Namespaces offer another form of isolation for process interaction within operating systems, creating the workspace we call a container. Linux namespaces are created via a syscall named unshare, while clone and setns allow you to manipulate namespaces in other manners.
Namespaces limit the visibility a process has on other processes, networking, filesystems, and user ID components. Container processes are limited to seeing only what is in the same namespace. Processes from containers or the host processes are not directly accessible from within this container process. Additionally, Docker gives each container its own networking stack that protects the sockets and interfaces in a similar fashion.
If cgroups limit how much of a thing you can use, namespaces limit what things you can see. The following diagram shows the composition of a container:
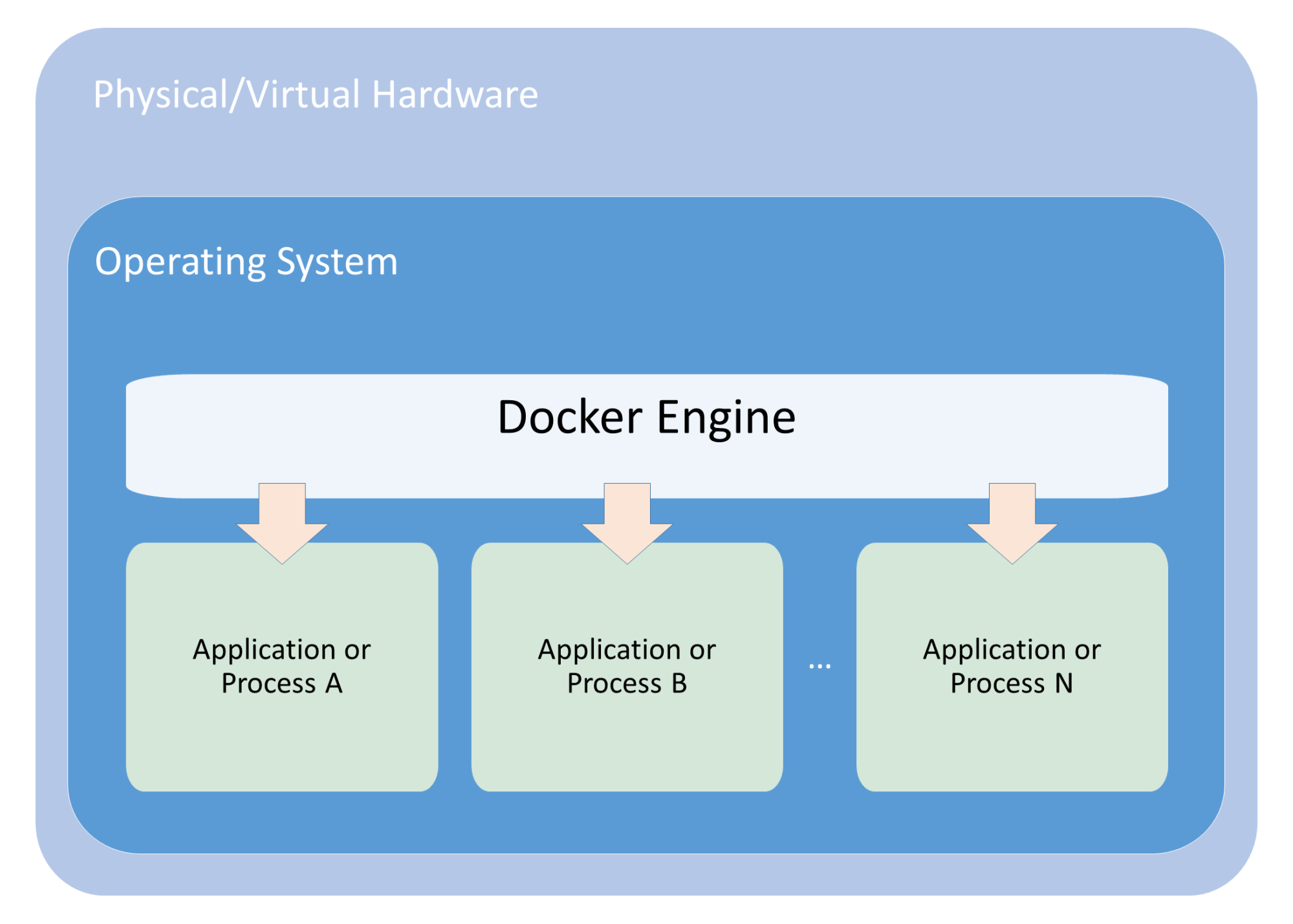
In the case of the Docker engine, the following namespaces are used:
- pid: Provides process isolation via an independent set of process IDs from other namespaces. These are nested.
- net: Manages network interfaces by virtualizing the network stack through providing a loopback interface, and can create physical and virtual network interfaces that exist in a single namespace at a time.
- ipc: Manages access to interprocess communication.
- mnt: Controls filesystem mount points. These were the first kind of namespaces created in the Linux kernel, and can be private or shared.
- uts: The Unix time-sharing system isolates version IDs and kernel by allowing a single system to provide different host and domain naming schemes to different processes. The processes gethostname and sethostname use this namespace.
- user: This namespace allows you to map UID/GID from container to host, and prevents the need for extra configuration in the container.
