Lesson 9
Manage Security and Privacy
This lesson covers built-in macOS security features and how to manage and troubleshoot them.
Reference 9.1 Password Security
There are several ways to authenticate, or to verify your identity. In macOS, you can provide your user name and password to authenticate. If your Mac has a Touch Bar and you set up Touch ID, you can use your fingerprint instead of typing when you’re asked for your password as long as you’re logged in. Read Apple Support article HT207054, “Use Touch ID on your Mac” for more information.
Passwords You Use in macOS
You use several passwords to secure your Mac. You set an account password, and you can set a firmware password and resource and keychain passwords.
Users might use several password types:
![]() Each local user account has attributes that define the account. Users enter their local account password (an account attribute) to log in to their Mac. For security reasons, a user’s local-account password is encrypted and stored in the user account record.
Each local user account has attributes that define the account. Users enter their local account password (an account attribute) to log in to their Mac. For security reasons, a user’s local-account password is encrypted and stored in the user account record.
![]() Users might have an Apple ID and password. They use these to authorize Apple services, including iCloud, iTunes, and the App Store.
Users might have an Apple ID and password. They use these to authorize Apple services, including iCloud, iTunes, and the App Store.
![]() With the exception of a user account password, macOS protects authentication assets in encrypted keychain files. Each keychain file is encrypted with a keychain password. macOS keeps keychain passwords synchronized with a user’s local account password. You can maintain unique keychain passwords separate from an account password too. Maintaining synchronization between a user’s keychain password and account password is covered in Lesson 10, “Manage Password Changes.”
With the exception of a user account password, macOS protects authentication assets in encrypted keychain files. Each keychain file is encrypted with a keychain password. macOS keeps keychain passwords synchronized with a user’s local account password. You can maintain unique keychain passwords separate from an account password too. Maintaining synchronization between a user’s keychain password and account password is covered in Lesson 10, “Manage Password Changes.”
![]() Resource passwords are required by most macOS services (for example, email, websites, file servers, apps, and encrypted disk images). Many resource passwords are saved for you by Keychain Access.
Resource passwords are required by most macOS services (for example, email, websites, file servers, apps, and encrypted disk images). Many resource passwords are saved for you by Keychain Access.
![]() A firmware password prevents you from starting up a Mac from any disk other than your designated startup disk. As a result, it also blocks you from using most startup key combinations. For example, if you set a firmware password, an unauthorized user can’t hold down the Option key during startup to select an alternate operating system, bypassing your secure startup disk. Setting a firmware password is covered in Lesson 10.
A firmware password prevents you from starting up a Mac from any disk other than your designated startup disk. As a result, it also blocks you from using most startup key combinations. For example, if you set a firmware password, an unauthorized user can’t hold down the Option key during startup to select an alternate operating system, bypassing your secure startup disk. Setting a firmware password is covered in Lesson 10.
Keychain
macOS keeps your resource passwords, certificates, keys, website forms, and secure notes in encrypted storage called keychains. When you allow macOS to remember a password or other sensitive items, it saves them to a keychain. Your login password is not saved to a keychain.
macOS encrypts keychain files. They are impenetrable unless you know the keychain password. If you forget a keychain password, you lose the file contents forever.
You can use Keychain Access to view and modify most keychain items. You can use Launchpad or Spotlight to open Keychain Access, and it’s in /Applications/Utilities. You can also create and delete keychain files, and change keychain settings and passwords. You can manage web-specific keychain items from Safari preferences.
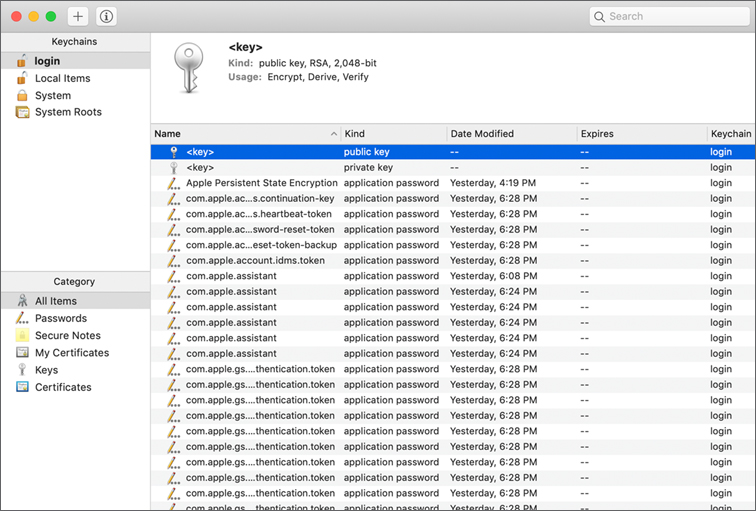
Local Keychain Files
Keychain files are stored throughout macOS for different users and resources. Here are some examples:
![]() /Users/username/Library/Keychains/login.keychain—When you use Keychain Access, this keychain name is “login.” macOS creates every standard or administrator user with a single login keychain. As a default, the password for this keychain matches the user’s account password, so this keychain is automatically unlocked and available when the user logs in. If the user’s account password doesn’t match the keychain password when the user logs in, macOS renames the keychain with a filename that begins with “login_renamed_” followed by a number. For example, the first time the password mismatch happens, the new filename is login_renamed_1.keychain-db. macOS then creates a new login keychain with a password that matches the user’s password.
/Users/username/Library/Keychains/login.keychain—When you use Keychain Access, this keychain name is “login.” macOS creates every standard or administrator user with a single login keychain. As a default, the password for this keychain matches the user’s account password, so this keychain is automatically unlocked and available when the user logs in. If the user’s account password doesn’t match the keychain password when the user logs in, macOS renames the keychain with a filename that begins with “login_renamed_” followed by a number. For example, the first time the password mismatch happens, the new filename is login_renamed_1.keychain-db. macOS then creates a new login keychain with a password that matches the user’s password.
![]() /Users/username/Library/Keychains/others.keychain—You can create more keychains if you want to segregate your authentication assets. For example, you can keep your default login keychain for items that require less security and create a more secure keychain that doesn’t automatically unlock for items that require a lot of security.
/Users/username/Library/Keychains/others.keychain—You can create more keychains if you want to segregate your authentication assets. For example, you can keep your default login keychain for items that require less security and create a more secure keychain that doesn’t automatically unlock for items that require a lot of security.
![]() /Users/username/Library/Keychains/UUID/—This keychain folder is created for every user account and contains the keychain database used by iCloud Keychain. If iCloud Keychain isn’t enabled, the database is still created. When iCloud Keychain isn’t enabled, this keychain folder appears with the name Local Items in Keychain Access. If iCloud Keychain is enabled, this keychain folder appears with the name iCloud in Keychain Access. The folder’s universally unique identifier (UUID) doesn’t match a user’s local account UUID, but the folder is associated with the user because it’s in the user’s home folder.
/Users/username/Library/Keychains/UUID/—This keychain folder is created for every user account and contains the keychain database used by iCloud Keychain. If iCloud Keychain isn’t enabled, the database is still created. When iCloud Keychain isn’t enabled, this keychain folder appears with the name Local Items in Keychain Access. If iCloud Keychain is enabled, this keychain folder appears with the name iCloud in Keychain Access. The folder’s universally unique identifier (UUID) doesn’t match a user’s local account UUID, but the folder is associated with the user because it’s in the user’s home folder.
![]() /Library/Keychains/System.keychain—This keychain appears with the name System in Keychain Access. This keychain maintains authentication assets that aren’t user specific. Items stored here include Wi-Fi wireless network passwords, 802.1X network passwords or certificates, and local Kerberos (a network authentication protocol) support items. Although all users benefit from this keychain, only administrator users can make changes to it.
/Library/Keychains/System.keychain—This keychain appears with the name System in Keychain Access. This keychain maintains authentication assets that aren’t user specific. Items stored here include Wi-Fi wireless network passwords, 802.1X network passwords or certificates, and local Kerberos (a network authentication protocol) support items. Although all users benefit from this keychain, only administrator users can make changes to it.
![]() /System/Library/Keychains/—Most of the items in this folder don’t appear in Keychain Access by default. The one item you will see in Keychain Access from this folder is System Roots. This keychain stores root certificates that are used to identify trusted network services. You can’t modify these items.
/System/Library/Keychains/—Most of the items in this folder don’t appear in Keychain Access by default. The one item you will see in Keychain Access from this folder is System Roots. This keychain stores root certificates that are used to identify trusted network services. You can’t modify these items.
Apple and third-party developers might create additional keychains for securely storing data. You can find keychain files with seemingly random names throughout macOS. Leave these files alone unless you’re instructed by a trusted source to remove or modify them to resolve an issue.
Reference 9.2 Manage Secrets in Keychain
To manage keychain items, including saved passwords, open Keychain Access. The default selection shows a user’s login keychain contents. Select another keychain from the list to view its contents.

Double-click a keychain item to view its attributes. If the item is a password, select “Show password” to see the saved password. You’re often prompted to provide a keychain password.
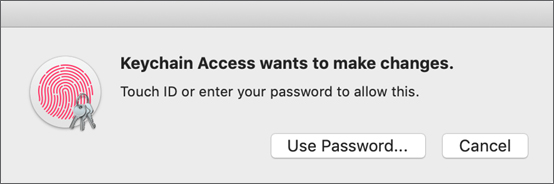
This ensures that only a keychain owner can make changes. After you authenticate, you can change attributes in the keychain item dialog. Click the Access Control button to adjust app access for a selected item.
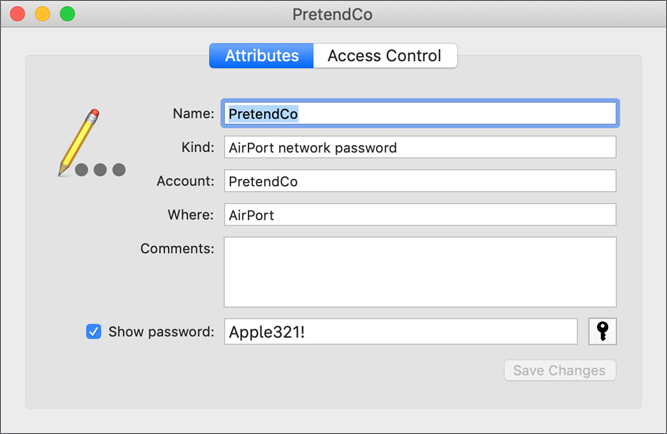
iCloud authentication mechanisms create keychain items that you might not recognize. Many of these are certificates or keys, which you shouldn’t modify.
To search through keychain items in Keychain Access, select a keychain category on the left, or search for an item with Spotlight in the upper-right corner of the toolbar.
You can store secret text in keychains. In Keychain Access, choose File > New Secure Note Item to create a new secure note.
Manage Keychain Items with Safari
When you use Safari, you probably interact with keychains. Safari AutoFill prompts you to start saving web-form information and site passwords. It also suggests secure passwords for you to use for websites and asks if you’d like to save credit card information.
If iCloud Keychain isn’t enabled (iCloud Keychain is covered in Reference 9.3, “Use iCloud Keychain”), Safari saves secret information to the Local Items keychain.
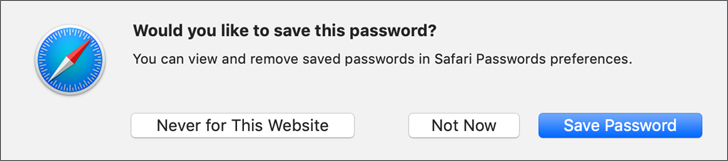
If iCloud Keychain is enabled, Safari saves secret information to iCloud Keychain.
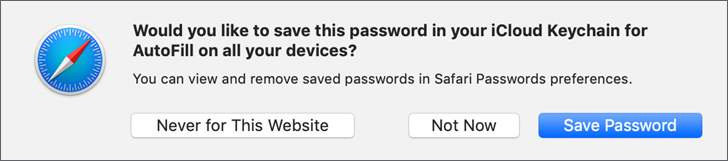
When you revisit a site or navigate to a new site with similar form information, Safari AutoFill automatically fills in information for you, as long as the keychain file is unlocked. If allowed, Safari also pulls information from your contact information.
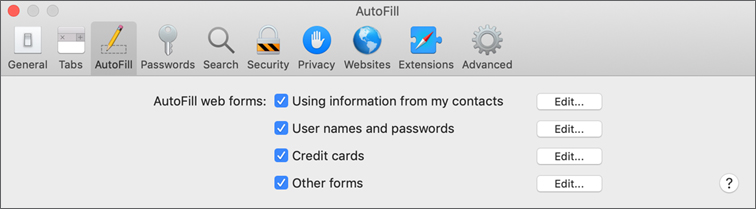
To manage Safari AutoFill settings, choose Safari > Preferences, and click the AutoFill button. The settings enable you to set which items are automatically saved and filled. Edit buttons enable you to manage items such as website passwords and saved credit cards.
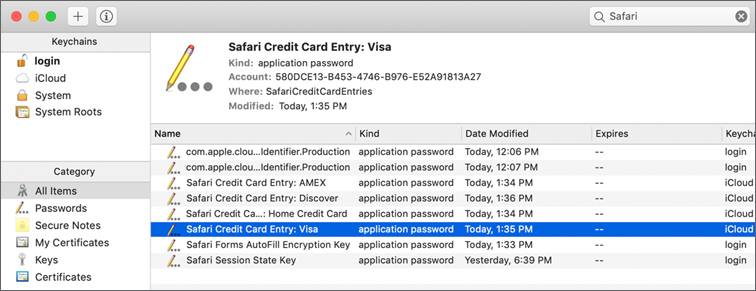
With the exception of your contact information, which is stored in Contacts, Safari AutoFill data is securely stored in your iCloud or your Local Items keychain. Click the Help button (question mark) in the AutoFill pane of Safari preferences to read more about AutoFill items. You can view and manage AutoFill items from Keychain Access.
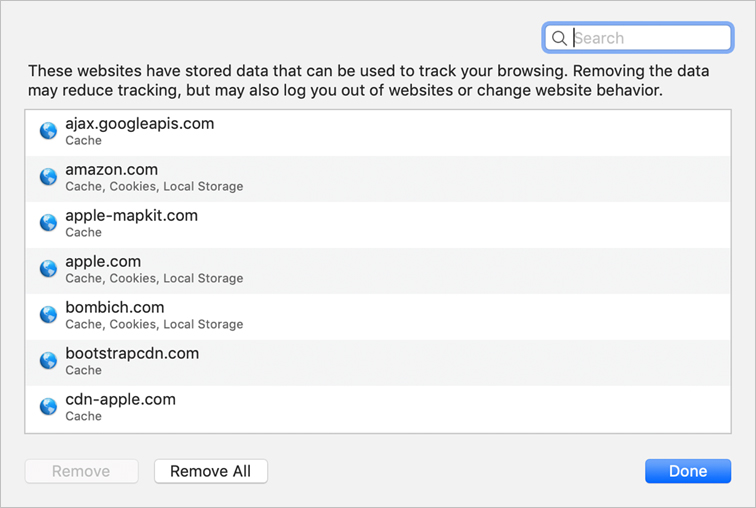
Some websites remember your authentication inside a cookie, so you might not see an entry in a keychain file for every website that automatically remembers your account. Open Safari preferences and click the Privacy button to view and delete cookies.
Reference 9.3 Use iCloud Keychain
iCloud Keychain shares your commonly used secrets between your Apple devices through iCloud. iCloud includes strong personal security technology, as detailed in Apple Support article HT202303, “iCloud security overview.”
When you need to create a new password for a website, Safari suggests a unique, hard-to-guess password and saves it in your iCloud Keychain. Safari fills it in automatically the next time you need to sign in, so you don’t have to remember it or enter it on any of your devices. Use iCloud Keychain to keep information safe. Read Apple Support article HT203783, “Get help with iCloud Keychain,” for more information.
If you enable iCloud Keychain, the Local Items keychain is renamed iCloud. Contents in your iCloud Keychain are also stored on the Apple iCloud servers and pushed to your other configured Apple devices. iCloud Keychain provides a secure way to access your secrets from any of your Apple devices that are connected to the Internet.
If you disable it, your iCloud Keychain is renamed Local Items, and you can choose to keep secret items locally.
Use your login keychain password to access your Local Items keychain or your iCloud Keychain. When you change your login keychain password, macOS applies the change to your Local Items keychain or your iCloud Keychain. For this reason, Keychain Access doesn’t allow you to change your Local Items keychain or your iCloud Keychain password.
Two-Factor Authentication for Apple ID
With two-factor authentication, your account can be accessed only on devices you trust, like your iPhone, iPad, or Mac. When you sign in to a new device for the first time, you must provide two pieces of information—your Apple ID password and the six-digit verification code that’s displayed on your trusted devices. When you enter the code, you verify that you trust the new device. For example, if you have an iPhone and sign in to your account for the first time on a newly purchased Mac, you are prompted to enter your password and the verification code that’s automatically displayed on your devices that are signed in to the same Apple ID. You can have the verification code sent to trusted phone numbers as well.
Because your password alone is no longer enough to access your account, two-factor authentication dramatically improves the security of your Apple ID and all the personal information you store with Apple.
After you sign in, you won’t be asked for a verification code on that device again unless you sign out completely, erase the device, or need to change your password for security reasons. When you sign in on the web at www.icloud.com, you can choose to trust your browser so that you won’t be asked for a verification code the next time you sign in from that Mac.
For more information about two-factor authentication, see Apple Support articles HT204915, “Two-factor authentication for Apple ID,” HT205075, “Availability of two-factor authentication for Apple ID,” and HT207198, “Switch from two-step verification to two-factor authentication.”
iCloud Security Code
iCloud Keychain is enabled by default only when you use an Apple ID that has two-factor authentication turned on. Alternatively, when you first enable iCloud Keychain using an Apple ID without two-factor authentication, macOS prompts you to enter your iCloud Security Code. Or if you don’t have one yet, macOS prompts you to create an iCloud Security Code that is used to further protect your secrets.
The iCloud Security Code is a separate security technology. When you enable iCloud Keychain with an Apple ID that doesn’t have two-factor authentication, macOS prompts you to select one of the following iCloud Security Code options:
![]() Code plus verification is the default iCloud Security Code. It’s a simple code paired with Short Message Service (SMS) text message verification. You must select a six-digit numeric code and provide a phone number that can receive SMS text messages for further verification.
Code plus verification is the default iCloud Security Code. It’s a simple code paired with Short Message Service (SMS) text message verification. You must select a six-digit numeric code and provide a phone number that can receive SMS text messages for further verification.
![]() You can create a code up to 32 characters long, but you must keep track of this code.
You can create a code up to 32 characters long, but you must keep track of this code.
![]() You can choose to have a random complex (32-character) iCloud Security Code generated and paired with an SMS text message verification. You must keep track of the code. You provide a phone number that can receive SMS text messages for verification.
You can choose to have a random complex (32-character) iCloud Security Code generated and paired with an SMS text message verification. You must keep track of the code. You provide a phone number that can receive SMS text messages for verification.
![]() You can opt to not create a security code. If you don’t create a security code, setting up iCloud Keychain on a new device will require your approval from a different device.
You can opt to not create a security code. If you don’t create a security code, setting up iCloud Keychain on a new device will require your approval from a different device.
Note ![]()
If you enter the wrong iCloud Security Code too many times when using iCloud Keychain, your iCloud Keychain is disabled on that device, and your keychain in iCloud is deleted. Read Apple Support article HT202755, “If you enter your iCloud Security Code incorrectly too many times” for more information.
If you sign in to another Apple device using an Apple ID with two-factor authentication, iCloud Keychain is automatically enabled. For Apple IDs without two-factor authentication, you can grant access for additional devices with a device authorization mechanism. Any device configured with the iCloud Keychain service is a trusted device. Any trusted device can be used to verify additional devices for iCloud Keychain.
For example, after you set up iCloud Keychain on your Mac and try to enable it on a different Mac, macOS will ask if you want to allow this.
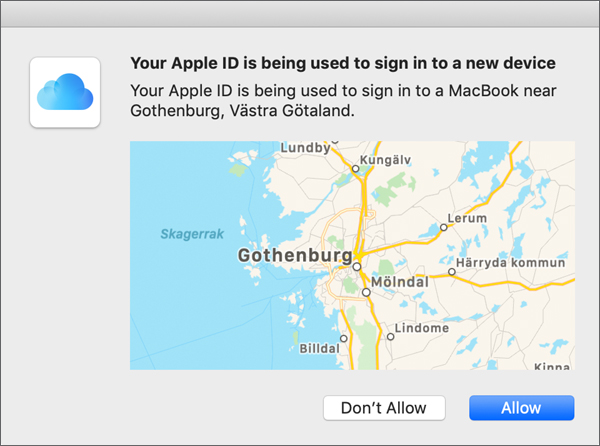
After you click Allow you’ll see a randomly generated six-digit code. Continuing the example, enter this verification code on your second Mac and then click Done.
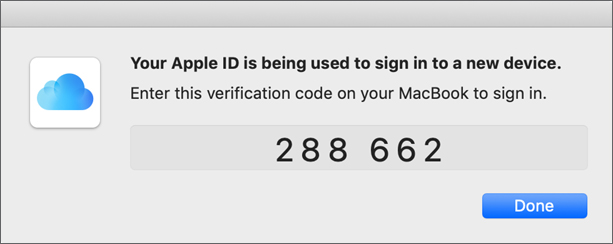
If you don’t have two-factor authentication enabled, and you set up an iCloud Security Code instead, you can use the iCloud Security Code for verification instead of device-based authorization.
Reference 9.4 User-Approved MDM
“User-Approved MDM” enrollment was introduced in macOS High Sierra 10.13.2. This enrollment type is required only if you want to manage certain security-sensitive settings that include:
![]() Kernel extension loading policy
Kernel extension loading policy
![]() Autonomous single-app mode (often used in education for testing apps, and for kiosk apps)
Autonomous single-app mode (often used in education for testing apps, and for kiosk apps)
![]() User consent for data access
User consent for data access
You can already manage security-sensitive settings on devices whose MDM enrollment is done through automatic device enrollment such as with Apple Business Manager or Apple School Manager, so User-Approved MDM is unnecessary for these devices.
You can still manage settings that aren’t security sensitive for devices that are enrolled in MDM without the User-Approved option.
Here are ways a Mac gets enrolled with User-Approved MDM:
![]() If you use Apple Business Manager or Apple School Manager to automatically enroll your Mac in an MDM solution, its enrollment is equivalent to User-Approved.
If you use Apple Business Manager or Apple School Manager to automatically enroll your Mac in an MDM solution, its enrollment is equivalent to User-Approved.
![]() If a Mac was enrolled in non-User-Approved MDM before it was updated to macOS 10.13.4 or newer, its enrollment is converted to User-Approved when installing macOS 10.13.4 or newer.
If a Mac was enrolled in non-User-Approved MDM before it was updated to macOS 10.13.4 or newer, its enrollment is converted to User-Approved when installing macOS 10.13.4 or newer.
![]() If you download or email yourself an enrollment profile, then double-click the enrollment profile, you must follow the prompts in System Preferences to enroll in MDM.
If you download or email yourself an enrollment profile, then double-click the enrollment profile, you must follow the prompts in System Preferences to enroll in MDM.
![]() If you use a screen sharing solution to enroll a Mac in MDM, synthetic input detection prevents User-Approved enrollment.
If you use a screen sharing solution to enroll a Mac in MDM, synthetic input detection prevents User-Approved enrollment.
![]() If you use automation to enroll a Mac in MDM, it won’t result in User-Approved enrollment.
If you use automation to enroll a Mac in MDM, it won’t result in User-Approved enrollment.
If your Mac was enrolled in MDM without user consent in macOS 10.13.4 or later, its enrollment will not be User-Approved.
To manage security-sensitive settings, you can approve your enrollment and attain User-Approved enrollment with the following steps:
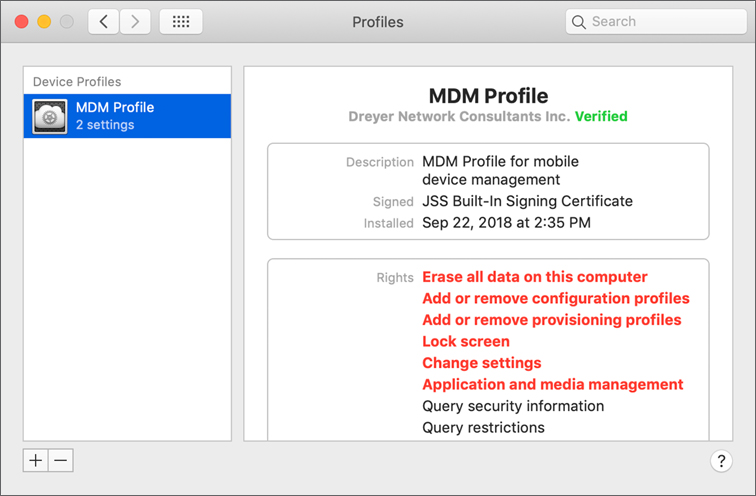
Choose Apple menu > System Preferences, and then click Profiles.
Select your enrollment profile. It has a yellow badge:
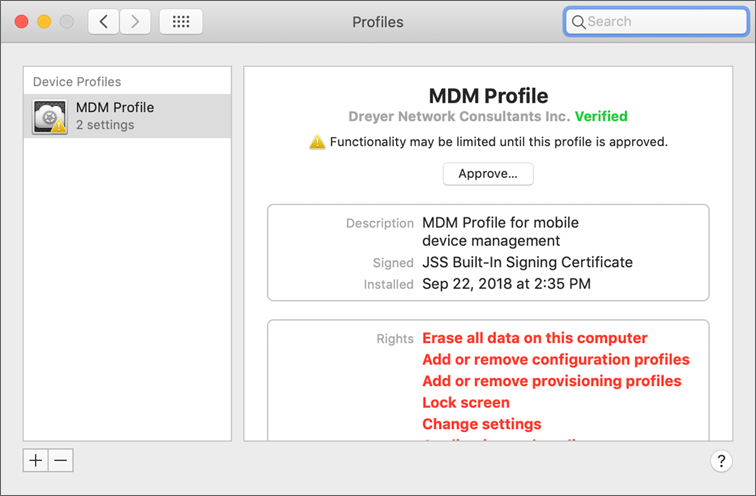
Click the Approve button on the right, and then follow the onscreen instructions.
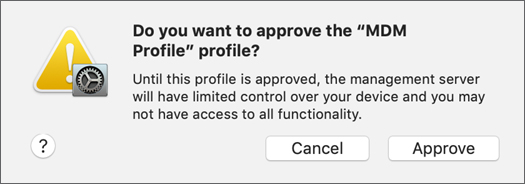
The badge is removed in Profiles preferences, and you have User-Approved MDM enrollment.
For more information about User-Approved enrollment, read HT208019, “Prepare for changes to kernel extensions in macOS High Sierra.”
Reference 9.5 Manage System-wide Security
In addition to account passwords and keychain items, there are macOS-wide security preferences that affect all users on a Mac. Several of these preferences are disabled by default.
Security & Privacy: General Settings
Security & Privacy preferences is a combination of systemwide settings and personal settings that enable you manage macOS security features. You must be an administrator user to make changes to settings that might affect systemwide security or other users. In Security & Privacy preferences, systemwide security settings are dimmed when the lock is locked. The lock indicates that administrator user authentication is required. Personal security settings are always available.
In addition to using Users & Groups preferences, users can change their passwords in the General settings pane.
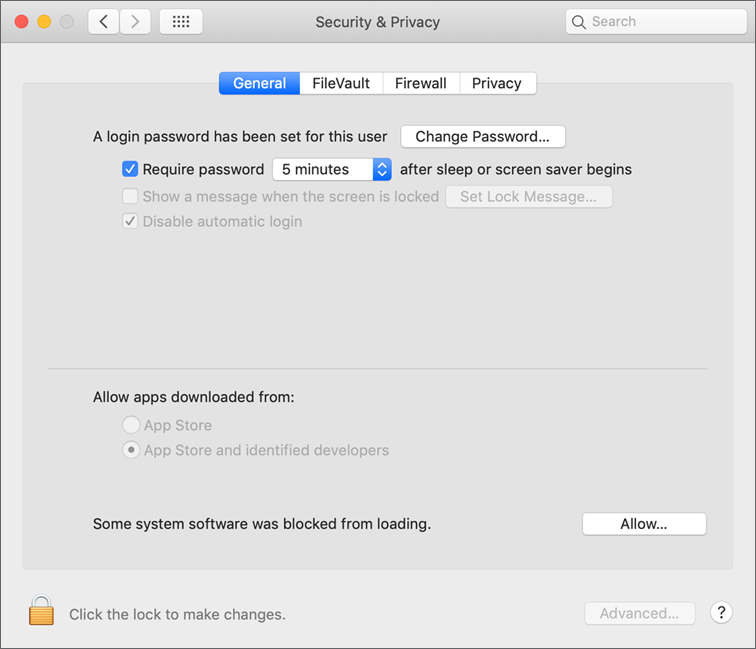
You can choose to require a password to wake a Mac from sleep or screen saver mode and to define a delay before this requirement sets in. Both standard and administrator users can set this for their accounts. If you want to set this for every account from Security & Privacy preferences, consider using a configuration profile.
Administrators can also configure a custom message to show at the login window or when the screen is locked. When setting the message, you can press Option-Return to force a new line. You can have up to three lines of text.
Administrators can disable automatic login for all accounts. This setting is required on Mac computers with FileVault enabled.
If you’re logged in with your iCloud account, and it’s associated with an Apple Watch, this option is displayed: “Allow your Apple Watch to unlock your Mac.” For more information. see support article HT206995, “How to unlock your Mac with your Apple Watch.”
macOS enables you to restrict untrusted apps that are downloaded from the Internet from being opened. Near the bottom of the General pane you can configure the sources of apps that macOS allows you to run. Lesson 18, “Install Apps,” covers this topic in greater detail.
Security & Privacy: Advanced Settings
Advanced security settings show after you unlock Security & Privacy preferences and click the Advanced button in the lower-right corner of the pane.
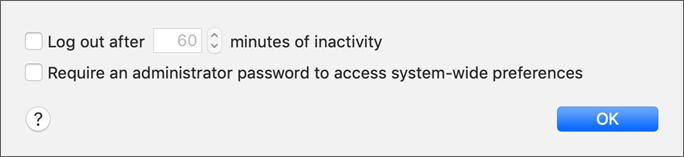
You can choose to require users to automatically log out of accounts after a certain amount of inactivity, and to require an administrator password to access systemwide preferences.
Security & Privacy: FileVault Settings
This pane is where you enable and configure FileVault. Lesson 12, “Manage FileVault,” covers FileVault in greater detail.
Security & Privacy: Firewall Settings
This pane is where you enable and configure personal network firewall settings. Lesson 25, “Manage Host Sharing and Personal Firewall,” covers this topic in greater detail.
Use Find My Mac
Find My Mac helps you locate a lost Mac by enabling you to remotely access the Mac computer’s Location Services. In addition to locating a lost Mac, Find My Mac enables you to remotely lock, erase, and display a message on a Mac.
You can use iCloud to locate a lost iPhone, iPod touch, or iPad. This service is collectively known as Find My iPhone, which is also the name of a free iOS app that you can use to find Mac computers and iOS devices.
Find My Mac prerequisites:
![]() The Mac must have an active Internet connection.
The Mac must have an active Internet connection.
![]() The Mac must have Location Services enabled. If you don’t enable Location Services during Setup Assistant or from Security & Privacy preferences, you’re prompted to when you turn on Find My Mac.
The Mac must have Location Services enabled. If you don’t enable Location Services during Setup Assistant or from Security & Privacy preferences, you’re prompted to when you turn on Find My Mac.
![]() You must configure the Mac to use iCloud, with Find My Mac enabled. You can configure or disable Find My Mac any time from iCloud preferences. Although multiple users can sign in to most iCloud services on a single Mac, only one iCloud account per device can be enabled for Find My Mac.
You must configure the Mac to use iCloud, with Find My Mac enabled. You can configure or disable Find My Mac any time from iCloud preferences. Although multiple users can sign in to most iCloud services on a single Mac, only one iCloud account per device can be enabled for Find My Mac.

After you configure Find My Mac, access iCloud at www.icloud.com to look for a lost device from another Mac or PC. Log in with the appropriate iCloud account, and select Find iPhone on the iCloud homepage.
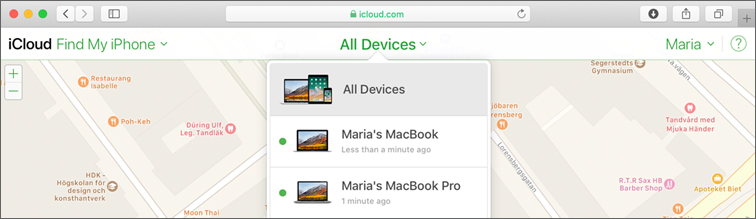
If Find My iPhone is successful, iCloud displays a map with the relative location of all the devices configured with the iCloud account. When you select a located device on the map, you can play a sound on, lock, or erase the device. You can also see the power status in the upper-right corner of the device view.
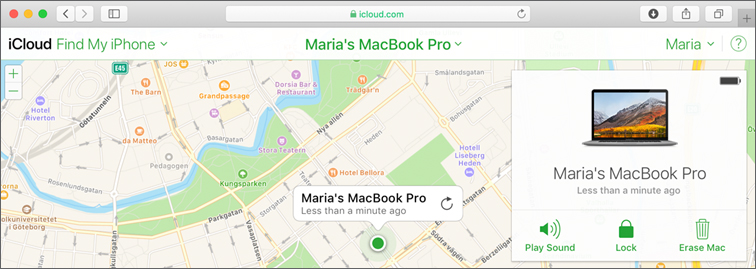
When you issue a remote lock or erase, you first see a prompt to confirm that you want to lock or erase.
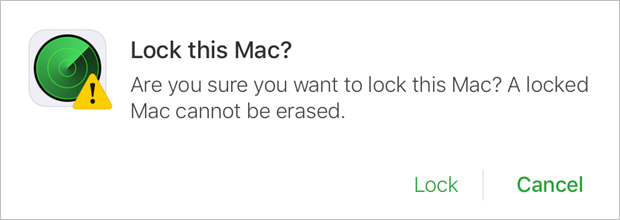
![]() For a remote lock, the prompt is “Lock this Mac? Are you sure you want to lock this Mac? A locked Mac cannot be erased.” This is because a locked Mac won’t receive a remote erase command until the Mac is unlocked again. Before you take action, decide whether you want to send a remote lock command or a remote erase command.
For a remote lock, the prompt is “Lock this Mac? Are you sure you want to lock this Mac? A locked Mac cannot be erased.” This is because a locked Mac won’t receive a remote erase command until the Mac is unlocked again. Before you take action, decide whether you want to send a remote lock command or a remote erase command.
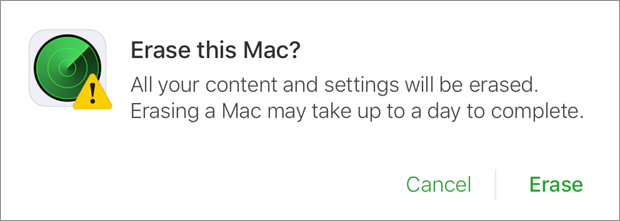
![]() For a remote erase, the prompt is “Erase this Mac? All your content and settings will be erased. Erasing a Mac may take up to a day to complete.” After you click Erase, to continue with the remote erase you must provide your Apple ID credentials and then use two-step or two-factor authentication to prove your identity.
For a remote erase, the prompt is “Erase this Mac? All your content and settings will be erased. Erasing a Mac may take up to a day to complete.” After you click Erase, to continue with the remote erase you must provide your Apple ID credentials and then use two-step or two-factor authentication to prove your identity.
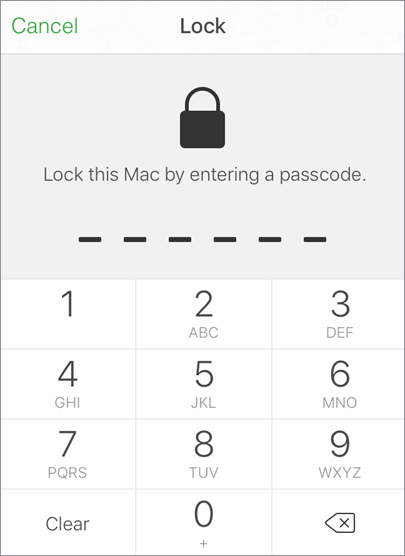
To continue with the remote lock or erase, you must provide a six-digit passcode (also referred to as a PIN), and then verify the passcode.
After you enter and verify the passcode, you can enter a message that will be displayed on the Mac after it has been locked or erased.
Note ![]()
MDM solutions provide remote lock and erase (also called wipe) operations similar to the remote lock and erase operations that Find My iPhone provides, but MDM solutions do not require Location Services to be enabled.
Once a Mac receives a command for a remote lock or a remote erase, the Mac immediately restarts. Upon restart the Mac prompts you for the passcode with the message, “Enter your system lock PIN code to unlock this Mac.” The passcode protects the contents of the Mac from unauthorized users. Without the correct passcode, an unauthorized user can’t access any internal disk on the Mac. Also, without the correct passcode, an unauthorized user can’t start the Mac in target disk mode (covered in Lesson 11, “Manage File Systems and Storage”) or otherwise modify how the Mac starts up. The remote lock function works even while the Mac is using a firmware password, which is covered in Reference 10.4, “Secure Mac Startup.”
For the remote erase operation, upon restart a Mac removes all user data. Additionally, a Mac that’s protected with FileVault deletes the encryption keys needed to decrypt the startup disk. This is called an instant wipe, and it makes the data on your startup disk completely inaccessible. See Lesson 12, “Manage FileVault,” for more information about FileVault.
When you enable Find My Mac, macOS automatically enables the guest account for local login. It’s a trap for unauthorized users. The intent is to help a stolen Mac become locked when found. The unauthorized user can choose Guest User as a login option at startup or wakeup, which allows limited access to macOS. If the Mac has the default settings, the unauthorized user is allowed only to select a Wi-Fi network and use Safari. This enables the lost Mac to get back online so that the owner can use Find My Mac to locate it.
Disabling Find My Mac doesn’t automatically disable the guest account. If you disable Find My Mac and you don’t want the guest user account to be enabled, you have to disable it manually in Users & Groups preferences.
Note
If you set a firmware password on your Mac before it was lost, then erase it and later find it, you may need to take your Mac to an authorized repair center to unlock it before you can use it again.
Reference 9.6 Manage User Privacy
macOS includes privacy settings that are enabled by default for every user. These settings might prevent functionality that a user would like. You can edit these settings to allow access to private information. macOS Mojave introduces a privacy database, which stores decisions a user makes about whether apps may access personal data. Read the following section to find out more about how you edit settings to allow access to private information.
Find out more about Apple’s deep commitment to personal privacy at www.apple.com/privacy/.
More information on managing privacy for Siri and Spotlight is in Lesson 16, “Use Metadata, Spotlight, and Siri.”
Security & Privacy: Privacy Settings
Administrator and standard users can manage service access to personal information in the Privacy pane.
When an administrator specifies a privacy selection (enabled or disabled), standard users can’t change it. For example, if an administrator disables the ability for Weather to access Location Services, it remains disabled for all standard users.
When a new app requests information to certain classes of data, macOS asks you for permission. For example, when you make a new event and specify a location for the event, Calendar asks you to allow access to Location Services to provide you with improved location searches and travel time estimates.
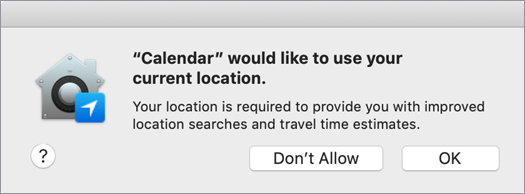
If you click OK, the app or service is added to your privacy database for the appropriate class of data. If you click Don’t Allow, the app or service won’t have permission to the class of data, and it won’t ask for permission again unless you reset the privacy database. For more information about resetting the privacy database, see the man page for tccutil.
You can use your MDM solution to apply a Privacy Preferences Policy Control payload with a configuration profile if each of the following conditions are met:
![]() Your Mac has macOS Mojave or newer.
Your Mac has macOS Mojave or newer.
![]() Your Mac has User-Approved MDM.
Your Mac has User-Approved MDM.
![]() Your MDM solution supports the Privacy Preferences Policy Control payload.
Your MDM solution supports the Privacy Preferences Policy Control payload.
If your MDM solution installs a Privacy Preferences Policy Control payload on a Mac with macOS High Sierra, you might have to reinstall the configuration profile after you upgrade the Mac to macOS Mojave for the settings to take effect. For more information about using this payload, see Apple Support article HT209028, “Prepare your institution for iOS 12 or macOS Mojave” and the Configuration Profile Reference at https://developer.apple.com/enterprise/documentation/Configuration-Profile-Reference.pdf.
From the Privacy pane, you can view apps or services that have asked for information and choose to allow or disallow further attempts by them to collect information. The left column in the Privacy pane displays a list of classes of data related to information that apps and services might request.
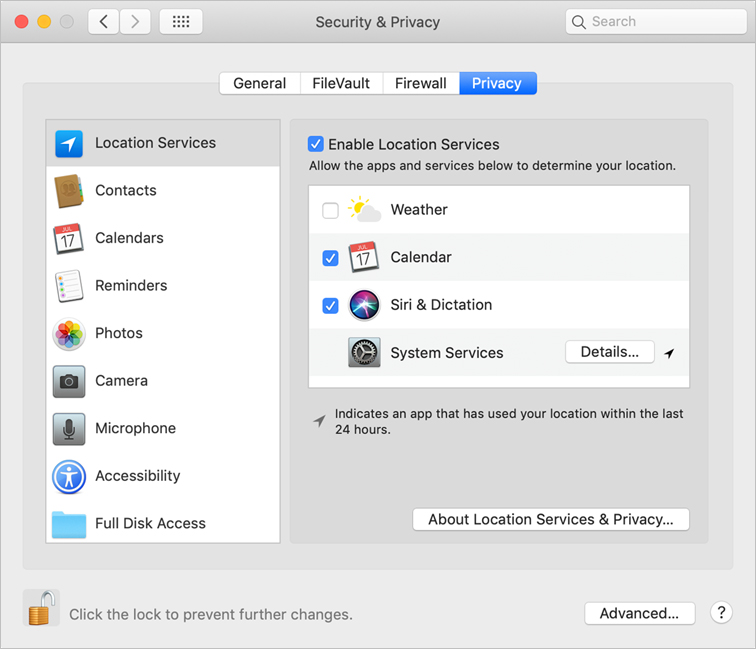
Each class of data on the left has a list on the right of apps and services that can access that class of data. Some settings in the Privacy pane apply to all users on your Mac. Other settings—for example, Contacts, Calendars, Reminders, and Photos settings—are limited to the currently logged-in user.
Select a class of data on the left, and then deselect an app or service on the right to prevent it from accessing the class of data. For some categories such as Accessibility and Full Disk Access, you can click Add (+) and add an app to the list of apps that can access the category.
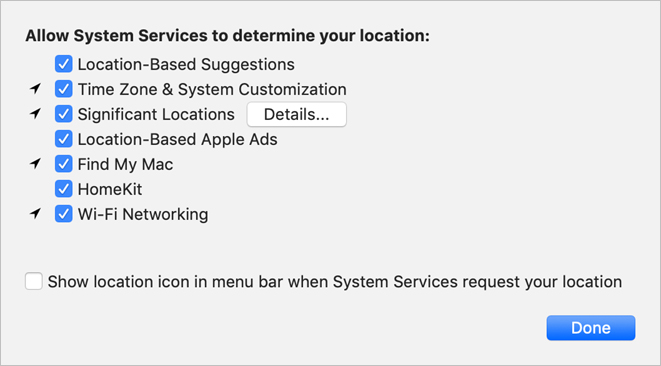
![]() Location Services—Location Services allows apps and websites to gather and use information based on the current location of your Mac. Your approximate location is determined using information from local Wi-Fi networks, and is collected by Location Services in a way that doesn’t personally identify you. Location Services lets apps, such as web browsers, gather and use information based on your location. You can turn off Location Services completely, or you can select which apps can see information about your location. Click About Location Services & Privacy for detailed information. Click Details next to System Services to see or edit the list of services that can determine your location. While Location Services is selected, next to System Services you can click Details to configure the system services that are allowed to access Location Services. You can modify these settings only if Security & Privacy preferences is unlocked. There’s also an option to display a location icon in menu bar when System Services requests your location. The menu item appears as a northeast compass arrow.
Location Services—Location Services allows apps and websites to gather and use information based on the current location of your Mac. Your approximate location is determined using information from local Wi-Fi networks, and is collected by Location Services in a way that doesn’t personally identify you. Location Services lets apps, such as web browsers, gather and use information based on your location. You can turn off Location Services completely, or you can select which apps can see information about your location. Click About Location Services & Privacy for detailed information. Click Details next to System Services to see or edit the list of services that can determine your location. While Location Services is selected, next to System Services you can click Details to configure the system services that are allowed to access Location Services. You can modify these settings only if Security & Privacy preferences is unlocked. There’s also an option to display a location icon in menu bar when System Services requests your location. The menu item appears as a northeast compass arrow.
![]() Contacts, Calendars, Reminders, and Photos—Shows apps that may gather and use information from your contacts, photos, calendar, or reminders.
Contacts, Calendars, Reminders, and Photos—Shows apps that may gather and use information from your contacts, photos, calendar, or reminders.
![]() Camera and Microphone—Shows apps that have access to the microphone or camera on your Mac.
Camera and Microphone—Shows apps that have access to the microphone or camera on your Mac.
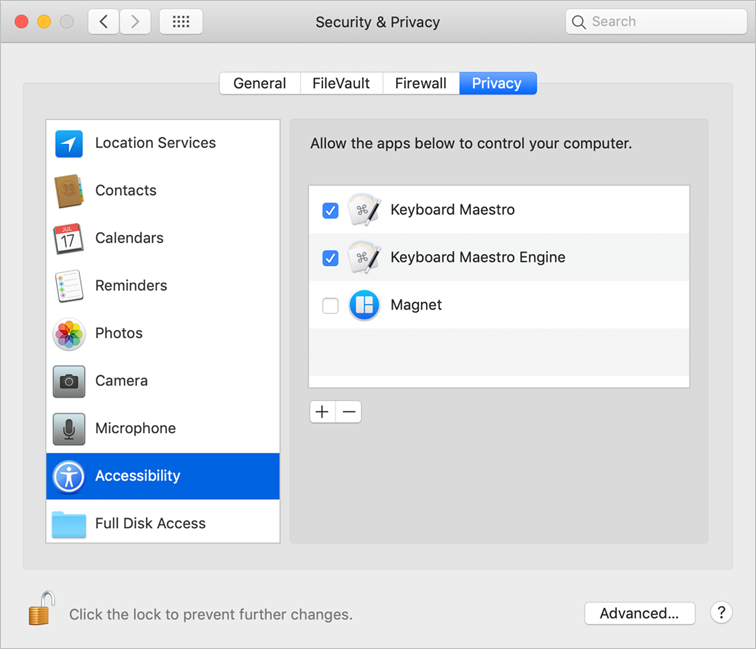
![]() Accessibility—Shows apps that run scripts and system commands to control your Mac. After you enable them, assistive apps grant access to control macOS input and modify interface behavior.
Accessibility—Shows apps that run scripts and system commands to control your Mac. After you enable them, assistive apps grant access to control macOS input and modify interface behavior.
![]() Full Disk Access—Shows apps that can access your entire disk. macOS Mojave introduces Full Disk Access as a new pane in the Privacy pane of Security & Privacy preferences. If an app requires full disk access, the first time you open that app in macOS Mojave, it might prompt you to manually add one or more apps to the Full Disk Access pane. If you’ve upgraded your Mac to macOS Mojave, then you might need to manually add apps and even helper apps that require full disk access to the Full Disk Access pane in order for those apps to continue to work correctly in macOS Mojave.
Full Disk Access—Shows apps that can access your entire disk. macOS Mojave introduces Full Disk Access as a new pane in the Privacy pane of Security & Privacy preferences. If an app requires full disk access, the first time you open that app in macOS Mojave, it might prompt you to manually add one or more apps to the Full Disk Access pane. If you’ve upgraded your Mac to macOS Mojave, then you might need to manually add apps and even helper apps that require full disk access to the Full Disk Access pane in order for those apps to continue to work correctly in macOS Mojave.
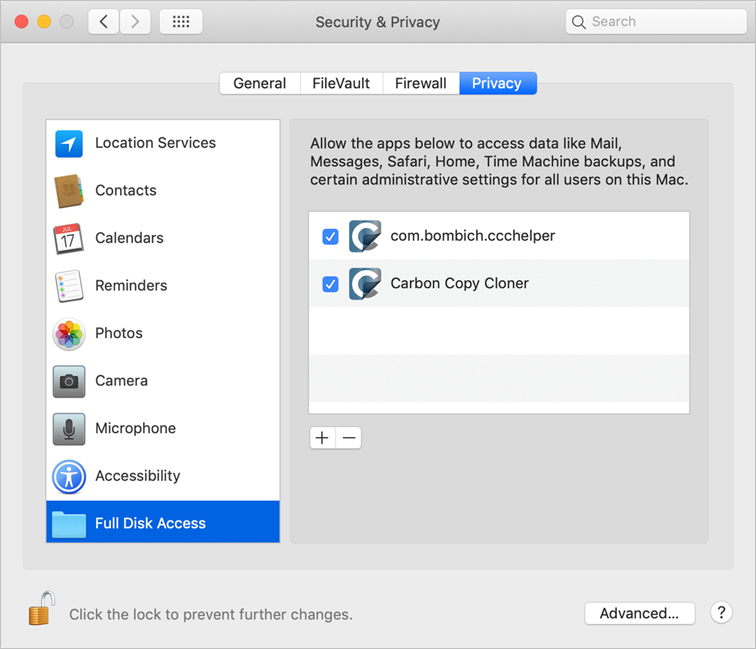
![]() Automation—Shows apps that can access and control other apps on your Mac. macOS Mojave introduces Automation as a new pane in the Privacy pane of Security & Privacy preferences. This list can include apps that are created with Automator or Script Editor, which are built in with macOS. Automator enables you to automate much of what you do on your Mac. It creates workflows with hundreds of actions that are available in the Automator Library. Script Editor enables you to create scripts, tools, and apps that perform repetitive tasks, automate complex workflows, manipulate apps, or even control your Mac. You can use various scripting languages, including AppleScript, JavaScript for Automation, shell scripts, and some third-party scripting languages. For more information about automation, open Automator and choose Help > Automator Help, or go to http://macosxautomation.com.
Automation—Shows apps that can access and control other apps on your Mac. macOS Mojave introduces Automation as a new pane in the Privacy pane of Security & Privacy preferences. This list can include apps that are created with Automator or Script Editor, which are built in with macOS. Automator enables you to automate much of what you do on your Mac. It creates workflows with hundreds of actions that are available in the Automator Library. Script Editor enables you to create scripts, tools, and apps that perform repetitive tasks, automate complex workflows, manipulate apps, or even control your Mac. You can use various scripting languages, including AppleScript, JavaScript for Automation, shell scripts, and some third-party scripting languages. For more information about automation, open Automator and choose Help > Automator Help, or go to http://macosxautomation.com.
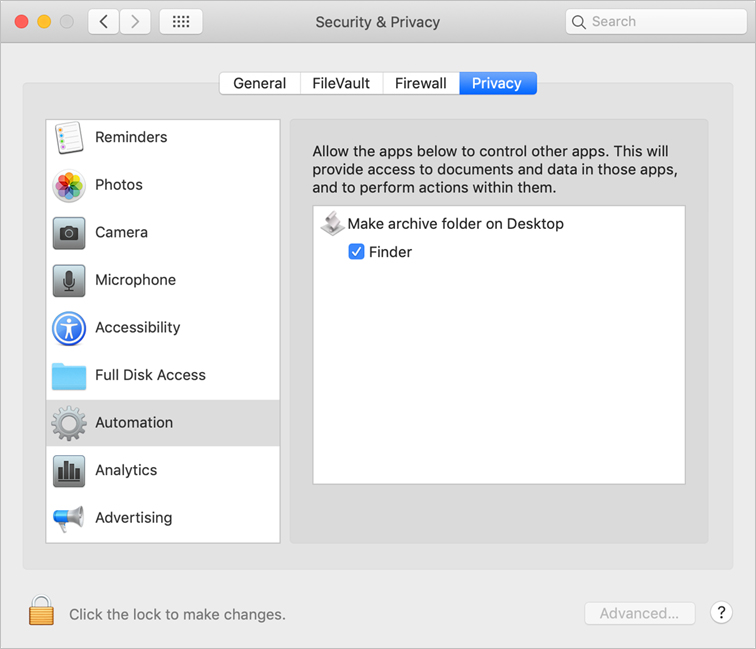
![]() Analytics—To help Apple and other developers serve customers better and improve the quality of their products, you can choose to automatically send analytics information to Apple and app developers. If you agree to send Mac Analytics to Apple, you include the following: details about app or macOS crashes, freezes, or kernel panics; information about events on your Mac (for example, whether a function such as waking your Mac was successful); and usage information (for example, data about how you use Apple and third-party software, hardware, and services). This information helps Apple and app developers resolve recurring issues. All analytics information is sent to Apple anonymously.
Analytics—To help Apple and other developers serve customers better and improve the quality of their products, you can choose to automatically send analytics information to Apple and app developers. If you agree to send Mac Analytics to Apple, you include the following: details about app or macOS crashes, freezes, or kernel panics; information about events on your Mac (for example, whether a function such as waking your Mac was successful); and usage information (for example, data about how you use Apple and third-party software, hardware, and services). This information helps Apple and app developers resolve recurring issues. All analytics information is sent to Apple anonymously.
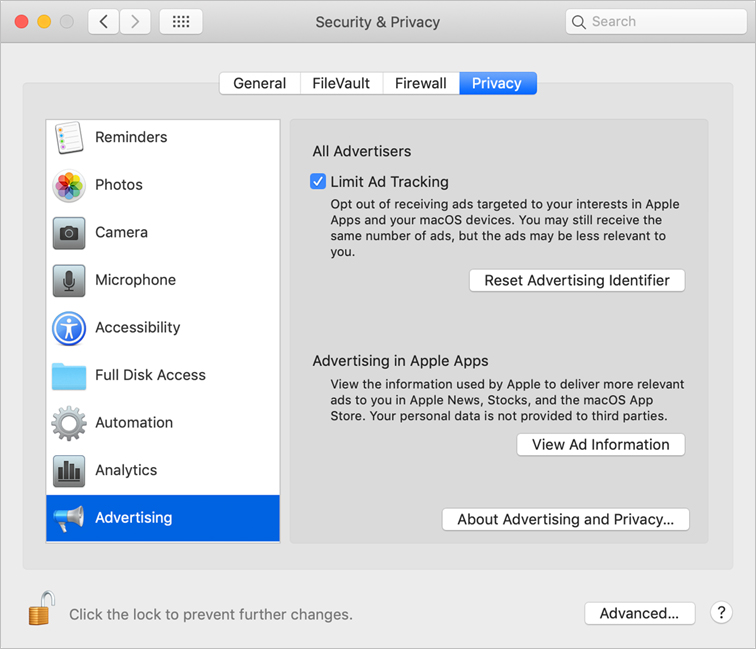
![]() Advertising—macOS Mojave introduces Advertising as a new pane in the Privacy pane of Security & Privacy preferences. Sometimes you’ll receive ads in Apple apps and on your macOS devices that are targeted to your interests. To limit these ads, select the Limit Ad Tracking option. You may still receive ads, but they won’t be sent based on data captured by ad tracking. To view what information about your device is used to deliver ads to you in Apple News, Stocks, and the App Store, click View Ad Information. To review Apple’s Advertising and Privacy policy, click About Advertising and Privacy.
Advertising—macOS Mojave introduces Advertising as a new pane in the Privacy pane of Security & Privacy preferences. Sometimes you’ll receive ads in Apple apps and on your macOS devices that are targeted to your interests. To limit these ads, select the Limit Ad Tracking option. You may still receive ads, but they won’t be sent based on data captured by ad tracking. To view what information about your device is used to deliver ads to you in Apple News, Stocks, and the App Store, click View Ad Information. To review Apple’s Advertising and Privacy policy, click About Advertising and Privacy.
Dictation Privacy
Enable and manage the Dictation feature in the Dictation pane of Keyboard preferences. Dictation supports many languages, including multiple regional dialects.
To use a different language or to help Dictation automatically enter the correct spoken text, click the Language menu, choose Add Language, and then select the languages and dialects that the users of your Mac speak. Dictation supports basic text-related spoken commands for formatting and punctuation.
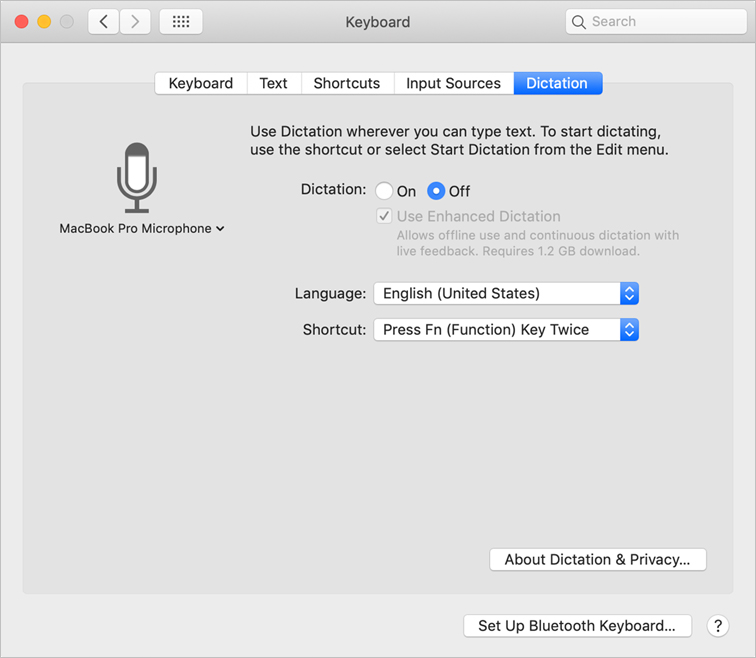
Dictation is off by default. After you turn Dictation on, the Enhanced Dictation option is enabled by default, and your Mac attempts to download additional dictation assets. When you use Enhanced Dictation, your Mac converts what you say into text without sending your dictated speech to Apple.
If you turn Enhanced Dictation off, when you dictate text what you say is sent to Apple to be converted to text. To help your Mac recognize what you’re saying, other information is sent, too, such as your Contacts names.
If you turn Enhanced Dictation back on, user data and recent voice input data are removed from Apple servers. Click About Dictation & Privacy for more details.
Read Apple Support article HT202584, “Use your voice to enter text on your Mac.”
Safari Privacy
Safari can try to block the hidden methods used to gather information about your web use. Find additional privacy settings in the Safari preferences window.
The “Prevent cross-site tracking” option is turned on by default. Some websites use third-party content providers, which can track you across websites to advertise to you. With this option turned on, tracking data is periodically deleted unless you visit the third-party content provider.
The “Ask websites not to track me” option is turned off by default. With this option turned on, each time you get content from a website, you add a request not to track you, but it’s up to the website to honor this request.
The “Block all cookies” option is turned off by default. Cookies are bits of information about your web history that can be used to track your presence on the Internet. Turning on this option might prevent some websites from working properly.
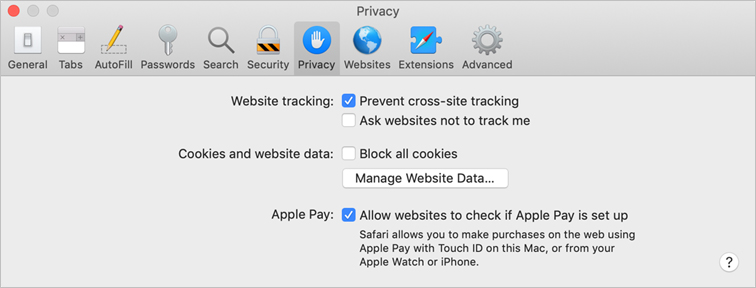
Click Manage Website Data to see which websites store cookies and other information on your Mac. You can remove cookies and website data for individual websites or for all of them.
Reference 9.7 Approve Kernel Extensions
macOS High Sierra introduced a feature that requires user approval before loading new third-party kernel extensions (KEXTs). A KEXT is a dynamically loaded bundle of executable code that runs in kernel space to perform low-level tasks that cannot be performed in user space. KEXTs typically belong to one of three categories:
![]() Low-level device drivers
Low-level device drivers
![]() Network filters
Network filters
![]() File system
File system
macOS requires user consent to load KEXTs with or after the installation of macOS High Sierra or macOS Mojave. This is known as User Approved Kernel Extension Loading. Any user can approve a kernel extension, even without administrator privileges.
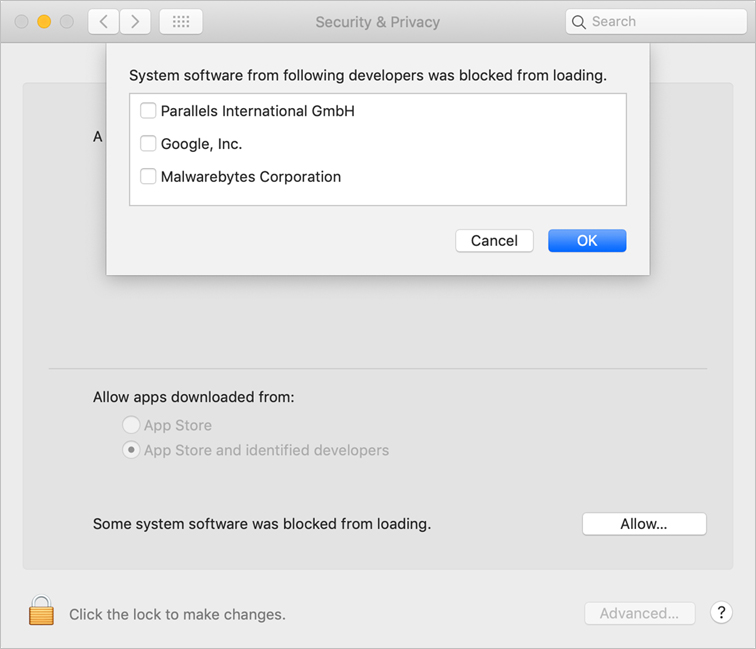
When you install software that attempts to install a KEXT, macOS displays a dialog that states that it blocked installing the KEXT.
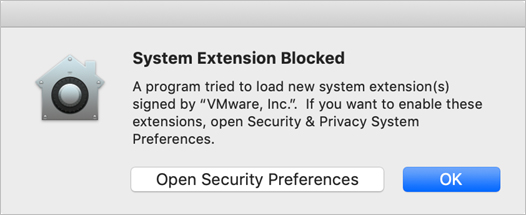
Click OK to dismiss the dialog, and then open Security & Privacy preferences.
Click Allow to allow macOS to install the new KEXT.
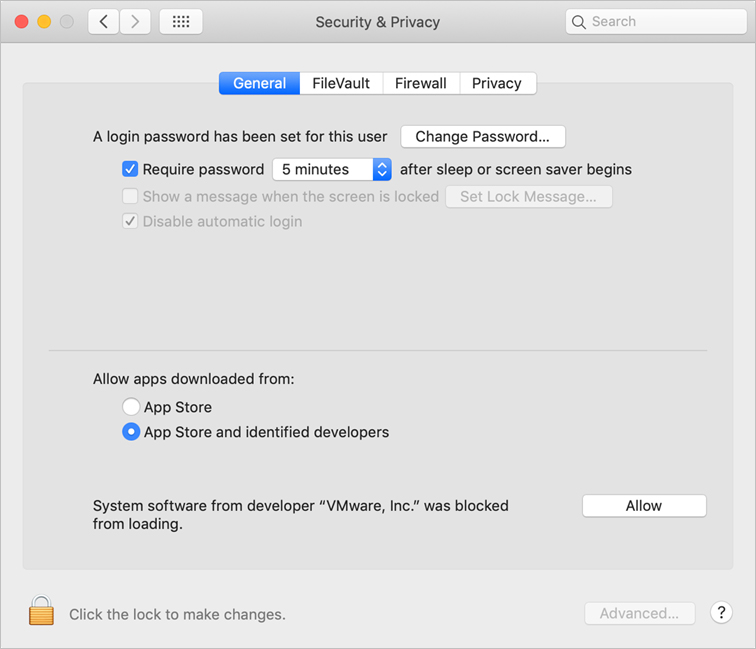
If macOS blocked more than one KEXT, click Allow to view the list of items that were blocked from loading.
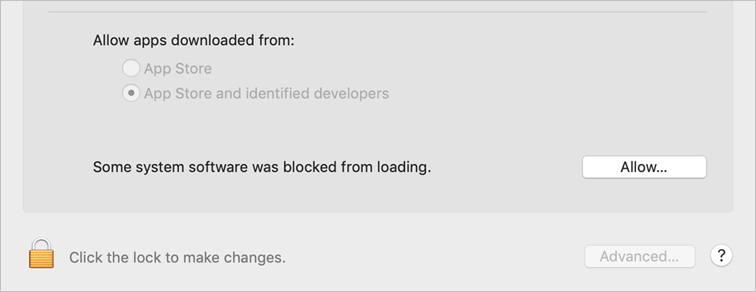
Select the checkbox for each KEXT you want to allow to load, and then click OK.
Kernel extensions don’t require authorization if they:
![]() Were on the Mac before you upgraded to macOS High Sierra.
Were on the Mac before you upgraded to macOS High Sierra.
![]() Are replacing previously approved extensions.
Are replacing previously approved extensions.
![]() If your Mac was automatically enrolled with your MDM solution with either Apple Business Manager or Apple School Manager, or your Mac has User-Approved MDM enrollment, and the KEXT is whitelisted in a Kernel Extension Policy payload from your MDM solution.
If your Mac was automatically enrolled with your MDM solution with either Apple Business Manager or Apple School Manager, or your Mac has User-Approved MDM enrollment, and the KEXT is whitelisted in a Kernel Extension Policy payload from your MDM solution.
![]() If you use the spctl command in macOS Recovery. This method is reset when you update macOS, and when you reset your nonvolatile RAM (NVRAM).
If you use the spctl command in macOS Recovery. This method is reset when you update macOS, and when you reset your nonvolatile RAM (NVRAM).
For more information, read Apple Support article HT208019, “Prepare for changes to kernel extensions in macOS High Sierra.”
If your Mac has User-Approved MDM, you can use your MDM solution to allow:
![]() Approval of specific KEXTs
Approval of specific KEXTs
![]() Approval of developer Team IDs
Approval of developer Team IDs
![]() Ability to enable or disable users to approve KEXTs
Ability to enable or disable users to approve KEXTs
Reference 9.8 Lock Your Screen
If you’re logged in to your Mac and you need to step away from it, lock your screen so that no one can access your Mac in your absence. Click the Apple menu, then choose Lock Screen (or press Control-Command-Q).
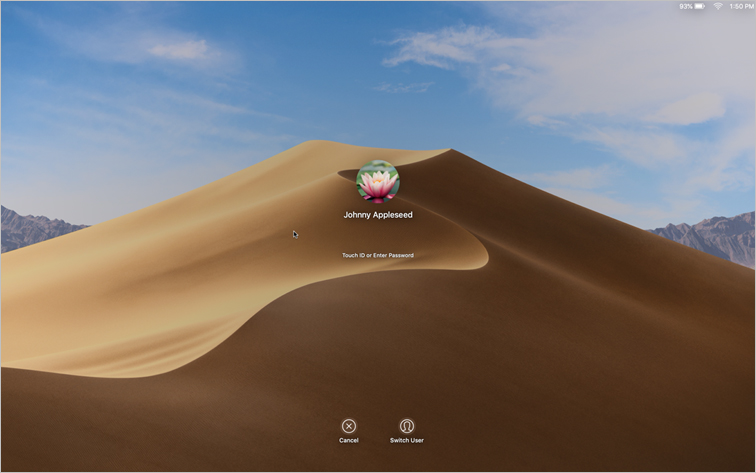
macOS locks your screen immediately, and you’ll see a login window with your user picture, your full name, and the password field. No one can use your Mac without first authenticating as you.
If your organization requires a Mac to display a lock screen message, read Apple Support article HT203580, “How to set a lock message on the login window of your Mac.”
Exercise 9.1 Manage Keychains
By default, when you log in to your account, your keychain is automatically unlocked and remains unlocked until you log out. If you want more security, you can configure the keychain to lock after a period of inactivity or when your Mac goes to sleep.
In this exercise, you explore keychain management techniques.
Configure the Keychain to Lock Automatically
Log in as Johnny Appleseed (password: Apple321!).
In the Finder, open the Utilities folder choosing Go > Utilities or by pressing Shift-Command-U.
In the Utilities folder, open Keychain Access.
In the upper-left corner, you will notice that the open padlock icon next to the login keychain indicates that it is unlocked.
From the menu bar, choose Edit > Change Settings for Keychain “login.”
Select “Lock after 5 minutes of inactivity” and “Lock when sleeping.”
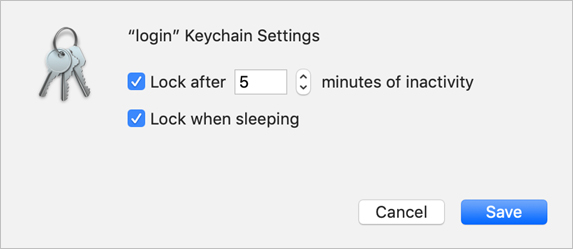
Click Save.
Open System Preferences, and select Security & Privacy preferences.
If necessary, click General and deselect the “Require password” option.
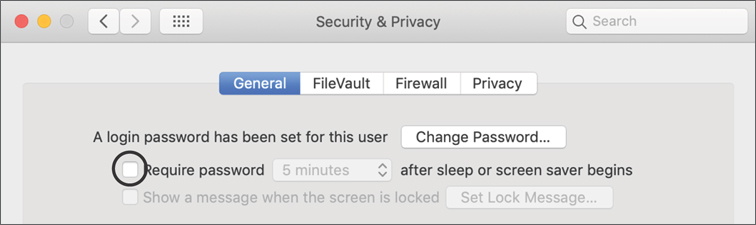
If you are prompted to enter Johnny Appleseed’s password (Apple321!), do so and click OK.
This is a per-user preference setting, so administrator authorization isn’t required.
If a confirmation dialog appears, click Turn Off Screen Lock.
Close System Preferences.
If you are presented with a “Do you want to turn off iCloud Keychain?” dialog, click Turn Off Keychain.
Choose Apple menu > Sleep.
Press any key to wake the Mac.
If you are prompted to enter your keychain password for the accountsd or identityservicesd process, click Cancel. Don’t enter Johnny’s password.
If necessary, open Keychain Access.
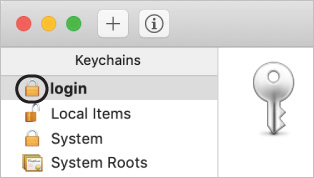
The lock icon next to the login keychain appears locked (not open), indicating that the keychain is locked.
If you were prompted by identityservicesd or accountsd, they weren’t able to access items in your keychain because the keychain was locked and they were inaccessible.
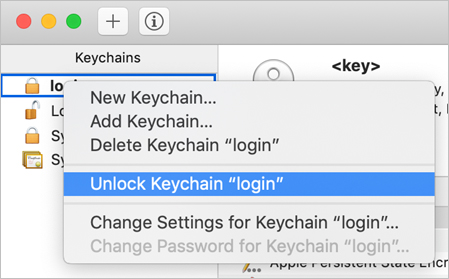
In Keychain Access, Control-click the login keychain and select Unlock Keychain “login.”
Enter Johnny’s password and click OK.
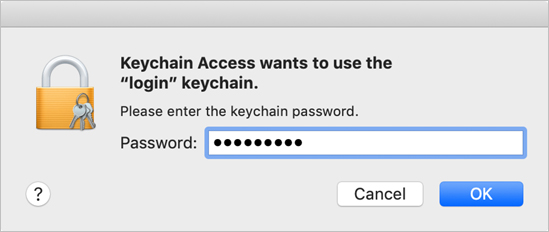
The lock opens and your keychain unlocks.
Configure the Login Session to Lock
Instead of locking only the keychain, you can configure the entire login session to lock on sleep or after a period of inactivity.
Open Security & Privacy preferences and click General.
Select “Require password,” and choose “immediately” from the menu.
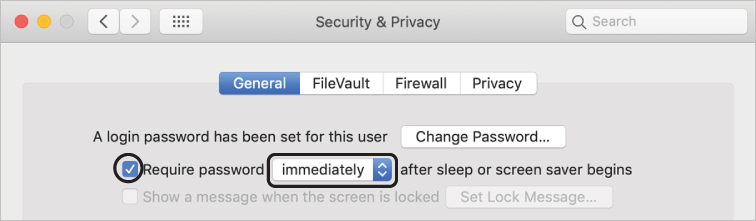
If you are prompted, enter Johnny Appleseed’s password (Apple321!)
Choose Apple menu > Sleep.
There are many ways to activate this lock. You could use Desktop & Screen Saver preferences to configure a hot corner to activate the screen saver, or if your keyboard has a media eject key or power button, press Control-Shift-(media eject or power) to put your Mac to sleep.
Press any key to wake the Mac.
You see an unlock screen similar to the login screen, but with only Johnny’s account shown.
Enter Johnny’s password and press Return.
Your session unlocks. When you entered the password, the keychain unlocked along with the login session.
To simplify the rest of the exercises, you can relax these security measures.
Deselect the “Require password” option in Security & Privacy preferences. If necessary, click Turn Off Screen Lock in the confirmation dialog.
Quit System Preferences.
In Keychain Access, from the menu bar, choose Edit > Change Settings for Keychain “login.”
If you are prompted, enter Johnny’s password to unlock the keychain.
Deselect both “Lock after 5 minutes of inactivity” and “Lock when sleeping.”
Click Save.
Store a Password in a Keychain
Your keychain has a number of automatically created entries. In this section, you create an entry manually.
Open the ParticipantMaterials/Lesson9 folder. Remember that you created a shortcut to ParticipantMaterials in your Dock.
Open the file named “Johnny’s private files.dmg.”
This disk image is encrypted, so the system prompts you for the password to open it.
Select “Remember password in my keychain.”
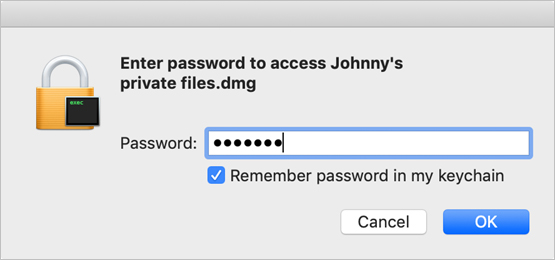
Enter the password private.
Click OK.
If you are prompted to enter the keychain password, enter Johnny’s account password.
Select the disk image on your desktop, and press Command-E to eject it.
Open the disk image again.
Since the password is now stored in your keychain and the keychain is unlocked, the image opens without asking you for the password.
Eject the disk image.
Retrieve a Password in a Keychain
Even though passwords are stored to make them available for apps, there may be times when a user needs to retrieve a stored password. For example, a user who wants to use webmail on a different Mac may want to retrieve his or her email password to do so. In this section, you use the keychain to retrieve a forgotten password.
If necessary, open Keychain Access from the Utilities folder. Remember that you can reach this folder in the Finder by choosing Go > Utilities or by pressing Shift-Command-U.
Double-click the password entry named “Johnny’s private files.dmg.” Scroll down or use the search filter at the upper-right corner of Keychain Access if you need to.
A window opens, displaying information about this password entry.
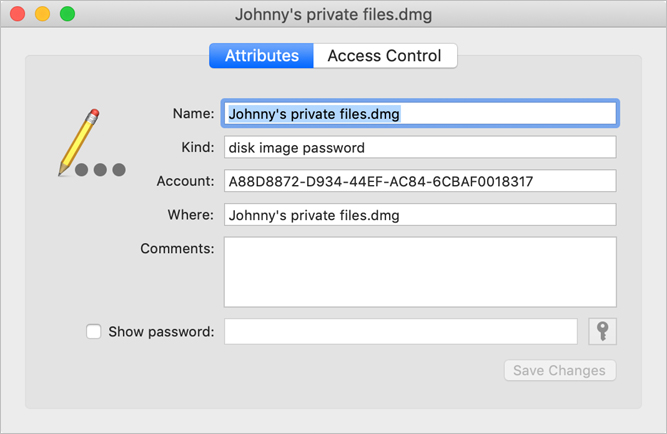
Click Access Control.
The Access Control pane displays information about what apps or system components are allowed access to the keychain entry. In this case, the diskimages-helper app can automatically access the password, but if any other app requests access, macOS asks the user for confirmation first.
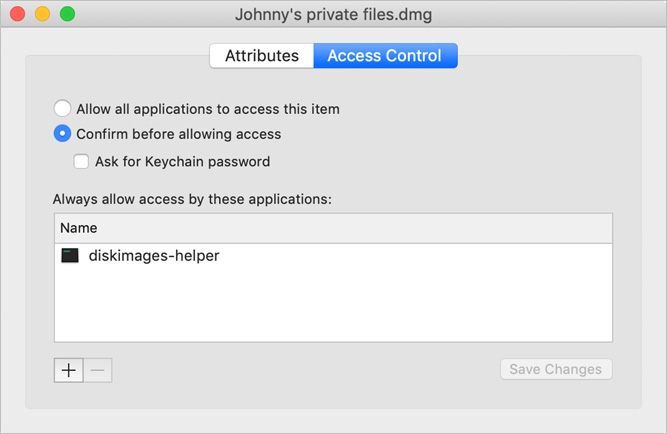
Normally, the app that created a keychain entry is the only one that is allowed automatic access to it, but you can change this policy.
Click Attributes.
In the Attributes pane, select Show Password.
A dialog informs you that Keychain Access wants to use your confidential information, stored in “Johnny’s private files.dmg,” in your keychain. Even though your keychain is unlocked, this item access policy requires confirmation before anything other than diskimages-helper is allowed to read the password.
Enter Johnny’s account password, and click Always Allow.
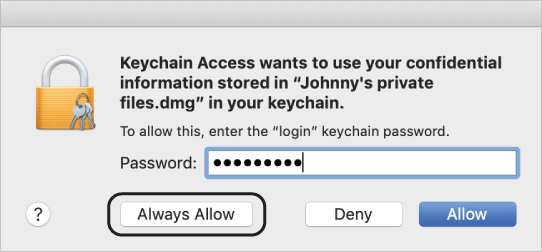
The disk image password becomes visible.
Click Access Control.
Keychain Access is added to the “Always allow access” list for this item. If you had clicked Allow, Keychain Access would have been allowed access to the password but would not have been added to this access control list. Since it is added to the list, Keychain Access can display the password without asking for confirmation.
If Keychain Access doesn’t appear in the Access Control tab, quit Keychain Access and select the Access Control tab for “Johnny’s private files.dmg” again.
Close the “Johnny’s private files.dmg” window.
Move a Password to the System Keychain
Normally, resource passwords are stored in a user keychain and are accessible only by that user. You can move resource passwords to the System keychain, making them accessible to all users.
Find the “Johnny’s private files.dmg” keychain item, and drag it to the System keychain in the Keychains section of the sidebar.
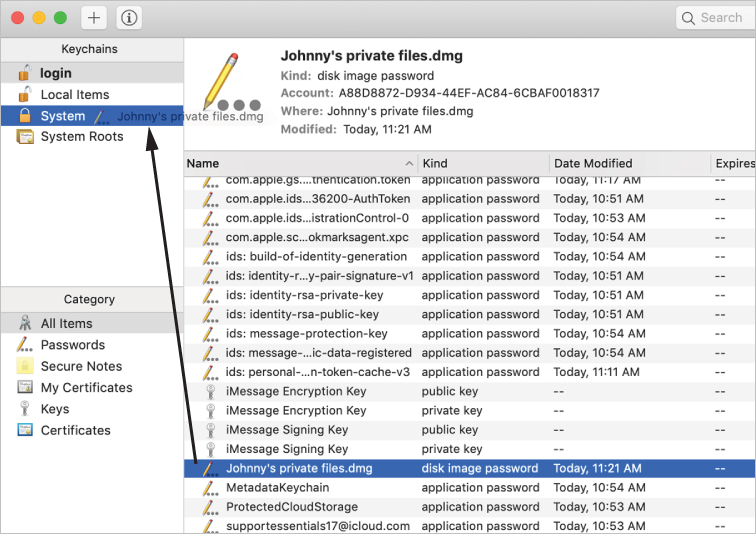
Authenticate as Local Administrator (password: Apple321!).
When you’re prompted to allow kcproxy to use the confidential information in “Johnny’s private files.dmg,” click Allow, and if necessary, authenticate as Johnny.
kcproxy is a tool that Keychain Access uses to move entries into the System keychain.
“Johnny’s private files.dmg” disappears from your login keychain.
Click the System keychain.
“Johnny’s private files.dmg” is now listed here, along with several automatically created items, and any Wi-Fi passwords stored on your Mac are listed.
Quit Keychain Access and log out of the Johnny Appleseed account.
Log in as Emily Davidson (password: Apple321!).
Use the next two steps to open /Users/Shared/ParticipantMaterials/Lesson9/Johnny’s private files.dmg.
Emily’s Finder preferences aren’t customized to allow easy access outside her home folder.
Choose Go > Computer (Shift-Command-C).
Open Macintosh HD > Users > Shared > ParticipantMaterials > Lesson9.
The disk image opens. Because the keychain item access controls allow diskimages-helper full access to the item for all users, you aren’t prompted to authenticate or allow access.
Eject the disk image and log out of the Emily Davidson account.
Exercise 9.2 Approve Kernel Extension Loading
macOS Mojave requires user approval before loading new third-party kernel extensions (KEXTs). This required user approval is called User Approved Kernel Extension Loading. Normally macOS loads and unloads kernel extensions as needed. The kernel extension for this exercise was created as an example, so for the purposes of this exercise, you install a kernel extension manually and approve its loading.
Install a Kernel Extension
Log in as Local Administrator (password: Apple321!).
Open the ParticipantMaterials/Lesson9 folder.
There is a shortcut to ParticipantMaterials in the Finder sidebar and in your Dock.
Open the file named DemoExtension.dmg.
The disk image mounts and displays a kernel extension. Often, a kernel extension is part of an installer or app. In this example, you install it manually by copying the kernel extension to the /Library/Extensions folder. You will learn more about installing apps in Lesson 18, “Install Apps.”
Click Launchpad in the Dock and open Terminal.
You could also use Spotlight, or from the menu bar choose Go > Utilities, then open Terminal from the Utilities folder.
In Terminal, type sudo cp -r /Volumes/DemoExtension/DemoExtension.kext /Library/Extensions and press Return.
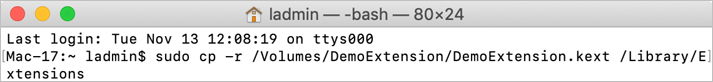
Because you are using the sudo command, you must authenticate as Local Administrator (either the full name Local Administrator or the account name ladmin). to elevate your permissions.
Type your password.
Press Return.
The command should return no output. This indicates that copying the kernel extension to /Library/Extensions succeeded.
This command copies the kernel extension to the appropriate third-party location, and the extension is ready to be loaded.
Load and Approve a Kernel Extension
If macOS attempts to load the kernel extension on its own, read the dialog in step 3 and continue with step 4. Otherwise, proceed with step 2.
In Terminal, type sudo kextutil /Library/Extensions/DemoExtension.kext, and press Return.
If necessary, authenticate as ladmin.
macOS attempts to load the kernel extension. But, because of macOS Mojave security measures, you see a dialog that tells you the attempt to load the Kernel Extension was blocked.
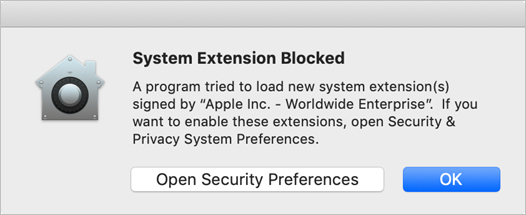
Read the dialog, and then click OK.
Open Security & Privacy preferences.
In the General pane of Security & Privacy preferences, you see a button that enables a user to allow this kernel extension to load.
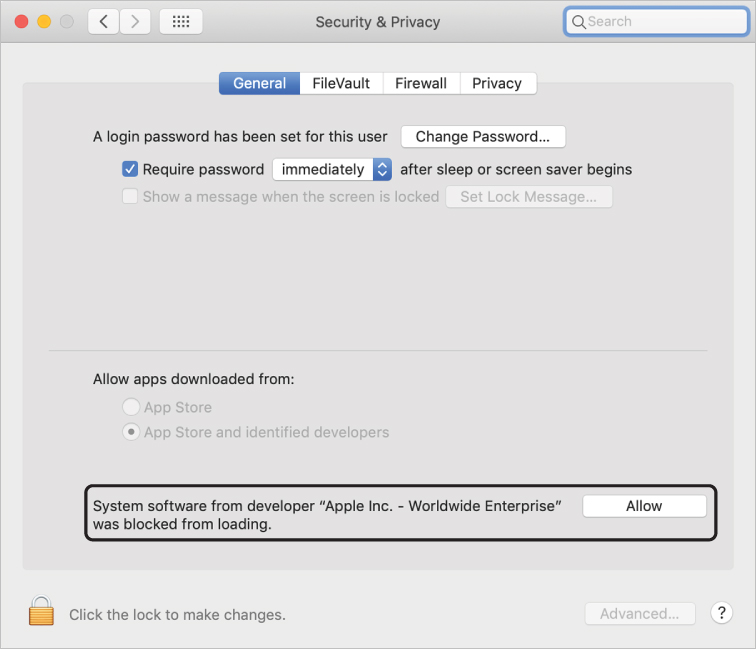
Click Allow.
The message disappears, and the kernel extension is loaded. Users do not need to authenticate or be in the admin group to allow a kernel extension to load.
Open System Information. Press and hold the Option key and choose Apple > System Information.
Locate Software in the sidebar, and click Extensions.
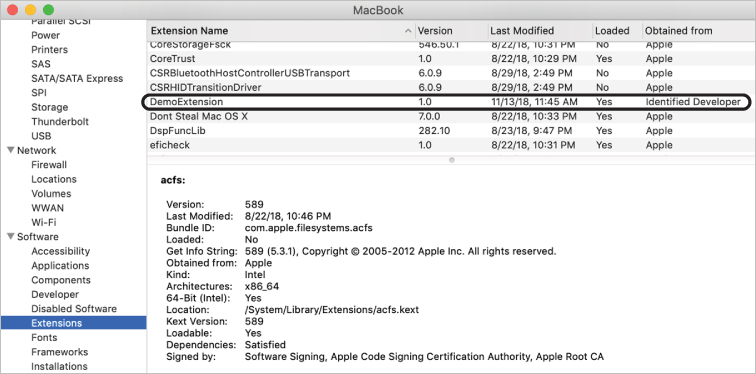
DemoExtension exists and is loaded.
Quit System Preferences, System Information, and Terminal.
This demo kernel extension will remain loaded on your Mac. This demo kernel extension doesn’t affect the performance of your Mac, but you shouldn’t use this kernel extension outside the context of these exercises.
Exercise 9.3 Approve App Access to Your Mac
macOS Mojave requires user approval before it allows cross-app data requests. You manage this in Security & Privacy preferences. In this exercise, you install an app that requests access to your contacts.
Install an App
Log in as Johnny Appleseed (password: Apple321!).
Open the ParticipantMaterials/Lesson9 folder.
There is a shortcut to ParticipantMaterials in the Finder sidebar and in your Dock.
Open the file named Directory.dmg.
Directory is an app that must be installed in the Applications folder.
From the menu bar, choose Go > Applications (Shift-Command-A).
Drag and drop the Directory app from the disk image to your Applications folder.
At the “Modifying ‘Applications’ requires an administrator name and password” prompt, select Authenticate, and authenticate as Local Administrator.
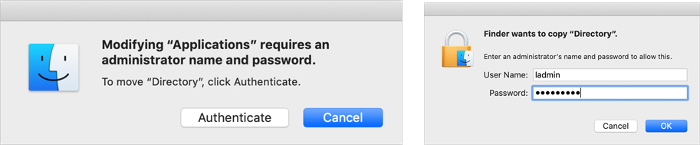
The Directory app is installed in your Applications folder.
Approve an App
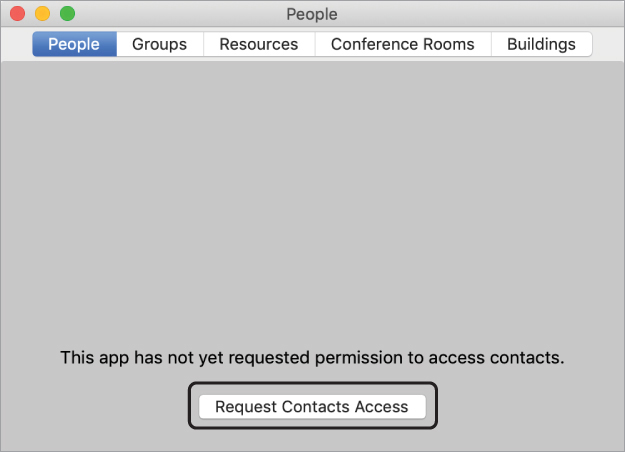
Open Directory.

In Directory, you see a Request Contacts Access button. Many apps have different mechanisms for app approval, but if an app in macOS Mojave wants data from another source, it must first obtain user consent.
Select the Request Contacts Access button in Directory.
At the “Directory would like to access your contacts” prompt, click OK.
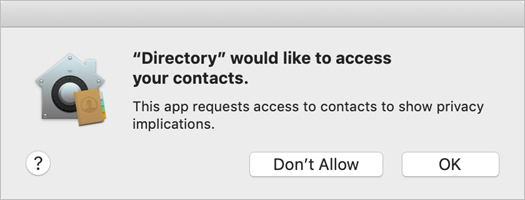
You approved the cross-app data request.
In Directory, it says that Contacts access is authorized.
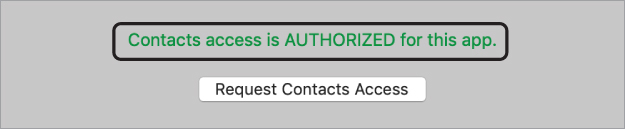
Quit Directory, and open Security and Privacy preferences.
Click Privacy.
Note the different categories in the left sidebar.
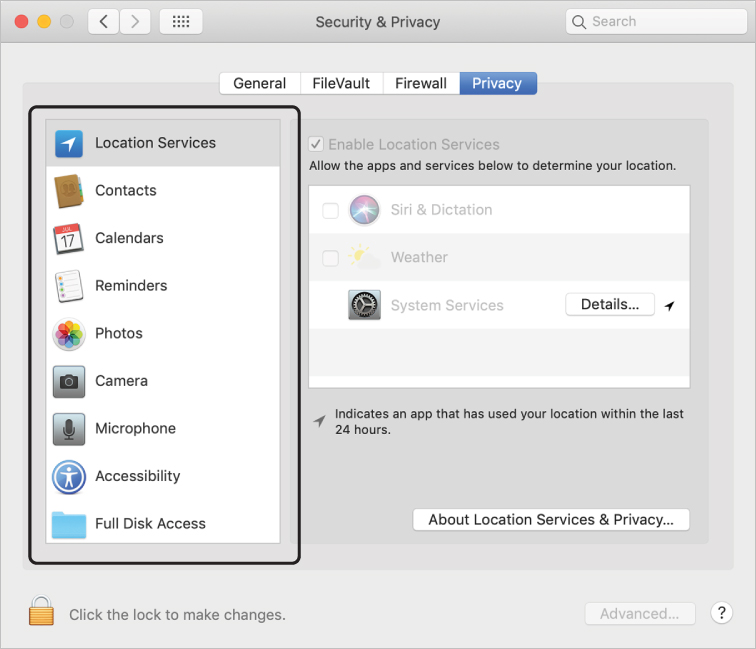
Select Contacts.
There is a checkbox next to Directory. This tells you that Directory is approved for access to Contacts.
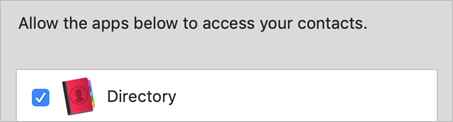
Deselect the checkbox next to Directory, and then reopen Directory.
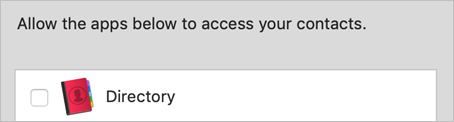
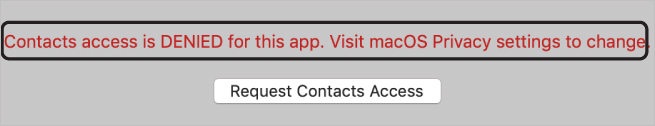
Directory now says that Contacts access is denied and tells you to visit the macOS Privacy Settings to change access.
