Day 10 Wireless Standards, Components, and Security
CCNA 640-802 Exam Topics
![]() Describe standards associated with wireless media (IEEE, Wi-Fi Alliance, ITU/FCC).
Describe standards associated with wireless media (IEEE, Wi-Fi Alliance, ITU/FCC).
![]() Identify and describe the purpose of the components in a small wireless network (SSID, BSS, ESS).
Identify and describe the purpose of the components in a small wireless network (SSID, BSS, ESS).
![]() Compare and contrast wireless security features and capabilities of WPA security (open, WEP, WPA-1/2).
Compare and contrast wireless security features and capabilities of WPA security (open, WEP, WPA-1/2).
Key Topics
For the next two days, we will review wireless concepts and configurations. Today we look at the basic wireless concepts, components, and security features.
Wireless Standards
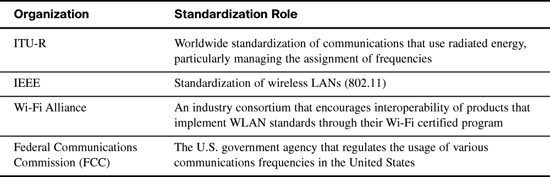
Four organizations have a great deal of impact on the standards used for wireless LANs today. Table 10-1 lists these organizations and describes their roles.
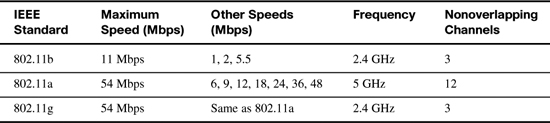
The IEEE introduced wireless LAN (WLAN) standards with the creation of the 1997 ratification of the 802.11 standard, which has been replaced by more advanced standards. In order of ratification, the standards are 802.11b, 802.11a, and 802.11g. Of note, the 802.11n standard is in draft form. Final ratification is not expected until December 2009. However, draft standard products are already available.
Table 10-2 lists some key points about the currently ratified standards.
Wireless Modes of Operation
WLANs can use one of two modes:
![]() Ad hoc mode:: With ad hoc mode, a wireless device wants to communicate with only one or a few other devices directly, usually for a short period of time. In these cases, the devices send WLAN frames directly to each other.
Ad hoc mode:: With ad hoc mode, a wireless device wants to communicate with only one or a few other devices directly, usually for a short period of time. In these cases, the devices send WLAN frames directly to each other.
![]() Infrastructure mode:: In infrastructure mode, each device communicates with a wireless access point (AP), with the AP connecting via wired Ethernet to the rest of the network infrastructure. Infrastructure mode allows the WLAN devices to communicate with servers and the Internet in an existing wired network.
Infrastructure mode:: In infrastructure mode, each device communicates with a wireless access point (AP), with the AP connecting via wired Ethernet to the rest of the network infrastructure. Infrastructure mode allows the WLAN devices to communicate with servers and the Internet in an existing wired network.
Infrastructure mode supports two sets of services, called service sets. The first, called a Basic Service Set (BSS), uses a single AP to create the wireless LAN. The other, called Extended Service Set (ESS), uses more than one AP, often with overlapping cells to allow roaming in a larger area.
Table 10-3 summarizes the wireless modes.
Wireless Frequencies
The FCC defines three unlicensed frequency bands. The bands are referenced by a particular frequency in the band, although by definition, a frequency band is a range of frequencies. Table 10-4 lists the frequency bands that matter to some degree for WLAN communications.
Wireless Encoding and Channels
You should know the names of three general classes of encoding, in part because the type of encoding requires some planning and forethought for some WLANs:
![]() Frequency Hopping Spread Spectrum (FHSS):: FHSS uses all frequencies in the band, hopping to different ones. By using slightly different frequencies for consecutive transmissions, a device can hopefully avoid interference from other devices that use the same unlicensed band. The original 802.11 WLAN standards used FHSS, but the current standards do not.
Frequency Hopping Spread Spectrum (FHSS):: FHSS uses all frequencies in the band, hopping to different ones. By using slightly different frequencies for consecutive transmissions, a device can hopefully avoid interference from other devices that use the same unlicensed band. The original 802.11 WLAN standards used FHSS, but the current standards do not.
![]() Direct Sequence Spread Spectrum (DSSS):: DSSS was designed for use in the 2.4 GHz unlicensed band and is used by 802.11b. As regulated by the FCC, this band can have 11 overlapping DSSS channels. Three of the channels (channels 1, 6, and 11) do not overlap enough to impact each other. So when designing an ESS WLAN, APs with overlapping areas should be set to use different nonoverlapping channels, as shown in Figure 10-1.
Direct Sequence Spread Spectrum (DSSS):: DSSS was designed for use in the 2.4 GHz unlicensed band and is used by 802.11b. As regulated by the FCC, this band can have 11 overlapping DSSS channels. Three of the channels (channels 1, 6, and 11) do not overlap enough to impact each other. So when designing an ESS WLAN, APs with overlapping areas should be set to use different nonoverlapping channels, as shown in Figure 10-1.
![]() Orthogonal Frequency Division Multiplexing (OFDM):: Like DSSS, WLANs that use OFDM can use multiple nonoverlapping channels. OFDM is used by 802.11a.
Orthogonal Frequency Division Multiplexing (OFDM):: Like DSSS, WLANs that use OFDM can use multiple nonoverlapping channels. OFDM is used by 802.11a.
Wireless Coverage Area
The actual size of a WLAN’s coverage area depends on a large number of factors, including the following:
![]() The frequency band used by the WLAN standard
The frequency band used by the WLAN standard
![]() The obstructions between and near the WLAN devices
The obstructions between and near the WLAN devices
![]() The interference from other sources of radio frequency (RF) energy
The interference from other sources of radio frequency (RF) energy
![]() The antennas used on both the clients and APs
The antennas used on both the clients and APs
![]() The options used by DSSS and OFDM when encoding data over the air.
The options used by DSSS and OFDM when encoding data over the air.
Generally speaking, WLAN standards that use higher frequencies can send data faster, but with the price of smaller coverage areas. To cover all the required space, an ESS that uses higher frequencies would then require more APs, driving up the cost of the WLAN deployment.
Table 10-5 lists the main IEEE WLAN ratified standards, the maximum speed, and the number of nonoverlapping channels.
CSMA/CA
Unlike Ethernet switching technologies, you cannot isolate the wireless signals from hosts sharing the same AP from interfering with each other. So if two or more WLAN devices send at the same time, using the same or overlapping frequency ranges, a collision occurs, and none of the transmitted signals can be understood by those receiving the signal. In addition, the device that is transmitting data cannot concurrently listen for received data. This means that the sending devices do not know that the collision occurred.
The solution is to use the carrier sense multiple access with collision avoidance (CSMA/CA) algorithm to minimize the statistical chance that collisions could occur. However, CSMA/CA does not prevent collisions, so the WLAN standards must have a process to deal with collisions when they do occur. The following list summarizes the key points about the CSMA/CA algorithm:
-
Listen to ensure that the medium (space) is not busy (no radio waves currently are being received at the frequencies to be used).
-
Set a random wait timer before sending a frame to statistically reduce the chance of devices all trying to send at the same time.
-
When the random timer has passed, listen again to ensure that the medium is not busy. If it isn’t, send the frame.
-
After the entire frame has been sent, wait for an acknowledgment.
-
If no acknowledgment is received, resend the frame, using CSMA/CA logic to wait for the appropriate time to send again.
Wireless Security Risks
WLANs introduce a number of vulnerabilities that do not exist for wired Ethernet LANs. Threats to WLAN security include the following:
![]() War drivers:: A person who drives around, trying to find APs that have no security or weak security.
War drivers:: A person who drives around, trying to find APs that have no security or weak security.
![]() Hackers:: The motivation for hackers is to either find information or deny services. Interestingly, the end goal might be to compromise the hosts inside the wired network, using the wireless network as a way to access the enterprise network without having to go through Internet connections that have firewalls.
Hackers:: The motivation for hackers is to either find information or deny services. Interestingly, the end goal might be to compromise the hosts inside the wired network, using the wireless network as a way to access the enterprise network without having to go through Internet connections that have firewalls.
![]() Employees:: An employee could install an access point (AP) in his office, using default settings of no security, and create a small wireless LAN. This would allow a hacker easy access to the rest of the enterprise.
Employees:: An employee could install an access point (AP) in his office, using default settings of no security, and create a small wireless LAN. This would allow a hacker easy access to the rest of the enterprise.
![]() Rogue AP:: The attacker captures packets in the existing wireless LAN, finding the service set identifier (SSID) and cracking any used security keys. Then the attacker can set up an AP, which the enterprise’s clients unwittingly associate with.
Rogue AP:: The attacker captures packets in the existing wireless LAN, finding the service set identifier (SSID) and cracking any used security keys. Then the attacker can set up an AP, which the enterprise’s clients unwittingly associate with.
To reduce the risk of such attacks, three main types of tools can be used on a WLAN:
![]() Mutual authentication:: A process that uses a secret password, called a key, on both the client and the AP. By using some sophisticated mathematical algorithms, the AP can confirm that the client does indeed know the right key value.
Mutual authentication:: A process that uses a secret password, called a key, on both the client and the AP. By using some sophisticated mathematical algorithms, the AP can confirm that the client does indeed know the right key value.
![]() Encryption:: Uses a secret key and a mathematical formula to scramble the contents of the WLAN frame. The receiving device then uses another formula to decrypt the data.
Encryption:: Uses a secret key and a mathematical formula to scramble the contents of the WLAN frame. The receiving device then uses another formula to decrypt the data.
![]() Intrusion tools:: Includes intrusion detection systems (IDS) and intrusion prevention systems (IPS), as well as WLAN-specific tools. Cisco defines the Structured Wireless-Aware Network (SWAN) architecture. It includes many tools, some of which specifically address the issue of detecting and identifying rogue APs, and whether they represent threats.
Intrusion tools:: Includes intrusion detection systems (IDS) and intrusion prevention systems (IPS), as well as WLAN-specific tools. Cisco defines the Structured Wireless-Aware Network (SWAN) architecture. It includes many tools, some of which specifically address the issue of detecting and identifying rogue APs, and whether they represent threats.
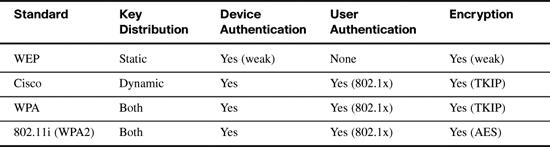
Table 10-6 lists the key vulnerabilities, along with the general solution.
Wireless Security Standards
The initial security standard for WLANs, called Wired Equivalent Privacy (WEP), had many problems. The next three standards represent a progression whose goal in part was to fix the problems created by WEP. In chronological order, Cisco first addressed the problem with some proprietary solutions. Then the Wi-Fi Alliance helped fix the problem by defining an industrywide standard. Finally, the IEEE completed work on an official public standard, 802.11i.
The following is a brief review of these four security standards:
![]() WEP:: In 1997, the original security standard provided authentication and encryption, which can be easily cracked. Main issues included:
WEP:: In 1997, the original security standard provided authentication and encryption, which can be easily cracked. Main issues included:
— Static preshared keys (PSKs) that required manual configuration, thus people simply left the defaults.
— PSK values were short with only 40 unique bits, making them easy to crack.
![]() Cisco Interim Solution:: Cisco’s proprietary answer to the problems with WEP came out in 2001 to provide a solution quicker than the Wi-Fi Alliance or IEEE promised solutions. The Cisco answer included some proprietary improvements for encryption, along with the IEEE 802.1x standard for end user authentication. The main features of Cisco enhancements included the following:
Cisco Interim Solution:: Cisco’s proprietary answer to the problems with WEP came out in 2001 to provide a solution quicker than the Wi-Fi Alliance or IEEE promised solutions. The Cisco answer included some proprietary improvements for encryption, along with the IEEE 802.1x standard for end user authentication. The main features of Cisco enhancements included the following:
— Dynamic key exchange so that if a key is discovered, it is short-lived
— A new encryption key for each packet
— User authentication using 802.1x instead of device authentication
![]() Wi-Fi Protected Access (WPA):: WPA came out in 2003 and essentially does the same thing as the Cisco interim solution. WPA includes the option to use dynamic key exchange, using the Temporal Key Integrity Protocol (TKIP). Cisco used a proprietary version of TKIP. WPA allows for the use of either IEEE 802.1X user authentication or simple device authentication using preshared keys. The encryption algorithm uses the Message Integrity Check (MIC) algorithm, again similar to the process used in the Cisco-proprietary solution. WPA improved security and, through the Wi-Fi Alliance certification program, gave vendors an incentive to have their products carry the Wi-Fi certification label.
Wi-Fi Protected Access (WPA):: WPA came out in 2003 and essentially does the same thing as the Cisco interim solution. WPA includes the option to use dynamic key exchange, using the Temporal Key Integrity Protocol (TKIP). Cisco used a proprietary version of TKIP. WPA allows for the use of either IEEE 802.1X user authentication or simple device authentication using preshared keys. The encryption algorithm uses the Message Integrity Check (MIC) algorithm, again similar to the process used in the Cisco-proprietary solution. WPA improved security and, through the Wi-Fi Alliance certification program, gave vendors an incentive to have their products carry the Wi-Fi certification label.
![]() 802.11i (WPA2):: In 2005, IEEE ratified 802.11i, which includes dynamic key exchange, much stronger encryption using the Advanced Encryption Standard (AES), and user authentication. 802.11i is not backward compatible with either Cisco’s solution or WPA. Because the Wi-Fi Alliance certification is so popular and well known, 802.11i products are certified with the WPA2 label.
802.11i (WPA2):: In 2005, IEEE ratified 802.11i, which includes dynamic key exchange, much stronger encryption using the Advanced Encryption Standard (AES), and user authentication. 802.11i is not backward compatible with either Cisco’s solution or WPA. Because the Wi-Fi Alliance certification is so popular and well known, 802.11i products are certified with the WPA2 label.
Table 10-7 summarizes the key features of the various WLAN security standards.