Session, Presentation, and Application Layers
Recall that there are two popular network models in use: the OSI Reference Model and the TCP/IP Reference Model. In this chapter you’ll learn about the top three layers of the OSI model. Those three OSI layers correspond to the Application Layer (top layer) in the TCP/IP model. FIGURE 6-1 shows how the layers in each model (OSI and TCP/IP) relate to one another.
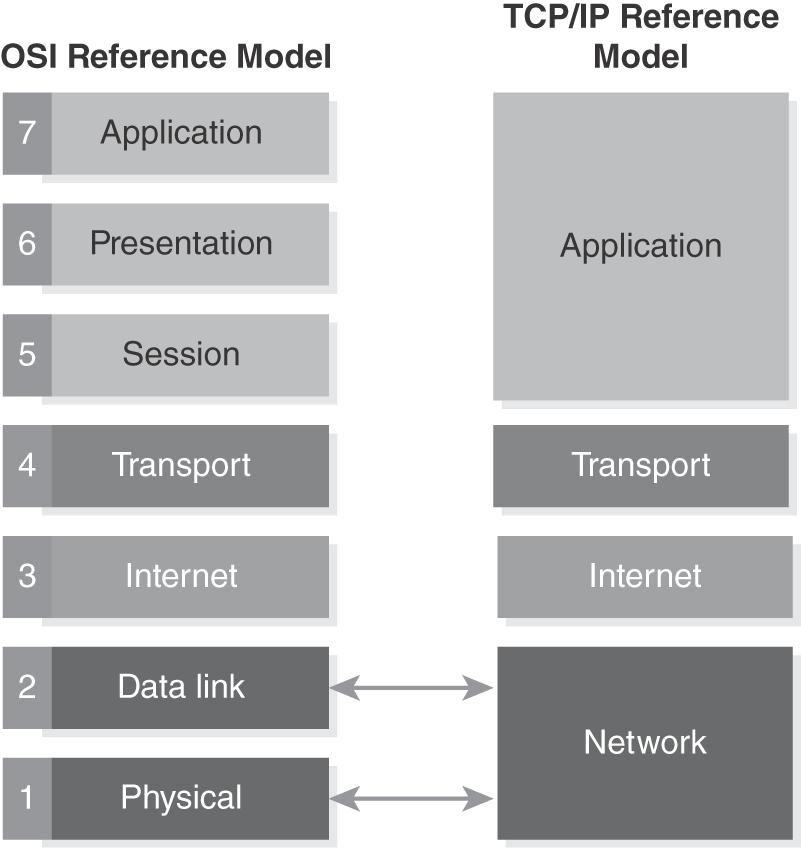
FIGURE 6-1 OSI model compared to the TCP/IP model.
The fact that the TCP/IP model groups these layers together should tell you something. Although each layer has its own responsibilities, they are closely related. The functions you’ll learn about in this chapter tend to be the parts of networking that impact users most directly.
Session Layer: OSI Layer 5
The Session Layer, OSI Layer 5, controls the conversations between computers. Notice that lower layers focus on sending pieces of data between nodes. That data may be just electronic signals, a stream of bytes, or some group of data (commonly called a packet or frame). Layer 5 is the first layer that connects packets together into conversations. This layer sets up, manages, and terminates connections between applications on source and destination computers. Layer 5 can provide several different modes of communicating, including:
- Full duplex—In the full-duplex mode, both ends of a connection can communicate simultaneously. Telephones use full-duplex communications.
- Half duplex—In the half-duplex mode, both ends of a connection can communicate, but only one at a time. Two-way radios (where you have to push a button to talk) operate in half-duplex mode.
- Simplex—In the simplex mode, the source can only send data to the destination. The destination cannot respond.
Today, many of the Layer 5 functions are built into other protocols that operate at different layers. Layer 5 was included in the OSI Reference Model to highlight the importance of creating and destroying connections in an orderly manner. Some of the common protocols that explicitly operate at OSI Layer 5 include:
- H.254—H.254 is a call control protocol used in multimedia communication.
- L2TP—A tunneling protocol that supports virtual private networks (VPNs). Layer 2 Tunneling Protocol (L2TP) operates like a Layer 2 protocol, but actually operates at Layer 5.
- NetBIOS—Network Basic Input/Output System (NetBIOS) allows applications on different computers to communicate over a local area network (LAN) and share files.
- RPC—Remote Procedure Call (RPC) is a protocol that supports a user or process on one computer running a program (or procedure) on a remote computer.
- SMB—Server Message Block (SMB) is a protocol that allows remote and shared access to files, printers, and serial ports across a network.
- SOCKS—A protocol that serves as a proxy server, sending and receiving network traffic using a well-known port (generally 1080), and then redirecting traffic to another port. The SOCKS protocol is often used to bypass ports a firewall blocks and has even been used to create a simple VPN.
 NOTE
NOTE
Application environments that use remote procedure calls commonly operate using Layer 5 services.
Presentation Layer: OSI Layer 6
The Presentation Layer, OSI Layer 6, provides the interface between the Application Layer (above the Presentation Layer in FIGURE 6-1) and the Session Layer (below the Presentation Layer in FIGURE 6-1). The Presentation Layer on the sending computer is responsible for formatting and coding Application Layer data (i.e., high-level data that comes from applications) into a form that is acceptable for transmitting on the network. The Presentation Layer on the receiving computer translates data it receives from the Session Layer into a format that is acceptable to the Application Layer. (This layer got its name from its main purpose of making received data presentable to the Application Layer.) Some of the most common services the Presentation Layer provides include formatting and encrypting data. Encrypting data can occur at other layers, but the Presentation Layer is responsible for encrypting Application Layer data. Some of the common protocols that operate at the Presentation Layer include:
- IMAP—One of the most popular standards for retrieving email via an email client from an email server. Internet Message Access Protocol (IMAP) supports server-based email access from multiple clients by leaving email storage up to the server. (The older POP protocol downloaded email messages and put the burden of management on the client.)
- SSH—A cryptographic protocol for interacting and executing network services over an unsecured network segment. Secure Shell (SSH) can provide a secure command line prompt on a remote computer as well as secure remote command execution.
- SSL—Secure Sockets Layer (SSL) is a protocol that uses asymmetric cryptography (i.e., private/public encryption key pairs) to encrypt connections between network nodes.
- TLS—The successor to SSL. The newer Transport Layer Security (TLS) versions are significantly more secure and fix many vulnerabilities present in SSL.
The Presentation Layer performs the following actions:
- The sender Presentation Layer accepts data from the sender Application Layer, formats and optionally encrypts it, and then sends it down to the sender Session Layer.
- The receiving Presentation Layer accepts data from the receiving Session Layer, decrypts it if necessary, and formats it for the Application Layer. It then sends the data up to the receiving Application Layer.
In addition to encrypting and decrypting data, the Presentation layer converts data into standard formats for application program use. Some of the file formats that the Presentation Layer implements are American Standard Code for Information Interchange (ASCII) and Extended Binary Coded Decimal Interchange Code (EBCDIC) for text data, and Tagged Image File Format (TIFF), Graphics Interface Format (GIF), Joint Photographic Experts Group (JPEG), Moving Picture Experts Group (MPEG), or Musical Instrument Digital Interface (MIDI) for binary media files. The Presentation Layer ensures that each file format standard is observed to present (hence the layer’s name) the proper type of files to the Application Layer. Of course, the previous explanation is the Presentation Layer’s actions for received data. When the Application Layer sends data to a remote destination, the Presentation Layer converts data from one of the file formats listed into a standard format that the Session Layer (and below) can use.
Application Layer: OSI Layer 7
The highest layer in the OSI model (and in the TCP/IP model) is the Application Layer. This layer is also called Layer 7 in the OSI model. Layer 7 is generally the only layer that interacts directly with the human being, although the Application Layer may also just interact with other processes. The Application Layer is where the front-end software interfaces with the computer user, often referred to as the user interface. The Application Layer is at the top of both models and is the farthest from the actual network and Physical Layer. It’s the software entry point for sending messages to and from an application’s users. The process to exchange a message with another computer generally starts with a Layer 7 software call. That means the application software calls another program or routine that does the following:
- When sending a message, the Application Layer software accepts some message as input from the application software. The Application Layer software adds any additional data, such as the address of the target computer.
- The Application Layer software calls other software from the next lower layer and sends the new message (the original message with additional information).
- The Application Layer software may chop the message into smaller chunks before sending each chunk to the next layer.
- The Application Layer software then may wait for a reply.
Once the Application Layer sends the message to the next lower layer, it either continues with other tasks or waits to receive a response. The Application Layer serves as the primary interface for application software to interact with networks.
Protocols define how each layer talks to the same layer on another computer or device. Multiple protocols operate at each layer in the OSI model. Each protocol provides the required services for a layer and addresses specific needs. Some common protocols that operate at Layer 7 are:
- Dynamic Host Configuration Protocol (DHCP)—Automatic IP address configuration protocol for networks.
- File Transfer Protocol (FTP)—Protocol used to transfer files between network nodes.
- Hypertext Transport Protocol (HTTP)—Primary protocol used on the web to deliver hypertext documents. Data is sent in plain text, so Hypertext Transfer Protocol Secure (HTTPS) is now recommended.
- Network File System (NFS)—A distributed file system that allows multiple computers to share files and directories with remote computers and users. Using Network File System (NFS), users can interact with remote files as if they are accessing local storage.
- Real-Time Transport Protocol (RTP)—Real-Time Transport Protocol (RTP) defines standard packets for handling streaming media on a network.
- Session Initiation Protocol (SIP)—Protocol used to control multimedia communication using networks.
- Simple Mail Transfer Protocol (SMTP)—Protocol for sending and receiving email messages between message transfer agents. Email clients mostly use IMAP or Post Office Protocol 3 (POP3) for sending and receiving email messages, but the servers that handle transferring those messages throughout networks to reach the destination (where the receiving client can get to it) use SMTP.
- Simple Network Management Protocol (SNMP)—Protocol used for transferring network management information about IP network devices.
- Telnet—An application protocol to support a remote virtual terminal session. Telnet allows a user on one computer to log in and use a command line on a remote computer. Because all text is sent “in the clear” (i.e., not encrypted), Telnet is dangerous to use from a security perspective. Best practices discourage any Telnet use and recommend SSH instead.
FYI
It’s important to understand that what the OSI Reference Model calls an application is not what most people normally think of as an application. In the OSI model, the Application Layer provides services for user applications, such as web browsers (or email clients, or Usenet readers). The browser itself (such as Microsoft Edge, Mozilla Firefox, or Google Chrome) is an application running on your PC. It uses the services of a protocol that operates at the network’s Application Layer, such as HTTP. Not all user applications use the network’s Application Layer in the same way; for example, if a word processor is used to open a file on another machine on a network, the word processor isn’t using the Application Layer—it just sees a file that has been mapped to a network somewhere else. The operating system redirects what the word processor does over the network.
The Application Layer is the most visible layer in the OSI model. Most computer users have at least heard of HTTP because they use a browser to surf the web. HTTP is the most widely recognized Application Layer protocol.
