Encrypting with Symmetric Keys
In cryptography, messages are encrypted using keys, which are strings to make the original message gobbledygook. Broadly speaking, the keys are of two types:
-
Symmetric key algorithms where both the sender and receiver use the same key to encrypt and decrypt messages. In classical cryptography, the Advanced Encryption Standard (AES)[50] is a widely used symmetric key algorithm.
-
Asymmetric Key algorithms use different keys for encrypting and decrypting messages. These algorithms, such as RSA,[51] are also called public/private key algorithms since one of the keys is publicly known. Using the public key, anyone can encrypt a message, but only the intended receiver can decrypt it based on the private key. These algorithms are used, for instance, to send encrypted information, such as credit card transactions, over the web. With asymmetric cryptography, the key distribution is moot since the public key is well known and doesn’t have to be kept secret.
Both types of algorithms are secure. Though with symmetric key algorithms, you have the additional burden of ensuring that the secret key is first securely communicated to the receiver. But, as we’ll see, with quantum computing, safely delivering keys is assured.
Once a secret key is generated, the message can be encrypted by adding the secret key to the message doing modulo-2 addition, for example, on each bit. In modulo-2 addition, you add each bit of the message with the corresponding bit of the secret key but throw out the carry over. Thus,
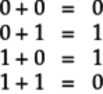
So if your message is 0110101001 and the secret key is 0101010101, then the encrypted message is:

The encrypted message 0011111100 is sent to the receiver, who then decrypts it by subtracting the secret key to recover the original message:

Despite the simplicity of symmetric key methods, if the key is used just once, it’s highly resistant to attacks.
The concepts of quantum cryptography are, at first sight, strange. So that you don’t get lost in the minutiae, we next outline the main ideas that’ll help frame the subsequent discussion. We’ll call it the Tell-Your-Boss version, as it’s a quick way to get across the key concepts without going into details.
