CHAPTER 4
Vulnerability Assessment Tools
In this chapter you will learn:
• When and how you can use different tools and technologies
• How to choose among similar tools and technologies
• How to review and interpret results of vulnerability scan reports
• How to use vulnerability assessment tools for specialized environments
We shape our tools and thereafter our tools shape us.
—Father John Culkin
The purpose of this chapter is to introduce you to (or perhaps reacquaint you with) vulnerability assessment tools with which you will need to be familiar for the CySA+ exam. We are not trying to provide a full review of each tool or even cover all the features. Instead, we give you enough information to help you understand the purpose of each tool and when you may want to use one over another. If you read about a tool for the first time in this chapter, you may want to spend more time familiarizing yourself with it before you take the exam. Given the diversity and scale of the modern network, making sense of the output of a vulnerability scan may be a daunting task. Fortunately, many tools deliver their comprehensive reports with visual tools and technical details behind the vulnerabilities they uncover. Understanding why vulnerabilities exist and how they can be exploited will assist you in analyzing the final scan report.
Some of the tools within a single category do pretty much the same thing, albeit in different ways. For each tool category, we provide an overview before comparing notable products in that class. We then provide an illustrative scenario that offers a more detailed description of each tool and how it fits in that scenario.
Web Application Scanners
Web application vulnerability scanners are automated scanning tools that scan web applications, normally from the outside, and from the perspective of a malicious user. Like other vulnerability scanners, they will scan only for vulnerabilities and malware for which plug-ins have been developed. Some of the most common types of vulnerabilities that scanners look for are listed here:
• Outdated server components
• Misconfigured server
• Secure authentication of users
• Secure session management
• Information leaks
• Cross-site scripting (XSS) vulnerabilities
• Improper use of HTTPS
Many commercial and open source web application vulnerability scanners are available. Most of them enable you to develop customized tests for your specific environment, so if you have some unique policies or security requirements that must be satisfied, it is worthwhile to learn how to write plug-ins or tests for your preferred scanner.
OWASP Zed Attack Proxy
The OWASP Zed Attack Proxy (ZAP) is one of the Open Web Application Security Project (OWASP) Foundation’s flagship projects, popular because of its powerful features. ZAP uses its position between the user’s browser and the web application to intercept and inspect user requests, modify the contents if required, and then forward them to a web server. This is exactly the same process that occurs during a man-in-the-middle attack. ZAP is designed to be used by security practitioners at all levels. Figure 4-1 shows the results of an attack conducted with nothing more than a target specified.
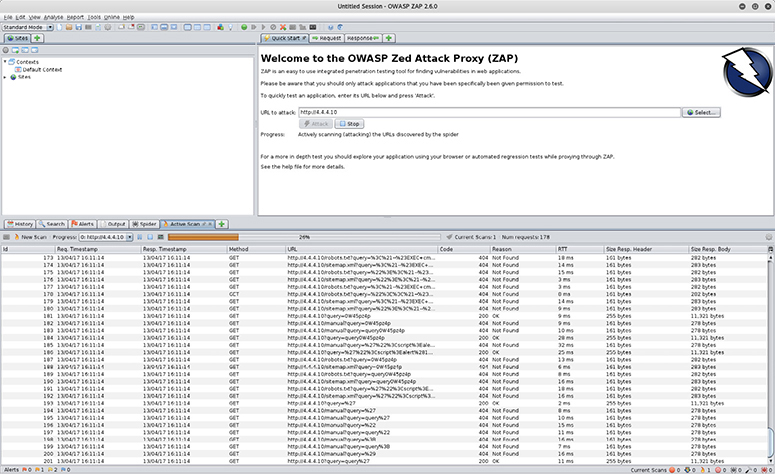
Figure 4-1 ZAP screen showing progress in an active scanning attack
In this example, ZAP rapidly fabricates a list of GET requests using known directories and files to test the site. These locations should not be publicly viewable, so the results here will inform an administrator of misconfigurations in the server and unexpected data exposure.
Burp Suite
Burp Suite is an integrated web application testing platform. Often used to map and analyze a web application’s vulnerabilities, Burp offers seamless use of automated and manual functions when finding and exploiting vulnerabilities. In proxy mode, Burp will enable the user to manually inspect every request passing through from the user to the server. Options to forward or drop the request are shown in Figure 4-2.

Figure 4-2 Burp Suite intercept screen and options in proxy mode
Although Burp is designed for a human to be in the decision loop, it does offer a point-and-click web-scanning feature in the paid version that may be useful.
Nikto
Nikto is a web server vulnerability scanner whose main strength is finding vulnerabilities such as SQL and command-injection susceptibilities, XSS, and improper server configuration. Although Nikto lacks a graphical interface as a command-line–executed utility, it’s able to perform thousands of tests very quickly and provides details on the nature of the weaknesses it finds. To conduct a scan against a web server, you specify the IP with the –host option enabled. By default, the results of the scan will be output to the same window. Although not practical for detailed analysis, Nikto is useful for quickly confirming the status of a host. By using other options in the command line, you can export the results to an output file for follow-up evaluation. Note that the output includes the type of vulnerability, a short description, and any reference information about the vulnerability.
Although its utility is limited to web servers, Nikto’s strength is its speed in assessing software vulnerabilities and configuration issues. As a command-line utility, it’s not as user friendly as some other tools. Nikto requires at least a target host to be specified, with any additional options, such as nonstandard ports, added in the command line. Figure 4-3 shows the command issued to perform a scan against a web team’s new site, which operates on port 3780.
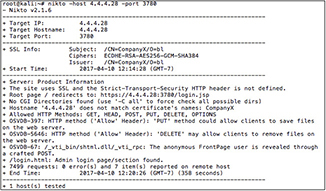
Figure 4-3 Nikto command-line output for a test against a web server located at IP 4.4.4.28
Nikto enables reports to be saved in a variety of ways, including HTML. An example of Nikto HTML test files is shown in Figure 4-4. This report includes a summary of the command issued, information about the servers tested, and hyperlinks to the relevant resources and their vulnerability data. Although this is good for technical teams to act on, it may not be as useful for nontechnical decision-makers.
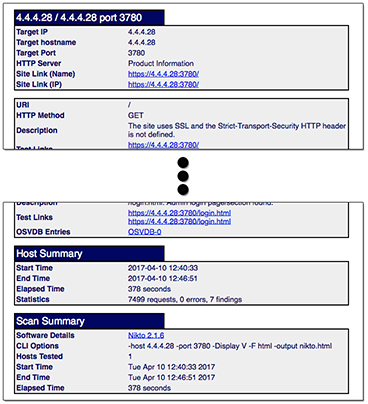
Figure 4-4 Nikto HTML output from a test against a web server located at IP 4.4.4.28
Arachni
Arachni is a Ruby-based, modular web app scanner with a special focus on speed. Unlike many other scanners, Arachni performs many of its scans in parallel, enabling the app to scale to large test jobs without sacrificing performance. The tool’s developer, Tasos Laskos, designed Arachni to train itself throughout its audits using several techniques. Among them is the tool’s ability to incorporate the feedback it gets from initial responses during the test to inform which new techniques should be used moving forward. In presenting the final results, Arachni is also able to reduce the occurrence of false positives through a process the author refers to as meta-analysis, which considers several factors from the tests responses. Arachni can perform audits for vulnerabilities including SQL injection, cross-site request forgery (CSRF), code injection, LDAP injection, path traversal, file inclusion, and XSS.
Despite being fairly performant, Arachni has few requirements to operate. It needs only a target URL to get started and can be initiated via a web interface or command line.
Infrastructure Vulnerability Scanners
Modern scanners cannot find weaknesses they’re not aware of or do not understand. The most popular vulnerability scanners have amassed enormous libraries of vulnerabilities that cover the vast majority of flaws most likely to be exploited. We’ll discuss a few popular vulnerability scanners in the next few pages. Many of these tools enable analysts to get a picture of the network from the perspective of an outsider as well as from a legitimate user. In the latter case, the scanner will most often perform an authenticated scan in one of two primary ways. The first method is to install local agents on the endpoints to synchronize with the vulnerability scan server and provide analysis on the endpoint during the course of the scan. The second method is to provide administrative credentials directly to the scanner, which it will invoke as necessary during the scan. It’s good practice to use both authenticated and unauthenticated scans during an assessment, because the use of one type may uncover vulnerabilities that would not be found by the other.
Nessus
Nessus, a popular and powerful scanner, began its life as an open source and free utility in the late 1990s and has since become a top choice for conducting vulnerability scans. With more than 80,000 plug-ins, Tenable’s Nessus enables users to schedule and conduct scans across multiple networks based on custom policies. Nessus includes basic port-scanning functionality. Its real power, however, lies in its multitude of features for vulnerability identification, misconfiguration detection, default password exposure, and compliance determination. The standard installation includes the Nessus server, which will coordinate the vulnerability scan, generate reports, and facilitate the vulnerability management feature. It can reside on the same machine as the Nessus web client or can be located elsewhere on the network. The client is designed to be run from the web interface, which enables the administrator to manipulate scan settings using any browser that supports HTML5.
Figure 4-5 shows the Nessus architecture being used against several targets on the network. Located on the Nessus server are the various plug-ins used in conducting assessments against the targets. With registration, Tenable provides updates of plug-ins and the server software often, usually once a day.
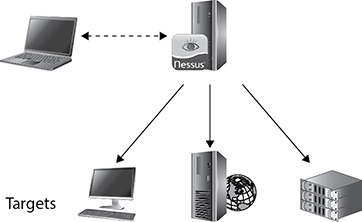
Figure 4-5 Nessus client/server architecture shown against several network targets
Assuming the server is running on the same local machine as the client, as is often the case, you can access the Nessus web interface by pointing your browser to http://localhost:8834, as shown in Figure 4-6. When you start Nessus for the first time, there is a bit of a delay for initial configuration, registration, and updating. Be patient, and you’ll soon be ready to conduct your first scan.

Figure 4-6 View of the initial Nessus loading from a standard web browser
Once the initial setup is complete, you can specify the details for any type of scan from the same interface. By default, the most popular scans are already enabled, but it’s good practice to walk through all the settings to learn what exactly will be happening on your network. Figure 4-7 shows the general Settings page, which provides space for a name and description of the scan. Scans created here can be used for immediate or scheduled action. Targets can be specified in one of several ways, including via a single IPv4 address, a single IPv6 address, a range of IPv4 or IPv6 addresses, or a hostname. In addition, the server will also correctly interpret classless inter-domain routing (CIDR) or netmask notation to specify IPv4 subnets. Nessus also provides a space to upload groups of specific target machines in ASCII text format, making it easy to reuse pre-populated lists. In this Settings page, you can also set schedules for scans, adjust notification preferences, and define certain technical limits for the scan. Nessus classifies some plug-ins as dangerous, meaning that their use may cause damage to some systems in certain conditions. When you’re preparing to execute a scan, it may be useful to use the Nessus “safe checks” option to avoid launching potentially destructive attacks. We’ll step through setting up for a basic Nessus scan over the next few pages.

Figure 4-7 Nessus configuration screen before conducting a vulnerability scan
Nessus allows for great flexibility and depth in the scanning process. You can configure Nessus to pass along any credentials that may be useful. In the Credentials page, shown in Figure 4-8, there is space to configure credentials for Windows hosts. Nessus supports passing authentication for a wide range of cloud services, databases, hosts, network devices, and hypervisors.

Figure 4-8 Nessus Credentials page
In the Compliance page, shown in Figure 4-9, you can configure compliance checks for the scan. Included in the default installation are many preconfigured checks developed in-house or based on industry best practices and benchmarks. As an admin, you can also develop and upload your own custom configuration, called an audit file, for use in the compliance check. The audit file gives instructions used to assess the configuration of endpoints and network device systems against a compliance policy or for the presence of sensitive data.
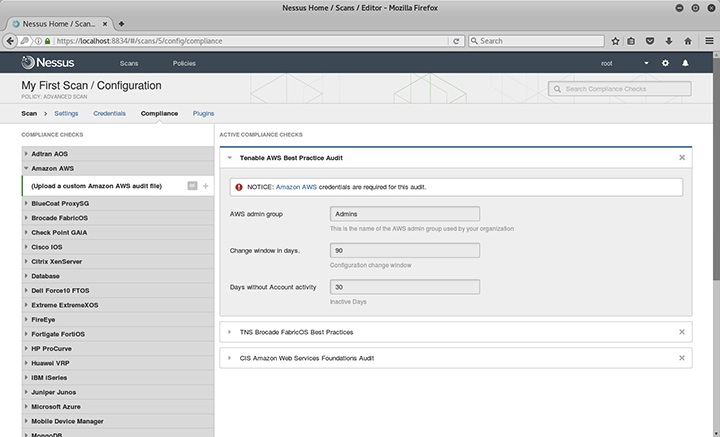
Figure 4-9 Nessus compliance checks with the Tenable AWS Best Practice Audit options displayed
When using compliance checks, you should be aware of some of the tradeoffs. Enabling these checks may slow down the scan, because many more aspects of the target system will be checked, and potentially at a deeper level. In some cases, active scanning may reduce functionality of both the client and target machines. Furthermore, these compliance checks may also be interpreted as intrusive by the target, which may trigger alerts on intermediate security devices and endpoint software.
On the next page, Plugins, you can see the status of all the plug-ins available for scanning. Nessus maintains a library of these small programs, which checks for known flaws. Plug-ins are written in the Nessus Attack Scripting Language (NASL) and contain information about the vulnerability, its remediation steps, and the mechanism that the plug-in uses to determine the existence of the vulnerability. Usually released within 24 hours of a public disclosure, plug-ins are constantly updated as part of the Nessus subscription. As shown in Figure 4-10, you can activate (or deactivate) any plug-ins required for the scan, or just get details into what exactly is performed by the plug-in during the assessment.
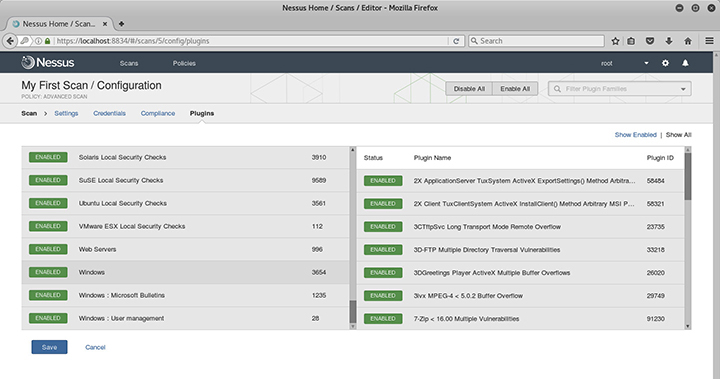
Figure 4-10 Nessus plug-in selection interface
With all the necessary settings saved, you can begin scanning targets for vulnerabilities. When Nessus discovers a vulnerability, it assigns a severity level to it in the scan results, as shown in Figure 4-11.
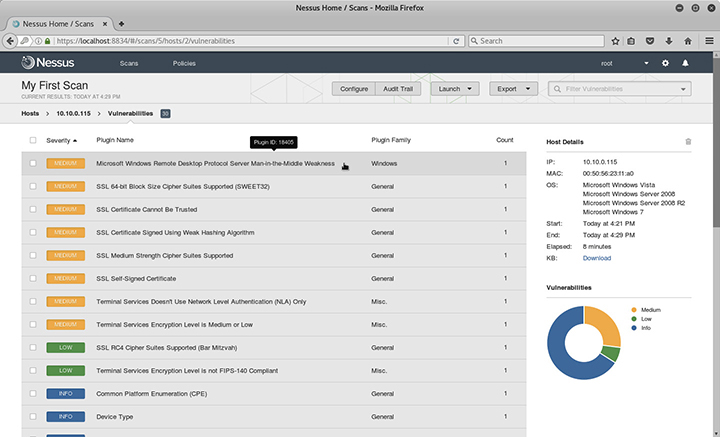
Figure 4-11 List of discovered vulnerabilities in the Nessus web interface
Technical details for each vulnerability, the method used in identifying it, and any database references are displayed here. Nessus is particularly strong at assessing compliance using its library of compliance checks. These compliance checks, or any other type of scan, can be scheduled to occur as desired, fulfilling your CISO’s desire to conduct periodic scans automatically. As for reports, Nessus offers several export options, as shown in Figure 4-12.

Figure 4-12 Nessus export options for report generation after a vulnerability scan
Nessus can generate reports that list only vulnerabilities with an associated exploit alongside suggested remediation steps. For an audience such as company leaders, explaining in plain language the concrete steps that may be taken to improve organizational security is key. Nessus provides these suggestions for individual hosts as well as for the network at large.
OpenVAS
The Open Vulnerability Assessment System, or OpenVAS, is a free framework that consists of several analysis tools for both vulnerability identification and management. OpenVAS is a fork of the original Nessus project that began shortly after Tenable closed development of the Nessus framework. OpenVAS is similar to Nessus in that it supports browser-based access to its OpenVAS Manager, which uses the OpenVAS Scanner to conduct assessments based on a collection of more than 47,000 network vulnerability tests (NVTs). Results of these NVTs are then sent back to the Manager for storage.
You can access OpenVAS’s interface by using a standard browser to access http://localhost:9392. Figure 4-13 shows the welcome screen from which an admin can access all settings for both the OpenVAS Manager and OpenVAS Scanner. There is also an empty field on the right side of the screen that can be used to launch quick scans.

Figure 4-13 OpenVAS welcome screen
OpenVAS also provides details on active NVTs used in the scan, as shown in Figure 4-14. You can see the status of each of the tests and, as with Nessus, get details on the test itself. In addition to the summary of the NVT, a vulnerability score is given, plus a level of confidence assigned to the detection method.

Figure 4-14 OpenVAS network vulnerability test families
Qualys
QualysGuard is a product of the California-based security company Qualys, an early player in the vulnerability management market. The company currently provides several cloud-based vulnerability assessment and management products through a Software as a Service (SaaS) model. For internal scans, a local virtual machine conducts the assessment and reports to the Qualys server. Figure 4-15 shows a QualysGuard dashboard with various options under the vulnerability management module.
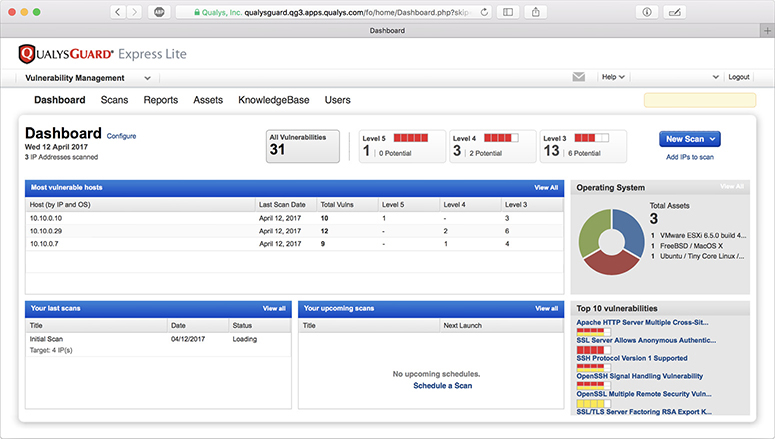
Figure 4-15 The QualysGuard dashboard for managing its cloud-based vulnerability assessment and management tasks
All network discovery, mapping, asset prioritization, scheduling, vulnerability assessment reporting, and remediation tracking tasks can be accessed via the web-based UI. The platform can generate detailed reports using several templates. Included in the default installation is a template called “Executive Report,” which provides just the type of data the CISO needs for her discussion. A portion of results of this report is shown in Figure 4-16.
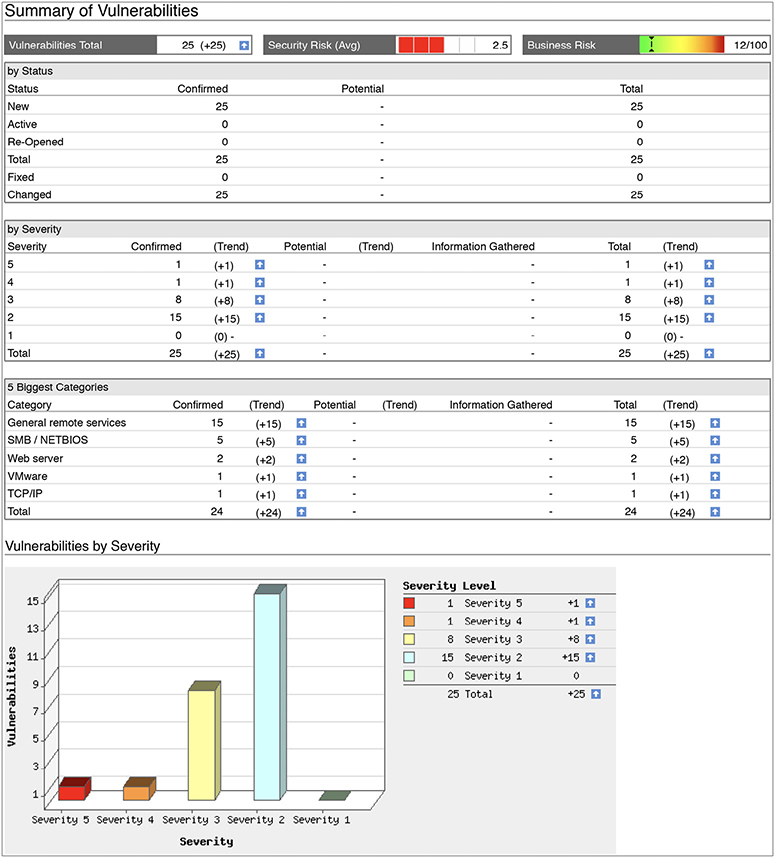
Figure 4-16 A portion of the QualysGuard report generated from the “Executive Report” template
Software Assessment Tools and Techniques
As software becomes larger and complex, the potential for vulnerabilities increases. Software vulnerabilities are part of the overall attack surface, and attackers waste no time discovering what flaws exist—in many cases using the techniques we’ll describe shortly. Software vulnerability detection methods usual fall into the categories of static analysis, dynamic analysis, reverse engineering, or fuzzing. These methods can be done separately or, ideally, together and as a part of a comprehensive software assessment process.
Static Analysis
Static code analysis is a technique meant to help identify software defects or security policy violations and is carried out by examining the code without executing the program (hence the term static). The term static analysis is generally reserved for automated tools that assist analysts and developers, whereas manual inspection by humans is generally referred to as code review. Because it is an automated process, static analysis enables developers and security staff to scan their source code quickly for programming flaws and vulnerabilities.
Figure 4-17 shows an example of a tool called Lapse+, which was developed by OWASP to find vulnerabilities in Java applications. This tool is highlighting an instance wherein user input is directly used, without sufficient validation, to build a SQL query against a database. In this particular case, this query is verifying the username and password. This insecure code block would allow a threat actor to conduct a SQL injection attack against this system. This actor would likely gain access by providing the string 'foo' OR 1==1 -- if the database was on a MySQL server.
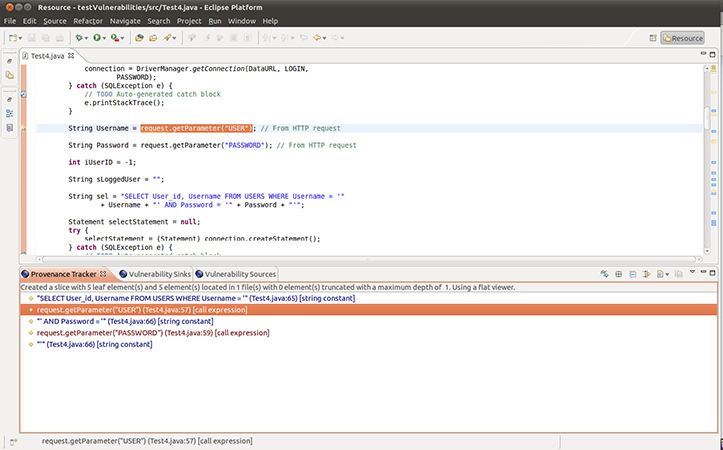
Figure 4-17 Code analysis of a vulnerable web application (Source: www.owasp.org)
Automated static analysis like that performed by Lapse+ provides a scalable method of security code review and ensures that secure coding policies are being followed. There are numerous manifestations of static analysis tools, ranging from tools that simply consider the behavior of single statements to tools that analyze the entire source code at once. However, you should keep in mind that static code analysis cannot usually reveal logic errors or vulnerabilities (that is, behaviors that are evident only at runtime) and therefore should be used in conjunction with manual code review to ensure a more thorough evaluation.
Dynamic Analysis
This method doesn’t really care about what the binary is, but rather what the binary does. Referred to as dynamic analysis, this method often requires a sandbox in which to execute the malware. This sandbox creates an environment that looks like a real operating system to the software and provides such things as access to a file system, network interface, memory, and anything else the software might need. Each request is carefully documented to establish a timeline of behavior that enables us to understand what it does. The main advantage of dynamic analysis is that it tends to be significantly faster and requires less expertise than alternatives. It can be particularly helpful for code that has been heavily obfuscated or is difficult to interpret. The biggest disadvantage is that dynamic analysis doesn’t reveal all that the software does, but simply all that it did during its execution in the sandbox.
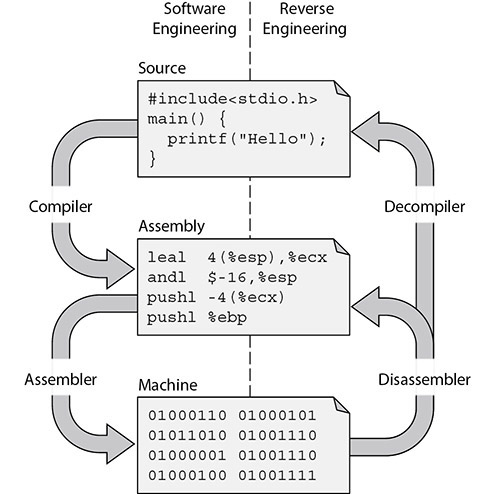
Reverse Engineering
Reverse engineering is the detailed examination of a product to learn what it does and how it works. In this approach to understanding what software is doing, a highly skilled analyst will either disassemble or decompile the binary code to translate its 1’s and 0’s into either assembly language or whichever higher level language it was created in. This enables a reverse engineer to see all possible functions of the software, not just those that it exhibited during a limited run in a sandbox. It is then possible, for example, to understand what kind of input is expected, discover dependencies, and highlight inefficient or dangerous techniques. It can be argued that static analysis is a subset, or supporting function, of an overall reverse engineering effort.
Fuzzing
Fuzzing is a technique used to discover flaws and vulnerabilities in software by sending large amounts of malformed, unexpected, or random data to the target program in order to trigger failures. Attackers could manipulate these errors and flaws to inject their own code into the system and compromise its security and stability. Fuzzing tools are commonly successful at identifying buffer overflows, denial of service (DoS) vulnerabilities, injection weaknesses, validation flaws, and other activities that can cause software to freeze, crash, or throw unexpected errors. Figure 4-18 shows a popular fuzzer called American Fuzzy Lop (AFL) crashing a targeted application.
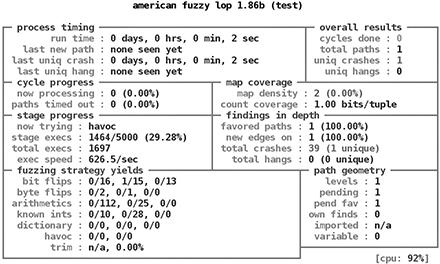
Figure 4-18 A fuzzer testing an application
Fuzzers don’t always generate random inputs from scratch. Purely random generation is known to be an inefficient way to fuzz systems. Instead, they often start with an input that is pretty close to normal and then make lots of small changes to see which ones seem more effective at exposing a flaw. Eventually, an input will cause an interesting condition in the target, at which point the security team will need a tool that can determine where the flaw is and how it could be exploited (if at all). This observation and analysis tool is often bundled with the fuzzer, because one is pretty useless without the other.
untidy
untidy is a popular Extensible Markup Language (XML) fuzzer. Used to test web application clients and servers, untidy takes valid XML and modifies it before inputting it into the application. The untidy fuzzer is now part of the Peach Fuzzer project.
Peach Fuzzer
The Peach Fuzzer is a powerful fuzzing suite that’s capable of testing a wide range of targets. Peach uses XML-based modules, called pits, to provide all the information needed to run the fuzz. These modules are configurable based on the testing needs. Before conducting a fuzz test, the user must specify the type of test, the target, and any monitoring settings desired.
Microsoft SDL Fuzzers
As part of its Security Development Lifecycle (SDL) toolset, Microsoft released two types of standalone fuzzers designed to be used in the verification phase of the SDL: the MiniFuzz File Fuzzer and the Regex Fuzzer. However, Microsoft has dropped support and no longer provides these applications for download.
Enumeration Tools and Techniques
Network enumeration is the interrogation of a set of hosts to look for specific information. A horizontal network scan, for instance, sends messages to a set of host addresses asking the question, “Are you there?” Its goal is to determine which addresses correspond to active (responding) systems. A vertical scan, on the other hand, sends messages to a set of protocol/port combinations (for example, UDP 53 or TCP 25) asking the same question, with the goal of determining which ports are listening for client connection attempts. It is possible to combine both horizontal and vertical scans, as shown in Figure 4-19. The point of a network scan of any flavor is to find out who is listening (and responding) on a network. This is useful in finding systems that are not behaving as they ought to.
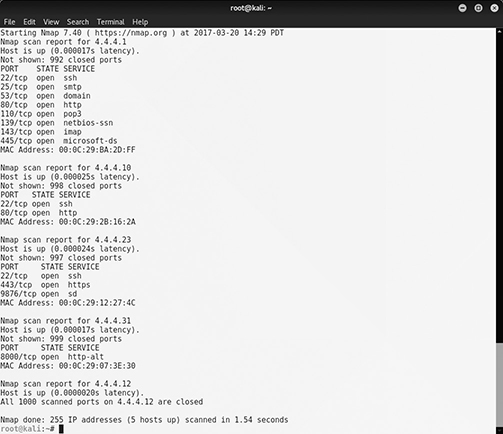
Figure 4-19 nmap performing both horizontal and vertical scans
Consider the case in which a software development team sets up a test web server to ensure that the web app on which the team members are working is functioning properly. There is no malice, but not knowing that this server is running (and how) could seriously compromise the integrity of the defenses. On the other hand, we can sometimes find evidence that a host has been compromised and is now running a malicious service. Though these situations should be rare in a well-managed network, scanning is one of the quintessential skills of any security professional, because it is one of very few ways to know and map what is really on our networks.
nmap
nmap, one of the most popular tools used for the enumeration of a targeted host, is synonymous with network scanning. The name is shorthand for “network mapper,” which is an apt description of what it does. nmap works by sending specially crafted messages to the target hosts and then examining the responses. This can tell not only which hosts are active on the network and which of their ports are listening, but it can also help us determine the operating system, hostname, and even patch level of some systems. Though nmap is a command-line interface (CLI) tool, a number of front ends provide a graphical user interface (GUI), including Zenmap (Windows), NmapFE (Linux), and Xnmap (macOS).
nmap scan results are not as rich in diverse content as those of other data sources, but they offer surgical precision for the information they do yield. Moreover, successive runs of nmap with identical parameters, together with a bit of scripting, enable the user to quickly identify changes to the configuration of a target. Attackers may be interested in new services because they are likelier to have exploitable configuration errors. Defenders, on the other hand, may be interested in new services because they could indicate a compromised host. nmap is even used by some organizations to inventory assets on a network by periodically doing full scans and comparing hosts and services to an existing baseline.
hping
Designed to provide advanced features beyond those offered from the built-in ping utility, hping is a useful enumeration tool that enables users to craft custom packets to assist with the discovery of network flaws, or it can be used by attackers to facilitate targeted exploit delivery. In addition to providing packet analysis functionality of TCP, UDP, and ICMP traffic, hping includes a traceroute mode and supports IP fragmentation. Figure 4-20 shows the output of a basic hping command targeting the loopback address.
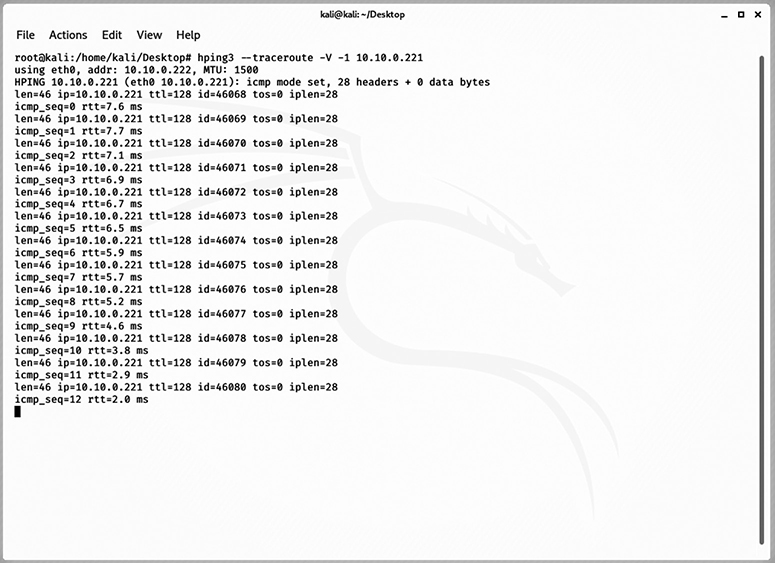
Figure 4-20 Output from hping performed against a host on the LAN
Passive vs. Active Enumeration Techniques
Passive enumeration techniques are used to gain information about the target without interfacing with or interrogating the target directly. In fact, access to the target isn’t necessarily required since alternative sources for target information are queried. Common examples include using a whois query, nslookup, or specialized tools like dnsrecon. A useful application of these tools for the purpose of vulnerability assessment could be to assist in discovery of what an asset looks like to outsiders. Figure 4-21 shows a dnsrecon lookup against google.com and provides a good deal of insight into the records associated with the company.

Figure 4-21 Output from dnsrecon performed against google.com
Active enumeration techniques involve interfacing directly with the target system. Port scanning is one of the most widely used active scanning techniques and uses any number of tools and techniques directly against a target to discover open ports and available services.
nslookup
The name server lookup, or nslookup, utility can be thought of as the user interface for Domain Name System (DNS). It enables us to resolve the IP address corresponding to a fully qualified domain name (FQDN) of a host. Depending on the situation, it is also possible to do the inverse (that is, resolve the IP address of an FQDN). The tool allows for the specification of a DNS server to be used, or it can use the system default. Lastly, it is possible to fully interrogate the target server and obtain other record data, such as Mail Exchange (MX) for e-mail or Canonical Name (CNAME).
responder
In the Windows environment, the Link-Local Multicast Name Resolution (LLMNR) protocol or NetBIOS Name Service (NBT-NS) can be used to query local computers on a LAN if a host is unable to resolve a hostname using DNS. If either of these two fallback protocols does not work, any host can respond with an answer that may be viewed as authoritative by the requesting machine. responder is a powerful tool that can be used to gain remote access by poisoning name services to gather hashes and credentials from systems within a LAN. Figure 4-22 is a snapshot of the responder reference page from the command line–based tool.
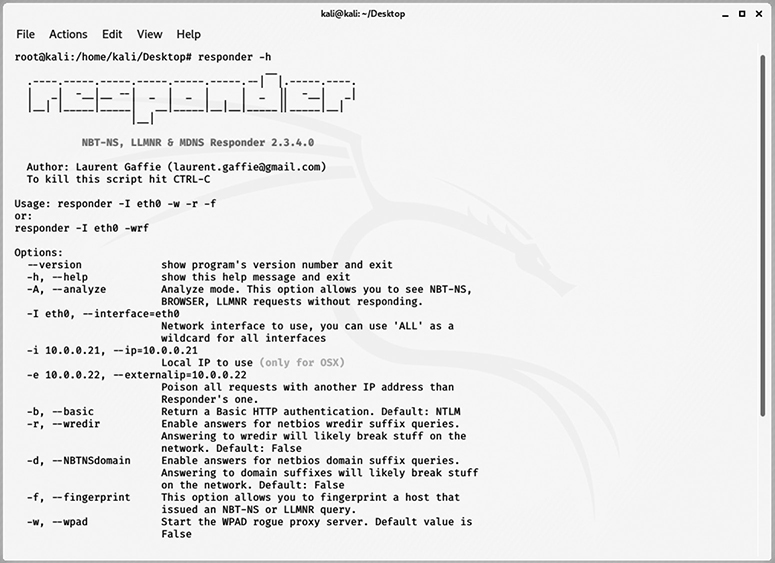
Figure 4-22 responder usage and options screen
Wireless Assessment Tools
It is difficult to run any kind of corporate network without considering the implications of wireless networks. Even if you don’t allow wireless devices at all (not even mobile phones) in your building, how would you know that the policy is being followed by all employees, all the time? Admittedly, most organizations will not (and often cannot) implement such draconian measures, which makes wireless local area network (WLAN) auditing and analysis particularly important.
To conduct a WLAN analysis, you must first capture data. Normally, when a WLAN interface card connects to a wireless access point (WAP), the client device will be in managed mode and the WAP will be in master mode. Master mode (also known as infrastructure mode) means that the interface will be responsible for managing all aspects of the WLAN configuration (such as channel and service set ID [SSID]). The client in managed mode is being managed by the master and thus will change channels or other settings when told to do so. Wireless interfaces can also communicate directly in mesh mode, which enables the interface to negotiate directly with another interface in a relationship that does not have master and managed nodes (also known as ad hoc mode). In each of these three modes, the interface will be limited to one connection to one network. To monitor multiple networks simultaneously, we need a fourth mode of operation. In monitor mode, the wireless interface will be able to see all available WLANs and their characteristics without connecting to any of them. This is the mode we need in order to perform a WLAN audit. Fortunately, WLAN analyzers, such as Kismet, take care of these details and enable us simply to run the application and see what is out there.
The most important step to a security analysis of your WLANs is to know your devices. Chief among these, of course, are the WAPs, but you must also keep track of wireless clients. How would you know that something odd is going on? Quite simply, by keeping track of what “normal” looks like. When analyzing the structure of WLANs, you must start from a known-good list of access points and client devices. Because, presumably, your organization installed (or had someone install) all the WAPs, you should have a record of their settings (for example, protocol, channel, and location) as well as their Media Access Control (MAC) and IP addresses. As you conduct your periodic audits, you will be able to tell if a new WAP shows up in your scan, potentially indicating a rogue access point.
Looking for rogue or unauthorized clients is a bit tricky because it is not difficult to change the MAC address on many networked devices. Indeed, all major operating systems have built-in tools that enable you to do just that. Because the main indicator of an end device’s identity is so susceptible to forgery, you may not be able to detect unauthorized nodes unless you implement some form of authentication, such as implementing WPA Enterprise and IEEE 802.1x. Absent authentication, you will have a very difficult time identifying all but the most naïve intruders connected to your WLAN.
Aircrack-ng
Aircrack-ng is the most popular open source wireless network security tool. Despite the name, the tool is actually a full-featured suite of wireless tools. It’s used primarily for its ability to audit the security of WLANs through attacks on WPA keys, replay attacks, deauthentication, and the creation of fake access points, as shown in Figure 4-23. In support of all of this functionality, Aircrack-ng also allows for indiscriminate wireless monitoring, packet captures, and, if equipped with the correct hardware, wireless injection.
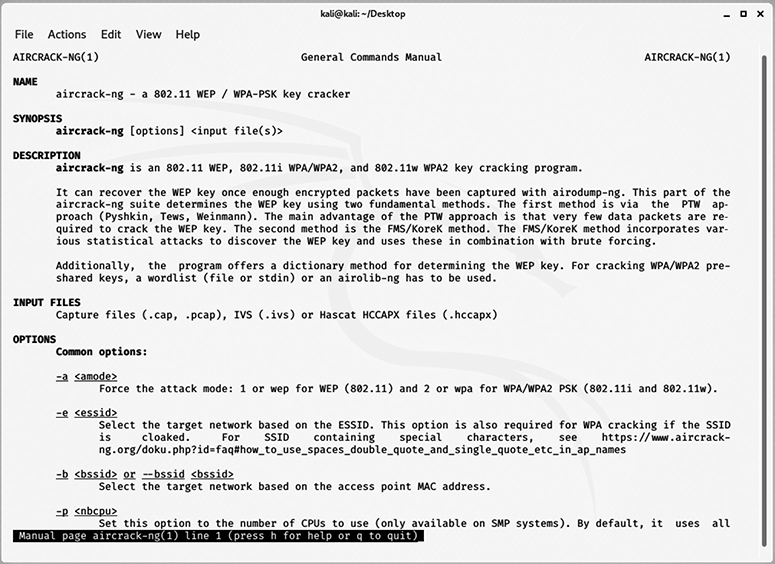
Figure 4-23 Aircrack-ng description and option screen
Reaver
It’s well known that many wireless security protocols have significant flaws associated with them, which may allow for an attacker to gain foothold into a network that’s within reach of a wireless signal. Reaver takes advantage of a vulnerability that exists in access points that use the Wi-Fi Protected Setup (WPS) feature. The WPS protocol emerged in the 2000s as a way for users to get set up on a network without having to remember complicated passwords or configuration settings. Unfortunately, a major flaw lies in the how WPS handles validation of the PIN. After splitting up the PIN into two halves, each portion is validated separately. This method significantly reduces the sample space, which Reaver leverages to guess the full password. As you can see from Figure 4-24, usage is straightforward. The analyst simply calls the command from the CLI, specifies the interface over which the attack will be delivered, and identifies the target access point. From a vulnerability management point of view, the solution is to disable WPS altogether.

Figure 4-24 Reaver standard and advanced options screen
oclHashcat
Recent developments in graphics card technology have allowed for incredibly detailed graphics on home PC and dedicated gaming rigs. The same array of processors powering those graphics cards has also enabled users to perform similar computationally intensive operations, such as password cracking, on the cheap. A few years ago, an analyst might be able to perform a successful password-cracking operation using one or two processors and the Hashcat utility in a matter of hours or days. Nowadays, the same cracking operation performed on a graphics card–optimized version called oclHashcat enables that analyst to complete the same task orders of magnitude faster. For the user, this means the time to recover passwords successfully goes from days to hours or minutes.
Hashcat supports many operating modes, character sets, and formats. A small sample of the operating modes that may be most useful to a security analyst are listed in Table 4-1.

Table 4-1 Selection of Operating Modes for Hashcat/oclHashcat
In addition to the robust mode support, Hashcat also supports the following attack modes:
• Brute-force attack
• Combinator attack
• Dictionary attack
• Hybrid attack
• Mask attack
• Rule-based attack
Figure 4-25 shows the output after initiating a dictionary brute-force attack on a list of hashes. Upon starting, Hashcat identifies suitable processor candidates to perform the password cracking. It then lists the unique digests, or hashes, on which the utility will operate. For the duration of the cracking operation, Hashcat will output useful statistics about its performance. This includes the estimated time of completion, cracking speed, and successfully recovered passwords.

Figure 4-25 Hashcat in operation against a list of MD5 hashes using two GPUs
In this example, we’ve specified that the successfully cracked passwords be outputted to a text file, shown in Figure 4-26. Note that the hash and its plaintext equivalent are placed side by side.

Figure 4-26 Contents of Hashcat output file
Cloud Infrastructure Assessment Tools
Although the elastic nature of cloud computing and storage makes for rapid scalability and efficiency, its dynamic nature also means you need to think about tracking and prioritizing vulnerabilities in a different way. Thankfully, with the rise of cloud services, several fantastic tools are now available to assess cloud host vulnerabilities caused by misconfigurations, access flaws, and custom deployments. Many of these tools automate monitoring against industry standards, compliance checklists, regulatory mandates, and best practices to prevent common issues such as data spillage and instance takeover.
Scout Suite
Scout Suite is an open source auditing tool developed by NCC Group, a security consulting company that specializes in verification, auditing, and managed services. With support for Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform, the tool enables security teams to determine the security posture of their cloud assets. It works by managing the interactions with could assets via the platform API, gathering information to make determinations of potentially vulnerable configurations. The results can be easily prepared for manual inspection or follow-up orchestration because of its structured format.
The tool requires a bit of preparation in the way of terms of service agreements and environmental setup, but usage is straightforward once configuration is in place. While Scout Suite ships with a default set of rules, the framework enables an analyst to provide custom rules to change the breadth of coverage during a scan. As shown the Figure 4-27, the rules are captured in a JSON file, which can be adjusted to the needs of the vulnerability team and specified during the utility’s execution.
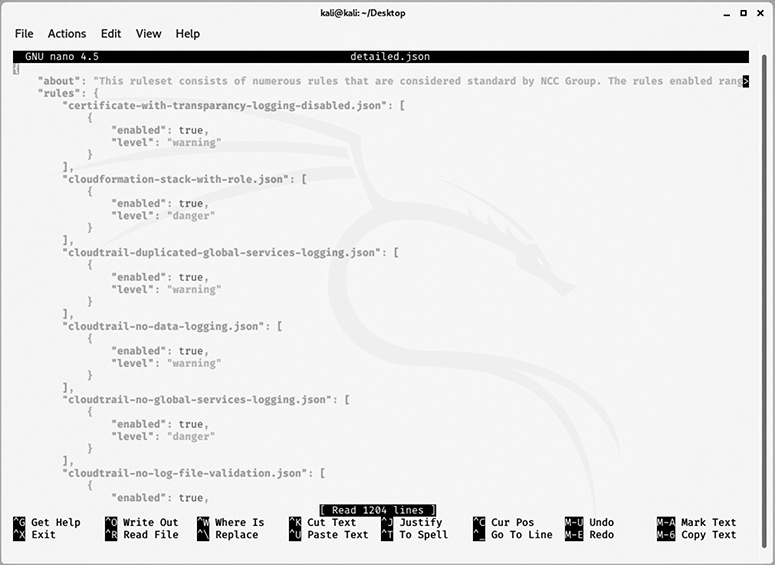
Figure 4-27 JSON file containing Scout Suite ruleset
Prowler
Similar to Scout Suite, Prowler is a framework designed as a scalable and repeatable method of acquiring measurable data related to the security readiness of your organization’s cloud infrastructure. Prowler assesses cloud assets based in part on the Center for Internet Security (CIS) best practices for configuring security options for various AWS resources. Like Scout Suite, Prowler offers a fair amount of configuration to allow the tool programmatic access via the Amazon API. Additionally, the AWS CLI will have to be installed on the machine or instance running the tool. Prowler allows for the definition of custom checks, but by default it ships with the following best practice test configurations, or “groups”:
• Identity and Access Management
• Logging
• Monitoring
• Networking
• CIS Level 1
• CIS Level 2
• Forensics
• GDPR
• HIPAA
Pacu
Rhino Security Labs, a boutique security services firm made famous by its cutting-edge cloud penetration testing services, released the AWS exploitation framework Pacu in 2018. Pacu is open source and has a modular architecture based on common syntax and data structure to allow for simple expansion of its features. A key difference between Pacu and other cloud-focused assessment tools is that it’s meant to be used in penetration tests and not just compliance checks. Accordingly, the framework makes it easy to document and export results in a manner familiar to those who frequently perform security engagements. Pacu is available via Rhino Lab’s GitHub page, along with all the documentation and initial configurations needed to get started testing instances and services. Pacu ships with more than 30 modules that enable a range of attacks, including user privilege escalation, enumeration, and attacking vulnerable Lambda functions. Each of the modules has comprehensive details about the module’s usage, as shown in Figure 4-28.

Figure 4-28 Pacu Help screen detailing usage of a plug-in module
Chapter Review
Vulnerability scanning is a key responsibility of any security team. Your taking the steps to understand and track the vulnerabilities your network faces is important in determining the best mitigation strategies. Keeping key stakeholders involved in the effort will also enable you to make decisions that are in the best interests of the organization. When you increase the visibility of the vulnerability status of your network, you ensure that your security team can focus its efforts in the right place and that leadership can devote the right resources to keeping the network safe. We covered several tools, including Nessus, OpenVAS, and Nikto, all of which provide vulnerability scan information using continuously updated libraries of vulnerability information. Some of these tools also offer the ability to automate the process and output in formats for ingestion in other IT systems. Vulnerability scanning is a continuous process, requiring your security team to monitor the network regularly to determine changes in detected vulnerabilities, gauge the efficacy of the patches and compensating controls, and adjust its efforts accordingly to stay ahead of threats.
As a CySA+, you should at least be familiar with every tool we described here, and, ideally, you should be proficient with each. Our goal was not to provide you with the depth of knowledge we believe you should possess on these tools, but rather to give a high-level survey of these essential tools of the trade. We hope that you will use this as a springboard for your own self-study into any products with which you are not familiar. Though the exam will require that you have only a general familiarity with these tools, your real-world performance will likely be enhanced by a deeper knowledge of these tools of the trade.
Questions
1. Which of the following is an example of an infrastructure vulnerability scanner?
A. Bro
B. Aircrack-ng
C. OpenVAS
D. Burp Suite
2. To what class of tools does Reaver belong?
A. Wireless assessment tools
B. Interception proxies
C. Enumeration tools
D. Exploitation frameworks
Use the following scenario to answer Questions 3–5:
Your company’s internal development team just developed a new web application for deployment onto the public-facing web server. You are trying to ensure that it conforms to best security practices and does not introduce any vulnerabilities into your systems.
3. Which would be the best tool to use if you want to ensure that the web application is not transmitting passwords in cleartext?
A. Nikto
B. Hashcat
C. Burp Suite
D. Aircrack-ng
4. Having tested the web application against all the input values you can think of, you decide to try random data to see if you can force instability or crashes. Which is the best tool for this purpose?
A. Untidy
B. hping
C. Nessus
D. Qualys
5. Your developer team is preparing to roll out a beta version of the software tomorrow and wants to quickly test for vulnerabilities including SQL injection, path traversal, and cross-site scripting. Which of the following tools do you recommend to them?
A. nmap
B. Arachni
C. Hashcat
D. nslookup
6. Which utility provides advanced features beyond those offered by the built-in network tools?
A. OpenVAS
B. Zed Attack Proxy
C. hping
D. nslookup
7. You have a list of password hashes, and you want to quickly assess and recover a password from each. Which is the most appropriate tool to use for this operation?
A. Hashcat
B. ifconfig
C. nslookup
D. MD5
8. Of the cloud infrastructure assessment tools we covered in this chapter, which of the following is designed as both a compliance assessment tool and penetration testing framework?
A. Pacu
B. Scout Suite
C. Reaver
D. Prowler
Answers
1. C. OpenVAS (in addition to Qualys, Nessus and Nikto) is an infrastructure vulnerability scanner with which you should be familiar.
2. A. Reaver is a wireless assessment tool that takes advantage of a vulnerability that exists in access points that use the Wi-Fi Protected Setup (WPS) feature.
3. C. Burp Suite is an integrated web application testing platform often used to map and analyze a web application’s vulnerabilities. It is able to intercept web traffic and enables analysts to examine each request and response.
4. A. The class of tools that tests applications by bombarding them with random values is called fuzzing tools. Untidy and Peach Fuzzer are all examples covered in this chapter.
5. B. Arachni has the ability to incorporate the feedback it gets from initial responses during the test to inform what new techniques should be used moving forward. In presenting the final results, Arachni is also able to reduce the occurrence of false positives through a process its author refers to as meta-analysis, which considers several factors from the tests responses.
6. C. hping is a free packet generator and network analyzer that supports TCP, UDP, and ICMP, and it includes a traceroute functionality.
7. A. Hashcat and its graphics card–optimized version oclHashcat are advanced password recovery tools that support a variety of operating modes, character sets, and formats.
8. A. Cloud infrastructure assessment tools assess cloud host vulnerabilities caused by misconfigurations, access flaws, and custom deployments, many times checking against industry standards and compliance checklists. Pacu performs these assessments and also enables penetration testers to exploit configuration flaws that are discovered.