as the root user and not over a SSH session:
- Let's install the necessary tools:
root@raspberrypi ~ # apt-get install ecryptfs-utils lsof cryptsetup - Next, we need to load the
ecryptfskernel module:root@raspberrypi ~ # modprobe ecryptfs - To help us migrate to an encrypted home directory,
ecryptfsprovides a handy script that will make some initial safety checks and then guide us through the whole process. The script will ensure that no running process is reading or writing files to our home directory. Now we can try running theecryptfshome directory migration script:root@raspberrypi / # ecryptfs-migrate-home -u piIf it finds any files being accessed in
/home/pi,it will print the process that is holding the file open together with its process ID (PID). You'll have to shut down the offending application nicely, or kill it using thekill [pid]command. - With the initial checks out of the way, the migration script will now ask for your login passphrase. This is your regular login password for the
piuser.The script will now rename your current home directory, create an encrypted home directory, and copy all the contents back, encrypting everything as it goes.
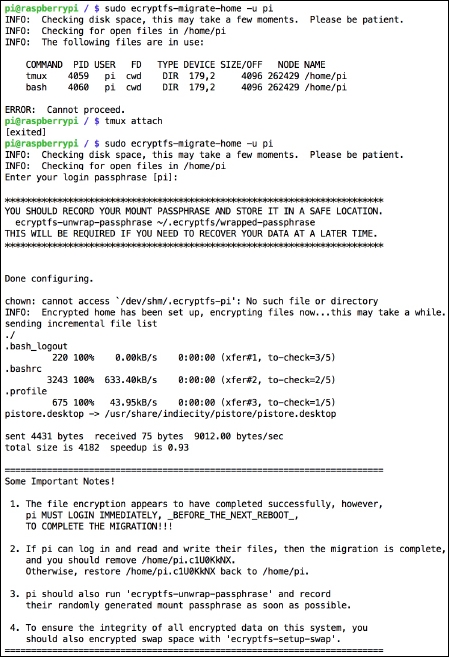 Migration to encrypted home directory with eCryptfs
Migration to encrypted home directory with eCryptfsOnce the migration script has finished, we're going to follow the advice it gave us very closely.
- Log out now and log back in as the
piuser. You'll notice that the time it takes to log in has increased dramatically because of the automaticecryptfsmounting that's going on in the background. - Once you're logged in, type
lsto verify that your home directory looks roughly intact. Then typemountto verify that anecryptfsfile system is really mounted over/home/pi, like in the following screenshot: Encrypted file system mounted on top of home directory
Encrypted file system mounted on top of home directory - If everything seems fine, you should now delete the unencrypted backup copy of your home directory that the migration script made previously. The name of this directory was randomly generated and is called
/home/pi.[XXXXXXXX]. Typels /hometo find the name of yours, then issue the following command:pi@raspberrypi ~ $ sudo rm -rf /home/pi.[XXXXXXXX] - (Optional) Type the following command to reveal your recovery mount password:
pi@raspberrypi ~ $ ecryptfs-unwrap-passphraseThis randomly generated passphrase can be used to recover your data from another computer.
- Finally, we're going to encrypt the swap file on our system. A swap file/partition is a reserved area on the SD card that can be used by the kernel to move data in and out of memory. On Raspbian, this 100Mb file is called
/var/swapand is very rarely used. But just to make absolutely sure our encrypted home directory data doesn't leak into the swap file, we can run the following command:pi@raspberrypi ~ $ sudo ecryptfs-setup-swap
Even though your home directory is much more secure now that it's encrypted, there are still situations where one might want to abort a mission and pull the plug on the important data. For instance, let's say you're continuously recording inside a tmux session; your data remains mounted and unencrypted until the pi user logs out.
We will construct a booby trap hooked into the Raspbian login system. There will be two versions of the trigger mechanism:
- A special login name of your choice is used as a trigger word. As soon as you try to log in as this user, directly on the console with a keyboard or remotely over SSH, the encrypted
pihome directory is wiped clean and recreated. - A certain number of failed login attempts as the
piuser will be used as a trigger signal to wipe the encrypted home directory and recreate it.
The beauty of having both versions is that the special login name can be triggered by you from a distance, and the failed login attempt could be triggered by a foe trying to gain access to the Pi.
- The Raspbian login system uses Pluggable Authentication Module (PAM) to authenticate users. That's where we need to put our hook for the booby trap. Open up the common authentication configuration file for editing with the following command:
pi@raspberrypi ~ $ sudo nano /etc/pam.d/common-auth - Find the line that contains success=1 and change it to success=2.
This directive specifies how many rules to skip if the user login is successful. We change it to
2because we're going to add a new rule next.Create a new line under the one we just changed and put the following:
auth optional pam_exec.so /home/slatfatf.sh
This rule means that when a user login fails, a script that we'll write, called
/home/slatfatf.sh, will be run. You're free to name the script whatever you want and place it in any location (except thepihome directory). - Now create another new line at the bottom of the file and put the following:
auth optional pam_exec.so /bin/rm -f /home/slatfatf.count
This rule will reset the bad login counter whenever
pilogs in successfully: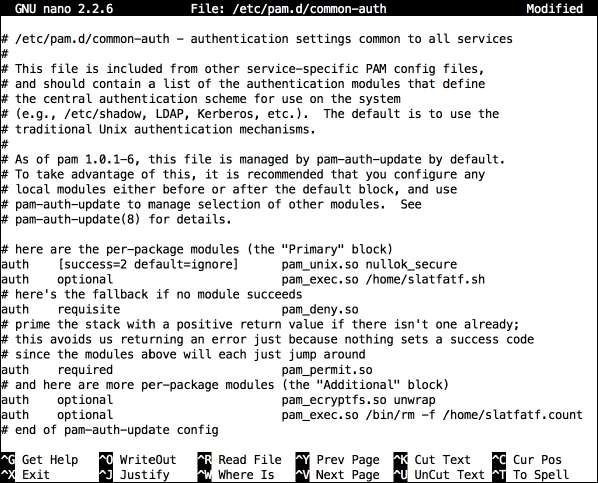 PAM configuration altered to execute custom script on failure
PAM configuration altered to execute custom script on failure - Now all we need is the script to run on login failures. Open it up for editing:
pi@raspberrypi ~ $ sudo nano /home/slatfatf.sh #!/bin/bash TRIGGER_USER="phoenix" MAXFAIL=3 COUNTFILE=/home/slatfatf.count self_destruct() { pkill -KILL -u pi umount /home/pi rm -rf /home/pi mkhomedir_helper pi rm -rf /home/.ecryptfs rm -f $COUNTFILE # rm -f /home/slatfatf.sh } if [ $PAM_USER == $TRIGGER_USER ]; then # self_destruct exit fi if [ $PAM_USER == "pi" ]; then if [ -f $COUNTFILE ]; then FAILCOUNT=$(cat $COUNTFILE) ((FAILCOUNT++)) if [ $FAILCOUNT -ge $MAXFAIL ]; then # self_destruct exit else echo $FAILCOUNT > $COUNTFILE fi else echo "1" > $COUNTFILE fi fi- The
TRIGGER_USERvariable holds the username that will trigger an immediate wipe of the home directory. Note that this should not be a real user account on the system. - The
MAXFAILvariable sets the number of failed login attempts in a row by thepiuser that triggers a wipe of the home directory. - The
COUNTFILEvariable holds the path to a text file that will be used to keep track of the number of failed login attempts by thepiuser. - The
self_destructfunction is where all the action is. It deletes and recreates thepiuser's home directory and erases a few traces of eCryptfs. - The
PAM_USERvariable is passed to our script from thepam_exec.somodule that started our script. It contains the name that was entered at the login prompt and failed to authenticate. - If the user that failed to log in was our
TRIGGER_USER, then start theself_destructsequence. - If the user that failed to log in was
pi, see whether the number inFAILCOUNTis greater, or equal toMAXFAILand if so, start theself_destructsequence.
- The
- The last step is to make the script executable with the following command:
pi@raspberrypi ~ $ sudo chmod +x /home/slatfatf.shTo verify that your trigger mechanism is set up correctly, you can make a failed login attempt with the
piuser to see that the /home/slatfatf.countfile is created.
