31. Protecting Windows from Viruses and Spyware
Avoiding Viruses and Spyware: The Basics
Let’s begin with a look at protecting your PC from direct attacks: that is, when an unauthorized cracker (which we define as a hacker who has succumbed to the Dark Side of the Force) sits down at your keyboard and tries to gain access to your system. Sure, it may be unlikely that a malicious user would gain physical access to the computer in your home or office, but it’s not impossible.
Crackers specialize in breaking into systems (“cracking” system security, hence the name), and at any given time, hundreds (perhaps even thousands) of crackers roam cyberspace looking for potential targets. If you’re online right now, the restless and far-seeing eyes of the crackers are bound to find you eventually.
Sounds unlikely, you say? You wish. The crackers are armed with programs that automatically search through millions of IP addresses (the addresses that uniquely identify any computer or device connected to the Internet). The crackers are specifically looking for computers that aren’t secure, and if they find one, they’ll pounce on it and crack their way into the system.
Again, if all this sounds unlikely or that it would take them forever to find you, think again. Tests have shown that new and completely unprotected systems routinely get cracked within 20 minutes of connecting to the Internet!
First, a Few Simple Precautions
So how do you thwart the world’s crackers? We often joke that it’s easy if you follow a simple four-prong plan:
![]() Don’t connect to the Internet. Ever.
Don’t connect to the Internet. Ever.
![]() Don’t install programs on your computer. No, not even that one.
Don’t install programs on your computer. No, not even that one.
![]() Don’t let anyone else work with, touch, glance at, talk about, or come within 20 feet of your computer.
Don’t let anyone else work with, touch, glance at, talk about, or come within 20 feet of your computer.
![]() Burglar-proof your home or office.
Burglar-proof your home or office.
The point here is that if you use your computer (and live your life) in an even remotely normal way, you open up your machine to security risks. That’s a bleak assessment, for sure, but fortunately it doesn’t take a lot of effort on your part to turn your computer into a maximum-security area. The security techniques in this chapter (and the next three chapters) will get to that goal, but first make sure you’ve nailed down the basics:
![]() Leave User Account Control (UAC) turned on—Yes, we know UAC is a hassle, but if you’re coming to Windows 10 from Windows Vista, you’ll find that it’s way better now because it doesn’t get in your face nearly as often. UAC is the best thing that’s happened to Windows security in a long time, and it’s a fact of life that your computer is much more secure when UAC has got your back. See “Making Sure User Account Control Is Turned On,” later in this chapter.
Leave User Account Control (UAC) turned on—Yes, we know UAC is a hassle, but if you’re coming to Windows 10 from Windows Vista, you’ll find that it’s way better now because it doesn’t get in your face nearly as often. UAC is the best thing that’s happened to Windows security in a long time, and it’s a fact of life that your computer is much more secure when UAC has got your back. See “Making Sure User Account Control Is Turned On,” later in this chapter.
![]() Be paranoid—The belief that everyone’s out to get you may be a sign of trouble in the real world, but it’s just common sense in the computer world. Assume someone will sit down at your desk when you’re not around; assume someone will try to log on to your computer when you leave for the night; assume all uninvited email attachments are viruses; assume unknown websites are malicious; assume any offer that sounds too good to be true probably is.
Be paranoid—The belief that everyone’s out to get you may be a sign of trouble in the real world, but it’s just common sense in the computer world. Assume someone will sit down at your desk when you’re not around; assume someone will try to log on to your computer when you leave for the night; assume all uninvited email attachments are viruses; assume unknown websites are malicious; assume any offer that sounds too good to be true probably is.
![]() Keep to yourself—We all share lots of personal info online these days, but there’s sharing and then there’s asking-for-trouble sharing. Don’t tell anybody any of your passwords. Don’t put your email address online unless it’s disguised in some way (for example, by writing it as “username at yourdomain dot com”). Don’t give out sensitive personal data such as your Social Security number, bank account number, or even your address and phone number (unless making a purchase with a reputable vendor). Only give your credit card data to online vendors you trust implicitly; even better, get a secure PayPal account and use that instead.
Keep to yourself—We all share lots of personal info online these days, but there’s sharing and then there’s asking-for-trouble sharing. Don’t tell anybody any of your passwords. Don’t put your email address online unless it’s disguised in some way (for example, by writing it as “username at yourdomain dot com”). Don’t give out sensitive personal data such as your Social Security number, bank account number, or even your address and phone number (unless making a purchase with a reputable vendor). Only give your credit card data to online vendors you trust implicitly; even better, get a secure PayPal account and use that instead.
![]() Test the firewall—A firewall’s not much good if it leaves your computer vulnerable to attack, so you should test the firewall to make sure it’s doing its job. We show you several ways to do this in Chapter 33, “Protecting Your Network from Hackers and Snoops.”
Test the firewall—A firewall’s not much good if it leaves your computer vulnerable to attack, so you should test the firewall to make sure it’s doing its job. We show you several ways to do this in Chapter 33, “Protecting Your Network from Hackers and Snoops.”
![]() For the details on using Windows Firewall, see “Configuring Windows Firewall,” p. 405.
For the details on using Windows Firewall, see “Configuring Windows Firewall,” p. 405.
To access the router setup pages, open a web browser, type the router address, and then press Enter. See your device documentation for the correct URL, but for most routers the address is http://192.168.1.1, http://192.168.0.1, or http://192.168.2.1. In most cases, you must log in with a username and password, so, again, see your documentation.
![]() Take advantage of your router’s firewall, too—Why have one line of defense when in all probability you can have two? If your network has a router and that router connects to the Internet, then it, too, has an IP address that crackers can scan for vulnerabilities, particularly holes that expose your network. To prevent this, most routers come with built-in hardware firewalls that provide robust security. Access your router’s setup pages, locate the firewall settings (see Figure 31.1 for an example), and then make sure the firewall is turned on.
Take advantage of your router’s firewall, too—Why have one line of defense when in all probability you can have two? If your network has a router and that router connects to the Internet, then it, too, has an IP address that crackers can scan for vulnerabilities, particularly holes that expose your network. To prevent this, most routers come with built-in hardware firewalls that provide robust security. Access your router’s setup pages, locate the firewall settings (see Figure 31.1 for an example), and then make sure the firewall is turned on.
![]() Update, update, update—Many crackers take advantage of known Windows vulnerabilities to compromise a system. To avoid this, keep your PC updated with the latest patches, fixes, and service packs, many of which are designed to plug security leaks.
Update, update, update—Many crackers take advantage of known Windows vulnerabilities to compromise a system. To avoid this, keep your PC updated with the latest patches, fixes, and service packs, many of which are designed to plug security leaks.
![]() To learn more about keeping your PC updated, see “Configuring and Managing Windows Update,” p. 629.
To learn more about keeping your PC updated, see “Configuring and Managing Windows Update,” p. 629.
![]() Never open an email attachment that comes from someone you don’t know.
Never open an email attachment that comes from someone you don’t know.
![]() Even if you know the sender, check the message: If it’s vague or extremely short (or just doesn’t sound like the sender), you should be immediately suspicious about the attachment. Otherwise, if the attachment isn’t something you’re expecting, assume that the sender’s system is infected. Write back and confirm that the sender emailed the message.
Even if you know the sender, check the message: If it’s vague or extremely short (or just doesn’t sound like the sender), you should be immediately suspicious about the attachment. Otherwise, if the attachment isn’t something you’re expecting, assume that the sender’s system is infected. Write back and confirm that the sender emailed the message.
![]() Install a top-of-the-line antivirus program, particularly one that checks incoming email. In addition, be sure to keep your antivirus program’s virus list up to date. As you read this, there are probably dozens, maybe even hundreds, of morally challenged scumnerds designing even nastier viruses. Regular updates will help you keep up. Here are some security suites to check out:
Install a top-of-the-line antivirus program, particularly one that checks incoming email. In addition, be sure to keep your antivirus program’s virus list up to date. As you read this, there are probably dozens, maybe even hundreds, of morally challenged scumnerds designing even nastier viruses. Regular updates will help you keep up. Here are some security suites to check out:
Norton Security (www.symantec.com)
McAfee Internet Security Suite (www.mcafee.com)
Avast! Antivirus (www.avast.com)
AVG Internet Security (http://free.avg.com/)
![]() Assume the worst—Back up your data regularly, keep your receipts, keep all email correspondence, and read the fine print.
Assume the worst—Back up your data regularly, keep your receipts, keep all email correspondence, and read the fine print.
Locking Your Computer
In Chapter 32, “Protecting Your Data from Loss and Theft,” you learn a few more security tweaks, including important measures such as advanced file permissions and encryption. These two features are great, but they each have one small flaw: They rely on the assumption that after you’ve entered a legitimate username and password to log on to your Windows user account, only you will use your computer. This means that after you log on, you become a “trusted” user and you have full access to your files, even if they’re protected by permissions and encryption.
This assumption is certainly reasonable on the surface. After all, you wouldn’t want to have to enter your account credentials every time you want to open, edit, create, or delete a document. So while you’re logged on and at your desk, you get full access to your stuff.
But what happens when you leave your desk? If you remain logged on to Windows, any other person who sits down at your computer can take advantage of your trusted-user status to view and work with secure files (including copying them to a USB flash drive inserted by the snoop). This is what we mean by permissions and encryption having a flaw, and it’s a potentially significant security hole in large offices where it wouldn’t be hard for someone to pull up your chair while you’re stuck in yet another meeting.
One way to prevent this problem would be to turn off your computer every time you leave your desk. That way, any would-be snoop would have to get past your login to get to your files. This, obviously, is wildly impractical and inefficient.
Is there a better solution? You bet: You can lock your system before leaving your desk. Anyone who tries to use your computer must enter your password to access the Windows desktop.
Locking Your Computer Manually
Windows 10 gives you three ways to lock your computer before heading off:
![]() In the Start menu, click your username and then click Lock.
In the Start menu, click your username and then click Lock.
![]() Press Windows Logo+L, or right-click the Start button.
Press Windows Logo+L, or right-click the Start button.
![]() Press Ctrl+Alt+Delete, and then click Lock.
Press Ctrl+Alt+Delete, and then click Lock.
Whichever method you use, you end up at the Windows 10 Lock screen. Press any key to switch to the sign-in screen.
Locking Your Computer Automatically
The locking techniques from the previous section are easy enough to do, but the hard part is remembering to do them. If you’re late for a meeting or a rendezvous, locking up your machine is probably the last thing on your mind as you dash out the door. The usual course of events in these situations is that just as you arrive at your destination you remember that you forgot to lock your PC, and you then spend the next hour fretting about your defenseless computer.
To avoid the fretting (not to mention the possible intrusion), you can configure your computer to lock automatically after a period of inactivity. Here’s how it’s done:
1. In the taskbar’s Search box, type screen saver.
2. Click Change Screen Saver.
3. If you want to have a screen saver kick in after your PC is inactive for a while, select a screen saver from the Screen Saver list.
4. Check the On Resume, Display Logon Screen box.
5. Use the Wait spin box to set the interval (in minutes) of idle time that Windows 10 waits before locking your PC.
6. Click OK.
Requiring Ctrl+Alt+Delete at Startup
Protecting your Windows 10 user account with a password, though an excellent idea, is not foolproof. Hackers are an endlessly resourceful bunch, and some of the smarter ones figured out a way to defeat the user account password system. The trick is that they install a virus or Trojan horse program—usually via an infected email message or malicious website—that loads itself when you start your computer. This program then displays a fake version of the Windows 10 sign-in screen. When you type your username and password into this dialog box, the program records it and your system security is compromised.
To thwart this clever ruse, Windows 10 enables you to configure your system so that you must press Ctrl+Alt+Delete before you can sign in. This key combination ensures that the authentic sign-in screen appears.
To require that users must press Ctrl+Alt+Delete before they can sign in, follow these steps:
1. Press Windows Logo+R to display the Run dialog box.
2. Type control userpasswords2 and then click OK. The User Accounts dialog box appears.
4. Check the Require Users to Press Ctrl+Alt+Delete box.
5. Click OK.
Checking Your Computer’s Security Settings
Windows 10 comes with four security features enabled by default:
![]() Windows Firewall is turned on.
Windows Firewall is turned on.
![]() Windows Defender protects your computer against spyware in real time and by scanning your PC on a schedule.
Windows Defender protects your computer against spyware in real time and by scanning your PC on a schedule.
![]() User Account Control is turned on.
User Account Control is turned on.
![]() The Administrator account is disabled.
The Administrator account is disabled.
However, even though these are the default settings, they’re important enough not to be left to chance. The next four sections show you how to check that these crucial security settings really are enabled on your PC.
Making Sure Windows Firewall Is Turned On
By far the most important thing you need to do to thwart crackers is to have a software firewall running on your computer. A firewall is a security feature that blocks unauthorized attempts to send data to your computer. The best firewalls completely hide your computer from the Internet, so those dastardly crackers don’t even know you’re there! Windows Firewall is turned on by default, but you should periodically check this, just to be safe:
1. In the taskbar’s Search box, type firewall and then click Windows Firewall in the search results. The Windows Firewall window appears. Look at the Windows Firewall State value. If it says On, as shown in Figure 31.2, you’re fine; otherwise, continue to step 2.
2. Click the link Turn Windows Firewall On or Off. The Customize Settings window appears.
3. In the Private Network Settings section, activate the Turn On Windows Firewall option.
4. In the Public Network Settings section, activate the Turn On Windows Firewall option.
5. Click OK.
Making Sure Windows Defender Is Turned On
We’ve been troubleshooting Windows PCs for many years. It used to be that users accidentally deleting system files or making ill-advised attempts to edit the Registry or some other important configuration file caused most problems. Earlier versions of Windows (particularly XP) could either prevent these kinds of PEBCAK (Problem Exists Between Chair And Keyboard) issues or recover from them without a lot of trouble. However, we’re all too well aware of the latest menace to rise in the past few years, and it has taken over as the top cause of desperate troubleshooting calls we receive: malware, the generic term for malicious software such as viruses and Trojan horses.
The worst malware offender by far these days is spyware, a plague upon the earth that threatens to deprive a significant portion of the online world of its sanity. As often happens with new concepts, the term spyware has become encrusted with multiple meanings as people attach similar ideas to a convenient and popular label. However, spyware is generally defined as any program that surreptitiously monitors a user’s computer activities—particularly the typing of passwords, PINs, and credit card numbers—or harvests sensitive data on the user’s computer and then sends that information to an individual or a company via the user’s Internet connection (the so-called back channel) without the user’s consent.
You might think that having a robust firewall between you and the bad guys would make malware a problem of the past. Unfortunately, that’s not true. These programs piggyback on other legitimate programs that users actually want to download, such as file-sharing programs, download managers, and screensavers. A drive-by download is the download and installation of a program without a user’s knowledge or consent. This relates closely to a pop-up download—the download and installation of a program after the user clicks an option in a pop-up browser window, particularly when the option’s intent is vaguely or misleadingly worded.
To make matters even worse, most spyware embeds itself deep into a system, and removing it is a delicate and time-consuming operation beyond the abilities of even experienced users. Some programs actually come with an Uninstall option, but it’s nothing but a ruse, of course. The program appears to remove itself from the system, but what it actually does is a covert reinstall—it reinstalls a fresh version of itself when the computer is idle.
All this means that you need to buttress your firewall with an antispyware program that can watch out for these unwanted programs and prevent them from getting their hooks into your system. In versions of Windows prior to Vista, you needed to install a third-party program. However, Windows Vista came with an antispyware program named Windows Defender, and that tool remains part of Windows 10.
Windows Defender protects your computer from spyware in two ways. It can scan your system for evidence of installed spyware programs (and remove or disable those programs, if necessary), and it can monitor your system in real time to watch for activities that indicate the presence of spyware (such as a drive-by download or data being sent via a back channel).
If the real-time protection feature of Windows Defender is turned off, you usually see the notification message shown in Figure 31.3. Click that message to turn on real-time protection.
Figure 31.3 Windows 10 displays this notification if Windows Defender isn’t monitoring your system in real time for spyware.
If you don’t see that notification, launch Windows Defender by typing defender in the taskbar’s Search box and then clicking Windows Defender in the search results. In the Windows Defender status bar, which appears just below the title bar, if you see “PC status: At risk,” it means that Windows Defender is not actively guarding against virus and spyware activity.
Follow these steps to ensure that Windows Defender is actively monitoring your system for suspicious activity:
1. Click the Home tab.
2. Click Settings. The Settings app runs and displays the Windows Defender settings. (To get there without starting Windows Defender, click Start, Settings, click Update & Security, and then click Windows Defender.)
3. Click the Real-Time Protection switch to On.
Spyware Scanning
For the scanning portion of its defenses, Windows Defender supports three different scan types:
![]() Quick—This scan checks just those areas of your system where it is likely to find evidence of spyware. This scan usually takes just a couple of minutes. This scan is the default, and you can initiate one at any time by selecting the Home tab and then clicking Scan Now.
Quick—This scan checks just those areas of your system where it is likely to find evidence of spyware. This scan usually takes just a couple of minutes. This scan is the default, and you can initiate one at any time by selecting the Home tab and then clicking Scan Now.
![]() Full—This scan checks for evidence of spyware in system memory, all running processes, and the system drive (usually drive C), and it performs a deep scan on all folders. This scan might take 30 minutes or more, depending on your system. To run this scan, select the Home tab, activate the Full option, and then click Scan Now.
Full—This scan checks for evidence of spyware in system memory, all running processes, and the system drive (usually drive C), and it performs a deep scan on all folders. This scan might take 30 minutes or more, depending on your system. To run this scan, select the Home tab, activate the Full option, and then click Scan Now.
![]() Custom—This scan checks just the drives and folders you select. The length of the scan depends on the number of locations you select and the number of objects in those locations. To run this scan, select the Home tab, activate the Custom option, and then click Scan Now. This displays the dialog box shown in Figure 31.4. Check the boxes for the drives and folders you want scanned, and then click OK to start the scan.
Custom—This scan checks just the drives and folders you select. The length of the scan depends on the number of locations you select and the number of objects in those locations. To run this scan, select the Home tab, activate the Custom option, and then click Scan Now. This displays the dialog box shown in Figure 31.4. Check the boxes for the drives and folders you want scanned, and then click OK to start the scan.
Figure 31.4 Select the Custom option, and then click Scan Now to choose which drives and folders Windows Defender includes in the scan.
Windows Defender Settings
To configure Windows Defender, click Settings to open the Settings app. Click Update & Security and then Windows Defender to display the Windows Defender settings. You can then work with the following options:
![]() Real-Time Protection—This switch toggles real-time protection on and off.
Real-Time Protection—This switch toggles real-time protection on and off.
![]() Cloud-Based Protection—This switch toggles cloud protection on and off. When cloud protection is on, you authorize Windows 10 to send data on malicious activity to a Microsoft cloud network that analyzes the threat and (at least theoretically) enables Microsoft to respond more quickly to new problems.
Cloud-Based Protection—This switch toggles cloud protection on and off. When cloud protection is on, you authorize Windows 10 to send data on malicious activity to a Microsoft cloud network that analyzes the threat and (at least theoretically) enables Microsoft to respond more quickly to new problems.
![]() Sample Submission—When this switch is On, you authorize Windows 10 to anonymously send examples of infected files from your PC to Microsoft.
Sample Submission—When this switch is On, you authorize Windows 10 to anonymously send examples of infected files from your PC to Microsoft.
![]() Exclusions—Click the Add Exclusions link to specify files, folders, or system processes that you don’t want Windows Defender to scan.
Exclusions—Click the Add Exclusions link to specify files, folders, or system processes that you don’t want Windows Defender to scan.
![]() Use Windows Defender—Click this link to run Windows Defender.
Use Windows Defender—Click this link to run Windows Defender.
![]() Tip
Tip
Windows Defender will often warn you that a program might be spyware and ask whether you want to allow the program to operate normally or to block it. If you accidentally allow an unsafe program, click the History tab, select the Allowed Items option, and then click View Details. Select the program in the Allowed Items list, and then click Remove. Similarly, if you accidentally blocked a safe program, select the Quarantined Items option, click View Details, select the program in the Quarantined Items list, and then click Restore.
Making Sure User Account Control Is Turned On
We talk about User Account Control in detail later in this chapter. For now, let’s just make sure it’s enabled on your system:
1. In the taskbar’s Search box, type uac, and then click Change User Account Control Settings in the search results. The User Account Control Settings dialog box appears.
2. Make sure the slider is set to anything other than Never Notify at the bottom. Again, we explain the different settings a bit later. If you’re not sure what to go with, for now choose Default (second from the top).
3. Click OK.
4. Restart your computer to put the new setting into effect.
Making Sure the Administrator Account Is Disabled
One of the confusing aspects about Windows 10 is that the Administrator account seems to disappear after the setup is complete. That’s because, for security reasons, Windows 10 doesn’t give you access to this all-powerful account. (The initial account you set up has administrator permissions, but it’s not the account named Administrator.) However, there are ways to activate this account, so it pays to take a second and make sure it’s still in its disabled state.
You can do this in several ways, but here’s a quick look at two of them:
![]() Using the Local Security Policy Editor—In the taskbar’s Search box, type secpol.msc, and then click secpol. In the Local Security Policy window, open the Local Policies, Security Options branch, and then double-click the Accounts: Administrator Account Status policy. Click Disabled, and then click OK.
Using the Local Security Policy Editor—In the taskbar’s Search box, type secpol.msc, and then click secpol. In the Local Security Policy window, open the Local Policies, Security Options branch, and then double-click the Accounts: Administrator Account Status policy. Click Disabled, and then click OK.
![]() Using the Local Users and Groups snap-in—In the taskbar’s Search box, type lusrmgr.msc, and then click lusrmgr. In the Local Users and Groups snap-in, click Users and then double-click Administrator. In the Administrator Properties dialog box, check the Account Is Disabled box and then click OK.
Using the Local Users and Groups snap-in—In the taskbar’s Search box, type lusrmgr.msc, and then click lusrmgr. In the Local Users and Groups snap-in, click Users and then double-click Administrator. In the Administrator Properties dialog box, check the Account Is Disabled box and then click OK.
These methods both suffer from a serious drawback: They work only in Windows 10 Pro or Enterprise. Fortunately, we haven’t exhausted all the ways to activate Windows 10’s Administrator account. Here’s a method that works with all versions of Windows 10:
1. Press Windows Logo+X (or right-click the Start button) to display the Advanced Tools menu.
2. Click Command Prompt (Admin). The User Account Control dialog box appears.
3. Enter your UAC credentials to continue.
4. At the command line, enter the following command:
net user Administrator /active:no
Understanding User Account Control (UAC)
Most (we’re actually tempted to say the vast majority) of the security-related problems in versions of Windows prior to Vista boiled down to a single root cause: Most users were running Windows with administrator-level permissions. Administrators can do anything to a Windows machine, including installing programs, adding devices, updating drivers, installing updates and patches, changing Registry settings, running administrative tools, and creating and modifying user accounts. This is convenient, but it leads to a huge problem: Any malware that insinuates itself onto your system will also be capable of operating with administrative permissions, thus enabling the program to wreak havoc on the computer and just about anything connected to it.
Windows Vista tried to solve this problem, and its solution was called User Account Control (UAC), which used a principle called the least-privileged user. The idea behind this is to create an account level that has no more permissions than it requires. Again, such accounts are prevented from editing the Registry and performing other administrative tasks. However, these users can perform other day-to-day tasks:
![]() Install programs and updates
Install programs and updates
![]() Add printer drivers
Add printer drivers
![]() Change wireless security options (such as adding a WEP or WPA key)
Change wireless security options (such as adding a WEP or WPA key)
The least-privileged user concept arrived in the form of a new account type called the standard user. This meant that Windows Vista had three basic account levels:
![]() Administrator account—This built-in account could do anything to the computer.
Administrator account—This built-in account could do anything to the computer.
![]() Administrators group—Members of this group (except the Administrator account) ran as standard users but could elevate their privileges when required just by clicking a button in a dialog box (see the next section).
Administrators group—Members of this group (except the Administrator account) ran as standard users but could elevate their privileges when required just by clicking a button in a dialog box (see the next section).
![]() Standard Users group—These were the least-privileged users, although they, too, could elevate their privileges when needed. However, they required access to an administrator password to do so.
Standard Users group—These were the least-privileged users, although they, too, could elevate their privileges when needed. However, they required access to an administrator password to do so.
However, if there was a problem with the UAC implementation in Vista, it was that it was a tad, well, enthusiastic (to put the best face on it). Any minor setting change (even changing the date or time) required elevation, and if you were a dedicated settings changer, UAC probably caused you to tear out more than a few clumps of hair in frustration.
The good (some would say great) news in Windows 7 was that Microsoft did two things to rein in UAC:
![]() It made UAC configurable so that you could tailor the notifications to suit your situation.
It made UAC configurable so that you could tailor the notifications to suit your situation.
![]() It set up the default configuration of UAC so that it only rarely prompted you for elevation when you changed the settings on your PC. Two notable (and excusable) exceptions were when you changed the UAC configuration itself and when you started the Registry Editor.
It set up the default configuration of UAC so that it only rarely prompted you for elevation when you changed the settings on your PC. Two notable (and excusable) exceptions were when you changed the UAC configuration itself and when you started the Registry Editor.
Elevating Privileges
The idea of elevating privileges is at the heart of the UAC security model. In Windows XP, you could use the Run As command to run a task as a different user (that is, one with higher privileges). In Windows 10 (as with Windows 8/8.1, Windows 7, and Vista), you usually don’t need to do this because Windows 10 prompts you for the elevation automatically.
With your main Windows 10 user account (which, again, is a member of the Administrators group), you run with the privileges of a standard user for extra security. When you attempt a task that requires administrative privileges, Windows 10 prompts for your consent by displaying a User Account Control dialog box similar to the one shown in Figure 31.5 (we’re assuming here that you’re using the default UAC setting). Click Yes to permit the task to proceed. If this dialog box appears unexpectedly instead of in response to an action you’ve just taken, it’s possible that a malware program is trying to perform some task that requires administrative privileges; you can thwart that task by clicking No instead.
Figure 31.5 When your main Windows 10 administrative account launches a task that requires elevated privileges, Windows 10 displays this dialog box to ask for consent.
If you’re running as a standard user and attempt a task that requires administrative privileges, Windows 10 uses an extra level of protection. That is, instead of just prompting you for consent, it prompts you for the password of the main administrative account, as shown in Figure 31.6. Type the password for the main administrative account, and then click Yes. Again, if this dialog box shows up unexpectedly, it might be malware, so you should click No to prevent the task from going through.
Figure 31.6 When a standard user launches a task that requires administrative privileges, Windows 10 displays this dialog box to ask for administrative credentials.
Note, too, that in both cases Windows 10 switches to secure desktop mode, which means that you can’t do anything else with Windows 10 until you give your consent or credentials or cancel the operation. Windows 10 indicates the secure desktop by darkening everything on the screen except the User Account Control dialog box.
It’s also possible to elevate your privileges for any individual program. In File Explorer, you do this either by right-clicking the program file or shortcut, or by clicking the file and then clicking the Manage tab, and then clicking Run as Administrator.
Configuring User Account Control
As we mentioned earlier, Windows 10 supports a configurable UAC so that you can set it to a level that you’re comfortable with. Here’s how to configure UAC in Windows 10:
1. In the taskbar’s Search box, type uac, and then click Change User Account Control Settings in the search results. The User Account Control Settings window appears, as shown in Figure 31.7.
Figure 31.7 In Windows 10, you can use the User Account Control Settings window to set up UAC as you see fit.
2. Use the slider to choose one of the following four UAC settings:
![]() Always Notify—This is the top level, and it works much like UAC in Windows Vista in that you’re prompted for elevation when you change Windows settings, and when programs try to change settings and install software.
Always Notify—This is the top level, and it works much like UAC in Windows Vista in that you’re prompted for elevation when you change Windows settings, and when programs try to change settings and install software.
![]() Default—This is the second highest level, and it prompts you for elevation only when programs try to change settings and install software. This level uses secure desktop mode to display the UAC dialog box.
Default—This is the second highest level, and it prompts you for elevation only when programs try to change settings and install software. This level uses secure desktop mode to display the UAC dialog box.
![]() No Secure Desktop—This is the second lowest level, and it’s the same as the Default level (that is, it prompts you for elevation only when programs try to change settings and install software), but this level doesn’t use secure desktop mode when displaying the UAC dialog box.
No Secure Desktop—This is the second lowest level, and it’s the same as the Default level (that is, it prompts you for elevation only when programs try to change settings and install software), but this level doesn’t use secure desktop mode when displaying the UAC dialog box.
![]() Never Notify—This is the bottom level, and it turns off UAC. Of course you, as a responsible PC user, would never select this setting, right? We figured as much.
Never Notify—This is the bottom level, and it turns off UAC. Of course you, as a responsible PC user, would never select this setting, right? We figured as much.
3. Click OK. The User Account Control dialog box appears.
4. Enter your UAC credentials to put the new setting into effect.
Setting User Account Control Policies
You can customize User Account Control to a certain extent by using local group policies. In the Local Security Settings snap-in (In the taskbar’s Search box, type secpol.msc and then click secpol), open the Local Policies, Security Options branch. Here, you’ll find 10 policies related to User Account Control:
![]() User Account Control: Admin Approval Mode for the Built-in Administrator Account—This policy controls whether the Administrator account falls under User Account Control. If you enable this policy, the Administrator account is treated like any other account in the Administrators group and the user must click Continue in the consent dialog box when Windows 10 requires approval for an action.
User Account Control: Admin Approval Mode for the Built-in Administrator Account—This policy controls whether the Administrator account falls under User Account Control. If you enable this policy, the Administrator account is treated like any other account in the Administrators group and the user must click Continue in the consent dialog box when Windows 10 requires approval for an action.
![]() User Account Control: Allow UIAccess Applications to Prompt for Elevation Without Using the Secure Desktop—Use this policy to enable or disable whether Windows 10 allows elevation for accessibility applications that require access to the user interface of another window without using the secure desktop mode.
User Account Control: Allow UIAccess Applications to Prompt for Elevation Without Using the Secure Desktop—Use this policy to enable or disable whether Windows 10 allows elevation for accessibility applications that require access to the user interface of another window without using the secure desktop mode.
![]() User Account Control: Behavior of the Elevation Prompt for Administrators in Admin Approval Mode—This policy controls the prompt that appears when the main administrative account requires elevated privileges. The default setting is Prompt for Consent for Non-Windows Binaries, where the user clicks either Yes or No. You can also choose Prompt for Credentials to force the user to type her password. If you choose No Prompt, the main administrative account can’t elevate its privileges.
User Account Control: Behavior of the Elevation Prompt for Administrators in Admin Approval Mode—This policy controls the prompt that appears when the main administrative account requires elevated privileges. The default setting is Prompt for Consent for Non-Windows Binaries, where the user clicks either Yes or No. You can also choose Prompt for Credentials to force the user to type her password. If you choose No Prompt, the main administrative account can’t elevate its privileges.
![]() User Account Control: Behavior of the Elevation Prompt for Standard Users—This policy controls the prompt that appears when a standard user requires elevated privileges. For a more detailed look at this policy, see “Preventing Elevation for All Standard Users,” next.
User Account Control: Behavior of the Elevation Prompt for Standard Users—This policy controls the prompt that appears when a standard user requires elevated privileges. For a more detailed look at this policy, see “Preventing Elevation for All Standard Users,” next.
![]() User Account Control: Detect Application Installations and Prompt for Elevation—Use this policy to enable or disable automatic privilege elevation while installing programs.
User Account Control: Detect Application Installations and Prompt for Elevation—Use this policy to enable or disable automatic privilege elevation while installing programs.
![]() User Account Control: Only Elevate Executables That Are Signed and Validated—Use this policy to enable or disable whether Windows 10 checks the security signature of any program that asks for elevated privileges.
User Account Control: Only Elevate Executables That Are Signed and Validated—Use this policy to enable or disable whether Windows 10 checks the security signature of any program that asks for elevated privileges.
![]() User Account Control: Only Elevate UIAccess Applications That Are Installed in Secure Locations—Use this policy to enable or disable whether Windows 10 allows elevation for accessibility applications that require access to the user interface of another window only if they are installed in a secure location (such as the
User Account Control: Only Elevate UIAccess Applications That Are Installed in Secure Locations—Use this policy to enable or disable whether Windows 10 allows elevation for accessibility applications that require access to the user interface of another window only if they are installed in a secure location (such as the %ProgramFiles% folder).
![]() User Account Control: Run All Administrators in Admin Approval Mode—Use this policy to enable or disable running the main administrative account (excluding the Administrator account) as a standard user.
User Account Control: Run All Administrators in Admin Approval Mode—Use this policy to enable or disable running the main administrative account (excluding the Administrator account) as a standard user.
![]() Note
Note
File and Registry virtualization creates virtual %SystemRoot% and %ProgramFiles% folders as well as a virtual HKEY_LOCAL_MACHINE Registry key, all of which are stored with the user’s files. This enables a program installer to proceed without jeopardizing actual system files.
![]() User Account Control: Switch to the Secure Desktop When Prompting for Elevation—Use this policy to enable or disable whether Windows 10 switches to the secure desktop when the elevation prompts appear.
User Account Control: Switch to the Secure Desktop When Prompting for Elevation—Use this policy to enable or disable whether Windows 10 switches to the secure desktop when the elevation prompts appear.
![]() User Account Control: Virtualize File and Registry Write Failures to Per-User Locations—Use this policy to enable or disable file and Registry virtualization for standard users.
User Account Control: Virtualize File and Registry Write Failures to Per-User Locations—Use this policy to enable or disable file and Registry virtualization for standard users.
Preventing Elevation for All Standard Users
You saw earlier (in “Elevating Privileges”) that when a standard user attempts a task that requires elevation, he sees a UAC dialog box that requires an administrator password, and the screen switches to secure desktop mode.
There are two problems with this:
![]() Standard users almost never have the proper credentials to elevate an action.
Standard users almost never have the proper credentials to elevate an action.
![]() The combination of the sudden appearance of the User Account Control dialog box and the change into secure desktop mode is confusing for many users, particularly the inexperienced.
The combination of the sudden appearance of the User Account Control dialog box and the change into secure desktop mode is confusing for many users, particularly the inexperienced.
![]() Note
Note
These steps require the Local Security Settings snap-in, which is available only with Windows 10 Pro. If you’re not running this version, normally we’d show you how to modify the Registry to get the same effect. Unfortunately, the policy value we tweak here doesn’t have a Registry equivalent for security reasons.
These two problems mean that in most cases it would be better if standard users didn’t get prompted to elevate their privileges. Instead, it would be better to display an Access Denied message and let the users move on from there.
You can use the Local Security Settings snap-in to set this up. Here are the steps to follow:
1. From the Start screen, type secpol.msc and then click secpol. The Local Security Policy snap-in appears.
2. Open the Local Policies branch.
3. Click the Security Options branch.
4. Double-click the User Account Control: Behavior of the Elevation Prompt for Standard Users policy.
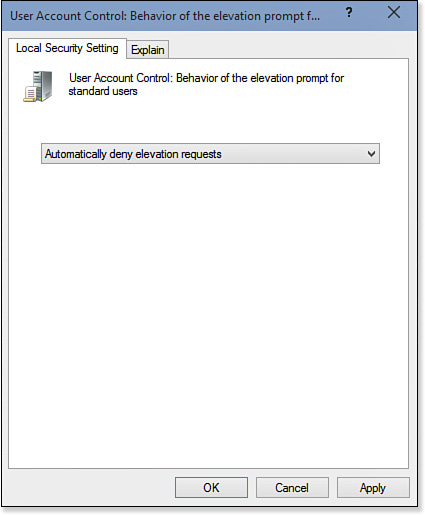
5. In the list, choose Automatically Deny Elevation Requests, as shown in Figure 31.8.
Figure 31.8 Open the User Account Control: Behavior of the Elevation Prompt for Standard Users policy and choose Automatically Deny Elevation Requests.
6. Click OK to put the new setting into effect.
Now when a standard user attempts something that requires elevated privileges, he just sees a simple dialog box like the one shown in Figure 31.9. Windows 10 doesn’t switch into secure desktop mode, and the user just has to click the command button to continue.
Figure 31.9 When standard users are denied elevation requests, they see a simple dialog box when they attempt an administrator-level task.
Enhancing Your Browsing Security
As more people, businesses, and organizations establish a presence online, the world becomes an increasingly connected place. And the more connected the world becomes, the more opportunities arise for communicating with others, doing research, sharing information, and collaborating on projects. The flip side to this new connectedness is the increased risk of connecting with a remote user whose intentions are less than honorable. The person at the other end of the connection could be a fraud artist who sets up a legitimate-looking website to steal your password or credit card number or a cracker who breaks in to your Internet account. It could be a virus programmer who sends a Trojan horse attached to an email or a website operator who uses web browser security holes to run malicious code on your machine.
While all this was happening, Microsoft’s operating systems seemed to become less secure. It’s difficult to say whether overall operating system security got worse with each new release, but it’s not hard to see that a perfect security storm was brewing:
![]() Thanks to the Internet, news of vulnerabilities spread quickly and efficiently.
Thanks to the Internet, news of vulnerabilities spread quickly and efficiently.
![]() An increasing number of malicious users online worked to exploit those vulnerabilities.
An increasing number of malicious users online worked to exploit those vulnerabilities.
![]() An increasing number of Windows users got online, most of whom didn’t keep up with the latest security patches from Microsoft.
An increasing number of Windows users got online, most of whom didn’t keep up with the latest security patches from Microsoft.
![]() An increasing number of online users had always-on broadband connections, which give malicious users more time to locate and break in to poorly patched machines.
An increasing number of online users had always-on broadband connections, which give malicious users more time to locate and break in to poorly patched machines.
So, even though it might have been the case that each new version of Windows was no less secure than its predecessors, it appeared that Windows was becoming increasingly vulnerable to attack.
Surfing the Web may be inherently unsecure, but fortunately Internet Explorer comes with lots of defensive weapons that you can deploy. The next few sections take a look at the most important ones.
Blocking Pop-Up Windows
Among the most annoying things on the Web are those ubiquitous pop-up windows that infest your screen with advertisements when you visit certain sites. (A variation on the theme is the pop-under, a window that opens under your current browser window, so you don’t know it’s there until you close the window.) Pop-up windows can also be dangerous because some unscrupulous software makers have figured out ways to use them to install software on your computer without your permission. They’re nasty things, any way you look at them.
Fortunately, Microsoft has given us a way to stop most pop-ups before they start. Internet Explorer comes with a feature called the Pop-up Blocker that looks for pop-ups and prevents them from opening. It’s not perfect (the occasional pop-under still breaks through the defenses), but it makes surfing sites much more pleasant. Follow these steps to use and configure the Pop-up Blocker:
1. In Internet Explorer, press Alt+T to open the Tools menu; then hover the mouse pointer over Pop-up Blocker.
2. If you see the command Turn Off Pop-up Blocker, skip to step 3; otherwise, select Turn On Pop-up Blocker, click Yes when Internet Explorer asks you to confirm, and then press Alt+T and click Pop-up Blocker.
3. Click Pop-up Blocker Settings to display the Pop-up Blocker Settings dialog box. You have the following options:
![]() Address of Web Site to Allow—Use this option when you have a site that displays pop-ups you want to see. Type the address and then click Add.
Address of Web Site to Allow—Use this option when you have a site that displays pop-ups you want to see. Type the address and then click Add.
![]() Play a Sound When a Pop-up Is Blocked—When this box is checked, Internet Explorer plays a brief sound each time it blocks a pop-up. In Internet Explorer 11 and later, you can’t uncheck this box.
Play a Sound When a Pop-up Is Blocked—When this box is checked, Internet Explorer plays a brief sound each time it blocks a pop-up. In Internet Explorer 11 and later, you can’t uncheck this box.
![]() Show Notification Bar When a Pop-up Is Blocked—When this box is checked, Internet Explorer displays a Notification bar message at the bottom of the window each time it blocks a pop-up so that you know it’s working on your behalf.
Show Notification Bar When a Pop-up Is Blocked—When this box is checked, Internet Explorer displays a Notification bar message at the bottom of the window each time it blocks a pop-up so that you know it’s working on your behalf.
![]() Blocking Level—Use this list to choose how aggressively you want it to block pop-ups: High (no pop-ups get through, ever), Medium (the default level, which blocks most—but not all—pop-ups), or Low (allows pop-ups from secure sites).
Blocking Level—Use this list to choose how aggressively you want it to block pop-ups: High (no pop-ups get through, ever), Medium (the default level, which blocks most—but not all—pop-ups), or Low (allows pop-ups from secure sites).
4. Click Close.
With the Pop-Up Blocker on the case, it monitors your surfing and steps in front of any pop-up window that tries to disturb your peace. A Notification bar appears at the bottom of the window to let you know that Pop-up Blocker thwarted a pop-up (see Figure 31.10). The Notification bar offers the following choices:
![]() Allow Once—Click this command to enable pop-ups on the site just this one time.
Allow Once—Click this command to enable pop-ups on the site just this one time.
![]() Options for This Site: Always Allow—Click this command to allow future pop-ups for the current domain.
Options for This Site: Always Allow—Click this command to allow future pop-ups for the current domain.
![]() Options for This Site: More Settings—Click this command to display the Pop-Up Blocker Settings dialog box.
Options for This Site: More Settings—Click this command to display the Pop-Up Blocker Settings dialog box.
Figure 31.10 When the Pop-up Blocker has your back, it displays the Notification bar each time it thwarts a pop-up.
Adding and Removing Zone Sites
When implementing security for Internet Explorer, Microsoft realized that different sites have different security needs. For example, it makes sense to have stringent security for Internet sites, but you can probably scale back the security a bit when browsing pages on your corporate intranet.
To handle these different types of sites, Internet Explorer defines various security zones, and you can customize the security requirements for each zone. To work with zones, select Tools, Internet Options, and then select the Security tab (see Figure 31.11) in the Internet Properties dialog box that appears.
Figure 31.11 Use the Security tab to set up security zones and customize the security options for each zone.
The list at the top of the dialog box shows icons for the four types of zones available:
![]() Internet—Websites that aren’t in any of the other three zones. The default security level is Medium-High.
Internet—Websites that aren’t in any of the other three zones. The default security level is Medium-High.
![]() Local Intranet—Web pages on your computer and your network (intranet). The default security level is Medium-Low.
Local Intranet—Web pages on your computer and your network (intranet). The default security level is Medium-Low.
![]() Trusted Sites—Websites that implement secure pages and that you’re sure have safe content. The default security level is Medium.
Trusted Sites—Websites that implement secure pages and that you’re sure have safe content. The default security level is Medium.
![]() Restricted Sites—Websites that don’t implement secure pages or that you don’t trust, for whatever reason. The default security level is High.
Restricted Sites—Websites that don’t implement secure pages or that you don’t trust, for whatever reason. The default security level is High.
Three of these zones—Local Intranet, Trusted Sites, and Restricted Sites—enable you to add sites. To do so, follow these steps:
1. Select the zone you want to work with and then click Sites.
2. If you selected Trusted Sites or Restricted Sites, skip to step 4. Otherwise, if you selected the Local Intranet zone, you see a dialog box with four check boxes. The Automatically Detect Intranet Network check box is unchecked by default. If you were to check it, Windows 10 would try to detect intranets automatically. We recommend leaving it unchecked, which gives you more detailed control by enabling the other three:
![]() Include All Local (Intranet) Sites Not Listed in Other Zones—When checked, this option includes all intranet sites in the zone. If you add specific intranet sites to other zones, those sites aren’t included in this zone.
Include All Local (Intranet) Sites Not Listed in Other Zones—When checked, this option includes all intranet sites in the zone. If you add specific intranet sites to other zones, those sites aren’t included in this zone.
![]() Include All Sites That Bypass the Proxy Server—When this box is checked, sites that you’ve set up to bypass your proxy server (if you have one) are included in this zone.
Include All Sites That Bypass the Proxy Server—When this box is checked, sites that you’ve set up to bypass your proxy server (if you have one) are included in this zone.
![]() Include All Network Paths (UNCs)—When this box is checked, all network paths that use the Universal Naming Convention are included in this zone. (UNC is a standard format used with network addresses. They usually take the form \server
esource, where server is the name of the network server and resource is the name of a shared network resource.)
Include All Network Paths (UNCs)—When this box is checked, all network paths that use the Universal Naming Convention are included in this zone. (UNC is a standard format used with network addresses. They usually take the form \server
esource, where server is the name of the network server and resource is the name of a shared network resource.)
![]() Note
Note
When typing an address, you can include an asterisk as a wildcard character. For example, the address http://*.microsoft.com adds every microsoft.com domain, including www.microsoft.com, support.microsoft.com, windowsupdate.microsoft.com, and so on.
3. To add sites to the Local Intranet zone, click Advanced.
4. Type the site’s address in the Add This Website to the Zone text box and then click Add.
5. If you make a mistake and enter the wrong site, select it in the Websites list and then click Remove.
6. Two of these dialog boxes (Local Intranet and Trusted Sites) have a Require Server Verification (https:) for All Sites In This Zone check box. If you check this option, each site you enter must use the secure HTTPS protocol.
7. Click Close.
Changing a Zone’s Security Level
To change the security level for a zone, select the zone and then use the Security Level for This Zone slider to set the level. To set up your own security settings, click Custom Level. This displays the Security Settings dialog box shown in Figure 31.12.
The Security Settings dialog box provides you with a long list of possible security issues, and your job is to specify how you want Internet Explorer to handle each issue. You usually have three choices:
![]() Disable—Security is on. For example, if the issue is whether to run an ActiveX control, the control does not run.
Disable—Security is on. For example, if the issue is whether to run an ActiveX control, the control does not run.
![]() Enable—Security is off. For example, if the issue is whether to run an ActiveX control, the control runs automatically.
Enable—Security is off. For example, if the issue is whether to run an ActiveX control, the control runs automatically.
![]() Prompt—Internet Explorer asks how you want to handle the issue (for example, whether you want to accept or reject an ActiveX control).
Prompt—Internet Explorer asks how you want to handle the issue (for example, whether you want to accept or reject an ActiveX control).
Protected Mode: Reducing Internet Explorer’s Privileges
Because spyware often leeches onto a system through a drive-by or pop-up download, it makes sense to set up the web browser as the first line of defense. Microsoft has done just that by including Protected mode for Internet Explorer. Protected mode builds on Windows 10’s User Account Control feature. Protected mode means that Internet Explorer runs with a privilege level that’s high enough to surf the Web, but that’s about it. Internet Explorer can’t install software without your permission, modify the user’s files or settings, add shortcuts to the Startup folder, or even change its own settings for the default home page and search engine. The Internet Explorer code is completely isolated from any other running application or process on your system. In fact, Internet Explorer can write data only to the Temporary Internet Files folder. If it needs to write elsewhere (during a file download, for example), it must get your permission. Therefore, Internet Explorer blocks any add-ons or other malware that attempts a covert install via Internet Explorer before they can even get to Windows Defender.
![]() Note
Note
If you don’t want to run Internet Explorer in Protected mode for some reason, you can turn it off. Select Tools, Internet Options, select the Security tab, and then click the Internet zone. Click the Enable Protected Mode check box to deactivate it, click OK, and then click OK again in the Warning! dialog box. You must restart Internet Explorer to activate this change. Then you will see a message in the Notification bar each time you restart Internet Explorer telling you that Protected mode is turned off for this zone. You are given the option to not see this message again or to turn on Protected mode.
Total Security: Internet Explorer Without Add-Ons
For the ultimate in browsing security, Windows 10 ships with an alternative Internet Explorer shortcut that loads the browser without any third-party add-ons, extensions, toolbars, or ActiveX controls. This shortcut is useful if you suspect your computer is infected with spyware that has hijacked your browser. This often means not only that the spyware has changed your home page, but in many cases the spyware also prevents you from accessing antispyware or antivirus sites. By running Internet Explorer without any add-ons, you effectively disable the spyware, and you can then surf to whatever site you need. Internet Explorer without add-ons is also completely safe from being infected with spyware, so running this version of Internet Explorer is useful if you’ll be surfing in darker areas of the Web where you suspect the possibility of infection is very high.
To run Internet Explorer without add-ons, follow these steps:
1. Press Windows Logo+R. The Run dialog box appears.
2. Type iexplore -extoff.
3. Click OK. Internet Explorer runs without loading any add-ons.
If you find yourself using this version of Internet Explorer regularly, consider creating a shortcut for it on the Start screen, as described (in a different context) in Chapter 4, “Using the Windows 10 Interface.”
![]() To learn how to add a shortcut tile to the Start screen, see “Adding Shutdown and Restart Shortcuts,” p. 124.
To learn how to add a shortcut tile to the Start screen, see “Adding Shutdown and Restart Shortcuts,” p. 124.
Understanding Internet Explorer’s Advanced Security Options
To close our look at Windows 10’s web security features, this section takes you through Internet Explorer’s Advanced security options. Select Tools, Internet Options, display the Advanced tab, and then scroll down to the Security section to see the following options:
![]() Allow Active Content from CDs to Run on My Computer—Leave this box unchecked to prevent active content such as scripts and controls located in CD-based web pages to execute on your computer. However, if you have a CD-based program that won’t function, you might need to check this box to enable the program to work properly.
Allow Active Content from CDs to Run on My Computer—Leave this box unchecked to prevent active content such as scripts and controls located in CD-based web pages to execute on your computer. However, if you have a CD-based program that won’t function, you might need to check this box to enable the program to work properly.
![]() Allow Active Content to Run in Files on My Computer—Leave this box unchecked to prevent active content, such as scripts and controls located in local web pages from executing on your computer. If you’re testing a web page that includes active content, check this box so that you can test the web pages locally.
Allow Active Content to Run in Files on My Computer—Leave this box unchecked to prevent active content, such as scripts and controls located in local web pages from executing on your computer. If you’re testing a web page that includes active content, check this box so that you can test the web pages locally.
![]() Allow Software to Run or Install Even If the Signature Is Invalid—Leave this box unchecked to avoid running or installing software that doesn’t have a valid digital signature. If you can’t get a program to run or install, consider checking this box.
Allow Software to Run or Install Even If the Signature Is Invalid—Leave this box unchecked to avoid running or installing software that doesn’t have a valid digital signature. If you can’t get a program to run or install, consider checking this box.
![]() Block Unsecured Images with Other Mixed Content—If you check this box, Internet Explorer looks for images that were delivered to the current secure (HTTPS) page via an unsecure (HTTP) source. If it detects such an image, it treats the entire page as unsecure. Unsecure images are not dangerous, so you shouldn’t have to activate this option.
Block Unsecured Images with Other Mixed Content—If you check this box, Internet Explorer looks for images that were delivered to the current secure (HTTPS) page via an unsecure (HTTP) source. If it detects such an image, it treats the entire page as unsecure. Unsecure images are not dangerous, so you shouldn’t have to activate this option.
![]() Check for Publisher’s Certificate Revocation—When this option is checked, Internet Explorer examines a site’s digital security certificates to see whether they have been revoked.
Check for Publisher’s Certificate Revocation—When this option is checked, Internet Explorer examines a site’s digital security certificates to see whether they have been revoked.
![]() Check for Server Certificate Revocation—If you check this option, Internet Explorer also checks the security certificate for the web page’s server.
Check for Server Certificate Revocation—If you check this option, Internet Explorer also checks the security certificate for the web page’s server.
![]() Check for Signatures on Downloaded Programs—If you check this box, Internet Explorer checks for a digital signature on any program that you download.
Check for Signatures on Downloaded Programs—If you check this box, Internet Explorer checks for a digital signature on any program that you download.
![]() Do Not Save Encrypted Pages to Disk—If you check this option, Internet Explorer won’t store encrypted files in the Temporary Internet Files folder.
Do Not Save Encrypted Pages to Disk—If you check this option, Internet Explorer won’t store encrypted files in the Temporary Internet Files folder.
![]() Empty Temporary Internet Files Folder When Browser Is Closed—With this option checked, Internet Explorer removes all files from the Temporary Internet Files folder when you exit the program.
Empty Temporary Internet Files Folder When Browser Is Closed—With this option checked, Internet Explorer removes all files from the Temporary Internet Files folder when you exit the program.
![]() Enable 64-bit Processes for Enhanced Protected Mode—If you check this box, Internet Explorer uses 64-bit tabs, which increases Enhanced Protected Mode security because 64-bit processes offer stronger protection against memory-related attacks. However, many ActiveX controls and other add-ons are not 64-bit, so activating this option could cause compatibility problems with some websites.
Enable 64-bit Processes for Enhanced Protected Mode—If you check this box, Internet Explorer uses 64-bit tabs, which increases Enhanced Protected Mode security because 64-bit processes offer stronger protection against memory-related attacks. However, many ActiveX controls and other add-ons are not 64-bit, so activating this option could cause compatibility problems with some websites.
![]() Enable DOM Storage—This option is activated by default, and it enables Internet Explorer to use the Document Object Model (DOM) to store website data on your computer. DOM storage is similar to cookie data, except that DOM storage spans multiple tabs and windows. DOM storage consists of both session storage, where data is saved only for the current browser session, and local storage, where data never expires and you can store up to 10MB of data. DOM storage is superior to cookies, so in most cases you should leave this setting activated. If you’re worried that having up to 10MB of site data on your computer represents a security or privacy risk, you can disable this option.
Enable DOM Storage—This option is activated by default, and it enables Internet Explorer to use the Document Object Model (DOM) to store website data on your computer. DOM storage is similar to cookie data, except that DOM storage spans multiple tabs and windows. DOM storage consists of both session storage, where data is saved only for the current browser session, and local storage, where data never expires and you can store up to 10MB of data. DOM storage is superior to cookies, so in most cases you should leave this setting activated. If you’re worried that having up to 10MB of site data on your computer represents a security or privacy risk, you can disable this option.
![]() Enable Enhanced Protected Mode—Check this box to use the Enhanced Protected Mode features in Internet Explorer 11. These new features include using 64-bit processes (which prevent attackers from planting malicious code on your system; see the last bulleted point on the previous page), preventing Internet Explorer from accessing your user account data unless you grant explicit permission for it to do so, and preventing Internet Explorer from accessing certain corporate intranet data. Many add-ons aren’t compatible with Enhanced Protected Mode, so you can turn off this setting if you’re worried about add-on compatibility. However, we strongly recommend leaving it on for safer browsing. Changing this setting requires you to restart Internet Explorer.
Enable Enhanced Protected Mode—Check this box to use the Enhanced Protected Mode features in Internet Explorer 11. These new features include using 64-bit processes (which prevent attackers from planting malicious code on your system; see the last bulleted point on the previous page), preventing Internet Explorer from accessing your user account data unless you grant explicit permission for it to do so, and preventing Internet Explorer from accessing certain corporate intranet data. Many add-ons aren’t compatible with Enhanced Protected Mode, so you can turn off this setting if you’re worried about add-on compatibility. However, we strongly recommend leaving it on for safer browsing. Changing this setting requires you to restart Internet Explorer.
![]() Enable Integrated Windows Authentication—With this box activated, Internet Explorer uses Integrated Windows Authentication (formerly known as Windows NT Challenge/Response Authentication) to attempt to log on to a restricted site. This means the browser attempts to log on using the current credentials from the user’s network domain logon. If this doesn’t work, Internet Explorer displays a dialog box prompting the user for a username and password.
Enable Integrated Windows Authentication—With this box activated, Internet Explorer uses Integrated Windows Authentication (formerly known as Windows NT Challenge/Response Authentication) to attempt to log on to a restricted site. This means the browser attempts to log on using the current credentials from the user’s network domain logon. If this doesn’t work, Internet Explorer displays a dialog box prompting the user for a username and password.
![]() Enable Native XMLHTTP Support—With this box checked, Internet Explorer works properly with sites that use the XMLHTTPRequest API to transfer XML data between the browser and a server. This API is most commonly used in Ajax-powered sites. Ajax (Asynchronous JavaScript and XML) is a web development technique that creates sites that operate much like desktop programs. In particular, the XMLHTTPRequest API enables the browser to request and accept data from the server without reloading the page.
Enable Native XMLHTTP Support—With this box checked, Internet Explorer works properly with sites that use the XMLHTTPRequest API to transfer XML data between the browser and a server. This API is most commonly used in Ajax-powered sites. Ajax (Asynchronous JavaScript and XML) is a web development technique that creates sites that operate much like desktop programs. In particular, the XMLHTTPRequest API enables the browser to request and accept data from the server without reloading the page.
![]() Enable SmartScreen Filter—This option toggles the SmartScreen phishing filter on and off.
Enable SmartScreen Filter—This option toggles the SmartScreen phishing filter on and off.
![]() Send Do Not Track Requests to Sites You Visit in Internet Explorer—When enabled, this setting tells Internet Explorer to send the Do Not Track (DNT) header on all HTTP and HTTPS requests. The DNT header tells the server that you don’t want to be tracked. If you uncheck this box, Internet Explorer sends the DNT header only when you’re using InPrivate Browsing mode or when you’re using a Tracking Protection List. You must restart Internet Explorer if you change this setting.
Send Do Not Track Requests to Sites You Visit in Internet Explorer—When enabled, this setting tells Internet Explorer to send the Do Not Track (DNT) header on all HTTP and HTTPS requests. The DNT header tells the server that you don’t want to be tracked. If you uncheck this box, Internet Explorer sends the DNT header only when you’re using InPrivate Browsing mode or when you’re using a Tracking Protection List. You must restart Internet Explorer if you change this setting.
![]() Use SSL 2.0—This check box toggles support for the Secure Sockets Layer Level 2 security protocol on and off. This version of SSL is currently the Web’s standard security protocol.
Use SSL 2.0—This check box toggles support for the Secure Sockets Layer Level 2 security protocol on and off. This version of SSL is currently the Web’s standard security protocol.
![]() Use SSL 3.0—This check box toggles support for SSL Level 3 on and off. SSL 3.0 is more secure than SSL 2.0 (it can authenticate both the client and the server) but isn’t currently as popular as SSL 2.0.
Use SSL 3.0—This check box toggles support for SSL Level 3 on and off. SSL 3.0 is more secure than SSL 2.0 (it can authenticate both the client and the server) but isn’t currently as popular as SSL 2.0.
![]() Use TLS 1.0—This check box toggles support for Transport Layer Security (TLS) version 1.0 on and off. TLS is the successor to SSL and is starting to be implemented more widely, which might be why Internet Explorer 11 checks this box by default, along with TLS 1.1 and TLS 1.2.
Use TLS 1.0—This check box toggles support for Transport Layer Security (TLS) version 1.0 on and off. TLS is the successor to SSL and is starting to be implemented more widely, which might be why Internet Explorer 11 checks this box by default, along with TLS 1.1 and TLS 1.2.
![]() Use TLS 1.1—This check box toggles support for TLS version 1.1. Check this option if you have trouble accessing a secure site (for example, if Internet Explorer displays an error telling you the site’s security certificate can’t be verified).
Use TLS 1.1—This check box toggles support for TLS version 1.1. Check this option if you have trouble accessing a secure site (for example, if Internet Explorer displays an error telling you the site’s security certificate can’t be verified).
![]() Use TLS 1.2—This check box toggles support for TLS version 1.2. Check this option if you have trouble accessing a secure site and enabling support for TSL 1.1 didn’t help.
Use TLS 1.2—This check box toggles support for TLS version 1.2. Check this option if you have trouble accessing a secure site and enabling support for TSL 1.1 didn’t help.
![]() Warn About Certificate Address Mismatch—When enabled, this option tells Internet Explorer to display a warning dialog box if a site is using an invalid digital security certificate.
Warn About Certificate Address Mismatch—When enabled, this option tells Internet Explorer to display a warning dialog box if a site is using an invalid digital security certificate.
![]() Warn If Changing Between Secure and Not Secure Mode—When enabled, this option tells Internet Explorer to display a warning dialog box whenever you enter and leave a secure site.
Warn If Changing Between Secure and Not Secure Mode—When enabled, this option tells Internet Explorer to display a warning dialog box whenever you enter and leave a secure site.
![]() Warn If POST Submittal Is Redirected to a Zone That Does Not Permit Posts—When enabled, this option tells Internet Explorer to display a warning dialog box if a form submission is sent to a site other than the one hosting the form.
Warn If POST Submittal Is Redirected to a Zone That Does Not Permit Posts—When enabled, this option tells Internet Explorer to display a warning dialog box if a form submission is sent to a site other than the one hosting the form.