A
Academic Programs
Information provided by Loss Prevention magazine and published with permission:
Eastern Kentucky University, Department of Loss Prevention and Safety, Richmond, KY
Online MS degree in loss prevention and safety
BS degree in assets protection with multiple options
Info: 859-622-1051 or www.eku.edu
Farmingdale State University of New York, Department of Security Systems, Farmingdale, NY
BS degree in security systems, managing security technology
Fox Valley Technical College, Department of Security and Crime Prevention, Appleton, WI
Online associate degree in security and loss prevention
Online certificate for 17 hours in private investigation
Info: 920-735-2410 or www.fvtc.edu/security-crimeprevention
Michigan State University, School of Criminal Justice, East Lansing, MI
Online MS degree in criminal justice with security management specialization
Online graduate level certificate program in security management
Info: 517-355-2228 or www.cj.msu.edu
Northern Michigan University, Department of Criminal Justice, Marquette, MI
Online certificate for 12 hours of loss prevention coursework
Info: 906-227-2660 or www.nmu.edu/cj
St. Cloud State University, Department of Criminal Justice, St. Cloud, MN
BA degree in criminal justice with private security minor
Info: 320-308-5541 or www.stcloudstate.edu
Tri-State University, Department of Criminal Justice, Psychology and Social Sciences, Angola, IN
Associate degree in criminal justice
Satellite locations: Fort Wayne and South Bend, IN
Info: 260-665-4862 or www.tristate.edu
University of California, Department of Criminology, Law and Society, Irvine, CA
Online master of advanced study degree in criminology, law, and society
Info: 949-824-1442 or www.seweb.uci.edu/distance/mas-cls/
University of Detroit Mercy, Department of Criminal Justice and Security Administration, Detroit, MI
MS degree in security administration
Info: 313-993-1051 or www.udmercy.edu
University of Florida, Department of Criminology, Gainesville, FL
MA degree in criminology with loss prevention coursework
BA degree in criminology with loss prevention coursework
Info: 352-392-1025 or www.crim.ufl.edu
Vincennes University, Department of Loss Prevention and Safety, Vincennes, IN
Associate degree in loss prevention and safety
Info: 812-888-6839 or www.vinu.edu
Western Illinois University, Department of Law Enforcement and Justice Administration, Macomb, IL
MA degree in law enforcement and justice administration
BS degree in law enforcement and justice administration
Minors available in security administration and fire administration
Satellite location: Moline, IL
Info: 309-298-1038 or www.wiu.edu
York College of Pennsylvania, Department of Behavioral Sciences, York, PA
BS degree in criminal justice administration with asset protection minor, internship required
Info: 717-849-1600 or www.ycp.edu
Youngstown State University, Department of Criminal Justice, Youngstown, OH
BS degree in criminal justice with loss prevention emphasis
Associate degree in applied science with loss prevention track
Info: 330-941-3279 or http://bchhs.ysu.edu/dcj/dcj.html
Alarm Systems
A burglar alarm system must be a part of any retail security program. A burglar alarm system is not just a tool used to protect the assets of your business, but it is a valuable management tool. An alarm system should not just be used to “catch” a burglar. It should be a system that protects the assets of your facility, which includes the building itself, the property inside, and most importantly your employees. Alarm system technology is designed to report events that are deemed “abnormal” conditions.
A burglar alarm system is a major investment for any business. Therefore, the design, management, and supervision of the system should be a top priority. A burglar alarm system must be under the direct control of a security manager or owner. This will ensure that the system is under the supervision of one or two people who have the responsibility for the records of the alarm system. Documents such as the alarm contract, schedule of protection, passcodes, alarm condition reports, emergency call lists, user’s identification, testing, billing records, and maintenance records should be organized and kept in a secure location.
A. Designing a Burglar Alarm System
The design of a burglar alarm system can be complex, depending on the type of retail business. A small retail business may require only a basic system, while a large department store will require a more complex one. When designing your alarm system, use an alarm company that will assist you with the design of the system as well as provide you with the monitoring, maintenance, and other services that enhance the security features of the system. Alarm company sales representatives must have the knowledge to help you with your system needs. This is particularly important if you are unsure about what products and services are needed. Before choosing an alarm company, obtain multiple proposals and compare them. Do not choose your provider based on the lowest price. Remember, service and reputation of the alarm company are very important considerations. Specify a system with individual addressable alarm “zones” or “points.” This type of system allows for the easy identification of alarms, trouble signals, and maintenance issues that may occur.
There are two types of alarm field transmitting devices: hard-wired and wireless. A hard-wired system uses data cable that is run from the field devices, i.e., contacts and motion detectors to the alarm control panel. A “wireless” system utilizes field devices that transmit signals to a wireless receiver that is located near or at the control panel. Wireless devices are often used in place of hard-wired ones due to physical issues that would prevent hardwiring the devices. Wireless and hard-wired devices can be used in conjunction with each other. Wireless devices can be reliable; however, the size and physical layout of a building may restrict or prohibit signal integrity, and the wireless device may not work. Hard-wired systems should be used so that signal integrity is not compromised.
An alarm system design begins with the protection of the footprint of the building. A review of the perimeter of the building should be done to determine its vulnerability to unlawful or unauthorized access. Parking lot security protection may be your first consideration. If so, exterior beams and motion detectors can be used to protect the perimeter of the building. However, if the parking lot area is open or must be accessed, such as in a shopping center, protection of the parking lot may be impractical. The objective of alarm system protection is to install devices that will provide the earliest possible detection of a burglar or intruder. This is particularly important because even if the intruder is detected and the police are notified, the response time of the police may be limited depending on their proximity to the site. Therefore, when designing the system, you should keep in mind that the loss sustained in a burglary may be reduced if the proper detection and sounding equipment is used.
All perimeter doors should have a magnetic door contact. All windows should have either an infrared motion detector and/or a glassbreak sensor installed. Redundant protection of doors should be considered by using infrared motion detectors to cover the door entrances in addition to door contacts. Multistory buildings present additional security issues. Typically, the second or third floor of a building would not need protection unless the doors and windows are accessible from the outside. If they are, then each door and window area should likewise be protected using door contacts and infrared motion detectors and/or glassbreak sensors. The top floor of a building may have a roof hatch installed. If so, a roof hatch contact should be installed. Buildings that are connected to each other, such as a mall configuration, may require additional roof protection using photoelectric beams.
A warehouse or receiving dock should be treated as a high security area. These areas are used to receive merchandise and to store it after receipt. Infrared motion detectors should be used to protect overhead roll-up doors. Many burglaries are committed by offenders who back up a van to the overhead door and, using the van as a shield, cut holes into the roll-up door and gain entry into the warehouse. Without interior protection, these offenders then load the merchandise into the van and are undetected. Additional infrared motion detectors should be installed at all entry locations within the warehouse.
Cashier offices are also high security areas. Businesses that store large amounts of cash or handle cash in a remote location must utilize an alarm system for protection of money and employees. Safes should have contacts on each door. In addition, a vibration alarm should be used to detect any vibration to the safe. Infrared motion detectors should also be used to cover the safe area for protection after hours. Electronic lock door release controls may be useful in protecting the cash room from unauthorized entry. These systems can be used in conjunction with a doorbell that alerts personnel that entry is requested. Hold-up buttons should be installed in the event of a robbery or duress incident. The installation and use of hold-up buttons must be carefully considered when designing the cashier alarm system. Some security professionals prefer hidden buttons, whereas others prefer exposed ones. In either case, training on the use of these devices is critical. If your cash room is compromised by an intruder while your employee is present, the use of the hold-up button may not be practical or safe to activate. In fact, safety of the employee is a priority, and these devices should not be used until the perpetrator leaves the area.
Computer server rooms are also high security areas. The loss of information to any business can be catastrophic. Protection of these areas must be a priority for any security professional. Server rooms should have a door contact and an infrared motion detector installed. In addition, a high temperature sensor should be installed so that in the event of a room cooling failure, alternative cooling can be provided to keep equipment from overheating.
High value merchandise areas, such as fine jewelry departments, should have additional protection. Safes should be contacted, and additional infrared motion detection should be installed. Hold-up buttons are also an option; however, the use of these devices must be carefully considered.
Other interior areas should be reviewed for vulnerability. If the building is susceptible to a “hide-in” offender, additional motion detection should be installed, particularly if the building has elevators, escalators, or stairwells.
B. Control Panels
The alarm control panel is the “brain” of the system. The control panel houses the electronic components that make the system function. Among those components are the wiring, circuit boards, modules, keypad, telephone dialer, and batteries. The control panel should be placed in a secure area away from the general public. Small businesses often use a telephone or electrical room while larger businesses may use a security office to house the control panel. The control panel acts as a communicator to the Alarm Monitoring Station. Each control panel must have 110 volt electrical power and a dedicated telephone line available for it to function.
Alarm control panels vary in size and features. Alarm control panels are measured by the number of “zones” or “points” that it can accommodate. A “zone” or “point” is defined as one protection device in the system. For example, a door contact is one “zone” or “point” in the system. A basic alarm control panel may consist of six or eight standard zones which can be expanded using zone expansion modules up to a maximum number of zones. Expansion modules are usually in multiples of eight zones. Larger control panels may have eight standard zones and be expandable to 128 or more zones. In addition, the number of available user codes will depend on the size of the control panel. Some control panels can be “partitioned.” A “partition” is a group of zones or points that are “divided” or “partitioned” so that the control panel can have two or more systems within one control panel. For example, the owner of a small business has a warehouse and an office within one building. The office area is staffed from 0800 hours until 1700 hours Monday through Friday. The warehouse is staffed from 0700 hours until 1800 hours Monday through Saturday. The warehouse personnel are not allowed access to the office during nonoffice hours. The office area can be “partitioned” from the warehouse so that the office has its own system, restricting access. Larger control panels have up to eight partitions. Each partition must have its own keypad. The selection of the control panel will depend on the number of zones needed, number of users, and number of partitions. When selecting a control panel, keep in mind any future expansion of your system. If you are contemplating a large system, it is best to purchase a control panel that will accommodate your expansion plans ahead of time.
C. Keypads
Several types of keypads are available. The basic keypad is a numeric keypad, which displays the zone number on the keypad. If you have a small system and can remember the zoning information, this may be the appropriate keypad. However, the alphanumeric keypad provides the zone number and the name of the zone on the face of the keypad display. For example, if the front door is open, the keypad will display “Zone 1 Front Door.” Alphanumeric keypads are recommended because they provide more detailed information. Other keypads have features that include voice response, two-way voice communications from the Alarm Monitoring Station, and web-based information. Keypads are used to arm and disarm the system, program user codes, retrieve alarm information, and program the system (this task is performed by the alarm installer). A keypad should be located as close to the entry point of the building as possible so that arming and disarming of the system is convenient. Each alarm system must have a delay door so that the keypad user can set the system and exit within a certain period of time, usually one minute or less. Similarly, when someone enters the building to disarm the system, the keypad should be located so that the alarm can be disarmed within a certain period of time. Failure to disarm the system within that period can cause an alarm condition and possible police response. Some systems may have up to a 4-minute delay depending on the user’s requirements.
D. Sounders
The use of sounders is recommended for most system applications. Most small businesses utilize an interior siren that activates during an alarm condition. This device can discourage intruders to leave the scene, reducing loss and/or further damage to the premises. One or more of these devices may be needed to adequately cover the size of your facility. Exterior sirens, bells, and strobe lights are also utilized as notification devices.
E. Telephone Line Security
All alarm signals are transmitted over telephone lines. The security of the telephone lines inside a building is very important. If your telephone lines are exposed and can be cut or vandalized, then a secondary transmission system should be installed for your alarm system. Cellular radio transmitters are used for this purpose. These devices take over the transmission of alarm signals if telephone lines are cut or the line fails. An additional monthly charge is assessed for this service. Cellular signal strength is important in this type of application. Your alarm company representative can determine if there is sufficient cellular coverage to accommodate this feature.
F. Alarm Company Services
Alarm companies provide services associated with any alarm system. Monitoring of the system is a basic service, and is either provided at the company’s own central monitoring station or is serviced by a major alarm monitoring company. Those companies that do not have their own central monitoring station are “dealers” for the monitoring company and therefore contract the service to the company that has a central monitoring station. Large alarm companies may have one or more central monitoring stations. It is not uncommon for the central monitoring station to be thousands of miles away from the site that is being monitored.
Monitoring of the alarm system means that in the event of an “abnormal” condition, such as alarm activation, the alarm company will then act upon the condition based on your instructions. This may mean that the police are called immediately upon receipt of the alarm, or the subscriber is called first before the police are notified. In any event, alarm companies will relinquish their responsibility of notification once the subscriber is contacted. It is important to remember that anyone who is designated to receive alarm notification from the alarm company be properly trained on how to handle such calls. Many times these calls are made in the middle of the night, and when a call is received, the recipient is not prepared to deal with the alarm incident. Therefore, upon receipt of the call from the alarm company, the recipient should ask the alarm operator several questions:
• What zone(s) or point(s) were activated?
• How many alarm signals were received, and are they the same zone or point?
• Have the police been notified, and if so, when will they arrive at the premises?
Asking these questions will give the subscriber, the alarm company, and the police a clearer understanding of what may have or is occurring at the time of the alarm. The recipient should advise the alarm operator whether he or she intends to respond to the premises. It should be a standard procedure that each alarm be responded to and investigated no matter what time of day or night. The operator should then advise the police accordingly. At no time should a subscriber who responds to an alarm enter the premises with the presence of the police.
In addition to monitoring services, there are system supervision services that are offered by alarm companies. These services enhance the security features of the system and should be included in the monitoring services. Opening and closing reports by user number are tools the alarm system administrator can review to determine the exact times that the system is turned on and off and who operates the system. Supervised openings and closings are used to notify the subscriber in the event that the premises are not opened or closed within a specified period of the scheduled time. Supervised openings and closings are highly recommended in order to adequately ensure that the premise alarm system is turned on and off daily. These services may also be available “online,” along with administrative features which allow subscribers to change their emergency list electronically.
Maintenance, or an extended warranty, is another service that can be provided by the alarm company. Most alarm companies guarantee the installation of a new system for a 1-year period. At the end of 1 year, in the event of a part failure, the subscriber can either pay for a service call or, if he or she has a maintenance warranty, the service call and parts replacement are provided free of charge. Alarm companies charge a percentage of the installation of the system as an extended warranty fee and calculate the charge at a monthly rate. The decision whether to purchase a maintenance agreement is purely financial and should be discussed in detail with your alarm company representative.
G. The Proposal
Once you have designed your system with the alarm company representative, a proposal is then prepared and presented to the decision maker. A proposal from the alarm company should include a brief history of the alarm company, the location of the closest field office and its corporate headquarters, the location of its central monitoring station(s), a schedule of protection or list of components for the system, the services provided, any system exclusions or items that you must provide, a complete scope of work to be done, total cost of the system (parts and labor), and the cost of the monthly services provided. Some alarm companies provide rental or lease terms in addition to the outright purchase of the system. Third-party leasing companies also provide an alternative financing choice.
H. The Contract
One of the most misunderstood aspects of any alarm transaction is the monitoring contract, or commercial service agreement. Every alarm company requires that a contract for the installation and the services be signed by the subscriber. Alarm companies do this for a very good reason: to limit their liability. Most alarm companies use the same format for their contracts. Variations in contract terms may be the length of the contract, direct sale or rental/leasing of the system, and the services that are provided. The most important point to remember is that a contract is binding between the parties and it is a legal document. Before a contract is signed, it should be carefully reviewed for its content. Some companies have their legal department review the contract and may add or strike clauses to it. Contracts have a beginning and ending date with a specific procedure on how the services are canceled. Companies that cancel agreements prior to their expiration dates may be subject to paying the balance of the contract’s term. Companies that are dissatisfied with their alarm provider will often cancel the agreement without considering the financial impact of such a decision. It also may mean that the equipment can be removed from the premises (if owned by the alarm company), creating an additional expense. The importance of knowing the contract terms and conditions cannot be overstated. Make sure that you understand each and every clause in the contract before signing it.
I. It Is Now Your System
After all the decisions concerning the design of your burglar alarm system have been made, you have signed the contract, and the system is installed, what happens next? The most challenging part of your job will be managing the alarm system. As previously stated, the alarm system must be supervised and managed by one or two responsible people. This may be a security manager and his or her staff, or the business owner. The most important parts of managing the alarm system are good record keeping and regular testing of the system. Record keeping can be very simple. A very good method of record keeping is the use of a binder. Sections should be divided to include the following:
• The name, address, and telephone number of your alarm company.
• The name of your account manager or sales representative.
• Your account number and system number.
• An inventory list of each alarm component including the type of alarm control panel, keypad, “zone” or “point” number, and location of each component.
• A list of each alarm user number, name of user, and passcode. The master code and password should also be listed.
• A current emergency notification list.
• A record of each time that the alarm was tested.
• A record of each alarm condition or abnormal alarm activation.
The second most important component of managing your alarm system is testing. Testing of the alarm system is absolutely necessary and is your responsibility. Many times subscribers have a break-in and complain that the system did not activate. In most situations, the system components fail because regular testing of the system never occurred, and therefore, the component that failed did so because no one knew that it did not function. Testing should be done on a monthly basis. The best method for testing the system is to call your monitoring station and advise it that you are going to arm the system and test each component. The test begins by turning on the alarm system. Using your alarm inventory list as a guide, open every door, walk-test every motion detector, and activate each hold-up button. Each device should activate and send a signal to the monitoring station. At the conclusion of your test, turn off the alarm system and call the monitoring station to notify the end of the test. Ask the monitoring station to fax you a list of those signals that it received and compare it with those on your alarm inventory. Any discrepancies should be noted and, if necessary, a service call to the alarm company should be initiated.
J. False Alarms
The term “false alarm” is used to describe the activation of an alarm system in which the cause of the alarm cannot be determined or a user error has occurred. An alarm system will activate whenever there is an actual intrusion, the system malfunctions due to a device failure or other catastrophic event, or the user of the system activates the alarm in error. In any case, law enforcement agencies are dispatched to the site and, in the majority of cases, discover that the cause of the alarm cannot be determined. Thus the term “false alarm” is used. False or unfounded alarms are so commonplace that many cities throughout the United States are enacting “Alarm Ordinances” which outline how cities will govern the use of alarm systems. These ordinances may require the payment of fees for an alarm use permit, require a copy of the emergency call list, and list the number of times that the police will respond to a “false” alarm before a fine is assessed to the subscriber. The more false alarms that occur, the higher the fines become. In some cities, the police will not respond to alarms after a certain number of false alarms have occurred. The city may cite the subscriber and require that they appear at a hearing to explain the reasons why the alarms occurred and what steps are being taken to reduce or eliminate the problem. Your alarm company representative should be familiar with which cities have alarm ordinances. You should ensure that you check with your city to verify the requirements that they have before the alarm system is installed.
Some law enforcement agencies have enacted a policy that the police will not respond to any alarm unless actual verification can be made. This can be done by the subscriber responding to the site, which is risky, having a security patrol service respond to the site, which can cause delays and is often a very expensive service, or utilize a closed circuit television system that is integrated with the burglar alarm system so that in the event of an alarm, the monitoring station can “look in” to the site using the camera system and verify whether a burglary has occurred. This service is commonly referred to as “remotely monitored video,” and alarm companies charge an additional monitoring fee for this service. Adding a closed circuit television camera system to work in conjunction with the alarm system can add several thousand dollars to the security investment; however, the decision to make this investment may prove valuable in terms of reducing losses to the assets of the business.
As we have previously stated, an alarm system consists of electronic devices that are activated by people. This means that you are responsible for the training, testing, and maintenance of your system. You must ensure that all persons who will operate the system have a complete understanding of the system and its functions, not just how to turn the system on and off. All alarms must be investigated as to the cause of the alarm. Any alarm that is determined to be caused by equipment failure must be corrected. Remember, there is a dual responsibility for the proper operation of your alarm system. The first responsibility is yours, and second is the alarm company’s. Your diligence and supervision will make your investment in an alarm system a positive one.
Amateur Shoplifters
“Amateur shoplifters” represent one of the two major classifications of persons who engage in shoplifting. Professionals represent the other classification. So-called amateurs by far constitute the greater number of individuals who steal goods from retailers because they comprise the whole range or mix of our society in terms of age, occupation, education, social status, and character. Although these “amateurs” engage in criminal conduct, i.e., larceny, they are not “criminals.” They more often than not represent a true and abiding dilemma for our American judicial system.
As Shoplifters Alternative reports, amateur shoplifters fall into two categories: casual and habitual. The casual shoplifter constitutes a large percentage of people who steal a little, while the habitual offender represents a small percentage of people who steal a lot. Their calculations indicate the habitual offenders are responsible for over 90% of the nonprofessional shoplifting losses and approximately 85% of total shoplifting losses.(1)
If those calculations are anywhere near accurate, it tells us the vast bulk of the problem of shoplifting is theft committed by the average, ordinary, otherwise law-abiding citizen. Who are these citizens? These amateurs may be subclassified into four groups, as follows:
Rather than stealing for profit (income), they are more compulsive and seize on what they see as the opportune moment to take without being seen or caught. They don’t operate with a specific plan or goal. They typically rationalize their behavior to justify their actions, and such rationalization includes
• The store makes too much profit.
• The store will never miss it.
• The store has no identity; hence, no one is hurt by the little loss.
• The store deserves it because of poor service or past bad experiences with the store.
The primary difference between the amateur and professional, other than the activity is not a source of income, is motivation. Amateurs steal for a variety of reasons, but the four most common reasons include
2. To keep and use/wear the item
3. To bow to peer pressure, seeking acceptance
4. And perhaps most importantly, to reward oneself and make oneself “feel good” (to compensate oneself when surrounded by circumstances which have negative influence on one’s life which makes the person feel depressed or unhappy).
The earlier referred-to “dilemma” faced by the courts when confronted by one of these amateurs? What is the court to do with the lady whose son is the local high school football coach and her husband is the president of the Rotary Club? Or a lady who has no criminal record, who’s known in the community as a leader in charitable fund-raising drives, and is a hospital volunteer. And such persons as this lady represent not only the bulk of shoplifters, but they are the ones easiest to catch in the act of shoplifting and hence they are the “face” of shoplifting. The habitual thief and the professional are less likely to be detected, and their true character is obscured behind the image represented by the casual amateur. So the crime of larceny, shoplifting, tends to be viewed as more of a tort, a civil wrong, than a criminal act.
Two relatively effective programs are available today to deal with these amateurs. One is commonly referred to as Civil Recovery or Civil Demand, a legal process whereby the shoplifter is “fined” by the store for his or her theft conduct. The store sends a demand for a given sum, such as $200 to offset store expenses to deal with shoplifters, and the customer can satisfy such demand and the matter is closed. Failure to satisfy the demand may result in civil filing in lower courts, such as Small Claims courts.
The other viable program for amateurs is a diversion program in which the shoplifter must attend state controlled “classes,” similar to driver’s schools for those who are cited by the police for vehicle code violations.
Asphyxia
The dictionary defines “asphyxia” as unconsciousness or death caused by lack of oxygen. You might reasonably ask, “What has asphyxia got to do with retail crime?” The answer is the increasing number of civil suits filed against retailers alleging that a customer’s death was caused by asphyxia at the hands of loss prevention (LP) personnel. Such cases usually narrow the cause of action to wrongful death by “positional asphyxia.”
The subject of positional asphyxia (originally called “hogtying” or “hobbling”) first gained prominence in the late 1990s when suits against police departments for wrongful death from hogtying led to restraints or prohibitions against the practice.
Investigations into positional asphyxia incidents disclosed the typical scenario:
• The suspect is restrained in a face down position, and breathing may become labored.
• Weight is applied to the suspect’s back; the more weight, the more the degree of compression and difficulty breathing.
• The suspect’s natural reaction to difficulty in breathing is to struggle more violently in an effort to breathe.
• In reaction to the increased violence, the officer applies more weight, and the potentially deadly cycle is repeated.
Investigation also found certain factors exacerbated the deadly potential for positional asphyxia:
Under what circumstances do retail customers succumb to positional asphyxia? When they are detained for shoplifting and either attempt to escape or struggle to prevent apprehension. In the ensuing attempt by loss prevention to bring them under control, they are forced to the ground and sat upon in an attempt to fully restrain them until the police arrive.
In the typical scenario once the suspect is forced to the ground, loss prevention personnel and perhaps store nonloss prevention personnel, including at times customers whose help is either sought or volunteered, all “pile on” the suspect who is face down while, if handcuffs are available, there are attempts to apply them to the suspect. Your authors support the use of handcuffs, but formal training is required and must be documented in the agent’s file. If handcuffs are not available (in some cases by company policy), the suspect is spread-eagled on the ground, and one or more persons sit on him or her until the police arrive. As noted previously, these actions can lead to a vicious cycle and produce deadly results!
Loss prevention personnel (whether proprietary or contract) should be trained in proper apprehension techniques and the proper use of force. They should be aware of the potentially deadly effects of using techniques such as hogtying or sitting on a suspect who is face down on the ground as a control technique and avoid using them. If the use of handcuffs is not permitted by company policy and if the suspect cannot be controlled without risking positional asphyxia, he or she should be permitted to escape.
The following factors should be kept in mind when dealing with restrained suspects to will minimize the potential for positional asphyxia:
• Refrain from exerting pressure on the back, especially for extended periods. Exert or leverage pressure on the arms, legs, and shoulders as much as possible to control subjects while they are in the prone position.
• Move restrained individuals from the prone position or face-down position as quickly as possible. This is especially true for obese and overweight individuals. Place the subjects on their side or sit them up to allow for easier breathing.
• The LP agent has a serious responsibility to ensure suspects on the ground are breathing without interruption. One way to do that is to keep talking to them, thus evoking a verbal response. Continuously observe the subjects and be certain they appear coherent and able to communicate adequately.
• If suspects claims they cannot breathe, take immediate remedial action by changing their position to an upright one and remove any pressure from their rib cage.
We are aware of a number of concluded cases and at least two current (2006) cases wherein retailers are being sued for wrongful death caused by positional asphyxia. Needless to say, no act of shoplifting should result in the death of the shoplifter at the hands of loss prevention personnel.
Company policy regarding shoplifting apprehensions should be carefully thought out and crafted in a manner which avoids the possibility of either permitting or not affirmatively prohibiting actions which may lead to deadly results.
Auras (Guilt Auras)
There is a belief, especially amongst long-time loss prevention professionals that some agent practitioners can “see” or “sense” a guilt “aura” radiating around someone in the store who is in the process of shoplifting (or employee about to or is engaged in theft). It’s that aura which attracts the attention of the LP agent. Consider this: How does a floor agent pick through hundreds or thousands of customers who shop or appear to shop in the store each day and pick out that one person who ends up stealing? One answer: auras. And consider this: Why do some agents excel in detecting shoplifters while coworkers struggle to make a detention? One answer: The former can sense auras and the latter can’t.
Persons engaged in the crime (or for that matter, any evil deed) often fear their state of guilt is detectable and that makes them uneasy. That uneasiness is what makes them so “goosey” or hyper, and they dump so quickly, hence the “Oh Shit Syndrome.”
It was commonly understood by experienced loss prevention practitioners in retailing that the biggest problem on the floor in catching shoplifters was some innocent customer or sales associate coming on the scene and inadvertently “burning” what surely was going to be, if uninterrupted, a theft followed by an arrest. Eye contact was all that was necessary to spoil a shoplifting act in progress. This was the nemesis of the store detective—good work shattered by innocent eye contact from someone who had no clue the customer was in the process of stealing.
In the 1970s we labeled this the “Oh Shit Syndrome,” i.e., the emotional and personal reaction on the part of a person engaged in an evil deed because of the inevitable sense of guilt (guilt aura) and belief he or she has been detected by virtue of seeing someone looking at him o her. It wasn’t a “scientifically” proven phenomenon, but rather recognition of a predictable reality.
Award Programs
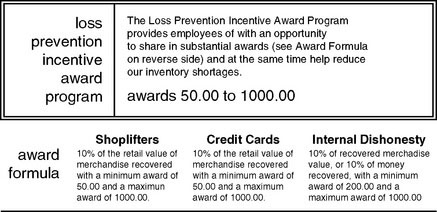
Award programs which reward sales associates with cash rewards for alertness to both external and internal theft can be an effective antitheft tool.
Rewards are normally paid to employees who report customers they believe are attempting to shoplift, provided the customer is subsequently apprehended and stolen merchandise is recovered.
Most such programs provide for minimum and maximum reward dollars, with some programs tying the amount of the reward to the value of the merchandise recovered.
These same programs can reward employees for reporting employee theft and frauds against the company.
Figure A-1 shows a typical incentive award program.
We also suggest that the award be presented in person by the corporate head of loss prevention (LP) or the highest level LP executive available.
In addition to the award itself, we also encourage that a letter along the lines of that shown here be given to the reward recipient.
Company Letterhead Loss Prevention Department
Thank you very much for your alertness and assistance to this department.
Losses to our company are of continuous concern, and it is gratifying that employees such as you are dedicated to protecting the best interests of (Company name).
I am pleased to have you receive this award for your alertness, and a copy of this letter will be forwarded to the Human Resources department for inclusion in your personnel record.
(1) Shoplifting. Managing the Problem. (2006). ASIS International.