Access Controls
Access controls are needed to identify, authenticate, and authorize users, and to account for them through monitoring. Access can come in different layers. The more sensitive the data being accessed, the more layers of security controls are needed. A user may require any or all of the following access controls:
- Network access controls for local and WLAN access
- Local access controls when sitting in a workspace
- Wireless access controls when mobile at a workplace
- Local access with multifactor authentication
- Network access controls that support remote access with multifactor authentication
- Remote access to a web-hosted Software as a Service (SaaS) application or secure portal (e.g., HTTPS, with updated digital certificates) that requires access controls with multifactor authentication
Identification, Authentication, Authorization, and Accounting
Identification is the process of confirming a specific user. Each user must have a unique user ID to identify themselves. Just like duplicate IP addresses, duplicate user IDs cannot exist on a network. Examples of user IDs include email address, employee ID number, first initial plus last name, and other alphanumeric usernames. The user ID is what is used to uniquely assign role-based access control to systems, applications, and data. It is important that each user uses only their own user ID. Uniquely identifying an authorized user is important to audit trails and logs.
Authentication is the method for verifying the user is who they say they are. How do computer systems and applications authenticate a user? There are multiple methods:
- Something the user knows, such as a password or PIN number
- Something the user has, such as a hardware fob, a soft token, or an SMS text message of a PIN number
- Something the user is, such as biometrics (fingerprint, facial recognition, etc.)
- Somewhere the user is, such as Global Positioning System (GPS) location finder data
- Something the user does, such as their profession
Each of these individual methods can be combined to create a multifactor authentication solution prior to granting a user access. Multifactor means two-factor, three-factor, or higher. This is critical for applications that contain sensitive data.
Local authentication means the authentication mechanism is embedded in the application itself and hosted by the server. Application developers sometimes include access control front ends that require user authentication. This is referred to as local authentication when it is between the user and the server on the same network.
Technical TIP
Several authentication servers are commonly deployed:
- RADIUS—Remote Authentication Dial-In User Service (RADIUS) is a networking protocol operating on port 1812. RADIUS supports authentication, authorization, and accounting management. RADIUS uses User Datagram Protocol (UDP).
- TACACS+—Terminal Access Controller Access Control Server (TACACS+) is a security protocol. TACACS+ supports authentication, authorization, and accounting management for users who want to gain access to the network. TACACS+ uses Transmission Control Protocol (TCP).
- Kerberos—Kerberos is a network authentication protocol that works on the basis of tickets that permit endpoints to communicate over a nonsecure network. Endpoints confirm their identity to one another in a secure manner.
- Windows Active Directory domain controllers—A domain controller (DC) server responds to security authentication requests from Windows endpoints.
RADIUS and TACACS+ servers are commonly used for system administrators and IT personnel for both local and remote access to IT systems. FIGURE 9-7 depicts a RADIUS authentication server dialoguing with a user’s laptop computer.
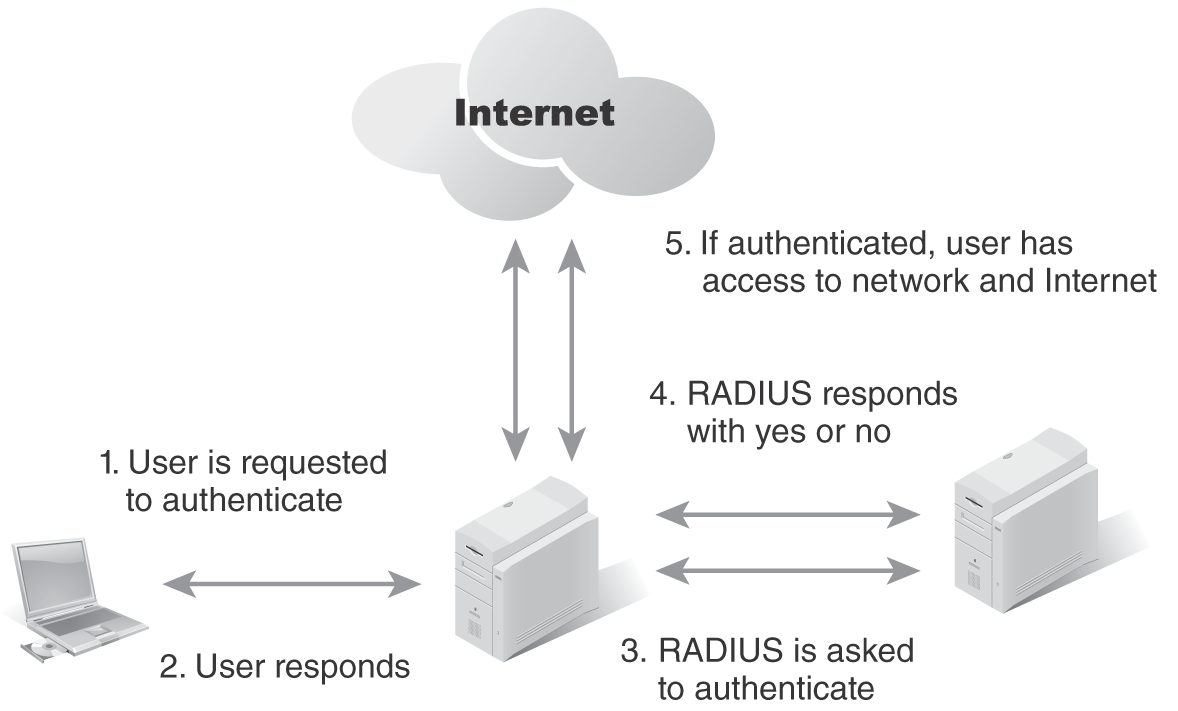
FIGURE 9-7 RADIUS server authentication.
Authorization means the user is preapproved to gain access. This access is based on job role and access to systems, applications, and data. Authorization is provided by the human resources department as well as the department head who hired the user. Job roles define the systems, applications, and data the user needs to access to perform the job tasks. This is where role based access control (RBAC) comes into play. Preauthorization allows for immediate access to the applications needed to perform the job function. Once HR clears the new user, access controls are granted.
Accounting refers to continuous monitoring. Each user’s audit trails and logs are part of accounting. Capturing user audit trails and logs provides a complete view of the user’s interaction with systems, applications, and data. Accounting provides access, duration, and other metrics that can be measured. It also can help with capacity planning, network performance, and incident response. Trending and baselining can be defined with proper accounting. FIGURE 9-8 shows how a NAC device provides a prescreening function based on a policy definition for different endpoints.
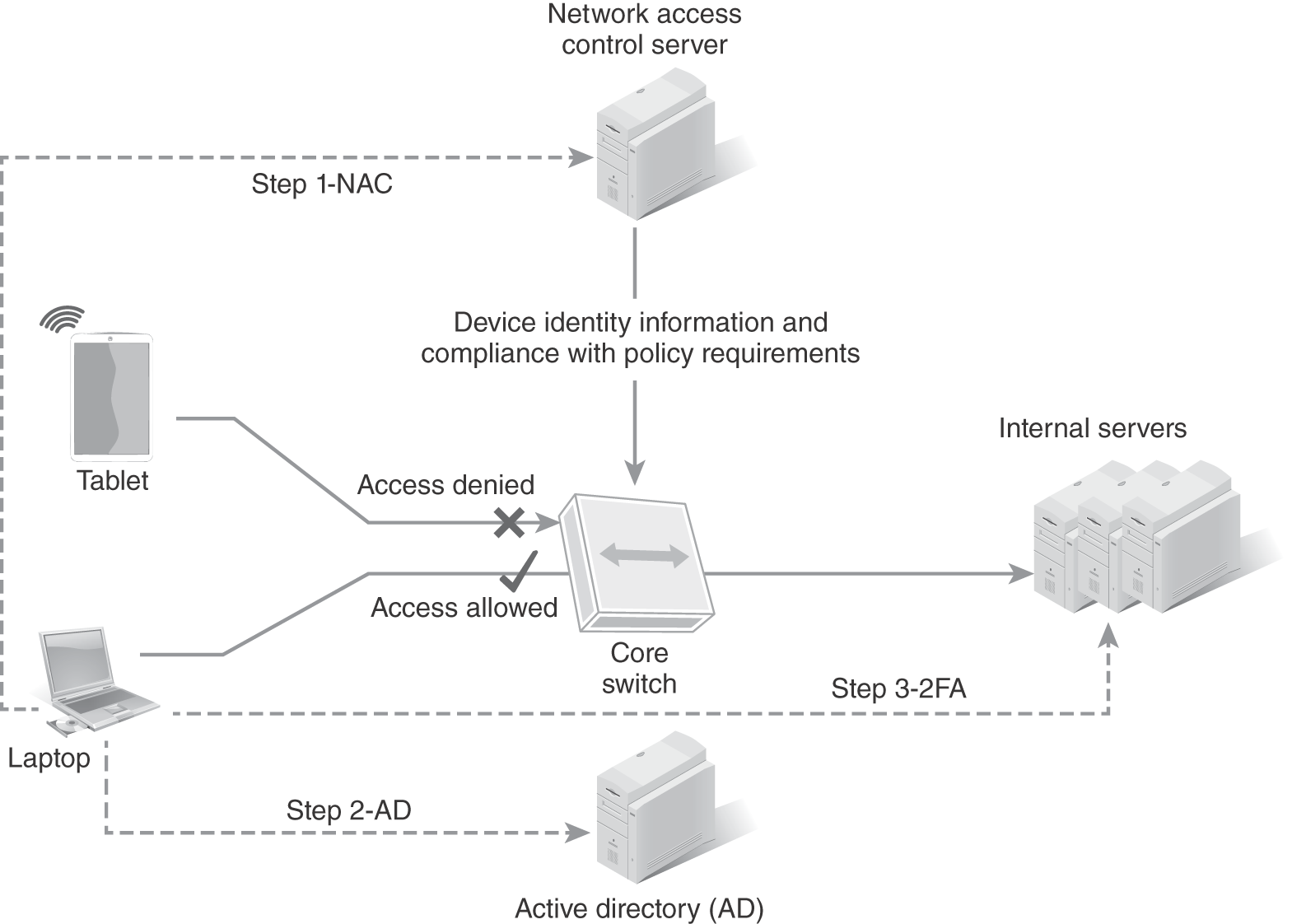
FIGURE 9-8 NAC with ID and authentication to Windows Active Directory.
Two additional technologies that have come about are single sign-on (SSO) and identity access management (IAM). Users that have different job functions require access to different systems and applications. This can be cumbersome when a user has access to many different systems and applications. SSO solves that problem by providing the user with a single login and password authentication requirement. In order for SSO to work effectively, role-based access control must be set up to provide seamless authentication.
As organizations grow in size, the number of users, applications, and their access become increasingly more difficult to manage and control. Identity access management (IAM) integrates user or group identification, authentication, and authorization for application access by associating user rights and restrictions with user profiles or identities.
Remote Access Controls and Multifactor Authentication
Mobile users or teleworkers require a remote access solution to access an organization’s LAN, systems, applications, and data. Remote access is typically supported via one of two methods:
- An IPSec VPN connection coupled with two-factor authentication
- An application gateway that requires ID and authentication with two-factor authentication
Remote access to any sensitive data must have at least two-factor or more authentication with audit and monitoring enabled to capture all logs.
