Chapter 4. Configuring the Cisco Unity Connection System
Upon completing this chapter, you will be able to do the following:
![]() Describe the Cisco Unity Connection system settings
Describe the Cisco Unity Connection system settings
![]() Explain the inheritance and precedence of settings when configuring user or call handler settings
Explain the inheritance and precedence of settings when configuring user or call handler settings
![]() Describe the Cisco Unity Connection general settings, including time and localization settings
Describe the Cisco Unity Connection general settings, including time and localization settings
![]() Describe a scenario where time zones are used in different locations of a centralized voice-messaging solution
Describe a scenario where time zones are used in different locations of a centralized voice-messaging solution
![]() Explain the system distribution lists in Cisco Unity Connection and how they are used to send voice messages to multiple users
Explain the system distribution lists in Cisco Unity Connection and how they are used to send voice messages to multiple users
![]() Describe the authentication rules that are used to secure access to Cisco Unity Connection
Describe the authentication rules that are used to secure access to Cisco Unity Connection
![]() Describe the roles that can be assigned to users in Cisco Unity Connection to give them administrator access rights for limited parts of the system
Describe the roles that can be assigned to users in Cisco Unity Connection to give them administrator access rights for limited parts of the system
![]() Describe the restriction tables that can be used to prevent calls such as calls to long-distance or international phone numbers
Describe the restriction tables that can be used to prevent calls such as calls to long-distance or international phone numbers
![]() Describe the components of LDAP integration: LDAP synchronization and LDAP authentication
Describe the components of LDAP integration: LDAP synchronization and LDAP authentication
![]() Explain how to import users from an LDAP server
Explain how to import users from an LDAP server
![]() Describe how to automatically convert the synchronized extension of LDAP users
Describe how to automatically convert the synchronized extension of LDAP users
![]() Explain the search base for the user selection and synchronization
Explain the search base for the user selection and synchronization
![]() Explain how an LDAP filter is used to optimize the user selection and synchronization results
Explain how an LDAP filter is used to optimize the user selection and synchronization results
This chapter explains Cisco Unity Connection system settings, which contain many configuration options. The chapter also discusses schedules and holiday schedules and their effect on greetings, announcements and so on. System distribution lists and authentication rules are described in more detail, followed by roles and restriction tables to restrict calls for message notification or caller transfer. User templates help you to efficiently create user accounts that are based on standardized templates. Users can be imported from the Lightweight Directory Access Protocol (LDAP) server or Cisco Unified Communications Manager.
Cisco Unity Connection System Settings Overview
This section describes the Cisco Unity Connection system settings.
The system settings in Cisco Unity Connection enable the administrator to modify the default system behavior. Figure 4-1 lists several examples and shows the system settings menu options.
The predefined roles can be used to limit the graphical user interface (GUI) access to certain configuration areas or to limit the telephony user interface (TUI) options for different kinds of administrators.
The enterprise and service parameters in Cisco Unity Connection are like the Cisco Unified Communications Manager (CUCM) enterprise parameters and service parameters. For instance, there are the parameters that allow you to change quality of service (QoS) settings and so on.
LDAP can be integrated and allows the use of the LDAP directory and LDAP authentication. With the use of LDAP authentication, a single password login can be provided to the users.
General Settings Versus User Settings
This section explains the inheritance and precedence of settings when configuring user or call handler settings.
As in CUCM, parameters can be set in the enterprise or service parameters, which are valid for all entities in the Cisco Unity Connection system. A change in the enterprise or service parameters immediately affects all entities. Default parameters, such as a default partition, are preselected for all new objects that contain that parameter field. Figure 4-2 illustrates the inheritance and precedence of settings.
The next level of parameter settings is the general settings, which can alter system settings. A change at this level immediately affects all entities.
A call handler answer calls and can take messages and provide menus of options (for example, “For customer service press 1, for sales press 2”), route calls to users and to other call handlers, and play audiotext (prerecorded information).
The user, call handler, and contact templates can override the general settings, applicable to new objects, because parameters are copied from the template during the creation of a new object, which is called initial mode. A change to a template does not affect existing objects.
On the user account, call handler, and contact level, a configuration parameter overrides the general settings and takes precedence. If, for instance, a manager needs additional mailbox space for voice messages, the mailbox quota setting can be modified on the user account level for the manager account only.
General Configuration
This section describes the Cisco Unity Connection general settings, including time and localization settings. Table 4-1 shows the Unity Connection general configuration and the time zone options.
In Unity Connection, you create partitions as a way to group together objects to which callers and users can address messages or place calls while interacting with Unity Connection. One or more partitions can be grouped together as members of a search space, and a partition can be a member of more than one search space.
Search spaces are used to define the search scope of objects (users, distribution lists, and so on) that a user or outside caller can reach while interacting with Unity Connection. For example, the search scope that is applied to a user identifies which users, distribution lists, or Voice Profile for Internet Messaging (VPIM) contacts the user can address messages to. The search scope that is applied to a user also identifies which users and contacts the user can call by name dialing when using the voice-recognition conversation.
In Cisco Unity Connection Administration, choose System Settings > General Configuration to modify the following preconfigured settings:
![]() The default time zone setting determines when schedules are active. In addition, the default time zone is applied to users and call handlers that have the Use Default Time Zone check box checked.
The default time zone setting determines when schedules are active. In addition, the default time zone is applied to users and call handlers that have the Use Default Time Zone check box checked.
![]() From the System Default Language drop-down list, choose the language in which system prompts are played to users and callers. Additional language files can be loaded after installation. Languages are not licensed, and Cisco Unity Connection 10.x does not enforce a limit on the number of languages you can install and use. However, the more languages you install, the less hard disk space is available for storing voice messages. For details, see the “Adding or Removing Unity Connection Languages” section of the Install, Upgrade, and Maintenance Guide for Cisco Unity Connection Release 10.x document available at http://www.cisco.com/c/en/us/td/docs/voice_ip_comm/connection/10x/install_upgrade/guide/10xcuciumgx.html:
From the System Default Language drop-down list, choose the language in which system prompts are played to users and callers. Additional language files can be loaded after installation. Languages are not licensed, and Cisco Unity Connection 10.x does not enforce a limit on the number of languages you can install and use. However, the more languages you install, the less hard disk space is available for storing voice messages. For details, see the “Adding or Removing Unity Connection Languages” section of the Install, Upgrade, and Maintenance Guide for Cisco Unity Connection Release 10.x document available at http://www.cisco.com/c/en/us/td/docs/voice_ip_comm/connection/10x/install_upgrade/guide/10xcuciumgx.html:
![]() From the Recording Format drop-down list, choose the default format (codec) for recorded messages. The default setting is G.711 mu-law. The other options are PCM linear, G.711 a-law, G.729A, G.726, and GSM 06.10.
From the Recording Format drop-down list, choose the default format (codec) for recorded messages. The default setting is G.711 mu-law. The other options are PCM linear, G.711 a-law, G.729A, G.726, and GSM 06.10.
![]() Enter the maximum greeting length for system call handler greetings. The range is 1 to 1200 seconds; the default setting is 90 seconds.
Enter the maximum greeting length for system call handler greetings. The range is 1 to 1200 seconds; the default setting is 90 seconds.
![]() If automatic gain control (AGC) is enabled, enter the average volume, in decibels, that Cisco Unity Connection automatically maintains for recording voice messages and user greetings, in the Target Decibel Level for Recordings and Messages area. The AGC decibel levels are set in negative numbers.
If automatic gain control (AGC) is enabled, enter the average volume, in decibels, that Cisco Unity Connection automatically maintains for recording voice messages and user greetings, in the Target Decibel Level for Recordings and Messages area. The AGC decibel levels are set in negative numbers.
![]() From the Default Partition and Default Search drop-down lists, choose the partition and search space that Cisco Unity Connection uses as the default when creating new objects, such as users or templates. If these options are modified in a template, such as when creating a new user, the template settings will be used instead of the default settings.
From the Default Partition and Default Search drop-down lists, choose the partition and search space that Cisco Unity Connection uses as the default when creating new objects, such as users or templates. If these options are modified in a template, such as when creating a new user, the template settings will be used instead of the default settings.
The time settings are configured in Cisco Unified Operating System Administration, under Settings > NTP Servers. Ensure that the external server is stratum 9 or better (9 to 1). The NTP server settings can be configured only on the first node or publisher.
You must have an NTP server reachable for Unity Connection to be installed.
The time zone that is set during the Cisco Unity Connection installation can be changed only via CLI. Any change that is made to the NTP servers can take as many as 5 minutes to take effect.
To see the currently configured time zone, issue the show timezone config command. Use the show timezone list command to search for the correct time zone. Use the set timezone command to change the time zone; for example, use the option 152 to indicate New York time.
A reason to change the time zone could be that a Cisco Unity Connection server has moved to another location (time zone). A wrong time zone makes the time stamps in the Cisco Unity Connection system wrong, which could represent a difficulty when troubleshooting different Cisco Unified Communications systems at the same time. The time zone must be configured on Unity Connection.
Time Zone Usage
This section describes a scenario in which time zones are used at different locations of a centralized voice-messaging solution.
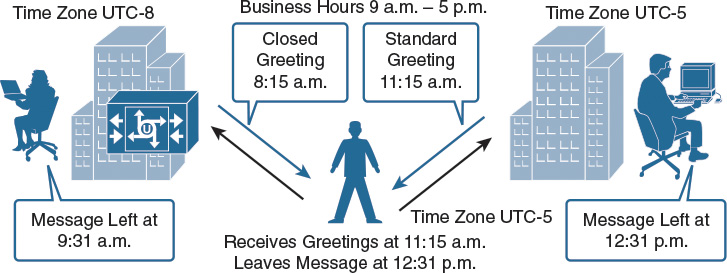
Figure 4-3 shows a centralized Cisco Unity Connection system with users in two locations in different time zones.
Mailboxes, call handlers, greetings, and other objects in Cisco Unity Connection rely on the time zone and a schedule. Users with a schedule that is set to business hours—Monday through Friday from 9:00 a.m. to 5:00 p.m. (0900 to 1700)—has an active standard transfer rule on their mailbox during this time.
For example, in combination with time zone settings, the business hours are set to eastern standard time (EST, coordinated universal time [UTC] –5 hours). A call that originates at 4:00 p.m. (1600) Pacific standard time (PST, UTC –8 hours), and that is directed to a Cisco Unity Connection system based in the EST zone, actually reaches Cisco Unity Connection at 7:00 p.m. (1900).
In the example, the business hours are set to Monday through Friday from 9:00 a.m. to 5:00 p.m. (0900 to 1700). The time zones are set to UTC –5 and to UTC –8. If a caller who is based in EST calls a local number at 11:15 a.m. (1115), Cisco Unity Connection answers the call at 11:15 a.m. (1115). If the caller dials a number that is based in PST, the call arrives at 8:15 a.m. (0815) PST and Cisco Unity Connection plays a closed greeting, according to the business hour schedule.
The time zones are used in different ways. When a call is forwarded to voice mail, the configured time zone of the called user controls the announcement, depending on the time when the message is left. The greeting (for example, standard or closed) is also chosen according to the time of the call at the called location, in combination with a schedule. The same is true for the call handlers.
Schedules are one of the variables that Cisco Unity Connection uses to manage calls. Call handler transfer rules can be varied based on a schedule, and schedules can be applied to routing rules to change call-routing patterns for different time periods. Schedules also affect when user and call handler greetings play.
Cisco Unity Connection offers three predefined schedules: All Hours, Weekdays, and Voice Recognition Update. All can be modified, but not deleted. By default, the Weekdays schedule is configured to observe standard hours from 8:00 a.m. through 5:00 p.m. (0800 through 1700), Monday through Friday. The schedule is also configured to observe the predefined holiday schedule, which does not contain any dates or times by default.
For each schedule that is created or modified, multiple ranges of hours and days make up the standard and closed hours. The definition of these ranges is as follows:
![]() Standard hours: The standard hours and days make up the normal business hours, when the organization is open. Standard hours can include multiple time ranges and different time ranges on different days. For example, standard hours for an organization might be Monday through Friday from 8:00 a.m. (0800) to noon (1200) and 1:00 p.m. to 5:00 p.m. (1300 to 1700), to accommodate a lunch break, and Saturday from 9:00 a.m. to 1:00 p.m. (0900 to 1300). Standard transfer rules are in effect during the days and time ranges that are added to the standard schedule; standard user and call handler greetings play during standard hours.
Standard hours: The standard hours and days make up the normal business hours, when the organization is open. Standard hours can include multiple time ranges and different time ranges on different days. For example, standard hours for an organization might be Monday through Friday from 8:00 a.m. (0800) to noon (1200) and 1:00 p.m. to 5:00 p.m. (1300 to 1700), to accommodate a lunch break, and Saturday from 9:00 a.m. to 1:00 p.m. (0900 to 1300). Standard transfer rules are in effect during the days and time ranges that are added to the standard schedule; standard user and call handler greetings play during standard hours.
![]() Closed hours: The hours and days that are not identified as standard hours are considered nonbusiness hours, when the organization is closed. Closed user and call handler transfer rules operate at all times—including holidays—that are not specified by the standard schedule. Closed user and call handler greetings play according to the closed hours.
Closed hours: The hours and days that are not identified as standard hours are considered nonbusiness hours, when the organization is closed. Closed user and call handler transfer rules operate at all times—including holidays—that are not specified by the standard schedule. Closed user and call handler greetings play according to the closed hours.
You can specify the holidays in advance (that is, for future years). In addition to other schedules, you can set up a holiday schedule that defines specific holiday dates and times:
![]() When a holiday schedule is in effect, Cisco Unity Connection plays holiday greetings (if enabled) and observes closed-hours transfer rules. Several years of holidays can be set up at one time. Because many holidays occur on different dates each year, confirm that the holiday schedule remains accurate annually.
When a holiday schedule is in effect, Cisco Unity Connection plays holiday greetings (if enabled) and observes closed-hours transfer rules. Several years of holidays can be set up at one time. Because many holidays occur on different dates each year, confirm that the holiday schedule remains accurate annually.
![]() Holiday greetings for users and call handlers play during this period.
Holiday greetings for users and call handlers play during this period.
Cisco Unity Connection Distribution Lists
This section explains the system distribution lists in Cisco Unity Connection and how they are used to send voice messages to multiple users. Figure 4-4 illustrates the Unity Connection system and private distribution list options.
Members of a system distribution list typically are users who need the same information regularly, such as employees in a department or members of a team. The predefined system distribution lists are the following:
![]() Undeliverable Messages
Undeliverable Messages
![]() All Voice Mail Users
All Voice Mail Users
![]() All Voicemail-Enabled Contacts
All Voicemail-Enabled Contacts
A voicemail user can configure private distribution lists. An administrator can define a maximum of 99 private distribution lists per user; the default is 25.
Within the private distribution list, the number of members can be set to a maximum of 999; the default is 99.
Cisco Unity Connection Authentication
This section describes the authentication rules that are used to secure access to Cisco Unity Connection.
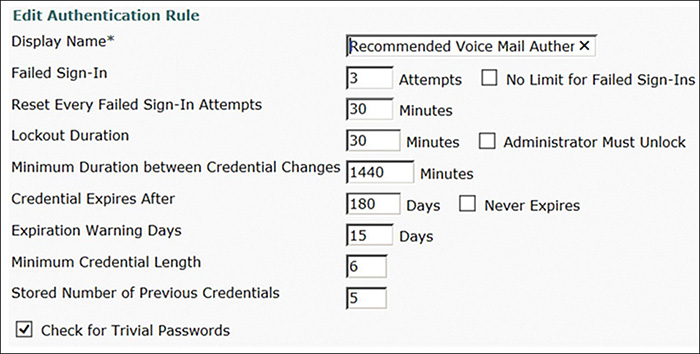
For Cisco Unity Connection users who are authenticated by an LDAP directory, this authentication rule applies only to voicemail passwords (PINs). The LDAP directory, rather than Cisco Unity Connection, manages web authentication and failed sign-in attempts. For Cisco Unity Connection users who are not linked to user data in an LDAP directory, this authentication rule applies both to voice-mail passwords and to web passwords. Figure 4-5 shows the different authentication rule options.
The following settings can be configured under System Settings > Authentication Rules section of the Cisco Unity Connection Administration:
![]() Display Name: Enter a descriptive name for the authentication rule.
Display Name: Enter a descriptive name for the authentication rule.
![]() Failed Sign-In: Enter the number of failed sign in attempts that are allowed before an account is locked. When this field is set to zero, no limit is placed on the number of failed sign-in attempts, and the user will not be locked out of the account. The default setting is three attempts.
Failed Sign-In: Enter the number of failed sign in attempts that are allowed before an account is locked. When this field is set to zero, no limit is placed on the number of failed sign-in attempts, and the user will not be locked out of the account. The default setting is three attempts.
![]() No Limit for Failed Sign-Ins: Check this check box to set no limit on the number of failed sign-in attempts and prevent users from being locked out of the account.
No Limit for Failed Sign-Ins: Check this check box to set no limit on the number of failed sign-in attempts and prevent users from being locked out of the account.
![]() Reset Every Failed Sign-In Attempts: Enter the number of minutes after which Cisco Unity Connection will clear the count of failed sign-in attempts (unless the failed sign in limit is already reached and the account is locked). When this field is set to zero, a failed sign-in attempt will result in the user account being locked until an administrator manually unlocks it. The default setting is 30 minutes.
Reset Every Failed Sign-In Attempts: Enter the number of minutes after which Cisco Unity Connection will clear the count of failed sign-in attempts (unless the failed sign in limit is already reached and the account is locked). When this field is set to zero, a failed sign-in attempt will result in the user account being locked until an administrator manually unlocks it. The default setting is 30 minutes.
![]() Lockout Duration: Enter the number of minutes that a user account will remain locked after the allowed number of failed sign in attempts has been reached. While the account is locked, users cannot access Cisco Unity Connection by phone. If a value of zero is entered, the account remains locked until an administrator manually unlocks it. The default is 30 minutes.
Lockout Duration: Enter the number of minutes that a user account will remain locked after the allowed number of failed sign in attempts has been reached. While the account is locked, users cannot access Cisco Unity Connection by phone. If a value of zero is entered, the account remains locked until an administrator manually unlocks it. The default is 30 minutes.
![]() Administrator Must Unlock: Check this check box so that locked accounts will remain locked until manually unlocked by an administrator.
Administrator Must Unlock: Check this check box so that locked accounts will remain locked until manually unlocked by an administrator.
![]() Minimum Duration Between Credential Changes: Enter the number of minutes that must elapse between password changes. This setting does not apply when administrators change the password in Cisco Unity Connection Administration. The default is 240 minutes.
Minimum Duration Between Credential Changes: Enter the number of minutes that must elapse between password changes. This setting does not apply when administrators change the password in Cisco Unity Connection Administration. The default is 240 minutes.
![]() Credential Expires After: The default setting is 180 days.
Credential Expires After: The default setting is 180 days.
![]() Never Expires: Check this check box so that passwords that are based on this authentication rule never expire. Use of this check box is most applicable for low-security users or for accounts that more than one person can access. Note that when this check box is checked, users can still change passwords at any time.
Never Expires: Check this check box so that passwords that are based on this authentication rule never expire. Use of this check box is most applicable for low-security users or for accounts that more than one person can access. Note that when this check box is checked, users can still change passwords at any time.
![]() Expiration Warning Days: Enter the number of days before passwords expire that Cisco Unity Connection will warn users about that expiration. A value of zero means that Cisco Unity Connection will not warn users that a password is about to expire.
Expiration Warning Days: Enter the number of days before passwords expire that Cisco Unity Connection will warn users about that expiration. A value of zero means that Cisco Unity Connection will not warn users that a password is about to expire.
![]() Minimum Credential Length: Enter the required number of digits for user passwords. Enter a value between 1 and 64, where the default is 8 digits for the password and 6 digits for the PIN. In general, shorter passwords are easier to use, but longer passwords are more secure, so more than 8 characters (password) or 6 digits (PIN) are recommended. When the minimum credential length changes, users will be required to use the new length the next time that they change their passwords.
Minimum Credential Length: Enter the required number of digits for user passwords. Enter a value between 1 and 64, where the default is 8 digits for the password and 6 digits for the PIN. In general, shorter passwords are easier to use, but longer passwords are more secure, so more than 8 characters (password) or 6 digits (PIN) are recommended. When the minimum credential length changes, users will be required to use the new length the next time that they change their passwords.
![]() Stored Number of Previous Credentials: Enter a value for the number of previous passwords that Cisco Unity Connection stores for a user. When a user enters a new password, Cisco Unity Connection compares it to the stored passwords, and rejects it if it matches a password in the history. A value of zero means that Cisco Unity Connection will not store any previous passwords for the user. The default is five passwords.
Stored Number of Previous Credentials: Enter a value for the number of previous passwords that Cisco Unity Connection stores for a user. When a user enters a new password, Cisco Unity Connection compares it to the stored passwords, and rejects it if it matches a password in the history. A value of zero means that Cisco Unity Connection will not store any previous passwords for the user. The default is five passwords.
![]() Check for Trivial Passwords: Check this check box. The next section provides more information about trivial passwords.
Check for Trivial Passwords: Check this check box. The next section provides more information about trivial passwords.
Check for Trivial Passwords
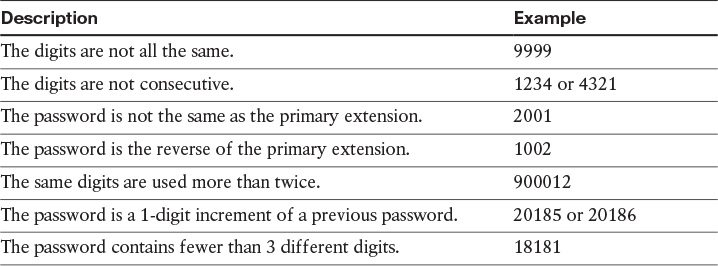
Table 4-2 gives examples of providing unsecure trivial user passwords.
To secure access to Cisco Unity Connection via TUI, check the Check for Trivial Passwords check box for the authentication rules and create a company password policy to enforce the password check. If checking for trivial passwords, Cisco Unity Connection verifies that a new password meets the system-specified criteria when user phone passwords are changed.
In addition to checking the Check for Trivial Passwords check box, consider providing users with a password policy that advises them to avoid unsupported passwords.
Roles
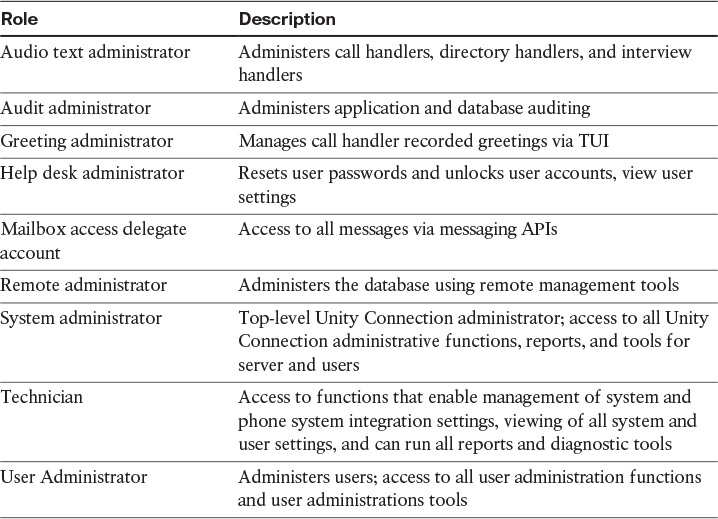
This section describes the roles that can be assigned to users in Cisco Unity Connection to give them administrator access rights for limited parts of the system.
Cisco Unity Connection offers levels of privileges for administrator accounts that are set according to a list of predefined roles as illustrated in Table 4-3. Roles specify which tasks administrators can execute. Before adding administrator accounts, choose the roles that are assigned to each account.
System administrator is the role of the default administrator account that the installer specified during initial setup of Unity Connection. A system administrator is the only role that has permission to create administrative accounts. There also is a tenant administrator.
To see the specific privileges for each administrator role, choose System Settings > Roles in Cisco Unity Connection Administration, and click the name of the role. Changes cannot be made to the permissions that are associated with each predefined role.
Cisco Unity Connection Restriction Tables
This section describes the restriction tables that can be used to prevent calls such as calls to long-distance or international phone numbers.
Cisco Unity Connection comes with predefined restriction tables, which can be modified but not deleted. By default, each of these restriction tables prevents access to long-distance phone numbers.
The following restriction tables are predefined:
![]() Default Fax: This table restricts the numbers that can be used for fax delivery.
Default Fax: This table restricts the numbers that can be used for fax delivery.
![]() Default Outdial: This table restricts the numbers that can be used for message notifications. The table also restricts the user extensions that Cisco Unity Connection can dial when the phone is chosen as the recording and playback device in the Media Master.
Default Outdial: This table restricts the numbers that can be used for message notifications. The table also restricts the user extensions that Cisco Unity Connection can dial when the phone is chosen as the recording and playback device in the Media Master.
![]() Default System Transfer: This table restricts the numbers that can be used for caller system transfers, which allow unidentified callers to transfer to a number that they specify. For example, callers might want to dial a lobby or conference room phone that is not associated with a Cisco Unity Connection user. By default, the table does not allow Cisco Unity Connection to dial any numbers.
Default System Transfer: This table restricts the numbers that can be used for caller system transfers, which allow unidentified callers to transfer to a number that they specify. For example, callers might want to dial a lobby or conference room phone that is not associated with a Cisco Unity Connection user. By default, the table does not allow Cisco Unity Connection to dial any numbers.
![]() Default Transfer: This table restricts the numbers that can be used for call transfer.
Default Transfer: This table restricts the numbers that can be used for call transfer.
![]() User-Defined and Automatically Added Alternate Extensions: This table restricts the numbers that can be offered as alternate extensions. For example, you can restrict a lobby or conference room extension so that users who often call Cisco Unity Connection from those shared phones are not automatically prompted to add the number as an alternate extension.
User-Defined and Automatically Added Alternate Extensions: This table restricts the numbers that can be offered as alternate extensions. For example, you can restrict a lobby or conference room extension so that users who often call Cisco Unity Connection from those shared phones are not automatically prompted to add the number as an alternate extension.
Cisco Unity Connection LDAP Integration
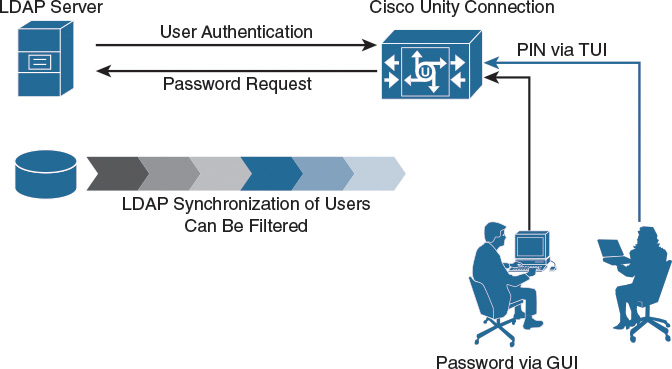
This section describes the components of LDAP integration: LDAP synchronization and LDAP authentication (as illustrated in Figure 4-6).
LDAP integration comprises two parts. In LDAP synchronization, users are imported from the LDAP server to Cisco Unity Connection. Cisco Unity Connection cannot copy any information to the LDAP server. In LDAP authentication, users can use the domain password to log in to Cisco Unity Connection user pages. However, the PIN is always kept local in Cisco Unity Connection.
Import of Users from LDAP Server
This section explains how to import users from an LDAP server.
To import users from LDAP, activate the Cisco DirSync service under Tools > Service Activation in Cisco Unified Serviceability.
To set up the LDAP system, configure the following parameters under the section System Settings > LDAP in the Cisco Unity Connection Administration:
![]() Enable Synchronizing from LDAP Server: Check this check box so that Cisco Unity Connection gets basic information about Cisco Unity Connection users from the LDAP directories that are specified on the LDAP Directory configuration page.
Enable Synchronizing from LDAP Server: Check this check box so that Cisco Unity Connection gets basic information about Cisco Unity Connection users from the LDAP directories that are specified on the LDAP Directory configuration page.
![]() LDAP Server Type: Choose the type of LDAP server from which Cisco Unity Connection will import the user data.
LDAP Server Type: Choose the type of LDAP server from which Cisco Unity Connection will import the user data.
![]() LDAP Attribute for User ID: Choose the field in the LDAP directory that should appear in the Alias field in Cisco Unity Connection for imported LDAP users. sAMAccountName specifies, for example, jdoe as the user alias. If you want to integrate with multiple domains, use the userPrincipalName (for example, [email protected]).
LDAP Attribute for User ID: Choose the field in the LDAP directory that should appear in the Alias field in Cisco Unity Connection for imported LDAP users. sAMAccountName specifies, for example, jdoe as the user alias. If you want to integrate with multiple domains, use the userPrincipalName (for example, [email protected]).
The LDAP directory configuration is like the CUCM LDAP directory configuration. The configuration requires the following LDAP directory settings:
![]() LDAP Manager Distinguished Name and LDAP Password: Enter the name and password of an LDAP directory administrator account that has access to data in the LDAP user search base that is specified in the LDAP User Search Base field.
LDAP Manager Distinguished Name and LDAP Password: Enter the name and password of an LDAP directory administrator account that has access to data in the LDAP user search base that is specified in the LDAP User Search Base field.
![]() LDAP User Search Base: Enter the LDAP directory location that contains the user data that should be synchronized with Cisco Unity Connection user data. Cisco Unity Connection imports all users in the tree or subtree (domain or organizational unit) that the search base specifies.
LDAP User Search Base: Enter the LDAP directory location that contains the user data that should be synchronized with Cisco Unity Connection user data. Cisco Unity Connection imports all users in the tree or subtree (domain or organizational unit) that the search base specifies.
The synchronization can be done once or on a regular basis:
![]() Perform Sync Just Once: Check this check box to resynchronize user data in the Cisco Unity Connection database and in the LDAP directory one time, rather than at regular intervals.
Perform Sync Just Once: Check this check box to resynchronize user data in the Cisco Unity Connection database and in the LDAP directory one time, rather than at regular intervals.
![]() Perform a Re-Sync Every: To resynchronize user data in the Cisco Unity Connection database with user data in the LDAP directory at regular intervals, specify the frequency with which the resynchronizations should occur. The minimum interval is 6 hours. The first resynchronization occurs on the date and time that is specified in the Next Re-Sync Time field.
Perform a Re-Sync Every: To resynchronize user data in the Cisco Unity Connection database with user data in the LDAP directory at regular intervals, specify the frequency with which the resynchronizations should occur. The minimum interval is 6 hours. The first resynchronization occurs on the date and time that is specified in the Next Re-Sync Time field.
These fields can be synchronized with an LDAP server:
![]() User ID: The value of the LDAP field that is listed here is stored in the Alias field in the Cisco Unity Connection database. The field that is listed here was specified on the LDAP Setup page, in the LDAP Attribute for User ID list.
User ID: The value of the LDAP field that is listed here is stored in the Alias field in the Cisco Unity Connection database. The field that is listed here was specified on the LDAP Setup page, in the LDAP Attribute for User ID list.
![]() Middle Name: Choose which value from the LDAP directory to store here: middleName or initials.
Middle Name: Choose which value from the LDAP directory to store here: middleName or initials.
![]() Manager ID: The value of the manager field in the LDAP directory is always stored in the Manager ID field in the Cisco Unity Connection database.
Manager ID: The value of the manager field in the LDAP directory is always stored in the Manager ID field in the Cisco Unity Connection database.
![]() Phone Number: Choose which value from the LDAP directory to store here: telephoneNumber or ipPhone.
Phone Number: Choose which value from the LDAP directory to store here: telephoneNumber or ipPhone.
![]() Title: Synchronize the title.
Title: Synchronize the title.
![]() Mobile Number: Synchronize the mobile number that is stored in the attribute mobile.
Mobile Number: Synchronize the mobile number that is stored in the attribute mobile.
![]() Directory URI: Synchronize the URI from the msRTCSIP-primaryuseraddress or mail. You may select None to not synchronize this parameter.
Directory URI: Synchronize the URI from the msRTCSIP-primaryuseraddress or mail. You may select None to not synchronize this parameter.
![]() First Name: The value of the givenName field in the LDAP directory is always stored in the First Name field.
First Name: The value of the givenName field in the LDAP directory is always stored in the First Name field.
![]() Last Name: The value of the sn field (surname) in the LDAP directory is always stored in the Last Name field. Without this parameter defined in the LDAP server, the user is not listed in the import result window.
Last Name: The value of the sn field (surname) in the LDAP directory is always stored in the Last Name field. Without this parameter defined in the LDAP server, the user is not listed in the import result window.
![]() Department: The value of the department field in the LDAP directory is always stored in the Department field. The value of the department field in the LDAP directory is always stored in the Department field.
Department: The value of the department field in the LDAP directory is always stored in the Department field. The value of the department field in the LDAP directory is always stored in the Department field.
![]() Mail ID: Choose which value from the LDAP directory to store here: mail or sAMAccountName.
Mail ID: Choose which value from the LDAP directory to store here: mail or sAMAccountName.
![]() Home Number: A configured home number is synchronized.
Home Number: A configured home number is synchronized.
![]() Pager Number: A configured pager number can be synchronized as well.
Pager Number: A configured pager number can be synchronized as well.
In addition to these parameters, you can synchronize up to five custom attributes. In the group information section, you can specify a mask to apply to synced telephone numbers to create a new line for inserted users.
Finally, set the LDAP server parameters IP address and port 389. To point to a Microsoft Global Catalog, use port 3268 instead. The connection to the LDAP server should be secured. Cisco Unity Connection uses port 636 when you choose LDAPS for the protocol used to communicate with domain controllers. If you are using Secure Sockets Layer (SSL) to encrypt data that is transmitted between the LDAP server Global Catalog and the Cisco Unity Connection server, the port 3269 is used.
To start the import process, select the LDAP server from which you want to import users. If you do not see any users, the LDAP server has not been successfully synchronized with Cisco Unity Connection. In addition, users without a last name that is configured in the LDAP server are not displayed in this import list.
When all issues are resolved, choose the voice-mail template that you want to apply. Choose the users whom you want to import and start the import process. Also, you can import all users rather than choosing individual users.
Imported User
Compared to a manually configured user, the Alias, First Name, and Last Name fields for an imported user are read-only fields. If you want to change these field parameters, you must make the change in the LDAP server.
You can also convert the LDAP integrated user to a local user as shown in Figure 4-7. This process can be reversed by integrating a local user with the LDAP server. However, both of these processes must be done manually. CUCM works differently. Local users are automatically converted to LDAP users (again) after the next LDAP synchronization.
You can modify the extension number for single users. For multiple users, you can automate this process in the advanced LDAP settings.
Phone Number Conversion
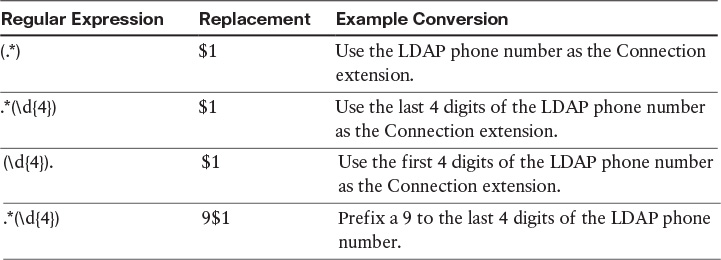
This section describes how to automatically convert the synchronized extension of LDAP users.
If you want to map phone numbers in the LDAP directory to extensions in Cisco Unity Connection but the phone numbers do not match the extensions, you can add a regular expression and a replacement pattern that together convert the phone numbers into extensions, as shown in Table 4-4.
The following are the mechanisms of regular expressions.
![]() The regular expression determines which phone numbers to operate on (for example, phone numbers that are ten digits long) and the portion of the phone numbers to use as a basis for the extensions (for example, the last four digits).
The regular expression determines which phone numbers to operate on (for example, phone numbers that are ten digits long) and the portion of the phone numbers to use as a basis for the extensions (for example, the last four digits).
![]() The replacement pattern specifies to use either the values selected by the regular expression or to perform additional operations (for example, prefix a 9).
The replacement pattern specifies to use either the values selected by the regular expression or to perform additional operations (for example, prefix a 9).
Cisco Unity Connection uses the regular expression package of the Java library. Table 4-4 lists some examples of the conversions that are possible with the expanded functionality.
Note the following:
![]() Cisco Unity Connection automatically removes nonnumeric characters from the phone number, so the regular expression does not need to account for nonnumeric characters.
Cisco Unity Connection automatically removes nonnumeric characters from the phone number, so the regular expression does not need to account for nonnumeric characters.
![]() LDAP phone numbers are converted to Cisco Unity Connection extensions only once, when you first synchronize Cisco Unity Connection data with LDAP data. On subsequent, scheduled synchronizations, values in the Cisco Unity Connection Extension field are not updated with changes to the LDAP phone number. As a result, you can change the LDAP phone number as required, including specifying a completely different number, and the extension will not be overwritten the next time that Cisco Unity Connection synchronizes data with the LDAP directory.
LDAP phone numbers are converted to Cisco Unity Connection extensions only once, when you first synchronize Cisco Unity Connection data with LDAP data. On subsequent, scheduled synchronizations, values in the Cisco Unity Connection Extension field are not updated with changes to the LDAP phone number. As a result, you can change the LDAP phone number as required, including specifying a completely different number, and the extension will not be overwritten the next time that Cisco Unity Connection synchronizes data with the LDAP directory.
![]() You can write more than one combination of a regular expression and a replacement pattern that produces the same result.
You can write more than one combination of a regular expression and a replacement pattern that produces the same result.
Search Base
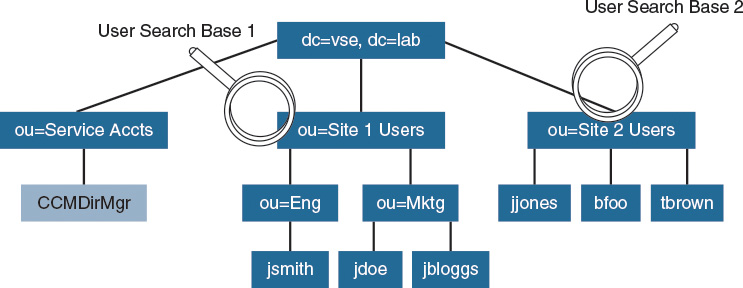
This section explains the search base for the user selection and synchronization.
The Cisco DirSync service, which is enabled through the Cisco Unity Connection Serviceability web page, performs the synchronization. When the service is enabled, as many as five synchronization agreements can be configured in Cisco Unity Connection.
An agreement specifies a search base, which is a position in the LDAP tree where Cisco Unity Connection will begin its search for user accounts to import. Cisco Unity Connection can import only users that exist in the domain that is specified by the search base for a particular synchronization agreement. Figure 4-8 shows two synchronization agreements:
![]() One synchronization agreement specifies User Search Base 1 and imports users jsmith, jdoe, and jbloggs.
One synchronization agreement specifies User Search Base 1 and imports users jsmith, jdoe, and jbloggs.
![]() The other synchronization agreement specifies User Search Base 2 and imports users jjones, bfoo, and tbrown.
The other synchronization agreement specifies User Search Base 2 and imports users jjones, bfoo, and tbrown.
The CCMDirMgr account is not imported because it does not reside below the point in the LDAP tree that the user search base specifies.
When users are organized in a structure in the LDAP directory, use that structure to control which user groups are imported. In this example, a single synchronization agreement could have been used to specify the root of the domain. However, that search base would also have imported the Service Accts (except when the sn fields were empty). The search base does not need to specify the domain root; it may specify any point in the tree.
LDAP Filter
This section explains how an LDAP filter is used to optimize the user selection and synchronization results.
You can configure only five search agreements. If you need more than five search agreements, you must point the search agreement to the root domain in combination with LDAP filters. With these filters you can, for example, only import users from certain subdomains or from certain locations. Filters give you more scalability for importing users from large LDAP directories with many subdomains and organizational units.
Table 4-5 describes the search filter syntax that can be used for the LDAP filter in the LDAP directory configuration. Search filters allow the definition of search criteria and provide more efficient and effective searches. Unicode strings represent these search filters.
These are some examples of LDAP search filters.
Table 4-6 lists frequently used search filter operators.
To match a part of a directory number (for example, to look for the groups in two subtrees), use a filter such as the following:
(&(objectClass=group)(|(ou:dn:=Chicago)(ou:dn:=Miami)))
This filter will find groups that have an organizational unit component in the directory number (DN), which is either Chicago or Miami.
To exclude entities that match an expression, use an exclamation point (!):
(&(objectClass=group)(&(ou:dn:=Chicago)(!(ou:dn:=Boston))))
This filter will find all Chicago groups except those that have a Boston organizational unit component. Note the extra parentheses: (!(<expression>)).
After creating the filter, apply the filter in the LDAP directory configuration. Because only one filter can be selected in the LDAP directory configuration, more organizational units or other objects must be added to the filter. The filter can contain a maximum of 2048 characters. Enclose the filter text within parentheses ( ).
The LDAP filter filters the results of LDAP searches. LDAP users that match the filter are imported into the Cisco Unity Connection database, whereas LDAP users that do not match the filter are not imported. The filter text that is entered must comply with the regular LDAP search-filter standards that are specified in RFC 4515. You should verify the LDAP search filter against the LDAP directory and search base.
Note
You can test the filter with LDAP browsers; for example, you can test with Softerra LDAP Administrator at http://www.ldapadministrator.com/.
Import of Users from CUCM
This section shows the import process for users that are located on CUCM.
To import users from CUCM, activate the Cisco Administrative XML (AXL) service on CUCM. Then configure the AXL server in the phone system configuration. Add a new AXL server with the IP address of the CUCM and the port number 8443. Then enter the username and password of the CUCM application user.
Users who are not configured with a primary extension cannot be imported. Go to the end-user configuration in CUCM and set the primary extension. Then go back to Cisco Unity Connection and try the import process again. Users who are already configured in Cisco Unity Connection are not shown during the import process.
Importing users from CUCM has the advantage that all users are already synchronized and filtered from the LDAP directory. The preferred way of selecting the user source is to have the primary extension number that is configured for all users.
Imported CUCM User
Figure 4-9 shows the CUCM imported user configuration. In contrast with an LDAP synchronized user, the Extension field is also a read-only field. If you want to change these parameters, you must make the change in CUCM. CUCM imported users cannot be migrated to LDAP synchronized users. The LDAP integration status cannot be modified.
![]() Cisco Unity Connection system settings are the core of the Cisco Unity Connection configuration. These settings control integrations, enterprise and service parameters, access rights to Cisco Unity Connection and so on.
Cisco Unity Connection system settings are the core of the Cisco Unity Connection configuration. These settings control integrations, enterprise and service parameters, access rights to Cisco Unity Connection and so on.
![]() During the installation, the correct time zone is set. This time zone controls the schedules and holidays and which greeting or transfer rule is active.
During the installation, the correct time zone is set. This time zone controls the schedules and holidays and which greeting or transfer rule is active.
![]() Use the authentication rules to secure the access to Cisco Unity Connection via GUI or TUI. Enable the check for trivial passwords. For administrator access, predefined roles are set up. The system administrator has the most powerful access.
Use the authentication rules to secure the access to Cisco Unity Connection via GUI or TUI. Enable the check for trivial passwords. For administrator access, predefined roles are set up. The system administrator has the most powerful access.
![]() Restriction tables can be used to restrict caller transfer or message notification to certain numbers. By default, international and long-distance numbers are disallowed.
Restriction tables can be used to restrict caller transfer or message notification to certain numbers. By default, international and long-distance numbers are disallowed.
![]() By using LDAP synchronization, you can import users from an LDAP server to Cisco Unity Connection. Cisco Unity Connection cannot copy data to the LDAP server. When using LDAP authentication, users can log in to the user pages by entering the domain password.
By using LDAP synchronization, you can import users from an LDAP server to Cisco Unity Connection. Cisco Unity Connection cannot copy data to the LDAP server. When using LDAP authentication, users can log in to the user pages by entering the domain password.
![]() You can also import users from the CUCM, because you can assume that the CUCM user base is already optimized.
You can also import users from the CUCM, because you can assume that the CUCM user base is already optimized.
Review Questions
Answer the following questions, and then see Appendix A, “Answers to Review Questions,” for the answers.
1. What is the default maximum greeting length (in seconds) in Cisco Unity Connection?
a. 60
b. 90
c. 120
d. 180
e. 300
2. What does the question mark (?) mean when configuring patterns in restriction tables?
a. Match zero or more digits
b. Match exactly one digit
c. Match one or more digits
d. None of the above
3. Which configuration is the correct LDAP user search base configuration for a default domain cisco.com?
a. dc=Users, dc=cisco, dc=com
b. cn=Users, dc=cisco, dc=com
c. cn=Users, cn=cisco, dc=com
d. cn=Users, cn=cisco, cn=com
4. Which option is a userPrincipalName?
a. jdoe
d. None of the above
5. Which LDAP filter would you use to filter on the last name Doe?
a. (sn=doe)
b. (ln=doe)
c. !(sn=doe)