 APPENDIX D Sample Security Policies and Templates
by
Fundamentals of Communications and Networking, 3rd Edition
APPENDIX D Sample Security Policies and Templates
by
Fundamentals of Communications and Networking, 3rd Edition
- Cover
- Title Page
- Copyright Page
- Brief Contents
- Contents
- Dedication
- Preface
- Acknowledgments
- About the Authors
- CHAPTER 1 Evolution of Communication Technologies
- Today’s Hyperconnected World
- From Analog to Digital to IP
- Internet and IP Connectivity Are Pervasive
- How Unified Communications Connect People and Businesses
- How Communications Have Evolved
- Snail Mail
- Store-and-Forward Messages
- Real-Time Communication
- Social Media
- The Web’s Impact on Business
- E-commerce Business Models
- Solving E-commerce Business Challenges
- The Internet of Things’ Impact on Business
- The Cloud’s Impact on Business
- Virtualization
- Types of Cloud Services and Delivery Models
- CHAPTER SUMMARY
- KEY CONCEPTS AND TERMS
- CHAPTER 1 ASSESSMENT
- CHAPTER 2 Solving Today’s Business Communication Challenges
- Introducing Organizational Communication Challenges
- Enterprise Challenges
- Government Challenges
- SMB/SOHO Challenges
- Solving Enterprise Business Communication Challenges
- Banking and Financial Services Challenges
- Healthcare and Patient Care Services Challenges
- K–12 and Higher Education Services Challenges
- Commercial Retail Products and Services Challenges
- Manufacturing Services Challenges
- Travel and Transportation Services Challenges
- Solving Government Business Communication Challenges
- Solving SMB Business Communication Challenges
- Solving SOHO Business Communication Challenges
- Transforming Communication Requirements into Network Solutions
- Defining Your Organization’s Networking Requirements
- CHAPTER SUMMARY
- KEY CONCEPTS AND TERMS
- CHAPTER 2 ASSESSMENT
- CHAPTER 3 Circuit-Switched, Packet-Switched, and IP-Based Communications
- Open Systems Interconnection Reference Model
- TCP/IP Reference Model
- Application Layer
- Transport Layer
- Internet Layer
- Network Access Layer
- TCP/IP Suite
- Circuit Switching Versus Packet Switching
- Circuit Switching
- Packet Switching
- IP-Based Communications
- Network Topology Overview
- Point-to-Point Networks
- Bus
- Ring
- Star
- Mesh
- Fully Connected Mesh
- Hybrid
- Internetworking
- Internetworking with Bridges
- Internetworking with Switches
- Internetworking with Routers
- Internetworking with a Bridge/Router
- Internetworking with a Gateway
- Switching Concepts
- Switch Functionality
- Switch Forwarding Methods
- Routing Concepts
- Network Layer Address
- Static Route
- Dynamic Route
- Resiliency and Redundancy
- Layer 2 Resiliency
- Layer 3 Resiliency
- Virtual Networking Components
- Network Storage Types
- CHAPTER SUMMARY
- KEY CONCEPTS AND TERMS
- CHAPTER 3 ASSESSMENT
- CHAPTER 4 The Physical and Data Link Layers
- Physical Layer and Data Link Layer
- Physical Layer: OSI Layer
- Data Link Layer: OSI Layer
- Ethernet and IEEE 802.3 Frame Formats
- Ethernet Evolution
- IEEE 802.3 Standards and Specifications
- Solving Business Challenges
- IEEE 802.3 CSMA/CD Standards
- How Multiple Nodes Share Network Media
- Internetworking LANs: Bridging Versus Routing
- Repeaters and Hubs: Layer 1 Forwarding
- Bridges and Switches: Layer 2 Forwarding
- Ethernet Network Design Fundamentals
- Edge Network: Workgroup LANs
- Edge Network: Use of PoE Switches
- Edge Network: Departmental LAN
- Building Backbone: Collapsed Backbones
- Campus Backbone: Collapsed Data Center Backbone
- Metropolitan Area Backbone: Metro Ethernet Backbone
- GigE and 10 GigE Specifications
- 25, 40, and 100 GigE: Server Farms and Backbone Trunking
- CHAPTER SUMMARY
- KEY CONCEPTS AND TERMS
- CHAPTER 4 ASSESSMENT
- CHAPTER 5 The Network and Transport Layers
- Network and Transport Layers
- Network Layer: OSI Layer
- Transport Layer: OSI Layer
- The Internet Protocol
- IP Addressing: IPv4 versus IPv6
- IPv4
- IPv6
- IPv4 to IPv6
- IP Communications
- Connectionless Versus Connection-Oriented Communications
- Scenario 1: Connection-Oriented Conversation
- Scenario 2: Connectionless Conversation
- CHAPTER SUMMARY
- KEY CONCEPTS AND TERMS
- CHAPTER 5 ASSESSMENT
- CHAPTER 6 The Session, Presentation, and Application Layers
- Session, Presentation, and Application Layers
- Session Layer: OSI Layer 5
- Presentation Layer: OSI Layer 6
- Application Layer: OSI Layer 7
- Application Architectures
- Architecture Types and Examples
- Features and Benefits of Each Architecture Type
- Aligning Architecture with Business Requirements
- Application Layer Ports and Sockets
- World Wide Web
- From the Internet to the Web: How the World Wide Web Works
- HTTP: The Web’s Workhorse
- Impact on Security
- CHAPTER SUMMARY
- KEY CONCEPTS AND TERMS
- CHAPTER 6 ASSESSMENT
- CHAPTER 7 Layer 2 Networking
- Layer 2 Networking Basics
- Layer 1 and Layer 2 Evolution
- What Layer 2 Networking Means
- Ethernet LAN Topologies
- Layer 2 Network Redundancy and Resiliency
- VLAN Tagging
- IEEE 802.3ad Link Aggregation
- Network Backbones
- Network Power
- Layer 2 Business Solutions
- SOHO Organization
- SMB Organization
- Enterprise Organization
- CHAPTER SUMMARY
- KEY CONCEPTS AND TERMS
- CHAPTER 7 ASSESSMENT
- CHAPTER 8 Layer 3 Networking
- Network Layer Basics
- Network Layer Protocols
- Router Protocols
- Convergence
- Load Balancing
- Traffic Flow
- Internetwork Routing Functions
- LAN-to-LAN Routing
- LAN-to-WAN Routing
- Routing Metrics and Protocols
- Exterior Versus Interior Routing Protocols
- Routing Information Protocol (RIP)
- RIP Version 2 (RIPv2)
- Open Shortest Path First Version 2 (OSPFv2)
- Intermediate System-to-Intermediate System (IS-IS)
- Interior Gateway Routing Protocol (IGRP)
- Enhanced Interior Gateway Routing Protocol (EIGRP)
- Border Gateway Protocol (BGP)
- Layer 3 Network Redundancy and Resiliency
- Configuring Resilience
- Routing Protocol Resilience
- CHAPTER SUMMARY
- KEY CONCEPTS AND TERMS
- CHAPTER 8 ASSESSMENT
- CHAPTER 9 Network Infrastructure Implementations
- Physical Infrastructures
- Hosting Infrastructures
- Foundational Network Services
- IP Address Management (IPAM)
- Dynamic Host Control Protocol (DHCP)
- Domain Name System (DNS)
- Network Time Protocol (NTP)
- Network Devices and Where to Position Them
- Asset Visibility
- Creating an IT Asset Inventory
- Access Controls
- Identification, Authentication, Authorization, and Accounting
- Remote Access Controls and Multifactor Authentication
- Network Access Controls
- Visibility
- Control
- Device Identification
- Advanced Networking Devices
- Advanced Switching Devices
- Layered Security Solutions
- Performance-Enhancing Devices
- CHAPTER SUMMARY
- KEY CONCEPTS AND TERMS
- CHAPTER 9 ASSESSMENT
- CHAPTER 10 Wireless Networks
- Supporting the Mobile Worker
- Wired Versus Wireless
- Evolution of Wireless LAN Networking
- IEEE 802.11 Family of Standards
- The IEEE 802.11 Legacy Standard
- The IEEE 802.11b WLAN Standard
- The IEEE 802.11a WLAN Standard
- The IEEE 802.11g WLAN Standard
- The IEEE 802.11n WLAN Standard
- The IEEE 802.11ac WLAN Standard
- The IEEE 802.11ax WLAN Standard
- WLAN Security
- Authentication and Access Control
- Security Threats to WLANs
- IEEE 802.1X Security
- Encryption and Data Privacy
- Security Protocols and Access Control
- Security Practices
- Unauthorized Access to Shared Resources
- WLAN Planning and Design
- RF Design Issues
- Capacity and Coverage
- Speed and Distance Requirements
- Channel Bandwidth
- Channel Bonding
- MIMO/MU-MIMO
- Unidirectional/Omnidirectional
- Performing a Site Survey
- Conducting the Site Tests
- CHAPTER SUMMARY
- KEY CONCEPTS AND TERMS
- CHAPTER 10 ASSESSMENT
- CHAPTER 11 Wide Area Networks
- WAN Business Drivers
- WANs and Service Providers
- WAN and SD-WAN Business Drivers
- Evolution of WAN Technologies
- WAN Technologies in the 1970s
- WAN Technologies in the 1980s
- WAN Technologies in the 1990s
- WAN Technologies in the 2000s
- WAN Technologies in the 2010s
- WAN Management and Requirements
- Fault Management Requirements
- Configuration Management Requirements
- Accounting Management Requirements
- Performance Management Requirements
- Security Management Requirements
- WAN Solutions for Different Scenarios
- Enterprise Business
- Small to Medium Business (SMB)
- Small Office/Home Office (SOHO)
- CHAPTER SUMMARY
- KEY CONCEPTS AND TERMS
- CHAPTER 11 ASSESSMENT
- CHAPTER 12 Network Operations and Management
- The Scope of Network Operations and Management
- IT and IT Security Policy Framework
- Policy and Procedure Best Practices
- Network Operations and Management
- Staffing and Resources
- Real-Time Availability
- Audit and Monitoring
- Collecting Data
- Reporting Information
- Configuration Change Management
- Change Control Board Membership
- Change Control Board Function
- Change Control Board Policies and Practices
- Capacity Planning and Readiness
- IT Asset Inventory
- Network Performance
- Service Providers
- Network Management
- Simple Network Management Protocol (SNMP)
- Management Information Bases (MIBs)
- SNMP Traps
- FCAPS: Fault Management
- FCAPS: Configuration Management
- FCAPS: Accounting Management
- FCAPS: Performance Management
- FCAPS: Security Management
- Network Security
- Physical Security
- Access Controls
- Wireless Security
- Common Network Attacks
- Network Device Hardening
- Network Mitigation Solutions
- Changing Attacks
- Blended Response
- CHAPTER SUMMARY
- KEY CONCEPTS AND TERMS
- CHAPTER 12 ASSESSMENT
- CHAPTER 13 Network Auditing, Monitoring, and Incident Response
- Security Auditing and Analysis
- Purpose of Audits
- Customer Confidence
- Auditing Benchmarks
- Security Monitoring
- Security Monitoring for Computer Systems
- Types of Log Information to Capture
- Responding to Security Incidents
- Incident Response Plan, Policies, Procedures, and Guidelines
- Incident Response Team
- Phases of an Incident and Response
- The Role of Business Continuity and Disaster Recovery Plans
- Recovering Systems
- Business Impact Analysis
- Risk Assessment
- Risk Management
- Planning for Disaster and Recovery
- Policies, Procedures, Priorities, and Practices
- Testing and Evaluation
- Preparation and Staging of Testing Procedures
- Frequency of Tests
- Analysis of Test Results
- CHAPTER SUMMARY
- KEY CONCEPTS AND TERMS
- CHAPTER 13 ASSESSMENT
- CHAPTER 14 Network Security
- Network Security Essentials
- What Is Confidentiality?
- What Is Integrity?
- What Is Availability?
- Network Security Scope
- Network Risks, Threats, and Vulnerabilities
- Conducting a Network Security Risk Assessment
- Layered Network Security Architectures
- Network Security Controls
- How to Implement Security Controls
- CHAPTER SUMMARY
- KEY CONCEPTS AND TERMS
- CHAPTER 14 ASSESSMENT
- CHAPTER 15 Network Troubleshooting
- Network Operations Center
- Network Troubleshooting and Ticketing
- NOC and IT Service Desk Structure
- Network Troubleshooting Approach
- Network Troubleshooting Tools
- Physical Layer Tools
- Network Performance Monitoring Tools
- Network Traffic Tools
- Network Connectivity Tools
- Network Scanning and Discovery Tools
- Vulnerability Assessment Tools
- Protocol Analyzer Tools
- Network Troubleshooting Using Protocol Analysis
- How Protocols Behave
- Network Troubleshooting Scenarios
- Names Not Resolving
- Incorrect Gateway Definition
- Incorrect Netmask
- Duplicate IP Address
- Duplicate MAC Addresses
- Expired IP Address
- Rogue DHCP Server
- Untrusted SSL Certificate
- Incorrect Time
- Exhausted DHCP Scope
- Blocked TCP/UDP Ports
- Incorrect Host-Based Firewall Settings
- Incorrect ACL Settings
- Unresponsive Service
- CHAPTER SUMMARY
- KEY CONCEPTS AND TERMS
- CHAPTER 15 ASSESSMENT
- APPENDIX A Answer Key
- APPENDIX B IP Addressing Primer
- APPENDIX C Structured Wiring System Primer
- APPENDIX D Sample Security Policies and Templates
- APPENDIX E Standard Acronyms
- Glossary of Key Terms
- References
- Index

© escyth/Shutterstock
Sample Security Policies and Templates |
APPENDIX |
Included in this appendix are some foundational policy templates that are needed to help mitigate risk. The following policy templates are included in this appendix:
- Access Control Policy—Defines how your organization will handle identification, authorization, and authentication
- Acceptable Use Policy—Defines what is acceptable use and what is not acceptable use of organization-owned IT assets and communication tools
- Data Classification Policy—Defines categories or classes of data and their sensitivity as they pertain to proper handling of sensitive data
- Network Security Policy—Defines how the network infrastructure will enable security controls to mitigate risks, threats, and vulnerabilities throughout the network
Sample Company IT Policy |
Effective Date: |
SAMPLE COMPANY ACCESS CONTROL POLICY |
Enterprise or Departmental: Enterprise Policy |
| Approved: | |
| Executive Sponsor: | |
| Policy Revision # & Date: | |
| Subject: | |
| Access Control Policy | |
PURPOSE
The intent of this policy is to define the organization’s requirement for providing employees, users, authorized third parties, and system administrators with access to systems, applications, and data.
Given the organization’s Data Classification Policy, role-based access controls will be defined for each job function. Each job description will have job tasks and functions defined that may require access to systems, applications, and data. Depending on the sensitivity of the job function, access to sensitive data may be required.
SCOPE
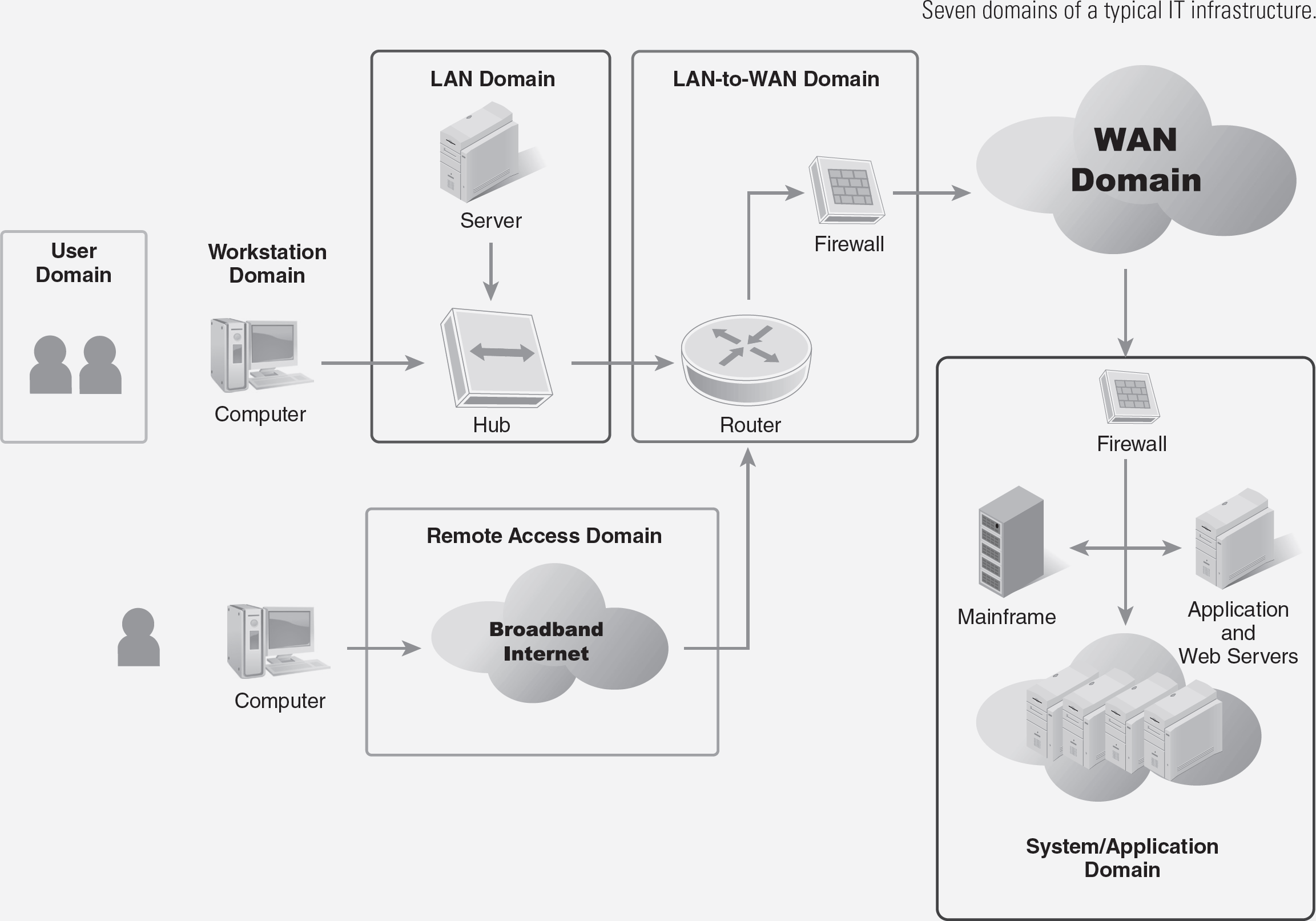
The physical scope of this policy shall include the following domains within the seven domains of a typical IT infrastructure (see figure on next page):
- Workstation Domain—Workstation, laptop, and endpoint devices
- LAN Domain—Network backbone, distribution, and edge LAN switches
- Remote Access Domain—Public Internet or other wide area network service
- System/Application Domain—Virtual servers, servers, server farm switches, and virtual networks
The operational and management scope of this Access Control Policy shall include:
- Authorization—New hire, HR onboarding, and role-based access controls are defined.
- Identification—Unique login ID is provided.
- Authentication—Temporary password is provided requiring user to change to complex and very strong password.
- Accounting—Audit trails, logs, and user additions and deletions.
DEFINITIONS
Access controls—The process and procedures for how authorized users are to gain access to the network, systems, applications, and data.
Active Directory—Windows system that provides identification and authentication for access to the LAN.
Authentication—The process of ensuring that the individual is who he or she claims to be by asking for a password or series of questions to verify the individual’s identity.
Authorization—HR onboarded new hire is authorized to obtain role-based access controls based on the job duties and tasks required.
Identification—The assignment of a user ID or login ID for the user.
Multifactor authentication—After the initial login ID and password are used, another method of user authentication is enabled such as two-factor authentication using a hard token or soft token passcode.
Role-based access controls—Within an organization, different job functions require different access to different IT systems, applications, and data. Role-based access controls define access to IT systems, applications, and data based on the role or job function required.
Security information event management (SIEM)—A sophisticated log aggregation system that can analyze audit trails and logs, and correlate events and security incidents on an IP data network. The SIEM is the central data repository for audit trails and logs of IT assets where threat analysis is performed.
Separation of duties—A security control where roles and responsibilities are shared and distributed to privileged system administrators so that all the power is not with one individual.
Two-factor authentication (2FA)—Provides identification of users by means of the combination of two different components. These components may be something the user knows, something the user possesses, or something inseparable from the user. Two-factor authentication is a type of multifactor authentication.
User ID/login ID—A unique identifier that is given to an authorized user. User IDs and login IDs can be a user’s email address or other username assigned within Windows Active Directory (AD) or where all user IDs and login IDs are created.
POLICY
All employees, authorized users, and authorized third parties shall be granted access to the organization’s network, systems, applications, and data as needed to perform their job responsibilities.
The following defines the security controls for access controls:
- HR onboarding must be completed prior to the new hire obtaining their login credential (authorization).
- Access privileges are determined based on least privileges necessary to perform job responsibilities (authorization).
- Access privileges are based on role-based access controls.
- Security awareness training must be completed within 1 week of hire after receiving the login credentials.
- Each employee, authorized user, and authorized third-party representative must have and will be assigned a unique user ID and password for the following (authentication):
- Access to the organization’s workstation/laptop screensaver (same as Active Directory password)
- Access to the organization’s LAN via Windows Active Directory ID and authentication
- Role-based access to the systems, applications, and data required of the job responsibilities
- Users are not to share their user ID or password with anyone.
- Users are to abide by the organization’s password management standard requiring the user to have a 12-character, complex, and stringent password (e.g., 1 capital, 1 lowercase, 1 number, 1 character, no reuse, etc.) Alpha-character names or numbers that have meaning to the individual are not permitted to be used (e.g., names of children or pets, birth year, graduation year, street address number, etc.).
- Users shall utilize their AD login credentials when remotely accessing the network plus must use 2FA via a soft-token solution.
- All user login attempts and logout attempts must have audit trails and logs sent to the organization’s syslog or security information event management (SIEM) server for log aggregation.
- All Windows event code messages and logs (local and remote users) must be sent to the organization’s syslog or SIEM server for log aggregation.
- System administrators shall have proper separation of duties providing a hierarchical privileged access to the network, systems, and applications and different functions.
NONCOMPLIANCE OR POLICY VIOLATIONS
Noncompliance with this policy definition will be monitored, tracked, and handled by the Human Resources department, the employee’s department head, and the Information Technology department.
All employees, authorized users, and authorized third parties that are in violation of this policy will be required to work with the Human Resources department and Information Technology department to remediate.
This remediation effort may include review of policies and procedures, retaking the security awareness training course, and/or other disciplinary actions.
REVISIONS
| REVISION DATE | AUTHOR | DESCRIPTION |
|---|---|---|
Sample Company IT Policy |
Effective Date: |
SAMPLE COMPANY ACCESS CONTROL POLICY |
Enterprise or Departmental: Enterprise Policy |
| Approved: | |
| Executive Sponsor: | |
| Policy Revision # & Date: | |
| Subject: | |
| Acceptable Use Policy—IT Assets, Network, Internet, and Email | |
PURPOSE
This policy shall define acceptable use of the organization’s IT assets, Internet, email, systems, applications, and data. This policy shall also define unacceptable use.
SCOPE
The scope of this enterprise-wide policy encompasses the entire organization and all employees, authorized users, and authorized third parties who are granted access controls to the IT infrastructure.
All employees, contractors, and authorized third parties that are provided with a login ID and password must comply with this acceptable use policy. This policy mandates that all employees, contractors, and authorized third parties take special precautions as they pertain to the access, use, handling, storage, and transmission of sensitive data as part of normal day-to-day operations and business functions.
DEFINITIONS
Cipher-text—Data that cannot be seen or comprehended given that it is encrypted or scrambled and is unreadable.
Clear-text—Data that can be seen and comprehended given that it is displayed “as is.”
Encryption—Utilizes a cryptographic algorithm to encode messages or information in a way that only authorized recipients can decode the message or information.
Information security—The tenets of information security include confidentiality, integrity, and availability. Information security, as a whole, is the responsibility of all employees and authorized users of the organization’s network, systems, applications, and data.
Sensitive data—Data that is under a regulatory compliance law or is sensitive as defined by the organization.
ACCEPTABLE USE POLICY
POLICY
All authorized users (employees, contractors, or authorized third parties) that require access to the organization’s IT assets, systems, applications, and data must read, acknowledge, and sign this Acceptable Use Policy prior to being granted login credentials.
More importantly, this policy shall define what is acceptable use and what is unacceptable use of the organization’s owned IT systems, applications, and data.
ACCEPTABLE USE
- Be aware and be accountable for your own actions when using organization-owned IT assets, especially when sensitive data is accessed or transmitted.
- Use provided computer equipment, hardware, and software applications, including use of the public Internet, to do your job functions and tasks only. Limited and reasonable use of computer equipment and networks for personal reasons is acceptable only if it does not result in any additional costs, loss of work time, or abuse to organization-owned IT assets and resources.
- Protect your user ID, password, and computer from unauthorized use. You are responsible for all activities on your user ID or that originate from your computer.
- Ensure that no sensitive data is screen captured or cut and pasted into separate or stand-alone documents, or saved to unapproved data storage devices such as CDs, DVDs, or USB thumb drives. External storage media, such as a CD, DVD, or USB thumb drive, must use encrypted/password protected files or have encryption enabled on the media device itself.
- Use only legal versions of copyrighted software that meets vendor license requirements as authorized by the Information Technology department.
- Be aware of where you put sensitive data if on shared resources. These resources include server disk storage space, shared LAN drives, and other data repositories.
- Use the Internet and electronic mail for business purposes only.
- Exercise caution when opening emails or attachments, clicking on imbedded URL links in emails, or clicking on email attachments. Do NOT open anything from an email address that is not familiar. Contact the Information Technology department if you are uncertain about the authenticity of a suspicious email that you receive.
- If you receive junk text messages, junk emails, or spam email marketing messages, contact the Information Technology department to assist with your email spam filter and eliminating the receipt of unnecessary email messages in your inbox.
- Only use devices that have been approved by the organization for business functions. This includes workstations, laptops, tablets, smartphones, and encrypted USB thumb drives or external drives. If you are unsure as to whether a device is approved or not, please request the Information Technology department to check if the equipment in question is located on the list of company-approved products.
UNACCEPTABLE USE
- Any violation of local, state, or federal laws or regulations and organization policies, including but not limited to inappropriate uses discussed herein, is considered unacceptable use. Users in violation of this may result in immediate loss of use and access privileges, disciplinary action, or termination of employment.
- Do not use the same password for two or more accounts and do not use personal passwords as business passwords (or vice versa).
- Do not reuse passwords.
- Do not store passwords on paper or in any file near or around your workspace area unencrypted—memorize or use a secure password management tool.
- Do not use your computer, the Internet, email, or social media (Facebook, YouTube, Instagram, Twitter, etc.) in a manner that would reflect adversely on the organization. This includes activities like storing or transmitting pornography, accessing pornography websites, sending chain email messages, sending unofficial advertising, soliciting or selling via email, and other uses that are incompatible with public service. Material that is fraudulent, harassing, embarrassing, sexually explicit, profane, obscene, intimidating, defamatory, or otherwise unlawful or inappropriate may not be sent by email or other form of electronic communication (such as bulletin board systems, newsgroups, or chat groups) or displayed on or stored in the organization’s computers.
- The organization does not permit access to external webmail such as Hotmail, Gmail, or Yahoo Mail for personal use.
- Do not do things that could harm the organization’s computers or networks or that could damage or destroy information stored on the network. This includes spreading malicious software such as a computer virus, malware, ransomware, or other attack.
- Do not install any personally owned hardware or software to any organization-owned workstation, laptop, printer, server, or any other type of IT equipment without advance notification and approval from the Information Technology department. This includes use of external USB thumb drives that are not provided by the organization’s Information Technology department.
- Do not do anything that could violate software licensing or copyright laws. This includes:
(1) Providing copies of software to anyone else
(2) Installing software on organization-owned computer equipment without notifying and getting advance approval of the Information Technology department
(3) Downloading software from the Internet without advance approval from the Information Technology department
(4) Modifying or altering installed software without advance approval from the Information Technology department
- Sensitive data must never be sent through clear-text using email or another messaging application. If sensitive data must be transmitted, encryption must be used to transmit the data.
- Do not circumvent security measures or the policies or procedures documented by the organization.
NONCOMPLIANCE OR POLICY VIOLATIONS
Noncompliance with this policy will be monitored, tracked, and handled by the organization’s Human Resource department and Information Technology department.
Any employees or authorized users that are in violation of this policy will be required to work with the Human Resources department for remediation.
This remediation effort may include review of the organization’s policies, retake of the security awareness training course, or other disciplinary actions.
ACKNOWLEDGEMENT
I have read, reviewed, and acknowledge that I understand this Acceptable Use Policy as it pertains to my job responsibilities and tasks.
Employee/User:
Name
Signature
Title
Date
Human Resources:
Name
Signature
Title
Date
Supervisor/Manager:
Name
Signature
Title
Date
Sample Company IT Policy |
Effective Date: |
SAMPLE COMPANY ACCESS CONTROL POLICY |
Enterprise or Departmental: Enterprise Policy |
| Approved: | |
| Executive Sponsor: | |
| Policy Revision # & Date: | |
| Subject: | |
| Data Classification Policy | |
PURPOSE
The intent of this policy is to provide the organization with a consistent definition for different classes of information. Once defined, all employees and users will access, use, handle, process, store, and transmit data consistently according to its classification. This is important given the sensitive data used by the organization.
SCOPE
The scope of this enterprise-wide policy includes all employees, authorized users, and authorized third parties who are granted access to the organization’s systems, applications, and data.
DEFINITIONS
Application owner—The owner or technical application lead responsible for the purchase and implementation of a software application used by the organization.
Data classification—The act of classifying data/information assets used by the organization.
Data governance—The definition for how the organization will use, handle, store, and/or transmit sensitive data.
Data owner—The technical lead responsible for the back-end database or other data repository that stores sensitive data. Typically, the data owner would be responsible and accountable for designing, testing, and ensuring that data encryption at rest can be enabled without performance degradation.
Department head—The department leader or supervisor who is ultimately responsible and accountable for the actions of the employees and authorized users in that department.
Encryption at rest—Actual data that resides in the back-end SQL database tables. Encryption at rest refers to the data being encrypted at rest within the actual SQL database table and data backup files. This means that the data is unreadable without the decryption key.
Nonpublic information (NPI)—Shall mean all electronic information that is not publicly available and is:
(1) Business-related information of an organization, the unauthorized disclosure, access, or use of which would cause a material adverse impact to the business, operations, or security of the organization
(2) Any information concerning an individual that, because of name, number, personal mark, or other identifier, can be used to identify such individual, in combination with any one or more of the following data elements: (i) Social Security number; (ii) driver’s license number or nondriver identification card number; (iii) account number, or credit or debit card number; (iv) any security code, access code, or password that would permit access to an individual’s financial account; or (v) biometric records
(3) Any information or data, except age or gender, in any form or medium created by or derived from a health care provider or an individual and that relates to (i) the past, present, or future physical, mental, or behavioral health or condition of any individual or a member of the individual’s family; (ii) the provision of health care to any individual; or (iii) payment for the provision of health care to any individual
Personally identifiable information (PII) data—Information that, if obtained, can be used to identify, contact, or locate a single person, or to identify an individual in context as a result of combining individual private data elements (e.g., first and last name, home address, Social Security number, date of birth, etc.).
POLICY
All employees, authorized users, and authorized third parties who are granted access controls to systems, applications, and data owned by the organization shall abide by this policy and the classifications of data.
It is the responsibility and accountability of each department head, application owner, and/or data owner to classify the data that is to be used, handled, stored, and transmitted on the organization’s network infrastructure.
The following schema will be used to classify data throughout the organization.
| CLASSIFICATION LEVEL | DESCRIPTION |
|---|---|
| Level 1 – Low Public Domain Low Sensitivity |
This category classifies data as Level 1 – Low. Data in this classification can be accessed and shared with the general public. No labeling or security controls are required when handling this category of data.Data classified in this category shall include but is not limited to:
|
| Level 2 – Medium Internal Business Use Only Medium Sensitivity |
This category identifies data that shall be labeled as Level 2 - Medium. Data in this classification shall be treated as confidential, Internal Business Use Only to be shared only with authorized users between the organization’s departments and employees.Data classified in this category shall include but is not limited to:
|
| Level 3 – High High Sensitivity | This category identifies data that shall be labeled as Level 3 – High. This classification is for the most sensitive data used, handled, stored, and/or transmitted throughout the organization’s network infrastructure and work environment.
Data classified in this category shall include but is not limited to:
|
MINIMUM SENSITIVITY LEVELS
The table below summarizes types of data utilized and stored throughout the network infrastructure by the organization and lists the minimum sensitivity level of these data categories or types.
This can be used as a guideline for classifying other forms of data that new applications may use, handle, store, or transmit.
| DATA CATEGORY | DESCRIPTION | MINIMUM CLASSIFICATION LEVEL |
|---|---|---|
| Investigative or Intelligence | Data under attorney–client privileged communications. Data/information related to investigations, law enforcement, subpoenas, court cases (not part of public record yet), and special operational activities. This includes information that could reasonably be expected to result in loss of life if inaccurate, disclosed, lost, or altered without permission. | 3 |
| Legal, Law Enforcement, and Emergency Response | Data/information related to legal, law enforcement activities, or emergency response that would adversely impact the organization or individual(s) involved if released. | 3 |
| Financial Data of Customers or the Organization | Customer or organization financial data that:(a) Is created or received by an organizational department or employee(b) Shall be fully encrypted in transmission; isolated from the rest of the organization’s network infrastructure; and, if in paper form, shall be stored in a physically secure room within the organization’s physical environment | 3 |
| Personally Identifiable Information (PII) DataSubject to Privacy Laws | Any item, collection, or grouping of data/information (e.g., PII) about a U.S. citizen or permanent resident employed by the organization (e.g., first and last name, home address, Social Security number, date of birth, etc.). | 3 |
| Emergency Operations and Procedures (BIA, BCP, DRP, and CSIRT Plan) | Information related to the organization’s IT security posture, including automated data processing security, internal operations, workflows, security controls, and risks, threats, and vulnerabilities.Organization’s internal security, emergency operations and procedures, IT documentation, business impact analysis (BIA), business continuity plan (BCP), disaster recovery plan (DRP), and computer security incident response team (CSIRT) plan shall be classified as Level 3 – High. | 3 |
| Financials, Business Workflows | Information related to the organization’s business partners’, vendors’, and contractors’ financials, taxes, revenue, accounting or commercial activities, business workflows, procurement, and any other nonexempt data. | 2 |
| Personnel | Data/information whose external or internal release would have a negative impact on an individual. | 2 |
| Internal Data for Business Use Only | Memos, spreadsheets, and documents containing general organizational business operations and information that would not be made generally available to the public. | 2 |
| External Data that Is ConsideredPublic Domain | Emails, memos, spreadsheets, SMS text messages, and documents containing general information that is not covered under Level 3 – High or Level 2 – Medium data classification definitions. This classification of data can be found in the public domain or can be shared in the public domain with no adverse effect or risk exposure to the organization. | 1 |
NON COMPLIANCE OR POLICY VIOLATIONS
Noncompliance with this policy will be monitored, tracked, and handled by the organization’s Information Technology department and Human Resources department.
The Information Technology department and each department head shall be held responsible and accountable for enforcing this policy throughout.
Resources, tools, and defined procedures are the responsibility of the Information Technology department and each application owner and/or data owner assigned.
APPROVAL
| Executive or Board Level Review & Approval: | _______________________ (Name) _______________________ (Title) _______________________ (Signature) _______________________ (Date) |
REVISIONS
| REVISION DATE | AUTHOR | DESCRIPTION |
|---|---|---|
Sample Company IT Policy |
Effective Date: |
SAMPLE COMPANY ACCESS CONTROL POLICY |
Enterprise or Departmental: Enterprise Policy |
| Approved: | |
| Executive Sponsor: | |
| Policy Revision # & Date: | |
| Subject: | |
| Network Security Policy | |
PURPOSE
The intent of this policy is to provide the organization’s Information Technology department with a clear and concise definition of why, where, and how to implement network security controls. By security control we mean any of the following:
- A network design or network security configuration implementation that addresses availability, integrity, or confidentiality
- The creation of IEEE 802.1Q virtual LANs (VLANs) to segment IP data networking traffic
- The use of internal firewalls and/or access control lists (ACLs) to shape traffic flow
- The implementation of redundant network connections to support highly available business functions and operations
- The design and implementation of a layered network security architecture starting at the perimeter or LAN-to-WAN Domain and including the Remote Access Domain
SCOPE
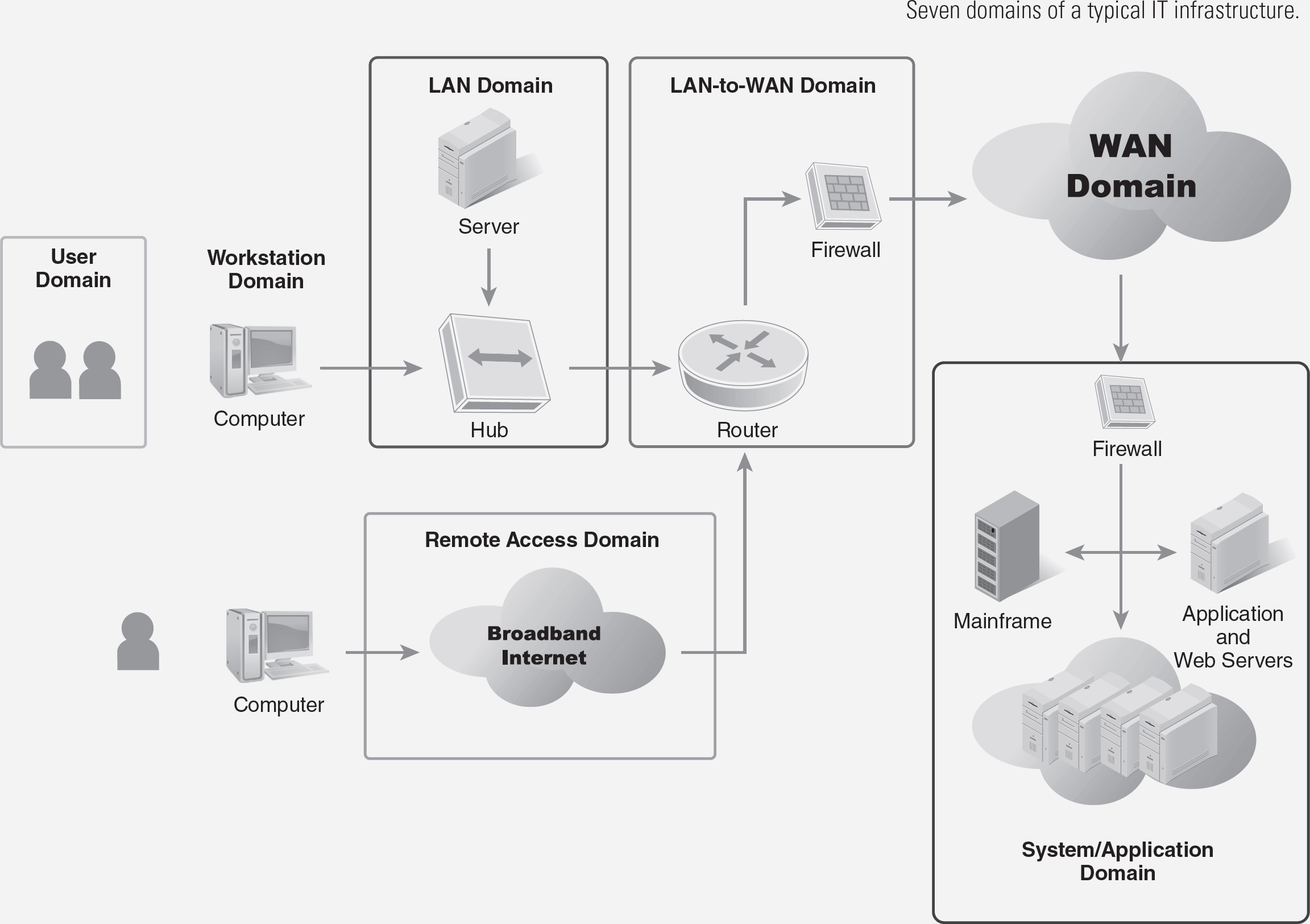
The scope of this enterprise-wide policy includes the following domains within the seven domains of a typical IT infrastructure (see figure on next page):
- LAN Domain—Network backbone, distribution, and edge LAN switches
- LAN-to-WAN Domain—DMZ/VLAN, public-facing IP hosts, firewall, intrusion detection system/intrusion protection system (IDS/IPS), and audit and monitoring
- WAN Domain—Public Internet or other wide area network (WAN) service
- System/Application Domain—Virtual servers, servers, server farm switches, and virtual networks
DEFINITIONS
Access control list (ACL)—A software configuration that acts like a filter in a Layer 3 switch or router. The ACL can be set to permit or deny IP packet header or port number information. Forwarding or filtering decisions are made at the interface level.
Demilitarized zone (DMZ)—An IP subnetwork that interconnects a private, closed IP data network with the public Internet within the LAN-to-WAN Domain. The DMZ is positioned at the IP data network’s perimeter, which contains and exposes an organization's external-facing services to a larger and untrusted network, such as the public Internet.
Firewall—A software or hardware-based network security device that controls incoming and outgoing IP network traffic. A stateful firewall means the IP packet header will be examined to determine whether packets should be forwarded or filtered based on applied IP and UDP/TCP rule sets. An IP stateful firewall provides an additional layer of security prior to an IP packet being forwarded to a secure IP data networking subnetwork or VLAN. The firewall also acts as the last line of defense for system and application servers that may have an internal firewall enabled on the server itself.
Virtual LAN (VLAN)—A Layer 2 IEEE 802.3 CSMA/CD Ethernet-based broadcast domain. Configuration of a Layer 2 virtual LAN (VLAN) is defined in the IEEE 802.1Q VLAN standard definition. Users in the same department are typically on the same Ethernet broadcast domain.
POLICY
This Network Security Policy requires the Information Technology department to build baseline definitions to ensure the confidentiality, integrity, and availability of system and network resources.
The following presents the policy requirements:
- Design and implement a closed internal IP data networking environment. (Closed means a secure, no-back-door point of entry into the IP data networking environment.)
- Design and implement segmented physical and logical IP subnetworks using IEEE 802.1Q Layer 2, virtual LAN (VLAN) technology to support the following VLANs:
- DMZ VLAN—External public-facing IPs where the closed network interconnects with the public Internet
- Server Farm VLAN—Dedicated VLANs for server farms, virtual hosts, and clusters
- Departmental VLAN—A locked-down Layer 2 VLAN to which only users of that department are logically connected
- Design and implement Layer 3 backbone networks where alternate routes are needed for the IP data network infrastructure to achieve an availability of 99.5% uptime.
- No unauthorized connections to the organization’s IP data networking infrastructure are permitted. Any rogue IT devices connected to the organization’s IP data network will be removed if determined to be a rogue IT asset or device.
- The organization has the right to audit and monitor all network connections and network traffic initiated by the employees, users, and authorized third parties.
- The production IP data network will have performance baseline definitions defined for:
- Core backbone network, server farm network, WAN infrastructure, and Internet access link
- Capacity planning, performance metrics, and growth projections are required in monthly reports
NON COMPLIANCE OR POLICY VIOLATIONS
Noncompliance with this policy will be monitored, tracked, and handled by the organization’s Information Technology department.
The Information Technology department shall be held responsible and accountable for enforcing this policy throughout.
Resources, tools, and defined procedures are the responsibility of the Information Technology department and the owner of this policy.
APPROVAL
| Executive or Board Level Review & Approval: | _______________________ (Name) _______________________ (Title) _______________________ (Signature) _______________________ (Date) |
REVISIONS
| REVISION DATE | AUTHOR | DESCRIPTION |
|---|---|---|
-
No Comment