P
Parking Area Crimes
Parking lots and garages represent a fruitful hunting ground for robbers, rapists, auto thieves, and purse snatchers. While often lucrative, they also represent a huge potential legal liability for operators, plus damaging publicity if pictured on the evening news in connection with a horrible crime.
Because of their layout and construction, there is no “one size fits all” security program for lots and garages. The keys to security are
To the extent that access can be controlled by the operator of the garage or lot, many criminals can be deterred or prevented from entering. This typically requires perimeter barriers such as fencing and/or walls at ground level. If walls and fences cannot be used, lesser demarcation of the lot boundaries with partial fencing, hedges, planters or shrubs, etc., can provide a psychological barrier to criminals and a clear indication of where the “private” property begins.
In many lots and garages, access to the garage can be controlled or closely monitored. A parking attendant can view the occupants of cars entering and leaving, and a closed-circuit television (CCTV) camera can record license numbers and drivers’ faces—both major deterrents to criminals.
The threat to persons and property in covered/enclosed parking garages can be very high. To limit access to garages, ground-level doors away from any parking attendant should not be accessible from the exterior of the building. There should not be any openings in the building walls within 15 feet of the ground through which a person could enter.
Isolated garage floors and garage and lot locations often make effective surveillance or monitoring difficult; however, live and recorded CCTV monitoring can reduce the risk (Note: If the CCTV cameras are not monitored live—and instead only recorded for later review and prosecution—prominent signage should state this so that customers do not rely on cameras which they think are being monitored and will produce immediate help).
When CCTV is used, good-quality color cameras that can operate in low light, along with high-resolution color monitoring/recording systems, are essential. Black-and-white monitors offer poor detail definition, a critical issue when attempting to identify suspects or potential problems.
Adequate lighting not only helps people recognize and avoid dangers, but also in many cases deters criminals by creating in them the fear of detection, identification, and apprehension.
Interior garage lighting should be a minimum of six foot-candles (measured both vertically and horizontally) throughout the garage, 24 hours per day. Sunlight seldom enters garage interiors and cannot be relied upon for lighting. If the facility has a significant history of crime or a recent history of violent crime, a higher level of illumination may be needed.
Energy-efficient metal-halide lighting provides reasonable color rendition for CCTV and direct viewing. Interior walls and ceilings should be painted with a glossy or semiglossy white paint to increase light reflection. This also increases the ability of parkers to observe movement and potential threats. Pillars and ramp corners should be painted in contrasting colors for driving safety.
Where appropriate, the use of a parking lot attendant can also serve as a powerful deterrent, if the attendant is able to view the lot and be seen. However, if there is no CCTV for remote viewing on large lots, and with the attendant’s booth facing out toward the street with his head often stuck in a book or portable TV, some attendants can’t see much of anything and don’t provide much, if any, security.
A key element of security in many surface parking lots is visibility, for employees, customers, and passers-by. Within the lot, trees and shrubs should not obstruct viewing. Tree branches and leaves should not be lower than 10 feet above the lot surface, and interior shrubs and bushes should not be higher than 18 inches above ground or curb so as not to obstruct vision or provide concealment for a robber or rapist.
A significant part of visibility is lighting. Lighting should enable parkers and employees to note individuals at night at a distance of 75 feet or more, and to identify a human face at about 30 feet, a distance that will allow them, if necessary, to take defensive action or avoidance while still at a safe distance. A minimum maintained illumination throughout open parking lots of not less than three foot-candles (measured vertically and horizontally) is recommended. This will also provide adequate illumination for driving purposes. Lighting at the entry/exit points should be at least 20 to 30 foot-candles for safety and security, and for adequate direct observation by employees or CCTV monitoring. Energy-efficient metal-halide lighting offers good color recognition.
Parking Lot Crimes and Other Problems
Use of the term “parking lots” does convey the nature of the problem to be addressed here, but more properly, the topic should be “Parking Environment Crimes and Other Problems” because not all parking is in “lots.” Parking environments are divided into three distinct parking facilities:
• Parking lots, which are outside surface parking areas, typically at grade level with the business or institution they serve, like the parking lots common around shopping centers.
• Parking ramps, which are typically multistory above-ground parking “garages” and may be
• Subterranean parking garages, which may or may not be part of an above-grade ramp complex.
Too few loss prevention practitioners, especially those at the store level, have an understanding of or an appreciation for the inherent risks in parking environments and how those risks impact on the retailer’s business. The security and LP industry concerns itself with two general areas of risks: crimes and torts which occur in the store’s parking areas. The impact of crimes in the parking areas, which really has no direct bearing on the nature of the retail business, is the victim of a crime, who, in our modern times, may commence a legal action against the retailer if the retailer has any control over or responsibility for the parking area. Civil lawsuits as a result of crime victimization in a store’s lot are commonly based on such theories as inadequate security or negligence in not providing sufficient security to prevent crimes, a condition which our society has come to expect when they park and walk in a store’s parking area. The second risk is the threat of crime (or other tortious conduct) may scare or drive away customers who will shop at other locations where the general perception is that it’s safer there.
Common Parking Lot Crimes
Crimes Against Persons in Parking Environments
2. Murder connected with spousal abuse
3. Murder connected with violence in the workplace
4. Serious injury to victim caused by an assault by an armed robber
6. Rape in the shrubbery/landscaping of the parking area or other remote areas of the parking complex
7. Abduction of a customer or employee
8. Armed robbery, no physical injury to the victim
9. “Mugging” (robbery) with injury
10. Purse snatching with injury to victim
11. Purse snatching without injury
13. Indecent exposure to female customers and employees
14. Assaults on car owners who accidentally come upon a thief entering or inside their auto
Crimes Against Property in Parking Facilities
2. Theft of auto parts, such as batteries, wheels, emblems, etc.
3. Theft of auto accessory or after-market equipment inside the vehicle
4. Theft of packages and other personal property from the interior of autos
5. Theft of equipment, supplies, materials, and tools from trucks
6. Vandalism to autos, such as “keying” a car or truck, puncturing/deflating tires, etc.
Victims may, and do, sue stores, and those victims who do not sue tend thereafter to shop elsewhere. And they certainly share the story of their victimization with many other people.
Courts across the land have universally held that parking environments are “inherently dangerous” because of the concentration of wealth in terms of property which is easily sold on the street and the sheer remoteness and isolated areas of such environments, with limited foot traffic. Further, the very nature of the environment is tolerant of lone males wandering among the cars, presumably “looking for” their own vehicle. But some are looking for victims or objects of theft.
Other Problems in Parking Environments
3. Solicitations for various causes
6. Teenagers or other unique groups who gather for social contact
An interesting example of “solicitations” took place in Los Angeles in the 1970s when a Muslim mosque became active in distributing its paper Mohamed Speaks, which then was a centerpiece of the Black Muslim community. Their efforts to distribute the newspaper were focused on the Crenshaw Shopping Center. The young men dressed in black suits, white shirts, and ties were universally well groomed and were passionate about their faith. The paper was free, but there was an air of expectation for a donation for the “free” paper, and many customers began to complain to store management that they felt intimidated by these young men and reported they were becoming too aggressive. The customers further informed management they would not return if something wasn’t done to shield them from the confrontations; they would shop elsewhere.
The security department was charged with gathering the necessary evidence to prove to the court the solicitors were threatening. Evidence was gathered and presented, and a restraining order was granted which denied these young men access to the parking lots. The problem was solved.
What Can Be Done at the Store Level?
Retail LP/Security practitioners aren’t expected to be experts in parking environment security, but there are some basic principles everyone should be aware of. Such basics include
• Parking areas must be well illuminated. Some daily/nightly effort should be taken to check the lights, and if a lamp is burned out, it must be reported and replaced.
• Exterior CCTV cameras, conspicuously mounted, should monitor the parking areas. They need not be monitored at all times, but they should part of a system which records the activity in the lot.
• We recommend signage in the lots which state, essentially, the area is monitored by CCTV for the safety of all.
• Large parking areas require some form of patrol by security personnel, either by foot or motorized. Vehicles used for this purpose should be distinctively and conspicuously marked and be equipped with some form of flashing light and voice communication equipment.
• A policy must exist wherein any “parking lot incident” is memorialized and maintained by LP personnel; i.e., if a sales associate reports her battery was stolen during her shift, that must be reported to LP and a report made and filed. Such incidents are just as important as is the report of a shoplifting detention.
• Monthly LP statistical reports should always reflect the number of parking lot incidents so the frequency of the crime is perpetually monitored (for corrective action if deemed appropriate or necessary).
• Every incident of a criminal nature that occurs in the parking area must be reported to the police.
• The store should have an after-dark “parking area escort service” if requested by a female customer.
• Female employees leaving the store at night, at either the conclusion of their shift or upon store closing, should be escorted to the employee parking area or required/encouraged to walk to the area in groups for their mutual safety.
• Designated employee parking areas must be illuminated as brightly as all other parking areas or, depending on geographical location, enjoy a greater level of lighting.
What Is the Store’s Role If the Parking Areas Are Not Specifically Under the Control of the Retailer/Store?
Let’s assume the store is in a mall, and the shopping center management is responsible for the common areas, including parking. Within reason, the store should nonetheless be aware of and concerned that the basic protection of the lots is in line with the points listed previously. We encourage an ongoing and regular meeting between store loss prevention and shopping center management, including the mall’s security director, to review and discuss security in the parking areas and known incidents of criminal attacks, as well as any other behavior or conduct of concern. Records of such meetings should be maintained by the store. The store is paying a common area maintenance fee for the overall management of the mall, including security, and is entitled to have a voice in making the parking safe for its employees and customers. To abrogate this responsibility is not only a moral failure, but could be construed as tortious, under certain circumstances.
Case in point: A medium-size retailer was a tenant in a large strip center. Doors to the store were on opposite sides of the selling floor; that is, one set of doors opened onto the interior of the mall, and the second set of doors opened onto the surface parking lot that surrounded the mall. Shopping center management was responsible for the maintenance and security of the parking lots.
One night two teenage girls entered the store through the parking lot doors. After shopping, they exited the store and entered their pickup truck, which was parked approximately 75 feet directly in front of the store. Several other vehicles were clustered in the same area. As the driver attempted to close her door, a man appeared, seized the door, forced his way into the cab of the truck, and drove the girls to a remote location, where he sexually molested them. A lawsuit was filed against the shopping center and the store for maintaining an unsecured and dangerous place to shop and inadequate security.
Upon examination of the lighting at the center, it was determined to be below the Illuminating Engineering Society’s minimum recommendations, hence inadequate. However, the store in question, upon recommendations made 5 years earlier by a security management consultant, had mounted extra lights to increase illumination in the immediate parking area outside the doors, shining into the lot. As a consequence, the suit against the store was dropped. The suit against the shopping center succeeded.
Performance and Development Review Process
When supervisory staff think of doing performance reviews, they often think of a time-consuming process and dislike the confrontations that often arise during the process. Those being evaluated sometimes view the process as one-sided and often see limited or no value in the process. There was a time in the not-too-distant past when it was acceptable for a retail loss prevention supervisor to do an employee’s evaluation, call the loss prevention employee into the office, have the employee read the evaluation, and then ask the employee to sign it. The employee had little or no input. It was little wonder the employee felt the process was one-sided. When done correctly, the performance evaluation process can be both positive and productive for both employee and supervisory staff.
The employee is often the most valuable resource in an organization.(1) The performance review process for a retail loss prevention organization should be designed so that it requires the employee and supervisor to work together at formalizing a plan to enhance the performance of the employee. Enhanced performance leads to greater job satisfaction for the employee and improvement in the organization’s performance. For that reason, the process should be more appropriately called a “Performance and Development Review Process.”
There are five main objectives in any effective performance evaluation process. They are
1. Evaluate performance since the last performance evaluation.
2. Recognize the areas where the employee has demonstrated strong performance.
3. Identify and address those areas where the employee needs to improve.
If everyone involved follows a step-by-step process, all five objectives can be successfully attained, and the employee, the supervisor, and loss prevention organization will benefit.
Benefits of an Effective Process
To get people, whether management, supervisors, or employees, to buy into any process, they have to see some benefit from it. So let’s start with the retail loss prevention employee.
A well-defined performance and development review process revolves around communication between the supervisor and the employee. The process will benefit the employee in two ways. First, it will benefit the employee by providing him with a clear understanding of what is expected and what needs to be done to meet those expectations.(2) During the process, the supervisor will discuss what specific performance factors the retail loss prevention employee will be evaluated on and what rating scale will be used. Second, it will also allow the employee an opportunity to discuss aspirations and get support and/or training needed to fulfill those aspirations.
The supervisor also benefits from the process in three ways. First, the process establishes a means for forming a more productive relationship with the retail loss prevention staff. Second, it provides an opportunity to clarify the expectations the supervisor has of the employee. Third, the process can provide a means to clarify the relationship between effective performance and the potential for promotions or merit increases.
The retail loss prevention organization stands to benefit in two important ways. First, the process will assist in identification of training and development needs to better enable employees to work toward the organization’s goals. Second, the process will assist in identification of employee potential so career development plans can be formulated. Many companies keep a list of where employees rank in the organization based on their evaluations. When opportunities for promotion open up, the evaluation results are weighed into the decision-making process. Third, the process can also serve as documentation in cases where employees are ultimately dismissed for poor performance.(3)
What Performance Gets Measured
Every employee position in the retail loss prevention organization should have a job description. The job description should detail the tasks the job holder is expected to undertake and how the job contributes to the overall mission of the organization. The Performance and Development Review form should define performance standards for the tasks associated with each employee’s job description. Therefore, the performance review factors will vary depending on the various tasks performed by the different occupations and levels of management.(4) The first line supervisor’s performance factors will differ from those of the loss prevention officer, the performance factors for the loss prevention officer will differ from those of the investigator, the investigator’s performance factors will differ from those of the secretary, and so on.
The factors used to measure performance should focus on results and be based on observable behavior. Action verbs should be used to describe the desired behavior. Table P-1 illustrates a few performance factors that could be used on a Performance and Development Review worksheet form for the loss prevention officer in a retail establishment.
Table P-1 Loss Prevention Officer Performance Factors
| FACTOR | TASK | RATING |
|---|---|---|
| JOB KNOWLEDGE | ||
| APPEARANCE | ||
| COMMUNICATION SKILLS | ||
| INVESTIGATIVE SKILLS | ||
| REPORT WRITING SKILLS |
The Six-Step Performance Review Process
An effective Performance and Development Review process in a retail loss prevention environment is designed around a six-step process. Those steps are shown in a circular diagram (see Table P-2) because the steps must be taken in order, and like any process, it is ongoing. The process should be done every year or more often if needed, as each individual’s circumstances require. There will be more discussion on that part of the process later.
Table P-2 The Performance and Development Review Process
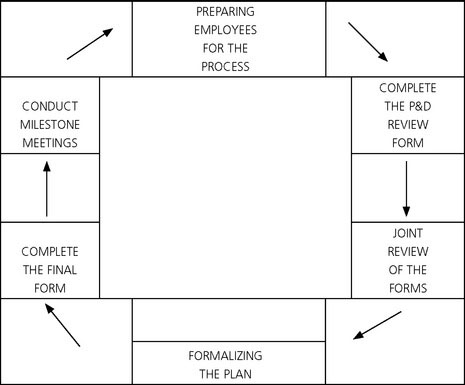 |
Step 1: Prepare Employee for the Review
The process should not be a surprise to the employee being evaluated. Contact the employee and arrange a time and date to meet to start the process. It is very important to make sure the supervisor keeps the appointment. Not keeping the appointment can send a signal that the process is not important.(5)
Give the employee being evaluated a copy of the Performance and Development Review worksheet. The worksheet will list the performance factors he will be evaluated on. If there will be any additional performance factors discussed in addition to the standard factors, they should be listed on the copy provided to the employee. Explain to the employee that he is to perform a self-evaluation on his performance during the period from his last evaluation forward to that date. In most cases, that time frame will be approximately 1 year. It should be explained to the employee that he will be rated on how he typically performs in the retail loss prevention environment, not how the employee performs compared to other employees.
Make expectations clear as to what the employee is to do with the forms. Encourage the employee to make notes on the form and write the rating somewhere near each performance factor. If a rating scale will be used, provide the employee with the rating scale. Review the rating scale to make sure the employee understands the definition of each rating. Keep the process simple by making the rating scale easy to understand. Table P-3 and Table P-4 provide examples of rating scales used by several organizations.
Table P-3 Example of Simple Rating Scale
| RATING | DEFINITION |
|---|---|
| UNSATISFACTORY | CONSISTENTLY FAILS TO MEET EXPECTATIONS REQUIRED OF THE POSITION |
| NEEDS IMPROVEMENT | OCCASIONALY MEETS EXPECTATIONS BUT NEEDS TO DO SO MORE CONSISTENTLY |
| MEETS EXPECTATIONS | CONSISTENTLY MEETS EXPECTATIONS OF THE POSITION |
| EXCEEDS EXPECTATIONS | FREQUENTLY EXCEEDS EXPECTATIONS OF THE POSITION |
Table P-4 Example of Rating Scale with Points
| POINTS | RATING | DEFINITION |
|---|---|---|
| 1 | UNSATISFACTORY | CONSISTENTLY FAILS TO MEET EXPECTATIONS REQUIRED OF THE POSITION |
| 2 | NEEDS IMPROVEMENT | OCCASIONALY MEETS EXPECTATIONS BUT NEEDS TO DO SO MORE CONSISTENTLY |
| 3 | MEETS EXPECTATIONS | CONSISTENTLY MEETS EXPECTATIONS OF THE POSITION |
| 4 | EXCEEDS EXPECTATIONS | FREQUENTLY EXCEEDS EXPECTATIONS OF THE POSITION |
Once the process is explained to the employee, agree on a place, date, and time to meet again to go over the self-evaluation part of the Performance and Development Review form, as well as the form you will have completed. Be sure to allow at least 7–10 days for completion of the forms. To allow more time than that can result in procrastination on the part of the employee or supervisor. Sufficient time should be allowed for both the supervisor and the employee to do their evaluations without rushing through it. The key to this step in the process is educating the employee on the process and getting the employee to participate.
Step 2: Complete the Performance and Development Review Forms
Before starting the Performance and Development Review form, the supervisor needs to do three things. First, review the employee’s last performance review. Check to see if the employee has taken action to improve in the areas where improvement was needed. Check to see if the short-term goals listed by the employee have been achieved. Has progress been made toward long-term goals?
Second, the supervisor should review the incident file kept on the employee. Supervisors should establish an incident file for all retail loss prevention employees.(6) Some supervisors keep an employee journal where they make notations on specific events that involve the employee. The incident file or journal should contain both positive and negative documentation of the employee’s performance.
The incident file is very important. It provides the documentation to support the rating. Employees should be encouraged to also keep an incident file or journal. The employee should use it during the self-evaluation process. When they are reviewing information in the incident file, it is important that the supervisor and the employee are reviewing only the performance taking place since the last evaluation.
Third, the supervisor should review some of the most common problems encountered when conducting performance reviews. One common problem is rushing through the process. Do not wait until the day before the scheduled meeting with the employee to start completing the review form. Another common problem is evaluating personalities instead of performance. Be aware of your feelings toward each employee and avoid being biased. Refrain from using the word “weakness” when referring to a performance area where improvement is needed.
Now the supervisor is ready to complete the Performance and Development Review worksheet in preparation for the meeting with the employee. The worksheet will list the performance factors the employee is being rated on as well as the various task associated with that performance factor. The supervisor should rate the employee on each performance factor based on how the employee typically performed since the last review. If a point system is used in conjunction with the rating scale, the point total should be noted after each performance factor. If just the rating is used, note it after the performance factor. The supervisor should feel free to make notes on the form for support of the rating or for discussion with the employee. This form should be considered a worksheet. The final form will be cleaned up and not have all the notes.
If a point system is used, the points should then be totaled up and divided by the number of performance factors to produce an average rating. The overall average will indicate the employee’s overall performance rating. Tenths of a point should be rounded off on the scale as follows:
1. 49 and below = UNSATISFACTORY
1. 50 and above = NEEDS IMPROVEMENT
2. 49 and below = NEEDS IMPROVEMENT
2. 50 and above = MEETS EXPECTATIONS
A system may be used wherein each factor’s rating stands alone and there is not an average used. Many times the size of the retail loss prevention organization dictates the method used. The important point is not to get too hung up on the numbers game. The objective is to evaluate performance and communicate to the employee what he can do to make himself a greater asset to the organization. It is important to remember that the performance review process is about managing and improving performance in the retail loss prevention environment and not about completing forms (7)
The last item to complete prior to meeting with employee is the area where the supervisor will list first areas of strengths and then areas where improvement is needed. There should be two or three areas listed for each. The area where strengths have been demonstrated is listed first so it can be discussed first. You want to reinforce the positive performance before starting a discussion on what areas the employee needs to work on before the next performance review.
After completing the performance and development review form and prior to discussion with the employee, be sure to give consideration to the employee’s reaction to those ratings where there may be disagreement. Make sure you have proper documentation to support your rating for those areas that may generate unfavorable reaction by the employee. Disagreement usually results from the employee thinking he is meeting expectations when he is not. The performance and review process is designed to correct that situation.
Step 3: Joint Review of the Evaluation Forms
There are steps the supervisor can take to make the employee feel more at ease when the time comes for the employee and supervisor to meet for review of the Performance and Development Review forms. If possible, schedule the meeting in a conference room or location other than the supervisor’s office. It is important to have the meeting on neutral ground. The location should afford privacy and be free from interruptions such as telephone calls and other employees barging in. Cell phones should be put on vibrate and not answered unless there is an emergency. The process is important and should be taken seriously.
The supervisor should state the purpose of the meeting. It should be made clear from the start that only the performance and development review will be discussed during the meeting. There should not be any discussion of salary issues. If the employee has questions or wants to discuss salary issues, arrangements should be made to do so at another time. The focus of this meeting needs to be on the employee’s performance.
Start the process by reviewing the last Performance and Development Review with the employee. If the organization’s Performance and Development Review includes a place for goals, review them as well. Did the employee accomplish the short-term (1-year) goals? Was significant process made toward long-term (5-year) goals? Did the employee take the steps planned for improvement in the last review?
The supervisor should also explain to the employee that both will review each performance factor one at a time. Do not exchange the performance factor worksheets. That can be done later. Let the employee go first by asking what rating he assigned to the first performance factor. The supervisor should encourage the employee to explain how the rating was decided on. This is an excellent opportunity to let the employee talk about himself. The supervisor then explains what rating he gave for the same factor and why. The supervisor should avoid using the term “weakness” when pointing out an area where improvement is needed. Documentation should be used by both to support the rating in cases where a disagreement arises. As both parties work their way through the performance factors, they can make notes on their worksheets. The supervisor should let the employee do most of the talking. A lot can be learned by being a good listener in this setting. The supervisor will be responsible for keeping the focus on the task at hand.
When a performance factor is reached where the rating is UNSATISFACTORY or NEEDS IMPROVEMENT, there should be discussion by both the employee and the supervisor as to why that situation exists and what can be done to help the employee improve. This process is designed to open up communication between the employee and the supervisor. It is an excellent opportunity for both to clarify expectations each has of the other.
It is not all that unusual for the employee’s self-rating to be lower than the evaluator’s. When ratings are not close, there should be discussion to point out why that might be. Documentation kept in the employee’s incident file or journal should be referred to in an effort to support the rating. Once all the performance factors have been reviewed and the ratings on each discussed, the overall rating should be agreed on.
The supervisor and the employee should then review the two or three areas where each feels there has been strong performance demonstrated and where improvement is needed. Once again, let the employee go first. The employee should review the areas where he feels he demonstrated an area of strength. An example might be a loss prevention officer who feels investigative skills is an area of strength. The supervisor would encourage the employee to explain why he feels that way. The supervisor then reviews the areas he feels is an area of strength. It would not be unusual for the supervisor to have the same areas listed. The same process is followed with the two or three areas where each feels improvement is needed. These same areas should already have been discussed while working through each performance factor. Doing it again at this point sets the stage to formulate a plan for development of the employee. The important part of the exercise is for quality communication between the employee and the supervisor that will clarify expectations each has of the other.
Step 4: Formalizing a Plan
Now that the employee and the supervisor have identified two or three performance factors where the employee needs improvement, they can both put together a plan with a goal of raising the employee’s performance from NEEDS IMPROVEMENT to MEETS EXPECTATIONS. If the employee’s performance is rated at MEETS EXPECTATIONS or better in all performance factors, two or three areas can still be picked where the employee can strengthen the MEETS
EXPECTATIONS performance or elevate it to the EXCEEDS EXPECTATIONS level of performance.
The plan developed by the employee and supervisor should include actions that can be implemented by both and designed to improve the employee’s performance in each of the specified factors. Those actions should be measurable so that each can review the plan during the course of the year to make sure a sincere effort is being made and the employee’s progress is on track for improvement. An example of development actions that can be implemented are as follows.
The Loss Prevention Officer is rated NEEDS IMPROVEMENT in the area of Job Knowledge. The plan could require the employee to take training related to increase job knowledge in retail loss prevention, either in-house or through an outside agency (college or career training institution). The supervisor’s commitment to the plan would be to locate retail loss prevention training that is available, secure funding for it, and/or arrange time in the work schedule for the employee to attend the training. The expected actions of each are measurable and easy to monitor for progress.
If the performance and development review process in place has a section for short-term and long-term goals, they should be discussed at this time as well. Both the short-term (1-year) and long-term (5-year) goals should be career-related goals that the employee hopes to accomplish. Examples of short-term goals would be to attend some specialized loss prevention training of personal interest to the employee or complete the last couple of classes needed for degree work at a college. Examples of long-term goals might be to get promoted to a supervisory position or complete work on a master’s degree. The supervisor can play an important part in assisting the employee with both short-term and long-term goals. This area is also important for the development of the employee.
Once this portion of the process is completed, the supervisor should explain to the employee that he will be transferring the results of their review, with their plan for improvement, onto a final Performance and Development Review form. It is that final form that goes into the employee’s Personnel File and gets forwarded to the human resources department. A date should be agreed on for the supervisor to meet back with the employee for the employee’s review of the finalized form. The supervisor should allow sufficient time prior to the next planned meeting date for completion of the final form. This is also an excellent opportunity to seek comments from the employee on his thoughts about the performance review process.
Step 5: Complete the Final Form
Now that the meat of the performance review process has been completed, the plan agreed upon by both should now be transferred from the worksheet to the final form that will be filed with the human resources department. A copy of the completed form will also be placed in the employee’s personnel file. The final form can take whatever design the organization chooses to use. It should be typed or computer-generated so it is neat and legible. The supervisor should meet with the employee again and allow him to review the final form.
The final form should contain the following information:
• All the performance factors reviewed should be listed. There should be a space next to each factor for the employee’s rating and a space for supporting comments for that rating. (See Table P-5 for an example)
• The form may have a place for the employee to list short-term and long-term goals.
• There should be a section of the form reserved for the employee to add his plan for improvement in those factors agreed on, as well as a section for the supervisor to add what actions will be taken to assist the employee in his improvement efforts.
• The form should have a section that will allow the employee to write in his comments about the performance review process. This area will also be where the employee can add comments if he disagrees with any ratings and why.
• There should be a place for the employee and the supervisor to sign and date each page of the form.
Table P-5 Example of Performance Factor Section on Final form
| PERFORMANCE FACTOR | RATING | SUPPORTING COMMENTS |
|---|---|---|
| DECISION MAKING | MEETS EXPECTATIONS | Makes sound decisions based on utilization of all information available at the time. Will seek advice of others before making decisions. |
| CARE OF EQUIPMENT | EXCEEDS EXPECTATIONS | Keeps equipment in excellent condition. Orders equipment when needed. Updates inventory in timely manner. |
| COMMUNICATION SKILLS | MEETS EXPECTATIONS | Communicates effectively with public and other loss prevention officers. Utilizes correct grammar in oral communication |
The employee should be given a copy of the completed, signed form. The supervisor should attach his worksheet used to his copy of the final form and place it in the employee’s incident file. It will be used as a reference during the course of the next review period and when training opportunities arise.
Step 6: Conduct Milestone Meetings
“Milestone meetings” should be arranged periodically throughout the year to review the retail loss prevention employee’s progress at reaching goals and taking steps agreed upon to improve performance. Ideally, the milestone meetings should take place quarterly or at a minimum of twice a year. The meetings do not need to be of a formal nature but should be documented by the supervisor. The meeting can be done over a cup of coffee or during a visit with the employee in the supervisor’s office. The important aspect of conducting the milestone meetings is to let the employee know you take his development serious enough to check on his progress. It also affords an excellent opportunity to monitor training agreed upon or for the employee to discuss any new concerns or problems he might have.
Summary
Conducting performance appraisals can be productive for both the employee and management in any retail loss prevention organization if they are thought of as a developmental tool. The time the employee and supervisor spend together to review the employee’s performance should provide an excellent opportunity for both to communicate and clarify expectations each has of the other. This is especially important in the retail environment where performance directly affects the organization’s bottom line.
Performance appraisals or evaluations should be done as often as needed and at least once a year. They should be a review of the employee’s performance since the last appraisal or evaluation. Some keys to the process would be for the supervisor to explain it to the employee; encourage participation from the employee; review and evaluate performance, not personality; and document positive performance as well as negative performance. Effective performance and development reviews are part of a continuing process all retail loss prevention organizations should be using to increase the value of the most important asset—their employees.
(1) Sachs R.T. The productive appraisal. New York: American Management Association, 1992.
(2) Fisher M. Performance appraisals. London: Kogan Page Limited, 1996.
(3) Sachs R.T. The productive appraisal. New York: American Management Association, 1992.
(4) Fisher M. Performance appraisals. London: Kogan Page Limited, 1996.
(5) Fisher M. Performance appraisals. London: Kogan Page Limited, 1996.
(6) Fisher M. Performance appraisals. London: Kogan Page Limited, 1996.
(7) Fisher M. Performance appraisals. London: Kogan Page Limited, 1996.
Pharmacy LP Investigations
Introduction
The operation of a pharmacy is one of the most complex businesses in retail. The pharmacy provides critical patient care that requires a special level of customer service. Customers visiting a pharmacy are comforted by seeing the same pharmacists and drug technicians because this is truly a relationship business. While the customer’s interaction is brief, the operation, as a whole, is a complex machine that is full of opportunity for shrinkage and theft.
For the loss prevention practitioner, the pharmacy can be an intimidating and even unfriendly place to work. My observations over the years is that knowledge of the operation, and therefore knowledge of the causes of shrink, can be gained only by being immersed in the pharmacy itself. Some loss prevention department staff are required to become certified pharmacy technicians in an effort to familiarize them with everything from the filling process to potential drug interactions. It is a highly technical business that is closely regulated by the Drug Enforcement Administration (DEA). It is a business of trust that a customer builds with the pharmacy staff. Most importantly, it is a business that cannot afford mistakes in the prescription filling process. Misfilling a prescription can be extremely harmful to the patient and could ultimately cause death.
What is important to understand about pharmacy shrinkage is that the traditional areas for loss are comparable to other retail sectors, but there are many more additional opportunities for shrink through insurance accounting issues, returning expired drugs for credit, acquisition costs of pharmaceuticals, LIFO inventories, and an endless list of other, more subtle areas. With the pharmacy of a typical drug store generating about half the sales of the entire store, shrinkage is critical from a financial standpoint. The twist that makes shrink wholly different in this case is that the shortage could be medication.
The true depth of internal thefts is unknown but pharmacy shrink is comparatively low to the rest of the store. Beneath the surface of that shrink, though, lies an unfathomable thirst for pharmaceutical narcotics bought on the street. In 2005 a Reuters report cited the National Center on Addiction and Substance Abuse at Columbia University survey that showed that more Americans were abusing controlled substances than cocaine, hallucinogens, inhalants, and heroin combined. According to that same Reuters article, the number of prescription drug abusers doubled from 1992 to 2003 to nearly 15 million.
A 100-count bottle of OxyContin 80 mg (street named Oxy’s, OC’s, Killers, Poor Man’s Heroin, and Hillbilly Heroin), the brand name of a powerful prescription pain medication, has an average street value of about $8,000, or $80 per tablet. A 500-count bottle of hydrocodone/acetaminophen 5/500, the generic name of another prescription pain medication with multiple brand names, the most common being Vicodin, has a value of ab out $2,500, or $5 per tablet.
Auburn University’s Harrison School of Pharmacy conducted a study in July 2004 that reported approximately 10% of pharmacists become chemically impaired at some point in their professional career. The University of Georgia in 2002 reported that 40% of the pharmacists they surveyed voluntarily admitted to taking a regulated prescription substance without a prescription, and 20% admitted to repeated use.(1)
Loss prevention’s role in the investigation of drug loss due to theft is a highly specialized combination of art and science. Shrink causation as a whole is deeply rooted in accounting and may not be ascertainable only at the store level. Shrink reduction in the pharmacy must be attacked from a corporation standpoint and not left to the imagination of only those at store level.
The Growing Addiction Problem
It is estimated that 8–12% of healthcare workers have substance abuse problems. Furthermore, 11–15% of pharmacists, at some time in their career, are confronted with alcohol and/or drug dependency problems, and the median age of recovering pharmacists is 43 years.(2)
Drug abuse has become a national health epidemic among young people. Diverted pain medications are widely sold across the United States and are second only to marijuana in illicit sales. The quantity of pharmaceuticals diverted through theft from legitimate sources, particularly pharmacies, is approximately 6.8 million dosage units (excluding liquids and powders) each year.(3)
According to the 2004 National Survey on Drug Use and Health, approximately 3 million persons aged 12 or older had used OxyContin nonmedically at least once in their lifetime. This is a statistically significant increase from the 2.8 million lifetime users in 2003.(4)
A questionnaire about OxyContin was included in the 2006 Monitoring the Future Study for the first time. During 2005, 1.8% of 8th graders, 3.2% of 10th graders, and 5.5% of 12th graders reported using OxyContin within the past year. During 2004, 1.7% of 8th graders, 3.5% of 10th graders, and 5.0% of 12th graders reported using OxyContin within the past year.(5)
During 2004, 2.5% of college students and 3.1% of young adults (ages 19–28) reported using OxyContin at least once during the past year. This is up from 2.2% and 2.6%, respectively, during 2003.(6)
Primer on Controlled Drugs
A controlled (scheduled) drug is one whose use and distribution is tightly controlled because of its abuse potential or risk. Controlled drugs are rated in the order of their abuse risk and placed in Schedules by the Federal Drug Enforcement Administration (DEA).
• Schedule I: Drugs with a high abuse risk. These drugs have no safe, accepted medical use in the United States.
• Schedule II: Drugs with a high abuse risk, but also have safe and accepted medical uses in the United States. These drugs can cause severe psychological or physical dependence. Schedule II drugs include certain narcotic, stimulant, and depressant drugs.
• Schedule III, IV, or V: Drugs with an abuse risk less than Schedule II. These drugs also have safe and accepted medical uses in the United States. Schedule III, IV, or V drugs include those containing smaller amounts of certain narcotic and non-narcotic drugs, antianxiety drugs, tranquilizers, sedatives, stimulants, and non-narcotic analgesics.(7)
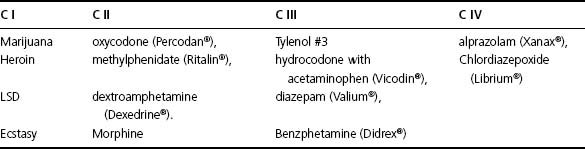
There is not a state or federal requirement that a pill-to-pill perpetual inventory be kept of all narcotics. Narcotics are grouped by class of 2 through 5 and are represented as here: CII, CIII, CIV, CV (see Table P-6). CII drugs are the most addictive and are generally pain medication. All drugs are regulated by the DEA, but CII is the only drug class that the DEA closely regulates and monitors as far as ordering and dispensing. OxyContin, as mentioned previously, is a CII.
Theft of Controlled Drugs
Basic Pharmacy Inventory
Drugs, just like clothes on a rack, are simply merchandise items as far as inventory accounting is concerned. Pills come from the manufacturer in bottles of 100 or 500 or even 1000, and liquids are usually shipped in bottles containing 480 milliliters (1 pint) or 960 ml (2 pints).
Controlled drugs are on the shelves with the other drugs and are in alphabetical order. There is not a federal or state requirement to keep the CII drugs under lock and key; therefore, they can be dispersed (kept on the shelves). Retail chains will generally maintain the CIIs under lock and key, but that is a company requirement and not a mandate by administrative order. Dispersing the CII drugs has a distinct advantage when considering loss mitigation against burglary or robbery. If kept in a locked drawer, all the most theft-prone drugs are simply in one place. There are specially made drug safes, but they are normally used in hospitals and require dual control. These are simply impractical for a pharmacy due to its size and the staffing requirements needed to manage its use.
The inventory replenishment/ordering is fairly basic: Each drug has a specified quantity on the shelf that is based on the volume of sales for that item. As prescriptions are filled, the physical and book inventory are decremented. When that quantity meets a specified threshold, more is ordered (automatically or manually) to replenish the stock. It is the common min/max concept. In a perfect world, it would be a perfect system.
Most drugs have a “name brand” product and a generic equivalent. As an example, Ritalin© is also sold under the generic as methylphenidate. While both are chemically the same, generic brands are manufactured by various companies and are generally less expensive than the name-brand product. Some insurance plans will not allow dispensing namebrand products if a generic is available, so doctors must designate that the prescription be “dispensed as written” or DAW.
The significance of this basic environment (brand versus generic) is that it allows for the appearance of shortages when in actuality one was probably substituted for another. These false variances would only cause investigative time to be spent needlessly. There are times when pharmacists change the prescribed medication to generic because the name brand is out or the customer’s insurance plan will pay only for generic and the doctor wrote for name brand. This is a common practice, but once the prescription is entered into the computer for generic, the inventory will be adjusted accordingly. If the record is not changed in the pharmacy system to properly reflect the correct medication dispensed, it will create “paper” variances. These factors and others make the detection of theft extremely challenging. Without an internal or commercially available inventory variance software, identifying theft is nearly impossible. As with any enterprisewide system, it would be impossible to investigate all shortages that are detected by a variance software. This truly creates an investigative process that deals with only “high” variances that surpass a certain threshold. Defining “high variance” is different for nearly every store.
Once Filled
Once the prescription is entered into the computer, the medication is removed from the shelf and staged for the pharmacy tech or pharmacist to fill. The prescription is filled, bagged, and placed in a “will call” bin. This process can be repeated as many a 1,000 times a day or more, and in the 24-hour stores, it’s repeated at all hours.
From an inventory accounting standpoint, the filled prescriptions are still considered to be in the physical inventory and are not relieved from inventory until they are rung through a register. Ideally, this would be accomplished through a bar-coding system of the bag’s label that was created by the pharmacy system. When the register transaction is completed, the inventory is relieved. This creates an end-to-end transaction process. This, too, depending on the system, assists in maintaining a proper stock amount so that the pharmacy does not run out of that particular drug.
Point of Sale
The final step of the sales process is at the register. This point provides the means to use subterfuge to pass stolen drugs and, more frequently, presents the opportunity to fail to properly record a transaction and steal cash. The cash register is an enormous point of theft of cash because the sales are predominantly insurance co-pays that are even dollar amounts such as $10, $20, etc. Prescription bags have large labels attached to them which include literature for the drugs. Customers would not be suspicious of not receiving a register receipt and, as such, the cashier would not need higher level math skills to manipulate a register. The No-Sale function on a pharmacy register can prove to be disastrous if not properly managed.
Register manipulations through voids of any kind and refunds are equal opportunity offenders. Refunding a prescription is rare, but the highest dollar merchandise in the store can be found near the pharmacy. Cash register exception reporting must be fine-tuned for the pharmacy. The number of transactions is much lower than the front end, but they are, by average, much higher average transactions. A successful search for theft tracks can be accomplished only if the pharmacy sales transactions are separated from the rest of the store. Their transactions are unique and would skew any reporting system if included within the store as a whole.
Many POS systems are tied to the pharmacy dispensing system to maintain an accurate perpetual inventory. Rigorous enforcement of policy and procedure will always act as a deterrent. However, work flow in a pharmacy tends to break down those standards during peak pickup times. This is especially true in high-volume pharmacies.
Return to Stock
The desired final destination for all filled prescriptions is in the customer’s hands. Surprisingly, many prescriptions are never picked up, and the medication must be returned to the shelves. This process is accomplished through the pharmacy management system to correct the inventory accuracy. The actual bottle or vial is placed back in the location from which it was filled and can be used again to fill later prescriptions. It is a violation of law to combine the contents of a returned prescription with the contents of what is on the shelf. The shelf contents may have a different manufacturer or a different lot number, and therefore the vial or bottle is placed on the shelf. This practice allows for easy monitoring of how return-to-stock procedures are being handled. If there are no containers on the shelves from previously filled prescriptions, then the contents are being mixed.
The shrinkage and theft opportunity here is that a person can indicate that the prescription was returned to the shelves and then actually steal it. Again, this will create a variance in the system but does little to point an investigation in the right direction. Additionally, as with all theft, detection is severely limited if the subject steals small amounts of drugs at a time.
Drug Diversion Investigation
Stealing drugs is just a variation of a old theme. Whether with narcotics or some other medication, the pharmacy business is no different from any other retail sector as far as theft is concerned. The primary concerns are as follows:
1. Theft can be of a filled customer’s prescription, either partially or in total.
2. Fictitious or forged prescriptions can be created, and the drug is then either passed or actually paid for at the register.
3. The automated or manual ordering system can be overridden to bring in more drugs than the order should be.
4. Large quantities of drugs are purchased through a licensed pharmacy and sold on the street. Part of the proceeds are used to purchase more drugs, and the rest of the money must be laundered through shell companies or other cooperating pharmacies. This is a multimillion dollar enterprise.
Diversion as described in point 4 is large-scale fraud. It is as pervasive as the trafficking in illicit drugs, and there is no centralized database that can be tapped into either on the state or federal level that would assist investigators to be proactive. Investigations begin through normal law enforcement activity and audits conducted by the DEA and State Boards of Pharmacy. Retail pharmacy chains have a great deal of exposure if diversion occurs within their stores. For that reason, operations and loss prevention must work hand in glove to properly monitor and investigate unusual drug movement. That is not to say that large pharmacy cases do not exist, but they are the exception and not the rule. Diversion of “small” quantities for sale will be the primary topic here.
It should be stated that diversion can occur with any drug and it does not necessarily have to be sold on the street. Drugs can be diverted to a privately owned independent pharmacy to be sold to defraud Medicare. A pharmacist who normally works at a hospital and is diverting drugs there can use the retailer’s pharmacy as a method of replacing those stolen.
Second, there is theft of narcotics for personal use due to addiction, also known as “impairment.” A percentage of healthcare workers are addicted to narcotics to which they have access. In the sense that theft is theft, there are some extenuating circumstances that should be discussed.
The scenarios are endless, but the major areas of vulnerability are fairly common. How could there be so much vulnerability in an area of such confined space? The truth is that the confined space adds to the opportunity for theft. A pharmacy, during high traffic times, is a beehive of activity with little time to notice the behavior of those around you.
Discovery Phase
Identification of potential drug loss is really simple inventory math. In its most basic description, the suspect must order more drugs than is being used to fill prescriptions. Diversion on a large scale is rare in a chain drug store because of the monitoring that takes place. Unusual ordering activity, P&L book inventory values spiking, and other areas might also give some insight to operations. Being able to detect a problem across numerous stores or across an entire chain would be impossible without software monitoring.
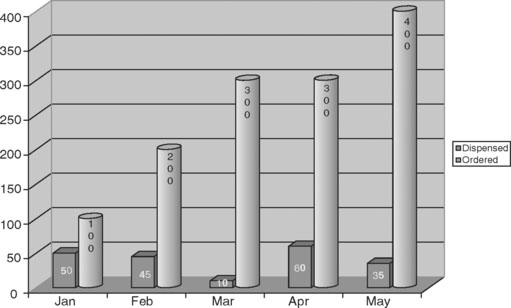
Following is the typical scenario that initiates an investigation. This is a generalization as every company has different methods to order drugs: A pharmacy orders two bottles of Drug A. The bottles contain 100 tablets each. The order can be entered manually through a handheld device, or it can be ordered through an automated replenishment system. Its source can be a company distribution center or an outside vendor. Two bottles of 100 tablets are sent to the store, where it is received and placed on the shelf. Over a period of time, the pharmacy fills prescriptions that equal 100 tablets. In a perfect scenario, there would be one bottle of 100 left (see Figure P-1). Either through auto replenishment or through manual orders, more bottles are ordered. To successfully steal drugs, the normal order quantity must be overridden in the system. Over time the number of bottles (or number of dosage units, in this case tablets) ordered begins to exceed the amount needed for filled prescriptions. A data mining program would begin to alert the investigator that the pharmacy was experiencing ordering activity that was not justified for the number for actual prescriptions. According to a report, over the period of time reviewed, the pharmacy had ordered 13 bottles (1300 dosage units) and had dispensed only 2 bottles (200 dosage units). Again, in our sample case, there should be 11 bottles of tablets on the shelf. A visual inspection of that specific drug reveals there are only 2 bottles. The next phase of the investigation begins.
Investigative Phase
Pharmacy drug loss investigations are initially highly confidential because the number of potential suspects includes anyone who has access to the pharmacy or who can potentially gain access to the pharmacy. The one saving grace of these types of investigations is that if the suspect is a pharmacy employee, the thief is usually going to be the person who is overriding the internal systems replenishment process. However, even with that group narrowed, it is unknown as to how the drugs are leaving the pharmacy. This could involve accomplices, multiple suspects, or outside vendors. Carrying out one bottle of pills is fairly easy to do on your person, especially if the pills are no longer in the bottle. Diverting large quantities may present a challenge but may be overcome by simply using the mail or commercial carrier to ship them home.
Once a loss has been determined, the DEA must be notified in writing within 1 business day. This can be accomplished by faxing a simple memo to the local DEA office regarding the initial reporting of a loss. Further investigation would be needed to confirm the actual loss. The DEA has very stringent administrative policies regarding loss reporting, but unless it is a special circumstance, the agency will not become actively involved. Every state also has a State Board of Pharmacy that regulates the licensing of the pharmacists and the pharmacy itself. The reporting requirements vary for each state, but, in general, there is no requirement to inform them of any investigation. However, it is a good practice to do so.
Narrowing the scope of the investigation to an individual takes a thorough review of store-level paperwork, schedules, or through any technological means. Again, the sensitive nature of the investigation generally prohibits the usual hands-on investigative techniques at the outset. Unless a trusted individual is cooperating with loss prevention, a great deal of work must be done before store opening or after store closing. To reinforce the sensitive nature of the investigation, a confidentiality agreement can be requested of any assisting employee. Breaking the confidentiality agreement would result in termination.
CCTV is almost paramount, and it may require multiple cameras. The layout of the pharmacy makes camera placement difficult, as an overhead view of the target drug severely limits view. Theft of one bottle of pills from shelf to pocket takes 2 seconds, but there is no need to review video unless there is a known shortage. This will required frequent, if not daily, reconciliations of that drug to determine if there is a shortage.
Investigative Scenario
Whether detected by automated means, audit, or tip, the investigative process can be very long. However, with proper preparation, these cases are likely to last no more than a few weeks.
When surveillance is begun, there is a period of time when it requires total confidentiality. Operations staff should be notified, however, because they may have to escort you in to the pharmacy during nonoperating hours. A licensed pharmacist must be present if you are entering the pharmacy. Entering the pharmacy is key obviously to physically recording the on-hand count of any targeted drugs. Using an automated system allows decisions to be made as to where to position a camera(s) to get the most likely theft.
The difficulty of these investigations is confirming a loss. An actual pill/liquid count is generally not necessary, as the theft usually involves full bottles. Nonetheless, it requires surveillance to determine where suspicious activity is occurring. In the multistore environment of retail drug establishments, there is not always the luxury of having stores closely clustered together. Pharmacies at great distances from the investigator’s home may require a revised approach to complete the investigation. Retrieval of video may be an issue if a DVR is used. Using time-lapse VCR may be of more benefit if the investigation is being assisted by a member of store management.
If the amount of stolen drugs is high, it is very likely that that local authorities or the DEA will be involved. There may be requests to allow the thefts to continue to occur while their criminal investigation proceeds. This should obviously be reviewed by a corporate legal department.
Apprehension Stage
Closing out an investigation can occur with or without an apprehension. In both instances, several administrative items must be concluded.
If a company employee is apprehended, the usual internal steps should be taken regarding evidence and statements. Prosecution has several variations that are of interest. Drugs are generally inventoried at cost and may be converted to retail for physical inventory purposes. This sometimes presents a challenge to local authorities as to how to assess value. This is important because most jurisdictions will charge the individual with theft because there is no statue that provides for illegally taking of controlled drugs. This truly points out the value of having the DEA or State Board of Pharmacy involved even if just as an advisor. Those agencies can assist in the proper framing of criminal charges if necessary. In the case of a pharmacist and in some states a drug tech, the State Board of Pharmacy will hold an administrative hearing to determine the fate of the offender’s license. More importantly, the state can sanction the license of the store’s pharmacy too and levy a fine against the company. While the pharmacy’s license could be revoked, it would be extremely rare in a chain drug store.
If a good relationship exists between the investigator and law enforcement, loss prevention should be allowed to complete the internal investigation. This allows the company to fulfill all obligations to protect company assets and at the same time still provides law enforcement with a prosecutable case. Collaboration is the key to successfully investigate any drug loss.
Drug Testing and Polygraph as an Investigative Tool
Because narcotics are involved, there are two additional investigative avenues afforded: drug testing and polygraph. Despite common belief, the use of the polygraph is still viable. The Employee Polygraph Protection Act of 1989 allows pre-employment and investigative use of polygraph. This is a thorny subject. Policy and procedure for its use should be well planned and distributed to all employees. There should be a formal review process in place that includes the legal department and loss prevention senior management for requesting the use of polygraph. It is recommended that the polygraph request is presented to the employee in writing. That request should outline why the examination is being requested and should outline both company policy and the Employee Polygraph Protection Act of 1988 (EPPA) for the employee’s review. The employee should be allowed to keep a copy of this document as well. If considering the use of polygraph, keep in mind that neither refusal to take the polygraph nor the results of the polygraph can be used solely as justification for termination. The polygraph is simply a tool within the totality of the investigation. It has been my experience that it is rare when an employee actually appears for the process.
Note: While we believe the polygraph is a valuable investigative tool, as noted in the preceding text, the nuances of the EPPA are many and complicated, and the penalties for violation of its provisions can be severe. Therefore, before any mention of the use of the polygraph is made during an investigation, we strongly suggest competent legal counsel be consulted. CAS/JHC.
Employee Polygraph Protection Act(7)
Prohibitions
Employers are generally prohibited from requiring or requesting any employee or job applicant to take a lie detector test, and from discharging, disciplining, or discriminating against an employee or prospective employee for refusing to take a test or for exercising other rights under the act.
Examinee Rights
The act permits polygraph (a kind of lie detector) tests to be administered in the private sector subject to restrictions, to certain prospective employees of security service firms (armored car, alarm, and guard), and of pharmaceutical manufacturers, distributors, and dispensers.
The act also permits polygraph testing of certain employees of private firms who are reasonably suspected of involvement in a workplace incident (theft, embezzlement, etc.) that resulted in economic loss to the employer.
Drug Testing
Drug testing can also be employed, but it must comply with the Federal Workplace Drug Testing Guidelines. If a drug test is conducted for a pharmacy investigation involving personal use or addiction, it is recommended that the test be administered after the investigation target has been on duty for a few hours. Most companies have very clear drug testing policies, and retail drug chains have fundamental policies and procedures firmly in place. Those policies will generally state that failure to submit to a drug test is basis for termination. Due to the nature of the test, it will be unannounced, and proper relief of staff is critical to maintain the operation of the pharmacy. If an employee refuses to submit to a drug test, there should be sufficient policy in place to seek termination.
Confirming the Loss and Conducting an Audit
Regardless of the end result of the investigation, an inventory is recommended for all controlled drugs at the conclusion of the internal investigation. This should be done for two reasons:
There are variables as to how the inventory is performed to ensure that the pharmacy’s record keeping is in compliance. There is somewhat of a Catch-22 with this process, however. By law, the initial loss was reported to the DEA and possibly the State Board of Pharmacy. They can accept your internal inventory results or conduct independent audits of their own. The State Boards of Pharmacy have the power to adjudicate any violations of record keeping found during an audit. Even though their audits were initiated by the company itself, penalties such as fines can be assessed. Obviously, if a pharmacist is involved, the board will take action against his license.
This is truly an end-to-end investigation that provides a paper trail and a reconcilable inventory to determine exact loss. These cases require extreme patience that may even dictate that thefts are allowed to occur to expand the investigation as needed.
Forged Prescriptions(8)
Signs to aid in the detection of fraudulent prescriptions: Forged prescriptions are a significant problem for today’s pharmacies. Pharmacists should be aware of the various kinds of fraudulent prescriptions which may be presented for dispensing:
• Legitimate prescription pads are stolen from physicians’ offices, and prescriptions are written for fictitious patients.
• Some patients, in an effort to obtain additional amounts of legitimately prescribed drugs, alter the physician’s prescription.
• Some drug abusers will have prescription pads from a legitimate doctor printed with a different call-back number that is answered by an accomplice to verify the prescription.
• Some drug abusers will call in their own prescriptions and give their own telephone number as a call-back confirmation.
• Computers are often used to create prescriptions for nonexistent doctors or to copy legitimate doctors’ prescriptions.
Characteristics of Forged Prescriptions
1. The prescription looks “too good”; the prescriber’s handwriting is too legible.
2. Quantities, directions, or dosages differ from usual medical usage.
3. The prescription does not comply with the acceptable standard abbreviations or appears to be textbook presentations.
4. The prescription appears to be photocopied.
5. Directions are written in full with no abbreviations.
6. The prescription is written in different color inks or written in different handwriting.
Theft and the Impaired Pharmacist
Impaired pharmacists are no different from any other person with an addictive disease. The addiction may start with taking pills to take the edge off the day or to help with backache from standing all day. Taking the drugs may initially be circumstance driven, but then the drugs may be taken in anticipation of the original problem. As the body increases its tolerance, larger doses or more powerful drugs are needed to obtain the same effect. The early stages are difficult to detect unless it involves CII drugs, as there is a requirement of perpetual inventory on these.
These types of thefts are long term, however, and the loss begins to accumulate. The pharmacist or drug tech knows that continued abuse of one specific drug will eventually be detected, so he begins stealing a variety of drugs that deliver the same effect. A unique factor to the investigation of impairment thefts is that some pharmacists “float.” They are not assigned to a specific store, or they act as part-time pharmacists who are called in for staffing reasons. These are absolute moving targets who take advantage of the variety of stores they work. Now the situation is complicated by a person stealing multiple drugs and multiple locations. However, once a possible suspect is identified, that person can be moved to one store for surveillance purposes.
Narcotics, specifically pain medication, are the most abused type of drug. Whether liquid cough syrups with codeine or heavy pain management pills such as Vicodin or OxyContin, the theft methodology is fairly consistent. Drugs must be brought into the pharmacy by any means available and then be hidden or must be removed from the pharmacy as quickly as possible. Liquids are often drunk directly from a bottle and then placed back on the shelf. The consumed liquid is then replaced by adding distilled water to the container. This practice creates an obvious health risk for patients.
The impaired pharmacist has a disease that cannot be addressed through awareness meetings or poster campaigns. These individuals need professional help and, like most addicts, are reluctant to come forward to get the help they need. Their biggest fear is that their license to practice pharmacy may be in jeopardy. Pharmacies should have available the phone numbers of the state’s impaired pharmacist hotline so they can get immediate help. One of the primary organizations that deal with pharmacist rehabilitation is the Pharmacy Recovery Network (www.usaprn.org). The success rate for many of the PRN programs is as high as 85%.
Understanding addiction as a disease will help the loss prevention professional a great deal in this industry. This is somewhat of a learning curve for those coming from other types of retail. The interplay between the theft of narcotics and the need to satisfy an addiction is important to understand. An impaired pharmacist may seek medical treatment on his own, and it may be through that process he will divulge the amount of drugs stolen. Even though the pharmacist stole from the company for his own use, restitution may be the final outcome. In short, a pharmacist may be allowed to enter into a rehabilitation program, make restitution for the drugs stolen, and be returned to work upon successful completion of treatment.
This situation is not to be confused with a theft investigation whereby the offending pharmacist is identified and apprehended. There is no “get out of jail free” card for the pharmacist by announcing that he wants to go into a rehabilitation program after he has been caught. Theft cases are handled just as any other.
Reinstating an impaired pharmacist is not as problematic as you might think. Every state has special programs legislated for health professionals with addictions, where the treatment is rigorous and the penalty for relapse is the possibility of permanent loss of license to practice. While the risks are high, the rewards are substantial, as these highly successful state-sponsored programs allow professionals to regain their health and their careers.
These voluntary programs, paid for through health professional license renewal fees, operate on the same basic requirements in each state. The health professional undergoes detoxification before signing a contract agreeing to 3 years of monitoring and random drug tests between 3 and 10 times each month. Weekly group therapy meetings, regular sessions with an addiction physician, at least three 12-step meetings per week are also required. The patient also identifies a sponsor and a work-site monitor.
Approximately 95% of participants in state health professional recovery programs remain sober for at least 5 years, which is a remarkable success rate, especially when compared to other treatment programs that display relapse rates of 66% or higher.(9)
Additionally, reinstatement is a sound business decision because, quite simply, there is a shortage of pharmacists. If the retailer did not reinstate the pharmacist, the pharmacist would certainly work for another company. It is an issue of supply and demand.
Conclusion
The pharmacy is a valuable resource for the community and, when properly managed, can build sales and profit for the retailer. However, this business sector demands great internal care regarding theft, shrinkage, and compliancy. It is an attractant for criminal activity on many levels that requires special investigative strategies and techniques. It requires detailed knowledge of systems and procedures unlike any other retail sector. The challenges for loss prevention staff are enormous because of the complexity of just the business aspects that need to be understood.
Investigations must be concluded quickly and with precision so that the public’s interests are not harmed. At the same time, however, there must be insight into addiction as a disease to allow the practitioner to be somewhat proactive while in the stores. It is a novel business sector that will continue to demand skills and technology that are outside the scope of traditional loss prevention.
(1) Muha, J. (2006, September 1). Drug diversion—Preventing retail pharmacy theft. Loss Prevention Magazine and LossPreventionMagazine.com.
(2) Terrie Y.C. Pharmacy times lean on me: Help for the impaired pharmacist. http://www.pharmacytimes.com/Article.cfm?Menu=1&ID=4115, 2006, November.
(3) Drug Enforcement Administration. National drug threat assessment, DEA, Pharmaceutical Drugs. http://www.dea.gov/concern/18862/pharm.htm.
(4) Substance Abuse and Mental Health Services Administration. (2005, September). Results from the 2004 National Survey on Drug Use and Health: National Findings.
(5) National Institute on Drug Abuse. (2006, April). Monitoring the future national results on adolescent drug use: Overview of key findings, 2005.
(6) National Institute on Drug Abuse. (2005, October). Monitoring the future national survey results on drug use, 1975–2004. Volume II: College students and adults ages 19–45.
(7) Texas State Board of Pharmacy. Controlled drugs. http://www.tsbp.state.tx.us/consumer/broch2.htm.
(8) WH Publication 1462. (2003, June). www.dol.gov/esa/regs/compliance/posters/pdf/eppac.pdf.
(9) Drug Enforcement Administration, Office of Diversion Control. A pharmacist’s guide to prescription control. 1(1). www.deadiversion.usdoj.gov/pubs/brochures/pharmguide.htm, 2000, February.
(10) Programs for Addicted Professionals National Institute on Chemical Dependency. www.nicd.us/addictedprofessionals.html.
Photographing Shoplifting Suspects
We recommend that photographs be taken of apprehended shoplifters, together with the merchandise taken by them, when they are in the LP office being processed. The photograph should also contain on a piece of paper (taped to the wall behind it) or on a chalkboard similarly located the name, date, time, and dollar amount of merchandise stolen, together with the name(s) of the apprehending LP agents, written in felt-tip pen or chalk letters large enough to be easily read. It is not unknown for shoplifters to use false names, and a photograph will remove any question at trial as to who was actually arrested. Either a Polaroid or digital camera can be used for this purpose, and if the apprehension report is computerized, the digital photo can be “pasted” onto the report.
Note: State laws should be checked regarding photographing suspects; some states prohibit such photos.
The time is important because “savvy” shoplifters will often, immediately after their release, return to the store and purchase an item identical to the one stolen, giving them a receipt for that item. When appearing in court, they will then claim a “mistake” and produce the receipt alleging the item was purchased. If the time is in the photo and on the arrest report, combined with the fact that modern POS terminals show the time of purchase, their subterfuge will be readily apparent.
Photographs of the stolen merchandise are also allowed as evidence in lieu of the actual merchandise in many jurisdictions. If permitted, this permits recovered and undamaged merchandise to be returned to stock immediately, thus minimizing any loss of sales because of the incident.
In any investigation (excluding shoplifting as noted previously), photographs of the crime scene and any recovered evidence, together with both still and video footage of surveillances and scenes of pertinent activities captured by CCTV, should be obtained and retained as part of the investigative file, and all photographs and video footage should meet the chain of evidence requirements.
Polygraph
The polygraph (frequently called a “lie detector”) is an instrument which measures and records, via a paper graph and/or computer, psychological phenomena that may be used by trained persons as a reliable technique for diagnosing truth or deception. The instrument records the test subject’s breathing, blood pressure and pulse, and electrodermal conductivity (GSR—galvanic skin reflex). There are several techniques (the most common known as the “control question technique”) for the development of questions to be answered by the subject and for the diagnosis of deception.
The Employee Polygraph Protection Act of 1988 (EPPA) generally prevents employers from using the polygraphs, either for pre-employment screening or during the course of employment, with certain exceptions. Employers generally may not request or require any employer or job applicant to take a polygraph test, or discipline or discharge or take any employment action against an applicant or employee for refusing to take a polygraph test. Additionally, employers are required to display the EPPA poster (explaining workers’ rights) in the workplace.
Since the exceptions to the act are complicated, we suggest that, before any mention of the polygraph is made in the work environment, competent legal advice be sought.
Post Orders
The issuance of “post orders” (what to do and how to do it) by security guard providers is an industry standard. Security officers are not expected to remember everything about their duties. Thus, post orders are essential. The individual guard can refer to these orders (instructions) for guidance whenever he is unclear as to what should be done or how it should be done. Post orders should have been prepared by the security provider, after consultation with the client, then approved by the client, and maintained at and available to all security personnel assigned to the client.
A redacted copy of a good example of post orders follows:
Number of Security Officers: (1) PER SHIFT
Equipment Required: KEYS, PAGER
PURPOSE
To provide security for the client in a manner that will make our presence highly visible and deter those who might consider committing theft or vandalism and provide direction to visitors or the general public. Security, in this context, shall be defined as providing a contact point for employees or tenants experiencing problems within the boundaries of the complex, to investigate such problems, to initiate corrective action for such problems, to report to the civil authorities such matters properly within their jurisdiction, and to properly and completely document such actions. Security services shall not include personal services to the employees or tenant, nor shall you honor any request that will distract you from your duties outlined herein. Any difference of opinion in this matter shall immediately be reported to your field supervisor. A written report shall be forwarded to the management representative the following business day.
CONDUCT AND APPEARANCE
At all times you are to conduct yourself in a professional manner. All contact with employees, management, or the public are to be carried out in a business-like manner. You are to avoid all familiarity even if specifically invited. Verbal contacts are to be carried out in a polite but firm manner. ARGUMENTS ARE TO BE AVOIDED AT ALL TIMES. In the event that someone refuses to comply with your requests, or questions your authority, you are directed to immediately report the matter to your field supervisor or to the proper civil authorities.
While on duty you are to be in complete and proper uniform. Uniform shall be neat, clean, well pressed, and in good repair. Your uniform is the visual representation of your authority. You are a professional; wear your uniform with pride.
STARTING OF POST
Immediately upon arrival, begin your log and receive a briefing from the retiring officer. Upon reporting for duty you shall notify the dispatch center stating your name and the post number. Check for any specific instructions left by the management for the night’s shift. Commence your initial security inspection of the premises.
REPORT WRITING
All reports will be written in a clear and legible hand, and shall be concise, informative, and restricted to the facts. Facts shall be labeled as facts; hearsay and supposition shall be labeled as such.
Reporting is one of the most important aspects of any security post. A security officer might view the log sheet as an invoice as well as an information pas down. It is an invoice to each client because it shows the client what he has received in return for his investment in security services. It is also a means by which the client can judge the quality of our service.
PERFORMING YOUR PATROL
During your patrol rounds, you are to observe and report any items found in the building or on the grounds that may constitute a potential hazard. Potential hazards include, but are not limited to, the following: damaged gates or fences, broken windows or doors, fire equipment blocked, stairways or fire escapes obstructed, lights burned out or broken, or fixtures on the common areas that are not functioning properly. It is your duty to inform the management of any repair or maintenance problems in writing on your log sheet.
CLOSING YOUR POST
Before closing the post for your shift, be sure that you have completed your security log sheet for the shift and any incident reports necessary. Brief your relieving officer on all items of interest, and call the dispatch center to inform them that your have completed your shift. Leave a copy of your log on site in the designated area. Check in any equipment issued to the officer assuming duty or to the center office.
EMERGENCY OPERATION PROCEDURE
When an emergency occurs which requires the police department, fire department, or paramedics to respond, immediately contact the dispatch center either by radio or phone (1–800-xxx-xxxx) When the dispatcher comes on the line, give him/her the name of the complex and the complete address, including the unit and the nearest street access. State the nature of the emergency, speak slowly and distinctly. DO NOT HANG UP THE PHONE UNTIL THE DISPATCH OPERATOR STATES THAT YOU CAN. Then proceed to the appropriate access area to assist the emergency service.
When the emergency service arrives, assist if requested. When the emergency is over, advise the dispatch of your status and resume normal operation as soon as possible.
| Police Department | 911 |
| Fire Department | 911 |
| Paramedics | 911 |
| Harbor Police | 223–1133 |
| ProtectAll Security | |
| Dispatch | 555–1234 |
| 800 Line | 800-555-1239 |
| Sales and Service | 555–2345 |
SEE ATTACHMENT HERE TO FOR THIS POST
POST ORDER ATTACHMENT FOR 2055 Goodview Blvd, San Diego
*NEED TO PICK UP KEYS PRIOR TO SHIFT AND RETURN AFTER LAST SHIFT WITH LOGS. DO NOT LEAVE KEYS IN OFFICE AT ANY TIME.
ASSUME POST—CALL 10–41 TO DISPATCH OFFICE.
MAKE CONTINUOUS PATROLS OF THE SHOPPING CENTER. CHECK THE REAR OF THE CENTER FOR LOITERING, UNAUTHORIZED WASTE REMOVAL, KIDS/YOUNG ADULTS, UNAUTHORIZED VEHICLES LEFT OVER NIGHT (ONLY VEHICLES FROM AUTO IMPORTS ARE ALLOWED TO PARK OVERNIGHT). MOVE KIDS OFF PROPERTY, CANNOT BE PLAYING ANYWHERE OR RIDING SKATE BOARDS. BE SURE NO LOITERING AND SKATEBOARDING SIGNS ARE UP.
MAKE VISIBLE PATROLS OF THE FRONT OF SHOPPING CENTER, INCLUDING JOE’S GRILL AND MAX 8 THEATER. THE FAST FOOD PLACE IN THIS CENTER DOES NOT PAY FOR SECURITY SERVICES; DO NOT FOLLOW ANY INSTRUCTIONS FROM THEIR MANAGEMENT. NO LOITERING IS ALLOWED AT ANY TIME ON PROPERTY.
YOGI’S ALSO DOES NOT PAY FOR SECURITY, BUT MONITOR THEIR LOT IN CASE PROBLEMS START THERE AND MOVE INTO OUR RESPONSIBILITIES.
GAS STATIONS ARE NOT PART OF OUR RESPONSIBILITY; PROVIDE NO COVERAGE IN THESE AREAS… .
IF FRESH GRAFFITI IS DISCOVERED, ADVISE DISPATCH TO CALL CLIENT AT DAY CONTACT NUMBER SO THEY CAN ARRANGE TO HAVE IT PAINTED OVER.
THERE HAVE BEEN A LOT OF PROBLEMS AROUND PIZZA PLUS AND THE ARCADE AREAS. SPEND A LOT OF TIME NEAR THERE.
IF VEHICLE ACCIDENT OR ANY INJURY OR DAMAGES TO PATRONS, TENANTS OR BLDGS ON SITE, CLIENT MUST BE ADVISED ALONG WITH A SUPERVISOR. DETAILED INCIDENT REPORT MUST BE TURNED INTO OFFICE AT E.O.S. THAT DAY REPORT MUST INCLUDE NAMES OF PARTIES, DESCRIPTION OF WHAT HAPPENED, DAMAGE OR INJURY DESCRIPTION, IF POLICE OR AMBULANCE CAME AND THE NAMES AND IDS OF THESE EMERG PERSONNEL AND TIMES OF ALL.
POST COMPLETED—CALL 10–42 TO DISPATCH OFFICE.
LOG SHEET TO BE LEFT: AT OFFICE, INCIDENTS/PROBLEMS WILL BE SENT TO MGT. COMPANY.
Pre-Employment Screening
Is pre-employment screening necessary? If so, of what should it consist of, and how should it be accomplished?
We believe pre-employment screening is a business necessity today for the following reasons:
• The acknowledged rising levels of theft, drug abuse, and other counterproductive behavior in the workplace.
• The growing legal responsibility of employers for actions of their employees. Although the courts have laid down no hard-and-fast rules as to the required thoroughness of pre-employment investigations required to mitigate such liability, they have held employers liable for not conducting adequate pre-employment investigations.
• The scarcity of qualified workers and the extremely high cost of turnover, estimated at 38% of annual salary.
• The increasing trend of job applicants to falsify their educational, employment, and other job-related background information.
While statistics vary, companies have reported the following for blue-collar applicants: 39% of walk-in applicants left when told that background investigations would be conducted; 15% left when given the background forms to fill out; and 5% never returned after filling out the forms. Many applicants, when they see notices that drug screening is a part of the application process, simply turn around and leave.
The 2005 National Retail Security Final Report indicates that nearly $15 billion is lost to U.S. businesses each year from employee theft. Intangible theft (late arrivals, bogus sick days, deliberate unproductive time, etc.) and drug abuse add significantly to this amount.
It is apparent that the penalties for guessing wrong when it comes to making an employment decision can be extremely costly; therefore, it is essential that some method be utilized to screen job applicants to minimize losses which result from poor employee selection.
The next question is: What should pre-employment screening be designed to accomplish?
Because employees are complex human beings, a multidimensional approach to selection is demanded. Simply put, we should screen for success and effectiveness. How can this be accomplished? The answer is to utilize proven and validated techniques which can assess both the strengths and weaknesses of applicants, thereby providing the decision maker with all the information which will enable an intelligent decision and permit matching the applicant to existing jobs and the personality of the employer and its work environment.
Pre-employment screening should be designed to “pass” as many applicants as possible and yet reject those whose employment will result in counterproductive or dishonest behavior or who will fail because they cannot meet the performance standards of the job. The bottom line is that short-tenured or unproductive employees are extremely costly and a drain on profitability.
The goal of pre-employment screening should be to identify those applicants who possess those factors of personality (stability, stress and frustration tolerance, learning ability, and self-reliance) together with a work ethic which stresses high work quality and quantity; who will have low tolerance of absenteeism, theft, and antiorganizational attitudes; and who will tend to stay with the company.
What are some of the techniques which have been traditionally utilized to accomplish pre-employment screening?
• Polygraph: Legislated unlawful by the Employee Polygraph Protection Act of 1989.
• Interviews: The courts are now saying that interviews must be limited to purposes such as verifying background data, assessing skills, developing employment history information, reviewing educational background, etc.
Interviews, while they may develop employment history, cannot really be predictive of honesty or integrity on the job. There is also an inherent danger that interviews may be discriminatory in that we tend to hire in our own self-image. There is no question that interviews, properly structured and conducted by a skilled interviewer, can be most helpful in determining skill levels and some personality factors and may develop information with respect to falsified credentials or background data.
• Records (DMV and Credit) Checks: Such checks must be relevant to the job. For example, a DMV driving records check for a sales associate that was used to deny employment would probably be impermissible. There are also restrictions on using credit checks for other than certain few selected job categories. Credit checks are subject to the federal rules under the Fair Credit Reporting Act (FCRA).
• Arrest Records: Use for granting/denying employment is illegal.
• Conviction Records: Allowable but can be used to deny employment only if the crime for which the applicant was convicted can reasonably be expected to occur on the job in a way harmful to the employer. It is also worthy to note that nationally it is estimated that only one in six criminals is ever caught or arrested; therefore, there is only a 1 in 6 chance of a record existing. Conducting such records checks can be a good defense to wrongful hiring or retention suits, particularly in the case of loss prevention personnel.
• Reference Checks: Obtaining written information from references or former employers is very difficult; employers are afraid of defamation suits. However, a skilled investigator, armed with properly executed releases, can develop reliable information in many instances. Reference and employment checks are singularly important because they tend to disclose recent prior performance, which psychologists universally agree is a highly reliable predictor of future performance.
Typical of what is allowed in checking references is outlined in the Arkansas Department of Labor’s Code § 11-3-204:
Providing references to prospective employers.
“I, (applicant), hereby give consent to any and all prior employers of mine to provide information with regard to my employment with prior employers to (prospective employer).”
(c) The provisions of this section shall also apply to any current or former employee, agent, or other representative of the current or former employer who is authorized to provide and who provides information in accordance with the provisions of this section.
(e) The immunity conferred by this section shall not apply when an employer or prospective employer discriminates or retaliates against an employee because the employee or the prospective employee has exercised or is believed to have exercised any federal or state statutory right or undertaken any action encouraged by the public policy of this state.
• Handwriting (Graphology): No scientific validity; however, I experienced some startling and accurate assessments made by one graphologist. Based on that experience, she was recommended to the ASIS program chair for the annual national program. She appeared and received high ratings by attendees in her session.
• Full Background Investigations: Can be very thorough when properly done. Expensive. Should be used for the most sensitive or high-level positions.
• Drug Testing: Becoming more popular; some legal restrictions or prohibitions. Programs must be well thought out and implemented only after careful study and legal advise. Tend to be expensive and slow. Can be invasive.
The U.S. Navy found a policy of random testing reduced positive results by 66%. Should be considered for certain classes of employees (e.g., those involved with industrial equipment or vehicles or in very sensitive or high-theft exposure areas).
• Store’s Mutual Associations: Inexpensive and worthwhile; names filed limited to those caught and therefore not very extensive.
• Public (for Fee) Pre-Employment Screening Firms: These firms offer services such as criminal background checks, education and professional license verification, motor vehicle reports, reference checks, and more.
Services can be purchased individually or in a package. Concerns include accuracy of data and currency.
• Resume and Application Form Review: Inexpensive but relatively unreliable; 30% contain material misrepresentations. Should be done by trained personnel. Reliance on this alone takes little time but can result in a lot of trouble.
• Psychological Tests: Also known as “Honesty Tests” and/or “Pencil-Paper Polygraph Tests.” Those which are validated are legally permissible. There is predictive validity for several tests. Under legislative (both federal and state) scrutiny. While there may be some legal risks attached to the use of psychological tests and particularly “honesty tests,” many have found them to be useful to either predict or deter dishonesty. Other types of tests have also come under fire; a former security employee at a Target store in Oakland, California, sued that company for race discrimination because he was denied employment after taking the Minnesota Multi-Phasic Inventory (a long-used and well-validated psychological test), and the court ruled in his favor.
What should a test publisher be able to prove?
• The publisher must demonstrate research on validity and peer review in accepted professional publications and journals.
• The publisher must have full-time professional staff.
• The publisher must have history and validity performance and national clients.
• The publisher must have research staff.
• The test must be easy to use, time efficient, and results must be available when needed.
• Test results must be clear and unambiguous.
• The test publisher must have long record of either a lack of claims or successful defense of adverse impact claims/suits.
• There should be evidence that applicants do not feel the test is intrusive.
A model pre-employment screening program will
• Raise the quality of the workforce;
• Reduce turnover and improve morale;
• Reduce theft and counterproductive employee behavior;
• Be easy to administer and produce no adverse reaction or resentful result on the part of the applicant.
Finally, most studies conclude that measures of integrity correlate with other types of counterproductive behavior, and that to discover any flaw in an applicant, whether it be honesty or some other defect, will probably be predictive of other problems as well.
Recommendations
Companies should adopt an escalating protocol for pre-employment screening and testing of applicants/new hires which will begin with the least expensive procedure and work its way up to the more costly techniques, consistent with the level of risk and exposure for a given position. Such a protocol should meet the objectives of a model screening program as noted previously. We suggest this can be accomplished by a pre-employment screening program which follows the steps outlined here, consistent with the sensitivity and risk level of the position applied for.
Thus, under these recommendations, for some positions (to be determined in conjunction with human resources), the process might eliminate steps 4 and/or 6; the length, detail, and depth of step 5, the Interview, would be keyed to job level.
Hence, the recommended steps would be as follows:
1. The applicant appears personally and fills out an employment application and is preliminarily qualified by employment desk personnel.
2. A careful application/resume review is performed by a trained reviewer.
3. For applicants whose applications are accepted, a proven integrity test is administered for all applicants. To be of value, this test should be used consistently, and agreed-upon cutoff or disqualifying scores should not be modified.
4. A background investigation is performed which may include any or all of the following items: credit check, conviction checks, reference checks, education verification, DMV check, SSN check, etc.
5. A structured behavioral interview is performed by trained personnel. This step would be mandatory for all applicants as the final step before placement.
Premises and Personal Injury Liability
It is a legal reality that a store owner owes a duty to his customers (legally called “business invitees”) to provide them with a safe shopping environment.
Premises liability is the civil liability of a property owner which arises when the property owner fails to provide a reasonably safe environment, and as a result, someone is injured. The owner was negligent and thus liable.
Negligence is an “unintentional tort” (civil wrong). Negligence is established if
• There is a legal duty owed to a person.
• There is unreasonable conduct or a breach of that duty.
• There was a foreseeable proximate cause that a person might be injured.
Let’s look at an example of the concept of negligence: This morning, one of your maintenance people decides to wash and wax the entry hallway. The hallway’s surface is very slippery when wet. Your worker has wet-mopped the floor but failed to put out a caution sign warning of the slippery conditions. A guest enters the hallway, slips, and falls, breaking a hip.
Now we all agree that you have a duty to provide a safe environment for your residents and their guests. A wet and slippery floor is not a safe environment—right. So your conduct in not warning of this unsafe condition was unreasonable; in other words, you have breached your duty. Is it foreseeable that a person may slip and fall on a slippery floor? Of course.
That event has now happened—someone (soon to be called a “plaintiff”) has slipped, fallen, and is injured. There is now an injury or damage resulting from that breach. The slippery floor coupled with the failure to warn was the direct or proximate cause of the injury. “But for” the slippery floor and failure to warn, the injury would not have happened. You, because of the foreseeability of such an event, and your unreasonable conduct in not warning, were negligent.
Remember, too, negligence can be either an act or a failure to act when a reasonable person would have acted or avoided an action.
Simply stated, a duty is a legally sanctioned obligation the breach of which results in liability.
Recent years have seen the development of another type of negligence claim against retailers and property owners, which is more directly related to our concerns.
This development is the ever more popular premises security liability, which is the civil liability of property owners for the foreseeable criminal acts of third persons. It arises when property owners or their agent manager fails to provide adequate security to reasonably respond to the foreseeable harm which could injure persons invited onto the property. As a rapidly developing area of tort law, premises security liability is also often referred to as “negligent” or “inadequate” security cases.
Courts have recognized that landowners, despite their best efforts, cannot render their properties immune from crime. Therefore, where a duty is found to exist, businesses are required to provide “reasonable security” measures. These measures may depend on whether the injury causing incident was “foreseeable.”
What is the basic issue in all security negligence or inadequate security cases? It is whether the defendant (premise’s owner, manager, or operator) took notice of the signs of risk, responded with adequate security measures, and whether deficiency in security was a causal factor of the plaintiff’s injury.
The judgment of “adequacy” is made by a jury based on its understanding of the nature of the risk.
There are always three interconnected issues in connection with premises liability: duty, breach of duty, and foreseeable causation or proximate cause, with resulting injury to someone.
Foreseeability is simply answering this question: Did the owner know, or should he have known, that an event similar to the one which caused the injury or harm was likely to happen, and did he take reasonable steps to minimize the risk? If the answer is “yes,” then it is likely foreseeability exists.
Causation, or proximate cause, is simply defined as that which produces an event without which the injury would not have occurred. In California, for there to be causation the event must be a substantial factor in bringing about the injury.
Additionally, if enhanced security would not have deterred the incident, there may not be causation.
Remember the “But For” rule: “But for” the lack of proper lighting, this criminal attack and subsequent injury would not have occurred.
These types of security cases frequently result from injuries suffered in parking lots by patrons of big box stores and malls of all sizes and by patrons of bars, sporting events, and any other venue where there a crowds.
Retailers, however, face a third type of civil liability related to their dealing with shoplifters. This liability stems not from our failure to act or acting negligently, but rather actions of a more positive nature. The acts, or “intentional torts,” include false arrest/imprisonment, assault, malicious prosecution, defamation (libel-slander), invasion of privacy, tortious interference with employment, and tortious infliction of emotional distress.
If an allegation of inadequate security is made, and the retailer is sued, one of the issues will be how that retailer compares with other similar businesses. If you fall short in meeting the “standard”—if your security standards fall below those of your competitors in like situations—you will probably be held negligent and liable. The typical areas of comparison are
Fencing—lack of, inadequate, broken or in disrepair
Lighting—inadequate, broken, low power
Locks—key control; door peep viewers
Security policies—written, publicized, followed
CCTV—real, dummy, monitored, taped
Guards—post orders, training, screening, contract/proprietary, use of watch clocks Notices and warnings—how publicized
Knowledge of crime in area and reports kept; documentation and responses Parking lots—a subject unto themselves.
When a person is injured and sues, the object of that person’s lawsuit is to, as the courts say, “make them whole again.” How is this done? In our system, money is the means of redress; a court or jury decides how much money will adequately compensate the injured party to basically put that person in the position he was in before the injury or damage. Our tort system is really a “redistribution of wealth” system.
Damages awarded in security-related lawsuits have skyrocketed in recent years. A jury awarded a plaintiff over $7 million in 2006 when it found he had been unfairly treated by loss prevention and the company.
Awards in these cases can be made up of three parts:
• Special damages: To replace out-of-pocket expenses (e.g., lost wages).
• General damages: Awarded to make the plaintiff “whole.” This money is to compensate for pain and suffering, mental anguish, and emotional distress. If the jury is outraged by the retailer’s conduct, the higher these awards will be.
• Compensatory damages: The combination of special and general damages; they compensate the plaintiff for his injury.
• Punitive damages: Awarded when the plaintiff can establish the retailer was grossly negligent, wanton, or motivated by malice. For punitive damages to be awarded, it must be clearly shown the retailer was not merely negligent or the injury was the result of an honest error, but rather that he acted with malice, fraud, gross negligence, or oppression. Punitive damages are designed to punish and generally cannot be covered by insurance.
It should be clear by now that the retailer is vulnerable to a variety of tort claims by customers who claim injury by some act or failure to act on the part of the retailer. For this reason, it behooves the retailer to
• Avoid those acts or failures to act which, foreseeably, may lead to a person’s injury.
• When dealing with shoplifters, be sure that industry standards (such as the six steps required for a shoplifting stop) are meticulously followed.
• Have well-developed and reasonable security policies which are (a) written, (b) publicized, (c) followed, and (d) enforced.
Remember, a retailer has a duty to provide a safe shopping environment.
Preteen and Teenage Shoplifting
Experts agree that minors (juveniles and preteens) are responsible for about one-third of the shoplifting problem. If this is so, and it is, what percent of this problem is caused by the age group of 8–12 or preteen? The dilemma is no one knows for certain, but you can bet the answer is plenty! No one knows because statistics aren’t kept in any universal fashion, nor is there any central repository for such information in the country. Indeed, the last people to be made aware of this social problem are the police. Retailers are reluctant to call the police when they have a youngster in custody for stealing a candy bar or a bracelet from the fashion jewelry display. Many police jurisdictions, overworked and underfunded, have suggested their presence in such a small matter takes their attention away from more serious crimes. Stores understand this and develop policies that takes the police out of the shoplifting loop when the offender is a child.
With a youngster in tow for a small theft, the store has the option of scolding the child and sending him away or holding the child for a parent or other relative to come and take the child home. The first option is a great disservice to the parents, as well as the child. No lesson is learned when admonished by a stranger and released for a bad deed. And the parent is denied critical information about the conduct of the child. The second option often ends with at least one employee sitting with the child, sometimes for up to an hour or more until an adult comes. Or, a parent comes and is critical of the store for making a big fuss of the event. In the latter scenario, the lesson learned, for the child, is that it’s “no big deal” to get caught stealing. I am aware of times when the child claims innocence and the parent believes the child over the word of the store’s employee. Again, what lessons are learned here?
Of equal concern to our society is the not uncommon problem of adults using children to actually assist in their shoplifting efforts—from concealing goods in baby strollers, having toddlers innocently carry stolen items, to older children actively being engaged in the concealment of goods, fully knowledgeable of what’s occurring. Without question, some of these little people will grow into a life of crime, by design.
But what about children who aren’t coached or driven to learn antisocial behavior, who come from good homes, but have “sticky little fingers”? Most readers will probably agree that stealing small things, successfully, more likely than not will continue over time, and the next thing we know is the child is a young adult and still stealing. Grownup crooks typically don’t start being outlaws when they become adults.
Our hope, then, is to nip the problem in the bud. How do we do that, you ask? Following are some suggestions which we hope will effectively deal with the dilemma of youngsters who become involved in shoplifting:
• Set an example for your children about your respect for others’ property. This can be done in many ways, from little comments in a store such as “put it back on the shelf now; it’s not ours” to “Oh, my! This is Mr. Miller’s pen. I need to take it to the post office and send it to him.”
• Instill in your children a respect for others’ property. That begins with playmates’ toys and siblings’ possessions. Children must be taught about others’ property and their rights to property.
• Children must be corrected in a positive manner when caught taking others’ property, and the offender must return it in person. This “correction” or discipline goes something like this: “You’re okay, but what you did is not okay.” No berating. If the child has been discovered with merchandise, including candy, from a store, the child must be taken back to the store and must return the item with an apology. Merchants are accustomed to this and typically thank the child and instruct him not to do this again. This is good medicine.
• Ensure you know the source of everything your children possess. It’s necessary to say, “Mary, that’s a pretty necklace; where did you get it?” If she answers that her friend gave it to her, privately call her friend’s mother and inquire. The child will soon understand that any new items which show up in the room will be challenged.
• Know when your children are out “shopping,” where the shopping is taking place, and with whom. When the children return, express interest and curiosity about any package brought in and check the contents. Ask questions if there’s any doubt whatsoever.
People in their “tween” years are in a learning mode. Everyone needs to be taught the difference between right and wrong, and the parents who understand that can and will make a wonderful contribution to the children’s development. “Sticky little fingers” only need to be discovered early and washed clean—a wonderful opportunity for Mom and Dad, and such a wonderful lesson learned!
Preventing Theft of Merchandise by “Customers”
Minimizing the theft of merchandise by the public requires the implementation of various physical and procedural steps and an awareness by employees of the important role they play in preventing customer theft. This “awareness” by employees doesn’t come naturally. It must be taught.
What are the policies and practices which, if adopted, may significantly reduce theft? The following list identifies some of these relatively simple and inexpensive procedures:
• Acknowledge all customers as promptly as possible.
• If busy with a customer, acknowledge other customers either verbally (“I’ll be with you in a moment”) or visually (by a wave of the hand or a nod of the head).
• Try not to turn your back on customers.
• Try not to leave your service area unattended.
• If, as a nonsales associate, you are on the selling floor performing stocking, marking, or other functions, do not be oblivious to customers’ presence but rather acknowledge them with eye contact, smile, and ask if they are in need of assistance.
• Develop a warning system so that all employees can be alerted when the presence of potential thieves is suspected.
• Lock up expensive merchandise.
• Avoid stacking merchandise so high on counters or displays that it blocks a view of nearby areas.
• When merchandise is made up of pairs, display only one of the pair.
• Display countertop items in patterns or pyramids.
• Display hanging goods in such a manner as to make the removal of one item conspicuous. On a “T” stand, for example, hang three items on each side.
• Alternate hangers on racks containing expensive goods, like suits or expensive jackets.
• Keep counters and displays neat and orderly.
• Place telephones so sales associates can view their selling area when on the phone.
In addition to the preceding procedures, additional suggestions for merchandise protection can be grouped into four categories.
1. Protective Design: Protective design involves store layout and observation booths. A store’s layout, including the height of displays and width of aisles, can discourage or encourage shoplifters. Lighting should be designed so that there are no dark or shadowy corners. Restrooms and public telephones should be located away or separate from merchandise areas. In existing stores with restrooms immediately adjacent to displayed merchandise, those rooms should kept locked, requiring customers to obtain a key from a salesperson. In general, store layout should allow for eye coverage of most, if not all, of the selling area.
Observation booths can easily be designed into any store layout. These are booths high above the selling floor, manned by an employee often behind a two-way mirror, who has a good view of the entire store. Invisible observation booths have been an effective method of detecting theft activity.
2. Protective Devices: Protective devices include such things as two-way and convex mirrors, cameras, and electronic article surveillance tags. Some stores have found that stapling shut bags containing purchased merchandise has thwarted theft. Closed-circuit television cameras both deter some theft as well as assist in spotting theft activity. Electronic article surveillance (EAS) tags placed on expensive and easily stolen merchandise not only act as a deterrent to theft, but, if not defeated by a thief, also alert store personnel to the theft when the alarm sounds as the tagged merchandise is removed from the store. Even if tags are removed by a thief, their presence alerts to the fact that merchandise has probably been stolen. Care must be taken, however, to assure that EAS tags are either “deactivated” or removed from legitimately purchased goods. If not, honest customers will be unnecessarily detained, annoyed, and potentially create more harm than good.
3. Human Deterrents: Human deterrents involve uniformed guards or visible security officers and/or loss prevention agents, award programs, and employee education. The sight of a uniformed guard or visible security officer (VSO) often discourages both the professional and amateur shoplifter.
Award programs which reward employees who alert loss prevention to shoplifting activity can be very effective. Award programs are discussed elsewhere in this book.
Employee education programs, such as shortage awareness seminars and contests, films and videos, and reading material or posters available in break rooms, are designed to make your employees more knowledgeable and conscious of the theft problem. Remember, employees are the first and most important line of defense against external theft.
4. Psychological Deterrents: The use and type of psychological deterrents will depend on the size of the store, customer base, and the attitude of management toward these types of deterrents. For example, while shelf-edge signs displaying the message “Shoplifting is a crime and will be prosecuted” may be appropriate for a grocery or liquor store, such signs would most likely be unacceptable for a high-end specialty store. Similarly, PA announcements stating “Security is needed in area 4” may be useful in a drug store, but not in a jewelry store. Some stores have encouraged local police to park in front of the store, which arguably could discourage potential lifters from entering. Psychological deterrents may be useful and should not be discarded out of hand.
Product Tampering:—An Historical Perspective
The generally accepted definition of “product tampering” is the intentional adulteration or corruption of goods post manufacturing. It can be done to cause panic or hurt consumers, or faked to extort money from the manufacturer through product liability lawsuits. In rare cases, the merchant may become part of the lawsuit as a defendant under an allegation of negligence.
The first acknowledged case of product tampering occurred in 1978 when health officials in 18 countries were alerted that “oppressed Palestinian workers” had injected Israeli oranges at the source with liquid mercury, as part of an effort to damage the Israeli economy, of which orange exports amounted to about 10% of their economy.
Beginning in the 1980s and throughout that decade, there were numerous product tampering incidents, including one (1982) of the most remembered, which involved the death of seven persons in Chicago as the result of ingesting cyanide-poisoned Tylenol. Other incidents included
• Girl Scout cookies with needles (April 1984)
• Salmonella typhimurium bacteria in restaurant salad bars in The Dalles, Oregon, area by the Rajneesh cult (1984)
• Glico-Morinaga candy cyanide poisoning incidents in Japan (1984)
• Excedrin cyanide deaths in upstate New York (1986)
• Lipton Cup-a-Soup cyanide (1986)
• Tylenol cyanide (another case) (1986)
• Chicken fruit scandal (1989)
Based on the Tylenol case, the federal government passed the Federal Anti-Tampering Act (FATA) making it (in laymen’s terms) a federal crime to tamper with a consumer product or its labeling, conspiring to, threatening to, or claiming to have tampered or tainted consumer products for the purpose of causing illness or death or harm to the business.
Food and Drug Administration (FDA) agency regulations proscribed tamper-resistant packaging for many over-the-counter (OTC) drug products destined for retail sales. Various techniques for meeting FDA regulations covering antitampering packaging have evolved.
A recent case (2005) which received nationwide publicity that falls under the general “tampering” blanket was the “Chili-Finger” case at a San Jose, California, Wendy’s restaurant. A woman claimed to have found and bitten into a human finger in her chili while eating at Wendy’s. Subsequent investigation disclosed the woman, with her husband’s knowledge, planted the finger to file a false insurance claim. They were subsequently arrested, and the woman was sentenced to more than 12 years in prison. Wendy’s claimed to have lost $2.5 million in sales because of the adverse publicity.
While most retailers will not be named in the average product tampering civil law suit, the Wendy’s case shows the potential vulnerability to this type of case. Should such a complaint or claim of this type ever be made against a retailer, every effort should be made to preserve all possible evidence, retain the names of all witnesses and employees who could possibly have any knowledge of the incident, notify the police at once, and, if indicated, quickly involve any corporate structure that can work to control the public relations and adverse publicity aspects of the case, as well as employ professional forensic and investigative personnel.
Product Tampering and Contamination
The Turkey Crisis
I will never forget my first couple of weeks as the newly hired Director of Loss Prevention of a grocery chain. Early one morning, a week before the Thanksgiving holiday, the president of the company summoned me to his office. When I arrived, I immediately knew he wanted to discuss a matter of a serious nature. As two other senior company executives joined us, he announced we had been contacted by a local television affiliate in Tucson, Arizona. The network representative said they received a telephone call from a male caller who informed them that he had put cyanide in turkeys at our company’s supermarkets throughout the Tucson area. All eyes turned in my direction as the president asked me, “What are your recommendations?” The first thought that came to my head was to call the Federal Bureau of Investigation. I soon discovered the company did not have a written policy for handling product tampering cases or a crisis management team (CMT).
Most threats involving tampering have been shown to be hoaxes, but when a threat is received, it must be handled in a manner that assumes it to be real unless and/or until proven otherwise. Although the “turkey crisis” proved to be a hoax, the damage to the company, financially, was in the millions. The loss of public trust and lost sales dollars could not be quantified. Since the caller did not identify which stores contained contaminated products, all turkeys were removed from every store. We were aided by the news media in this product recall because they blanketed the airwaves informing the public to return any turkeys they had purchased. On the other side of the coin, it also created panic with our customers because our stores and corporate offices were undulated with calls. We paid for doctors’ visits as people thought they were sick (no contaminated turkeys were ever found), gave double refunds, and spent untold dollars in advertising to regain public confidence in our products, not to mention secured storage and eventual destruction of over 30,000 turkeys once the FBI and the Food and Drug Administration completed their investigations. The Environmental Protection Agency (EPA) was involved in the disposal of the turkeys, as it was not possible to test all the birds.
Famous Product Tampering Cases
The first reported product tampering case in the United States occurred in 1982 when seven people died after taking Tylenol capsules containing cyanide. An individual whose intent was random killings placed the tainted capsules on six different stores’ shelves in the Chicago area. This case remains unsolved, and the reward offered by Johnson & Johnson still stands today. The 1982 Tylenol case spawned further copycat cyanide tampering cases:
• In 1986, Louis Denber died from drinking cyanide-laced Lipton Chicken Noodle Cup-a-Soup.
• Excedrin tampering cases in 1986 resulted in several deaths. In June of that year, a 40-year-old Washington state woman woke at 6:00 a.m., with a headache and took two Excedrin capsules. Later, a family member found her lying on the bathroom floor, unconscious. She was rushed to the hospital, but she later died as a result of taking cyanide-laced capsules. Three days following a highly publicized recall, due to the previous death, police received a call from a woman, Stella Nickell, who suspected her husband had died from taking four Extra-Strength Excedrin capsules. His death had previously been listed as “complications from emphysema.” Subsequent testing revealed he had died of cyanide poisoning. Over a period of a few months, two more bottles of tainted Excedrin capsules were found on grocery shelves in Washington. The resulting investigation found Stella Nickell had murdered her husband and placed bottles of tainted Excedrin on store shelves to make it look like a copycat serial killer. She was convicted and sentenced to 90 years in prison, being the first person to be tried and convicted of product tampering.
• In 1991, Joseph Meling attempted to murder his wife by filling Sudafed capsules with cyanide. He also placed boxes of tainted capsules on store shelves; those capsules did kill two other people. Meling’s motive was to collect $700,000 in insurance money.
As I stated with my own product tampering example, the financial cost to a company can be devastating. In 1993 PepsiCo conducted a contest in which you were a winner if you found the words “Be young, have fun, drink Pepsi” in the bottom of a Diet Pepsi can. A retired meat salesman and his wife reportedly found a syringe in the bottom of a can when looking for the winning slogan. They gave the materials to their attorney, who then contacted the Pierce (Washington) County Health Department. After news stories aired on television, many more reports of finding objects including needles, pins, screws, a crack cocaine vial, and a bullet in Diet Pepsi cans surfaced. None of the tampering incidents were ever proven to be real; however, they cost PepsiCo over $35 million to repair the damaged caused by the tampering scare.
As I write this section, a series of food-related product tampering cases is occurring in the Northeast. In Pennsylvania, several grocery companies are experiencing issues ranging from a pin found in an onion, metal pellets found in ground beef, and a needle found in a sealed can of soup. In Maryland, a manager found two pins in a loaf of bread on the store shelf. A number of these tampering cases involve the same grocery chain.
Product Tampering:—The Public and Media Threat
Product tampering cases are a real threat, not only to the public, but also to your company’s profits and reputation. In most cases, unlike the “turkey crisis,” the news media are not notified until you make them aware. With food product tampering cases, the FBI or the Food and Drug Administration will be involved in the decision-making process when determining whether a public warning is necessary. When your store is deciding to go public, make a determination of whether the threat is real or a hoax. When the decision is made to inform the public, the possibility of encouraging copycat crimes is very high. In 1982, the FDA counted 270-suspected incidents of product tampering, of which 36 were listed as “hard core, true tamperings.” These copycat tampering threats were a direct result of the Tylenol tampering murders.
If the threat is determined to be a hoax, all agencies involved will back off, except for law enforcement agencies. You’re left with a very costly public relations nightmare. In the Pepsi product tampering crisis (described earlier), the original complaint was made on Wednesday, June 9, 1993. Seattle area television stations aired the story on Thursday, June 10. The Seattle Times reported the story that Friday morning, and another claim was made that evening. On Sunday, June 13, another claim was made by a Cleveland woman. At the end of the day on Monday, June 14, eight more claims of finding contaminated items in Diet Pepsi cans had been made. By Monday evening, the story was the number-two story on the Associated Press headlines. The number-one story was the nomination of Ruth Bader Ginsburg to the Supreme Court.
PepsiCo decided to fight the media crisis with media. The company produced video news releases that were estimated to be aired on 403 television stations and seen by 187 million viewers. The words “copycat” and “hoax” appeared in their news releases. On Thursday, June 17, Pepsi executives had a supermarket video surveillance tape of a Colorado woman putting objects into a Diet Pepsi can. Pepsi pressured the FDA to issue a statement calling the incidents a series of hoaxes. PepsiCo Inc. declared that its “needle-in-the-can scare was over.” Ads were prepared: “As America knows, those stories about Diet Pepsi were a hoax. Plain and simple, not true.” Pepsi took out full-page newspaper ads which read, “Pepsi is pleased to announce … nothing.” Several weeks later, over the July 4 holiday, Pepsi took out more ads celebrating its freedom and gave out coupons with the slogan, “Thanks, America.” As a result of PepsiCo’s aggressive handling of the media crisis, the scare ended in less 8 eight days. A very large crisis for the company was diverted by adhering to the plan developed and being upfront about the situation.
Reacting to the Product Tampering Threat at the Store
Threats can be received by mail (snail/electronic) or by telephone. Telephone threats, in my own experience, have been the most popular vehicle for delivering a product tampering scare. The following steps are recommended in the event your store receives a product tampering threat of noncompany-manufactured product:
1. Upon receiving a threat of product tampering at the store, the person receiving the call or letter must immediately inform the store manager. Do not contact any law enforcement agency. The crisis management team coordinator should contact the appropriate law enforcement agency. In most tampering cases, the Federal Bureau of Investigation is called.
2. If the threat was received over the telephone, immediately complete your company’s Bomb Threat Checklist with the associate who took the call.
3. If the threat is received in the form of a letter or note, handle the document, using gloves, at the corners only. Do not allow anyone to handle the note, except when placing it into a large envelope.
4. Instruct the associate not to discuss the matter with anyone other than the store manager or the CMT.
5. For threats received over the telephone, do not hang up before the caller is finished talking. Do not make any disparaging remarks to the caller. Do make sure you have the message properly recorded in writing, repeat it to the caller, and ask when he or she will call again.
6. If the caller states the location of a tampered product, complete the following steps:
The In-House Contaminated Manufactured Product Recovery Program
Although the contaminated product recovery program I have outlined here is directed toward the retail grocery industry, and its company-owned manufacturing plants in mind, I have found that this program may be modified to fit any retail operation. Large grocery operations maintain their own processing plants, such as bakery and dairy processing. Consumer health and satisfaction are primary concerns of any grocery company, and companies are dedicated to investigating complaints of in-house manufactured products when the possibility exists that the manufactured product may be contaminated.
The company’s crisis management team coordinator (CMTC) should direct all investigations involving alleged contaminated product. Along with the CMT, other members should include, but not be limited to, the loss prevention department, the manufacturing general manager, and an independent laboratory for the evaluation and analysis of the product in question. The following guidelines should be considered when a customer returns company-manufactured products to the store due to alleged contamination:
1. Responsibilities of the store manager or the person in charge include
2. The crisis management team coordinator’s responsibilities include
3. Loss prevention investigator responsibilities include
Examining Returned or Refunded Medicines
Retailers commonly allow customers to return previously purchased over-the-counter (OTC) medicines. It is important to have a program in place to ensure all returned medicines are inspected prior to being returned to the shelves for resale. The Consumer Healthcare Products Association has recommended the following important safety tips for inspecting returned OTC medicines and dietary supplement products:
• Check for dirt or discoloration on the package. This could be a sign of improper storage.
• Check for tape on the package. This may indicate that the product has been removed and replaced with something else.
• Check for ink spots on the package. Some individuals who replace the contents of a package with another product or even foreign material mark the tampered-with carton so they do not accidentally repurchase it themselves.
• Check for excess glue on the package. If applied by the actual supplier, the glue should be virtually unnoticeable.
• Check for loose flaps, cuts, or tears on the packaging.
• Check for stickers or strange tags.
• If the package makes a strange sound when shaken, this could be a sign that something other than the intended product is in the container.
Makeup of the Crisis Management Team (CMT)
As I stated in “The Turkey Crisis” section, the company did not have a crisis management team in place. If there had been one, certainly the process of handling the tampering threat would have gone smoother. It is crucial to have a written policy manual outlining the responses to be taken when a crisis strikes. The crisis management policy manual must be kept in each business location, in a secure location, easily retrievable by store management, and placed on your operational audit program. Every member of the CMT should have copies of the policy manual in their
Members of a crisis management team may include
• Senior Vice President of Administration
• Vice President of Operations
• Senior Vice President of Finance
A senior member of the CMT should be designated as the team coordinator. There can be only one captain of the ship, and this principle applies here. One problem we experienced was that senior members of management were accepting calls from the news media, and we were not communicating a consistent message. All communications with the news media, initial contacts with law enforcement, and crisis communication updates are the responsibility of crisis management team coordinator.
Summary
Product tampering cases, whether real or a hoax, are very demanding on a company’s resources. It is imperative that you take a proactive approach and have written procedures and actionable contingency plans in place. Have a prepared list of industry professionals to contact when a crisis strikes. Contract with a nationally recognized laboratory to analyze company-manufactured products when needed. In other words, BE PREPARED. The next “turkey crisis” is just around the corner.
Proprietary Information
Every retailer should have a written policy reflecting the rules and regulations necessary to safeguard company proprietary information. For the sake of this section, we view all company internal records and documents not specifically designed or designated for public consumption as confidential.
The risk, which must be addressed, has to do with the unauthorized disclosure of company information, and such disclosures can be in the form of the spoken word, written documents, computer or video images, or recordings.
An example of a common rule throughout business and industry as it relates to company information is “No employee may speak to a representative of the media without authorization.” That sets the tone for the need to ensure that everyone understands the WWII caution, “What you see here, what is said here, what you do here, stays here.”
Such rules and regulations are intended to apply to everyone in the general employee population. For those employees in LP, however, we feel the need for further and more detailed or specific restrictions with regard to proprietary and/or confidential information.
Suggestions for the company to assist in protecting the loss prevention manual are contained in the section “Documentation” in this book.
We now make some recommendations with respect to policies which apply singularly to LP employees, whether they are clerical personnel, agents, investigators, or executives. We suggest that a “nondisclosure agreement” be signed by all LP employees, the violation of which could subject them to immediate termination and, if appropriate, civil action. This signed agreement would prohibit the unauthorized discussion, disclosure, release, duplication, or publication of confidential, proprietary, restricted or sensitive LP information or documents, including, but not necessarily limited to
• Investigations, past or current
• Names of persons arrested for or suspected of criminal offenses
• Shrinkage (shortage) figures
• LP budgetary information, including salary information
• Proposed or planned reorganizational structure
• Proposed or pending promotions within the LP department
• Names of witnesses in current investigations
• Disciplinary action taken with regard to any LP or company employee
• Any proposed LP operations designated as “sensitive” by proper authority
• Disclosure of any confidential informants, including names or locations
While the preceding list may seem imposing, the nature of security/LP operations is such that any unauthorized disclosure of information, the sensitivity of which may or may not be known by the discloser, can adversely impact the company and/or personnel, and must be prevented. (See also “Code of Ethics for LP Personnel.”)
Prosecution vs. Release
The decision, and any conditions thereto, as to whether to prosecute, release, or conditionally release persons apprehended shoplifting is a senior management responsibility. What are some of the factors that should be considered in reaching this decision?
To begin with, any prosecution will become a matter of public record, which, if the case involves a celebrity or public figure, will also receive publicity. Additionally, unless the suspect pleads guilty, there will be the requirement for the arresting persons and perhaps other store witnesses to spend time testifying in court. In the case of a small store, such required absence of employees may create a major interruption to normal business activities and become the deciding factor in reaching a decision to prosecute.
Local prosecutorial policies of the prosecuting authority (normally the district attorney) and police resources and response time may well be appropriate for calculating into the decision process.
Some retailers are repelled by the idea of letting a thief get off without consequence, and their decision to prosecute is emotional rather than a more reasoned one.
The use of a conditional release should not be overlooked; it is considered by some as a compromise between a simple release and prosecution. (See “Conditional (Controlled) Release” in this book.)
Whatever decision is made, and any conditions connected with that decision, such as what we consider the infamous rule adopted by a major retailer mandating release if the theft is a first-time offense involving merchandise valued under $25 (and then published in 2006), it is essential that it must be applied consistently. Any selective release or prosecution outside company-stated policy opens up the company to charges of discrimination.
Note: The less publicity given to apprehension and prosecution policies, the better. Public awareness, for example, that first-time offenders who shoplift under a specified dollar amount will be automatically released can, in my opinion, do nothing but increase theft activity.
Public Restrooms
Public restrooms in stores can present a number of potential problems, including unauthorized entry, illicit sexual activity, and the potential for child molestation.
I contacted as this section was being written about a case in which a male store janitorial employee entered an occupied ladies restroom and violated the customer’s privacy and allegedly committed a sexual assault. The issues in this case were whether the store had adequate security, and/or if it had employed more loss prevention personnel and/or CCTVs outside the restroom entrances, would this incident have occurred? Since this book may be published while this case is still in litigation, we will not comment further on the merits of either the plaintiff’s or defendant’s case.
Public restrooms are known as places for engaging in illicit sexual activities, and rest-rooms in stores are no exception. This activity has the potential for creating several problems, among which are
• The offense taken by customers encountering this activity.
• The potential that a customer will be approached for illicit activity in error.
• The potential for the exposure of children to this activity.
• The store getting a reputation as a place known for this illegal activity and thus being avoided by customers.
• The potential for serious crimes such as rape or murder occurring in restrooms; I once testified in a case involving the murder of a young girl who was taken by a man into a restroom to commit the crime.
Stores, particularly the larger ones, must be alert to the potential for crime in their restrooms and develop a policy on how persons caught engaging in such activity will be dealt with. Signs indicating that restrooms are routinely patrolled by security personnel and law violations will be prosecuted are perfectly proper and may discourage those with improper reasons for entry.
Additionally, stores should establish policies and procedures to cover how janitorial and other maintenance will be performed in restrooms to avoid opposite sex personnel entering restrooms and creating embarrassment and privacy invasion of those legitimately occupying the restroom.