The Internet Protocol
The primary protocol that relays packets across most of today’s diverse networks is the Internet Protocol (IP). IP is the most popular Layer 3 protocol for both large and small networks. The appeal of IP is in its ability to span networks. Network devices can efficiently use switching to direct packets to the correct destination in the same network; however, to direct packets to destinations outside the network, devices must examine the Layer 3 network address and route each packet to its destination. IP provides packet routing and host identification to deliver packets to their destinations. IP treats all packets, also called datagrams, separately. It doesn’t support the concept of grouping packets together. This means that each packet needs complete address information for the source and destination hosts. Each packet also needs sequence information to tell the destination how to reassemble the packets into the original message.
IP’s primary service is packet routing, so the protocol relies solely on the network address to determine each packet’s next logical step as it travels to its destination. IP defines methods to address network devices to optimize routing efficiency. Each packet contains a header with the destination’s IP address (see FIGURES 5-3 and 5-4). This address identifies the destination host and provides information about the logical location of the host in its network. IP receives a packet from a higher layer, normally Layer 4, and adds additional data in a new IP header to the packet. The process of adding the IP header data is called encapsulation.
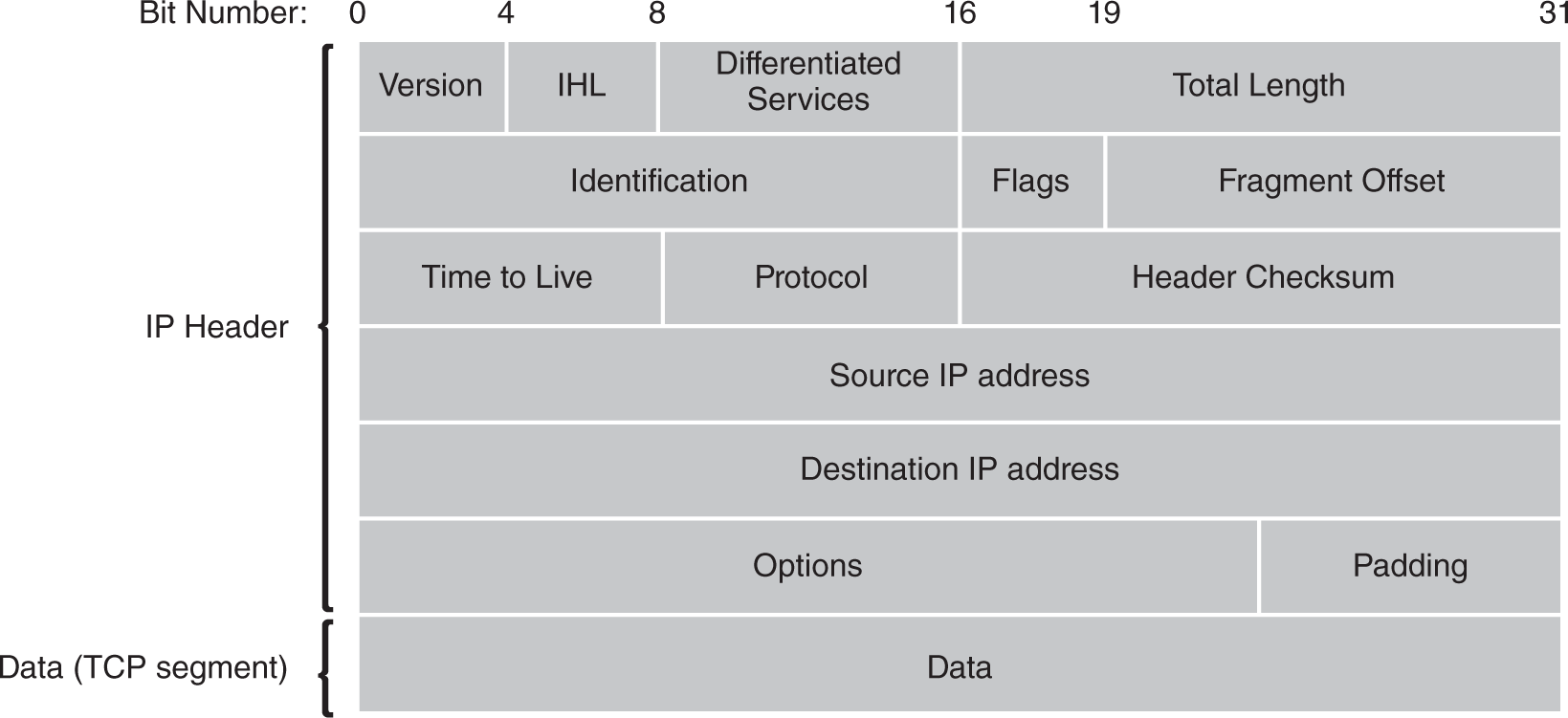
FIGURE 5-3 IPv4 packet header.
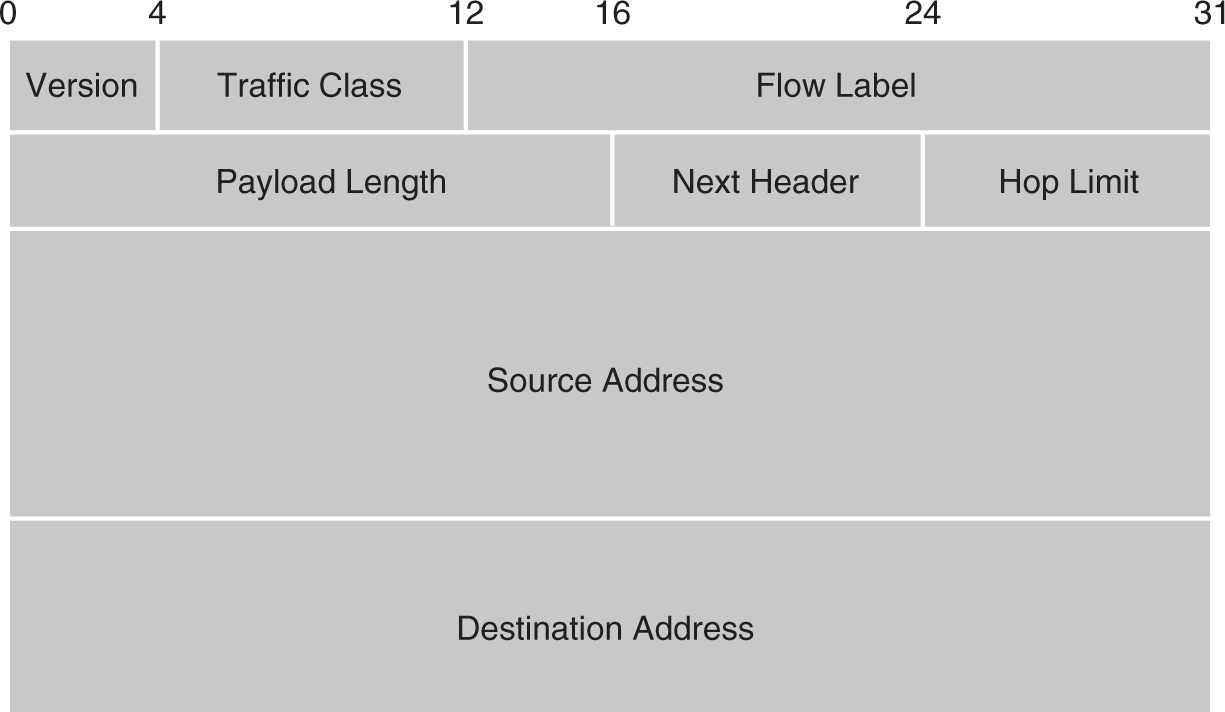
FIGURE 5-4 IPv6 packet header.
IP does more than just address packets. IPv4 provides the following services:
- Version—A 4-bit value that signifies which IP version is being used, such as version 4 for IPv4.
- Addressing—Each IP header contains 32-bit addresses that identify the source and destination hosts. Intermediate routers that use these addresses choose a path through the network for the packet.
- Fragmentation—The IP software may chop packets into smaller packets. This process is called fragmentation. Fragmentation allows computers to send large packets across a network that can handle only smaller packets. The source computer fragments packets, and the destination computer reassembles packets. Both processes occur transparently.
- Packet timeouts—IP adds a Time To Live (TTL) value to each packet header. Each router that handles the packet decrements the TTL value. If TTL reaches zero, the current router drops the packet. This protection mechanism keeps packets from following circular paths and flooding a network.
- Type of service—IP allows software to prioritize network traffic. Each IP packet contains header data that labels the packet with a type of service. Network devices can use these labels to handle packets with a higher or lower priority.
- Additional features—IP supports several optional features, including:
- Source routing—Allows the source to set requirements on the path the packet takes through the network
- Record route—Traces the route a packet takes
- Security labels—Assign security features label to packets
IPv6 introduced a more streamlined packet format design. IPv6 provides the following services:
- Version—A 4-bit value that signifies which IP version is being used. For IPv6, this value is 6.
- Traffic class—An 8-bit field used by source hosts and forwarding routers to distinguish classes or priorities for IPv6 packets.
- Flow label—IPv6 allows sources to designate special handling by routers, such as nondefault quality of service (QoS) or real-time applications or service.
- Addressing—Each IP header contains 128-bit addresses that identify the source and destination hosts. Intermediate routers that use these addresses choose a path through the network for the packet.
Two of the most consistent characteristics of networks are that the components are unreliable, and the best route through the network at any time is dynamic. Although today’s network hardware and software are far more reliable than at any time in the past, networks still do fall short of their goals. Components may fail at any time and may cause gaps in the network topology. Excessive use can cause network performance to suffer. In most networks, the best path between any two nodes depends on current conditions. The best path during low use may not be the same path when many applications are using the network. In any case, it’s unwise for any software to assume the network is reliable or static all of the time. IP helps address reliability issues and ensures that packets make it to their destination.
It may not seem difficult to monitor a network’s performance and to select the best path between nodes, but the task is more difficult than it appears. IP networks have no central authority to monitor and control components and traffic. This design feature means that the end nodes contain most of the necessary network information. The source node sends a message based on that node’s view of the network. Each subsequent network device forwards the packets based on its current view of connected networks. Each packet progressively makes its way from its source to its target, based on the destination host address (see FIGURE 5-5).
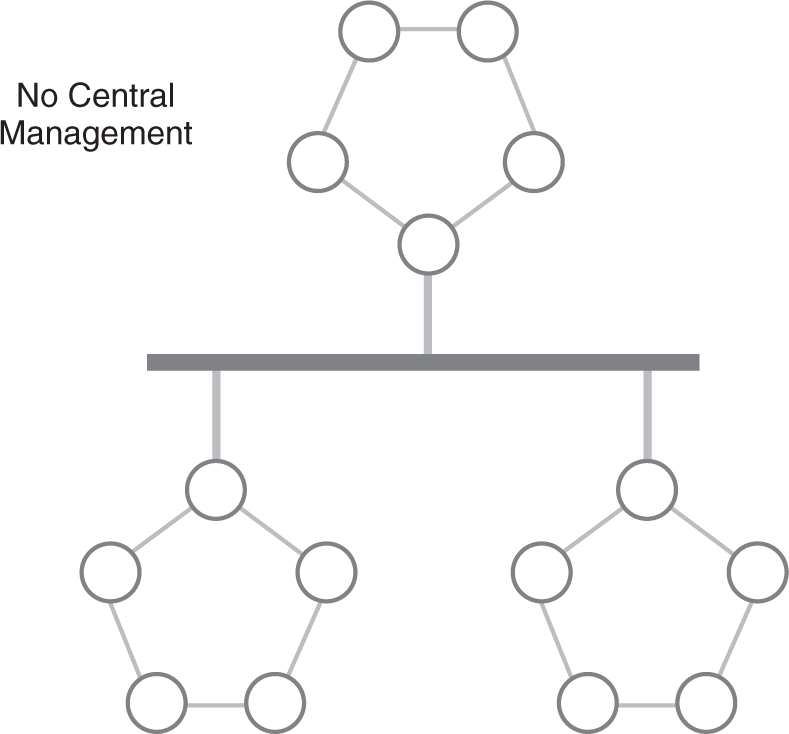
FIGURE 5-5 Decentralized IP network.
Because IP networks are decentralized and dynamic, there is always the possibility that a packet won’t reach its destination node. Even if the packet does reach its destination, it may be different from the original packet. Errors or malicious software can change packets as they travel across a network. Source nodes need to know when a packet does not reach its destination, and destination nodes need to be able to detect when a packet changed during transmission. IP doesn’t provide automatic notification of lost packets. Upper layers handle lost packets.
FYI
The decentralized nature of IP networks is one of its original design goals. IP was one of the original protocols developed for the U.S. Department of Defense’s networks. The designers wanted a decentralized network design that could withstand enemy attacks and still operate. An IP network can do just that. As long as network devices can find a path between a packet’s source and destination, the network can still operate.
The earlier IP version, IPv4, includes a checksum for each packet header (see FIGURE 5-6). The checksum is a numeric value that represents the entire header. The checksum changes when any part of a header changes. Checksums are an easy way for any network node to tell if a header has changed. Each node can calculate a new checksum for a packet header and compare it to the stored checksum. If the two checksums are different, the packet header has changed during transmission. Although this method helps nodes detect errors and changes, it takes time to process each header. The newer version of IP, IPv6, does not include checksums. This decision was made to increase IP’s performance and its ability to quickly route a packet with minimal overhead. Error detection and correction is left to upper layer protocols.
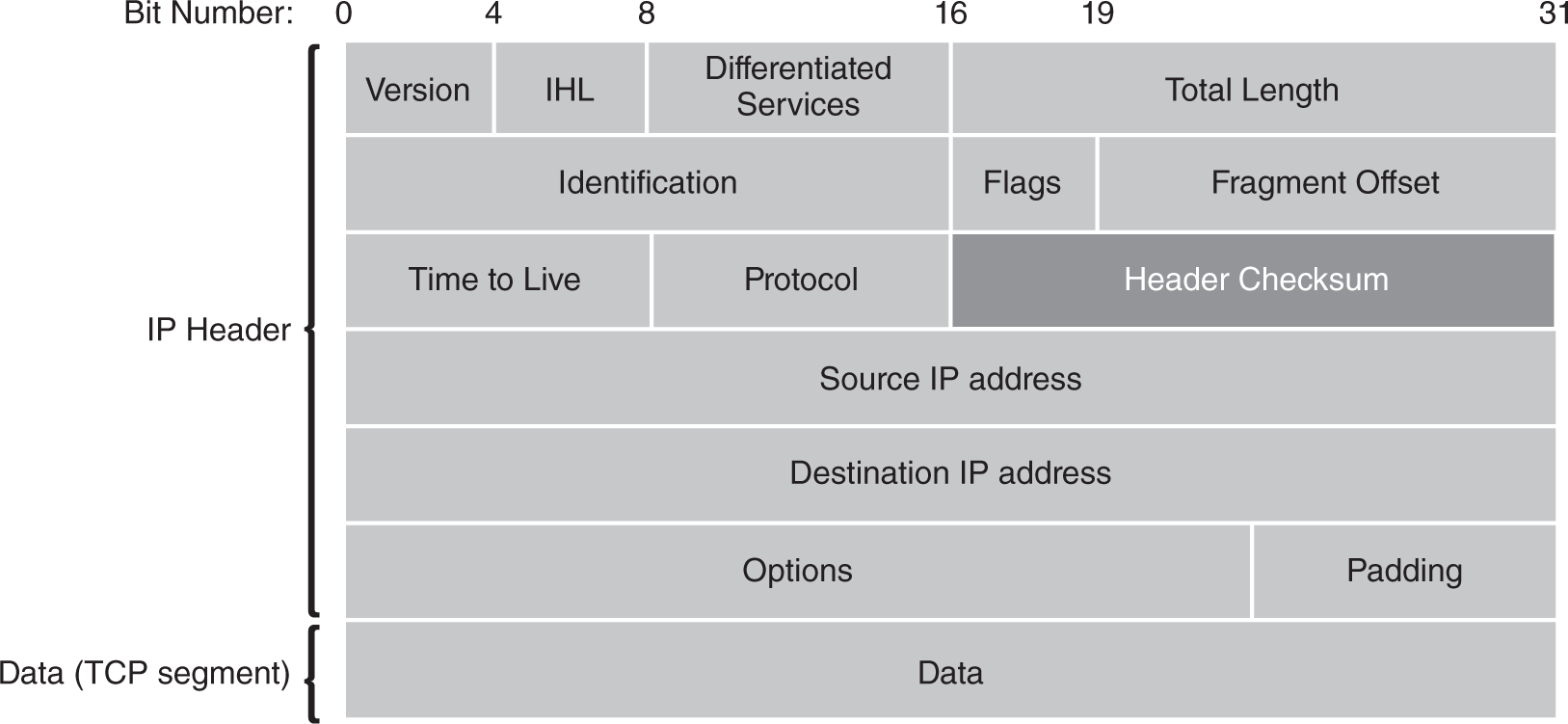
FIGURE 5-6 IPv6 header checksum.
IP earns its place in today’s networks by providing a robust method to address nodes and to route packets between nodes. A node’s IP address defines its logical subnetwork. Network IP addresses provide information about how the organization designed the network and how it grouped nodes together. They also show how the organization divides nodes into separate logical groups. A good IP addressing strategy can make an IP network more efficient and more functional. Placing nodes that communicate frequently in the same subnetwork can reduce the overhead required to route packets between the nodes. A sensible addressing strategy also makes a network easier to understand and manage. You will learn about different IP addressing options in the next section.
