Three Switch Functions at Layer 2
There are three distinct functions of layer 2 switching (you need to remember these!): address learning, forward/filter decisions, and loop avoidance.
Address Learning Layer 2 switches and bridges remember the source hardware address of each frame received on an interface, and they enter this information into a MAC database called a forward/filter table.
Forward/Filter Decisions When a frame is received on an interface, the switch looks at the destination hardware address and finds the exit interface in the MAC database. The frame is only forwarded out the specified destination port.
Loop Avoidance If multiple connections between switches are created for redundancy purposes, network loops can occur. Spanning Tree Protocol (STP) is used to stop network loops while still permitting redundancy. STP is covered extensively in my CCNA: Cisco Certified Network Associate Study Guide, Seventh Edition (Sybex, 2011), and it is not an ICND1 objective.
I'm going to talk about address learning and forward/filtering decisions in detail in the next sections, which are very large ICND1 objectives.
Address Learning
When a switch is first powered on, the MAC forward/filter table is empty, as shown in Figure 7.4.
FIGURE 7.4 Empty forward/filter table on a switch
When a device transmits and an interface receives a frame, the switch places the frame's source address in the MAC forward/filter table, allowing it to remember which interface the sending device is located on. The switch then has no choice but to flood the network with this frame out of every port except the source port because it has no idea where the destination device is actually located.
If a device answers this flooded frame and sends a frame back, then the switch will take the source address from that frame and place that MAC address in its database as well, associating this address with the interface that received the frame. Since the switch now has both of the relevant MAC addresses in its filtering table, the two devices can make a point-to-point connection. The switch doesn't need to flood the frame as it did the first time because now the frames can and will be forwarded only between the two devices. This is exactly the thing that makes layer 2 switches better than hubs. In a hub network, all frames are forwarded out all ports every time—no matter what. Figure 7.5 shows the processes involved in building a MAC database.
FIGURE 7.5 How switches learn hosts' locations
In this figure, you can see four hosts attached to a switch. When the switch is powered on, it has nothing in its MAC address forward/filter table, just as in Figure 7.4. But when the hosts start communicating, the switch places the source hardware address of each frame in the table along with the port that the frame's address corresponds to.
Let me give you an example of how a forward/filter table is populated.
- Host A sends a frame to Host B. Host A's MAC address is 0000.8c01.000A; Host B's MAC address is 0000.8c01.000B.
- The switch receives the frame on the E0/0 interface and places the source address in the MAC address table.
- Since the destination address is not in the MAC database, the frame is forwarded out all interfaces—except the source port.
- Host B receives the frame and responds to Host A. The switch receives this frame on interface E0/1 and places the source hardware address in the MAC database.
- Host A and Host B can now make a point-to-point connection, and only the two devices will receive the frames. Hosts C and D will not see the frames, nor are their MAC addresses found in the database because they haven't yet sent a frame to the switch.
If Host A and Host B don't communicate to the switch again within a certain amount of time, the switch will flush their entries from the database to keep it as current as possible.
Forward/Filter Decisions
When a frame arrives at a switch interface, the destination hardware address is compared to the forward/filter MAC database. If the destination hardware address is known and listed in the database, the frame is sent out only the correct exit interface. The switch doesn't transmit the frame out any interface except for the destination interface. This preserves bandwidth on the other network segments and is called frame filtering.
But if the destination hardware address is not listed in the MAC database, then the frame is flooded out all active interfaces except the interface the frame was received on. If a device answers the flooded frame, the MAC database is updated with the device's location (interface).
If a host or server sends a broadcast on the LAN, the switch will flood the frame out all active ports except the source port by default. Remember, the switch creates smaller collision domains, but it's still one large broadcast domain by default.
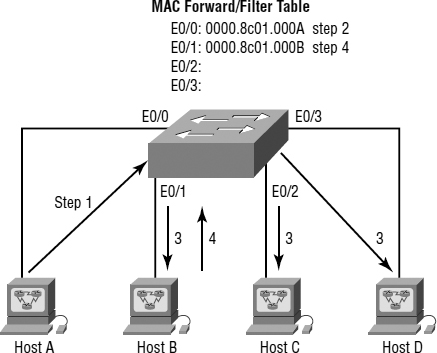
In Figure 7.6, Host A sends a data frame to Host D. What will the switch do when it receives the frame from Host A?
FIGURE 7.6 Forward/filter table
Since Host A's MAC address is not in the forward/filter table, the switch will add the source address and port to the MAC address table and then forward the frame to Host D. If Host D's MAC address was not in the forward/filter table, the switch would have flooded the frame out all ports except for port Fa0/3.
Now let's take a look at the output of a show mac address-table command from another switch.
Switch#sh mac address-table
Vlan Mac Address Type Ports
-- ------ ---- ---
1 0005.dccb.d74b DYNAMIC Fa0/1
1 000a.f467.9e80 DYNAMIC Fa0/3
1 000a.f467.9e8b DYNAMIC Fa0/4
1 000a.f467.9e8c DYNAMIC Fa0/3
1 0010.7b7f.c2b0 DYNAMIC Fa0/3
1 0030.80dc.460b DYNAMIC Fa0/3
1 0030.9492.a5dd DYNAMIC Fa0/1
1 00d0.58ad.05f4 DYNAMIC Fa0/1
Suppose the preceding switch received a frame with the following MAC addresses:
Source MAC: 0005.dccb.d74b
Destination MAC: 000a.f467.9e8c
How will the switch handle this frame? Answer: the destination MAC address will be found in the MAC address table, and the frame will be forwarded out Fa0/3 only. Remember that if the destination MAC address is not found in the forward/filter table, it will forward the frame out all ports of the switch looking for the destination device. Now that you can see the MAC address table and how switches add hosts addresses to the forward filter table, how can you secure unauthorized users from just plugging a hub or access point into an open switch port?
Port Security
Okay—So just how do you stop someone from simply plugging a host into one of your switch ports—or, worse, adding a hub, switch, or access point into the Ethernet jack in their office? By default, MAC addresses will just dynamically appear in your MAC forward/filter database. You can stop them in their tracks by using port security, which prevents unauthorized hosts from accessing the LAN.
Here are your options:
Switch#config t Switch(config)#int f0/1 Switch(config-if)#switchport port-security ? aging Port-security aging commands mac-address Secure mac address maximum Max secure addresses violation Security violation mode <cr>
You can see clearly in the preceding output that the switchport port-security command can be used with four options. Personally, I like the port-security command because it allows me to easily control users on my network. You can use the switchport port-security mac-address mac-address command to assign individual MAC addresses to each switch port, but if you choose to go there, you'd better have a lot of time on your hands!
If you want to set up a switch port to allow only one host per port and to shut down the port if this rule is violated, use the following commands:
Switch#config t Switch(config)#int f0/1 Switch(config-if)#switchport port-security maximum 1 Switch(config-if)#switchport port-security violation shutdown
These commands are probably the most popular because they prevent users from connecting to a switch or access point that's in their office. The maximum setting of 1 means only one MAC address can be used on that port; if the user tries to add another host on that segment, the switch port will shut down. If that happens, you'd have to manually go into the switch and enable the port with a no shutdown command.
Probably one of my favorite commands is the sticky command. Not only does it perform a cool function, but it's got a cool name! You can find this command under the mac-address command.
Switch(config-if)#switchport port-security mac-address sticky Switch(config-if)#switchport port-security maximum 2 Switch(config-if)#switchport port-security violation shutdown
Basically, what this does is provide static MAC address security without having to type in everyone's MAC address on the network. As I said—cool!
In the preceding example, the first two MAC addresses into the port “stick” as static addresses and will stay that way for however long you set the aging command for. Why did I set it to 2? Well, I needed one for the PC/data and one for telephony/phone.
 More detail regarding port security can be found in Chapter 9, “Security.”
More detail regarding port security can be found in Chapter 9, “Security.”