Virtual Private Networks
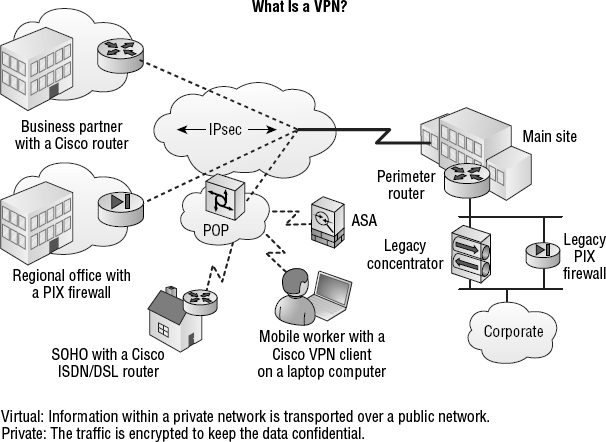
I'd be pretty willing to bet you've heard the term VPN more than once. Maybe you even know what one is, but just in case, a virtual private network (VPN) allows the creation of private networks across untrusted networks, enabling privacy and tunneling of non-TCP/IP protocols. Figure 9.2 shows the typical VPN network in use today.
VPNs are used daily to give remote users and disjointed networks connectivity over a public medium like the Internet instead of using more expensive permanent means. For example, instead of shelling out for a point-to-point connection between two sites (which is pretty secure in itself), you can use a less-expensive Internet connection to each site and then run a VPN tunnel between the sites. These are the benefits of a VPN for a typical small to large business:
- Cost
- Security
- Scalability
FIGURE 9.2 A typical VPN network
There are three different categories of VPNs, based upon the role they play in a business.
Remote Access VPNs Remote access VPNs allow remote users like telecommuters to securely access the corporate network wherever and whenever they need.
Site-to-Site VPNs Site-to-site VPNs, or intranet VPNs, allow a company to connect its remote sites to the corporate backbone securely over a public medium like the Internet instead of requiring more expensive WAN connections such as MPLS or Frame Relay. You would install a Cisco Adaptive Security Appliance at a branch office to enable and mange an IPsec site-to-site VPN.
Extranet VPNs Extranet VPNs allow an organization's suppliers, partners, and customers to be connected to the corporate network in a limited way for business-to-business (B2B) communications.
 A typical branch office would use a Cisco Adaptive Security Appliance to connect VPN tunnels to the corporate network across the public internet.
A typical branch office would use a Cisco Adaptive Security Appliance to connect VPN tunnels to the corporate network across the public internet.
IPsec
There's more than one way to bring a VPN into being. The first approach uses IPsec to create authentication and encryption services between endpoints on an IP network. The IPsec protocol suite is an open standard protocol framework that is commonly used in VPNs to provide secure end-to-end connections.
The second way is done via tunneling protocols, allowing you to establish a tunnel between endpoints on a network. The tunnel itself is a means for data or protocols to be encapsulated inside another protocol—clean!
However, what I want to discuss in this section of this chapter is the IPsec security services that are provided to a VPN. Here are the most common services and protocols used for these services:
- Confidentiality (encryption)
- Data integrity (verify data wasn't altered)
- Authentication (certify the source)
Confidentiality/Encryption When confidentiality is required, the Encapsulating Security Payload (ESP) IPsec security protocol should be used. ESP encrypts the payload of the IP packet and is unencrypted at the other end of the tunnel.
Data Integrity HMAC-SHA-1 and RSA are two data integrity algorithms that are commonly used in VPN solutions. HMAC-SHA-1 provides hashing of the data to verify the data was not altered along the way, and RSA provides encrypted key exchange between two peers so that each host has the key to unencrypt the data when received.
Authentication The authentication component of VPN technology ensures that data can be read only by its intended recipient by using Pre-Shared Key (PSK) or RSA signatures.