Introduction to Security
You see this a lot—typically, in medium to large enterprise networks, the various strategies for security are based on some recipe of internal and perimeter routers plus firewall devices. Internal routers provide additional security to the network by screening traffic to various parts of the protected corporate network, and they do this using access lists.
 Access lists are beyond the scope of this book, but they're covered in CCNA: Cisco Certified Network Associate Study Guide, Seventh Edition (Sybex, 2011).
Access lists are beyond the scope of this book, but they're covered in CCNA: Cisco Certified Network Associate Study Guide, Seventh Edition (Sybex, 2011).
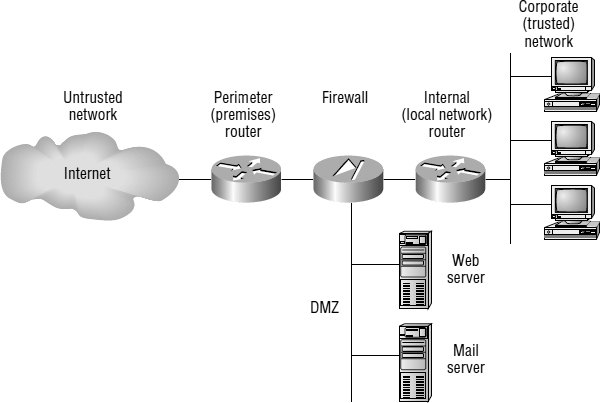
Figure 9.1 shows where each of these types of devices is found.
FIGURE 9.1 A typical secured network
To protect network device configuration files from outside network security threats, use a firewall, as shown in Figure 9.1, to restrict access from the outside to the network devices, and use SSH instead of Telnet to access device configurations.
Figure 9.1 uses the terms trusted network and untrusted network. You can see where they are found in a typical secured network as well as the demilitarized zone (DMZ), which use global (real) Internet addresses or private addresses, depending on how you configure your firewall. However, this is typically where you'll find the HTTP, DNS, email, and other Internet-type corporate servers.
Instead of having routers, you can use virtual local area networks (VLANs) with switches on the inside trusted network. Multilayer switches containing their own security features can sometimes replace internal (LAN) routers to provide higher performance in VLAN architectures.
Let's discuss the security threats a typical secured internetwork faces; then I'll provide some ways of protecting the Cisco router and switch.
Recognizing Security Threats
Yes, it's true: security attacks vary considerably in their complexity and threat level. You see, it all comes down to planning—or, rather, lack thereof. Basically, the vital tool that the Internet has become today was absolutely unforeseen by those who brought it into being. This is a big reason why security is now such an issue; most IP implementations are innately insecure. No worries, though, because Cisco has a few tricks up its sleeve to help you with this.
WUI
Security attacks sometimes happen because of witless user ignorance (WUI). Knowing this term isn't an exam objective, but WUI causes security attacks more than you'd think!
The following are common trouble spots in the type of enterprise network shown in Figure 9.1:
Wireless LANs (WLANs) Any user that can connect to the WLAN can access the devices in the trusted network. People from outside the building may even be able to gain access if the WLAN access points are left unsecured. Use the highest security you can afford on your WLANs.
Mobile Devices When a mobile user connects their laptop at home or at another remote location, the laptop may become infected with a virus or a Trojan horse. When the user returns to the office and connects to the trusted network, the infection may spread. It is critical that all PCs and laptops are running the latest virus scanning software.
Employees I am sure this is no shock to you, but some employees may be disgruntled workers. This may be the worst security problem a company can have. The employees are inside the trusted network and have access to many, if not all, devices and servers. It is important to grant each employee the minimum access they need.
 Remember, attacks from inside the network remain as high a threat as those from outside. Prepare your network security plan accordingly.
Remember, attacks from inside the network remain as high a threat as those from outside. Prepare your network security plan accordingly.
Common Attack Profiles
This section covers the most common attacks used on today's networks.
Application-Layer Attacks These attacks commonly zero in on well-known holes in the software that's typically found running on servers. Favorite targets include FTP, sendmail, and HTTP. Because the permission levels granted to these accounts are most often “privileged,” bad guys simply access and exploit the machine that's running one of the applications I just mentioned.
Autorooters You can think of these as a kind of hacker automaton. Bad guys use something called a rootkit to probe, scan, and then capture data on a strategically positioned computer that's poised to give them “eyes” into entire systems—automatically!
Back Doors These are simply paths leading into a computer or network. Through simple invasions, or via more elaborate Trojan horse code, bad guys can use their implanted inroads into a specific host or even a network whenever they want—until you detect and stop them, that is!
Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks These are bad—pretty tough to get rid of, too! But even hackers don't respect other hackers who execute them because, though nasty, they're really easy to accomplish. (This means that some 10-year-old could actually bring you to your knees, and that is just wrong!) Basically, a DoS attack is a flood of packets requesting a TCP connection to server. And there are several different flavors.
TCP SYN Flood TCP SYN flood attacks begin with a client-initiated, seemingly run-of-the-mill, TCP connection that sends a SYN message to a server. The server predictably responds by sending a SYN-ACK message back to the client machine, which then establishes the connection by returning an ACK message. That sounds fine, but it's actually during this process—when the connection is only halfway open—that the victim machine is flooded with a deluge of half-open connections and pretty much becomes paralyzed.
“Ping of Death” Attacks You probably know that TCP/IP's maximum packet size is 65,536 octets. It's okay if you didn't know that—just understand that this attack is executed by simply pinging with oversized packets, causing a device to keep rebooting incessantly, freeze up, or just totally crash.
Tribe Flood Network (TFN) and Tribe Flood Network 2000 (TFN2K) These nasty little numbers are more complex in that they initiate synchronized DoS attacks from multiple sources and can target multiple devices. This is achieved, in part, by something known as IP spoofing, which I'll be describing soon.
Stacheldraht This attack is actually a mélange of methods, and it translates from the German term for barbed wire. It basically incorporates TFN and adds a dash of encryption. It all begins with a huge invasion at the root level, followed up with a DoS attack finale.
IP Spoofing This is pretty much what it sounds like it is—a bad guy from within or outside of your network masquerades as a trusted host machine by doing one of two things.
- Presenting with an IP address that's inside your network's scope of trusted addresses
- Using an approved, trusted external IP address
Because the hacker's true identity is veiled behind the spoofed address, this is often just the beginning of your problems.
Keystroke Loggers This is a software program that is actually kinda cool, depending on which side of the program you are on. The keystroke logger keeps track of all keystrokes a person types on a keyboard. Some loggers actually can email the information to the attacker.
Man-in-the-Middle Attacks Interception! But it's not a football; it's a bunch of your network's packets—your precious data! A common guilty party could be someone working for your very own ISP using a tool known as a sniffer (discussed later) and augmenting it with routing and transport protocols.
Network Reconnaissance Before breaking into a network, hackers often gather all the information they can about it, because the more they know about the network, the better they can compromise it. They accomplish their objectives through methods such as port scans, DNS queries, and ping sweeps.
Packet Sniffers This is the tool I mentioned earlier, but I didn't tell you what it is, and it may come as a surprise that it's actually software. Here's how it works:
- A network adapter card is set to promiscuous mode (meaning it reads every frame that is on the LAN or WLAN even if the frame is destined for another device on the network) so it will send all packets snagged from the network's physical layer through to a special application to be viewed and sorted out.
- A packet sniffer nicks some highly valuable, sensitive data including, but not limited to, passwords and usernames, making them prized among identity thieves.
Password Attacks These come in many flavors, and even though they can be achieved via more sophisticated types of attacks like IP spoofing, packet sniffing, and Trojan horses, their sole purpose is to—surprise—discover user passwords so the thief can pretend they're a valid user and then access that user's privileges and resources.
Brute-Force Attack This is another user or software-oriented attack that employs a program running on a targeted network to try to log in to some type of shared network resource like a server. For the hacker, it's ideal if the accessed accounts have a lot of privileges because then the bad guys can form back doors to use for gaining access later and bypass the need for passwords entirely. Basically, a brute-force attack is guessing the password, but the software today can use the full dictionary very quickly!
Port Redirection Attacks This approach requires a host machine that the hacker has broken into and uses to get wonky traffic (that normally wouldn't be allowed passage) through a firewall by using various ports (as described in Chapter 2, “Internet Protocols”).
Trojan Horse Attacks and Viruses These two are actually pretty similar—both Trojan horses and viruses infect user machines with malicious code and mess it up with varying degrees of paralysis, destruction, and even death! But they do have their differences—viruses are really just nasty programs attached to command.com, which just happens to be the main interpreter for all Windows systems. Viruses then run amok, deleting files and infecting any flavor files they find on the now-diseased machine. The difference between a virus and a Trojan horse is that Trojans are actually complete applications encased inside code that makes them appear to be a completely different entity—say, a simple, innocent game—not the ugly implements of destruction they truly are!
Trust Exploitation Attacks These attacks happen when someone exploits a trust relationship inside your network. For example, a company's perimeter network connection usually shelters important things such as SMTP, DNS, and HTTP servers, making the servers really vulnerable because they're all on the same segment.
To be honest, I'm not going to go into detail on how to mitigate each and every one of the security threats I just talked about, not only because that would be outside the scope of this book but also because the methods I am going to teach you will truly protect you from being attacked in general. You will learn enough tricks to make all but the most determined bad guys give up on you and search for easier prey. Basically, think of this as a chapter on how to practice “safe networking.”