T
Taking Over a Loss Prevention Department
You have just started in your new position as a director of loss prevention. It doesn’t matter whether you were hired from the outside or promoted internally: You face the same challenges. The first several months will determine your success or failure. So what do you do?
Start by identifying how you will focus your efforts. What are the company’s expectations for you? In most situations you recently went through an interview process with the senior management of your company. What were their expectations for an LP director? They usually have a high-level view of the role of loss prevention; however, their perspectives will help you understand what they would like to see from you. For example, is their focus on shortage reduction/control, apprehensions, investigations, auditing, physical security, or a combination of some or all of them? You can also identify loss prevention challengers and supporters during this process. This can help you better prepare for interactions with senior management in the future.
The next step, which is critical to your success, is to determine what your direct supervisor expects of you. Once you are in place, try to set up a meeting with your supervisor as soon as possible. The quicker you understand his expectations, the quicker you can start developing your action plans. Initially, the best way to do this is simply to ask. Because you’re new to the organization, people expect you to ask a lot of questions. Take advantage of that. Usually, your new supervisor will have a list of things that are a priority for him. What are they? The hope is that, by asking, you will start a dialogue that will clearly define these expectations. If not, schedule additional meetings until you fully understand what your supervisor expects from you. Obviously, these priorities should be high on your list of action items.
An important factor for you to consider is the company’s reporting structure. Whom do you report to? The CEO, president, COO, store operations, finance? Each of these reporting structures will impact how you approach your job. The executive level that the LP director reports to will dictate how the company perceives LP. The higher the executive level, the more cooperation LP will get throughout the company. Ideally, you want to report to the highest ranking executive in the company. However, this is not always the case. Here are two examples of challenges you may face if you report to either store operations or finance. If you report to store operations, you will be able to effectively impact stores but may be less involved in corporate processes that impact shortage like buying, merchandising, allocation, information technology (IT), etc. If you report to finance, you may be viewed more as an auditor than a partner with store operations. You can be effective in any reporting structure, but make sure you incorporate an understanding of your reporting structure into your planning.
Another part of the company’s reporting structure that is important is who your coworkers are? Who are your peers? To be most effective, you need the support from directors in all other areas of the company. Set up “meet-and-greets” with as many department heads as possible to introduce yourself and understand their expectations of LP. Identify their opinions on strengths and areas of opportunity for the LP department. You should also specifically identify whom you need to partner with to achieve maximum results. For example, directors of store operations are critical to running effective LP programs in the stores, human resources people are important to investigations, etc. Make sure you cultivate these relationships.
Now it’s time to look at your own department. The first thing to evaluate is the structure. How many direct reports do you have? What are their functions? How many field people do you have? What are their functions? Whom do they report to? For example, some report to LP management, whereas others report to store/distribution center management. Where are they located? The answers to these questions will give you a good idea of the resources you have available to you from a personnel standpoint. Keep in mind that if you have limited LP people or even if you don’t have any, your company employees are a great resource to help support and drive your programs.
Meet with your direct reports as quickly as possible. A good approach is to meet them first as a group. This helps to understand the synergy in the group and identify common issues. Then meet with each one individually. This will enable you to understand the specific issues each one is facing. A helpful insight into your direct reports can come from past performance reviews. Take the time to read each one and understand what past supervisors thought of their performance and capabilities.
Schedule visits to your stores, distribution centers, and any other facilities your company maintains. You must observe firsthand how the business looks and works. If your company has a large number of stores, visit a representative sample—for example, different geographical areas, high sales volume stores, low sales volume stores, high-shortage stores, low-shortage stores, unique stores that do not fit the company’s standard setup, etc. You do not need to visit every store in the chain during the first few months in your new job; it is more important to understand how stores are physically laid out and operate. However, if you have a small number of distribution centers and ancillary facilities, visit all of them. Since distribution centers and ancillary facilities are usually unique, it is important to understand, similar to the stores, how they are laid out and operate.
Mix up the people you travel with. Visit stores with your LP people, senior management, district managers, regional vice presidents, human resources, etc. Visit your DCs with your LP people and distribution center management. You learn a lot about people when you travel together. Take advantage of the travel time to ask questions and get their perspectives on all areas of the company. You will gain valuable information because they are all great resources.
Many times directors will go into a new company and quickly assess the LP department. Based on their assessment, they quickly roll out new programs. Often these programs fail because the new director has not taken the time to understand the culture and the history of the company. Existing programs are in place for a reason. Existing employees will resent being treated as if what they did before was ineffective. LP people operate the way they do because they were trained and directed by previous LP management to operate that way. Spend the time to understand why current programs are in place. What is the best way to do this? Ask questions and listen. Listening is becoming a lost art. You will roll out more effective programs with less resistance if you take the time to understand the culture and history. Knowing the history of your company will help you to avoid mistakes made by previous management. Even though you are looking forward, learn from the past. You may want to change the culture you find, but it is usually more of an evolutionary process than a revolutionary process. Changing the thought processes of your department and the company takes time and effort, but it can be done. Just take it one step at a time.
During this initial time in your new position, you will be exposed to a tremendous amount of information. It is important to take notes from every one of your meetings. Unless you write it down, you will forget a lot of what you have learned. Write down what you see as opportunities. This list will enable you to develop action plans based on prioritizing the input from company management. Refer to this list every month and add new opportunities that you identify.
It’s time to start developing your action plans. You’ve heard what your supervisor’s, senior management’s and your direct reports’ perspectives are on LP; now how are you going to focus the LP department? Internal investigations? External investigations? Shortage reduction/control? Auditing? Asset protection? An effective loss prevention program is best achieved through a balanced approach.
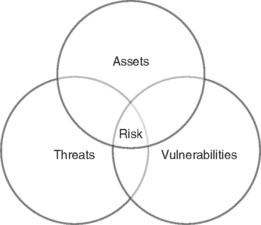
Your two primary objectives should be to protect the assets of the company and reduce shortage. The assets of the company include people, property, merchandise, money (cash, credit, checks, etc.), information, and the company’s reputation.
Reducing shortage will add profitability to your company. The three major areas that contribute to shortage are internal theft, external theft (vendor theft can be categorized as external theft), and operational execution. These three areas cover almost everything you will deal with in your role as an LP director. Numerous categories fall into these three areas, and it is difficult to control everything. However, if you focus on only one or two of these major areas, the one (s) you don’t focus on will increase and could cancel out the success you’ve gained in the other areas.
Your vision and strategy should incorporate protecting the assets of the company and the three major areas that can cause shortage. Within your vision and strategy, you must identify your focus areas. Loss prevention can be a very reactionary business. It is important to develop an organization that can react accordingly to the incidents that occur in a retail environment; however, you must also ensure that you are working toward your vision. Sometimes you can spend weeks doing nothing but reacting to the needs of the business, but you must always bring yourself back to your vision. LP directors who do nothing but react may keep their supervisor and business partners happy in the short term, but they won’t improve the overall operations of the LP department.
Almost everything you work on should fall into your vision and strategy. Once you define your vision and strategy, you should review it with your supervisor to ensure that you are both in agreement.
You are now ready to get into the details. The first thing to look at is the LP department metrics. What statistics do they measure and hold themselves accountable to? Measurements can include shortage, internal cases, external cases, cash over/shorts, merchandise recovery, credit card fraud, bad checks, counterfeits, etc. Determine how the statistics are trending for the year in each category. Look at the past 3–5 years to understand the history. This will enable you to gauge the productivity of your department and identify areas of opportunity where you can focus your efforts.
How does your LP department track its statistics? Is there daily, weekly, monthly, quarterly, or annual reporting? It is important to have LP statistical measurement reports at least once a month. Does your department track statistics manually or using a case management system? If these reports are not system generated, it is worth the time and energy to develop them. This can be done within your own department if you have the expertise, or you may have to work with your IT people. If you have a case management system, these reports can be easily created. Either way, make it happen. It will definitely enable you to better manage your department.
Does your LP Department look at productivity by individual? One of the most effective tools to monitor and increase productivity is ranking reports. By ranking each person against his peers in every measurable category, you can identify top performers and poor performers. It is not unusual to discover that a small portion of your staff is producing the majority of your statistics. This is especially true with internal and external cases. By improving or replacing poor performers, you can raise the bar for everyone and increase overall productivity. Specifically, these reports will enable you to recognize good performance. A recognition program directly tied into individual productivity is generally well received by investigative personnel. It creates competition, which most LP people thrive on, without creating quotas. Quotas have resulted in numerous civil litigations and should be avoided.
Ranking reports also help you identify areas that might need additional training. For example, if all your investigators have low internal case productivity, what training is needed to improve their performance?
Recognition should be an ongoing component of your department. People are your most important asset. They need to be cultivated on a frequent basis. Do you appreciate being recognized for your performance? Of course, you do. Well, your people do too! If they don’t already exist, develop multiple ways to recognize good performance. This can be for statistical performance, effectively handling a specific incident, leadership, or any type of metrics. Just be sure to make this recognition meaningful. Too much recognition can take away the value to the employee. This is a good area to partner with HR. The HR staff usually have a number of programs that they can share with you. A good recognition program encourages people to strive for better performance. The better your people’s performance, the better your results.
It is critical that you manage your LP data effectively. All incident reports (internal and external apprehensions, investigations, recoveries, robberies, burglaries, unusual incidents, etc.) must be maintained and accessible. When you are taking over an LP department, it would be unusual to find that it does not already have an existing methodology for documenting and tracking its activities. Understand how it works to make sure you are comfortable that it does what you need it to do. For example, how do you request and receive an investigative report for an outlying store or location?
If you do not have IT capabilities for your LP people, you must have paper reports that capture all relevant information surrounding your areas of responsibility. If you use a systems-based case management program, evaluate its capabilities. Ensure that it provides you with the data analysis tools that you need. If you don’t have a systems-based case management system, you should make the effort to get one. Many case management systems are available. By working in partnership with your IT department, you should select the software and system that are compatible with your company’s existing IT platform. If you purchase a systems-based LP case management program, make sure it is able to feed external systems, e.g., civil recovery/demand.
If you have a staff that catches shoplifters, most states have statutes that allow merchants to civilly recover damages from adults or the parents/legal guardians of juveniles who shoplift from that merchant. It is usually called “civil recovery” or “civil demand.” The collection of restitution and civil recovery/demand should be pursued in all applicable internal and external cases. The amount that can be collected varies by state and statute. You should make sure you have your legal counsel approve the requested amount of damages in each state.
In situations in which employees steal from the company, a promissory note or restitution procedure should be in place. If an employee admits to causing a specific amount of loss to the company and is willing to pay it back, he should be asked to sign a promissory note. This form creates a legal agreement with the employee that enables you to pursue him civilly if he does not pay you back in accordance with the terms and conditions of the promissory note. Again, you should make sure your legal counsel has reviewed and approved this form.
Many companies use external vendors to handle the collection efforts for them. Some companies have their own internal collection departments. Again, in most companies, one of these processes should already be in place. Either way, review the process to make sure that you are maximizing the collection of civil remedy/demand and restitution dollars. The collected funds can be used to purchase LP equipment and services that will deter future losses. By utilizing the collected dollars in LP deterrent programs, you can more easily justify outside legal challenges that you are using civil demand/remedy as a profit center for your company.
Another important area to review is the LP budget. First, understand what your annual budget is and how it was developed. How is the department trending for the year? Is it on budget? Is it over budget? Is it under budget? Are expenses being managed properly? Poor expense management will usually put you under an unwelcome spotlight, so make sure you understand the finance methodology of your company. It is critical that you have mechanisms in place that will alert you to over-budget and under-budget situations before you receive summary reports from the finance department.
The next step is for you to understand how the LP department in your new company operates. The best way to do this is by reviewing the department’s existing policies and procedures. Is there an LP department operations manual or just a collection of memos and directives which define the operating platform for the department? Having a comprehensive and detailed operations manual is critical to the success of an LP department. An operations manual should define the expectations for the LP department. It should also contain all the policies and procedures necessary to execute the expectations for the department. The content should include internal investigative procedures, e.g., evidence collection and retention, case development, interview techniques, prosecution guidelines, etc. It should include external theft procedures, e.g., the steps necessary to make an apprehension for shoplifting, use of force, evidence collection and retention, prosecution guidelines, etc. It should also include operational procedures, e.g., audits, checklists, etc. The LP operations manual should be the foundation for the daily operations of the department. It will ensure consistency throughout your LP organization. All training should be developed from the policies and procedures contained in the operations manual.
If there is no LP operations manual, create one. If one already exists, you should revise it in accordance with your philosophy and approach. The LP operations manual should always be a “work in progress.” As you grow in the job, you should constantly revise it as you develop your department. Once created or revised, the manual should be made available to all levels of your department.
When creating or revising LP policies and procedures, involve members of the LP department in the process. An effective methodology is to create task forces composed of members of the LP department. Assign these groups to write new or revise existing polices and procedures. This enables you to take advantage of their experience within the department and the company, as well as have them be part of the process. This leads to ownership and makes it easier to facilitate change. This concept works very well if you decide to create or rewrite the LP operations manual.
Are there LP personnel training programs in place? If a training program doesn’t exist, develop one. This should become a top priority for you. An effective training program is absolutely essential. Well-trained people enable you to execute your operations effectively and consistently.
If there is an existing LP training program in place, review the content. Is it comprehensive? Does it cover all the areas that are covered in the LP operations manual? Will it keep the company protected from legal challenges of inadequate training? Are the training programs managed by the LP department or the company’s training department? Either way, the high risk that goes along with conducting internal and external investigations can be mitigated with thorough training. Multiple methods for training should be utilized—for example, written, video, e-learning, on-the-job, classroom, etc. All training should be documented, and individual training records should be maintained on each LP person. Training should be updated along with new policies and procedures.
The best way to ensure compliance to your policies and procedures by LP personnel is to have a disciplinary action process. If LP people violate the policies and procedures you put into place, there should be accountability. This will allow you to remove nonconforming employees who can put the company at risk by their actions. Effectively managing a disciplinary process will result in better consistency in your operations.
Effective communication is extremely critical to the success of an LP department. You must have some method of communicating timely information to the LP organization. This information can include new LP and/or company policies and procedures, investigative alerts, open jobs, etc. Some type of “communication binder” should be maintained in all field locations. This communication binder can be an actual binder or an electronic folder. An electronic folder that serves this purpose will depend on your company’s IT infrastructure.
One concept that helps to develop a team is to create an identity for the LP department. This can include an LP department logo, tag line, and mission statement or any combination of the three. Many companies have a mission statement, but it is not specific to LP. Use the basic concepts from the company mission statement but tailor it to the LP department. Here is an example of an LP department mission statement:
Company XYZ Loss Prevention is committed to consistently driving processes that will improve profitability by reducing losses through investigations and operational compliance while providing a safe environment for our Employees and Customers.
A fun way to create an LP logo or tagline is to hold a contest within the LP department. Your own people can come up with some great concepts that you can turn into the LP department identifiers. The fact that they created the logo and/or tagline themselves will cause them to take ownership. If your LP people can’t come up with anything that fits your vision, work with your marketing department or, if you don’t have a marketing department, use an outside vendor.
Another concept that helps develop a team and holds your people to a higher level of accountability is a “standards of conduct.” A standards of conduct should clearly define your expectations for your LP people. It is an add-on to the company’s employee handbook. By spelling out your expectations, you can raise the performance level of your people. Because it sets a higher standard for LP people above that of the regular employees, you must work with human resources staff to gain their support. That way, if an LP person violates the standards of conduct, he can be disciplined in accordance with the standards of conduct, not the employee handbook. It will enable you to foster a higher level of ethics and integrity in your LP team. Here is an example of a loss prevention standards of conduct.
Standards of Conduct
A Company XYZ Loss Prevention employee’s conduct must be above reproach at all times. Their conduct must comply both with applicable state and federal laws which define the legal limits of their conduct and with Company XYZ policies and procedures which, at times, are more restrictive than state and federal law.
All Company XYZ Loss Prevention personnel are required to read and sign the “Standards of Conduct” form.
These standards are not intended to cover all situations, rules, policies, regulations, etc., and should not be construed as such. They are, however, indicative of the spirit and intent of Company XYZ policy and the expectation of your conduct and behavior. These standards are of such importance that any person failing to comply with them will be subject to disciplinary actions, up to and including termination without prior warning.
Maintaining the standards outlined on the following pages and the philosophical spirit reflected by them, should be the guideline in each loss prevention employee’s professional approach to their daily activities.
These standards are in addition to the policies and procedures defined in the Employee Handbook.
The original, signed “Standards of Conduct” form must be maintained in the loss prevention employee’s personnel file. (Copy Attached)
Standards of Conduct
These Standards of Conduct are expected of all Loss Prevention personnel so that no person will have cause to question our professionalism, integrity, credibility, and objectivity. In the performance of our job, we must be highly professional and must meet more exacting standards of behavior and adherence to rules. The nature of our function, authority, and responsibility requires this higher standard.
The following type of behavior is not in keeping with Company XYZ Loss Prevention Standards of Conduct:
1. Any activity, which reflects adversely on the ethical or professional stature of Company XYZ Loss Prevention Department. Covered under this statement are such activities as
2. Failure to objectively and factually report information required or obtained within the scope of employment. This statement covers not only the willful misstatement of facts, but also knowingly omitting pertinent information from reports and/or the purposeful “slanting” or “coloring” of reports.
3. The failure to report any information, however obtained, which could conceivably bear on or be pertinent to any Loss Prevention investigation or be of legitimate interest to company management. For example, any customer or Employee detention must be reported to your Supervisor in accordance with established time frames.
4. Failure to submit reports as required by Company XYZ Loss Prevention policies and procedures.
5. Violation of any of the provisions of Company XYZ “Use of Force and Weapons” policy.
6. Any misuse, careless or improper handling of funds, evidence, or records entrusted to our care.
7. Any misuse of company equipment or property, misuse of position or authority, or agreement to accept “favors” not granted others and available or offered us because of our position is prohibited. Covered under this statement are such things as the following:
8. Failure to follow Company XYZ Loss Prevention policies and procedures with regard to stopping, questioning, and/or apprehending both Employees and the customers.
9. The failure to be completely truthful and candid in response to any official request for information.
10. Inappropriate use of CCTV cameras and equipment. CCTV cameras and equipment must be used for work-related purposes only.
11. Failure to follow policies and procedures outlined in the Loss Prevention Department Operations Manual or directed by the Director of Loss Prevention in the form of a memo.
The above statements are not intended to cover all situations, rules, policies, regulations, etc., and should not be construed as such. They are, however, indicative of the spirit and intent of Company XYZ Loss Prevention policy and the expectations of your conduct and behavior. These standards are of such importance that any person failing to comply with them will be subject to disciplinary action up to and including termination of employment without prior warning.
Maintaining the standards above and the philosophical framework created by them should be the guideline in your professional approach to your daily activities.
I HAVE READ AND UNDERSTAND Company XYZ Loss Prevention Standards of Conduct. I understand these standards are not intended to establish any expressed or implied contractual rights. I also understand that any violation of these standards may result in disciplinary action, up to and including termination of my employment without prior warning. These standards are in addition to the policies and procedures defined in the Employee Handbook.
| NAME (PRINT) Employee NO. | ___________________________ |
| SIGNATURE DATE | ___________________________ |
Technology should not determine your LP strategies. Technology should help you achieve your LP strategies. As part of your assessment process, you need to evaluate the technology currently available to your department. Do you have CCTV? If so, how is it utilized? Are there fixed cameras; Pan, Tilt, and Zoom (PTZ) cameras; or both? Is it overt, covert, or both? Do you have digital video recording (DVR) technology or analog video recording technology (VHS)? Are there remote monitoring capabilities? Do your people have desktop computers or laptops with docking stations? Do they have access to LP/company systems for investigative purposes?
Physical security is a responsibility that most likely falls directly onto your shoulders: burglar and fire alarm systems, lock strategies for doors, access control (if applicable), cabling of high-value apparel, locking caselines, locking fixtures, safes, securing of high-value products (pharmacy, fine jewelry), protecting of merchandise trailers, etc. There is information available on these topics in this book. You should learn about each category so that you can incorporate your physical security strategies into your overall vision for your LP department. When it comes to physical security, the simpler, the better. The easier a physical security system is to use, the better compliance you will get from the users. This is important because, even if you have a great physical security system, if no one uses it, it has little value.
Now ask yourself, does your current equipment and technology enable you to accomplish your vision for the LP department? If not, determine what you need. How do you know what’s available? Simple, talk to the LP vendor community. There are hundreds of vendors who sell and service LP equipment and technology. All of them would be interested in educating you on their product(s). Once you have learned about and are ready to choose a type of equipment or technology, reach out to fellow LP directors that use the particular product(s) and ask them for feedback. Most will be happy to give it to you. Or, reach out to your fellow directors first and then talk to the vendors. Whichever approach you take, other LP directors are a great resource.
Now you’ve done your homework on the equipment and/or technology you want to buy, and you’re ready to start the process to purchase it. The first step is to learn what your finance department requires to justify an expenditure. All companies have different methodologies for this process, but all require that you demonstrate a return on investment (ROI). Learn the formula for your company and incorporate it into all your proposals.
Exception reporting is an essential LP tool. Strategically using exception reporting will improve your efficiency because you can focus on problem (exception) resolution. You don’t need to know when things are working as expected, only if there is a problem. Of course, the most common exception reporting systems for LP are POS based; however, exception reports on almost any company process that impacts shortage are valuable. Knowing which stores have high or low results in comparison to the entire store population enables you to focus on areas and locations that are exceptions. For example, for Mark Out of Stock (MOS) percentages, a high number could mean that the store is not handling MOS merchandise properly or there is some other issue. By investigating that high number, you can identify, address, and correct the issue which will reduce the MOS. Reduced MOS improves profitability. If a store has a low MOS number, it could mean that it is not processing MOS properly or possibly even throwing it away. This would cause shortage, and the store would not be replenished for the damaged merchandise. Use exception reporting to identify anomalies and investigate the anomalies. You will be able to spend less time and get better results because you are addressing exceptions only.
To stop return fraud, a refund control program is absolutely necessary. Without an effective refund control program, your company is at risk. Poor refund control can lead to internal theft (fraudulent returns by employees) and external theft (shoplifting for the specific intent to return.) It can also allow duplicate receipts, counterfeit receipts, and the reuse of the same receipt multiple times.
Thieves find ways to circumvent polices at individual stores. The best defense is a corporatewide system to track returns. The main focus should be on nonreceipted returns. If your POS system allows a way for cash to be obtained without a receipt, the thieves will find it. A refund control system that stops nonreceipted returns works by requesting IDs from individuals returning merchandise without receipts. You set the parameters for how many returns you will allow before you shut them down. This is called “velocity.” The system should also identify counterfeit receipts and previously used receipts and stop them as well.
Refund control systems can be developed internally or purchased from an outside vendor. Either way, refund control is a must have.
One of the issues that you will face when it comes to the implementation of new company systems is where and when the LP requirements are included in the process. For example, a new POS system needs your involvement to make sure the proper controls are included to prevent losses at the registers and in the cash office. Many times, the LP requirements are scheduled to be implemented at a future date. This future date is often called “Phase 2.” Be aggressive in having the LP requirements included in “Phase 1.” “Phase 2” may be delayed or even canceled, and you will have lost your opportunity to get the LP components you need. Developing an effective partnership with the IT department will enable you to always be part of “Phase 1.”
Organized retail crime (ORC) is a significant part of external theft losses in most retail environments. Evaluate the extent to which your company is a target of ORC. Based on this analysis, determine how to use your LP and store resources to minimize this threat. Do you lock up your targeted product? Do you place it behind counters? Do you work with law enforcement to apprehend the thieves? Do you allocate some of your LP personnel to focus only on ORC? Whatever plan of action you develop, be sure to include ORC in your strategies to control losses.
Shortage programs are an integral part of any LP program. Controlling shortage is a process. You must have all areas of the company working together to control shortage. There must be daily attention to all shortage control procedures. For this to happen, there must be support for reducing shortage that comes from the senior management of the company; otherwise, it will not be a priority.
The first step in creating a shortage program or enhancing an existing one is an Executive Shortage Committee. This committee should include senior management and director-level people. The higher the management levels in these meetings, the better. Representation should include LP, finance, operations, distribution, buying line, IT, internal audit, inventory management, human resources, etc. You want people on the committee who can go back to their departments and make things happen. This committee should focus on all areas of the business that can impact shortage. It should develop action plans that the people on the committee can go out and execute. Examples include store/DC LP standards, focus on high-shortage stores, focus on high-shortage merchandise, EAS tagging standards, etc.
A shortage program should include monthly shortage meetings in all stores and DCs. These meetings should include the facility manager and key people in the location. The monthly topics should focus on high-shortage areas and processes. All facility employees should be made aware of the focus topic each month. This can be done through separate meetings held at different times throughout the day. Retail schedules rarely allow for store-wide meetings, so the individual meetings should be scheduled so that all employees are given the necessary information.
Another effective method is the development and implementation of individual store shortage “action plans.” These action plans should be based on the shortage results from the most recent inventory. Focus areas can be companywide, store specific, or a combination of both. The plans should define what each store is going to do to address the high-shortage areas. District/regional store operations and LP managers should be required to approve the action plans. The action plans should be inspected throughout the year, and stores must be held accountable for not executing their plans.
Some companies focus their efforts on high-shortage or “target” stores. These “target store” programs are based on the concept that reducing shortage in the highest shortage stores will be the best return on the investment of resources. This approach is usually very successful in those stores. The challenge with this approach is that “nontarget” stores can experience increased shortage because there is not a focus on them. Those stores can then become the new “target” stores.
An effective shortage program must include employee awareness training. Employee awareness starts with educating employees on their role in controlling losses in the company. What can they do every day to positively impact shortage? You must define the expectations for every employee. They need to take ownership for controlling losses. If they have “ownership” for controlling losses, they will be more likely to help than if they don’t feel they have any responsibility. This can be done by communicating your message(s) in new hire orientations, company newsletters, posters, etc. Developing a shortage logo and tagline will “brand” your program. As with an LP department logo and tagline, create a companywide contest to get ideas. Your company employees can often come up with some great concepts. If your company employees can’t come up with anything that fits your vision, work with your marketing department or, if you don’t have a marketing department, use an outside vendor.
Since shortage control requires daily attention, your goal should be to create a culture of loss prevention. You want all employees doing the right things every day. Doing the right things means not stealing, reporting those that do steal, and following established procedures to prevent loss. A loss prevention culture takes time to develop, but it will pay off every year in low shortage if it is maintained throughout the company.
A quote that has been around for a while is “a well run store equals low shortage.” This makes perfect sense, but how do you ensure that a store is running well? How about another quote? “You get what you inspect.” An LP audit program enables you to monitor store compliance to shortage control policies and procedures on a periodic basis. By monitoring store performance and correcting identified deficiencies throughout the year, you can prevent a poor shortage result.
If your company does not have an LP audit program, you should consider putting one in place. If your company does have an existing audit program, you should evaluate its effectiveness. Often you will find the existing audit program does not have a true impact on controlling shortage.
The two keys to a successful LP audit program are objectivity and accountability. The first key is objectivity. The audits must give an accurate picture of what is actually happening in a store. If they don’t, they have limited value. To be able to correct issues, you must know what they are. Auditors must be able to objectively report their findings. Of course, that makes sense, but it doesn’t always happen. Here is something to consider. If the person who conducts the audits reports directly to the district manager or regional manager who is responsible for running the stores, can he truly audit objectively? Will this “partnership” be jeopardized if the LP person fails them in an audit? Will performance evaluations be negatively impacted? Review audits for the past year. Are all stores passing? If they are, it is an indicator that the audits may not be objective. It would be a very well run company indeed if every store passed every audit. Try to set up your LP auditors so that they report independently from the people who run the facilities they are auditing.
The second key is accountability. If a store fails an audit, are there consequences? Are the consequences serious enough to get the attention of the person being audited? For example, if a store fails an audit, does it result in disciplinary action? Does it impact its performance evaluation or bonus? If the consequences aren’t meaningful, store management will not focus the appropriate attention on taking the actions necessary to pass the audits. You must elicit senior management’s support in developing the appropriate consequences so that store management knows that it is a company priority.
If you don’t have an effective store audit program or don’t have one at all, how do you get started? Create a task force that includes loss prevention executives and store line senior management. If store management is included in this process, there will be more of a sense of ownership, and the audit will have more credibility. Develop an audit that addresses shortage control in all areas of store operations. This does not normally include creating new polices and procedures, but just selecting those that will make a difference in reducing shortage. The contents of an LP audit should include cash office, receiving, point of sale (POS), physical security, EAS tagging compliance (if applicable), and anything else that impacts shortage. As a side benefit, this process can result in strengthening controls in almost all existing store procedures, because when the task force reviews all procedures, they will usually find ways to improve them.
To ensure that the new audit works effectively, make sure you “field test” it. This enables you to identify problem questions and correct them before you roll out the entire program.
Once finalized, the revised procedures and new audit forms should be provided to all stores. Stores should be given some time to “ramp up” before the new audits are scheduled to begin.
One way to ensure auditing consistency is to create a loss prevention auditor’s manual which contains detailed explanations of what the auditor should be reviewing for every question on the audit. This manual will ensure that all auditors review the same areas in exactly the same way. The completed manual should also be provided to every store so that they also know every question and the audit instructions. Communicating this information to the stores will eliminate many of the challenges when points are not awarded.
To help stores pass their audits, which is, of course, the goal of the program, stores should be required to complete daily or weekly checklists. These checklists are tools to ensure daily attention to the policies and procedures that are reviewed on the audit. Checklists can be created directly from the audit. Many times stores will break the audit into sections and use them as checklists.
Another component of an audit program that gets results is a random and unannounced audit schedule. The only way to get a true picture of what is really happening in a store is to show up when the store doesn’t expect you. Another benefit of a random and unannounced audit schedule is that all stores will operate more consistently on a daily basis in expectation of receiving an audit.
Audits must be conducted often enough to allow “course correction” during the year. Many companies take once-a-year inventories. It is the consistent execution of shortage control policies and procedures that provides the positive end-of-year results. One formula that works well is a quarterly audit in all stores and a monthly audit in high-shortage stores. Of course, your program must fit your company’s structure and budget. Timely reporting of audits is also important. As soon as an audit is completed, the results should be communicated to the store and the district manager. After that, audit scores should be tracked along with all the other company performance measurements and be included in annual performance evaluations.
Cash control is an important part of any LP program. Review the existing procedures: “Follow the money.” What are the controls in the cash office? Are all cash office personnel background-screened? Is the physical security of the cash office (locks, safe, camera coverage, etc.) adequate? How are the basic funds for each register drawer set up? How are they transported to the sales floor? What are the controls at the registers? How is change handled? How are cash pickups done? Who counts the daily sales and creates the deposits? Who verifies the deposits? Are the deposits taken to the bank by sales personnel, or are they picked up by an armored carrier service? Are there controls in place to make sure that the deposits arrive at the bank? If a deposit does not make it to the bank or there are discrepancies with the deposits that are identified by the bank, how is it communicated and to whom? The answers to these questions will enable you to identify the effectiveness of your company’s cash control procedures.
Timely notification of cash register overages and/or shorts to LP is essential. Determine how stores communicate register shortages to LP for investigation. Make sure that LP is notified as quickly as possible. Once notified, how do the LP personnel keep track of the shortages by store? Cash shortage investigations should always be a high priority for your LP personnel. Employees who steal cash are usually stealing in other ways, too.
Credit card fraud, fraudulent and/or bad checks, fraudulent traveler’s checks, and counterfeit currency are other concerns that should not be ignored. Each of these areas has available controls that can be utilized by retailers. Meet with your finance department to learn about the controls that are currently in place. Ask the finance staff to provide you with regular reports on fraud losses. Review how employees are trained to accept checks. Is there a check guarantee program? Are ultraviolet lights used to check for counterfeit currency, traveler’s checks, and credit cards? Do employees check for identification? Are imprinters used for credit cards that won’t scan? The best way to prevent fraud is by having well-trained and alert employees. Train employees to follow all the required steps when accepting credit cards, checks, traveler’s checks, and currency.
One of the most effective ways to get information regarding people or issues that are causing theft or shortage is an employee hotline. Implementing a confidential way that employees can communicate information will increase your chances of identifying where and how losses are occurring in your organization. In addition, by paying out cash awards for information that leads to correcting the cause (s) of the loss, you will increase the information flow. Although most people don’t call specifically to get the money, they appreciate getting the award.
Employee hotlines can be managed internally or by an outside vendor. As long as the information can be provided and managed confidentially, either way will work. However, make sure it is an 800 number so that employees can call from anywhere. Many companies use an outside vendor because they believe it makes the employees more comfortable in making the call knowing it is not going to a person inside the company.
Once you have established an employee hotline, publicize it through all available methods—employee training and orientations, newsletters, the company website, paychecks, wallet cards, posters, employee handbook, etc. One effective way to ensure that all employees always have access to the number is to print it on their discount cards. In addition to the LP hotline, make sure that you get all your LP messages out using the same methods.
When rolling out LP programs, always use the company’s current communication protocol. For example, if you roll out a new procedure on controlling credit card fraud to the stores, use the existing company communication vehicles. If the stores get a weekly operational hardcopy communication, include your LP procedures. If the stores get a weekly email communication, include your LP messages. This way, the stores receive the LP information as part of the other information that is rolled out that week. Incorporating LP information into the communication vehicles of the business is the best way to get your messages out to your audience.
Background screening is the best way to prevent hiring dishonest employees before they even walk onto the selling floor. Review your company’s existing background screening program. Do you have one? If you do, is there drug screening? Are there criminal checks? Credit checks? Employment verification? Education verification?
Because of the high turnover in retailing, background screening is expensive, so implement a strategy that is cost effective. Determine the risk levels of your employees. Management and cash office personnel should be at the top of your list in terms of risk level. People in these positions have the most access to cash, merchandise, and company property. Evaluate all the positions in your company and develop a background screening strategy that fits. HR is an excellent partner in this evaluation process.
Participation in a national retail database is an absolute. National retail databases include dishonest employees and shoplifters from fellow retailers. This information is the most specific to the retail industry. They are relatively low cost and usually have a higher “hit” rate than the other checks and verifications. However, these databases are only as good as the information that is submitted to them. Talk to other LP directors and find the national database that includes the most retailers that you are likely to hire your employees from. If your company does not participate in one of these databases, you should definitely consider joining one.
Threat Assessment and Management: An Integrative Approach
John K. Tsukayama and Gary M. Farkas
Introduction
Prevention of crime in the workplace typically is the sole province of the security professional. In the retail sector, internal dishonesty and shoplifting offenses are the primary loss prevention concerns of in-house or contracted security agencies. Aside from those occasions when advanced technology needs to be adopted or mystery shoppers employed, external consultants are rarely used in the typical retail establishment’s loss prevention efforts.
Workplace violence is a unique concern in the retail environment. While industrial facilities and many service businesses can establish basic perimeter defenses against suspected threats, the retail establishment’s need for open access creates vulnerabilities not seen in other industries. The unrestricted environment of the retail sector allows both the general public as well as former and current employees (some of whom may have hostile intent) to closely approach intended targets.
Because of the unique demands of workplace violence prevention efforts, the retail security professional needs to be aware of the specialized and generally accepted principles of Threat Assessment and Management (TAM). This approach blends the expertise of the security professional with those of other consultants. In this section, we discuss how psychological and security professionals, working closely together, can add value to a retail organization’s efforts to reduce the risk of workplace violence due to disgruntled employees or known outsiders.
A Special Loss Prevention Problem
Traditionally, loss prevention investigators have had the task of gathering evidence relating to a known crime that has already occurred, or one that is believed to be already occurring. In those cases, either normal reconstructive or constructive methods will be applied. The who, what, where, when, why, and how aspects of the process of investigation will guide the investigator to collect and present evidence that can be used to justify appropriate action. In the private sector, the goals of loss prevention, economic recovery, and employment termination are typical, whereas in the public sector, the goal is normally the bringing of criminal charges.
There is, however, one kind of investigative problem that differs significantly from these norms. This type of investigation centers on the problem of targeted violence and has received increasing attention in the past 20 years. The relevant questions are not merely “What happened?” or “What is happening?” Rather, they are “What is likely to happen in the future?” and “What can be done to prevent it?”
The approach that has developed since the early 1990s is known as Threat Assessment and Management, or TAM. For our purposes, we will concentrate on the application of TAM to workplace violence prevention because this is an area of frequent occurrence in which loss prevention professionals can make important contributions. Therefore, knowledge of workplace violence is essential.
Types of Workplace Violence
There are generally considered to be four categories of workplace violence.(1) They are
• Type I: Violence by criminals with no other connection to the workplace. Entry is solely for the purpose of committing a crime such as robbery.
• Type II: Violence by customers, patients, students, clients, inmates, or others receiving goods or services from the organization.
• Type III: Violence by present or former employees against supervisors, employees, or managers.
• Type IV: Violence by persons who have a personal relationship with an employee but who do not themselves work in the organization.
The first two types of violence will tend to be addressed through normal crime prevention strategies and are typically investigated in a post-incident or reactive context. These violent incidents tend not to involve perpetrators who are targeting specific individuals for violence. One example is the convenience store or gas station robbery, an act whose criminal motive is not violence, but monetary gain. Another example is the outburst of anger that a drunken patron may direct at a bartender. This type of outburst is known as affective violence and is typically an immediate emotional reaction to a stressor, devoid of criminal motive.
In the last two categories, there is much more likely to be a specific individual who is being selected for violent victimization by the perpetrator. This is known as “targeted violence” and is the kind of violence that frequently exhibits a number of warning signs. If those warning signs are properly detected and assessed, they can give the organization the opportunity to steer the situation away from a violent outcome.
This kind of violence will tend to be what is known as predatory violence, which is violence that is planned, purposeful, and emotionless. The perpetrator will engage in behavior that is akin to hunting the intended victim(s) and may provide clues to intentions, methods, and targets prior to an actual attack. It is in these situations that TAM is intended to be used. Our focus will be on predatory violence relating to type II, III, and IV workplace violence.
Threats
The topic of threats is an area in targeted violence prevention that carries great potential for misunderstanding that leads to ineffective action or overreaction. In many organizations there exist workplace violence policies that prohibit employees from making verbal threats against others. The statement “I’m going to kill you” will generally be understood as a threat, and action will be taken. Consider, too, the statement “Unless something around here changes, people are going to get hurt.” Is that a threat or not?
The ambiguity involved in these situations requires refinement. The term “threat” tends to be used in two ways:
• Threats Made: The purest form of threat is an unconditional statement of intent to do harm. It is characterized as a communication.
• Threats Posed: A person, situation, or act that is regarded as a menace. It is characterized as a danger.
Another term we will use here is “instigator,” by which is meant a person who has either made a threat or poses a threat to the targeted victim(s).
Threats Made
There has been some significant research completed regarding threats to do harm that indicates the need to take a more thoughtful approach to threats made. For many years, it was believed that the persons most likely to carry out attacks are those who make direct threats. In the 1990s the U.S. Secret Service, the national Institute of Justice, and the Federal Bureau of Prisons studied the behavior of 83 persons who carried out actual attacks, or came close to attacks, on prominent public figures. As a result of that research, it was concluded that “persons who pose an actual threat often do not make threats, especially direct threats.”(2) It was further concluded that, “although some threateners may pose a real threat, usually they do not.”(3)
This is not to imply that because a direct threat has been made that you can discount it as an indicator of future violence. In the areas of school violence, domestic violence, and workplace violence, it is not uncommon for direct threats to precede violence. Loss prevention professionals need to heed all threats, both made and posed.
Threat management experts Frederick S. Calhoun and Stephen W. Weston provide a means of sorting the confusion regarding threats. In their book Contemporary Threat Management, they introduce the concept of what they term the “Intimacy Effect.”(4) Essentially, it is believed that greater intimacy between the instigator and the target will make direct threats more reliable as pre-incident behavior. Therefore, where there has been some degree of intimacy, such as between coworkers or spouses, a verbalized threat should be taken more seriously than one spoken about a public figure not personally known to the instigator.
Threats Posed
While many who make direct threats never attempt an attack, the lack of any threats made cannot lead the investigator to necessarily conclude that there is no threat posed. The central concept of a threat assessment investigation is to attempt to determine whether, at the present time, it appears that the instigator poses a threat to the target.
Persons known to possess all f the following should be considered threats posed to the target (s):
Lacking one or more of these factors probably lessens the threat posed, although movement toward target proximity would not necessarily be relevant if the means exist to create and deploy a mail bomb (or other similar device) delivered by a third party.
Red Flags
It should be clearly understood that there are no reliable profiles that can be of meaningful use to TAM practitioners. No set of attributes will be present in all those who perpetrate lethal targeted violence. Likewise, the absence of those attributes should not be taken as a signal that the instigator does not pose a danger to a particular target. For these reasons, “profiling” is not a responsible approach to take when considering potential targeted violence.
Some factors have been identified in cases involving targeted violence that do bear attention. Organizations should train supervisors and employees to be aware of these red flag items.
If they are present, the red flags should not be used to conclude that a danger is actually posed. In fact, in the majority of instances, individuals who exhibit one or more of these items never will carry out, or even desire to carry out, targeted violence.
The presence of the red flags should signal to the organization that some level of assessment should be performed to determine whether further concern is justified. Only after an adequate TAM process is completed is it wise to specify appropriate action by the organization. In many cases, TAM investigation will determine that the person of concern lacks the grievance, violent ideation, inclination, means, or preparation necessary to carry out an attack.
Employees should be encouraged to report the red flags (or any other reasons that cause them concern) to the TAM team with the understanding that no negative action will be taken against the person of concern solely on the basis of their report. To do otherwise may make employees hesitant to share information at an early stage when there still exists ample opportunity to address the situation while the instigator is still capable of being diverted.
Red Flags
Following is a list of red flags employees should be aware of:
4. Recently acquiring weapons, especially in conjunction with dispute events.
6. Hypersensitivity to normal criticism.
7. Harboring grudges in conjunction with imagined or actual grievances.
8. Preoccupation with themes of violence.
10. Interest in highly publicized incidents of violence.
11. Loss of significant relationships, including marriage or other intimate relationship.
12. Legal or financial problems.
13. Ominous, specific threats.
14. Suicidal/homicidal thoughts or speech.
15. Stalking or placing employees under observation.
16. Verbalizing a strongly held belief that others mean him harm.
17. Being frequently sad, angry, or depressed.
19. Marked changes in behavior or deteriorating hygiene.
No list of red flags or warning signs can be exhaustive, and the fact that something of concern to employees does not appear on this list should not prevent the TAM team from considering it when deciding to proceed with a formal assessment.
TAM Teams
TAM is a complex undertaking that has the twin objectives of determining whether the current situation is apparently moving toward a violent act and specifying a set of measures the organization can undertake to divert the instigator away from violence.
The practice of creating specially trained teams has arisen to provide the talents of a multidisciplinary group to both sort out the complexities and handle the numerous tasks associated with quality assessment and planning in the high-stakes endeavor of targeted violence prevention.
These teams are known by a variety of names. They may be called threat management teams, incident management teams, threat assessment teams, crisis management teams or go by any number of “committee” names. In any case, the teams will often include TAM-trained representatives from the following parts of the organization:
In addition, someone in the management chain above the affected employees will often be included so that the team has sufficient information regarding the day-to-day operations of the relevant department.
Certain outside consultants will often be contacted to assist the team in its assessment and planning duties. Some such consultants may include
• Psychiatrists or psychologists experienced in violence risk assessments;
• Investigators who specialize in TAM work;
Finally, the TAM team should be headed by a manager with the authority to fully commit the organization’s resources to the effort and expense necessary to take meaningful protective measures immediately upon determining that they are essential. This TAM team leader should make the final decision on the organization’s response if the team cannot reach consensus. If either the authority to proceed or sufficient decisiveness is lacking in this key person on the team, undue delay, inaction, and very possibly physical harm may ensue.
TAM Principles
While it is common to react to news of a mass workplace murder by assuming that the act was entirely unpredictable and thereby unpreventable, the process of threat assessment investigations relies on a number of major principles that represent an absolutely opposite view:
1. Targeted violence results from a process of thinking and behavior that can be understood and often detected in advance. To be able to carry out an act of targeted violence, the perpetrator must pass through a series of steps along the way. He must develop a sense of grievance or injustice that motivates him. He must hit upon violence as the only or best option available to him to redress his grievance. He must select the individual or organization to target. He must choose the method of attack as well as the date and time for an attack. To do so, he may conduct research on the target, including stalking the targeted individual or placing the target site under surveillance. He may need to acquire the means to approach the target, breach any security measures in place protecting the target, and carry out the intended attack to the desired conclusion. The instigator’s dispute with the target and subsequent planned violence may take center stage in his life and rise to the level of an overriding obsession that the instigator readily and compulsively talks about to those around him.
2. Targeted violence takes place in the interplay between the instigator, past stressful events, the target, and the current situation. It is considered useful to determine how the instigator has reacted to prior instances of unbearable stress. If, in earlier situations involving significant losses (home, family, job, position, etc.), the instigator attempted acts of violence (including directed at himself), this information may be crucial to an understanding of how he may perceive his present situation. Likewise, other information regarding the instigator’s background may be critical to the assessment process. Where he lives; his vehicles; his access to or familiarity with weapons; his educational, medical, and employment histories are all among the information about the instigator that the TAM team may require. Information regarding the target will also be critical. The TAM team should seek answers to the following questions. Is the target known to the instigator? Can the target be easily approached at work, home, or other obvious locations? Does the target take the threat posed seriously? Can the target’s normal locations be “hardened” (receive additional security measures)? Will the target accept and follow security advice? Finally, the current situation, both in terms of any event likely to trigger untoward acts and the overall atmosphere, environment, and influences acting on the instigator must be examined. Whether the instigator is surrounded by a culture, family, group of associates, or counselors that encourage or discourage violence as a means of conflict resolution is also important to determine.
3. Addressing targeted violence requires determining the “attack-related” actions of the instigator. As noted previously, the instigator will normally travel a path leading to an eventual attack. At each stage of this journey, he may communicate information or be observed in behavior that signals his thinking, planning, and preparation. Searching for information regarding these factors is key to the proper assessment of a situation, to determining whether the instigator poses a present danger to the target (s). If, for instance, the instigator is known to dislike a coworker with whom she has exchanged angry words, is this sufficient reason to consider her to pose a threat to the target? An assessment investigation that determines that the instigator recently has acquired a firearm and was seen sitting outside the targeted employee’s home in her car would clearly support an assessment that the situation should be of serious concern.
The Role of the Loss Prevention Professional in Threat Assessment and Management
The conduct of TAM assessment investigations relies on the same skills, techniques, and aptitudes of any other kind of investigation. The loss prevention professional should take steps to prevent the investigation itself from becoming a factor that contributes to an attack. Therefore, much of the work of the TAM team should be kept from becoming obvious to the instigator.
The following should all be considered in TAM assessment investigations by the loss prevention professional:
• Reviewing records. If the instigator is an employee, all available files must be reviewed, including employment application; background reference checks that were completed at the time of hire; all evaluations by supervisors, coworkers, or subordinates; records of counseling or discipline; any complaints, grievances, or even lawsuits against the employer, coworkers, and others; attendance and leave records; training records; and any prior safety or misconduct investigations involving the instigator. Examining the context in which the instigator first became of interest to the TAM team. Care should be taken to understand the reasons for the initial report concerning the instigator and determining the credibility of the complainant. The first notice to the TAM team that the instigator concerns a coworker, supervisor, or other company-related person may contain information that will help the TAM team understand the nature of the dispute or injustice that may be at the heart of any motivation to commit violence.
• Researching in the public record any history of court actions (civil or criminal) involving the instigator. If the instigator is involved in a years-long dispute with an individual supervisor or store, the record may be rich in information that describes the degree of anger that the instigator may harbor against the target (s). Similarly, if the instigator has elevated the grievance to a “cause” or “crusade” against perceived perpetrators of great injustice, the TAM team should carefully consider how committed the instigator may be to punishing the target, regardless of the cost, to himself or others.
• Interviewing persons with historical or current information on the instigator’s thinking, capabilities, motives, and plans. Care should be taken that anyone interviewed by the TAM team can be relied on not to disclose to the instigator that the assessment investigation is being conducted.
• Examining the instigator’s workspace. In the case of instigators who are employed by the retailer, and if consistent with established company policy, examining the instigator’s immediate work areas may be of immense value to the assessment. If the examination can include a review of the company computer files accessed by the instigator, it may be possible to uncover information relating to the underlying grievance held by the instigator, pre-attack planning and actions, ritual settlement of his affairs and disposing of his property, and the identity of intended targets. Also if permitted, the TAM team should try to view the instigator’s email traffic on the organization’s computer system.
• Making direct contact with the instigator. At some point, the TAM team may decide that the benefits of speaking directly with the instigator outweigh any risks of initiating such contact. Contact with the instigator may allow him to vent his frustrations and reduce his sense that only violence can give voice to his grievance. The instigator may provide a clear view of his intentions to actually cause violence and accept the attendant consequences. An instigator may reveal the amount of research, surveillance, and other attack preparation he has completed. The instigator may convince the TAM team that he lacks the organization, means, or capability to launch an attack during direct contact.
The focus of the TAM investigation should always be on seeking answers to the question of whether the instigator is progressing toward violence and, if so, how far advanced that progress may be. The answers to those questions are the heart of the actual threat assessment.
All the information that the loss prevention investigator is able to develop should be provided to the team and especially to the consulting psychologist. It is critical for the security professional to understand the ways in which the psychologist can contribute to the accuracy of the TAM team assessment and the active management of the instigator.
The security profession can provide the target hardening, investigation, and research capabilities to the overall TAM effort while the psychological profession offers insight into pathology and the likely effectiveness of treatments and health and social service diversions.
Unless the professions see themselves as allied in the TAM process, they are likely to work independently, possibly to cross-purposes. This can lead at best to uncoordinated actions of limited effect, and at worst to a string of actions that create a sequence of frustration, distrust, and hostility in the instigator that together can trigger actions that the instigator might not have otherwise felt compelled to undertake.
Without the TAM team approach, a security investigator could undertake a standard investigation interviewing coworkers, searching the instigator’s locker, and admonishing the instigator without knowing that the company human resources department had referred the instigator to a fitness for duty evaluation with a local psychologist. In such a case, the organization may be sending two messages to the instigator. On the one hand, he is likely to believe that he is being viewed as a criminal, while on the other, he is being told that the fitness for duty is intended to assess his suitability for return to work. One message may be perceived as confrontational and threatening, whereas the other may be viewed as collaborative and nonthreatening.
The instigator will likely consider the company to be double-dealing, insincere, and the psychologist to be simply trying to make a case for termination. With such a viewpoint, the instigator will be far less likely to be open to cooperative or therapeutic initiatives proposed by the company. He may also receive reinforcement for paranoid ideas that everyone at the company is “out to get him” and begin to add names to an internal list of people who deserve his retribution.
A key figure in the prevention of targeted violence is the psychologist who may be an active part of the TAM team or may assume other roles. Those roles and important considerations regarding those roles are discussed next.
The Role of the Psychologist in Threat Assessment and Management
Many experts in the field of workplace violence risk management suggest that mental health professionals, particularly psychologists, should be available as consultants to TAM teams.(5) Inclusion in this process acknowledges the necessity of having a better understanding of the mental status of the instigator, and the critical role that psychologists serve in acquiring and using this knowledge.
Psychologists are typically used by TAM teams in one of three capacities: background consultants, co-interviewers, and referral resources. In each capacity, the right psychologist can add value to the TAM effort by sharing their knowledge of mental illnesses, risk assessment, diversion techniques, and community treatment resources.
Background Consultant
As background consultants, psychologists are provided with investigative information. The TAM decision makers may benefit from insights drawn by the psychologist related to the likely mental status, possible future behavior of the instigator, and potential approaches that could be used to divert the instigator. Psychologists acting in this role are drawing on secondary sources of information, as they have no direct contact with the instigator. They are basing their advice on training and experience, combined with intelligence developed about the instigator. Their informed speculation can help guide the deliberations of the TAM decision makers.
Co-Interviewer
As a co-interviewer, the psychologist becomes a TAM investigator, typically partnering with a security professional to more directly assess the needs, motives, and capabilities of the instigator (for an excellent description of risks and benefits of interviewing instigators, see Calhoun & Weston [6]). Clearly, when employed as a co-investigator, the psychologist’s direct access to the instigator allows for a more comprehensive consideration of the instigator’s mental status. When practical, some interviewers (7, 8) may do this through telephonic interviews with the instigator, although face-to-face interviews must be considered a preferred—if riskier—methodology.
Referral Resource
TAM teams often find mental health professionals as useful referral resources. Psychologists, psychiatrists, and social workers may provide psychotherapy for instigators, helping them to learn socially appropriate ways of directing and managing their hostilities. Professionals used in this capacity are acting as part of a diversion effort. Selecting the right doctor for this job is critical because TAM investigators will want to have a continuous dialogue with the professional. While all mental health doctors will release information with their patients’ consent, there is a considerable difference in the information flow obtained by a professional who has a comprehensive understanding of TAM needs, compared to the doctor who rigidly guards what he believes is in the best interests of the instigator/client. The TAM effort can be impeded by a mental health professional randomly chosen or selected just because an opening in the schedule exists.
Having referral resources responsive to TAM needs requires knowing the community and developing a list of cooperating professionals. It is essential to create incentives so that the professional will give priority to your request. In some communities, it can be weeks or months before professionals have openings in their calendars. We have managed to have professionals create space in their busy schedules by having the organization pay them directly their full rate, bypassing insurance programs. This makes payment easier for the professional, and billing at the full rate provides a supplement to the contracted and lower rate typically paid by an insurer.
Another tactic we have used is to initiate payment to a provider to keep a therapy slot available. For example, if TAM considerations suggest that there is a likelihood of needing a referral resource in the near future, we contact the professional and ask that they start scheduling a block of time for our needs. This may be a specific time or just access to some unidentified time in their work week. We have had prescheduling of such therapy times for as long as eight sessions. Whether or not the instigator is actually referred, the professional will be reimbursed for his time. Of course, medical insurance will not reimburse for unused therapy time, and this method requires that the organization directly pay the service provider.
The Fitness for Duty Evaluation as an Investigatory and Diversion Method
The primary goal of TAM processes is to acquire sufficient information to increase the probability that instigators might be diverted into nonviolent courses of action. For those instigators who are employees of organizations, the fitness-for-duty (FFD) evaluation provides a method for not only data acquisition, but also for diversion.
The Standard Fitness for Duty Model
The FFD evaluation typically is used to determine if a mental health condition exists that interferes with an employee’s capacity to meet the demands of his job description.(9) The psychologist typically examines the personality and intellectual functioning of the employee to assess whether there are any barriers to continued employment and, if so, what corrective actions might be used to return an employee to work.
The typical FFD evaluation consists of an examination of employer records, followed by psychological testing and an interview. In many professionals’ offices, the psychologist or psychiatrist does not communicate with the employee until such time that the interview begins. Appointments and psychological testing are handled by administrative staff or student assistants. The psychologist’s or psychiatrist’s role typically ends upon submission of a report to the organization.
The Threat Assessment and Management Fitness for Duty Model
When endorsed by the employer, the model (TAM-FFD) used by the second author in TAM situations differs markedly from the typical FFD scenario. While the goals of the standard FFD apply, the TAM-FFD model extends the paradigm. The TAM-FFD process consists of first acquiring all possible available information on an employee and then establishing a relationship that we hope is conducive to enlisting the employee’s cooperation in the formal psychological evaluation as well as in future diversion efforts.
The TAM-FFD uses any and all available information about the employee. The organization’s human resources (HR) file is first reviewed. It is important to use all files contained in HR offices because general information, investigation reports, medical information, and personnel evaluations are sometimes kept in distinct files or even at several offices. HR files are a rich source of information about past history, beneficiaries, and changes of beneficiaries. These files can also provide information for use in related efforts to investigate the employee.
The TAM-FFD may include interviews with appropriate informants employed by the organization. Great sensitivity is necessary in selecting the informants for interviews because a guiding principle of the TAM process is to protect the dignity of the instigator. For this reason, substantial caution is used to identify discreet informants, and these are typically in a supervisory position. Occasionally, coworkers may be interviewed. In either case, considerable effort is made to alert the subjects of the interview that it is in their best interest to hold confidential the fact that the interview has taken place.
Mining public and nonpublic information databases is an essential part of the TAMFFD. Public information sources such as web search engines (e.g., Google.com) and meeting places (Myspace.com) can provide a rich insight into the actual lifestyle and aspirations of the employee/instigator. Through initial use of search engines, along with the employee name and email address, we have found extensive and useful leads. For example, on the MySpace.com site, one employee extensively wrote about his real and desired lifestyle, as well as his suicidal ideation.
Any information that can be developed regarding the instigator’s access to weapons can be helpful in the later portions of the TAM-FFD or by the threat management decision makers. Knowing how many weapons an instigator possesses allows his own admissions regarding this subject to be an insight into his cooperativeness.
Enlisting the employee’s cooperation is a multistep process that begins with how the employer presents the concept of the FFD to the employee. It is always encouraged to have the employer describe the FFD as a process that will assist the employer and employee/instigator to “move forward.” It is suggested that the employer describe himself as nonprofessional, who, because of the unique circumstances (reports of threats, unusual behavior, etc.) causes him to need to get the insight of a psychologist specializing in workplace situations. Furthermore, the employer is encouraged to depersonalize the situation, referring to workplace policies or legal advice that tie the employer’s hands. This method is generally successful in enabling the organization and employee to keep their focus on “moving forward,” which requires some degree of trust in each party.
The next step in the process involves the organization providing the employee/instigator with the appointment times and the psychologist’s contact information. It is important that the employee be directed to telephone the psychologist before the initial appointment. While it is described as a call to confirm the appointment and answer any questions that the employee might have, the initial contact, we hope, helps set the stage for a cooperative engagement. During this initial telephone call, accurate information about the assessment process is conveyed to the employee. At this stage, the employee is informed about how the evaluation will be conducted and the limited role of the evaluator. For example, the employee is informed that the evaluator does not make decisions related to termination actions. Alleviating the employee’s normal evaluation apprehension allows the employee the opportunity to be less guarded, as he too comes to see the process as a way of “moving forward.”
In the TAM-FFD model, the next contact with the employee/instigator is the psychological testing appointment. Our model involves having the psychologist continue to work on relationship building with the employee by having the psychologist fully engaged during the testing process. The TAM-FFD model has the psychologist administering all the tests, sometimes over a period of more than 5 hours. During this process, the psychologist is answering all questions and providing beverages typically found in an office setting.
The intense involvement of the psychologist allows direct observation of the instigator over a prolonged time, leading to a wealth of data that would not otherwise be evident. Furthermore, such a prolonged exposure to the psychologist maximizes the likelihood that the employee might actually share truthful and important information during the clinical interview. Imagine, for instance, the difference between being asked sensitive questions about your own idiosyncrasies, failings, grievances, aspirations, and plans by someone you met 5 minutes ago. Might you be less willing to truthfully share compared to a situation in which you had 5 hours of previous and relatively benign experience with the interviewer? Finally, building this relationship allows for the possible later use of the psychologist as a conduit between the employee and employer, as will be discussed later in this chapter.
The psychological interview enables a continuing check on the employee’s mental status (earlier observations of such taking place in the telephone call and testing process). The interview is an excellent forum for determining the presence of paranoid delusions and the possibility of auditory command hallucinations, both of which are critical risk factors in violence. (10, 11) Furthermore, the interview provides a venue for ascertaining the instigator’s interest, planning, ability, and value placed in violence. (12) The possible contributing influence of substance abuse also can be determined.
The TAM-FFD interview is focused toward the eventual goal of determining the employee’s interest in violence and whether he is willing to take affirmative steps to demonstrate that there is no inclination toward targeted violence. Toward the end of the TAM-FFD interview, the instigator is asked about whether, as a condition of return to work, he would be willing to signify that he has no interest in firearms. This is what is known as the “Test.” Of course, the hoped-for answer is that the employee desires to return to work in the worst possible way and would gladly relinquish rights to firearms ownership to accomplish this goal. In our experience, the vast majority of employees eagerly accept this as a condition of continued employment, thus passing the Test.
The passing of the Test allows the employer to confidently set return-to-work conditions that include relinquishing possession of currently owned firearms and disclaiming any intention of future firearms acquisition. While such efforts cannot completely obviate the possibility of the employee accessing firearms, it can be an important step securing a commitment not to injure others and removing already-acquired arms from the instigator. We have successfully used this method to frame not only the return-to-duty process, but also the termination process as part of a benefit package. We have the employee turn their weapons over to police authorities and provide supporting documentation to the employer. In stark contrast, in a case in which we were not a party, an instance of a workplace mass murder using firearms occurred after a return-to-work evaluation that did not address relinquishing firearms.(13)
One of the final aspects of the TAM-FFD is interviewing one or more family members. While this is not always needed or possible, bringing a spouse into the evaluation process provides for additional information to gauge the threat value placed by the instigator. The spousal interview is predicated on the assumption that the spouse does not want her husband to act out violently, hurt anyone, or be subject to incarceration. So long as the psychologist can convince the spouse that their goals are identical, the spouse may provide useful information about planned violence and the lifestyle of the employee. The spouse may share information about violence history, such as incidents of road rage or domestic violence, and confirm a history of substance abuse and weapons possession. Furthermore, a spousal interview allows for assessing whether the spouse might serve a function to de-escalate the situation. By building rapport early on, the spouse may later serve a role in “moving forward.” Unfortunately, it is our experience that spouses are only sometimes effectively used in this manner, as they often take the world-view of the instigator, believing that the instigator is being abused by his coworkers and organization.
After the Employer Decides: Monitoring the Status of the Instigator
After receiving the fitness for duty evaluation and also reviewing other consultant reports (e.g., legal and security), the employer ultimately determines whether to retain or terminate the employee. It is our view that this is only a decision that can be made by the employer, and we offer no direction to the employer on this issue. What we do provide, however, is a range of management options that are individually tailored to the needs of each situation and dependent on whether the employee/instigator is ultimately discharged or retained.
In a retention situation, the instigator typically requires a range of treatment options that may include one or more of the following: hospitalization, anger management, psychotherapy, medication, assertiveness and communication skills, or substance abuse treatment. The results of the TAM-FFD can be used by the employer to justify conditions of continued employment including referrals to various programs. While treatment providers can be invited to examine the TAM-FFD report, we urge caution about releasing a copy of the report to the provider if the employer has concerns about the contents of the report being seen by the employee. Once released, the report will become a permanent part of the instigator’s treatment file, subject to his review and permanent possession. It is our experience that instigators are unlikely to view their own TAM-FFD with objective detachment.
Some employers may ask, “Why not just make the treatment referral ourselves and save the money on the evaluation?” It is our experience that a comprehensive assessment allows for better case management. For example, a quick and simple organizational referral to, say, an anger management program may miss the complex treatment needs of the instigator. Furthermore, merely sending the instigator to a psychotherapist will not lead to a complete identification of the treatment needs. Rarely will the instigator self-identify all the factors leading to a referral and his own failings that need psychotherapeutic attention. An examination of the TAM-FFD will allow the therapist to better understand the client’s situation.
Monitoring compliance with TAM-FFD recommendations is a role frequently performed by the Employee Assistance Program (EAP), the employer’s counseling and referral resource. The EAP consultant can review the TAM-FFD and meet with the employee to review conditions of continued employment. The EAP can then monitor the instigator’s compliance with the programs and ultimately communicate with the employer about return-to-work readiness. On particularly complex cases (e.g., involving methamphetamine-induced persisting psychosis), the second author has suggested a second, return-to-work FFD, following completion of all treatment. Some employers may feel reassured when their TAM-FFD psychologist makes a final assessment of the employee’s readiness to return to duty.
In a discharge situation, the employer may consider the advantages of providing financial security and other benefits to the employee who will be terminated. We typically consider approaching the instigator with a package that includes incentives for him to “move forward” and disengage from his employer. Severance agreements typically include several months of continued salary, medical insurance (considered important so that the instigator can access treatment), and outplacement counseling.
Meeting the goal of disengagement requires that the ex-employee minimize or refrain from contacting the company. Sometimes the discharge agreement specifies that only one person in the organization (typically in HR) is designated as a contact point, either for the instigator or sometimes limited to only the instigator’s spouse. Alternatively, we have employed the services of the TAM-FFD psychologist as the contact person. Having previously developed a relationship, the ex-employee may see the psychologist as a comfortable conduit to the former employer. Using the psychologist as the only liaison also helps to sever the perceived bond between the employee and organization, thereby facilitating the separation process.
An additional role that can be employed by the TAM-FFD psychologist is to monitor the progress of the ex-employee. Regular telephonic contacts can assess the instigator’s perception of the helpfulness of the outplacement counseling, any problems in finding a new job, and whether the instigator appears to be coping and disengaging from the former employer.
In functioning in this monitoring role, it is important that the psychologist clarify that he is acting as a consultant to and liaison with the employer. The instigator must know that there is no confidential communication and that the consultant’s job is to assess “how things are going.”
Functioning in this role, the second author has had occasion to suggest modifications of the termination package, such as a longer period for outplacement counseling. Maintaining contact with the instigator also allows for feedback to other providers about the effectiveness of their interventions. For example, after one instigator had difficulty in finding a new job, it became evident that his interview skills needed polishing. A telephone call to the outplacement counselor served to alert the counselor to this need.
TAM Countermeasure Planning
If the TAM investigation substantiates a concern that a legitimate threat is posed by the instigator, certain countermeasures or other actions must be planned.
The key question for the TAM team process is simply, “What can we do to promote safety for the target and others in this situation?”
Unfortunately, the retail environment poses certain security problems not encountered in most office or industrial environments. In a law office, for example, all the working staff can be placed within secure space, and each visitor can be individually screened before being admitted. In insurance companies, all claimant meetings can be placed in a common set of rooms or booths situated outside the secure office space. In a factory, high perimeter fencing, gated driveways controlled by a security access booth, and rolling gates can substantially impede instigator access to targeted individuals. Retail store space is specifically designed to be inviting to the public and must allow visitors unimpeded access to the entire sales floor, other customers, and the majority of employees. In addition, the employee parking areas for retailers tend to be openly accessible to the public, so attacks in these areas are relatively simple to accomplish.
Retailers also have the added burden of loss of public confidence if a worst-case attack is accomplished in one of its retail stores. If a mass murder occurs in the factory where autos are manufactured, the public does not automatically relate it to any personal danger. If a similar attack is successful at a retail location, the resulting television coverage can have wideranging negative impact on the store’s branding efforts.
The TAM team cannot plan only short-term, immediate safety steps. While some factors, such as improving access control to the workplace, may be of immediate priority, the team should understand that the instigator may be a lasting problem for the target and entire workplace.
In light of the fact that physical separation of the targets from the instigator may not be achievable by barriers, locks, and traditional access control measures, the retail TAM team must consider relocation of the targeted employee to another store. In some cases that relocation may require that the employee agree not to tell friends, family, or associates where the new store is located. In extreme cases, the employee may even have to be relocated to another city or state. Depending on the severity of the threat situation, the employer may wish to negotiate a relocation and employment termination agreement with the targeted employee.
Certain long-term, and expensive, measures may be necessary. For instance, a short-term solution may be to have an armed security officer in the parking lot of a convenience store or at the entrance to a mall store. At the same time the retailer’s loss prevention department can ask the mall security department to be on the alert for the instigator. The store staff should be given particular instructions on what to do if the instigator is observed near the store, in the parking lot, or mall security advises that he is nearby. A long-term solution may be the transfer of the targeted staff to other stores. Some retailers, due to the size of their operations, may have the ability to transfer the targeted individual to stores located in other cities or states, effectively hiding the target from the instigator. Even after the period of immediate threat has passed, these security enhancements can continue to provide benefit by making workers feel safer in the workplace.
The TAM team must look at all major components of the problem in addressing possible solutions. The TAM team should ask itself, “What can be done to affect the situation in which the instigator operates to reduce the likelihood of an attack?” Likewise, the question “What can be done to alter the expected event to reduce the likelihood of violence?” should also be answered. Finally, the team should address the question, “What can be done with the target (person or site) to reduce the likelihood of an attack?”
The TAM team should not be afraid to be creative in its approaches to the problem. While it must be cautious, it can often determine solutions that fit the complexities of the situation well if it is willing to think “outside the box.”
Examples of this kind of thinking might include using the services of an FFD professional. Based on the results of the assessment, the organization may consider referring the instigator to anger management training, psychological counseling, and psychiatric treatment. If the instigator is willing but not able to afford the training and other services, the organization may consider funding these programs. Further, if the instigator is going to be terminated, and it is known that he is concerned for the long-term treatment of his child’s chronic disease, should the TAM team recommend a separation package that includes continuation of medical plan benefits for a certain period paid for by the organization? Also, if the target’s current workplace is well known to the instigator, should the organization consider a transfer for the target to another branch or even another city?
In addition, the TAM team should realize that most organizations cannot afford to “go to war” with the instigator. If an organization is pushed, it may fire the instigator or threaten a lawsuit. If an instigator is pushed, he may commit mass murder. He possesses offensive options that organizations simply cannot use.
Provocative, punitive, prosecution-based solutions will rarely net the enhancement in safety that the organization requires. It is often difficult for organizations to put aside an adversarial posture when dealing with instigators. Such actions tend to increase the intensity of the conflict with the instigator, not reduce it.
The TAM team should seek disengagement from the instigator, not further entanglement in lawsuits or criminal actions. While doing otherwise may satisfy an organization’s desire to somehow obtain “justice,” such pursuits will rarely provide a lessening of the safety problem. The instigator may not initially commit a serious criminal act that will lead to long-term incarceration. Making misdemeanor prosecution a centerpiece of countermeasure planning may only increase the likely danger. Courts will only be able to impose moderate sanctions at an early stage, which are unlikely to reduce the threat posed in a meaningful way. A series of arrests for minor offenses or being dragged through prolonged litigation initiated by the organization may simply add to the instigator’s reasons for viewing himself as the victim of injustice. He may then feel warranted in escalating his responses to this perceived provocation.
Having the instigator escalate to a stage where serious criminal justice sanctions can be employed is precisely what the TAM team should be working to avoid.
The Restraining Order
Many employers, police officers, investigators, and human resources managers believe that the best response to a threat situation is for targeted persons to obtain a restraining order (sometimes known as a “protective order”). This is a civil court order requiring the instigator to stay away from the targeted persons and premises and not harass or harm them. The police can arrest the instigator if he approaches or contacts the target(s).
While such an order can sometimes be useful, many people place too much confidence in its true protective power. The following are cautions to consider regarding such restraining or protective orders:
1. The act of being served a court order, typically by police officers, can convince the instigator that the target is escalating the conflict and is not interested in any peaceful settlement to the dispute. Some instigators justify moving to violence in their own minds because they believe the targets have decided to “go to war.”
2. The temporary restraining order will be followed by a court hearing at which the instigator and the targets are brought together in a courtroom. In some cases this is exactly what the instigator wants (physical closeness to and interaction with the target) and it results in increased engagement between the parties, rather than the preferred disengagement.
3. The court hearing allows the instigator to know the exact time and place where the target will be. If the instigator is bent on violence, especially after losing the hearing, he is afforded a perfect attack opportunity as the target leaves the secured area of the court complex. Parking lots, and even the courthouse steps, have been the scenes of fatal attacks.
4. In many jurisdictions, the court action must be initiated by individuals, as opposed to organizations, thereby requiring a degree of personalization between the individuals and instigator. This may focus the instigator’s anger at individual targeted persons, rather than a faceless corporation. This is seldom good for the individuals.
5. In most jurisdictions, the arrest of a person violating the restraining order will result in a low bail and a sense of humiliation and anger in the instigator toward the targets. Penalties tend to be very minimal fines or brief incarcerations. As such, an arrest has the potential of creating an angrier instigator who may have little regard for the restraining order.
Fundamentally, we must consider the wisdom of relying on a person whom we fear is willing to commit murder to conform to rational behavior simply because a court has ordered him to do so. Should we really expect that a person capable of homicide will be deterred because he may commit a misdemeanor contempt of court?
Too often, especially in domestic violence incidents, the victims are shot to death after obtaining the restraining or protective order. Simply put, papers do not stop bullets. TAM investigators and targeted individuals should not think otherwise.
TAM Reports
The TAM team should attempt to express, preferably in writing, its combined opinion on the state of the situation as it relates to whether the instigator appears to intend violence, is capable of carrying out that violence, and has engaged in pre-attack behaviors. The assessment should detail the methods used in obtaining the information and reaching the opinion, including any input received from outside consultants, researchers, and investigators. The assessment should also provide details of the information that persuades the TAM team that the situation is moving toward or away from violence.
The TAM report must also lay out the recommended steps the organization should take to prevent a violent outcome.
It is important to note that the TAM report and the assessment upon which it is based are both valid only as long as the underlying situation remains unchanged. As such, it is a “snapshot” in time which documents conditions as they were at a particular moment. Threat situations are extremely dynamic, constantly changing as new events occur. Therefore, new assessments and management plans also may need to be evaluated in light of these new events or when previously unknown information comes to light.
For example, if the instigator brandishes a firearm on day one, threatening to shoot his estranged wife, the assessment may be that the situation is one of high risk. If the instigator is taken into police custody on the morning of day two, the assessment may be downgraded only to shoot up again in a few hours when the instigator is released on bail. In a similar vein, if the target leaves town for a week to vacation at a location unknown to the instigator, the assessment of danger will probably lower, while it may rise upon the target’s return home.
Any TAM report must inform the reader that the assessment is subject to immediate change upon new developments or information. It should also identify any information limitations and assumptions included in the assessment.
Law Enforcement Assistance
If there is a truly imminent danger of serious physical attack, or if the instigator is present and is persistently unwilling to leave or desist from unlawful behavior, the police should be immediately called for an emergency response.
In less imminent circumstances, a TAM team may decide at some point to obtain help from the local police. If prepared to properly approach the police, the TAM team can maximize the assistance it can expect. Otherwise, such contact can be an exercise in frustration at best and make the situation much more dangerous at worst.
It is clear that the police in most jurisdictions are inundated with cases. As such, the police concentrate on matters that are judged to be especially serious, such as drug trafficking, organized crime, gangs, and homicides. In most cases, police patrol officers are responding to reports of completed crimes, documenting the available information. Where there is easily obtainable evidence and identified suspects, they will effect an arrest. In cases where a serious crime has not yet been committed, or the evidence is less than perfectly clear, it is rare for the police to go beyond the filing of an initial report. In the more serious crimes, investigations are referred to police detectives to pursue the case. This is not poor police practice, simply a logical allocation of police resources.
Very few police officers or detectives have been trained to see threat situations as matters to be approached with careful assessment and management. Traditional police emphasis has been on enforcement after crimes occur.
TAM teams wanting to obtain law enforcement assistance must therefore make full use of the assessment aspects of TAM in order to inform and educate the police on both the gravity of the threat situation and the ways law enforcement can best help.
The following are considerations to review prior to making law enforcement contact:
1. The TAM team should conduct a full investigation and assessment before calling the police.
2. The TAM team should be willing and able to lay out each and every factor leading to a conclusion that the situation appears to be potentially violent.
3. If the TAM team believes that the instigator represents a serious lethal threat and can point to specific statements and actions by the instigator that would convince police to be involved, the team should seek police assistance in managing the situation.
4. The TAM team should never overstate the credibility or reliability of information that forms the basis of its assessment. The TAM team should carefully review all evidence it is considering and remove all supposition or unsupported conclusions from its assessment. The police will not appreciate later learning that they have been “oversold” on the seriousness of the situation.
5. The TAM team should attempt to contact the police at the highest possible level, preferably through the chief, sheriff, district commander, or precinct commander. Senior police officials, provided with the specifics of a grave situation likely to represent a lethal threat to multiple targets, are much less likely to shrug off the report than the patrol officers. They are also able to command sufficient resources in terms of detectives, officers, and others to effectively help.
6. The TAM team should understand that contacting the police can lead to unintended consequences if the police choose to take aggressive action toward the instigator, such as a confrontation in which he is “warned” by the police on his doorstep. The TAM team should be able to address with the police what the assessment investigation may indicate will happen if such a provocative act occurs.
Law enforcement assistance can be crucial to a good outcome in many threat situations; however, as with restraining orders, TAM teams must properly plan how to approach and use police assistance. To do otherwise is unwise and may worsen the situation.
Case Study: A Threat in the Warehouse
The regional human resources manager of a multinational corporation phoned the first author on Monday afternoon saying that a warehouseman fearfully reported to her a threat by a delivery driver to shoot a supervisor who rescheduled the driver to start his day two hours later than before. They worked at a small branch operation 300 miles away.
The HR manager was authorized by the corporation to engage our TAM services. A temporary TAM team was formed that included two individuals from out of state: a corporate security manager and a psychologist retained for TAM services by the corporation’s national headquarters. The regional HR manager and the authors rounded out the team.
While the corporate officials traveled across the country, the first author discretely interviewed two workers who provided information about the instigator, “Tom”:
1. Tom had been fired elsewhere, boasting he had entered the office of a supervisor who had “messed with him,” pointed a gun at his head, threatening to kill him if not left alone. A friend hid the gun before police were called. There being no witnesses, Tom was never arrested.
2. Tom reportedly fired a rifle at drunken troublemakers menacing his family at a picnic. Police were not called.
3. Tom became violent when drunk, often brawling with little provocation.
4. Tom’s wife, a heart patient, cared for her aged father at their home and also babysat for their two grand-daughters. Tom’s employment provided the sole family income and health insurance. He was the only one who could pick up another grandchild after school because his old schedule ended so early.
5. Tom said that, if fired for refusing the new schedule, he would punch the supervisor, leave, return armed, and shoot everyone at the warehouse. He claimed his family would be better off if he went to jail.
6. Both informants, who knew Tom well, were convinced he would carry out the threat.
The team, including the corporate officials, met on Tuesday evening. The HR manager confirmed from company records that Tom’s health insurance covered his wife and that it was widely known that she could not work due to illness. Several members of Tom’s family had died at young ages, and he was afraid to die and leave his family destitute. Early contact with low-ranking police officials netted a directive to call “if something bad really happens.”
It was decided to directly contact the chief of police that night. The corporate security manager placed the call, informing the chief that there was a grave situation which had called him and the corporate psychologist to town, but that he was hesitant to discuss it on the phone. The chief agreed to meet the following afternoon.
Early the next morning the TAM team flew to the small town and secretly met with the local branch manager at a local hotel. He was shocked by the information the team had developed, but believed Tom was capable of carrying out the threat. Later that day the team briefed the police chief and his senior commanders. They pledged their cooperation, and one commander was assigned as liaison. The police believed Tom could have access to guns.
It was decided that Tom needed to be quickly removed from the workplace and armed security officers placed at the warehouse as soon as he knew he was being suspended. The TAM team wanted to get possession of his guns and allow the two psychologists to interview him at length. Obviously, the physical security of the psychologists during any meeting was paramount.
Flying home that night, the team discussed how to ensure Tom was not armed during the intervention meeting. Passing through the airport security checkpoints produced an idea. On Wednesday morning, the team had the HR manager telephone Tom at work and tell him that he was to fly to the regional headquarters to participate in an employee focus group over the next 2 days. He would stay at a hotel paid for by the company. He agreed.
On Thursday, the HR manager picked up Tom at the airport. Tom carried a small bag, which he had carried aboard the plane. Having passed through airport security, we were certain that he was not armed.
Meanwhile, we arranged for a provider of armed security guards to have two officers posted at the warehouse each day from 5:30 a.m. until 7:30 p.m., covering all hours that staff was at the site.
The psychologists and corporate security manager waited at the interview site, which included a conference room outfitted with covert audio and video monitored by two armed security officers in a nearby room. The first author’s investigators coordinated all the diverse parts of the plan.
Upon Tom’s arrival, the HR manager introduced him to the security manager and the psychologists. During the course of the next 4 hours, the psychologists spoke with Tom, assessing his attitudes, willingness to follow direction, and introducing him to the idea of his suspension. He was persuaded to allow the police to search his residence and vehicle for weapons. The first author coordinated with the liaison police commander, who dispatched a team of detectives to Tom’s house. They met with his wife and, after conducting the search, took away a number of weapons. Tom agreed to meet with a psychologist in his town who had previously been contacted by the second author. When he flew home Friday, he was calm, had explained the situation to his wife, and understood that the company was going to continue its inquiry into his actions and complaints. He accepted the fact of his suspension (with pay and benefits).
The armed security presence remained in place for a few more days, until it became clear that Tom was continuing his sessions with the psychologist, and a determination was made that he no longer posed a significant threat. The second author kept in phone contact with him on a regular basis, monitoring his progress and attitudes toward the company. He also conferred with the treating psychologist to confirm Tom’s compliance with his treatment plan. A few weeks later, Tom agreed to separate from the company and accepted a settlement package that provided a small amount of severance pay, extended family health coverage, and provided for the services of an outplacement firm. At last report, Tom had embarked on a new career, with different attitudes about work and coworkers.
This case study illustrates perfectly how a well-ordered response to a frightening initial informant report, using a multidisciplinary team and the threat assessment and management process, can move a potentially violent situation to a safe outcome. The investigative professional can fulfill a crucial role in that team, but only if he understands the proper methods and goals of TAM.
Conclusion
TAM investigations are becoming increasingly important for loss prevention professionals to master. The opportunities for coworker dispute, employee terminations, or even domestic violence to create real danger for the workplace through targeted violence are incalculable. The stakes can be extremely high, and the complexity of each situation must be carefully considered.
The retail loss prevention profession must take seriously its duty to protect employees from targeted violence. TAM is the set of actions, if learned and carefully employed using all the resources available to the employer, which minimize the likelihood of a catastrophic event occurring in the retail workplace.
As the specialized approaches used in workplace violence threat scenarios have become more widely adopted, the loss prevention practitioner is provided with the chance to divert, delay, redirect, or disrupt situations that might otherwise escalate to lethal violence.
While the threat may be forestalled today, the instigator may someday return. As such, these cases are rarely considered fully closed. They may become dormant for a while, but as long as the instigator can focus on the target and is at liberty to mount an attack, the situation will probably bear long-term monitoring.
We have found that, when an integrated approach is used and security professionals and psychologists work together, better outcomes can be achieved than when the professions work separately. Simply put, using such an approach creates a safer and more promising future for both the instigator as well as the rest of the workforce.(14)
(1) U.S. Department of Justice, Federal Bureau of Investigation. Workplace violence issues in response. 2003:13.
(2) U.S. Department of Justice, Office of Justice Programs. Protective intelligence & threat assessment investigations. 1998:14.
(3) U.S. Department of Justice, Office of Justice Programs. Protective intelligence & threat assessment investigations. 1998:14.
(4) Calhoun F.S., Weston S.W. Contemporary threat management. San Diego, CA: Specialized Training Services, 2003;48.
(5) McElhaney M. Aggression in the workplace: Preventing and managing high-risk behavior. AuthorHouse, 2004.
(6) Calhoun F.S., Weston S.W. Contemporary threat management. San Diego, CA: Specialized Training Services, 2003;145–181.
(7) Marc McElhaney, personal communication, 2004.
(8) Corcoran, M.H., and Cawood, J.S. (2003). Violence assessment and intervention: The practitioner’s handbook, 57.
(9) Stone A.V. Fitness for duty: Principles, methods, and legal issues. Boca Raton: CRC Press, 2000.
(10) Junginger J. Command hallucinations and the prediction of dangerousness. Psychiatric Services. 1995;46:911–914.
(11) Junginger J., Parks-Levy J., McGuire L. Delusions and symptom-consistent violence. Psychiatric Services. 1998;49:218–220.
(12) DeBecker G. The gift of fear. Boston: Little Brown, 1997;156.
(13) We are fully aware that some hold a very strong belief in the right to bear arms. Some may consider the Test as a provocative intrusion into this right. We are of the belief that the potential gain outweighs any potential risk, and in practice, we have had no problems in using this method.
(14) We thank Dr. Marc McElhaney for his kind review and comments of an earlier portion of this chapter.
Resources: Association of Threat Assessment Professionals
www.atapworldwide.org/index.htm.
Premier professional association for those engaged in high-stakes threat management. The purpose of ATAP is to afford its members a professional and educational environment to exchange ideas and strategies to address such issues as stalking, threats, and homeland security..
Documents:
Threat Assessment: An Approach to Prevent Targeted Violence (1995)
www.ncjrs.gov/pdffiles/threat.pdf
In-depth introduction to the concepts of threat assessment and management prepared by the U.S. National Institute of Justice.
Recommendations for Workplace Violence Prevention Programs in Late-Night Retail Establishments (1998)
www.osha.gov/Publications/osha3153.pdf
Information prepared by the U.S. Occupational Safety and Health Administration which primarily addresses the issue of robbery.
Dealing with Workplace Violence: A Guide for Agency Planners (1998)
www.opm.gov/Employment_and_Benefits/WorkLife/OfficialDocuments/handbooksguides/WorkplaceViolence/Prepared by the U.S. Office of Personnel Management as a guide to federal government agency planners in creating workplace violence prevention programs.
Workplace Violence: Prevention, Intervention, Recovery (2001)
http://hawaii.gov/ag/cpja/quicklinks/workplace_violence/
Comprehensive guide for private employers for establishing effective violence prevention programs, TAM interventions, and post-incident responses. Prepared by the Crime Prevention and Justice Assistance office of the State of Hawaii Department of the Attorney General.
Workplace Violence: Issues in Response (2004)
www.fbi.gov/publications/violence.pdf
This is the Federal Bureau of Investigation’s publication examining the issue of workplace violence and the role of law enforcement in its prevention.
ASIS International: Workplace Violence Prevention and Response Guideline (2005)
www.asisonline.org/guidelines/guidelineswpvfinal.pdf
Prepared by the American Society for Industrial Security International, this is a comprehensive guideline for private sector employers; it incorporates prevention and incident management information.
Examples of the Workplace-Related Situations Typically Encountered
Love Obsessed Kidnapper Begs to be Killed
Jociel G. Bulawin entered the store from where he was fired and confronted owner Mary McIntyre with two pistols. McIntyre had previously obtained a restraining order against Bulawin, who was romantically obsessed with her. When McIntyre and others in the store attempted to flee from him, Bulawin grabbed her by the hair and pulled her back into the store. Bulawin pointed a pistol at her, handed McIntyre a pistol, and begged her to kill him or he would kill her. The standoff lasted for 5 hours before McIntyre shot and killed Bulawin.
Domestic Attacker Killed In Store
Carrying a knife, Felix Vigil entered the large discount store where Joyce Cordova, his ex-wife, worked. Cordova had a restraining order against Vigil, but he repeatedly stabbed her. Albuquerque Police credit an armed customer, Due Moore, with saving Cordova’s wife when he shot and killed Vigil using a pistol which he was licensed to carry concealed.
Taylorsville, North Carolina 2006
Jerald Chapman waited in his car at the garden center of the store where his former girlfriend Rebecca Grogan worked. When she arrived shortly before 8:00 a.m., Chapman approached her car and shot her twice. He then shot himself, dying 6 days later. Grogan had recently moved out of the home shared with Chapman. Police credit the domestic dispute as the cause of the attack.
Paul Cook and his wife divorced in 1996. Five years later, Paul walked into the grocery store where she worked and pushed a grocery cart through the aisles for 10 minutes. He then approached an employee and asked for his ex-wife. After he was told that she was in a back room, Cook handed an employee a note that he was intending to kill her. Despite being told not to go into the back room, Cook found his ex-wife, exchanged words with her, and shot her. When confronted by arriving police, Paul shot and killed himself.
Employee Intervenes and Is Shot
Sharma Rochester confided to friends that she was concerned about her stepson Christopher Rochester wanting to do her harm. She obtained a restraining order to keep him away from her at both her home and the grocery store where she worked. John Brining, a 19-year-old bagger at the store was one of the people Sharma told. He made it a practice to check the parking lot before Sharma left to make sure that Christopher was not around. In March 2004, Christopher entered the store and put a gun to Sharma’s head while she stood at her checkstand. Sharma ducked behind the counter and John Brining intervened. Brining was shot once in the abdomen but survived. Christopher fled and later turned himself in to police.
“I’m Not Sorry for What I Did”
During a struggle at the store where she worked, Donna Jean Angelo was heard yelling “Let me go.” Her former boyfriend, Rodney Gene Startz, allegedly shot her in the head, leaving her to die. He fled to his home, eventually surrendering to responding police officers after a 7-hour standoff. Testimony indicated that Startz telephoned the victim’s brother to brag about the shooting. Angelo’s family said that Startz harassed her for months prior to her murder. Press accounts note that Startz had been arrested one month earlier for making harassing or obscene phone calls to Angelo. An arresting sheriff’s deputy testified that Startz told him, “I am not sorry for what I did. A man has to do what a man has to do.”
Returned Weapon Fired at Responders
After arriving at work, Elwood Lewis argued with coworkers and his boss, eventually firing a pistol at the boss. He was wrestled to the ground and coworkers unloaded the weapon, returning it to him when he promised to leave. When the police arrived, they found Lewis in the parking lot, having reloaded the weapon. He fired several shots at police, hitting no one. He was persuaded to surrender and subsequently charged with, among other things, attempted capital murder of a police officer, firearms charges, and attempted murder.
The day after Yasushi Kato was terminated, he returned to the closed restaurant where he had worked. He confronted restaurant owner Yukichi Ito, and an argument ensued. Kato stabbed Ito multiple times with a sushi knife. At trial, Kato blamed stress from being an undocumented foreign worker, having no money, and feeling isolated. He claimed that he was afraid of Ito. Under cross-examination, Kato admitted that he had told a psychiatrist that he wanted to kill Ito. Convicted of manslaughter, Kato received a 20-year sentence.
Threat Assessment in the Retail Environment
Risk assessments are the first step in creating an effective security program and are made up of a number of smaller components, including asset identification, security measure inventory, threat assessment, vulnerability assessment (security survey), and finally the overall risk assessment. Figure T-1 outlines these steps as a flowchart. This chapter focuses on the threat assessment step as it relates to retail security.
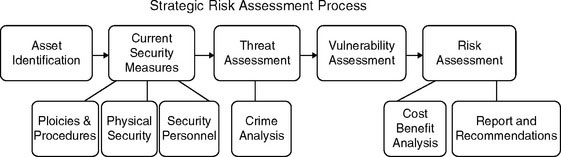
FIGURE T-1 Strategic Risk Assessment Process
Copyright © 2007 by Threat Analysis Group, LLC. Used by permission. Additional information available from Threat Analysis Group, LLC via www.threatanalysis.com
A threat is anything that can exploit vulnerabilities, intentionally or accidentally, and obtain, damage, or destroy an asset. Threats are classified as either human or natural. Threat can also be defined as an adversary’s intent, motivation, and capability to attack assets. A threat assessment, then, is an evaluation of human actions or natural events that can adversely affect business operations and specific assets. Historical information is a primary source for threat assessments, including past criminal and terrorist events. Crime analysis is a quantitative example of a threat assessment, whereas terrorism threat analysis is normally qualitative. In the retail environment, there are a number of common threats, inherent threats so to speak, that are common to all retailers. These inherent threats include internal theft and external theft. If retail security personnel know that theft is an inherent threat, why should they perform a threat assessment? We know that theft is a central issue for a retailer’s bottom line, but what about other crimes that affect profits in a less obvious way. Violent crime, for example, is a rare crime, but the impact is high. Customers victimized by third parties at a retail store are not likely to return. If a number of customers are victimized, a reputation for poor security can develop and impact sales. Liability exposure for third-party crimes is also a threat.
On the other end of the spectrum is the retail security professional who engages in security overkill, whereby security measures are overdeployed given the threat level, or security otherkill, where security resources are directed at a nonexistent problem. For example, a retail store experiencing a high level of robberies in a short time span decides to deploy security personnel. The security officers are charged with patrolling the store four times per hour, making frequent stops in the cash office. Despite the increase in security, the robberies persist. What happened? After a thorough analysis of the crime data, the retail security personnel might be shocked to find out that the robberies were mostly of customers in the parking lot. Otherkill.
What about the retail security professional who deploys security based on retail store managers who scream loudest. Often, this leads to security overkill, where stores with a low threat level are afforded a high level of security and stores with high threat levels are provided with minimum security. A threat assessment of all company stores, at least annually, will afford the retail security professional the ability to understand the threat at each store. Unfortunately, retail security professionals perform threat assessments only for stores they think are high crime. All too often, retailers have security personnel at a store where they don’t need the coverage, but at other stores where they don’t have security personnel, they need them. Threat assessments cure this problem.
Data-Driven Security
It has been argued that security is more of an art than a science. While that belief is generally true, the business of security is not an art. The security department is a business unit, not unlike other business units within a company that must justify their existence. The higher security moves up the corporate ladder, the more challenges the security director will face and the more business acumen will be required. A commonly accepted business paradigm is what cannot be measured cannot be managed. With the exception of shrink rates, the acceptance of this paradigm within retail security is not far reaching. No longer can retail security professionals rely solely on gut instincts. Data-driven security refers to using measurable factors to drive a retail security program, and one of the tools for allowing data to drive a security program is a threat assessment. Too often recommendations from the security department are presented with little or no thought as to why certain procedures or security equipment should be used. Often, the reason for deploying a security measure is that other companies are doing it. It is all too common in the security industry for there to be a propensity for using certain security measures without complete understanding of the problem or a thorough analysis of the security measure’s ability to be effective given the specific situation. Threat assessments can help retail security directors overcome this problem by identifying key concerns. How can security professionals justify to senior executives a sizable and usually growing annual security budget? By now, most security directors are keenly aware that a security program’s success depends on the commitment and support, or “buy-in” as it is commonly known today, of senior executives. Using anecdotal evidence to justify spending on physical security measures and costly protection personnel no longer suffices. A data-driven security program helps management understand that security is more than a must-have expense; it justifies costs to management by showing the proof of success that, when presented effectively, can garner the necessary buy-in from upper management and demonstrate a convincing return on investment. Security expenditures, just like other departmental budgets, need to be justified with empirical data and supplemented with cost-benefit analyses and comparisons.
Security Metrics
Threat assessments are also helpful in developing security metrics, which communicate vital information about threats to the retail stores and drive decision making. Metrics for various security components, such as the protection force or access control system, can be an effective tool for security professionals to understand the effectiveness of the overall security program. Metrics, as previously discussed, may also identify risk based on failures or successes of security components and can provide solutions to security problems. Security metrics focus on the results of security decisions such as reduction in thefts after implementation of a closed-circuit television (CCTV) or an electronic article surveillance (EAS) system. Security metrics help define how secure we are. They assist retail security professionals in answering basic questions posed by management, such as
• Are company assets protected?
• Which assets need more protection?
• Can the asset protection program be improved?
• What resources should be allocated to security?
Baseline measurements are often difficult to obtain, especially in the business of security where companies are, out of necessity, secretive about their protection systems. In recent years, security industry associations such as ASIS-International, the National Fire Protection Association (NFPA), and the International Association for Professional Security Consultants (IAPSC) have promulgated standards, guidelines, and best practices. In addition to published and accepted industry standards, the courts have outlined baselines of measurement for the security industry. An example of this is a Texas Supreme Court case, Timberwalk v. Cain, which outlines the specific factors necessary for establishing foreseeability of crime in premises liability lawsuits. In Timberwalk, the court set forth five criteria for measuring the risk of crime including recency, proximity, publicity, frequency, and similarity of past crimes. The professional security practitioner will stay abreast of industry standards and the law. While laws must normally be reasonably followed, security professionals may fine-tune published industry standards to meet the needs of their company.
Asset Identification and Existing Security Measures
All security programs, regardless of their complexity or industry application, are designed to protect assets, and generally speaking, assets are anything of value. Generally, assets consist of people, property, and information. A retail company’s assets include customers, employees, products sold by the retailer, and the supply chains and support services for getting the product to store shelves.
Asset attractiveness should also be considered in the threat assessment. Certain assets and businesses have a higher inherent threat level because of their inherent attractiveness to the criminal element. One example is electronics stores. Despite no previous crimes at a particular electronics store, the threat level for thefts of MP3 players is still high. The threat exposure is there, but the vulnerability need not be.
Existing security measures may include security personnel, physical measures, and policies and procedures. Security personnel include people specifically designated or indirectly working toward the protection of assets. Uniformed security officers would be the most visible and recognizable example of security personnel. Others may be involved in the protection as well who are not as easily identified, including undercover shoplifting agents, security managers dressed in business attire, and clerks trained in crime prevention. Physical security measures may include a range of low technology items such as barriers and curbing to high-tech measures such as closed-circuit television (CCTV) cameras, biometrics, and fencing. Physical security measures may also include items not visible to the naked or untrained eye, such as pressure mats and alarm sensors. Policies and procedures are written documents which relate directly to asset protection and guide the security program. Security manuals and security post orders are examples of policies and procedures.
Asset + Threat + Vulnerability = Risk
“Risk” is a commonly misused term, often used interchangeably with “threat.” Risk is basically a function of threats and vulnerabilities. In essence, risk is the possibility of asset loss, damage, or destruction as a result of a threat exploiting a specific vulnerability. Since threats are the focal point of this section, it is important to understand how threats impact a retailer’s assets. As you can see Figure T-2, reducing one of the factors that cause risk can reduce losses. A comprehensive security program attempts to limit all three in an effort to reduce risk to an acceptable level. Vulnerabilities are reduced through the application of security measures; assets are reduced to a level needed for business operations, with excess product stores in offsite warehouses; and threats are reduced through prosecution of shoplifters, proactive policing, and other methods.
The retail security professional’s strategic goal of countermeasure deployment is to reduce the opportunity for security breaches to occur by reducing vulnerabilities. Opportunities relate to targets in that removing or hardening an asset will lead to a reduction or an elimination of vulnerabilities. Asset protection programs integrate a combination of policies and procedures, physical countermeasures, and security personnel to protect assets against a design-basis threat. The characteristics of asset protection programs include deterrence, detection, delay, and defeat.
Controlling the capability and motivation of adversaries is a difficult proposition for retail security professionals. Motivation is created by the actual crime target and is considered the reason for security breaches. Since businesses usually require assets to operate, the removal of motivation is not always possible. Most retailers must instead turn their attention to blocking the opportunity of crime.
Threat Assessments
As discussed previously, threat assessments are evaluations of human actions or natural events that can adversely affect business operations and specific assets. Historical information is a primary source for threat assessments, including past criminal events, while real-time information is also being used with increasing frequency due to its availability in some arenas. Threat assessments are used to evaluate the likelihood of adverse events, such as robberies and assaults, against a given asset. Threat assessments can be quantitative or qualitative. Crime analysis is a quantitative example of a threat assessment. Retail security professionals use threat assessments as a decision-making tool that helps to establish and prioritize safety and security program requirements, planning, and resource allocation. The process of threat assessment includes
Threat Information Sources
Retail security professionals should endeavor to seek out all possible sources of threat information. Threat information should come from multiple and redundant sources. Depending on the nature of the assets in need of protection, the sources of threat information may include internal information, security breach investigative reports, law enforcement data, security consultants, media news reports, and industry associations, such as the Food Marketing Institute (FMI), National Retail Federation (NRF), and Retail Industry Leaders Association (RILA). Among the basic questions that retail security professionals ask are
• What assets have been targeted in the past?
• Why is that asset(s) targeted?
• Were any remedial security measures implemented in response to the attack?
Many retailers also maintain internal records of security incidents, breaches, and crimes. This information should be reviewed by retail security professionals on a regular basis while looking for trends and patterns that might indicate existing threats or point to a vulnerability that can be solved with remedial measures. External threat information should also be reviewed. This includes crime data from the local law enforcement where the facility is located. This is known as crime analysis and will be discussed in depth later in this section. Other external sources include private threat specialists.
Assessing Threats
After collecting, reviewing, and summarizing threat information from all available resources, retail security professionals must apply the threat to specific assets. Critical assets are the primary concern during the assessment; however, other assets may also be considered during the assessment phase. The goal of the assessment then is to estimate, quantitatively or qualitatively, the likelihood of occurrence that a threat will attack an asset.
Because of a lack of quantitative data, scenario-driven, qualitative assessments are appropriate for high-value assets that have suffered no prior attacks. A qualitative threat assessment is defined as a type of assessment which is driven primarily by the threat’s characteristics and are highly dependent on the assessment team’s skills. The threat assessment team or individual, using a qualitative approach, considers each asset in light of the given threat information for that asset and develops scenarios that may be used by adversaries to estimate the likelihood of attack. Using a qualitative rating system, the threat assessment team assigns a linguistic value to each scenario.
Accurate threat assessments are critical for retail security professionals; however, not even the best threat assessment can anticipate every possible scenario, including the addition of more assets. Criminals always adapt to and overcome updated countermeasures. In today’s world of technology, state-of-the-art countermeasures are outdated at an increasing pace, and criminals usually move at a similar pace. Retail security professionals should keep abreast of the latest threat information using the best available sources of information. Using the threat information sources discussed previously and adding to them where possible will assist in keeping the security professional abreast of the latest threats and the assessment report up-to-date.
Threat Dynamics
Everyday crimes, rather than terrorism or natural disasters, are the most common threat facing retail security professionals in protecting their assets, and a thorough assessment of the specific nature of crime and security breaches can reveal possible weaknesses in the store’s current security posture and provide a guide to effective solutions. A full understanding of everyday crime’s dynamic nature allows retail security professionals to select and implement appropriate countermeasures to reduce the opportunity for these incidents to occur in the future. Thus, the following section focuses on the dynamics of everyday threats, identifying their key elements, and how to analyze these elements to block specific threats. The retail security professionals should be well versed in a number of threat dimensions before selecting countermeasures. As conceptually outlined previously, these dimensions include
• The facility’s situational elements;
• Target/asset characteristics;
• Criminal motivation and capability;
Situational elements are those characteristics of the retail store that create an environment which is more or less conducive to certain types of crimes or security violations. For example, a shopping mall may suffer more from auto thefts in the parking lot than the average number in the community due to the number of targets (customer cars) in a small area. Another example of situational elements affecting crime may be the proximity of the facility to escape routes such as dense fields or wooded areas that can be used to conceal the offender on foot or quick escapes via highways used by the criminal in a motor vehicle. Situational elements also include the nature of the activities that occur on the property. Businesses face different problems than residential areas. The type of business that is conducted on a property may attract more crime. Jewelry stores, for example, maintain two types of attractive assets: large amounts of money and small, easily concealed property. While retail stores’ primary concern is usually shoplifting, an analysis of past crime data may reveal other threats that may not be evident. For example, a retail store that has a history of car-jacking robberies and assaults of customers may only be fully known by reviewing internal security reports or police crime information. Stores with high levels of auto thefts can narrow the field of targets by using threat assessments and crime analysis to determine which cars are more prone to theft.
Criminal motivation and capability are key to understanding the nature of crime on the property. Criminals, more often than not, are rational decision makers capable of being deterred or enticed to commit their acts. In modern criminal justice, it is widely accepted that certain people can be generally deterred from committing crimes given swift and severe punishment. Specific deterrence measures can be taken at the property level by introducing countermeasures that increase the risk of detection. For example, the presence of an EAS system or closed-circuit camera systems (CCTV) may deter many criminals. By the same token, people may also be encouraged to commit crime by providing them with ample opportunity and a low risk of detection. The criminal’s capability must also be considered by the retail security professional, whose goal is to reduce encouraging elements and increase the risk.
A criminal’s ability to select specific targets is a process by which the rational criminal will select the easiest target that provides the highest reward. Criminals also select targets where the rewards are high. Malls, for example, provide ample auto theft opportunities for the perpetrator who specializes in stealing cars. Target selection can be thought of primarily as a force of opportunity. The goal, then, for retail security professionals is to reduce the available crime opportunities at the facility.
Opportunity reduction strategies address the characteristics of the store that either encourage or deter crime. Each store will be different in terms of the solutions that are effective because each property has its own unique characteristics and unique threats. Unfortunately, what works at one store may not work at a similar store in a different geographic area. Opportunity reduction strategies may take the form of enhanced policies and procedures, physical security measures, or security personnel. Though the focus of this section is on cost-effective solutions to everyday crime concerns, you should not feel limited to using what is discussed herein, but rather are encouraged to be creative in your search for appropriate solutions for your particular concerns. While this section is not intended to be comprehensive in addressing every possible threat, it will endeavor to cover the more common crimes that affect many facilities. Retail security professionals are encouraged to study in depth the particular crimes that have historically occurred at their facilities.
Robbery
Robberies are a big concern for most retail security professionals and adversely affect business in a number of ways, including injuries, loss of property, negative reputation, and liability. There are two primary types of robberies: robberies of people and robberies of business. Shoplifting escalation (shoplifting incidents which legally escalate into robbery with the introduction of violence or force) and retail holdups are business-related robberies, and personal robberies include carjacking, purse snatching, and mugging.
A store’s situational characteristics which contribute to a robbery-prone environment are easily identified by experienced retail security professionals once they understand the precise type of robbery impacting the property. Poor lighting, hiding places, and unprotected assets provide ample opportunity for personal robberies. Poor employee training, unfettered access, and easy escape routes can create an environment prone to business robberies. Among the better security concepts developed in recent years is improved parking lot designs at retail stores and shopping malls. Additional curbing has been used to control the flow, direction, and speed of traffic, all of which create a deterrence to robbery and other crimes by creating obstacles to a robber’s escape from the property.
Robbery target characteristics depend on the nature of the robbery. Purse snatchings obviously require an unaware female holding a purse, while carjackings are limited to areas where cars can travel or park. Why does a convenience store experience more business robberies than another convenience store located across the street? Perhaps poor lighting and store windows cluttered with signs at the robbery-prone location are factors.
A robber’s motivation is typically a rational balancing of risk and reward. If an asset is valuable (high reward) and unprotected (low risk), the probability of attack increases. Jewelry stores are susceptible to robbery because of the high reward for perpetrators. As such, jewelry security professionals institute various strategies for protecting assets. Capability is dependent on the type of robbery executed. Jewelry store robberies take more skill than purse snatchings.
What does a robber look for in an attractive target? Regardless of the type of robbery, targets are rarely selected randomly. Obviously, the balancing test of risk and reward is a factor. Purse-snatch robbers seek out unaware women to target, with the reward being higher in higher socioeconomic areas.
Robbery opportunity reduction strategies vary with the type of robbery occurring on the property, but generally increased physical security measures, enhanced natural and artificial surveillance, and security personnel provide protection. Retailers may implement silent alarms or install bulletproof glass to protect against robbery. Convenience store owners may remove obstructive signs from windows to increase surveillance both into and out of the store. Often, simple and inexpensive changes in policies and procedures can have a positive impact on robbery reductions.
Theft and Auto Theft
Similar to robbery, there are many types of thefts. Situational elements at a facility are a primary determinant to the types of theft which occur. Retail stores are prone to shoplifting, while large parking structures experience auto thefts and burglaries of motor vehicles. Each year the automobile insurance industry releases data on the nation’s most frequently stolen cars and trucks. While it might surprise some readers that BMWs and Mercedes don’t make the top-10 list, it won’t surprise most security professionals. Other cars, such as Hondas, Toyotas, and Chevrolets, are easier to hide among the masses, are more easily fenced, or are more easily parted out for use in other cars. These characteristics lend certain cars to auto theft more than BMWs and Mercedes. What characteristics of your assets make a target more attractive? Cigarettes are a good target for young men, hence their location behind the counter in convenience stores.
The motivation and capability of thieves are subject to the risk-and-reward balancing test. Grocery stores, for example, often suffer from high levels of baby formula and over-the-counter drug thefts because of the high value of both items. These items are often turned over to a fence, or middle man, who will pay decent amounts to the thief and then sell the items back to the retailers. The capability of a thief is limited only by his skills and creativity. Some thieves work alone committing petty thefts, stealthy thieves may be pickpockets, and organized thieves may band together to commit larger thefts.
Normally, what a property owner finds valuable about an asset is also the same characteristic that a thief finds attractive. Jewelry is a good example, since it is valuable and easy to conceal because of its size. Financially motivated thieves will seek assets which they can later sell for a profit. Personally motivated thieves will steal assets which they can personally use, like drugs or expensive basketball shoes.
Opportunity reduction strategies for theft range from simple to the most complex, from moving an asset out of sight to installing vaults, alarms, and camera systems. Auto theft reduction may take the form of simple alarm systems to monitored tracking systems. Some grocery stores have taken to storing baby formula and over-the-counter drugs in locked cabinets. Clothing retailers have used electronic security tags (EAS) to prevent their clothes from being shoplifted. Here again, it is incumbent upon the retail security professional to fully understand the type of theft experienced at the facility to implement appropriate countermeasures.
Regardless of the retail crime experience, the threat assessment will help identify the problem qualitatively or quantitatively. While most retailers use a quantitative approach, a quantitative approach is much better for their needs given the vast amount of crime data available in the retail environment. It should be noted that the biggest failing in threat assessments is a lack of specificity. This is the key shortcoming of demographic social disorder models, which is a qualitative approach. Crime analysis, on the other hand, is a quantitative threat assessment approach and is as simple to implement as the qualitative approach.
Crime Analysis
The use of information regarding crimes and other security incidents helps the retail security professional plan, select, and implement appropriate security measures that address the actual risks of the store. Retail security professionals, after assessing the crime problem, can select the most effective countermeasures that eliminate risk or reduce it to an acceptable level. Budget justification is also accomplished through the use of statistics, since effective security measures will reduce the risk, and returns on security investments can be calculated and considered in the bottom line.
A common application of statistics in the security arena is the use security reports and crime data to determine the risks to a facility, including its assets and personnel. The use of statistics extends beyond planning security at an existing facility. Statistical data may also be used to select and plan security at new facilities. For example, the real estate department of a retail company may provide the retail security professional with a list of potential new sites, one of which will be selected based on, among other things, the threats at the location. In this role, the retail security professional serves as an advisor to the real estate department by conducting crime analysis of the proposed sites, as well as performs security surveys of each site to identify vulnerabilities in an effort to select the location that poses the least or a tolerable level of risk. In this scenario, the retail security professional will gather and analyze crime data for similar stores in the area surrounding each site to determine the security problems. The sites that have the fewest crimes can be evaluated further by means of a security survey which identifies potential or existing vulnerabilities. After the sites have been narrowed down by threat and surveys completed, the retail security professional has the necessary information to advise the real estate department.
Crime Triangle
Reducing the opportunity for crime to occur is a strategic goal of retail security professionals. The reason for this is the concept of a crime triangle, whereby three elements must exist for a crime to occur:
With little or no control over a determined offender’s desire, retail security professionals focus their attention on the remaining elements of the crime triangle by attempting to block opportunities and remove motivation, both of which can be controlled to a large extent by an effective security program. Motivation is created by the actual crime target. In the private sector, a criminal’s motive is the asset(s) that the security program is created to protect. Here again, assets include people, property, and information. Since organizations usually require assets to operate, the removal of motivation is a difficult task, if it is possible at all. Most businesses must instead turn their attention to blocking the opportunity of crime. The crime triangle is a simple yet effective method for illustrating how a crime can be prevented. As you can see in Figures T-3 and T-4, blocking opportunities for crime leads to a reduction in crime.
Purpose of Crime Analysis
Sir Arthur Conan Doyle, in his Sherlock Holmes mystery A Study in Scarlet, wrote, “There is a strong family resemblance about misdeeds, and if you have all the details of a thousand at your finger ends, it is odd if you can’t unravel the thousand and first.” It is on that basic premise that crime analysis is based. Whether a security professional is working proactively to address security concerns or reactively in litigation or during the investigation of a crime, crime analysis is an effective tool. From a security perspective, crime analysis is the identification of risk and vulnerability, and from a liability prevention perspective, crime analysis is the determination of foreseeability. Broadly speaking, crime analysis is the logical examination of crimes which have penetrated preventive measures, including the frequency of specific crimes, each incident’s temporal details (time and day), and the risk posed to a property’s inhabitants, as well as the application of revised security standards and preventive measures that, if adhered to and monitored, can be the panacea for a given crime dilemma (see Vellani and Nahoun).
While the preceding definition of crime analysis is holistic, it can be dissected into three basic elements:
• The logical examination of crimes which have penetrated preventive measures;
• The frequency of specific crimes, each incident’s temporal details (time and day), and the risk posed to a property’s inhabitants;
• The application of revised security standards and preventive measures.
Examining crimes perpetrated at company facilities is commonplace in today’s business environment. In larger retail companies, there may be a person or group of people who are solely dedicated to the function of crime analysis usually working under the risk management or security departments. In smaller retail companies, the crime analysis function is carried out by someone who also has other security management duties. Crime analysis may also be an outsourced function, whereby company personnel simply utilize crime data that a contractor has collected, entered into a database, and possibly provided some analytical workup or the tools to do so.
The second element is the analytical component. Crimes are analyzed in different ways depending on what security professional is trying to accomplish. Most commonly, facilities are ranked based on the crime level or rate. Generally, facilities with more crime or a higher crime rate are given a larger piece of the security budget, whereas less crime-prone sites are given less security money. Crimes are also analyzed on a store-by-store basis, allowing retail security professionals to select appropriate countermeasures. The various types of crime analysis methods are discussed in depth later in this section.
Finally, crime analysis is used to assess and select appropriate countermeasures. Crimes that are perpetrated on a property can usually be prevented using security devices or personnel; however, it should be noted that not all measures are cost effective nor reasonable. Certainly, a criminal perpetrator would be hard-pressed to steal an automobile from a small parking lot patrolled by 20 security officers, though that type of security extreme is not reasonable nor inexpensive. Crime analysis guides security professionals in the right direction by highlighting the types of crimes perpetrated (crime-specific analysis), problem areas on the property (spatial analysis), and times they occur (temporal analysis), among others. Using this information, security professionals can more easily select countermeasures aimed directly at the problem.
In summary, crime analysis seeks to
• Evaluate actual risk at a company facilities and rank facilities by risk level;
• Reduce crime on the property by aiding in the proper allocation of asset protection resources;
• Continually monitor effectiveness of the security program;
• Provide evidence of due diligence and reduce liability exposure.
Why would a retail security professional need to know how crime occurs? Understanding the factors that lead to crime, coupled with a comprehensive study of crime on the property, assists retail security professionals in creating effective security programs to block opportunities for crime. Crime analysis seeks to answer these questions:
Answers to these questions helps retail security professionals better understand the particular nature of crime on a given property and formulate specific responses. The What question tells us what specifically occurred. For example, was the crime against a person or property, violent or not, completed or attempted? What also distinguishes between types of crimes that require different solutions, such as whether a reported robbery was actually a burglary.
Where answers the location-specific question. Did the crime occur inside the walls of the location, in the parking lot, in the alleyway behind the site? If the incident occurred inside, did it occur in a public area or a controlled area? Determining the precise location assists retail security professionals in creating additional lines of defense around targeted assets. For example, if the crime analysis indicates that a vast majority of loss at a small grocery store is occurring at the point of sale, then little will be accomplished by installing a lock on the back office where the safe is located. In this example, the crime analysis will rule out certain measures, but by the same token, crime analysis will also spotlight certain solutions, such as increased employee training or updated accounting systems at the point of sale.
The When question gives the temporal details of each incident. Knowing when crimes are most frequent helps in the deployment of resources, especially costly security measures such as personnel. Temporal details include the date, time of day, day of week, and season that a crime occurred.
Who answers several important questions that help a retail security professional create an effective security program. Who is the victim(s), and who is the perpetrator? Knowledge of the types of criminals who operate on or near a given property assists retail security professionals in selecting the best measures to reduce crime opportunities.
How is the most consequential question to be answered by the crime analysis. How a crime is committed often directly answers this question: How can the crime be prevented in the future? More specific How questions may also be asked. How did the criminal access the property? If we know that a criminal has accessed the property via a hole in the back fence of the property, efforts can be taken to immediately repair the fence. Other specific questions reveal the method of operation (MO). How did a criminal enter the employee entrance of an electronics store to steal a television? How did a burglar open the safe without using force? Obviously, the list of examples is unlimited and retail security professionals need to ask as many questions about the criminal’s actions as possible to learn the most effective solutions. It is true that often the How will be the most difficult question to answer. This leads into a problematical area, as crime sources can be divided into two categories: internal and external. Internal sources of crime can be employees and other legitimate users of the space. They are called “legitimate users” of the space because they have a perfectly valid reason for attending the location, but in the course of their regular activities, they also carry out criminal activities.
External sources of crime are illegitimate users of the space whose prime motivation for coming to the site is to conduct some type of criminal activity. Security strategies may be vastly different between legitimate versus illegitimate users of space. For example, there can be several barriers between the outside public access and a specific target. If the property or retail security professional is concerned only with someone breaking into an area, then he will be ignoring the legitimate user who may have an access control card, personal identification number, password, biometric feature, or any number of other avenues of entry.
With these answers, security professionals are better armed to attack the crime problem.
Data Sources
Security Reports
A valuable and highly encouraged source of data is in-house security reports (SRs). As the name implies, these are reports of criminal activity and other incidents (parking, loitering, and security breaches) which may be of concern to retail security professionals. These reports may be generated by management directly or through contracted security companies. The validity of SR data is only as good as the policy which outlines the reporting and recording procedures, the quality of supervision over security personnel, and the verification process used to eliminate subjectivity. Regardless of the quality of their SRs, management should be cautious not to exclude other sources of data and rely solely on in-house security reports. In requiring the collection of security reports, management can stipulate precisely what information is beneficial for their purposes and is contained within each report. Having said that, management should strive to include the following minimum elements:
Law Enforcement Data
Police data are the most widely used source data for crime analysis because they present an accurate crime history for a property and are from an objective source. Since police departments don’t have a stake in a company or any associated liability exposure, their crime data are considered reliable and unbiased. Though some instances of crime statistics manipulation have occurred historically, rarely, if ever, are the statistics for specific facilities skewed. Most crime data manipulation occurs to overall city crime levels to serve various political goals. At the facility level, there is little reason for law enforcement agencies to skew the statistics.
Another advantage of police crime data is the vast availability due to extensive reporting, capturing, and maintenance of the crime statistics across most jurisdictions in the United States. While costs for the data vary from jurisdiction to jurisdiction, most fees are reasonable. The only downside to police data is the time required to obtain it from police agencies, with the necessary time ranging from hours to weeks.
Various crime data and analysis methodologies have been published and used by many cutting-edge companies in the protection of assets. Crime analysis methodologies have been published and subjected to peer-review in various security and police text books, the definitive security book being Applied Crime Analysis.
Law enforcement data are almost always accepted by the courts, and in fact are sometimes required by the courts in determining foreseeability of crime. Though a particular methodology may be subjected to scrutiny, the data are normally admissible. The security professional tasked with testifying on behalf of his employer is safe to rely on crime data from police departments as long as the methodology used is sound.
Law enforcement data sources include Calls for Service (CFS), Offense Reports, and Uniform Crime Reports (UCR). These data sets are typically easy to obtain, and in the case of UCR for large geographic areas are online at the Federal Bureau of Investigation website (www.fbi.gov). Local law enforcement data are normally accessible via Freedom of Information requests or under individual state laws regarding public information. For state laws and detailed instructions, contact the state’s Office of the Attorney General.
Uniform Crime Report
According to the Federal Bureau of Investigation, “the Uniform Crime Reporting Program was conceived in 1929 by the International Association of Chiefs of Police to meet a need for reliable, uniform crime statistics for the nation. In 1930, the FBI was tasked with collecting, publishing, and archiving those statistics. Today, several annual statistical publications, such as the comprehensive Crime in the United States, are produced from data provided by nearly 17,000 law enforcement agencies across the United States. Crime in the United States (CIUS) is an annual publication in which the FBI compiles volume and rate of crime offenses for the nation, the states, and individual agencies. This report also includes arrest, clearance, and law enforcement employee data.”
The Uniform Crime Report, or UCR as it is commonly known, is the nation’s crime measure. The UCR employs constant crime definitions across the country’s many law enforcement jurisdictions and measures the following crimes:
10. Forgery and Counterfeiting
13. Stolen Property—Buying, Receiving, Possessing
15. Weapons—Carrying, Possessing, etc.
16. Prostitution and Commercialized Vice
20. Offenses Against the Family and Children
These crimes were selected because they are serious by nature, they occur frequently, they are likely to be reported to law enforcement, they can be confirmed by means of investigation, and they occur across all jurisdictions in the country. Developed by the FBI, the UCR includes crime data for most geographic areas in the United States ranging from counties and cities to the nation as a whole. Intermediate areas such as state and metropolitan statistical area (MSA) crime data are also available. Though these areas are too large to be included as the primary focus of crime analysis, the methodology and classification system is what security professionals should understand and use at the property level.
When the UCR is used, it is best to examine violent and property crimes separately because they pose different concerns to retail security professionals and may require the application of different security measures. To be certain, crimes should be evaluated individually and as specifically as possible. For example, the crime of robbery can be further divided into robbery of a business and robbery of an individual. Often, the security measures used to counteract these two robbery types are different.
Calls for Service (CFS)
Though internal security reports and police crime data may overlap, it is incumbent upon the retail security professional to consider both in determining a store’s true risk. Thus, the next step is to contact the local police department and determine what types of data are available by address. Though it is rare, UCR data, or actual crime information, can be obtained by address; it should be requested and analyzed. If UCR data by address are not available, Calls for Service (or “911 dispatch logs” as they are referred to in some departments) should be requested from the law enforcement agency.
The primary data set is Calls for Service (CFS), which serves as the basis for crime analysis and provides for the most accurate portrayal of criminal and other activity at a property. Calls for Service can be thought of as the complete array of fragments that, when joined, form the most strikingly grounded survey of criminal activity for a specific property. Calls for Service consist of every report of crime, suspected crime, and activity called in to the police from a property. No other crime information source is as focused on a specific address for such a vast time span as Calls for Service, with the possible exception of in-house security reports generated by personnel operating on property 24 hours a day, 7 days a week. These inclusions, by definition, omit the imprecise factor of unreported crime. Research has concluded that unreported crime accounts for a 10% higher crime index, though this is highly dependent on the type of crime under observation. Despite the exclusion of unreported crime, Calls for Service still provide representative illustrations of criminal activity on a property.
Calls for Service are those crimes or other activities reported by a victim, witness, or other person to a local law enforcement agency via 911 emergency system and other channels. These reports may consist of actual crimes, from murder to theft, or suspicious activity, and other incidents such as missing children, motor vehicle accidents, and parking complaints. Whatever the concern, if it is reported by a person, it is noted by the law enforcement agency. The synopsis of the given incidents is included on the record, along with the location, date, and time the event was reported. In addition to the more obvious crimes, Calls for Service add elements that may be of interest to retail management, such as the previously mentioned suspicious activity, accidents, and parking violations which could be realized to be important in the holistic concept of crime prevention.
Being hyperinclusive, no single set of data exists that rivals Calls for Service for its accuracy. As with any set of statistics, many more desirable possibilities can be derived by performing additional correlations such as sorting crimes by precise location on the property and by times at which they occurred. When more raw data are available in a database, more meaningful cross-references and correlations are possible. You can consider that some of the fundamental ways people learn about various disciplines is through comparison, trial-and-error, or cause-and-effect methods; CFS allows trends or patterns in crime activity to come to light, which aids in the selection of appropriate crime countermeasures and provides for more enlightened comparisons between properties.
Among other considerations which users of Calls for Service should remember, Calls for Service data reflect information from the location where a complaint was made, which may or may not be the site of the incident. However, the location and precise nature of the calls can be verified and reliability enhanced when CFS are used in conjunction with the local law enforcement agency’s offense or incident reports, which will be discussed in depth later in this section.
Some newer Calls for Service systems encode data using the Federal Bureau of Investigation’s Uniform Crime Report codification system; thus, crimes can be easily differentiated from false reports and easily compared to city, state, and national crime levels. Older systems, though, must be converted to UCR through verification with offense reports.
Calls for Service are generally available from the local police department at a reasonable cost. In light of the availability and aforementioned considerations, CFS data can be used effectively to produce a fairly accurate crime history of a property, distinguish any crime trends or patterns, and compare properties.
Offense Reports
Offense reports are the written narrative of a crime investigation and are used to verify Calls for Service. This verification process is necessary because Calls for Service data reflect the location from where a complaint was made, not necessarily the incident location. Offense reports also confirm the type of crime committed, as well as the date and time of the offense. In many jurisdictions, only select portions of the offense report are available; however, there is usually enough information contained in the public information section to accurately build a database of crime incidents. Generally speaking, crime analysis seeks to build the most accurate database possible using only public information. During the course of a lawsuit, complete offense reports including arrest records and final case dispositions become available by subpoena, but the goal here is to proactively address the crime situation to prevent injuries and lawsuits.
More of an expansion of Calls for Service than an independent data source, offense reports, or “incident reports” as they are sometimes known, should clear up ambiguities and possible inaccuracies through verification of Calls for Service. Sometimes, however, an offense report is generated when police officers discover a crime independent from a call into the 911 emergency system. More precisely, offense reports are the written narrative of a call for service that resulted in an actual crime and includes the individual reports of all law enforcement agents, including officers, detectives, and supervisors who worked the case.
Although availability of offense reports may be limited by law because of inclusion of personal information, victim names, criminal methods, or ongoing investigation, retail security professionals should attempt to obtain them from the local law enforcement agency while in the process of conducting crime analysis. Often, however, most states allow the report or a portion of the narrative to be released to the general public upon request. As with all information, retail security professionals should seek access to as much relevant crime information as possible to help make knowledgeable management decisions. By no means should retail security professionals feel that they are in error for not including offense reports when they are not available, and on the contrary, they can only do what is reasonable and possible.
Methodology
The best method for learning the true threat at a retail store is to analyze internal security reports and verified police data using a computer spreadsheet application or database software program, such as Microsoft Excel or Access. Once this information is in a usable format, a number of basic and advanced statistical analyses can be performed. The retail security professional will adapt the analysis to best meet the needs of his organization. While some security professionals prefer highly detailed charting and graphing functions, others prefer to view the raw numbers. Either way is fine as long as the security professional is comfortable and able to disseminate the information to those who need the data. Among the statistical tools available to the retail security professional are crime specific analysis, modus operandi analysis, crime rate ranking, forecasting, temporal analysis, spatial analysis, and pattern analysis.
The crime analysis methodology outlined in this section has been tested in the courts and in private organizations, is based on a logical foundation, and provides useful information for a retail security professional. By no means is the methodology limited to what is described, as to a large extent, retail security professionals may find that the information requires customization to meet company needs. Whatever the case, this methodology provides the cornerstone from which to build a more comprehensive analysis when necessary.
Whatever methodology is utilized in crime analysis, it should at minimum coincide with case law on issues of foreseeability so that claims of negligent security can be negated. Most states use crime data to determine if crime was foreseeable (predictable) and if management is on notice of crime. If management is found to be on notice of crime in the area or on the property, they normally have a duty to protect their invitees (customers, employees, etc.) against it. Though a foreseeability analysis is a good place to start the process of crime analysis, it certainly need not be the end. To be proactive, retail security professionals require more data analysis to efficiently track security deficiencies and deploy more effective security measures.
Courts have typically accepted 2–5 years of historical crime data in premises liability lawsuits, while for security purposes, 3 years of crime data is recommended. At this point, the Calls for Service and corresponding offense reports should have been requested and received from the law enforcement agencies, and in-house security reports will have been incorporated into the database or spreadsheet application. Though crime analysis can be conducted using paper and pen, software applications are recommended because they allow for quicker data entry, sorting, and analysis of the data. Software applications also allow users to easily create graphs, charts, and maps. A typical spreadsheet will start with keying in basic elements from the CFS and offense reports, including
• Site (address and/or site number).
• Reported crime: This information is located on the CFS sheets and may also be listed in the offense report.
• UCR code: Since most police departments do not include this code, this may be inserted later.
• UCR description/actual crime committed: The first page of the offense report will normally have the final crime classification.
• Date: This is the date on which the crime occurred, not the date reported.
• Time: This is the time at which the crime occurred, not the time reported.
• Day of week: This may be inserted manually if not listed on the offense report.
• Offense report (or incident) number: This is the number listed on the offense report.
• Crime location: This is a description for advanced analysis and may not be known or gleaned from the offense reports. As mentioned earlier, when a security professional reviews a crime scene location, it is often important to determine whether the crime is internally or externally generated.
Since most law enforcement agencies use different offense report forms, at first it may be difficult to ascertain each of the elements which are to be included in the database; however, given some practice with each law enforcement agency’s forms, the process is rather routine. Once all the information from the offense reports has been entered, security report information can be entered, taking caution not to duplicate entries from the offense reports. Additional codes may be created for incidents of concern to management that are not included in the UCR coding system. The crime analysis format should be versatile and expandable so that, when new data become available or when management needs change, different types of analysis may be added.
Once the data, including calls for service, offense reports, and in-house security reports for the property, have been assembled, they need to be translated into a standardized set of codes that denote actual crimes. To ease comparisons, the UCR codification system should be used because it is simplistic and other data sets already use it. If anything other than UCR codes are provided, then the crimes must be transferred to UCR codes. This is required because police reports may differ in how they are worded or coded from the norm or from one another. To simplify matters, the UCR coding system is recommended because it includes a fairly complete listing of possible crimes, which will make analysis that much more complete.
Using this main database, retail security professionals can sort information by store; by type of crime; or by date, time, or day of week. The database will also allow retail security professionals to begin performing basic calculations such as totals for specific types of crime at each site and the average crimes per site. They may also be able to discern any patterns or trends in crime types or temporally (date, time, day).
Another piece of data that should be entered on the spreadsheet is the store’s annual traffic level, which is generated from internal records. The traffic level will be used as the store’s population to calculate crime rates and trends. Traffic levels may also be calculated using transaction counts or other data which reflect the number of persons at a property. Most retail security professionals would add other people who are frequently on premises, including employees such as store clerks.
Several different types of analysis make up a crime analysis as a whole. They include temporal analysis, crime-specific analysis, crime rate analysis, spatial analysis, modus operandi analysis, and forecasting. Each of these modes of analysis examines an aspect of crime’s impact at a facility, identifies crime patterns and trends, and indirectly identifies security measures that are appropriate to counter the known risks.
Return on Security Investment
In today’s business environment, it is important for all departments to show bang for the buck, and this philosophy applies to the security organization all too much because often its budget is among the first to be cut. Showing a return on investment simply means that security measures are either paying for themselves or better, adding to the bottom line. Return on security investment is important because it helps the retail security professional justify costs and obtain future budget monies. Some security programs will not pay for themselves, whereas others actually become a profit center.
For example, crime analysis almost always pays for itself because it helps the retail security professional select the most appropriate security solutions for specific problems and efficiently deploy the resources. Without it, the effective retail security professional has little to guide him toward effective, adequate, and reasonable solutions. More expensive counter-measures such as CCTV systems and personnel are harder to show return on investment; however, over the long run, these measures become relatively inexpensive when compared to the financial turmoil that can occur from even just one indefensible claim of negligent security.
A recent case study published by the American Society for Industrial Security International in Volume 6 of its Security Business Practices Reference discussed a retail company that was able to generate a 7% savings on its projected security budget using crime analysis. To select and deploy appropriate security measures, the retailer outsourced its crime analysis needs to my security consulting firm. Using the crime data generated for each of its stores, the retailer expanded its risk model from internal security reports only to include the police crime information in assessing the threat level at each of the company’s retail stores.
Since the company’s retail stores cater to a diverse group of people and are normally the anchor stores in strip centers, a lot of the crimes reported from each store did not actually occur at the facility. Offense reports were used to verify all violent crimes to ensure that only those that actually occurred at the property and occurred as reported were included in the database.
The security department utilized a crime analysis software application to analyze the databases of crime data for each of its stores. The database includes the time and date of each crime and the specific nature of the crime that occurred. The software allows the department to quickly determine where the violent crimes occurred on the property and identify the victim. With this information, the security personnel are able to determine not only whether a store is high, medium, or low risk, but also who is being targeted—customers or the store itself. With this specific information, the security department can deploy appropriate security measures to reduce the risk at each store specifically.
By the end of their first year with this new program, the security department was able to realize a sizable return on investment. Based on the company’s 300 stores, an annual savings, or cost avoidance, of $9.2 million was gained in the first year after implementation. This savings reflects a number of changes to the retailer’s security program but primarily constitutes the redeployment of security personnel during higher risk times. Prior to this new program, security personnel were used haphazardly with no regard for actual risk levels.
Though the preceding example is tangible, most savings in the business of security are intangible and not as easy to assess quantitatively. One of these categories is the savings generated by reducing crime and thus the avoidance of security-related litigation. Regardless of a security measure’s ability to be quantitatively assessed, retail security professionals should strive to calculate a return on security investment.
Sennewald C.A. Effective security management, 4th ed. Woburn: Butterworth-Heinemann, 2003.
Vellani K.H. Achieving return on investment from crime analysis. Security Business Practices Reference, vol. 6. ASIS Council on Business Practices, ASIS International, 2004..
Vellani K.H. Strategic security management: A risk assessment guide for decision makers. Woburn: Butterworth-Heinemann, 2006.
Vellani K.H., Nahoun J. Applied crime analysis. Woburn: ButterworthHeinemann, 2001.
Ticket Switching
Ticket switching (also called “price switching”) is a form of theft that, in some jurisdictions, may be considered as shoplifting. In this situation, the price ticket from an inexpensive or lower priced item is removed from the merchandise and placed on an item which is higher priced, with the hope that the cashier will not notice the price is incorrect and the higher priced item will be purchased for the lower price.
Some ticket switchers may choose to keep the merchandise purchased for their own use, whereas others will try to return the merchandise and obtain a cash refund. Those returning the merchandise will claim it was a gift because their receipt will obviously show the incorrect (lower) price.
A variation on ticket switching is container “substitution.” In this situation, goods from a higher priced item are placed in a container originally containing and marked for a lower priced item. Such attempts at fraud often occur in shoe departments, since shoe boxes are all the same size but contain merchandise varying dramatically in price.
It is also not unheard of that employees misticket goods. So care must be exercised when dealing with ticket switchers, to ensure that the switch is actually observed and that the suspect is seen discarding the higher priced ticket.
The advent of computers and their ability to read and reproduce universal product codes (UPCs) and/or bar-coded labels has seen the traditional ticket switcher turn to making his own bar-coded labels reflecting a low price and affixing them to merchandise cartons containing expensive items. Electronic items and components thereto are frequently targets of this fraud. A second person, working in conjunction with the person who affixed the fraudulent price label, is often utilized to make the actual purchase. Since this scam is relatively new, local laws should be checked to ascertain the correct charge for arrests made for this fraud.
Retailers with policies which permit loss prevention agents from detaining the customer who successfully completes a purchase of a switched-ticket item should require the agent not only to follow the “six steps,” but further, to recover, as evidence, both the ticket or tag representing the higher price as well as the lower price or both containers, depending on the nature of the theft.
One further caution is important when dealing with ticket switchers: If a switch is observed, the cashier handling the sale should not be alerted. If the cashier catches the fact the item is mispriced and corrects the price, fine—a fraud has been prevented. If the cashier is alerted and told to permit the fraudulent sale to be completed, many jurisdictions may take the position you facilitated the fraud and refuse criminal prosecution.
Till Taps
A “till tap” is the theft of money from a cashier’s till by an individual who reaches in the till, usually when it has been opened for a transaction, and grabs whatever bills are easily available to remove. Till taps are unlike a robbery in that the suspect will not make a demand for the money in the register but will simply reach in the opened till and take whatever bill is readily available and run, often without any use of physical force and even utterance of a word to the cashier.
The likelihood of till taps occurring can be greatly reduced in several ways. Subjects who are interested in committing till taps generally will watch a cashier’s actions prior to committing their crime. If the cashier is aware of who is standing near them and makes eye contact and acknowledges those individuals, this action in itself can sometimes help to prevent the offense from occurring. Most criminals do not like to be noticed or engaged in a conversation prior to committing their act.
An alert cashier can be a great deterrent to this and other types of criminal activity. Cashiers should also be trained to make sure large currency bills are not kept in the till. Till tap suspects are generally aware of where the cashier places large bills. If these bills are being placed underneath the till, in a secured drop box at the check stand, or being pulled by management on a regular basis, these actions alone, if observed by the suspect, may be enough for him to decide that the risk of apprehension is not worth the amount of money that is readily available for him to take. Secured drop boxes are available from several manufacturers and are relatively inexpensive; they can be mounted unobtrusively at the check stand so that a cashier can quickly slip large bills in them.
Typically, store management controls the keys to the drop boxes and makes regular pulls from the boxes to collect the excess funds and transport them to a secure counting area.
Another deterrent to till taps is for the register drawer to remain open a minimum amount of time during a transaction. Cashiers’ training should dictate that the till drawer be opened only during transactions and that they should not enter into a conversation with customers while leaving the drawer open. Obviously, the threat of a till tap is only during the period when a till is open and thus eliminated if the cashiers are diligent about minimizing the time it is left open. Cashiers should be instructed not to count down their tills at the checkstand and should be afforded a secure location to do this that is not in public view. Bills inside the till should be continually kept in a neat and orderly manner so that cashiers are not required to open the drawer for a long period of time to organize it.
Although the use of physical force by a suspect is rarely involved in a till tap situation, cashiers should use the same protocol as that of dealing with robbery suspects in that they should never try to restrain the individuals or chase them. Just because suspects did not display a weapon or make verbal demands does not mean that they are not dangerous and cannot cause physical harm to the cashiers or other store personnel who might decide to intervene in the situation to recover the money or apprehend the suspects. Employees should be trained to understand that no amount of money or store property is worth their risking their life.
Store design can also serve as another deterrent to till taps, as it does to other types of criminal activity. Whenever possible, registers should be located so that customers cannot stand out of the line of sight of the cashiers. Counters should be designed to be high enough so that register till is not easily accessible to the customer view or reach, keeping in mind that compliance with the American with Disabilities Act (ADA) must be maintained during this design process. Additionally, retail establishments must always be concerned with the flow and ease of customer traffic during the checkout process, and loss prevention practitioners need to understand this concern and try to propose reasonable compromises to achieve some degree of preventive deterrence.
While a till tap may not be the greatest loss prevention opportunity that a retail establishment faces, it certainly is one that is relatively easy to either deter or reduce the amount of loss if proper training is given to the cashiers and if procedures are put in place and consistently followed at the operational level.
Time Card Violations and Time Falsification
Falsifying an individual’s time is commonly achieved by the mechanical or electronic process of “timing in” and “timing out,” requiring the presence of the employee or another person representing the employee in a physical act to record the time. Hereafter, we’ll refer to this act as a “time-clock violation.”
The second common method of recording the hours an employee works is the sign-in and sign-out log, which memorializes the hours of work of a given employee but is hand recorded. Again, it does require someone to note the times with pen or pencil.
The last method of recording hours worked is the individual time sheet, which the employee keeps in his possession and completes day by day and submits to the human resources department or the timekeeper’s office on a weekly basis.
Any employee who falsifies the time he works should be terminated. And any employee who assists or facilitates such falsification of time for others should also be terminated.
Training
“Training” means different things to different people and, hence, is widely misunderstood. In 1978, in the first edition of Effective Security Management, I defined security training as follows:
Training is an educational, informative, skill development process that brings about anticipated performance through a change in comprehension and behavior.
Training, in our industry, must result in employees fully understanding three things:
No one other function can reap greater rewards than the training effort aimed at achieving these three absolutely critical steps!
Those steps are interrelated to a company’s policies, objectives, and procedures. Figure T-5 shows the relationship between the enumerated three factors and policies, objectives, and procedures.
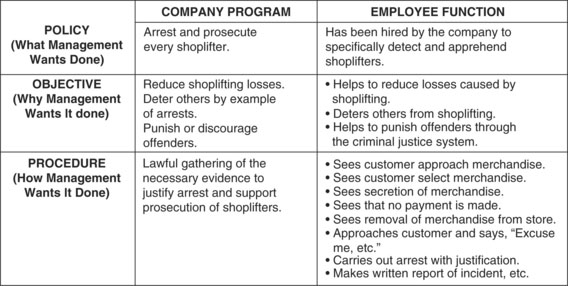
FIGURE T-5 The POP formula for effective shoplifting detective training.
[Source: Sennewald, C.A. (1985). Effective security management. Stoneham, MA: Butterworths.]
We recommend a structured 3-week training program leading to in-company “certification.” Those 3 weeks would unfold as follows:
| Week 1 | ||
| Day 1 | Orientation (company, store, department) | 8 hours |
| Day 2 | Department operating manual and laws | 8 hours |
| Day 3 | Shoplifting detention/prevention guidelines | 8 hours |
| Day 4 | The processing of a detainee | 8 hours |
| Day 5 | Litigation avoidance | 3 hours |
| Local procedures and courtroom demeanor | 4 hours | |
| Written Exam #1 | 1 hour | |
| Week 2 | ||
| Day 1 | Loss prevention awareness and concepts | 5 hours |
| Safety and fire prevention | 3 hours | |
| Day 2 | Customer and employee accidents | 3 hours |
| Store physical security and store inspection | 5 hours | |
| Day 3 | Internal theft, Part I | 6 hours |
| Written documentation | 2 hours | |
| Day 4 | Internal theft, Part II | 6 hours |
| Review/discuss Exam #1 | 1 hour | |
| Written Exam #2 | 1 hour | |
| Day 5 | On-the-job training (OJT) on the floor | |
| with training officer | 7 hours | |
| Report by trainee of experience on the floor | 1 hour | |
| Week 3 | ||
| Days 1–3 | OJT on the floor with training officer | 24 hours |
| Day 4 | Unsupervised detection/prevention | 8 hours |
| Day 5 | Unsupervised detection/prevention | 4 hours |
| Written report by trainee of experiences | 1 hour | |
| Review/discuss Exam #2 | 1 hour | |
| Course review, Q&A, certification | 2 hours |
The new loss prevention agent, upon successful completion of this program to the satisfaction of LP management, then becomes “certified” to function as an independent agent with the authority to make detention decisions. No agent may make such decisions until certified; i.e., certification is a professional “must” in the enlightened and modern loss prevention department. We encourage the actual awarding of a certificate which the agent can proudly display in his own home.
A note about the “training officer”: Historically, OJT means novices or new hires are scheduled to work side-by-side with an established member of the LP team. This should not occur, as is explained in the “On-the-Job Training (OJT)” section elsewhere in this volume. Depending on the size of the department and size of the LP staff by store, district, region, etc., specific and trained agents should hold a “rank” of training officer (TO) and be compensated for that level of responsibility, a position midway between LPO and LPM and only these officers may work in OJT teams.
On through the totality of the structured program, under the guidance of training officers (and members of LP supervision and management), can a retail company discharge its moral and legal duty to ensure
Trash
One operational necessity in retailing is the disposal of trash. “Trash disposal” is a multifaceted need and deals with a wide range of waste such as hazardous waste, unsaleable food items or items which have passed their “sell by” date, recyclable waste items, general housekeeping trash, and employee canteen or cafeteria garbage, etc. Depending on the size and nature of a given store, trash disposal is a cost and yet can be a source of income. Many larger businesses employee cardboard balers and have enough volume to receive money back from their baled cardboard.
Irrespective of the kinds of trash generated at a given retailer’s site, trash—where and how it’s stored and its disposition (removal from the site)—should create some level of interest in and concern by the loss prevention professional.
The hiding of store merchandise in trash for the purpose of recovering the goods once outside the store is an age-old problem. Typically, employees or their confederates return to the property at night, for the purpose of recovering merchandise stashed in the trash or garbage. One common theft strategy is sealing expensive merchandise in waterproof plastic bags and placing them in larger bags filled with garbage. Soft goods are sometimes placed in between layers of cardboard and baled. Such bales are then marked and the goods recovered after the bales are removed to a recycling facility. Small items, such as jewelry, are secreted inside used vacuum cleaner bags and recovered once outside the store and in the trash. Merchandise is submerged in mop water or window washing water and wheeled out of the store in the morning past any security controls.
Maintaining some level of control over trash isn’t the most pleasant task. After all, who wants to crawl into a dumpster? But control is a must. Various theft prevention measures can be employed which could reduce theft in this area. They include but aren’t limited to the following:
• Ensure that all loss prevention personnel are aware of this risk.
• Ensure all employees who have any involvement in handling trash are aware that loss prevention is aware of the risk.
• At night, illuminate the area where all trash and trash containers is staged outside the store.
• Lock trash containers at night.
• Have an LP agent conduct periodic inspection of trash containers. One common method is to move the trash around with a long stick or rod looking for any containers or packages which could hold merchandise.
• Inspect bales for any unusual markings which set one bale apart from all the others.
• From time to time, monitor housekeeping personnel who exit the store during early morning hours for outside chores.
Trespass
The diplomatic and practical skills of store managers are often tested by the wide spectrum of human problems related to “trespass.” In this section we will briefly review what trespass is, the widely different scenarios that involve trespass, and the remedies available to the merchant, which are often far from being satisfactory. All these potential problems should be reviewed well before they arise with counsel and the local police.
Criminal trespass laws vary from state to state, and often differentiate between misdemeanor and felony trespass. Broadly put, and for our purposes, trespass occurs when a person is on the premises of another without permission. Depending on the jurisdiction, the premises manager may need to post “no trespassing” signs on its property for trespass laws to be enforced.
We review here several different “trespasser” scenarios, along with the practical problems each presents.
The Homeless Trespasser
Some trespassers come on to business premises looking for a place to sleep. This may sound harmless enough to the public, as homeless people often want only to use deserted parking lots and similar spaces quietly to spend the night. However, homeless people may also engage in loud and disturbing behavior, may consume alcoholic beverages or controlled substances, may squabble or fight among themselves, may be a nuisance to neighbors, or may engage in violent crime. Quiet or not, they may also leave garbage and human waste behind.
No business wants to have such trespassers use business property in these ways. If a business premises has the appearance or reputation of being a place where homeless people camp, many customers, especially the elderly and the infirm, will shop elsewhere.
Store managers, or security personnel, should document and photograph the conditions created by homeless occupiers whenever it is possible to do so safely, in case their behavior needs to be described later to the police or in court. When homeless people are present, whether they are quiet trespassers or are engaged in disturbing or criminal behavior, it is advised that store managers or security personnel contact local law enforcement to help. Police can contact the trespassers, identify them, determine if they are arrestable for warrants or public intoxication, and often simply persuade them to move along.
But arresting trespassers is another matter. The laws of the states vary concerning who may actually arrest for trespass. In California and other states, a responding peace officer will usually tell store personnel that he cannot make an arrest for misdemeanor trespass, but that rather the arrest must be made, if at all, by a representative of the store, through the process commonly called “private” or “citizen’s arrest.” Store managers will often feel that they therefore should arrest for trespass to solve the problem. In reality, arrest for trespass is rarely satisfactory for several reasons. Caution is required.
It is very important that store personnel fully discuss what this type of arrest really means, and can accomplish, not only with the responding peace officer, but also with the store’s lawyers, because these arrests may create many traps for the unwary and usually do not solve the store’s problem anyway. First, the arrest itself will usually change nothing because the officer will commonly cite and release the trespasser at the store where the trespass has taken place or perhaps only a few blocks away. Second, trespassers are almost never brought to trial. And, in some instances, the trespasser will hire counsel and sue the store, claiming that he was arrested on account of his homelessness or for some other improper reason, not for trespass.
Another option, but a far more expensive one for dealing with chronic trespass, is for the store to seek an injunction against the individual who is using its property as a camp. If a judge enters an injunction, a peace officer, rather than by an employee, can arrest trespassers for its violation, for the trespass itself. But this approach has the same problems mentioned previously because the trespasser may not be convicted of anything at the end of the process.
In many instances, the legal approach to dealing with trespass is expensive and ineffective: store management may conclude therefore that making premises physically unavailable or inhospitable to the homeless will work better than arrests or lawsuits.
The Irate Customer
Another common scenario involves the “irate customer” who has entered a business’s premises with permission, express or implied, but who becomes angry, loud, and abusive toward store personnel. Typically, store personnel will approach irate customers and try to calm them so that store business and customers are not disturbed. When these efforts fail, store personnel can do one of two things: First, they can seek to use minimal reasonable force physically to eject the trespasser. Second, they can call the police for help. Both of these approaches are risky.
The law allows a business owner or manager to tell the irate customer to leave the premises, without providing reasons. Should the customer refuse a clear command, he is a trespasser. At this point, store personnel are allowed to use reasonable minimal force necessary only to eject the trespasser from the premises. While this course of conduct is generally not considered to be an assault or battery, it can often lead to litigation anyway. The irate customer may claim, rightly or wrongly, that he was defamed, belittled, or was the victim of intentional infliction of emotional distress. Or, the trespasser may claim to have been injured by assault or battery. Also, onlooking customers will usually be disturbed by any use of force, no matter how loud or irate the customer may have been. If force is to be used, it should be performed only by employees with training.
Although a loud and obnoxious customer may distract or disturb other shoppers, the risk arising from touching such a person is rarely justifiable in the absence of a threat to safety. All in all, the use of physical force should be reserved for situations in which ejection of the irate customer is both safe to the employees, the customer, and onlookers and is reasonably necessary to protect against the threat of violence or other crime.
The other option for dealing with the irate customer is to call the police. If there is any threat of violence, or of harm to anyone, the police should, of course, be called without regard to the threat of civil liability or the embarrassment of the customer or others. The police often will seek to mediate disputes, and the presence of uniformed officers can have a calming effect. However, store personnel should resist the temptation to arrest irate customers for trespass, or for anything else, without the advice of company attorneys and higher management, for the reasons stated previously with regard to homeless trespassers.
Usually, genuinely irate customers want to be heard and will calm down after they fail to get their way or feel that they have expressed themselves fully. Although a loud and angry irate customer may offend and distract onlooking customers, these same onlookers can sympathize quickly with the irate customer if they feel that the store used a heavy-handed or overly physical response. In short, store personnel seeking to protect the tranquility of onlookers may end up disturbing them more by poor responses to the situation.
One caveat: Sometimes people will pretend to be irate customers as a diversionary tactic, while their confederates shoplift or commit other crimes.
Signature Gatherers
Some states, like California, have case law that recognizes the right of persons under limited circumstances to express their political views or, more commonly, to collect signatures for ballot initiatives and petitions at malls and in front of large stores. Many malls, property management companies, and retailers have policies disallowing this conduct altogether or regulating it. As is the case with the homeless and irate shopper scenarios, it is important for store management to contact company lawyers for guidance when these problems arise. In California, professional signature gatherers tend to be very aggressive and often intentionally dare mall and store personnel into arresting them for trespass, hoping they can bring a false arrest claim and turn a quick buck.
When signature gatherers arrive in front of a store or at a mall common area, responsible personnel should provide them with a copy of the written policies and guidelines governing the use of the premises. It is often helpful to identify the initiative, petition, or candidate for whom signatures are being gathered so that company lawyers or others can contact the political organization for which the signature gatherers are working in an effort to win compliance. Often, signature gatherers will not listen to reason, but the candidates and initiatives for whom they are working will.
“Trespassing” a Violator
Many merchants will document and inform shoplifters and others who violate the law at their stores that they will be arrested for trespass in the future anytime they return to the store where the incident took place or to any other store the merchant operates. If such warnings are given, they need to be thoroughly documented.
In theory, a merchant may indeed arrest a known shoplifter, troublemaker, or lawbreaker, etc. for trespass, as long as the decision is based on the trespasser’s documented crimes, and not his status, e.g., race, ethnicity, religion, gender, etc. Caution is required in these cases for several reasons: First, in the normal trespass situation, the merchant will typically tell the trespasser to leave and may even seek to escort the trespasser out if this can be done safely. Making a private arrest for trespass based on an earlier warning is something else again: Store personnel may need to detain and restrain the trespasser until police arrive, and they may therefore open up the merchant to a lawsuit for false arrest, excessive force, and related claims.
The laws of the different states may also vary as to whether an initial warning not to trespass will remain valid over time and space. The safer course is therefore to treat the returning trespasser as if no earlier warning had been given and to ask him or her to leave. We recommend that store retail and security personnel review these policies with management, and that managers be aware of the potential risks and high costs of litigation before authorizing such arrests.
Labor Picketing and Handbilling
Merchants may occasionally be faced with persons wishing to picket or handbill about labor issues directly outside a store. Such activities may have a legally protected status, and therefore, merchants should immediately call on knowledgeable labor counsel for guidance before taking action. Picketers are not allowed to use violence, to make threats, or to block the doors of retail premises. In most cases, local police will not get involved, unless violence or other crimes (such as vandalism) are involved. However, courts may set reasonable limits upon what picketers may and may not do.
Making Decisions Based on Behavior, Not Status
In any situation involving trespassers, store personnel must never take action against anyone based on race, ethnicity, color, sexual orientation, gender, religion, or other “protected” characteristics. Instead, just as police officers must articulate specific facts to a judge to obtain search and arrest warrants, so too must store personnel be prepared to identify specific facts concerning what trespassers have said and done, to obtain assistance from the police and the courts.
When stores deny full service and accommodations to people in whole or in part because of their status, it is a sure thing that sooner or later the stores will be sued on a theory of discrimination. For that reason, we strongly recommend that when trespassers create problems, store personnel closely document their behavior.