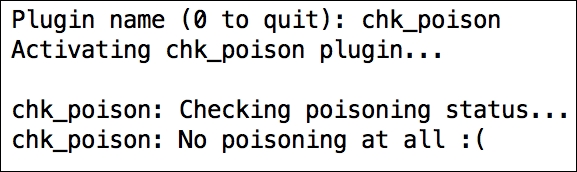
By now you might be wondering if there's a way to protect your network against the ARP poisoning attacks we've seen in this chapter.
The most common and straightforward defense is to define static ARP entries for important addresses on the network. You could do this on the router, if it has support for static ARP entries, and/or directly, on each machine connected to the network:
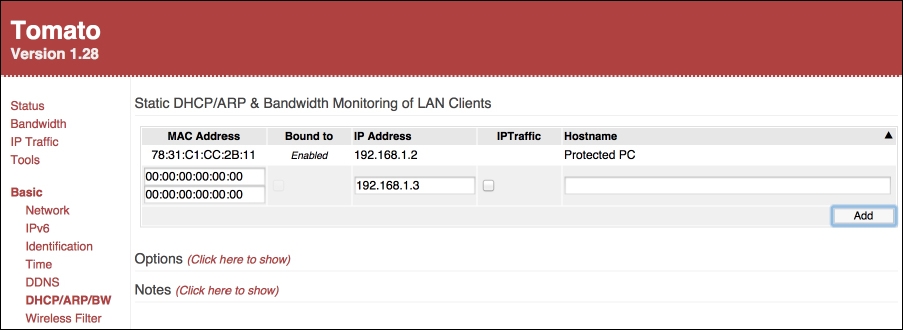
Most operating systems will display the ARP table with the arp -a command.
To turn a dynamic ARP entry for your router into a static entry in Windows, open a Command Prompt as Administrator and type in the following command, but replace [Router IP] and [Router MAC] with the IP and MAC address of your router:
C:> netsh -c "interface ipv4" add neighbors
"Wireless Network Connection" "[Router IP]"
"[Router MAC]"
The Wireless Network Connection argument might need to be adjusted to match the name of your interface. For wired connections, the common name is Local Area Connection.
The equivalent command for Mac OS X or Linux is:
$ sudo arp -s [Router IP] [Router MAC]
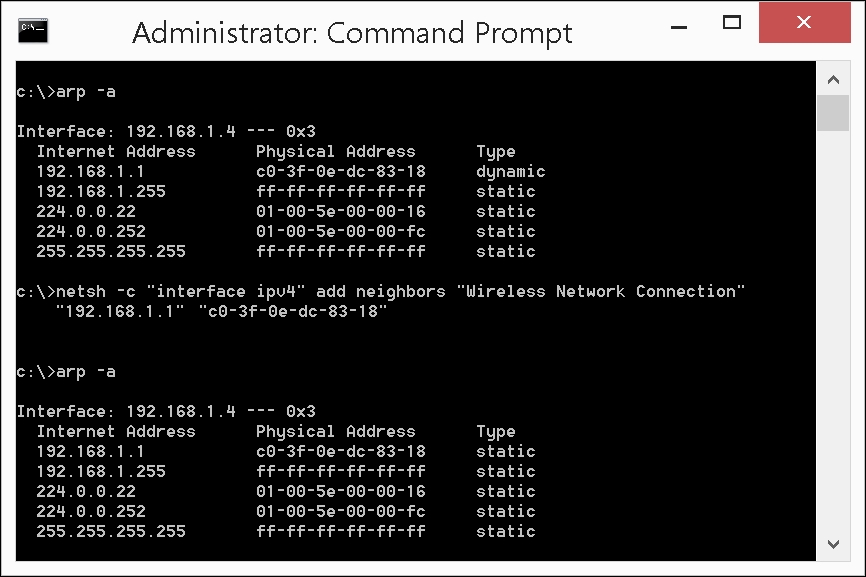
To verify that your static ARP entries mitigate the ARP poisoning attacks, start an Ettercap session and use the chk_poison plugin: