C
Cables
The use of clear plastic-coated 1/8- or 3/16-inch steel airplane cable to secure expensive ready-to-wear (RTW) merchandise to fixtures is an effective antitheft technique. The cables are placed through a sleeve, passed over the fixture hanging rod, and have loops at each end which can then be secured together with a small padlock. This arrangement prevents the merchandise from being removed and carried away from the fixture. Merchandise typically secured by this physical control strategy means includes leather jackets and men’s suits.
An alternative to the preceding technique is using cables with one end with a ball-like fitting, which in turn fits into a slot in a lockable box-like receptacle. When this arrangement is used, the ball end of the cable is inserted through the loop and then secured in the lockable receptacle.
A third variation of cable-securing devices is the use of small diameter (1/16 or 3/16 inch) electrical two-conductor cable, which connects into a fixture that completes an electrical circuit when the cable is in place. The cable is affixed to the merchandise in the same manner as the nonelectrical cable. If, however, the cable is cut or otherwise removed from its retaining receptacle, an audible alarm sounds, alerting sales associates to the fact that some merchandise is no longer secured.
Modified forms of both the electrical and nonelectrical cables are frequently used to secure electronic equipment such as laptops, digital cameras, and other expensive electronics.
Case Management and Electronic Incident Reporting
In recent years, we have seen an explosive growth in the area of loss prevention (LP) technology. Retailers are choosing to implement expensive solutions like digital video systems and exception-based reporting software in hopes that these solutions will help investigators to control shrink more effectively.
Recently, loss prevention departments have begun to invest in centralized incident reporting systems. Incident reporting tools can help an organization to collect, process, and analyze incident data in a way that traditional methods cannot offer.
Elements of an Incident Report
Regardless of whether an incident report is completed on paper or electronically in an incident reporting system, it includes several universal elements:
• Who: The report contains information about the principal subject and witnesses. This typically includes contact information and a review of that person’s involvement in the incident.
• What: Details about what happened. Generally, this is in narrative form and is written by the report taker. Often witness statements are included in the incident report.
• When: What date and time the initial incident occurred as well as other major milestones (i.e., interview and court dates).
• Where: Information about where an incident occurred. This would include street address, physical location within a store, etc.
Loss prevention professionals are probably very familiar with writing incident reports for the typical shoplifting and internal theft cases. Almost all reports contain who stole it, what they stole, when they stole it, where they stole it from, and why they stole it.
Interestingly, this same methodology is used by many other departments in the retail organization. For example, the human resources department typically handles reports of violation of company policy. The human resource representative’s report will include who violated the policy, what policy they violated, when they violated the policy, where they violated the policy, and why they violated the policy.
Another example is the risk management department. This department is typically tasked with providing a safe work environment but is also responsible for processing customer and employee accident reports when things go wrong. Who had the accident, what kind of accident occurred, when did the accident occur, where did the accident occur, and why did the accident occur?
Get the idea? Incident reporting systems are not just for loss prevention. The flexibility provided by many solutions allows for the system to be utilized by other parts of the retail organization. Incident reporting systems can help the risk management team to manage accident reports just as easily as it can help the loss prevention group to manage theft investigations.
Benefits of Electronic Incident Reporting
Besides the ability to store incident data for many different groups within the retail organization, an incident reporting system has several other benefits. Most importantly, an incident reporting system has the ability to store the incident data in an electronic format at a central location. This seems obvious, but it actually represents the fundamental difference between centralized incident management and traditional methods of collecting and storing incident data. The data collected by an incident reporting system (database) can be a very powerful tool.
Incident reporting systems can be configured to interact with other business systems, such as
• Internal employee databases: Link to the HR department’s employee master file for enhanced statistical reports.
• Civil collection providers: Transmit theft incidents electronically to the collection agency.
• Background screening providers: Transmit a prospective employee’s (or suspect’s) information to the vendor and order a background check.
• POS exception-based reporting tools: Start an incident from within an exception-based reporting tool.
• Digital CCTV systems: Easily attach video clips to an incident report.
The database can be used to generate statistical reports that can help an organization to gauge various metrics. When combined with other data sources, the data in the incident reporting system can be used to identify trends that otherwise would not be visible.
For example, when linked with data from an HR system, it would be possible to pull a report to analyze the relationship between store shrink, employee turnover, and theft incidents. Another possibility would be to analyze the department in which a suspect was first observed compared to the time of day in shoplifting cases. These types of reports would require significant resources if compiled by hand, but with the use of an electronic incident reporting system, the data are easily accessible.
Pitfalls of Incident Reporting
The benefits of using a centralized incident reporting system can be numerous but require more than just a financial investment in order to be achieved.
The successful implementation of an incident reporting system requires planning, communication, and follow-through. During the implementation process, it is important to maintain partnerships with the departments that will be utilizing the system, the IT department, and the vendor’s technical staff. With communication, the vendor can provide a solution that is tailored to the needs of everyone involved.
After a solution is implemented, it is critical that management support the system. It is important that managers train end users on system operations. No matter how easy the system is to use, end users should be taught the proper way to input, retrieve, and report on incident data.
Finally, it is important that the system be kept up-to-date with changes in corporate policies. Invariably, with time, things change. Make sure that the system is reconfigured as needed to accommodate these changes.
Cash Control: Automated
One much-repeated maxim in the loss prevention community goes something like this: “The more rapidly cash tender is recycled or deposited, the lesser the risk of cashier error and internal shrink.” At the same time, especially with retailers who see a high volume of cash transactions, the labor expenses and bank fees associated with handling cash are consistently on the rise. So how can retailers impose measures to control cashier errors and reduce theft, while stemming the increase of labor expenses and bank fees?
The issue becomes how to build the infrastructure to return the highest efficiency possible for cash management while striking a balance between the use of manpower and affordable technology. Finding the right formula will positively impact any end user retailer’s return on investment (ROI). This business problem led New Albany, Indiana-based FireKing Security Group to develop and bring to market the “PerfectCash” comprehensive cash handling solution suite with both hardware (safe with cash recycler) and software elements, all tied together with IP/LAN-based reporting capabilities (see Figure C-1).
PerfectCash takes cash handling and revenue room activities to the next level of security, efficiency, and automation. According to the company, the PerfectCash solution is “ideal for large retailers, department stores, and mass merchandisers who routinely process tens of thousands of dollars in cash each day.”
The vision behind PerfectCash is to move cash collection and processing functions closer to the point-of-sale, which serves to reduce double handling, errors, and opportunities for employee theft. PerfectCash is an enclosed system (similar but smaller scale than that of a bank or back office casino process), combining the preparation of opening tills, verification/preparation of end-of-day deposits, and general ledger reporting.
Via the automation of these processes that PerfectCash enables, end users of the solution, including one of the nation’s largest operators of department stores, have realized cost-labor savings that equal many times the purchase price during the first year of installment. With PerfectCash, there is also the added issue of the Sarbanes-Oxley (SOX) Act of 2002. PerfectCash give retailers added control over accounting and treasury functions, which leads to smoother compliance with SOX financial audit and reporting requirements.
Benefits to retailers who implement Perfect Cash are as follows:
• Reduced labor for deposit preparation
• Check truncation (Check 21 compliant)
• Reduced change order size and frequency
• Accurate and quicker deposits
• Automated and accurate “make ready” for registers
• Interface to back room settlement software providing real-time information about cash/check activity
By way of example, FireKing recently provided Macy’s West a customized PerfectCash solution for automating the deposit process and creating register replenishments, reducing processing time by 50%. PerfectCash can combine all the functions, and it works in a similar (but smaller) scale than that of a bank or back office casino process. Savings are realized through reducing the time to process and increasing accuracy.
For more information about PerfectCash, contact [email protected]
Cash Office Security
Nearly all retailers, large and small, have what serves as a cash office—a place where not only cash is kept, but in many cases accounting records, invoices, employees’ schedules, and other miscellaneous business records as well.
All cash offices have some sort of cash storage container, ranging from massive and alarmed safes to simple locking file cabinets, which many or may not have a “lockable strong box” for the cash itself.
Cash offices are as varied in their design and construction as the type of merchandise sold by a big box retailer. Small “Mom and Pop” retailers often use a walled or curtained-off area of the “back room” for a cash office. A major national department store may utilize a room built almost to the standards of a bank vault, complete with bulletproof glass, bulletproof walls, and a “bandit barrier” entrance. We should point out that, while there is normally only one way of ingress and egress into a cash vault, there should exist a breakout panel somewhere within the cash office so that in the case of a fire or other emergency, there is a means of escape.
A “bandit barrier” is a double door (inner and outer door) entrance with a small space between the doors. This is also known as or is called a “man trap” configuration. The doors are electrically controlled from inside the cash office (vault). Each door has a small window so the person seeking entrance (after pressing the “doorbell” to announce his or her presence and desire to enter the vault) can be visually identified. The outer door is electrically unlocked, and the visitor enters the interior space between the doors, closing the outer door behind him or her, since the inner door cannot open if the outer door is also open. Once inside the “barrier,” the inner door is then “buzzed” (unlocked electronically) open. More sophisticated vaults also have a phone by the outer door to the bandit barrier (with a corresponding phone just inside the vault by the inner door). This arrangement permits the person seeking entry to announce the purpose of his or her need for entry, which is a step beyond mere visual identification.
Grocery stores and some drug stores (and some other specialty stores) place their “office” on a raised platform above the store floor level; this office is enclosed on at least two (generally three) sides with windows at a height at which someone seated at a desk within the office can see through to the selling floor. This office generally serves as both a cash and paperwork space, as well as the store manager’s office. The fact that it is raised above the selling floor level permits anyone working in the office to observe the activities on the selling floor. In this scenario, the bulk of the store’s cash is kept in a floor safe and/or a heavy standard safe located near the front windows of the store. The floor safe is buried in the concrete of the selling floor and is extremely difficult to break into. The standard safe, which is on the floor generally, has a time lock and requires two keys to open in addition to the combination lock. One key is held by the store and one by the armored car pickup driver. The time lock prevents the safe from being opened except at specific times during the day, even if the proper combination is used. Many of these safes also have an electronic alarm, which is activated if the dialed combination is dialed incorrectly. For example, if the last number of the correct combination is 30 and the number 40 is intentionally dialed instead, this will automatically send a hold-up signal to the alarm monitoring company.
In large stores, where a vault-like cash office exists, we find no objection to leaving the main safe door closed, but with the combination in an unlocked position. In smaller stores, which do not have a vault-type cash office, we suggest that the safe be kept locked at all times. We must mention one caution here: The combination to any safe in the vault needs to be memorized. If the combination to the safe must be written down, it should be kept in a sealed envelope in an office away from the cash office, for example.
If any portion of the cash office serves an area where customers can obtain refunds, cash checks, and/or pay bills, we then suggest that drawers be built under the counter of the service window and utilized for the receipt and disbursement of cash. Such drawers should be equipped with a “hold-up” alarm triggering device. This device may take the form of a “finger pull” switch or a “bill trap,” a device which holds a piece of currency that, if removed, triggers the silent alarm. At one time “kick-bars” located on the floor, which could be activated by a cashier’s foot, were popular, but they have fallen out of favor because of the high rate if accidental false alarms. Cashiers and other vault personnel must be trained, however, as to conditions and circumstances under which these alarms should be triggered. They should be taught never to do anything which may provoke the robber. Their best course of action is to carefully observe the robber and get a good physical description, which can later be given to the police, utilizing the Robbery form (which is found in the “Forms” section of this book). Training on the proper actions to take when being held up should be periodically reviewed with all personnel, particularly new cash office employees.
Periodic audits of all with funds and a cash office should be made. We do not suggest the frequency for these audits; that should be determined by the chief of finance or head of the internal audit department. We do suggest, however, that when an audit of the funds in the safe is done, each bill in a bundled (banded) stack be counted. It is not unheard of for an employee in the cash office to steal funds by removing one or two bills from each bundled stack. If the bills in a bundled stack are not individually counted, such thefts could go undetected for extended periods of time.
Cash offices should be adequately alarmed. It is beyond the scope of this book to provide specific details with respect to such alarms, but suffice it to say, a qualified expert should be consulted to determine the most effective way to accomplish alarming the cash office.
It should also go without saying (but we will anyway) that all employees who will have access to the cash office be fully vetted.
A final word about cash deposits: We discuss in the section “Escort Policy and Procedure” (elsewhere in this book) their use when making bank deposits. However, we strongly suggest that if any significant amounts of money are involved, the use of an armored car service be considered. We have seen too many cases where, in the interest of saving the few dollars involved in the cost of an armored car service, the store owner or an employee personally made bank deposits only to be robbed going to or coming from the bank, and in many cases, was injured as well. We do not suggest being penny wise and pound foolish.
Cash Register Manipulations
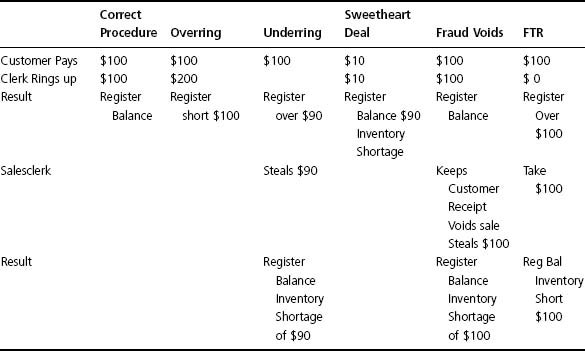
Table C-1 demonstrates the results of various types of cash register manipulations by dishonest employees acting alone or in concert with others.
To use this chart to understand cash register manipulations, you must use the left column in combination with the various situations along the top row of comments. For example, for the Correct Procedure, read down the column noted as “Correct Procedure,” while noting the actions of the customer and clerk on the left column. If the correct procedure is followed, the customer will pay $100 for $100 of merchandise, which results in a balanced register.
Consider, however, the results when a “Sweetheart Deal” (one in which the clerk sells a friend merchandise below the actual value of the goods). Here, the clerk sells $100 of goods for $10, which results in the clerk ringing up $10, causing the register to now balance. However, since $100 in merchandise left the store for a payment of only $10, the store now has a $90 inventory shortage. The other manipulations shown can be followed in the same manner.
CCTV: An Historical Perspective in Retailing
The use of visual surveillance by closed-circuit television (CCTV) in business began in the 1960s. Initially, the cameras were large and quite expensive. In large department stores, the initial use of a camera was for internal investigations. Even large chains had only one or two cameras. Smaller retail establishments (such as grocery and drug stores) also used CCTV as an antishoplifting device. Usually, the retailer would install one or two working CCTVs in a manner so that customers could view themselves on a nearby monitor. “Smile, you’re on candid camera” signs often hung beneath the monitors; other decals announced “This store utilizes closed-circuit television.” This arrangement sought to achieve two objectives: (a) Notify customers about the CCTV to minimize invasion of privacy complaints and (b) imply to the customer that other, less obvious cameras were monitoring and detecting illicit activity throughout the store. In actuality, most if not all other cameras were “dummies,” i.e., simply plastic camera body shells with ersatz lenses, blinking red lights, and wires simulating a working camera. The high cost of live CCTV necessitated this approach.
During the intervening 40 plus years, the development of CCTV paralleled the sophistication, miniaturization, and cost reductions reflected in the electronics and computer worlds. Today, color CCTV cameras are as small as a box of matches or the cap of a fountain pen. Their pictures can be transmitted to monitors over almost limitless distances via coax cable, telephone lines, microwave, optic fiber, and just plain wire. Monitors can display images from a dozen cameras simultaneously. Video tape recorders (VTRs) can now record the cameras’ images for periods up to 24 hours on one tape; the newest equipment is computerized digital VTRs, which can record on floppy disks and CDs over long periods of time. Modern cameras are capable of panning, tilting, and zooming in on a target, either by manual control or computerized response to predetermined events, such as motion or alarm signals.
Together with the technical developments of CCTV equipment and the significant reduction in its costs, new and effective uses of CCTV are constantly being found. CCTV is used by the Golden Gate Bridge to monitor traffic; by hotel lobbies, museums, and Amtrak stations to monitor patrons; by parking lots and garages to detect criminal activity; by bank ATMs as both a robbery deterrent and to identify those using the machines. Hundreds of businesses, from casinos to convenience stores, utilize CCTV for surveillance and security purposes.
Retailers have found CCTV valuable in not only deterring and detecting shoplifting, but also in investigating and documenting internal theft. They found that stores which installed CCTV had a perceptible drop in theft from shoplifting. One security agent, by monitoring an adequate number of properly placed cameras, could observe virtually the entire store, thus saving manpower costs.
Over 83% of retail establishments of all types utilize live CCTV. Today, retailers plan for CCTV installation in the same fashion as they do for cashiering facilities, merchandise displays, service areas, etc. Computer-controlled cameras are contained in opaque domes in ceilings; it is common to find major stores with dozens of cameras and CCTV monitoring rooms containing banks of dozens of TV screens, any one of which can be switched to a large viewing screen whose picture is simultaneously recorded. I have personally planned numerous such installations, recently having done so for the campus bookstores at major universities such as Stanford, Duke, and the University of California at San Diego. Retailing establishments found that CCTV perceptibly reduced shoplifting. More importantly, when shoplifting, robbery, burglary, or internal theft did occur, what better evidence to help convict the thief than videotape of the person actually committing the crime.
In retailing, CCTV performs many functions:
2. As a means of detecting theft
3. As an investigative tool, especially with regard to internal theft and fraud
5. As a means of preserving evidence of events which may later become the subject of litigation
The question is often asked what triggers a shopper becoming a subject of CCTV observation and monitoring. The answer is that many things can legitimately result in observation by a loss prevention agent monitoring the store’s CCTV system. Among these “triggers” are
• Random monitoring which results in loss prevention recognizing a person as a previously suspected or known shoplifter
• Random monitoring which results in the observation of suspicious behavior by a shopper, which may include:
While the retail industry was the first major user of CCTV for security purposes, its value as a crime deterrent was quickly recognized by others, and its use began pervading all aspects of society, as was alluded to earlier. It has been reported that the UK has found street surveillance by CCTV to be an effective crime deterrent, and such use is being proliferated throughout England. American businesses are also finding value in utilizing CCTV to surveil parking lots and building exteriors; CCTV is being used and can be seen (and in some cases not seen) in venues ranging from sports stadiums to casinos.
The continuing drop in CCTV prices has also contributed to the increased utilization of this technology. The use of miniaturized and disguised CCTV cameras connected to home VCRs (or the use of self-contained “camcorders”) has popularized the use of this technology by parents to monitor the activities of baby-sitters left in charge of their children in the parents’ absence.
We cannot discuss the widespread use of CCTV without concomitantly discussing the legal aspects of its use. The emphasis, increasing exponentially, on privacy rights has brought the increasing widespread use of CCTV into question from a privacy standpoint.
The consensus is, at least at the present time, no right to privacy exists when the subject of visual surveillance is in a public place. Obviously, covert surveillance in private areas of public buildings, such as restrooms and fitting rooms, is illegal. Even private office spaces, if occupants have a key and can lock the door, or otherwise make the case that they had a reasonable expectation of privacy, are more than likely off-limits to covert CCTV surveillance. Any time covert CCTV surveillance is planned, care should be taken to ascertain its proposed use is legal, and the opinion of knowledgeable legal counsel should be obtained. We must also emphasize that our discussion involves only visual surveillance; audio surveillance is an entirely different matter and brings into play a whole new set of rules, laws, and restrictions.
So what does the future hold with regard to visual public surveillance in general and the use of CCTV in particular? In our view, the foreseeable future will see increased visual surveillance. Technical developments, coupled with the increase in security needs of all sorts after September 11, 2001, foretell the ever-increasing use of CCTV by both the civilian, law enforcement, and military communities. We read of surveillance drones replacing manned surveillance aircraft in Afghanistan; we’ve seen TV shots of the wall-to-wall coverage by CCTV at the Winter Olympics and Super Bowl XLI; we see more advanced uses of technical surveillance such as facial recognition in use at public events and suggested for widespread use at airports to detect and deny access to aircraft for persons on official watch lists. If September 11, as horrendous as it was, had one good result, it was that “security” is no longer a dirty four-letter (times 2) word. This increased emphasis on security throughout the world can only harbinger the ever-increasing use of reasonable surveillance in all aspects of our lives, and in my view, a willingness of a vast majority of the public to forgo some privacy for increased safety.
Celebrity Appearances and Special Events
One aspect of loss prevention, although not common, is the need to address protection considerations when “celebrities” either visit stores or the retailer plays a significant role in such appearances.
Your authors have been responsible for the security at large “special events” (many for a local charity) and/or smaller personal appearances, both of which involved the presence of celebrities. In some cases these events involved multiday activities including fashion shows at local venues outside the store. This complicated the security aspects because large quantities of expensive merchandise (RTW, furs, fine jewelry) would have to be moved and stored (sometimes for several days) at a remote location, where it would be exposed to perhaps dozens of models, make-up artists, and other nonstore personnel. In other cases, the simple appearance of a celebrity (e.g., Elizabeth Taylor, Cher, Christie Brinkley, Catherine Deneuve) in the store created security problems ranging from crowd control to the physical protection of the celebrity, who, in some cases, was a vocal advocate for very controversial causes. Often, a private reception followed the celebrity’s public appearance, which added unique considerations.
Some celebrities have their own security personnel with whom a working relationship must be established. It is essential that “who will call the shots” must be sorted out in advance to prevent disagreements and confusion in the midst of the event. In other cases, public figures (e.g., Corazon Aquino, Rosalynn Carter) required coordination with the Secret Service (USSS) and/or department of state security (DSS).
The State department played a big role in Prince Charles’s visit to the Broadway Department Stores’ flagship store and worked closely and coordinated with that store’s security staff as well as the Los Angeles Police Department. The rules of the game included that the store was responsible for such in-store functional considerations as control over which elevators would and could operate and/or be used by the prince while inside the store. There was concern an elevator might stop and open on a floor that could compromise security. Such kinds of “proprietary knowledge” makes the private sector an invaluable partner with governmental agents as well as the celebrity’s own protection staff.
Additionally, security plans had to be coordinated with the stores’ publicity and merchandising departments. Security had to be not only effective, but also as invisible as possible so as not to detract from the visual/promotional aspects of the event. While all these challenges were interesting, they also consumed lots of time with the knowledge that any untoward event would receive national publicity and damage to the company’s reputation. Fortunately, my associates were both imaginative and practical in their planning and implementation of the security aspects of these events.
Let me cite just two examples of how celebrity events were dealt with from the security point of view.
Elizabeth Taylor appeared at Macy’s San Francisco promoting her “White Diamonds” fragrance. This event was overseen by Ms. Taylor’s publicist and the store’s public relations and special events departments; security aspects were determined by consultations between Ms. Taylor’s own security detail and the store’s security department. Based on Ms. Taylor’s request, all mail received at the store for her prior to the event and gifts for her during the event were given to store security and examined prior to delivery to Ms. Taylor. At all times during the public appearance, an ambulance (with paramedic crew) was available at the closet exit to the event. Credentials were issued to the press, store nonsecurity personnel, and security personnel. These credentials were color-coded to facilitate the wearer gaining or being denied access to specific areas.
Without my detailing all the specific security precautions, suffice it to say every contingency was planned for, and all security personnel had specific assignments should an untoward event occur. Every aspect of Ms. Taylor’s visit—from the arrival of her plane at the airport, her arrival at the store, the event itself, until she reboarded the plane at the conclusion of her visit—was preplanned. This planning included a suitable place for her to relax in the store, backup vehicles, radio communications, hotel security, travel routes, decoy limo, and prescreening of those receiving credentials. All planning was reduced to writing: floor plans for the event venue showing the location of stanchions, travel routes, press areas, holding areas, and security guard locations. A minute-by-minute time table was prepared to assure a smooth-running event.
In previsit correspondence from Ms. Taylor’s publicist, the following was noted: “Security control is the most important consideration for Miss Taylor’s personal appearance in your store.”
While the bulk of the security was performed by the store’s security staff (with added personnel from nearby stores), it was prudent to contract with a local guard service to provide approximately 30 uniformed (blazers) personnel, who were stationed at exits and throughout the crowd area. Each of these contracted personnel was prescreened and issued very precise post orders as to exact duties and responsibilities. The aspect of crowd control cannot be overstated: Always allow for more crowd control officers than you think will be needed. It’s better to be safe than have an untoward incident.
The second event I’d like to describe was the personal appearance of Luke Perry of the TV show Beverly Hills 90210. Figure C-02 shows the letter to the San Francisco Chief of Police that sets the stage for the extensive security arrangements for this event. As background for the letter, you should be aware that over 106,000 phone calls requesting tickets for this event were received; the volume of calls in a 2½ hour period actually “blew up” the switchboard and disrupted phone calls to the store until the switchboard could be replaced.
Security planning for this event was extensive. As the San Francisco Examiner reported: “Moscone Center hasn’t seen such security measures since the 1984 Democratic National Convention.”
The letter resulted in the use of 18 officers from the SFPD being assigned and paid for by Macy’s. (Note that 10B officers are those assigned by the police department but paid for by private [other than city] funds.) It also produced a four-page memorandum from the commanding officer of the detail with assignments, equipment required, and instructions for executing appropriate police action (e.g., arrests) if necessary.
For the event (two shows of about 1 hour each) itself within Moscone Center, we hired 120 uniformed security personnel from area security providers with experience dealing with large crowds (such as at the San Francisco 49ers football games). We assigned 30 of our own security personnel to the event.
Again, we had to plan for decoy units, communications, issuance of post orders, crowd control, barricades for the stage area, travel routes, medical emergencies, portable restroom facilities, security jackets, bullhorns, observation areas, fire lanes and zones, and credentials for personnel authorized in backstage areas.
The security budget for this event was $36,600, not including the cost of our own personnel.
Lessons Learned
Special events and celebrity appearances present challenging security problems, but the application of basic techniques and procedures, adjusted to meet the peculiar circumstances involved, with some imagination thrown in, will provide solutions.
What are some of the more important considerations in planning for a special event or celebrity appearance? We suggest the following:
Pre-planning: Who knows all the event details?
• Can drawings of the venue be obtained?
• Always overestimate number of security personnel needed.
• Establish an emergency evacuation route.
• Plan on how to detain/confine drunks and disorderlies.
• How will security personnel be fed if needed?
• Consult with and obtain OK from fire marshall.
• Will it be necessary to screen for weapons/explosives
• Need for undercover personnel in crowd?
• Arrange for adequate communications.
• Solidify transportation requirements.
• What communications are needed, frequencies, etc.?
• Adequate relaxation and hold areas for celebrity?
• How to deal with inebriated celebrities? (This does happen.)
The venue: public area or within private property?
• Can access be readily controlled?
• Is admittance by ticket or first-come first-in basis?
The celebrity: well-liked or controversial person?
• Does the celebrity have any input into security needs?
• Can the celebrity veto security plans?
• Are any governmental agencies involved?
• Does the celebrity have any of his or her own security personnel?
• Must valuables (merchandise, furs, fine jewelry) be left overnight?
• Black tie? Arrange for proper attire for security.
• How to authenticate legitimate attendees?
• Will food be served? If so, hors d’oeuvres or sitdown dinner?
Post event: Review event and conduct after-action review for lessons learned.
Celebrity and other “Sensitive” Arrest
There’s an inherent risk that a retailer may find himself or herself with a celebrity in custody for shoplifting. We define a “celebrity” as a person who is a public official, athlete, film personality, musician, or other type of figure with high public visibility. The question is: Now what to do? Should a celebrity be treated any differently than Jane or John Q. Public?
Celebrities may either attempt to hide their identity or use it to overpower employees with their importance and influence.
As soon as it is discovered that a celebrity has been apprehended, it is important to minimize the confusion which will naturally occur and to secure the area and the suspect to prevent any loss of evidence. Senior loss prevention and store management must be promptly informed of the situation for their information and counsel. If the celebrity has not at this point relinquished the item(s) stolen, he or she should now be requested to do so. Be sure that this surrender of merchandise is done in the presence of a witness. At this point, company policy for dealing with celebrities should be followed.
What should that policy be? That is a decision only senior management of the company can make. Management must realize that if an arrest is made, it will become a matter of public record and, most likely, extensive publicity, as best exemplified by Winona Ryder’s arrest in 2001, which is a classic and showcase example of the public interest and frenzy over this kind of incident. You can count on publicity if a celebrity is booked for shoplifting. The other side of the coin is why should a celebrity be treated differently than any other shoplifter? Written policy on how to deal with these rare events will dictate the course of action to be followed. And that action must be consistent to avoid subsequent claims of discrimination.
The range of options reflected in the policy could include, but is not limited to the following:
• If the celebrity offers to pay for the merchandise, after receiving an admission of guilt and release, accept payment by having the sale rung up on the selling floor in the normal manner.
• Decline the celebrity’s offer to pay, recover the goods, and obtain a written admission of guilt and release.
• Process the celebrity just as any other citizen who has been taken into custody for shoplifting and exercise one of the three normal dispositions; i.e., call the police, arrange for a conditional release, or release.
The other question which often arises is how to deal with law enforcement officers, senior public officials, and members of the celebrity’s immediate family. Local customs and the political realities must be taken into account. We suggest that if LEOs are apprehended, the head of the department be contacted and his or her advice followed. If spouses or children of LEOs are apprehended, contact the LEO and advise him or her of the situation and asked for a recommendation.
In the final analysis, however, the owner or senior management of the store must make the final decisions, and such decisions should be reflected in written policy.
Chase/Chasing Policy
Every retailer who has a policy authorizing employees to engage in the legal “merchant’s privilege” of detaining suspected shoplifters must have a clear written policy specifically addressing the issue of chasing or pursuing those who refuse to cooperate or otherwise attempt to escape. Injuries drive civil lawsuits, and the two most common causes of injuries evolve around (a) use of force and (b) pursuits. Indeed, out of concern over these two integral aspects of a detention process, some retailers have adopted policies which prohibit the use of force and “no touch no chase,” which we view as a virtual oxymoron. It simply makes no sense to charge employees with catching shoplifters but to deny them the necessary tools to do the job. This issue is addressed more fully in the No ‘Touch’ “Policy” section of this book.
Suffice it to say the majority of detentions for shoplifting are made with the understanding that legal, nondeadly force may be used, and if a person pushes or attempts to strike a loss prevention agent or otherwise bolts to escape, a reasonable and measured effort will be made to take that fleeing thief into custody. We subscribe to this strategy.
The chase/pursuit policy then must spell out what is “reasonable” and what is a “measured effort,” and that policy, because of the nature and dynamics of the process, must include aspects of the use of force.
The drafting or redrafting of the policy should include the following:
1. Agents charged with the task of detaining customers must undergo structured and professional training in how to approach a person about to be detained so as to minimize the risk of violence and effort to escape. Agents who have not been so trained or “certified” to make detentions should be prohibited from making detentions under any circumstances.
2. Ideally, no touching of the customer will be made while escorting the subject back into the store.
3. Minimal touching, such as guiding the subject with one hand on the subject’s upper arm or elbow, is the next level up from no physical contact.
4. Should the subject stop and simply refuse to move or continue, the agent should be authorized to use just that amount of force to overcome the resistance.
5. Should the subject bolt, the agent must make an immediate on-the-spot determination whether a pursuit can safely be made without running into or striking some innocent bystander.
6. If, at the outset of the escape, the subject drops the merchandise, policy must dictate if such action precludes further involvement, i.e., a pursuit, or not. If further pursuit is permitted, it must be kept in mind that any subsequent injuries to the suspect, a bystander, or the agent, the store will have a more difficult time defending a lawsuit, since the merchandise has been recovered and the store has now suffered no loss.
7. No running inside the store.
8. No running in a crowded mall or shopping center.
9. No running in a parking lot if the lot is crowded with pedestrian customers.
10. No pursuit across streets. We note that deaths from shoplifting suspects running into the street and being hit by cars occurs with regrettable frequency. Both of the authors have consulted in such cases and can attest to the utter heartbreak such incidents produce for all concerned parties.
11. Pursuit should not extend beyond the boundaries of the store’s property or shopping center limits.
12. If the fleeing subject is seized and goes to the ground, only holding force may be used until assistance arrives, i.e., no striking, kicking, punching, or choking.
13. No “piling on” a prone subject to avoid possible asphyxiation.
14. Handcuffs should quickly be applied and the subject helped to his or her feet and escorted back to the store.
The policy is necessary for several reasons:
• The agent must understand what his or her company expects in terms of performance and has taken reasonable steps to prepare that agent for this important responsibility.
• The safety and welfare of the general public are important to the company.
• The safety and welfare of the agent are important to the company.
• The safety and welfare of the shoplifting suspect are important.
In the event of civil litigation, the policies in place and the actions taken by the agents in making the apprehension must be demonstrably reasonable under the totality of the circumstances.
Check Fraud
Historically, suspects of check fraud have focused on stealing blank checks, mailed by banks, from unsuspecting customers’ unlocked mailboxes. This once-popular type of check fraud is making a comeback, aided by the fact that most bank customers do not include any preprinted information on their checks, such as Social Security numbers, addresses, or phone numbers. This type of information is added at the point of sale, verified by the merchant who is relying on the fraudulent identification manufactured by the criminals. This bogus identification often includes drivers’ licenses or state-issued identification cards that, with today’s technology, can be easily created.
The thieves continue to cash checks until one is rejected for insufficient funds—that is, if a clerk actually contacts the bank to verify funds. The culprits simply say they don’t know why the check was rejected, “I have plenty of money in the bank; I’ll get the cash and come back later to pay for it.” They never do. The thief just moves on to the next victim.
Although retailers have become more advanced in antifraud techniques, so have the criminals. Most check scams today involve a more detailed execution. Today’s fraud has evolved along with the technology, often using colored copiers, high-tech scanners, and over-the-counter solvents. Some of these new fraud techniques are described next.
Check Washing
Using a process known as “check washing,” suspects erase the ink on checks using chemicals that can be found on the shelves of a local supermarket:
It is estimated that check washing accounts for over $815 million of fraud losses every year in the United States.
Here’s the way the scam works: A suspect removes checks that are often left in an unattended mailbox that the consumer has used to pay personal bills. The suspect then washes the ink from the check, leaving the original signature, but altering the payee and the dollar amount. The suspect often cashes the check at supermarket chains, small gas stations, check cashing outlets, and credit unions using a fraudulent identification.
Despite the fact that check manufactures have tried to prevent check washing and fraud by making checks difficult to wash or copy, many suspects have become so good at check washing that retailers and consumers are unaware until they are given notice from the bank that they were victims.
As a consumer, you can protect yourself by not leaving your mail unattended, using a postal drop box when possible, and using a “gel” pen when writing a check.
As a retailer, you can look for the security features that check manufacturers have used when ordering company checks. Security features may include the following:
• Watermarks: Watermarks are made by applying different degrees of pressure during the manufacturing process. Watermarks are subtle and can be seen when a check is held up to the light. This feature is helpful when detecting a counterfeit check because most copiers and scanners that are used to make the counterfeit checks cannot accurately copy the watermark feature.
• Security inks: Security inks react with common chemicals that are often used to wash checks, making the check unusable.
• Chemical voids: The paper used to make checks is treated with a chemical that is not detectable until mixed with a solvent used to wash the check, producing the word “void” across the check.
• High-resolution micro printing: This is small printing that cannot be seen with the naked eye and is most often used in the signature line of the check. When magnified, the series of words becomes visible; if altered, the series of words becomes illegible.
• Gel-based pens: When writing a check, consumers should use a gel-based pen. Most gel-based pens have been found extremely difficult to wash from the original check. Ballpoint pens and markers are produced with dye-based ink that is easily washed with the average household product.
• Holostripe: Similar to the hologram on a credit card, this feature is inserted into the check and is difficult to duplicate using a color copier or scanner.
Counterfeit Checks
Retailers often fall victim to counterfeit checks and again are not aware the check was counterfeit until they are given notice by their financial institution. Due to the advancement in color copying and desktop publishing, this is also become a fast-growing scam.
Suspects often get their check printing material at a local office supply store where the check writing paper is readily available. (Most over-the-counter paper does not contain the security features mentioned previously.) The suspect then uses an active checking account number and makes several blank checks using a color copier or scanner that is located at his or her home or local printing warehouse. The suspect is then able to use the home-made checks at any retailer that accepts checks. The suspect will frequently write the check for an amount over the purchase price to obtain cash as well as the merchandise.
Suspects also make up checks which appear to be payroll checks from known companies, since major supermarket chains cash payroll checks.
Many retailers combat the check fraud issue by, for a fee, using outside companies that guarantee their checks if the retailer follows certain steps when accepting a check. The benefit of using an outside company is that it guarantees the checks will be paid, regardless whether they are subsequently found to be a fraud. The outside company compares the check data against its database to determine if the company should accept the check from the consumer.
The retailer’s responsibility is to download the program, train its employees to take accurate information, and leave the rest to the outside company. Most large retailers are not equipped to investigate and attempt to collect bad checks. By using an outside agency that guarantees the check, that agency then becomes responsible for investigating, collecting, and perhaps prosecuting the perpetrator.
Citizen’s Arrest (Private Person’s Arrest)
Citizen’s arrest is a concept that dates back to English Common Law. Prior to the development of modern police agencies, responsibility for law enforcement rested with the members of the community. When a crime occurred, every citizen had the right and the responsibility to arrest the criminal and deliver him or her to the local sheriff or other authority.
With the establishment of organized police departments, the need for individual citizens to make arrests has diminished. Still, the right of private citizens to make arrests remains.
Where and When Permitted
Black’s Law Dictionary defines an arrest as “The apprehending or detaining of a person in order to be forthcoming to answer an alleged or suspected crime.”(1) Ex parte Sherwood, (29 Tex. App. 334, 15 S.W. 812).
Usually, arrests are made by police officers acting as agents of the government. The law gives these officers broad authority and a high degree of immunity while carrying out their duties. There are, however, times when ordinary citizens are confronted by criminal activity and no police officer is available to intervene. Because of this possibility, the laws of every state define certain circumstances under which private citizens are authorized to arrest or detain another person.
Some states permit arrest for a wide range of crimes. Others place strict limits on the type of offenses subject to citizen arrest and on the conditions under which the arrest can be made.
The exact circumstance under which an arrest is authorized varies with each state. Some authorize private citizens to make arrests for felony crimes committed in their presence. Others also allow for the arrest of felons even when the crime was not committed in the presence of the arresting person, as long as there is reasonable cause to believe that the person arrested committed the crime. Many states also permit private citizens to make arrests for other less serious public offenses committed in their presence.
A sampling of citizen’s arrest laws shows the following:
• In California: A private person may arrest another:
• In New York State: Arrest without a warrant; by any person:
• In North Carolina: G.S. 15A-404 Detention of offenders by private persons.
In most cases the person making a citizen’s arrest must actually witness the crime. However, many states have enacted so-called Merchant Privilege Statutes. These laws expand the authority of merchants to detain persons for shoplifting and certain other crimes based on a reasonable belief that a crime occurred.
Who Can Make an Arrest?
Although usually referred to as a “citizen’s arrest,” a more accurate description is “private person arrest.” In most jurisdictions where these arrests are permitted, the language of the law extends the authority to any “private person.” This may include noncitizens and even those in the country illegally.
Liability
Under the laws of most states, police officers acting lawfully in their official capacity enjoy considerable immunity from lawsuits arising from their actions during arrests. The same is generally not true for private citizens. Performing a citizen’s arrest exposes the arresting party to both civil liability and criminal penalties if their actions are later found to be in error or in violation of the law. Where they apply, “Merchant Privilege” laws often provide for limited immunity from civil liability if there is reasonable cause to believe that a crime was committed and the arrest was made in a legal manner.
Before someone makes a citizen’s arrest, it is important to fully understand what the law permits in the state where the arrest is to be made.
Civil Disturbances
September 11, 2001, placed a whole new perspective to “civil disturbances”; it now includes terrorism attacks. Since the nature and extent of any such attacks, civil or terror, cannot be predicted and may take a variety of forms, we limit or discussion to some general precautions.
Do’s and Don’ts
• All executives and loss prevention/security personnel have keys to lock doors as necessary.
• All executives and loss prevention/security personnel are in possession of the following telephone numbers:
• Assure trash is removed from the dumpsters on a daily basis, if possible.
• Assure that only “necessary” terminals are opened once threat of civil disturbance is known.
• Both store manager and operations manager should carry one of the security radios at the first sign of any disturbance, if possible.
• Make sure your store command center telephone is staffed at all times by security, senior management, or some other responsible individual at the first sign of any disturbance, if available.
• Have a portable radio available so that local news broadcasts can me monitored.
• Assign a team of store volunteers that would include members from security, stock, dock, etc., to be available to board up windows with premeasured and cut ¾-inch plywood sheets. Assure an ample supply of nails, hammers, gloves, and eye protection is available to handle this task safely.
• Predetermine whether the store will be evacuated upon reasonable belief that it may be in the immediate area of any riot or civil disturbance. This determination should also factor in whether any personnel will remain, to protect the store and its contents, after the general evacuation order is given. If some personnel are to remain, assure they have adequate means to communicate with designated senior management and whether any other special equipment, in the use of which they have been trained, will be issued.
• Determine, in advance, what the pay policy will be for evacuated employees for the period(s) of time off normal work schedules due to an evacuation of the store and/or inability to obtain transportation to work.
• In the extreme event that your store is over run with demonstrators while customers and employees are still present, establish a safe haven such as your office, dock, etc., to shelter these individuals until order is restored. As soon as possible, notify mall security, law enforcement, and regional command for assistance.
• If you are ordered to evacuate the building, obtain the name of the person and the agency he or she represents for insurance purposes.
• Assure all flashlights are in good working order; keep a spare set of batteries.
• Conduct an emergency generator test (if applicable) and assure there is an adequate supply of fuel available.
• Determine, in advance, whether to leave the lights on or off if the store is totally evacuated.
• Do not chain or lock fire doors or emergency exits for any reason while employees and customers are in the building.
• Do not allow firearms on the property, unless armed contract guards have been hired (or previously trained armed proprietary personnel) will be on premises to protect company assets.
• Do not attempt to engage in physical altercations with any demonstrators who may enter or attempt to enter the store, unless those on the property have been given specific directions to the contrary detailing the amount and type of force they are permitted to use.
• Do not disobey the orders of any police or government official, i.e., National Guard.
• Stores should not directly communicate with other stores; this will only tie up the phone lines. All communication outward from stores should be restricted to their regional command center or local emergency services.
Figures C-3 and C-4 are forms which may prove beneficial.
Civil Recovery
Background
Since the early 1970s states have been passing civil legislation designed to penalize anyone who removes merchandise offered for sale from a store or distribution center without payment. Each state law varies with regard to the penalty amount, damages, and if there is a criminal matter pending.
These laws have proven themselves to be very effective in helping to reduce shrinkage by generating resources for retail loss prevention departments as well as providing a financial deterrent. This income stream helps defray the costs of preventing theft to those who incur it or, in the case of a minor, to the parents.
The language of a few of these laws seems to indicate their intent is to be an alternative to criminal prosecution. Most of the civil recovery laws are not used as an alternative but rather as a consequence to a criminal act. Each of these crimes has a victim. The victims in these cases are retailers, but mainly their good customers who in the past have paid in the form of higher prices.
These laws are currently being used by retailers as an add-on to their loss prevention toolbox. These tools, when added to the entire picture, complement controls and procedures to help bring down shrink.
Generally, theft is a crime of opportunity, and nobody has more of that than employees. Those who are terminated for theft are liable civilly in all states. The major difference between internal and external cases has to do with the condition of the merchandise. Customers are usually caught “red-handed” still in possession of stolen merchandise, which is returned to the retailer once the matter has been dispositioned, either in-house or by the courts. In most employee situations, the case is often built from investigation of past theft, and merchandise is often unrecov-ered. In this situation the retail value of the loss is added to the penalty. The maximum amount is determined by the small claims maximum in the state where the incident occurred.
For best results, case work should contain a narrative, but the crucial element is the theft admission statement signed by the former employee. This process allows the person to pay back the losses incurred through restitution as well as a portion of the investigative cost involved through the civil penalty.
Recovered expense dollars bring 100% to the bottom line, income previously unattainable, and losses which had been previously written off are now being regenerated.
Procedure
Each case must be reviewed by someone who has been properly trained in the area of case review. The condition of the recovered merchandise should be noted, specifically if it was recovered in unsaleable condition or unrecovered. A complete narrative should exist, keeping in compliance with shopkeeper’s privilege and private person’s arrest procedures. Responsible parent information on minor cases should also indicate to whom the child was released. In all cases, the subject disposition should be indicated. The preceding conditions, together with state law, will determine whether a demand should be issued and for which amount.
A series of letters is then sent to the individual demanding payment, which is either preset by the law or based on loss prevention costs. This process is known as “civil demand.” It is an attempt to resolve a financial matter prior to a court action. Once the matter moves to civil court, copies of the demand letters are provided as proof of an attempt to settle this between the parties.
Since there has been no judgment made prior to the civil demand process, care must be taken to limit exposure to liability when engaging a nonadjudicated individual by making outbound calls. In other words, this situation should not be treated as a debt-collection exercise. Once an arrangement has been made between the parties, calls to the individuals are best cast as follow-up to those arrangements.
Recommendations
Upon release of the individual, a notice should be given. The notice should contain language which indicates the state law, the incident, the fact that the store may seek a penalty, and a phone number to call with any questions. Store personnel should not try to explain the notice. They should refer all calls to the recovery agency or suggest the person seek legal counseling.
Store personnel should separate themselves from the collection process. Penalties assessed should be done after the entire case has been reviewed.
A central point for collections and case review should be established so payments, calls, and correspondence can be controlled. A company attorney should be designated to handle inquiries and research.
It is wise to find out what limitations are contained in the individual state statutes. For instance, there are a few states in which a civil demand cannot be issued if there is a criminal matter pending. Understanding the specific criteria to be met on a state-by-state basis is essential.
Effectiveness
The most effective use of civil recovery laws comes in the way of dealing with recidivism. Especially among minors, although most states hold parents responsible, a good way of handling minor cases is by helping parents to exercise control. By allowing the son or daughter to make payments, the consequence for his or her action is realized. Also, this process will not alienate the parents, who are, many times, good customers.
Our internal studies show a rate of recidivism of less than 1% in cases in which the people paid the civil demand. More importantly, in a case study of a major retailer, the overall shrinkage was significantly reduced upon the introduction of a civil demand program.
Outsourcing Collection Services
When a decision is made to create a partnership with a firm to handle any portion of civil collections, several factors should be considered. The first element in this choice should be the services offered by the firm. Many firms today will offer to collect civil recoveries as a return on the services offered by their firm, such as investigation, sale data analysis, and interview costs. Others are law firms, which will add attorney fees to the amount collected and at some point will be retaining more funds than the retailer. Still other firms have the best interest of the industry in mind. They will bring experience in law, loss prevention, and retail. They make the connection between software manufacturers, loss prevention departments, and collection attorneys.
When doing diligence on potential partners, ask for references and also include a request for names of clients lost and why. These requests should also be included in any request for proposal (RFP). Also, some firms will advertise, showing the names of retailers which are only servicing a portion of the cases. Investigate the ownership of the firm, the length of time in the industry, and the amount of litigation encountered along the way.
Currently, there are a few companies active in this arena. My apologies if I have left out any:
Civil Restitution
Civil restitution is a remedy that operates by state statute and is available to the injured party in addition to sums due by way of other restitution remedies.
One of the many challenges retail loss prevention professionals have faced over the years is balancing their efforts to reduce shrinkage against the organization’s need to reduce costs. Civil restitution initially came about as a bright idea to balance the expenses of store detective payroll by passing those costs along to the people who caused the expenditures in the first place—the shoplifters.
Some History of Civil Restitution
In the early 1970s, the state of Nevada enacted a statute involving the theft of library books and civil remedies available to the victims of these thefts. Later, 10 Western states enacted similar statutes, but specific to the act of shoplifting. At the forefront of this legislation was Ron Clark, then Loss Prevention Director of Payless Drugs in Oregon. Ron recognized the opportunities such legislation offered to loss prevention departments and their retail organizations. It was definitely a useful tool to “manage” shoplifting expenses by passing such costs along to those who caused the losses. Additionally, many loss prevention professionals observed that criminal prosecution of shoplifters was being sidelined by reduced budgets in law enforcement, prosecutors, and what appeared to be an apathetic attitude by some jurisdictions.
In the early 1980s, more and more companies jumped on the bandwagon, after initial court challenges were overturned and the path smoothed by the early pioneers. Many members of ASIS International (then the American Society for Industrial Security) Retail Loss Prevention Council proselytized these laws nationally, and we saw additional states enacting such legislation.
Additionally, many states amended their laws to include parents of juvenile shoplifters.
However, these statutes did vary in language and recovery amounts. This occurred because they were enacted by legislators who had to be sensitive to the individual needs, concerns, and the laws of their various jurisdictions.
Most professionals regarded civil restitution as a business tool, rather than punishment.
To Utilize Civil Restitution or Not
Whether a company decides to process civil restitution paperwork internally or opts to use one of the many qualified outside services, several decisions should be considered prior to the adoption of such a program.
First and foremost, upper management must buy into the process. To facilitate this, educate them on the laws appropriate in the area in which you do business and what remedies you have under these laws. Besides running a cost-benefit analysis of using such remedies, it would behoove the loss prevention professional to cover such issues as possible loss of business from irate parents who have received demand letters for their miscreant children’s illegal acts.
If upper management is adverse to such exposure, one alternative is to send demand letters only to adult shoplifters.
Either way, though, you need to make a decision on just to whom you will send demand letters. Will it be all shoplifters? Just those you prosecute? Just those you convict? Just those shoplifters stealing more than a specific dollar amount? Once you have made these decisions, you are ready to proceed further.
Once you have the buy-in and decided to whom you will send these demand letters, you need to decide what amount you should demand. Working closely with your attorneys and financial staff, develop what your average cost of handling a shoplifter may entail and document this information.
Costs relevant to shoplifting prevention in your stores may include such items as electronic article surveillance (EAS) systems, electronic and mechanical shoplift prevention devices (such as cables and the like), and labor costs of plainclothes or uniformed shoplift prevention/detention personnel.
Also, in some jurisdictions, you are allowed to ask for a civil penalty and add on the actual cost of the item stolen. In these jurisdictions, the more the shoplifter steals, the more he or she will have to pay for civil restitution!
Prosecute Versus Catch and Release and the Issue of Extortion
Some jurisdictions require you to prosecute the individuals before requesting a demand amount. Most do not. You have the option of catching the shoplifter and releasing him or her, and still making a civil demand for your costs.
Upon review with upper management and your legal department, it will become obvious what tack your company wishes to pursue regarding the issue of prosecution. Every company must make this decision based on what it feel is best for the company, in each individual state’s jurisdiction.
Additionally, the issue of catch and release may cause some concern regarding juvenile shoplifters. Most companies will require either law enforcement contact or, in the case of release, parental/guardian response to the location prior to release of a juvenile. Again, this is a matter for each individual company to address.
It is recommended that you never present the demand for civil restitution at the time of detention. Any monies gathered at that time could be the basis for allegations of extortion from hungry attorneys who are always on the prowl for a lawsuit against “deep pocket” companies.
However, it is advisable that you give the shoplifter some written document or oral statement backed up in the report that will inform him or her of the possibility of civil demands to be made at a later date. This avoids “surprises” when your demand letter arrives.
Who Decides Who Gets the Demand?
Deciding who gets the demand is an option many companies have agonized about. Many will train their line shoplift detention personnel as to the company’s guidelines on sending a civil demand and leave it up to the agent to recommend or not recommend the issuance of such a letter. This approach seems to work best that way, as the person most knowledgeable of the case, with all the facts in hand and with good education of the company’s civil demand letter guideline template in hand, calls the shots.
Whoever makes this decision, however, must be cognizant of the company’s policy or guideline on the parameters of what qualifies a situation for a civil demand letter and must approve the release of such a letter. This would apply whether the letters are created in-house or outside the company.
Setting Up Your Demand and Collection System
If you decide to create demand letters in-house, you will need to staff up. Consider that you will have to develop a system that will identify which shoplift detentions will merit a demand letter, send a letter on these detentions, track collection or nonpayment, and take further action.
Depending on your jurisdiction and laws, you may wish to pursue nonpayers in civil court. If you decide to follow this course of action, you certainly must first make a decision as to whether it is cost effective to do so. As with decisions to send letters, it is important to be consistent in the application of your decisions. All of this will require time, labor, and systems.
Should you decide to use an outside agency to send your demand letters, your major chore will be to select which detentions merit a demand letter and forward that information to your outside civil restitution agency. In most cases, these agencies will require either a set rate per letter or a percentage of the monies collected. They will follow up on nonpayers, and, in many cases, will function like a collection agency in this matter, sending several letters and even, possibly, making telephone contact with the nonpayers to elicit a payment of the monies due.
It is up to you to determine which will be the most cost-effective method for your company.
In any event, it is always wise to ensure that you are consistent in to whom you send demand letters, and to adhere to your program. This may avoid some legal problems in the future.
Once It Is Up and Running, What Other Issues May Arise?
One major issue is to set up a mechanism that will raise a red flag if a shoplifter is prosecuted and found not guilty. In those cases, it may be advisable to rescind your demand letter. However, you may wish to consult with your company attorney for his or her advice.
Also, it is always advisable to regularly review your cost-benefit analysis regarding costs per shoplifter and, if necessary, change your demand amounts to reflect this cost.
Don’t forget to ensure your upper management, who supported your program, receives regular reports on the income generated from your civil restitution program.
In some cases, loss prevention departments will credit part of the costs, or all, back to the retail location which incurred the expenses. Or, it is used to reduce the costs of the loss prevention department. Either way, the company’s bottom line is enhanced, and everyone likes that!
Collusion
Collusion is best defined as a secretive agreement between two or more people to commit an illegal or deceitful act. In the retail setting, collusion could be an agreement between
• Two or more “customers” to shoplift (as one example),
• A customer and an employee to transact a bogus or otherwise dishonest sales transaction (as a second example), or
• An executive, buyer, or purchasing agent and a second party to bill and pay for goods or services not delivered (as a third example).
We reference “examples” here because the wide range of types of “collusion” is worthy of and is the stuff mystery and crime books are written about. Suffice it then to focus on three examples which should set the stage of understanding for the loss prevention practitioner and/or manager’s role in dealing with collusion.
Collusion Between Two Customers to Successfully Shoplift
Customer A attracts some attention to himself in the selection of a relatively small but expensive item of merchandise and “palms” it in his hand. He walks away from the display still carrying the item. Loss prevention takes up the pursuit, following discreetly in anticipation of his leaving the store with the goods in his hand, unpaid for. As this Customer A turns the corner heading toward the door, Customer B, in a group of other customers, passes Customer A. Customer B is carrying a shopping bag. As the two pass, Customer A surreptitiously drops the merchandise into the shopping bag. Both, without acknowledging each other, proceed in different directions. Customer A is stopped outside the store by LP, and he has no merchandise in his possession. Customer B exits by another door with the stolen goods in her shopping bag, unbeknownst to Loss Prevention. The stage is now set for a “false arrest” lawsuit.
Another scenario could be that Customer A intentionally creates a distraction in the middle of the store causing customers and employees to draw toward that area, while a colleague (Customer B) in the corner hides merchandise and subsequently carries it out of the store.
Collusion Between a Customer and an Employee to Commit Theft
Customer A is the roommate of Employee A. Customer A fills her shopping cart with various items of merchandise and enters the checkout lane leading to the checkout cashier, Employee A. Employee A intentionally fails to record the prices of various items. The total sale may reflect the correct price of 20 items of merchandise, but 9 items of merchandise were never rung up or paid for, as intended in this collusive plan.
A second example: Customer B is Employee D’s sister-in-law. Customer B brings into the store a store bag and a receipt for $60 worth of merchandise charged to her account, but no merchandise. Employee D writes a fraudulent charge credit for the amount reflected on the charge receipt, which amounts to a theft of $60. The prior agreement between B and D to this scheme for committing this theft is also the crime of collusion.
Collusion Between a Second Party and an Executive, Buyer, or Purchasing Agent for Payment of Goods, Supplies, Materials, or Services Not Received and/or Rendered
The chief engineer of the warehouse and distribution center receives an invoice from a “painting contractor” for painting jobs around the facility. In reality, the painter painted the engineer’s mountain cabin and prepared the invoice reflecting work completed on company property, which was never done. The chief engineer approves the invoice and the painter is paid.
The buyer for hardware makes a deal with the stepladder supplier to inflate the invoice by $6 for each ladder purchased by the retailer, with the agreement they will subsequently split the $6 difference between the correct price and the inflated price paid by the company.
The store manager approves an in-store purchase of Christmas decorations, and the invoice is prepared by his brother-in-law. No decorations were received. His brother-in-law isn’t in the business of selling decorations. This arrangement represents collusion between the two to cheat the store and illegitimately receive money to which they were not entitled.
Two actual collusion cases are reviewed in the “Fraudulent Outsourcing and Invoicing” section in this book.
In the retail environment, there are endless possibilities for collusion between employees themselves, employees and customers, and between employees and vendors. The possibilities are limited only by imagination and creativeness. This potential for losses, which can easily reach into the thousands of dollars, is but one, albeit an important one, of the reasons for instituting a system of checks and balances and frequent audits, including the vetting of vendors, particularly those of the small independent contractor variety.
Company Property
The chief maintenance engineer of a major distribution center was detected stealing paint from the facility, and upon inspection of his garage at home, many items of merchandise and a sizeable collection of equipment and tools were discovered and believed to be the property of the company. The employee refused to admit to any theft other than the paint. A small percentage of merchandise bearing company price tickets was seized, but goods without any form of company identification and all the tools and hardware—from compressors to dollies and power tools—bore no company identification. Despite efforts to seek recovery through the criminal justice system, the then ex-employee was allowed to keep most of what was stolen property. Why? Because the company could not prove the items belonged to it.
This issue of establishing and proving ownership has long been a problem in the retail industry. How many fashion stores have had shipments of high price-point goods stolen, even in mass, like furs, and weeks later the police seize a large quantity of furs during one of their arrests and seek the owners/victims. And at store after store, despite evidence that furs were stolen and with copies of crime reports in hand, no one from any store could actually identify specific fur coats or shawls as theirs. The furs then ended up in police auctions. And so it has been with other kinds of merchandise as well as company property such as POS devices, copiers, computers, and a wide variety of expensive pieces of equipment.
Interestingly, many items of office equipment have serial numbers, but when one disappears, no one knows or has a record of that serial number. The question is: Who is or should be responsible for the inventory control of equipment? The loss prevention/security or operations department? Should the control (and records) be companywide or by individual facility? Who should audit this program and do spot checks to reconcile the books versus the actual inventory? The audit or loss prevention department?
Our recommendation is this: Control and audit of company property and equipment should be the responsibility of the loss prevention department, by individual unit. That said, then the challenge is to develop a program in which all company property is recorded by type and by serial number, if available, and to inscribe a number if no factory number is in place. Many police departments offer a property identification program in which a crime prevention officer comes to a small business or residence and inscribes with an etching tool the owner’s Social Security number or other number for future identification purposes in the event of a loss due to criminal activity.
One of your authors was the Chief of Campus Police (later renamed to Chief of Campus Security) of the Claremont Colleges in Southern California. Early in his tenure, he discovered bicycle theft was a serious and ongoing problem. The group of contiguous colleges with its thousands of student bicycles was a target for bicycle thieves. Although every bike had its own manufacturer’s identification number, students invariably did not record that number. Even if the student/owner was interested in the number, it was long, small, and hard to read; plus, the bike had to be turned upside-down to see it. An inspection of the various local police departments’ evidence rooms disclosed hundreds of recovered bicycles, all of course bearing ID numbers but unclaimed. Indeed, if a student went to a police department and claimed “that bike over there, the red one, is mine,” unless he or she had some evidence of ownership, that student walked home.
A workable solution: The campus police purchased a set of 10 numbered dies, a ball-peen hammer, and a ledger book. The various student newspapers of each college announced a new bicycle registration program in which the campus police would at no charge stamp a four-digit number on the upper side of the pedal sprocket and record that number.
Thereafter, when a student reported a missing or stolen bicycle, that loss was duly noted by the campus police, who subsequently would either visit the police station and look for the conspicuous college registration numbers because of the size and location and recover the bikes or delay visits until a few days before public auctions. Students were also encouraged to go to the police, but most opted not to.
The bottom line of this program is that many bicycles were recovered, in sharp contrast to earlier times without the program.
Does this strategy or something similar have application with company property in the retail industry?
Concessionaires and Tenants
Concessionaire departments, which comprise retail entities within the confines of a given store, do require special and unique attention. Examples of concessionaires and tenants could include fur salons, beauty salons, optometrists, watch repair, fine jewelry departments, wigs, fast-food entities, etc. These “special and unique” workers, who typically have access to the interior of the store during closed hours, appear to be but are not store employees. Yet they must comply to most store policies and procedures; e.g., if employees are required to enter and exit the store only through a designated “employee door,” concessionaire and tenant employees must be instructed to comply with that requirement. These “extraordinary” employees should be badged while in the store yet restricted from “back of the house” areas in which they have no business.
And concessionaires and tenants can pose unusual problems if their owner, operator, or employees are detected in any form of dishonesty. In the event such persons are detected in acts of dishonesty, they are to be processed not as employees but rather in keeping with the store’s procedures dealing with any nonemployees, i.e., shoplifters.
Conditional (Controlled) Release
Most retailers, when a shoplifter is apprehended, think they have only two courses of action: (a) release the shoplifter after a warning or (b) call the police and start the criminal prosecution procedure. What they do not realize is that they have a third option: the conditional (controlled) release.
What is a conditional release? It is an arrangement and written agreement between the person detained and the store whereby the first time a person is caught shoplifting, the disposition regarding that arrest is stayed with the understanding if not detected again within 1 year the matter will be dropped. If caught again, however, in that period of time in any of the company’s stores, the person will be prosecuted on both the original as well as the latest theft.
One aspect of the controlled release is that the suspect is aware that the company may file charges at a later date; this knowledge may cause the suspect a sleepless night or two worrying about this possibility. One hopes such worry may dissuade him or her from further acts of shoplifting.
Merchant may use the conditional release under any circumstance in which they feel it is appropriate.
For a suggested form to be given the person being released under this procedure, see the “Forms” section of this book.
Conscience Letters
Occasionally, a store will receive a letter, either anonymously or signed, from a person who has stolen from the store in the past and is confessing to that theft. These letters, known as “conscience letters,” are usually accompanied by a check or money order (and sometimes cash) to compensate the store for the amount of merchandise taken. These letters are from either shoplifters or former employees.
Such a letter is reproduced in Figures C-5A and C-5B; the name and address have been redacted.
When a conscience letter contains the name and address of the sender, it is appropriate to write a letter of thanks and acknowledge receipt of the funds, which should be deposited in a “restitution account.” If the store doesn’t have a restitution account, record the amount in the department from which the goods were taken and attach the cash register throw receipt to the letter and file in loss prevention department’s conscience letter file. If the store/company maintains an alpha negative file on all persons detained, add the sender’s name to the file and reference it to the conscience letter file.
Consent to Search
Occasionally, in connection with a theft investigation, it may prove useful to retrieve evidence by searching an automobile or a house. There are severe restrictions and legalities in pursuing such a search, and our advice is to consult with company or other competent legal counsel before conducting such a search. We set forth a form for obtaining consent for such a search in Figure C-6, but again advise consulting counsel before doing so.
Contract Security in Retail Environments
Ever since the first Pinkertons rode the rails protecting commerce in the Old West, private industry has utilized professional security services to safeguard their assets. The modern retailer is no different; uniformed security officers, often contracted from service providers, still dot the landscape of retail stores, both on the selling floor and behind the scenes. The prevailing reasoning is self-evident: A visible presence of store security deters theft and promotes awareness, and the security officer remains the essence of presence.
Over time, however, retail loss prevention directors have had to modify, reevaluate, and ultimately reinvent the role of contract security in a modern retail loss prevention program. Service providers, ever mindful of changing conditions, strive to meet the evolving needs as well.
Retailers today can choose from variable offerings of contract security services: the well-established uniformed guard; the emerging product offering that is contract store detectives, or “floor walkers”; and the more recent notion of engaging independent contractors, sometimes called “consultants,” for specialized LP functions relating to IT, internal audit, and shrink control program development.
Contract Security Guards
Since uniformed guards remain the most prevalent use of contract security in retail, it is appropriate to quickly review the key advantages most often cited in deploying “outside” guards.
Flexibility: The better guard companies can fill an immediate need almost instantly. Whether the need is temporary or permanent, night or day, fixed post or patrol, one officer or 10, LP directors using established providers can reliably summon the help they need with one call.
Few LP programs rely solely on contract guards for shrink control. However, the role of contract security officers has expanded well beyond the traditional “door guard”: Companies now employ contract security for lobby reception positions at the home office, permanent shift work at warehouses and distribution centers, augmented store presence for special events and the holiday sales season, overnight security on construction and renovation details, and response to adverse incidents such as robbery and other workplace-related violence.
Economy: The flat-rate, hourly billing formula indigenous to contract security provides cost control and accurate expense forecasting more reliably than the vagaries of payroll rates of proprietary staff. Fixed costs, with pay-as-you-go scheduling, allows for planned budgetary allocations by location and shift that eliminates expense “surprises” and provides an unambiguous cost/benefit analysis. Compared to technology and systems-reliant LP resources where ROI justification is sometimes elusive, guards are a tangible commodity, easily quantified: “this many dollars buys this many hours.” Further, it has been long held that for some security positions, contract security is more cost effective than proprietary, or in-house, security employees. Contract security advocates point to the corporate pay scales that often result in higher wages for security employees, coupled with overtime opportunity and a benefit package that includes medical insurance, worker’s compensation, vacation, sick days, and more to argue that the hourly rate charged by a security service provider can be significantly less costly in the long run than an in-house counterpart. These advocates do not contend you get a better guard—just a cheaper one.
New realities to the marketplace, however, should prompt the prudent LP director to periodically revisit the cost ratios between contract and proprietary security. Liability insurance, worker’s compensation, licensing and certifications, unemployment insurance, and payroll taxes continue to encroach on security companies’ profit margins, and escalating costs are passed along accordingly. In some states, sales tax can add another 5–8% to the bill in addition to the quoted hourly rate. The contract security industry is also keeping a close eye on the efforts of the Service Employees International Union (SEIU) and others in their drive to organize contract security officers. Such an event, security companies contend, would further elevate their cost of service.
Having quantified the advantages of contract security from the business side, its effectiveness as a loss prevention tool can be examined. It would be appropriate here to first outline the expectations a retail LP executive would have when engaging a contract guard service:
• A visible, competent presence of security that may deter customers from shoplifting.
• Guards who arrive on time, groomed and outfitted in a manner that projects a professional security image.
• Guards who represent the corporate LP program favorably to store management and staff.
• Guards who have minimum training in the basics of retail security, e.g., alert enough to deter a hit-and-run at the door; able to manage an EAS alarm without incident; detect and communicate suspicious customer activity to management.
Welcomed, but not necessarily expected, value-added services may include the following:
• An ability to identify suspicious employee activity and report it to the company supervisor for communication back to you.
• An ability to intercede, within reasonable bounds, to prevent a loss of merchandise to a shoplifter.
• Perhaps, in the right circumstances, escort a manager to and from a bank deposit that involves a short walk to an after-hours bank drop.
• Witness that the building is properly secured and alarmed at closing, and where prudent, see the closing employees safely to their cars.
Reasonable expectations of the service provider include the following:
• That the guard will have undergone and passed a criminal background check with the state prior to being posted to your location.
• That the guard is properly licensed and the guard company is in compliance with state regulatory requirements.
• That the client company has a modicum of protection from liability by virtue of clear indemnification language in your service contract.
• That the guard company will handle schedule rotations in such a way as to provide, if preferred, no more than three different officers to staff a 7-day post.
• Billing integrity, with auditable invoicing accountability.
The ability of service providers to meet or exceed expectations rests chiefly in the relationship cultivated between subscriber and the provider.
Vendor loyalty plays a significant part as providers often “go the extra mile” in both guard quality and cost accommodation for clients offering the prospect of steady work and consistent deployment requirements. LP directors can enhance the guard’s effectiveness with detailed post orders and site-specific training, a reasonable and self-serving accommodation the client can make, provided the company assigns a security officer who is educable and committed to making the investment in time worthwhile. For a contract security officer to make a contribution to a store’s performance, the cost is both money and time.
Many retail LP practitioners cite a “disconnect” between their expectations and the deliverables from guard companies. Grooming and professional appearance are issues; demeanor and conduct on post are increasingly casual; relevant training vis-à-vis shrink control is virtually absent. There is a perception—some would say a reality—that standards among service industry workers across-the-board have declined and that the contract security officer has followed this trend. As a result, the user’s expectations of the service provider may require reconsideration, even on something as basic as credible background checks.
Security jobs are often temporary positions, and the applicants are often transient workers; a criminal background check in one state may not always reveal misdeeds in another. Reference checking can be suspect as well. In some instances a security officer is hired one day and dispatched to your store that same night.
Security companies reflect the changes to the American workforce, and as the workforce continues to absorb workers from outside the country, a state criminal check for a security guard applicant recently immigrated is unlikely to yield any adverse information; fingerprint checks are not run through Interpol. An applicant’s criminal past in another country would likely go undetected.
Expectations for relevant training may also have to be curtailed. State and local licensing regulations require costly certifications and training, little of which is relevant to preventing inventory shrink. As a result, any orientation an entry-level security officer receives is that of a “generalist,” and the contract provider has little opportunity for additional training specific to the retailer’s needs. The days of a guard “in training” standing post with a seasoned officer at the security company’s expense are long gone. Moreover, as security companies attract and hire more foreign workers, it becomes questionable how well traditional training curricula allow for cultural differences and language limitations, and enables newly immigrated security officers to interact with retail customers and employees in a manner that reflects positively on the client company.
Another contributing factor for expectations falling short is the reality of litigation-avoidance that guard companies must address aggressively if they are to survive. Costly litigation, punitive awards, and rising premiums have had a numbing effect on the industry, and “marching orders” issued to guards by their employer to prevent confrontation and litigation can be so restrictive as to boil down to a mantra of “see nothing, say nothing, do nothing.” The long-held security officer’s credo of “observe and report” may now include the caveat: “and take no action.” Understandable? Certainly. Does it endear the guard to the store manager who is told a man just ran out with an armful of dresses as the guard looked on? Certainly not.
As with all resources, contract security guards have their benefits and their limitations. The savvy LP professional will understand that background checks are limited, training is questionable, and the security companies must look out for their own bottom line before that of their client. These factors will be weighed in the context of security needs and the economic realities of budget. If a provider cannot balance the mutual interests of the client as well as his or her own, other options will emerge.
Contract Store LP Agents
Store detectives (now called LP agents) had once been the core component of retail LP programs. Over time, as shrink control became the purview of both store operations and finance, these one-dimensional assets dwindled in import and number. Some were redirected to audit functions, others became employee investigation specialists, but many became the payroll trade-off for capital expenditures in systems and technology that have collectively and consistently reduced inventory shrink industrywide.
Yet, occasionally, certain situations arise in which only the apprehension of a shoplifter or dishonest employee is going to protect the assets. There is a hard-core element that will not be deterred by uniformed guards at the door, signs in the fitting room, or cameras behind smoked domes, whether they be daredevils, opportunists, or foot soldiers in an organized retail theft syndicate.
In the days before imbedded EAS, covert CCTV, automated POS exception analysis, RFID inventory control, and extensive security fixturing, it was the store detective who protected merchandise from theft. Some were nondescript floor walkers who blended in; others were eccentric characters who raised the game to an art level. Each, however, possessed a vanishing skill set to exploit the selling floor terrain and observe, react, and close on shoplifters and employees alike, with an impressive record for clean, substantial cases. But their payroll burden on downsizing companies, coupled with the exposure to litigation, augured the winnowing of this profession and ushered in the era of technology and audit, with undeniably favorable results.
Many LP directors understand program effectiveness is cyclical, and although store detectives will never again be the catchall LP solution, some still prefer to have a deployable asset on call that can enter a market and mitigate a debilitating external theft condition. Enter the entrepreneurial contract security provider, eager to either create or diversify product offerings to meet a need in the marketplace.
Since the mid-1990s, contract store detectives have been an innovation touted in discussion but embraced only at arm’s length in practice. Variations on the theme have included a “shared pool” of LP personnel provided to multiple users on a mall-by-mall basis; to uniformed guard companies offering “plain-clothes” personnel for patrol and added deterrence; to specialists who monitor CCTV stations remotely or onsite and communicate live-time to store personnel.
Economically, the program suffers from being an “add-on” expense rather than a “trade-off” cost, as would be the case where a contract guard replaces an in-house security employee. The contract security company providing personnel incurs real setup costs in training, travel expense, and exposure to litigation that drives up the hourly rate to the point at which the program becomes an indulgence rather than a necessity. Even success can be damaging to the program: The plaudits earned from sensational cases heralded at the time as legitimate justification wane over time as the case winds its way through the criminal justice system, generating costly invoices for time spent in courts, not in stores.
Still, the concept continues to garner interest. For companies unable to fund advances in systems and technology and unwilling to bear the payroll cost of full-time, in-house store detectives, a contract store detective program can be properly honed to deliver presence, deterrence, and perhaps a quantifiable return on investment through the recovery of merchandise.
Independent Contractors and Consultants
Many retail companies operate with nominal LP staffing; some with only a single LP executive at corporate; others with a small field staff reporting into store operations; still others with none at all. These are generally smaller, regional retailers or growth companies poised to expand through acquisition, or distressed companies that have significantly downsized. As LP needs become realized, management often turns to independent contractors and consultants to provide expertise, guidance, and procedural development to fledgling LP programs.
The ranks of independent LP professionals marketing their services today include some of the best known and highly accomplished practitioners in the industry. They are often called upon to invigorate a company’s LP efforts, tasked with creating awareness and training programs, developing policy and procedural guidelines, and negotiating vendor contracts.
It is not unheard of for companies to have an LP professional on retainer, involved in internal audit and inventory control, store planning and construction recommendations, logistics at distribution centers, security planning for special events, and incident management. These are executive functions normally carried out by LP directors, but where that position does not exist, LP consultants have sought to fill the void.
The trend and the resource has by no means been lost on larger companies with fully developed LP structures. In many cases, LP contractors are engaged on a temporary basis to nurture special projects through the developmental stage, provide or augment specialized functions within IT or finance, or fill a crucial job position during an executive search process.
Consulting engagements tend to be costly, and as such, companies prefer a finite timetable for contract security projects. Seldom do consultants remain for extended periods in positions better suited to an executive employee.
As the business of loss prevention continues to evolve and expand, expertise becomes more compartmentalized. Outsourcing to independent contractors proficient in specialized areas of the retail business, loss prevention included, should remain a viable option for companies determined to improve shrink performance.
Counterfeit Currency
We all handle money everyday. The most tested way to tell if you have a counterfeit U.S. bill in your hand is to feel it. When you receive a bill in your hand and that bill feels “funny,” it’s time to look at a few other security features that are easily identifiable within the new U.S. bills. The following examples will utilize the $20 bill. The new $5, $10, $50, and $100 bills all have similar security features within them.
The most common “test” that we all tend to fall back on is counterfeit marking pens. They leave a nice golden mark on a “good” bill and ugly black mark on a “bad” bill. The problem with the pens is that they will fool with you. If I take a US $1 bill, bleach it out, and then print a new denomination, say $20 on the $1 bill I just bleached out, is the pen going to detect what I did to change that $1 bill to a $20 bill? No, it will not. So, your company just lost $19 because of a $2 pen doing the job it’s supposed to do.
Watermark portrait. If you look at the new color $20 bill, you will notice that there is a watermark portrait to the right of the seal. This portrait is of Andrew Jackson. Each denomination has a different portrait with corresponding watermark. Sometimes counterfeiters will bleach out $5 bills and print $20, $50, or $100 denominations on the bleached $5 bill. If a cashier uses the counterfeit pen and holds the bill up to a light and sees the portrait of Abe Lincoln, he or she assumes it’s a good bill. It is not. The presidential portraits are not interchangeable:
• Abe Lincoln’s portrait belongs on a $5 bill.
• Alexander Hamilton’s portrait belongs on a $10 bill.
• Andrew Jackson’s portrait belongs on a $20 bill.
The $1 and $2 bills do not have watermark portraits.
So far, we have used two security tests to test our bills, and we have still taken in counterfeit money. So now let’s move on to some really cool security features that are built right into the bills.
The color shifting ink test. In the lower right corner of the new bills there is a denomination (10, 20, 50, or 100) number. This number, when the bill is tilted up and down, will change the color shifting ink in that number from copper to green.
Security thread or plastic strip There is a security thread that is embedded in the bill and runs vertically up one side of the note. Using a unique thread position for each denomination guards against certain counterfeit techniques, such as bleaching ink off a lower denomination and using the paper to “reprint” the bill as a higher value note. The strip is easily seen when the bill is held up to a light. You should be able to see the words “USA TWENTY” or whatever denomination of bill it is and a small U.S. flag. The security threads glow different colors for different denominations under an ultraviolet light. There are several types of ultraviolet lights available to the general public. These ultraviolet lights are cool in that, when you put real money under the light, the security thread glows:
• The $5 bill security thread glows blue.
• The $10 bill security thread glows orange.
• The $20 bill security thread glows green.
In addition, credit cards also have their own ultraviolet glow under these lights. State ID cards and state licenses all glow under an ultraviolet light as well. For instance, when you hold a California driver’s license under an ultraviolet light, the California state seal glows. In addition, MasterCard, Visa, and American Express glow under ultraviolet light. These are security features that many people who handle cash don’t know about.
The symbols of freedom. Each denomination has a different symbol of freedom on the bill:
• The new $10 bill has two images of the torch carried by the Statue of Liberty printed in red on the face of the note. A large image of the torch is printed in the background to the left of the portrait of Secretary Hamilton, while a second, smaller metallic red image of the torch is found on the lower right side of the portrait.
• The new $20 bill has a large blue eagle in the background of President Andrew Jackson. There is a smaller metallic green eagle with a shield just to the lower right of his portrait.
• The new $50 bill has images that represent the American flag. The traditional stars and stripes of the United States flag are printed in blue and red behind the portrait of President Grant. A field of blue stars is located to the left of the portrait, while three red stripes are located to the right of the portrait. A small metallic silver-blue star is located on the lower right side of the portrait.
• The newest $5 and $100 bills currently in circulation do not have the Symbols of Freedom security features.
Micro printing. Micro-printed words are hard to replicate because they are so small. The new color bills have a lot of newly designed micro printing within the bills:
• The new $5 bill has this feature in two areas. The words “FIVE DOLLARS” can be found in the side borders on the front, and “The United States of America” appears along the lower edge of the portrait’s oval frame.
• The new $10 bill has this feature in two areas. The word “USA” and the numeral “10” can be found repeated beneath the large printed torch, and the words “THE UNITED STATES OF AMERICA” and “TEN DOLLARS” can be found below the portrait, as well as vertically inside the left and right borders of the note.
• The new $20 bill has this feature in two areas. Bordering the first three letters of the “TWENTY USA” ribbon to the right of the portrait, the inscription “USA20” is printed in blue. “THE UNITED STATES OF AMERICA 20 USA 20” appears in black on the border below the Treasurer’s signature.
• The $50 bill has this feature in three areas. The words “FIFTY,” “USA,” and the numeral “50” can be found in two of the blue stars to the left of the portrait; the word “FIFTY” can be found repeated within both side borders of the note; and the words “THE UNITED STATES OF AMERICA” appear on President Ulysses S. Grant’s collar, under his beard.
• The $100 bill has this feature in two areas. On the face of the note “USA 100” is repeated within the number 100 in the lower left corner. “The United States of America” appears as a line in the left lapel of Franklin’s coat.
Acceptance Policies. Acceptance policies will differ from retailer to retailer. Make sure you are within your policies and procedures on what to do if a bad bill is passed. Following are some general guidelines:
• If a bill is determined to be counterfeit, without putting anyone in harm’s way, you need to delay the passer of the bill in order to obtain as much information about the passer as you can. In other words, you need to become a very good witness.
• “I’m sorry, sir[ma’am]. I don’t have the correct change for this bill.” This is an example of a statement that you can make to the passer. Then secure your till and walk directly to your back room. Contact your LP department, manager, or supervisor, whomever your store policies dictate.
• If the passer insists on getting his or her bill back, without getting into any altercation, whether it be verbal or physical, state to the passer, “I’m sorry, sir[ma’am]; by law I cannot give this bill back until a determination has been made regarding the bill.” Say this once. If the passer insists or appears as though he or she will become combative or you feel threatened, give the bill back and turn into the best witness you can.
• If you can safely follow the passer to the parking lot and observe what type of vehicle he or she is driving or which direction of travel is used, do so.
• Immediately notify authorities (this is if the situation has become combative) and tell them what happened.
• If the passer stays in the store when you are in the back room and LP or supervisors are checking on the bill, call your local authorities and inform them of the situation if it is determined to be a bad bill.
• Do not call the Secret Service directly. They will be notified directly from local law enforcement depending the outcome of their investigation of the counterfeit bill.
• At no time should any retail employee, security, loss prevention, manager, or any employee get confrontational with a counterfeit passer. Some of these people are very nasty and are armed or otherwise very, very dangerous.
It has been my experience that a majority of counterfeit bills are passed by people who are ignorant to the fact that they have counterfeit bills. So as not to wrongfully accuse an innocent person of a crime, approach each incident with caution but respect to the person who passed the bill. With a couple of key questions to the passer, you will be able to tell by attitude and body language if this person actually knows why his or her bill has been confiscated. An innocent person will want to know why he or she can’t get any money for the bad money just passed. A bad person will run or will insist on getting the money back or will escalate the situation verbally (become loud) or physically (display weapon or become combative). Remember, this a worthless piece of paper. It’s not worth your life or the bad press your company could get.
Training posters, DVDs, VHS tapes, flyers, and pamphlets are all free for the asking and are great new hire orientation tools for cash handlers, LP, security, and anybody else who needs or wants to learn about our money. All of this material can be obtained from The U.S. Bureau of Engraving and Printing website (www.moneyfactory.gov/).
Courtroom Appearance and Testimony
Loss prevention agents engaged in detection and detention of shoplifters will invariably be summoned to court for the purpose of testifying against a shoplifter or dishonest employee. That past person stands as a defendant in a criminal prosecution and has pled “Not Guilty” to the charge upon which he or she was arrested and is now being prosecuted. The prosecutor represents the people of the state against the defendant and is the LP agent’s “attorney.” The defendant, with rare exception, is represented by a either a public defender or a privately retained defense attorney.
The trial will be either a “court” trial, i.e., will be heard by a judge only, or a jury trial, wherein the matter will be heard and decided upon by members of the community who serve as jurors, usually 12 in number, but there could be fewer than that number. The summonsing process is typically by way of the issuance of a subpoena.
In preparation for this appearance, the agent is encouraged to review the report of the incident the night before trial and again on the morning of the trial to ensure the details are refreshed and can be recalled while on the stand.
The agent should arrive at the court at least one-half hour prior to the court going into session and upon arrival enter the courtroom and seek out the prosecutor and introduce himself or herself. Commonly, the prosecutor will want to meet and talk to the agent who indeed will be the key witness in the trial. That prosecutor (e.g., deputy district attorney, deputy state attorney) will have a copy of the agent’s original report as well as the police department’s crime or arrest report. That meeting and brief discussion are most important because it will bring the prosecutor “up to speed” on the matter. This is but one of many cases each prosecutor must handle each week, so he or she needs this quick orientation. At some point the prosecutor will invite the agent to sit at the counsel table with him or her for assistance during the trial.
The agent should be dressed in business attire, preferably a suit and tie or, if a female agent, in a conservative skirt and blouse with a jacket. If evidence was retained by the store, the agent should bring such evidence to court and give it to the prosecutor for his or her use in the trial.
When the judge enters the courtroom, all stand until the judge is seated. When the judge calls the case, the prosecutor will answer “Ready,” as does the defense, and the trial is underway. If the agent is seated at the counsel table, he or she should sit with folded hands and exhibit focused interest on the proceedings without any animated expressions or body language.
The prosecutor will make opening remarks to the court and jury, outlining the case and inform them how he or she will prove the guilt of the defendant. The defense then makes opening remarks emphasizing the innocence of the defendant. The agent must refrain from smiling, winking, or rolling his or her eyes during this process, despite the compulsion to do so. This is dead-serious business.
In a criminal trial the “people” (prosecutor) put forth their case first, i.e., call all witnesses and present evidence until their case is completed. It is during the people’s case that the LP agent will be called to the stand.
When the prosecutor is ready for the testimony of the agent, he or she will announce, “The people call Robert Miller (the agent) as our next witness.” The agent gets up and approaches the witness stand, which is located next to bench (behind which sits the judge), and before taking the seat in the witness box, will be asked to raise his or her right hand a swear or affirm the testimony about to be given will be the truth. Once the oath is taken, the agent takes the seat.
The agent will be asked, typically by the court clerk, to state his or her full name and address. The prosecutor, who is now standing, will commence with direct examination. For the sake of this writing, there are four examinations, normally: (1) Direct, by the people; (2) Cross-examination, by the defense; (3) Redirect, by the people; and (4) Recross, by the defense. The witness may be subjected to more than one redirect and recross, depending on the complexity of the case and the testimony offered.
Once seated, the agent should look at the jury, recognizing their presence, settle back with clasped hands, not cross one leg over the other, and relax in anticipation of the process of questioning which is about to unfold.
Invariably, in a typical shoplifting prosecution, the prosecutor will commence by re-asking the witness’s name and then ask:
“What is your occupation, sir?”
“I’m a Loss Prevention Officer with Big Home Stores.”
“How long have you been employed with Big Home?”
“And were you so employed on January 7 of this year?”
“Do you recognize the defendant in this case, seated at the counsel table with his attorney?”
“When and where did you first see him?”
“I first observed him in the tool crib area of Big Home on Broadway Blvd. about 11:30 in the morning.”
“Yes, sir, January 7. I’m sorry.”
“Was he alone in the tool crib?”
“No, sir. There were several customers in the same area.”
“What attracted your attention to him?”
“I noticed he was continually looking all around, not paying any attention to the merchandise in his hand.”
Note the relatively short responsive answers. The agent should only answer the questions and not volunteer any information except to answer questions as succinctly as possible.
The answers are directed to the questioner, but from time to time, part of an answer can be made while looking toward a juror, just to keep them in the loop. There are schools of thought that all answers should be directed to the jury, but we believe there’s an artificiality to that strategy, so we encourage most answers be directed back to the person who propounds the question. Indeed, testimony is an exchange between counsel and the witness, and the jurors are like an audience who continually weigh, measure, and assess the exchange. The witness and counsel are as if on stage.
The agent must be aware he or she is in a glass fishbowl while in the witness box, and every move and every word are noted. Jurors are critical in their evaluation of each witness, and they, like most humans, tend not to like some people because of how they look or speak and, on the opposite side of the coin, tend to like others. And those they tend to like, they tend to believe more than those they don’t like. It’s a weakness of human nature. If you’re in this position, the message here is: Don’t do or say anything that could alienate yourself from a juror, including using slang or industry jargon, like I went out and “busted” him, or indicating in any way a bias or prejudice. Loss prevention agents testifying in the court system are expected to conduct themselves as professionals.
After the prosecutor completes questions about the involvement in the event, he or she “passes” the witness to the defendant’s attorney for “cross-examination.”
The cross-examination is a process whereby the witness’s credibility is challenged.
“Now, Mr. Miller. You’ve told us you’ve been employed with Big Home for 22 months. Is that correct?”
“And you’re a loss prevention officer. Is that correct?”
“Now, you arrested my client in January, which is 7 months ago, correct?”
“So, at the time of this incident, you’d been an employee of Big Home for 15 months, is that so?”
“Now, when you were originally hired by Big Home, was your first assignment with Loss Prevention?”
“No, sir, I was hired as a sales associate in the garden shop.”
“In the garden shop as a sales associate! That’s interesting. So how long did you work in the garden shop before you went to Loss Prevention?”
“A year! So let’s see. You were a Loss Prevention Agent for only 3 months at the time you arrested my client. Is that correct?”
“When you were transferred into Loss Prevention, did the store send you to any outside training classes or school to be a Loss Prevention Agent?”
“On the job training. It means I worked alongside an experienced agent, on the job.”
“Who was that agent? What was his name?
“How long had John Mann worked at Big Store?”
“Did he train you in understanding the laws of arrest in this state?”
“He and I focused on the rule of when I can stop someone and when I can’t.”
“But you don’t know the statute detailing the laws pertaining to citizen’s arrests, do you?”
“No, sir, not by the legal code section or whatever.”
“Ever taken any college courses in criminal justice or criminology?”
Attorneys who engage in cross-examinations employ tactics which tend to unnerve and fluster witnesses in hopes they’ll get angry or otherwise do or say things which undermine their credibility in hopes of persuading the jury the witness isn’t telling the whole truth. Clearly, in the preceding exchange, the defense counsel is attempting to paint the agent as new, inexperienced, untrained, and unqualified to engage in this very complicated business of arresting customers. Bottom line: The attorney’s goal is to discredit the witness’s qualifications and his or her version of what transpired, leading, the attorney hopes, to an acquittal.
Hence, the agent undergoing cross-examination must remain calm, must not become argumentative, and must not glare at the attorney.
Two fundamental rules in testifying are as follows:
1. Always tell the truth, the absolute truth.
2. Don’t get sassy or argumentative with the opposing attorney. The defendant will win and you will lose.
Once the cross-examination is completed, the prosecutor may choose to exercise the right to engage in a redirect examination. Redirect examination is exercised when the prosecutor wants to clarify a point and expand on what was testified to on cross-examination, or to rehabilitate the witness.
“Rehabilitation” means to “rescue” or “patch up” something the witness said or failed to say which could prove pivotal in the jurors’ assessment of his or her qualifications or conduct. With respect to the apparent “success” of the defense attorney, as noted previously, the prosecutor could “rehabilitate” the witness, as follows:
“Mr. Miller, you’ve told the jury you underwent OJT training and explained it was working along with an experienced agent. Correct?”
“During that period of time, did your OJT training include any classroom sessions in the store about shoplifting matters and what the company required?”
“Did the classroom sessions include interactive video scenarios which tested your understanding of the company’s rules about detaining people for shoplifting?”
“And was it your understanding the rules of the company are based on state laws?”
“And how many classroom instructional hours did you undergo,
“Was your OJT, aside from the classroom instruction, structured in various experiences and exposure to policy and procedure?”
“Did that structured training experience lead to some form of certificate or recognition?”
“What did it lead to? I mean what was the end result of all this?”
“I earned company certification, and that certification qualifies a loss prevention agent to detain customers for theft if the elements of theft are present.”
When both sides have exhausted their examination of the agent, the court (judge) will excuse him or her and ask the witness to step down. The agent may say, “Thank you, your honor” and leave the witness stand and return to his or her seat at the counsel table.
It is the responsibility of the prosecution to prove their case beyond a reasonable doubt. Although the defense is not required to put on a case (call witnesses), more often than not they do. The key witness, aside from the LP agent, in a shoplifting trial is the defendant, who will deny any intention to steal, offering a fabricated version from a wide variety of spins and explanations to overcome the prosecutor’s accusation of theft. It is during this testimony when the agent can damage his or her own case, by reacting inappropriately to the defendant’s version of what transpired in the store. The damage is done by body language, i.e., raising eyebrows, smiling, sneering, raising the eyes to look upwards, rolling the eyes, shaking the head, or otherwise using his or her facial flexibility to silently express himself or herself. Someone on the jury, if not most jurors, will see this and usually take exception with it, considering such reaction unprofessional.
When both sides in this judicial confrontation rest, the jury will retire and deliberate. So-called facts are considered, but other factors come to bear on the final collective decision, including the appearance and presentation made by the loss prevention agent.
There’s much more than a win-or-lose battle between a shoplifter and LP agent here: A verdict of “Not Guilty” often opens the door for a civil suit against the store for arresting a person “not guilty” of any crime. Damage awards from such cases can be substantial.
Crime Prevention through Environmental Design (CPTED)
Introduction
Crime Prevention Through Environmental Design (CPTED) is a practical concept that has received considerable interest during the past four decades. It is based on the theory that the proper design and effective use of the built environment can lead to a reduction in the incidence and fear of crime, and to an improvement in the quality of life. This concept is supported by the fields of geography, psychology, and criminology, where it has long been known that
1. The design and use of the physical environment
2. Affects the behavior of people
3. Which influences the productive use of space
4. Leading to an increase or decrease in exposure to crime and loss
CPTED has been used to reduce crime, premise’s liability, and fear in a variety of settings. They include schools, neighborhoods, convenience stores, malls and shopping centers, parking structures, transit sites, hotels, hospitals, office buildings, and parks. There are state statutes, regulations, and safety standards that have been developed to promote the use of CPTED concepts. It is important to note that CPTED does not replace traditional approaches to crime and loss prevention. Moreover, it is a tool that helps to remove many barriers to social and management control.
The use of CPTED concepts requires that human activities and spaces be designed or used to incorporate natural strategies. Crime prevention has previously relied nearly exclusively on labor-intensive or mechanical approaches. Guards, hall monitors, and police patrols are examples of labor-intensive strategies. Security cameras, locks alarms, and fences are examples of mechanical approaches. These methods incur costs that are additional to the normal requirements for personnel, equipment, and buildings that are needed to carry out human activities. The four most common CPTED strategies are
Natural surveillance and access control strategies help to limit opportunity for crime. Examples include the placement of windows to overlook sidewalks and parking lots, the use of transparent weather vestibules at building entrances to divert persons to reception areas, the placement of employee work stations in open areas to increase the perception that these locations are being monitored, and the use of maze entrances in public restrooms to decrease the isolation that is produced by an anteroom or double-door system for entry. These concepts increase the perception that people can be seen by others and that there is a clear difference between public and private space. Potential offenders are made to feel at greater risk of scrutiny and that their means of escape are limited.
Territorial reinforcement promotes social control through a variety of means. They include an increased definition of space, improved proprietary concern, expanded sense of ownership, and enhanced activity support and motivation reinforcement. These objectives may be achieved by increasing the assignment of space to the normal users and reducing public or unassigned locations. Residents or desired users of space who participate in the routine maintenance of space increase their proprietary concern through “sweat equity.” Placing amenities such as seating or vending machines in common areas helps to attract larger numbers of normal or desired users of these areas. Scheduling activities in common areas increases the proper use, attracts more people, and increases the perception that these areas are under control. This makes the normal user feel safe, and the potential improper or undesired user feel at greater risk of apprehension or scrutiny.
Effective management and maintenance of activities and locations are crucial. Well-managed and maintained spaces have greater return on investment. A well-planned activity will result in fewer unanticipated problems. A well-maintained site will have fewer repairs and interruptions to scheduled activities. Accordingly, there will be fewer exposures to crimes and losses.
CPTED Historical Precedence
CPTED has its origins in the early history of the development of communities. The conscious planning of human habitats to include identity and protection goes back as far as our knowledge of human existence. Eighth century Chinese practitioners of Feng Shui promoted the design of harmony in space, from the size of the smallest rooms up to the planning of cities. Eighth through eleventh century plains dwellers in North America developed hierarchies of family places, community identity, and protection through the design of living space. The cliff dwellers (U.S. Mesa Verde National Park) developed impregnable living areas on the faces of cliffs that were accessible only by ladders and entrances that could be sealed. The cliff dwellers are also important examples of early attempts to use passive environmental engineering for climate control.
Modern warfare demonstrated how design can obviate technological and numerical superiority in the City of Hue, Viet Nam, and in Kuwait City, Kuwait. Both cities were of traditional French design with twisting, narrow streets that allowed for a small number of defenders to block the movements of large numbers of opposing troops. Post WWII residential development replaced grid pattern streets with curvilinear streets, which (in some settings) has improved safety, security, and neighborhood identity and property value.
CPTED Strategies
Many CPTED practitioners use the following strategies to guide their assessments of space and conceptual approaches to design:
• Provide clear border definition of controlled space
• Provide clearly marked transitions from public to private space
• Place gathering areas in locations with natural surveillance and access control
• Place safe activities in unsafe locations
• Place unsafe activities in safe locations
• Provide natural barriers to conflicting activities
• Improve scheduling of space to allow for “critical intensity”
• Increase the perception of natural surveillance
• Overcome distance and isolation through improved communication and design efficiencies
Related Topics
A number of related concepts have often become confused with the CPTED operating theories and applications. Some of these concepts overlap with CPTED, whereas others are very different. Following is an explanation of the unique elements of the related concepts:
• CPTED (Mechanical vs. natural approaches): There is some confusion and competition within the CPTED movement. It mostly boils down to one group that casually blends the three strategy areas (organized, mechanical, and natural approaches) versus another group of specialists whose principal emphasis is on natural approaches. The former is more of a crime control model, whereas the latter may be conceived as a planning model.
• Defensible Space: This concept was developed in the public housing environment. It is similar to CPTED in that it shares the basic requirements of natural surveillance, natural access control, and territorial concern. CPTED in its modern form was developed as an extension of Defensible Space concepts to commercial, retail, industrial, institutional, and low-density residential environments.
• Environmental Security: This concept was developed on a parallel basis to CPTED. It was initially used in residential settings. Environmental Security differs from CPTED in that it contemplates the use of a broad range of crime control strategies, including social, management, target hardening, activity support, and law enforcement.
• Security by Design: This concept is most aligned with a repackaging of solid security engineering, physical security, and procedural security measures to provide improved emphasis in the design process.
• Natural Crime Prevention: This concept grew out of the CPTED emphasis on natural strategies, those that factor behavior management and control into the design and use of the built environment.
• Safer Cities: This is another spin-off of CPTED that attempts to define an approach to crime prevention that incorporates traditional crime prevention and law enforcement strategies with CPTED. Of course, CPTED planners know that CPTED does not replace other crime prevention strategies, but that a high priority should be placed on natural strategies that take advantage of how human and physical resources are being expended.
• Situational Crime Prevention: This concept is much more comprehensive than CPTED because it incorporates other crime prevention and law enforcement strategies in an effort that focuses on place-specific crime problems.
• Place-Specific Crime Prevention: This is just another name for situational crime prevention and environmental security.
• 2nd Generation CPTED: This is a program title that was popularized in the mid-1990s by a new group of CPTED enthusiasts. The supporters seek to combine community involvement, a youth component, and other crime prevention strategies with CPTED concepts. This approach is essentially the same as the Environmental Security and Safer Cities programs.
It is clear from a review of these apparently competing concepts that they overlap and are extremely compatible. Many were developed to provide a vehicle for incorporating organized and mechanical strategies into a free-standing model. However, most long-time CPTED planners view CPTED as a small subset of the total set of things that have to be done in crime prevention and control. Criminologists know that a comprehensive system must include strategies on a continuum that ranges from prenatal care to dementia among elderly persons. It would be unconscionable for anyone to think otherwise.
Following are some of the many examples of CPTED applications:
• Weaving pathways or roads are preferred; they promote a wider field of vision for observation because of the need to maneuver.
• Offset-glass-lined store entrances in malls and shopping centers deflect SHA and increase visual access to identify the store and observe activities.
• Bay-type windows increase visual access to and from sidewalks and streets, promoting visual ease and harmony and increasing the perception of natural surveillance.
• Theater, meeting room, or classroom doors that open outward allow easier egress for life safety reasons.
• Eliminating sharp edges on buildings and corners in hallways is helpful. Round or curving edges result in increased comfort, wider fields of vision, and increased perception of surveillance.
• Landscaping which obscures windows and the pedestrian approaches to buildings reduces natural surveillance.
• Enclosed elevators may create anxiety; a glass-back elevator or one with mirrors on the back wall improves comfort; it also allows the potential user to see if anyone is inside and increases natural surveillance.
Visual Bubbles, Landscape, Art, and CPTED
Human beings are born with natural responses to certain environmental stimuli. Others are learned within the context of culture, education, training, and experience. Tests with newborn humans and animals reveal that they inherit natural responses to visual stimuli. For instance, when newborns are shown a film wherein they are approaching the edge of a cliff, the subjects will automatically react when they think they are going over the side. Visual stimuli are some of the most important to humans, but by no means are they mutually exclusive of other forms of perception.
Humans establish “visual bubbles,” which vary in depth, height, and width according to territorial definition and geography. A visual bubble may be defined as that space in which a person consciously recognizes things within the environment. Most environmental cues are dealt with subconsciously outside the visual bubble, unless something unusual happens to bring one of these elements to a conscious state.
Why is this important to a study of CPTED? The answer is that the visual sense scans the middle and far environment to collect information for immediate survival and protection. Environmental cues are assessed by all of human perceptual systems. But, the visual sense provides information about hazards, way finding, identity, and attractions For instance, highway safety is almost totally linked to visual perception. Traffic engineers know that certain locations have a high volume of accidents. Other locations seem to induce excessive speeds.
Following are some examples of the importance of planning for visual space in CPTED:
• Downtown pedestrian malls and regional retail malls quite often use landscape elements and sitting areas to push customers closer to businesses in the theory that they will be more likely to make a purchase if they are within the zone of influence of the business.
• The height of ceilings in hallways and meeting rooms has a direct relationship to attentiveness and movement; low ceilings suppress behavior, and high ceilings tend to stimulate activity and attention, which may be important to managing behavior.
• Transitional landscaping on curving portions of walking and bike trails increase the depth of vision and provide the user of this space with more information and choices regarding safety hazards or criminal threats.
• Wider porches in front of convenient stores help to give the customer more choices to avoid potential contact with nuisance persons, thus increasing sales to adult customers who would avoid the store if they had to encountered juveniles or day laborers.
• Towers and spires on buildings located on corners or intersections help in a way of finding and relieving anxiety about distances and identification of places.
• Opaque enclosures of trash receptacles and loading docks will dominate the field of vision of a passerby; conversely, transparent fencing material used in screening of trash receptacles and loading docks will cause these areas to fall into the background, which is precisely what the designer intended.
• Hostile landscaping can reduce maintenance costs and prevent graffiti and unwanted entry to properties.
• Landscaping helps to identify borders between public and private spaces; it also helps to reinforce the definition of desired behaviors by defining movement areas.
CPTED in the United States
Early interest in CPTED began with the research of Jane Jacobs in her book The Death and Life of Great American Cities, published in 1961. Jacobs described many observations of the relationships between urban design and crime. Her work stressed the importance of increasing territorial identity and natural surveillance.
Oscar Newman demonstrated the importance of natural surveillance, access control, and territorial concern in his 1972 book, Defensible Space. Newman proved that a relationship exists between space management and design and crime in public housing environments.
Dr. C. Ray Jeffery coined the phrase “Crime Prevention Through Environmental Design” in his 1971 book by that title. Jeffery described the relationship between urban design and crime. His book provided quotations from a 1968 report from the National Commission on the Causes and Prevention of Violence (USA) that warned the American public of the direct relationships between urban design and crime. This commission studied the massive urban violence and racial unrest that had occurred in U.S. cities between 1964 and 1968.
Richard Gardiner, a landscape architect and developer, successfully demonstrated the use of CPTED concepts in residential areas. His 1978 manual, Design for Safe Neighborhoods, presented the results of a successful project in a Hartford, Connecticut, neighborhood, which significantly reduced crime and improved the quality of life.
The most significant CPTED developmental effort in the United States was conducted from 1972–1980 by the Westinghouse Electric Corporation through a massive contractual effort that was funded by the U.S. Department of Justice. Westinghouse managed a large group of consultants and subcontractors who were responsible for adapting CPTED concepts that had been proven in public housing environments to retail, transportation, and school environments. Much was learned from these efforts, which provides the basis for current CPTED uses in the United States.
Interest in CPTED at the U.S. government level waned during the decade of the 1980s. However, state and local units of government took over the lead and produced a large number of successful projects. These led to the incorporation of CPTED into local building codes. Design review ordinances have been modified to require the use of CPTED in building design. Several state governments have passed legislation and developed new regulations governing the design and management of schools and the convenient food store industry. The states of Florida, Virginia, and Kentucky have taken the most steps by passing legislation and actively conducting training for the public and private sectors.
The National Crime Prevention Institute at the University of Louisville created the first CPTED training program in 1985. A design studio was created to assist in the teaching of CPTED concepts. This program has been attended by thousands of participants who have spread the use of CPTED concepts in their communities around the world. The content of this training program formed the basis for the 1991 book, Crime Prevention Through Environmental Design: Applications of Architectural Design and Space Management Concepts, by Timothy D. Crowe. This book—and its second edition (March 2000)—is the most widely used manual for CPTED at the present time in the United States.
The American Institute of Architects conducted the first national CPTED conference in December 1993. The U.S. Conference of Mayors conducted a National CPTED conference in June 1995 to report on the results of their nationwide survey of mayors. This survey documents the extent to which local governments have implemented CPTED concepts.
Results of CPTED
There are many case studies, which demonstrate reductions in crime and fear of crime. Significant results have been produced in many settings, including residential areas, convenience food stores, malls and shopping centers, transit stations, and parking structures. Journal and newspaper articles have reported on these successes.
Descriptive studies have reported on historical relationships between crime and the environment. The U.S. Department of Justice has published a number of bibliographies and documents about these observational studies. Small to medium-size cities have also reported on considerable crime and fear reductions directly attributable to CPTED traffic management strategies.
Statistical results are too numerous to list here, but it is clear that much documentation exists. Moreover, the historical basis of CPTED makes the success of these concepts self-evident. Following is a sample of the many success stories that have resulted from contemporary uses of CPTED concepts:
• Convenience Stores: Such stores have used CPTED to increase sales and reduce losses of up to 50% of thefts and 65% in armed robberies.
• Malls: Malls in Sacramento, California, and Knoxville, Tennessee, have reduced incidents by 24% and noncrime calls to police by another 14% using CPTED parking management concepts. Many others have achieved the same or better results. The Mall of America in Bloomington, Minnesota, used CPTED from the initial conceptual stage of design; the same or better results have been obtained by many other malls.
Author’s Comment: One of the authors was involved in the opening of a major retail store in the Mall of America. During the building of the store, the author had to meet with the Bloomington Police Department CPTED specialist to assure that the store design and security features were in compliance with the police department’s CPTED standards. Some of their concerns were the location of the cashiers’ (cash) office, emergency egress from the cash vault area, and assuring easy access for police officers from access roads to the security office when responding to requests for service.
• Corporations: Westinghouse, IBM, Mobil, TRINOVA, Macy’s, Disney World, Sam’s Club, and Pace Wholesale Warehouses have reduced losses and improved productivity using CPTED strategies.
• Office environments: Interior design research has determined that the lack of territorial identity in the office space contributes to lower morale, less productivity, and greater tolerance of dishonesty among fellow workers.
The Need for CPTED
Profit, productivity, and quality of life are compelling reasons for the use of CPTED concepts. A key element in the CPTED planning process is to develop clear behavioral objectives for spaces. This leads to improved decisions regarding design and use techniques. Civil liability provides a legitimate excuse to use CPTED concepts, that is, if improved profit, productivity, and quality of life are not enough. The U.S. Department of Justice has issued guidelines for the use of CPTED concepts to protect businesses from wrongful death or injury litigation.
The recent case law in general and premises liability has increased the responsibilities of property and business owners. Liability has been extended to architects, engineers, lending companies, and security contractors, when a wrongful injury or death suit is filed. Parking lots have been found by courts to be inherently dangerous, which means that an owner or operator is liable even when there have been no prior incidents. Likewise, the isolation of restrooms by location and by design has been determined to be inherently dangerous. The standard by which a property owner or operator is judged is based on proof of due diligence or having done all things reasonable to prevent injury. Employee, owner, and customer convenience is perhaps the greatest obstacle to maintaining safety and security in retail environments. More accidents and victimization are caused by the defeat of good security practices due to inconvenience than any other hazard. It is worse to have procedures that are not followed than to have none at all.
New properties and operations are held to a different standard than existing ones. The designer, planner, and owner of a new property or operation will be held accountable for conscious decisions that affect the propensity for subsequent injury. Accordingly, a final decision about the design and use plan for a property must be defensible. The opinions of a recognized expert in the substantive area of the loss, peril, and hazard establish proximate cause, which then makes injury foreseeable.
The so-called test of reasonableness that is the backbone of civil liability allows for the support of many factors in making conscious decisions. Aesthetics, mission, life safety, accessibility, feasibility, and environmental factors are weighed in the final determination of the adequacy of a property owner’s or manager’s duty and responsibility in the care and protection of the users of space. This is why CPTED has become so important to the civil law, because it allows for the blending of good aesthetics, profitability, and safety.
The Future of CPTED
CPTED in the 21st century will emulate the lessons from the past. The first decade has already been a transition period heralding an explosion of technological and space management advances in the use of the environment to promote behavior that is desired and conducive to human existence.
CPTED is a self-evident concept, which has been used successfully for the past 40 years. It has confirmed what many people think—that it is just good, common sense. The greatest impediment to the widespread use of CPTED is ignorance. Many people have never heard of CPTED. Some of the few who have heard of CPTED have attempted to exploit it, without developing an understanding of the concept. Others have attempted to pass off CPTED as another fad that will go away with time.
Note: For additional information on the role of CPTED, see the April 1996 issue of National Institute of Justice, published by the U.S. Department of Justice, Office of Justice Programs, discussing CPTED as applied to parking facilities and to premises liability.
Crisis Management
The time that crisis management will be required cannot be predicted; hence, the key to successful crisis management is preparation and planning for that eventuality.
Since retailers operate businesses which have members of the public on their premises during business hours, as well as employees during both business and nonbusiness hours, it becomes vital that plans exist to minimize injury to both customers and employees, as well as to protect the other assets of the business during emergency situations.
The start of the preparation process is the formation of a crisis management team and the formulation of their mission and responsibilities.
The purpose of a crisis management team (CMT) is to have a designated group of individuals who, in the event of a major emergency or crisis, are empowered to make decisions and authorize extraordinary action on behalf of the corporation. In general, a crisis exists whenever there is a business-related clear risk of life or grave personal injury to a company employee, a member of his or her family, or a customer or other person, or when some disastrous or calamitous event occurs which disrupts the essential processes of the corporation and threatens its ability to function.
In the event of a crisis, the CMT may be activated by any member; those immediately available from the total membership will then form the CMT.
Because of the extraordinary authority to act independently in the event of a crisis, and the potential for civil liability and/or just plain “finger pointing” based on any actions taken by the CMT, it is essential that the individuals comprising this group be of very senior rank, including the Chief Executive Officer (CEO), Chief Operating Officer (COO), Chief Financial Officer (CFO), Chief Security Officer (CSO), Executive Vice President (EVP), and other senior vice presidents. Both the senior HR person as well as the senior civic affairs or publicity person should be included, since many anticipated actions will involve personnel decisions and/or the need for press releases. Corporate counsel should be included on an ad hoc basis.
A final key component of the CMT (although not a decision-making member) is a recording secretary. From the moment the CMT is activated, the secretary (or someone else in his or her absence) should begin making minute-by-minute notes of the various decisions and actions of the CMT and any factors (such as recommendations by an expert) prompting such actions. A portable battery-operated audio recorder is a valuable aid in keeping such a record.
The CMT should be unfettered to the maximum possible extent in the exercise of their extraordinary responsibilities. However, because reliance upon expert advice is a defense to charges of unlawful or negligent conduct in such matters, early and continuing cooperation with appropriate law enforcement or other public safety agencies should be part of the CMT’s operating procedure, recognizing, however, that normally the CMT will be responsible for the ultimate decisions made.
In any crisis, communications assumes paramount importance. With this in mind, the establishment of a predesignated message center is mandated. Such a message center should also have an alternate location should the primary location be within the area of the emergency and unavailable for occupancy. Whenever the CMT declares a geographically large area as within the emergency zone, a pre-established toll-free (800) number should be activated for emergency use.
The CMT should have primary responsibility for
• Assisting stores in management and decision making during an emergency
• Assuring that individual stores are prepared for emergencies by reviewing individual store emergency plans for currency
• Making policy decisions on a companywide basis prior to an emergency
• If time and circumstances permit, reviewing decisions to close/evacuate a store
• Handling public relations following an emergency
• Determining the degree of aid to victims of an emergency
• Coordinating emergency transportation and storage for the protection of cash and target merchandise
Finally, the CMT should be responsible for a post-event review to determine any weaknesses in pre-emergency planning and making recommendations for corrections to and/or modification of existing plans.
Customer Accident Investigations
Why care so much about retail accidents? Slips and falls and other forms of injury cost retailers millions of dollars each year. So, it’s only logical to know how to respond properly to such incidents.
Types of Accidents/Injuries
When the topic of customer accidents is brought up, slips and falls come to mind. These may be the most common types of accidents, but retailers need to be mindful of other causes, such as
Purpose of Investigating
Why did the accident occur? What was the cause? The more detailed, the better. Any and all information can be used to help prevent future injuries. A thorough investigation can often limit the company’s liability and can expose fraudulent claims. But what I’ve found to be common is to find the truth in a claim that has been overly exaggerated from what actually happened. Detailed accident investigations will help lower a company’s annual loss.
Investigative Steps
So, you’ve been notified that an accident or injury has occurred. What now?
Step One: Speak with the injured person. I’ve always encouraged my loss prevention agents to always carry a pen and notepad while on the sales floor. That way, they can respond immediately without having to search for a notepad. Besides, showing up at the scene with a legal pad and clipboard could signal to the customer that this is a more serious situation than he or she thought. Your first duty is to make sure that the customer doesn’t need any medical attention. Listen carefully to his or her entire side of the story; then ask any open-ended questions that will help fill in any gaps. Next, ask the customer if he or she would like to make a report. If so, pull out your pen and notepad and jot down the customer’s name, phone number, address, age, date, time the accident occurred, exact location, and note the type and condition of shoes. The type or condition of shoes could be an important cause of the fall.
Step Two: After you’ve spoken with the customer, locate any possible witnesses. The witness could be an employee or customer who happened to be in the area of the accident. If the witness is a customer, get his or her side of the story, obtain his or her phone number, and ask if he or she may be contacted if any further information is required. If the witness is an employee, have him or her write a statement on a legal pad and sign it.
Step Three: Secure the scene. This will ensure that no other customers will be injured and will also protect any evidence of the accident. Immediately take pictures of the area using multiple angles. Every loss prevention or safety department should have a digital camera of at least 3 megapixels. This is enough to allow you to enlarge an image without degrading the clarity. A standard 35 mm camera will work as well; however, development and enlargements will have to take place offsite and could take up valuable time. Most of the time you will not have to bother with a tape measure at the scene. Most stores use tile flooring that is 1×1 foot in size and will allow the investigator to make approximate measurements.
Step Four: Compile your data. Now that you’ve collected the necessary information, write a narrative of your investigation starting with your interview with the customer. Do not quote the customer within your narrative. You should use another part of your report for the customer’s statement. On the report form, include your narrative, customer statement, accident scene observations, and the customer’s biographical information that you obtained during your interview. Print and attach photographs of the scene and save the photos to a disk to be included in your accident file or separate storage area. During this process, you should also search your store’s camera system to see if it captured the accident. If any video is captured, immediately copy this to disk or tape. Finally, contact your company’s insurance company or risk management department. Let them know at that time if you’ve captured the accident on tape or if you suspect that the accident claim is fraudulent or has been exaggerated. Also, if the accident was caused by a product or display fixture, hold it as evidence until risk management or the insurance company has given you permission to dispose of it.
The work you put into each investigation will serve you for some time to come. Accidents should be reviewed monthly with management. Discuss how these situations could have been prevented and implement these ideas to prevent further accidents.
Cybersecurity Rules for the Retail Industry
A history of the retail industry shows a clear relationship between the creation of a new technique to help customers make a purchase and criminals using that technique in order to steal. Whether it was the introduction of electricity in stores, locating shopping centers so they would be convenient for car drivers, or creating phone catalog sales for shopping at home, customers and criminals were both attracted.
Today, retail computer and communication advances are making shopping for customers easier, faster, and readily available around the clock. In a similar fashion, computer criminals have learned to take advantage of these advances in ways that threaten our central commercial arrangements, such as using credit cards, and even the identity and privacy of the public. It should also be noted that cyber crimes committed by companies, such as stock manipulations and scamming efforts, have also used technology for illegal purposes.
While earlier retail crimes were responded to with a combination of physical security and monitoring actions, loss absorption, industry cooperation, and legal sanctions, those options may not be sufficient for meeting computer-related crimes. These crimes are more complex than earlier crimes and require retailers to increase security efforts to a much larger and a much different level.
This section will review the nature of these cyber crimes in general and then discuss those cyber crimes specifically related to the retail industry. After that discussion, cybersecurity issues will be analyzed, followed by a presentation of the cybersecurity program elements that need to be found in retail settings.
Introduction
Let’s start with general cyber crime statistics. The following are some indications of the seriousness of the problem.
In 2006, at least 303 incidents of data disclosures in the United States were reported, potentially affecting 18.8+ individuals. Approximately 30%, governmental or military agencies; 27% of disclosures involve educational institutions; 23%, general business; 12%, healthcare facilities or companies; and 8%, banking, credit, or financial services entities. (1)
Identity theft has become of major concern to people. And they are right to worry, as indicated by the following statistics. A survey conducted by the Federal Trade Commission (FTC) in 2006 estimated that 8.3 million American consumers, or 3.7% of the adult population, became victims of identity theft in 2005. Most of the financial losses are suffered by credit issuers and banks, as victims are rarely held responsible for fraudulent debts incurred in their name; however, victims often bear the responsibility of contacting their banks and credit issuers after an identity theft has occurred. The same FTC survey determined that victim consumers spent over 200 million hours in 2005 attempting to recover from identity theft. (2)
• “New account” identity theft costs over $25 billion in losses to the victims each year.
• Of the new accounts that are opened by identity thieves, approximately half are credit card accounts, but cell phone accounts, utility accounts, bank accounts, and apartment rentals are also important targets for identity thieves.
• Between February 2005 and March 2006, more than 55 million Americans were put at risk by security breaches, leaving them vulnerable to identity theft. (3)
Even the period of time between when a computer comes online and when it is probed for vulnerabilities has shrunk. An example is found in a study from a major cybersecurity research center. Researchers took an out-of-the-box Linux PC without any special features, connected it to the Internet, and did nothing to announce its existence. The attacks started almost immediately.
|
First service probes/scans detected. First compromise attempts detected. Administrative access was obtained. Event logging was selectively disabled. System software was modified to suit the intruder. Attack software was installed. The PC was actively probing for new hosts to intrude. (4) |
Cyber crime has evolved over a relatively short period of time. Starting in the 1980s, some of the early crimes were often unsophisticated, involving methods of guessing, stealing or “social engineering” passwords, gaining physical access to machines, or relatively easily bypassing security controls. As this form of crime advanced, criminals learned how to misuse the technology in order to gain access to computer resources, services, and information. That stage of evolution involved hackers and others who were familiar with vulnerabilities of systems and the use of social engineering to manipulate authorized users. When increased protections were implemented by information security professionals, intruders expanded their illegal activities to cover a larger range of damages, such as distributed denial of service, virus destruction, and scanning of a user’s remote access to their organizations.
Currently, there are widespread malware intrusions, including spyware and spamming, while others seek to take advantage of users by means of phishing and identity theft. As wireless communication has grown, attacks on wireless devices have become more frequent. Some of the newer attacks are automated, attention is being directed toward drivers, and thumb drives have become useful crime tools. (5) (6)
There have also been increases in the impact of cyber crimes, creating damage to companies, customers, and the larger society. These damages are like pebbles thrown into water, expanding out from the initial point of contact. There are direct and indirect costs involved with a publicized unauthorized incursion into a company’s system. Research findings on these costs indicate that retail firms which have been attacked are penalized financially as well as in terms of customers’ willingness to continue to shop with them.
• According to a recent study, companies experiencing a data breach spent
• Another study found that customers view trustworthiness in safeguarding information as an important factor in their decision where to shop. While less than half of their consumer respondents rated organizations as particularly trustworthy in safeguarding private information, there were large differences between sectors. Financial institutions, healthcare providers, and law enforcement agencies were seen as the most trusted (60%, 56%, and 53%, respectively), while online Internet retailers (32%) and brick-and-mortar shops (28%) were considered the least trustworthy. (8)
• Related to the trustworthiness, firms which have been publicly exposed for having lost personal information lose an average of 2.6% of their total customer base. Note that under the California Database Protection Act (CA SB 1386) and similar laws being proposed in over 30 other states, organizations must report to affected persons when their information may have been stolen. Of great significance is the effect of a loss on the financial markets. On average, a firm loses around 0.63% to 2.10% value in stock price when a security breach is reported. (9)
The lessons are quite clear. Technology has become a major tool for criminals. They can attack retail companies, targeting them for money, stock manipulation, ransom, trade secrets, customer lists, competitor espionage, or entrance to the larger financial complex within which the company operates. The damages can be severe and may lead to such drastic events as the bankruptcy of companies.
Cyber Crimes in the Retail Industry
Whether it is called “computer crime,” “data crime,” “information protection,” “cyber crime,” or countless other terms, the issue discussed is how computers and other high-tech devices are used to gain unauthorized use of information and other assets. The term used here will be “cyber crimes.”
These crimes are unique from earlier retail security problems. There are three major new aspects to these crimes that make them so distinctive:
• New crimes: Traditional retail crimes, such as inventory shrinkage and fraud, have become computerized. This has created new threats, risks, and vulnerabilities for the use of criminals. Cyber crimes are growing, while responses to them continue to lag. Technical security continues to be difficult to achieve and expensive to implement. In addition, these crimes have produced difficulties for the law and law enforcement. Legal approaches to these crime problems result in legislators creating laws regarding rapidly changing technical factors. Law enforcement and prosecutors are faced with the need to adapt their approaches in order to develop legally acceptable cases.
• New criminals: The cyber criminal includes teenagers, organized criminal gangs, competitors, political activists, managers, IT professionals, and others. Some are technically skilled, whereas others may not be so expert but have knowledge, access, and opportunity. The criminal has the advantage in when to strike, what to attempt to strike, how to attack, what system vulnerabilities to take advantage of, how to cover electronic fingerprints, and the difficulties of detecting and prosecuting these acts. Internal crimes are made easier by employee knowledge of financial transactions, security measures, employee inexperience, and the wish of companies to minimize security costs.
• New dangers: Beyond the tempting financial targets, there is also a multitude of potential dangers for a company. These dangers have increased as companies have become dependent on technology in order to function. For retail organizations, outsiders could aim to close down a major computer service; make subtle changes to profit and loss data; exert control over certain key applications; or manipulate the computer functions that run a building’s air conditioning, water, heat, and electricity. With the Internet, a globalization of specialized criminals has also developed, leading to an international division of labor and crime easily crossing national borders.
Retailers face increased competition and difficulties in making profits. Cyber crimes are causing the industry to have to decide on how best to survive this additional problem. The cybersecurity discussion to follow will indicate the fundamental choices that will have to be met.
Cybersecurity in the Retail Industry
Some recent retail computer crimes provide us with important lessons about the need for cybersecurity. TJX, BJ’s Wholesale Club, and DSW are not the only retailers that have had security difficulties, but their very public problems appear to be leading to the creation of additional laws and regulations over how a company processes and protect data. As indicated in the Sarbanes-Oxley Act and Gramm-Leach-Bliley Act, business violations are leading to cybersecurity becoming a requirement that has to be met in order to be in compliance. Similarly, since retailing is a global activity, cyber crime and cybersecurity-related laws in other nations also have to be met.
Retail cybersecurity must develop an approach that is most appropriate for its environment. A major complication, however, is that changes in cybersecurity may run counter to the ways that security has been treated in the industry to date. IT and cybersecurity professionals and a growing number of C-level executives have accepted the view that security is no longer a technical problem but is an enterprisewide approach to business issues.
The result of this important transformation is that basic security concepts have shifted. The network of concern is no longer simply the hardware, software, and infrastructure. It is now viewed as the people, processes, and business units. Rather than viewing a major technical requirement as protecting the perimeter boundaries of the organization, the enterprise requirement focuses on matters of privacy and asset protection. The assets that a firm must protect are more than the desktops, laptops, servers, and databases. Now, in the enterprise view, the most important assets are customer data, employee data, and communication of information. Finally, technical matters are no longer the responsibility of IT and system administrators. Rather, technology and security are enterprise core competencies. (10)
These changes in retail cybersecurity affect how technology must be treated. Many of the newer retail services that are profitable are the result of technological innovations. Technical products and processes offer large opportunities and retailers must use their technology to its fullest. And, under-protected technology may indeed have an impact on that survival.
Technology has a dual use: providing new approaches to store profits as well as opening up opportunities for criminals to drain profits from these companies. If we examine several of the major advantages of technology for creating profitable environments, a parallel list can be drawn of how cybersecurity enhances those same technical features. Given that customers are central to the retail experience, we will emphasize the customer-oriented nature of technology. Certainly, cybersecurity has to be carefully applied so that it will not become counterproductive to the friendly shopper message of retail today.
Table C-7 indicates the contributions that a secure technology can provide to retailers. The technology itself can assist with attracting and gaining customers, but a secured technology will contribute significantly more to improving those efforts.
Table C-2 Security as Value Added to Customer Centered Technology
| Customer Emphasis | Technical Approach | Cyber Security Enhances Emphasis |
|---|---|---|
| Competitive Price | RFID, inventory management, forecasting, promotion management, supply chain, service level agreements, redundancies | Secure communications, multi-factor identification and authentication, role-based and rule-based authorization, VPN, firewall |
| Service & Performance | ERP, customer intelligence analysis, data collection, data mining, POS, personalized web sites | Data integrity, data confidentiality, service availability, encryption |
| Buy & Return Incentives | CRM, customer tracking, web site product appeal, rewards, purchase incentives, cross-linked web sites | Secure web browsing, extending security perimeter, wireless security, remote access protections |
These points apply to all aspects of the retail process. The process can be highly effective in anticipating and creating customer interest in particular products and services. International order fulfillment can be established, and monitoring of inventory can change the ways that prices are set. Stores can be opened online, and product presentations can be individualized to be based on a customer’s prior purchase patterns. Instantaneous payment is possible, and new profit centers can be established. Updates can be sent to customers with frequent purchase plans creating buyer loyalty.
At the same time, the process can expand the risks. For example, when a company connects to its partners and suppliers in the supply chain, the company potentially opens itself up to the security weaknesses of those involved in these relationships. It is the weak link theory applied on the global level.
Core Features of a Retail Cybersecurity Program
As mentioned earlier, a number of laws and regulations require security in organizations. In essence, those requirements point to elements of a cybersecurity program that companies should initiate. An additional feature of these requirements is that senior executives must sign off on reports that indicate the presence and the adequacy of those requirements in their organization.
Due to the centrality of credit card transactions, retailers have been encouraged and even pushed into accepting the Payment Card Industry Data Security Standard. The PCI DSS spells out the details of security that must be in place and can serve here as one model of the needed elements of a cybersecurity program.
As Dubin points out, “PCI DSS is not groundbreaking; it is simply a set of information security standards no different than those at any large bank or publicly held corporation. But it has molded security throughout the credit card industry lifecycle, from how banks issue cards to how retailers accept them.” (11)
In total, there are 12 PCI DSS-required controls. They cover access management, network security, incident response, network monitoring and testing, and information security policies.
Additionally, these 12 controls are grouped together under 6 PCI DSS “control objectives.” They include:
• Build and maintain a secure network. Ensure firewalls are installed and that changes to rules are adequately logged. Web servers that must access the Internet should be in a DMZ. Database servers holding customer account information should be inside the company’s network, protected by a firewall. Note: For the most part, these requirements are already part of the networking staff’s routine job responsibilities.
• Protect cardholder data. Stored account numbers must be encrypted or truncated, and customer data must be disposed of when no longer needed. This was the fatal mistake in the TJX case. Encryption over public networks for data in motion should be done using SSL.
• Maintain a vulnerability management program. This control covers a wide range of requirements. It requires antivirus software on all servers and workstations, and recommends everyone follow guidelines from the Open Web Application Security Project (OWASP) for developing Web applications.
• Implement strong access control measures. Restrict access to systems with account numbers and ensure user accounts are audited to remove outdated or malicious accounts. Stored passwords should also be encrypted.
• Regularly monitor and test networks. Require regular vulnerability scans, reviews of server logs, and the installation of intrusion detection or prevention systems (IDS and IPS).
• Maintain an information security policy. Draft an information security policy that covers access control, network and physical security, and application and system development. It’s important to keep the policy updated as systems and needs change, and to make sure it’s distributed to system users. (12)
These are the essential elements of a cybersecurity program. The elements are basic features that are found in many other industries but found less often in the retail world. As has been indicated here, there is a large price to be paid by businesses that do not follow these fundamentals.
TJX is the poster child of the price to pay. That company had stored old account information instead of deleting it. The company thus violated a PCI requirement, which mandates that a company remove data it no longer needs. During the breach, hackers stole an undetermined number of credit card accounts, some of which dated back to 2003. As a result, dozens of banks reported incidents of fraud from the compromised cards. There seems to be little doubt that TJX will be punished financially, it will lose customers, and its public reputation is in shambles. Unfortunately, TJX will not be the last retail company to discover that it is less expensive to prevent cyber crimes than to detect them.
Conclusion
The retail industry is struggling through a period of uncertainty. New forms of meeting customer demands and competition from a variety of sources have led to a complex playing field. Technology has added its own complexities, creating new possibilities for profit making as well as new opportunities for criminals. Today’s retailers have little choice in deciding whether to have adequate cybersecurity. That question has been resolved by legal and customer pronouncements. How cybersecurity programs will be integrated with business needs will turn out to be a major determinant of which companies will succeed and which will fail.
1 Identity Theft Resource Center. http://www.idtheftcenter.org/breaches.pdf.
2 Federal Trade Commission, The FTC in 2006: Committed to Consumers and Competition. April 2006.
3 Federal Trade Commission, The FTC in 2006: Committed to Consumers and Competition. April 2006.
4 Tim Shimeall, Cyberterrorism, PowerPoint Presentation, CERT Center, Software Engineering Institute, Carnegie Mellon University, Pittsburgh, PA.
5 Tim Shimeall, Cyberterrorism, PowerPoint Presentation, CERT Center, Software Engineering Institute, Carnegie Mellon University, Pittsburgh, PA.
6 Dennis Fisher, “Savvy hackers take the hardware approach,” March 7, 2007, SearchSecurity.com.
7 Ponemon Institute, 2006 Annual Study: Cost of a Data Breach: Understanding Financial Impact, Customer Turnover, and Preventative Solutions.
8 Secure the Trust of Your Brand: How Security and IT Integrity Influence Corporate Reputation. A CMO Council Report, September 2006.
9 Secure the Trust of Your Brand: How Security and IT Integrity Influence Corporate Reputation. A CMO Council Report, September 2006.
10 Julia Allen, Governing for Enterprise Security, Networked Systems Survivability Program, CERT, Technical Note, CMU/SEI-2005-TN-023, June 2005, p. 30.
11 Joel Dubin, “PCI compliance after the TJX data breach.” Security Wire Perspectives. March 8, 2007.
12 Joel Dubin, “PCI compliance after the TJX data breach.” Security Wire Perspectives. March 8, 2007.