Configuring Azure MFA for your users is really very simple—just perform the following steps:
- Sign in to the Azure portal with an administrator account and navigate to Azure Active Directory| Users and Groups | All users. Then, click on Multi-factor Authentication:

- A new page will be opened where you can see the MFA status of each user. Here, you can bulk update the status for all your users or you can select the users for which you want to update their MFA status:

- You can also manage this task with Azure Powershell (this is my recommended way if you need to activate MFA for a long list of users). With Azure Powershell, you can perform this task with a script like this:
$users = "[email protected]","[email protected]","[email protected]",
"[email protected]"
foreach ($user in $users)
{
$st = New-Object -TypeName Microsoft.Online.Administration.StrongAuthenticationRequirement
$st.RelyingParty = "*"
$st.State = “Enabled”
$sta = @($st)
Set-MsolUser -UserPrincipalName $user
-StrongAuthenticationRequirements $sta
}
- If you want to enable Azure MFA with a conditional policy, in the Azure portal, you need to select Azure Active Directory | Conditional Access:

- On the Conditional access blade, click on Add and then in the New blade, type the name of your new policy:
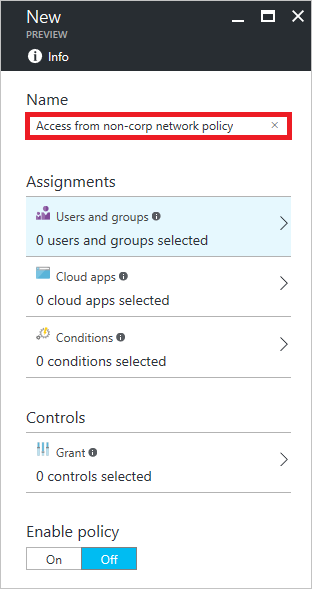
- In the Assignments section, navigate to Users and groups | Select users and groups | Select and select your users:

- Now, click on the Cloud apps section, then navigate to Select apps | Select and select your cloud app:

- After that, select the Conditions section and then click on Locations. Here, click on Yes in the Configure section and All locations in the Include section:

- Then, click on the Exclude tab and check the All Trusted IPs checkbox (so your trusted IP addresses will be exempt from the policy implemented):

- After confirming the operation (by clicking on the Done button), go back to the Controls option and click on Grant:

- On the Grant option window, select the Allow access option and check Require multi-factor authentication and Require all the selected controls:

- Now, as the last step, go back to the New blade, select Enable policy as ON and click on Create in order to create your conditional access policy:

For more details on conditional access activation, I recommend checking this link: https://docs.microsoft.com/en-us/azure/active-directory/active-directory-conditional-access-azure-portal
